Cisco Secure Access Data Sheet
Available Languages
Bias-Free Language
The documentation set for this product strives to use bias-free language. For the purposes of this documentation set, bias-free is defined as language that does not imply discrimination based on age, disability, gender, racial identity, ethnic identity, sexual orientation, socioeconomic status, and intersectionality. Exceptions may be present in the documentation due to language that is hardcoded in the user interfaces of the product software, language used based on RFP documentation, or language that is used by a referenced third-party product. Learn more about how Cisco is using Inclusive Language.
Protect your hybrid workforce with cloud-agile security
Hybrid work and Security Service Edge
The new era of hybrid work requires a revised approach to security, and SSE (Security Service Edge) is a key enabler of any organization’s hybrid-work strategy. SSE combines multiple security functions in the cloud to both protect employees, contractors or partners who work from any location as well as safeguard critical resources. Whether sessions involve applications in private data centers, SaaS locations, peer-to-peer, IaaS or Internet sites, SSE acts as a ‘security intermediary’ to identify and prevent multiple types of malicious activity. End users are assured of a secure, transparent user experience, anywhere they work — office, home, or on the road. SSE solutions must address three principal requirements: Deliver a superior user experience, reduce IT complexity, and improve security efficacy.
Cisco Secure Access is a converged cloud security SSE solution, grounded in zero trust, that provides seamless, transparent, and secure access from anything to anywhere. Cisco's award-winning Umbrella secure internet access solution has been expanded under the broader Secure Access name to cover a larger set of SSE related functions. It now includes all of the core SSE components (SWG, CASB, ZTNA, and FWaaS) plus an extended set of capabilities (multimode DLP, DNS Security, RBI, sandboxing, DEM insights, Talos threat intelligence and measures to secure the use of AI.) in one license and management platform. By leveraging these capabilities, all under one cloud-delivered platform, organizations can solve a variety of security challenges. Users can now safely and seamlessly access all the resources and apps they need, regardless of protocol, port, or level of customization.
Cisco Secure Access is designed with common administrative controls, data structures, and policy management that eases interoperability with other synergistic components. For instance, a wide variety of identity providers (IDPs) including any SAML based service (including AD, Azure AD, Okta, Ping, etc.) to provide identity confirmation and context. This solution works with other Cisco offerings including SD-WAN, XDR and digital experience monitoring as well as third party technologies to improve customer outcomes.
Secure Access enforces modern cybersecurity, while fundamentally reducing risk, radically simplifying IT operational complexity, and minimizing tasks performed by end-users.
Better for users
Cisco Secure Access dramatically improves the user experience to remove friction, overcomes potential side-stepping of necessary security procedures, and increases productivity. The solution utilizes a unified client that simplifies the way users connect; they authenticate and go straight to the desired application. Such an “all-access” feature automatically connects them with least privileged concepts, preconfigured security policies and adaptable enforcement measures that administrator’s control.
Whether sessions utilize ZTNA or VPNaaS for specific non-standard apps, users don’t need to take extra steps. Repeating cumbersome verification tasks over and over is prevented. This minimizes the user hassles related to such concerns as what access method is required for different resources, if a separate client needs to be launched, or a different sign-on process stipulation, is eliminated. Centralized access to all applications greatly eases the process users take to connect, ensures security, including user and device posture validation, and improves productivity.
Easier for IT
IT teams today struggle with integrating a plethora of security tools, require multiple management consoles and policy engines, and need to deploy and manage several software agents for each end-user device. These challenges are magnified by the separate reporting, alerts and incidents that arise from each security point product.
Cisco Secure Access simplifies and automates operations for security and IT teams via a single, cloud-managed console, unified client, centralized policy creation process, and aggregated reporting. Now instead of deploying numerous disparate products, IT only needs to manage one tool. This translates into measurable efficiency gains, resulting in cost reductions and a flexible IT environment that supports greater business agility. IT can now more rapidly detect and block threats, expedite investigations, and minimize remediation tasks, all while improving visibility into end user activity with less manual aggregation tasks. This enables granular, context aware control for users or groups from various locations to multiple destinations (internet, SaaS apps, private apps) including managed and unmanaged devices.
Safer for everyone
Cisco Secure Access provides industry leading security efficacy for both end users and on-premises resources. The extended capabilities of its defense-in-depth architectural approach secures against a diverse set of cybersecurity threats. End-users are protected from risks such as infected files, nefarious websites as well as phishing and ransomware schemes. IT and security teams can reduce the attack surface, enforce least privilege controls, enable posture validation, and eliminate security gaps in distributed environments.
