Installation and Configuration of AMP Module Through AnyConnect 4.x and AMP Enabler
Available Languages
Download Options
Bias-Free Language
The documentation set for this product strives to use bias-free language. For the purposes of this documentation set, bias-free is defined as language that does not imply discrimination based on age, disability, gender, racial identity, ethnic identity, sexual orientation, socioeconomic status, and intersectionality. Exceptions may be present in the documentation due to language that is hardcoded in the user interfaces of the product software, language used based on RFP documentation, or language that is used by a referenced third-party product. Learn more about how Cisco is using Inclusive Language.
Contents
Introduction
This document goes through steps to install the Advanced Malware Protection (AMP) connector with AnyConnect.
The AnyConnect AMP Enabler is used as a medium to deploy AMP for Endpoints. Itself it does not have any capability to convict file disposition. It pushes the AMP for Endpoints software to an endpoint from ASA. Once the AMP is installed it uses cloud capacity to check for files disposition. Further AMP service can submit files to dynamic analysis called ThreatGrid, to score unknown files behaviour. These files can be convicted as malicious if certain artifacts are met. This is widely usefull for zero-day attacks.
Prerequisites
Requirements
- AnyConnect Secure Mobility Client Version 4.x
- FireAMP / AMP for Endpoints
- Adaptive Security Device Manager (ASDM) Version 7.3.2 or later
Components Used
The information in this document is based on these software and hardware versions:
- Adaptive Security Appliance (ASA) 5525 with Software Version 9.5.1
- AnyConnect Secure Mobility Client 4.2.00096 on Microsoft Windows 7 Professional 64-bit
- ASDM Version 7.5.1(112)
AnyConnect Deployment for AMP Enabler through ASA
The steps involved in the configuration are as follows:
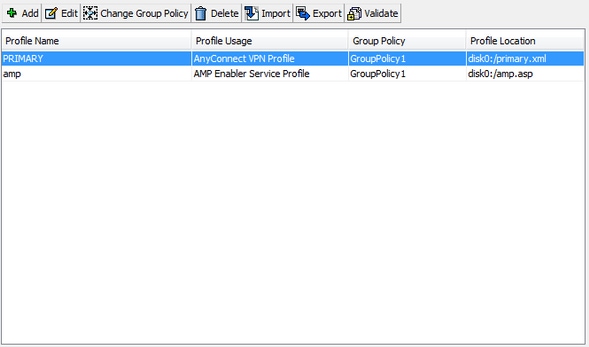
- Configure the AnyConnect AMP Enabler client profile.
- Edit the AnyConnect VPN group policy and download the AMP Enabler Service Profile.
- Login to the AMP dashboard in order to get the connector URL download link.
- Verify the installation on the user machine.
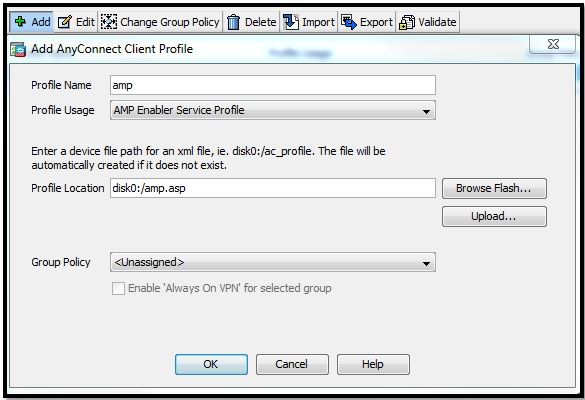
Step 1: Configure the AnyConnect AMP Enabler Client Profile
- Navigate to Configuration > Remote Access VPN > Network (Client) Access > AnyConnect Client Profile.
- Add the AMP Enabler Service Profile.
Step 2: Edit the Group-Policy to Download the AnyConnect AMP Enabler
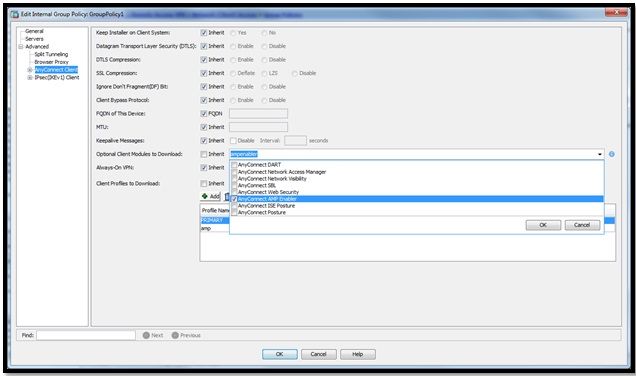
- Navigate to Configuration > Remove Access VPN > Group Policies > Edit.