Security teams can obtain visibility into unauthorized shadow IT operations and unsanctioned applications usage and block such activities. By cloaking internal resources and preventing hackers from discovering their presence, IT achieves an extra layer of security. All this functionality is backed by Cisco Talos threat intelligence with its unrivaled telemetry, extensive research, and advanced AI to identify and help stop threats and speed remediations. By mitigating risk, organizations maintain business continuity and avoid the reputation and financial impact of a breach.
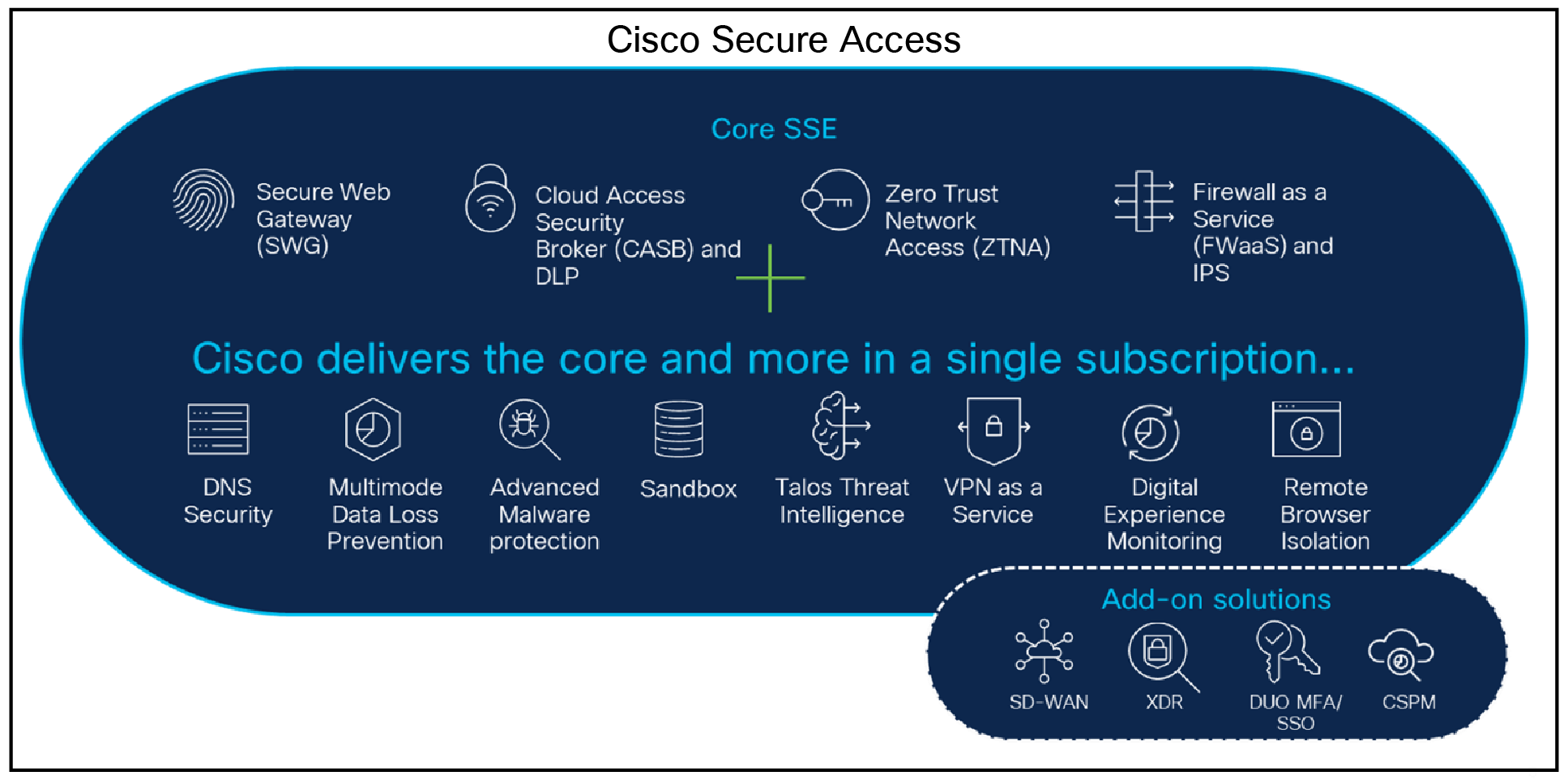
Go beyond core Security Service Edge (SSE) to better connect and protect your business
Table 1. Features and Benefits
| Feature |
Benefit |
| Zero Trust Network Access (ZTNA) |
Provide granular, app-specific access to private applications in on-premises data centers or in cloud/IaaS environments. Based on defined access control policies, its Identity aware proxy design uses least privilege principles and contextual insights to granularly deny access by default and brokers user access to applications when explicitly granted, irrespective of location.