- Go to Advanced > AnyConnect Client > Optional Client Modules to Download.
- Choose AnyConnect AMP Enabler.
Step 3: Download the FireAMP Policy
Note: Before you proceed, check if your system meets the requirements for the AMP of Endpoints Windows Connector.
System Requirements for AMP for Endpoints Windows Connector
These are the minimum system requirements for the FireAMP Connector based on the Windows operating system. The FireAMP Connector supports both 32-bit and 64-bit versions of these operating systems. The latest AMP documentation can be found in AMP deployment
| Operating System | Processor |
Memory |
Disk Space, Cloud Only Mode |
Disk Space |
|
Microsoft Windows 7 |
1 GHz or faster processor |
1 GB RAM |
150 MB available hard disk space - Cloud-only mode |
1GB available hard disk space - TETRA |
|
Microsoft Windows 8 and 8.1 (requires FireAMP Connector 5.1.3 or later) |
1 GHz or faster processor |
512 MB RAM |
150 MB available hard disk space - Cloud-only mode |
1GB available hard disk space – TETRA |
|
Microsoft Windows Server 2003 |
1 GHz or faster processor |
512 MB RAM |
150 MB available hard disk space - Cloud-only mode |
1GB available hard disk space - TETRA |
|
Microsoft Windows Server 2008 |
2 GHz or faster processor |
2 GB RAM |
150 MB available hard disk space – Cloud only mode |
1GB available hard disk space – TETRA |
|
Microsoft Windows Server 2012 (requires FireAMP Connector 5.1.3 or later) |
2 GHz or faster processor |
2 GB RAM |
150 MB available hard disk space - Cloud only mode |
1 GB available hard disk space – TETRA |
Most common is to have the AMP installer placed on the enterprise web server.
In order to download the connector, navigate to Management > Download Connector. Then choose type, and Download FireAMP (Windows, Android, Mac, Linux).
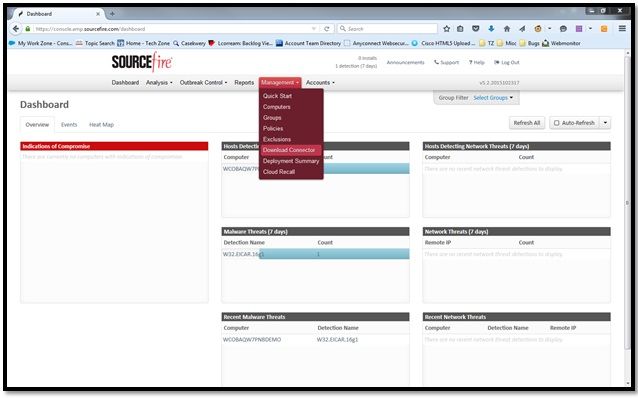
The Download Connector page allows you to download the install packages for each type of FireAMP connector. This package can be placed on a network share or distributed via management software.
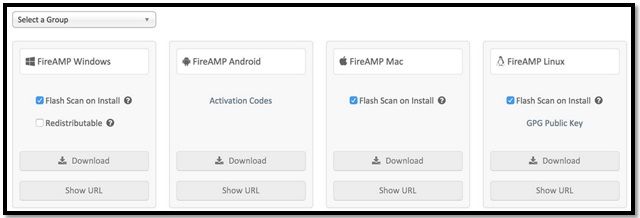
Select a Group
- Audit Only: Monitoring the system based on SHA-256 calculated over each file. This Audit only mode does not quarantine the malware, but sends an event as an alert.
- Protect: Protect mode with quarantine malicious files. Monitor file copy and move.
- Triage: This is for use on already compromised/infected computer.
- Server: Installation suite for Windows server, where the connector installs without Tetra engine and DFC driver. This group is designed by its name for non-domain controller servers.
- Domain Controller: The default policy for this group is set to audit mode as in Server group. Associate all your Active directory servers in this group, that means the connector will be running on a Windows Domain Controller.
The AMP has the feature called TETRA, which is full antivirus engine. This option is optional per policy.
Features
- Flash Scan on Install: Scan process runs during the installation. It is relatively quick to perform and recommended to run only once.