●
Two access methods: Client-based and clientless browser–based access, granular user, and application-based access policy, SAML authentication, Identity Provider (IdP), and contextual access control.
●
Client-based access leverages the unified Cisco Secure Client.
●
Establishes per-session secure access after a device posture check is performed.
●
Authenticates users through a secure, encrypted tunnel, allowing users to see only applications and services they have permission to access.
●
Application proxy provides transparent, secure remote access without exposing the applications to the Internet. It even hides the network details of private apps from the clients accessing those apps. This prevents attackers from learning anything from IP reconnaissance even if they have compromised a client device.
●
Prevents lateral attacker movement.
●
Implements location and device-specific access control policies, preventing possibly compromised devices from connecting to its services.
●
Administrators assign access privileges for contractors and employees only to resources they need access to, without any lateral move capability.
●
Administrators can configure posture profiles for endpoint OS type and version, browser type and version, and geolocation information to be used in the access decision.
●
Provides user with helpful information explaining the cause of denied access and offers suggested remediation steps.
●
Administrator may revoke ZTNA access for specific user and device combinations through the dashboard.
●
Administrators can enforce additional user authentication for specific applications through setting a maximum authentication interval for those applications.
|
| VPNaaS |
Not all private apps can be covered by ZTNA. A VPNaaS cloud-based option is included for secure remote access as well as secure internet access for non-web internet traffic.
● Functionality examples include: Use case support (split tunneling and tunnel all support, peer-to-peer communication, trusted network detection, BYO certificate, split DNS, dynamic split DNS); multiple authentication methods (SAML, Certificate, Radius); user ease of use (always on VPN, start before logon); IT operation simplification (Local IP Pool, multiple VPN profiles).
● Enables remote users to access private applications via the Security Access fabric using the Cisco Secure Client.
● Identity-based access control is available using SAML authentication through the customer’s IdP.
● Endpoint posture is also evaluated; this enables granular access control to private resources.
● Supports granular per application access control.
● Simplifies connectivity with no need to select head-end or tunnel type.
● Supports a management tunnel that is used to enable users to bring up a VPN tunnel and seamlessly authenticate to on-premises Active Directory when logging into PCs and performing password resets.
● Management tunnel can be used by desktop management teams to download software updates to PCs without user VPN login.
● Integration with Identity Services Engine (ISE) and support for RADIUS authentication.
|
| Secure Web Gateway (full proxy) |
Log and inspect all web traffic over ports 80/443 for greater transparency, control, and protection. IPsec tunnels, PAC files and proxy chaining are used to forward traffic for full visibility, URL and application-level controls, and advanced threat protection.
●
Content filtering by category or specific URLs to block destinations that violate policies or compliance regulations.
●
Scan all downloaded files for malware and other threats.
●
Sandboxing with Cisco Secure Malware Analytics analyzes unknown files (see dedicated section for Cisco Secure Malware Analytics).
●
File type blocking (e.g., block download of .exe files).
●
Full or selective TLS decryption to protect from hidden attacks and time-consuming infections.
●
Granular app controls to block specific user activities in select apps (e.g., file uploads to Dropbox, attachments to Gmail, post/shares on Facebook).
●
Detailed reporting with full URL addresses, network identity, allow or block actions, plus the external IP address.
●
Multimode protection of internet-based SaaS apps with customizable controls and traffic path options.
|
| Cloud access security broker (CASB) |
Expose shadow IT by detecting and reporting on cloud applications, including generative AI apps, in use. Manage cloud adoption, reduce risk, and block the use of offensive, non-productive, risky, or inappropriate cloud applications. Multimode capabilities to detect, log and control user/group activities.
● Data loss prevention (DLP) to block sensitive enterprise data in the cloud or in outbound web traffic from leaking to unauthorized persons. (see separate DLP section).
● Reports on vendor category, application name, and volume of activity for each discovered app.