- Redistributable: You should download one single package, which contains 32-bit and 64-bit installers. Rather than a bootstrapper, which is available leaving this option unticked and downloads the installer files, once executed.
Note: You can create your own group and configure associated policy to it. The purpose is to place all e.g. Active directory servers into one group, where the policy is in audit mode.
The bootstrapper and redistributable installer also both contain a policy.xml file that is used as a configuration file for the AMP connector.
Step 4: Download the Web Security Client Profile
Specify company web server or a network share with AMP installer. This is most commonly used across companies to save bandwidth and place trusted installers in centralized location.
Please be sure that the HTTPS link can be reached on the endpoints without any certificate error and that root certificate is installed in the machine store.
Go back to the AMP Profile created before on the ASA (step 1) and edit AMP Enabler Profile:
- For AMP Mode, click the Install AMP Enabler radio button.
- In the Windows Installer field, add the IP for the web server and the file for the FireAMP.
- Windows Options are optional.
Click OK and apply the changes.
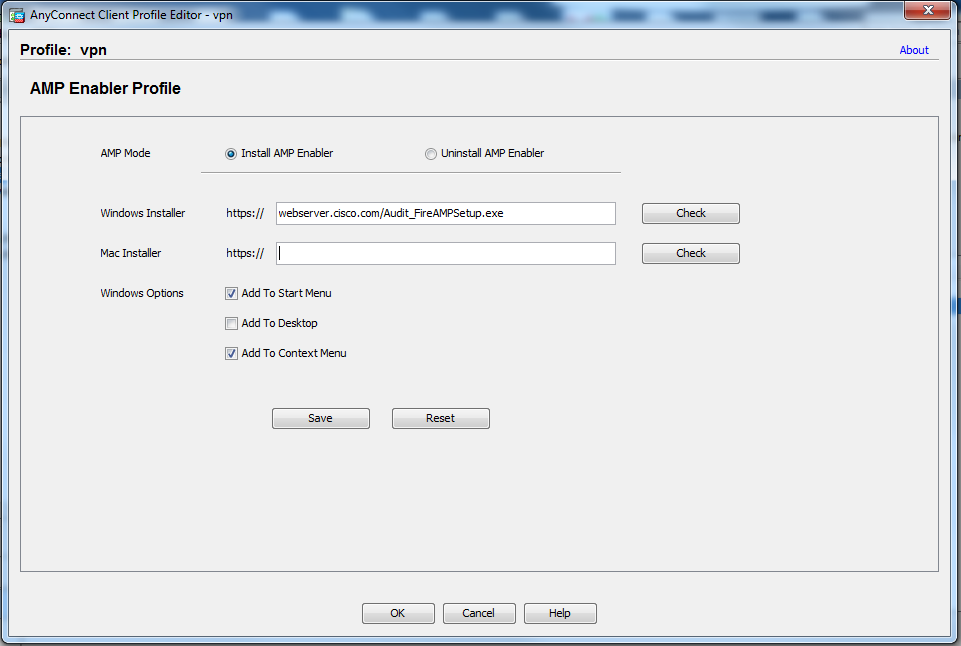
Step 5: Connect with AnyConnect and Verify the Installation of the Module
When Anyconnect VPN users connect, ASA pushes the AnyConnect AMP Enabler module through the VPN. For already logged in users, it is recommended to log off and then log in back for the functionality to be enabled.
10:08:29 AM Establishing VPN session... 10:08:29 AM The AnyConnect Downloader is performing update checks... 10:08:29 AM Checking for profile updates... 10:08:29 AM Checking for product updates... 10:08:31 AM Downloading AnyConnect AMP Enabler 4.4.01054 - 48% 10:08:32 AM Downloading AnyConnect AMP Enabler 4.4.01054 - 91% 10:08:33 AM Downloading AnyConnect AMP Enabler 4.4.01054 - 100%
Step 6: Start VPN Connection install AMP Enabler and AMP connector
Once you hit the button connect to start the VPN, it downloads the new downloader module. This will have AMP enabler and downloads the AMP package from the URL path you specified couple of steps before.