● App details and risk information such as web reputation score, financial viability, and relevant compliance certifications.
● Cloud malware detection to detect and remove malware from cloud-based file storage applications.
● Ability to block/allow specific cloud applications.
● Tenant restrictions to control the instance(s) of SaaS applications that all users or specific groups/individuals can access.
● Discover and control usage or attempted usage of 70+ generative AI applications. Block usage or create and enforce policies to control how these apps are used.
|
| Data Loss Prevention (DLP) |
Multimode data loss prevention. Analyze sensitive data in-line to provide visibility and control over sensitive data leaving your organization. API-based DLP functionality for out-of-band analysis of data at rest in the cloud. Includes unified policies and reporting for more efficient administration and regulatory compliance.
●
600+ built-in identifiers for compliance with PII, PHI, PCI, and other regulations, plus built-in data classifications for HIPAA, PCI, GDPR, and PII.
●
Customizable built-in content classifiers with threshold and proximity to tune and reduce false positives.
●
User-defined dictionaries with custom phrases (such as project code names).
●
Detection and reporting on sensitive data usage and drill-down reports to help identify misuse.
●
Ability to assign DLP policies to AI applications to help users more safely use publicly available AI services like ChatGPT, protecting against IP loss or IP contamination by detecting and blocking risky content.
●
Inspection of cloud app and web traffic content and enforcement of data policies.
●
API-based functionality supports Microsoft 365 (SharePoint and OneDrive), Google Drive, Webex, Box, and Dropbox.
●
For ChatGPT block uploads of proprietary source code to prevent its leakage to unauthorized users.
●
Block the download of content produced from ChatGPT to prevent users from generating source code in ChatGPT, downloading it and committing it to an organizational code repository.
|
| Firewall as a Service (FWaaS) |
Provides visibility and control for non-web traffic that originated from requests going to the internet, across all ports and protocols. Includes mobile apps, peer-to-peer file sharing, collaboration (e.g., Webex or ZOOM), O365, or any non-web or non-DNS traffic.
● Deployment, management and reporting through the Security Access single, unifieddashboard.
● Customizable policies (IP, port, protocol, application and IPS policies)
● Layer 3 / 4 firewall to log all activity and block unwanted traffic using IP, port, andprotocol rules.
● Scalable cloud compute resources eliminate appliance capacity concerns.
● Layer 7 application visibility and control to Identify a growing base of over 2,800 non-web applications and selectively block or allow.
● Decrypts traffic prior to inspection.
|
| Intrusion prevention system (IPS) |
IPS examines network traffic flows and prevents vulnerability exploits with an added layer of threat prevention using SNORT 3 technology and signature-based detection.
●
Using a unified dashboard, create policies to examine traffic and take automated actionsto catch and drop dangerous packets before they reachthe network.
●
Provides IPS protection for both internet and private traffic.
●
Configure access-policies and options for different custom profiles depending on trafficdestination.
●
Uses an extensive and growing base of over 40,000 signatures fromCisco Talos.
●
Signatures are available in pre-defined templates.
●
Detection and blocking of vulnerability exploitation.
|
| Cisco Secure Malware Analytics |
Combines advanced sandboxing with threat intelligence into one unified solution to protect organizations from malware. Provides access to the full Secure Malware Analytics console, enabling execution of malicious files in a glovebox, track file execution actions, and capture network activity generated by the file. When combined with Investigate, security analysts may go further and uncover malicious domains, IPs, ASNs mapped to a file’s actions to get the most complete view of an attackers’ infrastructure, tactics, and techniques.
● Ability to detect hidden attack methods and report on malicious files.
● APIs to integrate with XDR and commonly used SIEMs for enrichingsecurity data.
● Retrospective notification if file disposition changes (originally good / later deemed malicious).
|
| Remote Browser Isolation (RBI) |
RBI protects users and organizations from browser-based threats. It shifts the execution of browsing activity from the user to a remote cloud-based virtualized browser instance to protect from Internet threats. Website code is run separately and only a safe visual stream is delivered to the user. This is fully transparent to the end user. No need to worry about malware that hasn't been detected yet.
●
Isolation of web traffic between user device and browser-based threats
●
Protection from zero-day threats.
●
Granular controls for different risk profiles
●
•Rapid deployment without changing existing browser configuration.
●
On-demand scale to easily protect additional users.