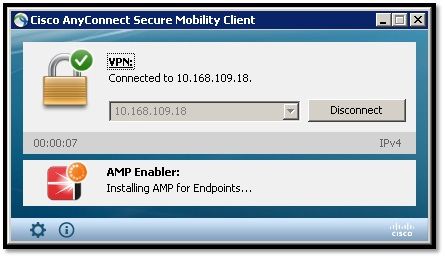
If you look at the event viewer: AMP enabler install: Date : 04/24/2017 Time : 10:08:34 Type : Information Source : acvpndownloader Description : Cisco AnyConnect Secure Mobility Client Downloader (2) exiting, version 4.4.01054 , return code 0 [0x00000000]
Step 7: Check AnyConnect and Verify If Everything is Installed
Once the VPN is connected and the configuration of the web server is installed, check AnyConnect and verify everything is installed properly.
In the services.msc you can find a new service called CiscoAMP_5.1.3. In the Powershell command we see:
PS C:\Users\winUser348> Get-Service -name "*CiscoAMP*" Status Name DisplayName ------ ---- ----------- Running CiscoAMP_5.1.3 Cisco AMP for Endpoints Connector 5...
The AMP Installer adds new drivers to the Windows OS. You might use the driverquery command to list the dirvers.
C:\Windows\System32>driverquery /v | findstr immunet ImmunetProte ImmunetProtectDriver ImmunetProtectDriver File System System Running OK TRUE FA LSE 4,096 69,632 0 3/17/2017 5:04:20 PM \??\C:\WINDOWS\System32\Drivers\immunetprotect.s 8,192 ImmunetSelfP ImmunetSelfProtectDriv ImmunetSelfProtectDriv File System System Running OK TRUE FA LSE 4,096 28,672 0 3/17/2017 5:04:08 PM \??\C:\WINDOWS\System32\Drivers\immunetselfprote 8,192
Step 8: Test with an Eicar String Contained in a Zombies PDF File
Test with an Eicar string contained in a Zombies PDF file in a test computer in order to verify the malicious file is quarantined.
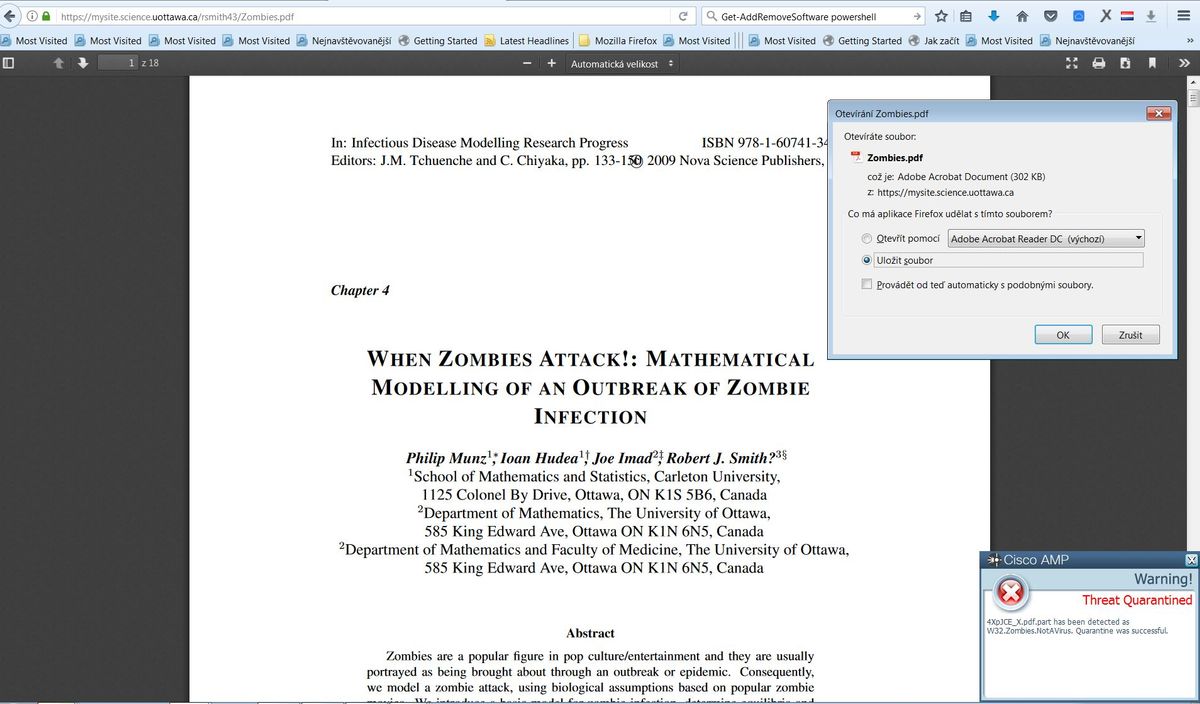 Zombies.pdf contains Eicar string
Zombies.pdf contains Eicar string
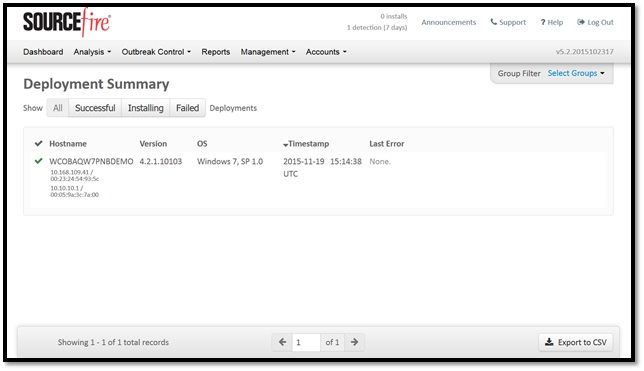
Step 9: Deployment Summary
This page shows you a list of successful and failed FireAMP connector installs as well as those currently in progress. You can go to Management > Deployment Summary.