●
Protect employees who may need to access known risky internet sites. Productivity isnot reduced due to blocking and users stay safe.
|
| DNS-layer security |
Enforces filtering at the DNS layer to block requests to malicious and unwanted destinations before a connection is established. Blocks threats over any port or protocol before they reach the network or endpoints.
● Protects internet access across all network devices, office locations, and roaming users.
● Provides detailed reporting for DNS activity by type of security threat or web content and the action taken.
● Retains logs of all activity.
● Accelerated rollout to thousands of locations and users to provide
● immediate protection.
|
| Talos threat intelligence |
Talos, a leading provider of cutting-edge security research globally, analyzes 100s of billions of DNS requests and other telemetry data daily. It continuously runs AI, statistical, and machine learning models against this massive database to provide insight into cyber threats and improve incident response rates.
● Uncover malicious domains, IPs, malware, and URLs before they’re used in attacks.
● Prioritize incident investigations.
● Speed incident investigations and response.
● Predict future attack origins by pinpointing and mapping out attackers’ infrastructures
.
|
| Cloud malware detection |
Detects and removes malware from cloud-based file storage applications. Enriches security protection by detecting and remediating malicious files before they reach an endpoint.
● Increases effectiveness and efficiency of security administrators — Once activated, all files in cloud-based services will be hashed and sent for malware scanning automatically. Any file containing malware will be flagged so a security admin can remediate, including quarantine and/or deletion.
● Supports Box, Dropbox, Webex, Microsoft 365, and Google Drive.
|
| Single management and reporting console |
Unified security policy creation, including intent-based rules, and management across internet, public SaaS apps, and private app access. Provides extensive logging and the ability to export logs to enterprise SOC, etc.
●
Single place to define policy for any user to any app. Simplifies the process of building security policies and drives consistency in policy definition for entire org.
●
Unified source (users, devices) and unified resources (apps, destination) allow the security policy to follow the users no matter the point of attach and no matter which app is accessed.
●
Reduces on-going policy management activities.
●
Improves visibility and time-to-detection with aggregated reporting.
●
Simplifies the overall SOC/security analyst investigation process.
|
| AI Assistant* |
Secure Access AI Assistant automatically converts conversational, English phrases into specific security policies.
● Security administrators can save time, improve operational efficiency, and reduce complexity.
● Multi-person administrator groups can create a more consistent and effective policy set.
● Cost reductions and resource savings are magnified when there is a need to create large sets of policies.
|
| Resource Connectors |
Resource Connectors simply administrative tasks to setup secure connectivity to private applications. These lightweight connectors manage the connection between Cisco Secure Access and the private apps, regardless of whether they are in an on-premises data center or in the cloud. Currently, resource connectors only support AWS and VMWare environments.
●
Reduce dependency on network teams for device and firewall rule changes.
●
Avoid routing complexities, such as setting up dynamic routing or overlapping subnets.
●
In scenarios such as a merger, networks are often kept separate with overlapping IPs, etc. Using tunnels gets complex. App Connectors can shield this complexity.
●
Protects private apps by hiding their location (IP address) and only allowing connections through the zero trust policies within Security Access.
●
Prevents lateral movement by isolating resources and networks.
|
| Experience Insights: Digital Experience Monitoring (DEM) |
Monitor health and performance of endpoints, applications, and network connectivity as users access resources. Optimize user productivity, simplify troubleshooting, and reduce time to resolution of incidents by automatically mining details on the user’s end-to-end experience, enabling the IT/security staff to rapidly resolve issues. Key insight examples:
● Endpoint performance — CPU levels, memory usage, and WIFI signal strength.
● Network performance — path visualization and performance of the last mile from the endpoint to Secure Access.
● Most commonly used SaaS applications (top 20) including Outlook, Slack, Salesforce, and SharePoint.
● User specific security events.
● Collaboration application performance and user experience scores for various apps including Webex, Zoom, and Microsoft Teams.
● issues on a segment-by-segment basis with metrics such as throughput, latency, and Suggested remediations for Administrators to efficiently troubleshoot issues.
● Isolate network connectivity packet loss.
|
| Mobile device ZTA support* |
Supports highly efficient zero trust access (ZTA) from Apple iOS devices. Apple and Cisco collaborated to create a unique ZTA process with performance and security benefits.
● Secure Access provides efficient enrollment, configuration, and troubleshooting.
● Simplified deployment with no need to roll out and manage a full client on iOS devices.
● Leverages the built-in functionality within the iOS operating system.
● Utilizes QUIC and MASQUE protocols for faster transit and VPP acceleration for better throughput.
● Takes advantage of Apple’s iCloud private relay with a single layer of encryption for fast, secure access.
● Same mobile ZTA enrollment experience as with desktops.
● Administrators can view details on connected iOS devices.
Supports ZTA functions on Samsung Galaxy devices.
●
Secure Access provides the ZTA enrollment, configuration, troubleshooting, and traffic steering.
●
Utilizes QUIC and MASQUE protocols for faster transit and VPP acceleration for better throughput.
●
Same mobile ZTA enrollment experience as with desktops.
●
For troubleshooting, user can export the logs available from the client and use these logs when interacting with the helpdesk.
|
| Catalyst SD-WAN branch users accessing the internet/SaaS apps |
Integration and automation between Catalyst SD-WAN and Secure Access enables traffic steering from branch users to web and SaaS apps through Cisco Secure Access.
● Increased threat protection from Secure Access’s multi-layer security solution
● More consistent experience when users move between roaming and on-premises locations.
● Simplifies IT/security operations with Secure Access’s centralized policy administration, easy up/down scalability, and relief from capacity constraints.
|
| Identity Services Engine (ISE) integration |
This is the first instantiation of ISE and Secure Access integration that provides granular, identity-based information to deepen visibility into what users are doing, when, and how. This integration enriches policy control and enforcement for VPNaaS traffic to:
●
Enable more precise enforcement of the right policy, for the right user or device, at the right time.
●
Deliver AI analytics to detect anomalies in device posture/identity and automatically apply the correct policy.
●
Support RADIUS for authentication requests with ISE
●
Moving forward, Cisco is driving toward common identity across products and capabilities, applied wherever users work, however they connect (wired or wireless), and whatever resources they access.
|
Cisco Secure Access is the evolution of Cisco Umbrella SIG and represents our broadest SSE solution in a single subscription to drive a higher level of security across all users while improving both IT and end user productivity. It is offered in packages that make it easy for customers to choose the right level of protection and coverage for their organizational needs. There are currently two packages: Cisco Secure Access Essentials and Cisco Secure Access Advantage.
Table 2. Core Offer Package
| Category |
Features |
Secure Access Essentials |
Secure Access Advantage |
| Secure Access |
Secure Internet Access (SIA)
●
SD-WAN DIA integration
●
Secure Client (license included)
◦ Roaming Security (DNS, Web, and Firewall-as-a-Service) |
|
|
| Secure Private Access (SPA)
● Secure Client (license included)
◦ ZTNA client ◦ VPN-as-a-Service
● ZTNA clientless
|
|
|
|
| Foundational Security |
DNS Protection |
|
|
| Firewall-as-a-Service for layer 3 & layer 4 controls of web and private apps |
|
|
|
| Secure web gateway (proxy web traffic, URL filtering, content filtering, advanced app controls) |
|
|
|
| CASB - Cloud app discovery, risk scoring, blocking, cloud malware detection; tenant controls |
|
|
|
| Remote Browser Isolation (License for risky traffic only*) |
|
|
|
| Secure Malware Analytics (sandbox) |
Limited |
Limited |
|
| Digital Experience Monitoring |
Experience Insights |
|
|
| Advanced Security |
Layer 7 Firewall-as-a-Service |
|
|
| IPS protection |
|
|
|
| Data Loss Prevention (DLP) for web applications including Generative AI/ChatGPT Control |
|
|
|
| Remote Browser Isolation (Any**) |
|
|
|
| Software Support |
Support 24x7 access to Cisco Software Support-Enhanced via email and phone with optional upgrade to Software Support-Premium |
|
|
Cisco Secure Access: Software Support Service
Cisco Secure Access product purchase requires separate SKU for Software Support-Enhanced, with the option to upgrade to Software Support-Premium.
Cisco Software Support Enhanced
● Technical Support (24x7 access to Cisco Cloud Security Support - phone/on-line).
● Software updates.
● Primary point of contact with software expertise.
● Technical on-boarding and adoption assistance.
Cisco Software Support Premium (optional upgrade)
Includes Enhanced level features plus:
● Prioritized case handling over Enhanced support.
● Assigned expert who provides incident management and proactive consultation and recommendations to ensure successful security software deployment and ongoing management and optimization.
● Support case analytics.
To learn more about Cisco Support Services for Security Software, click here.
For more information, please visit: Cisco Secure Access.