Step 10: Thread Detection Verification
Zombies.pdf triggered an quarantine event, send to the AMP dashboard.
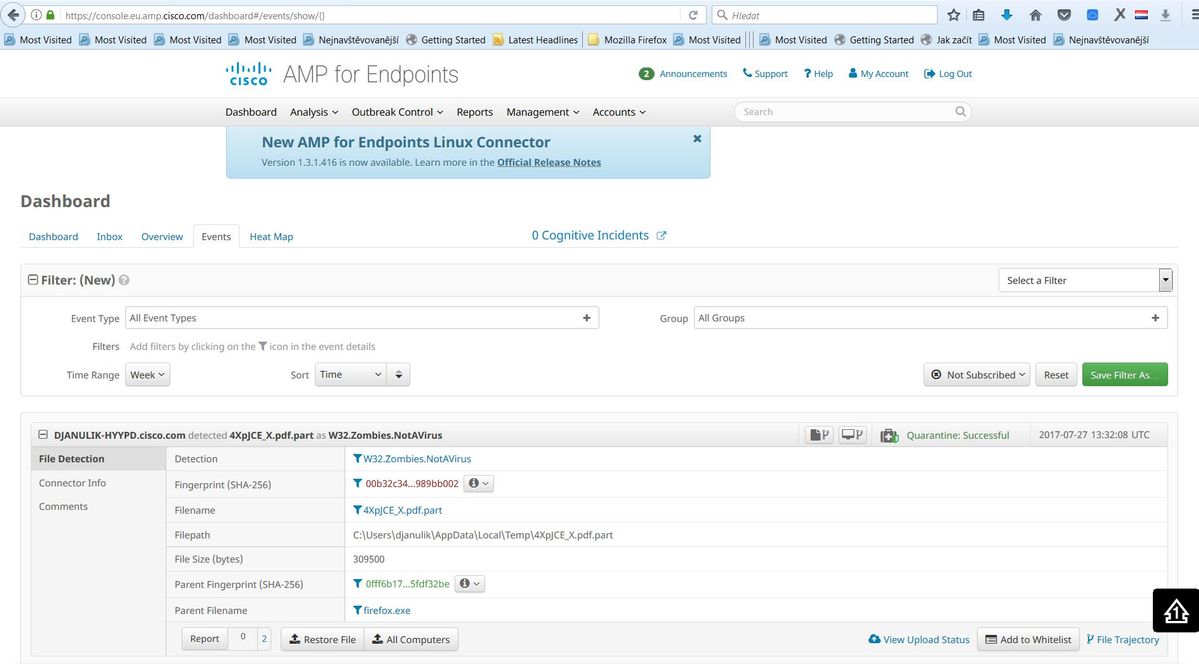 Quarantine event
Quarantine event
Additional Information
To get your AMP account, you can sign up for the ATS University. This gives you an overview of AMP functionality in LAB.
Related Information
Contributed by Cisco Engineers
- Leonardo CorreaCisco TAC Engineer
- Giovanny GonzalezCisco TAC Engineer
- Andres VegaCisco TAC Engineer
Contact Cisco
- Open a Support Case

- (Requires a Cisco Service Contract)
 Feedback
Feedback