Ultra Cloud Core User Plane Function
Introduction
This Release Notes identifies changes and issues related to this software release.
Release Lifecycle Milestones
|
Release Lifecycle Milestone |
Milestone |
Date |
|---|---|---|
|
First Customer Ship |
FCS |
31-Jan-2024 |
|
End of Life |
EoL |
31-Jan-2024 |
|
End of Software Maintenance |
EoSM |
31-Jul-2025 |
|
End of Vulnerability and Security Support |
EoVSS |
31-Jul-2025 |
|
Last Date of Support |
LDoS |
31-Jul-2026 |
These milestones and the intervals between them are defined in the Cisco Ultra Cloud Core (UCC) Software Release Lifecycle Product Bulletin available on cisco.com.
Release Package Version Information
|
Software Packages |
Version |
|---|---|
|
companion-vpc-21.28.m19.tgz.SPA.tar.gz |
21.28.m19 |
|
qvpc-si-21.28.m19.bin.SPA.tar.gz |
21.28.m19 |
|
qvpc-si-21.28.m19.qcow2.tgz.SPA.tar.gz |
21.28.m19 |
|
NED package |
ncs-6.1.5-cisco-staros-5.52 |
|
NSO |
6.1.5 |
Descriptions for the various packages provided with this release are available in the Release Package Descriptions section.
Verified Compatibility
|
Products |
Version |
|---|---|
|
ADC Plugin |
2.73.8.1991 |
|
RCM |
2024.01.0 |
|
Ultra Cloud Core SMI |
2024.01.1 |
|
Ultra Cloud Core SMF |
2024.01.0 |
What's New in this Release
New in Documentation
This version of Release Notes includes a new section titled What’s New in this Release comprising all new features, enhancements, and behavior changes applicable for the release.
This section will be available in all the 5G release notes and will supersede content in the Release Change Reference (RCR) document. Effective release 2024.01, the RCR document will be deprecated.
Features and Enhancements
This section covers a brief description of the features and enhancements introduced in this release. It also includes links to detailed documentation, where available.
| Feature | Description |
|---|---|
|
UPF supports dual stack to handle IPv4 and IPv6 connections on N3 and S1-U interfaces. Default Setting: Enabled – Always-on |
|
|
UPF supports encryption of dynamic fields in the redirected URL using the Blowfish and AES encryption methods. Default Setting: Disabled – Configuration required to enable |
Behavior Changes
This section covers a brief description of behavior changes introduced in this release.
| Behavior Change | Description |
|---|---|
|
Behavior of Sx Peers in SxDemux |
Previous Behavior: When the Sx peer moved from Associated state to New state, the Sx peers to be checkpointed for SxDemux recovery were deleted from SxDemux. New Behavior: When the Sx peer moves to Released state, the Sx peers to be checkpointed for SxDemux recovery will be deleted from SxDemux. |
|
Extended Intercept ID Display in CLI Output |
Previous Behavior: The output of the show lawful-intercept all CLI command displayed only the Intercept ID with the "Intercept-ID" variable. New Behavior: The "Intercept-ID" variable in the output show lawful-intercept all CLI command will also display the Extended Intercept ID (XID) if received through SMF. |
|
Handling Sx Services after Unplanned Switchover |
Previous Behavior: On Sx-service deletion, SxDemux sends DeRegistration information to VPNMgr to release IP pools related to peers under that service. New Behavior: On Sx-service deletion, SxDemux will first check other Sx services. If another Sx service exists with the same PFCP peer, then SxDemux will not send DeRegistration request to the VPNMgr. |
|
HTTP Request Methods during Redirection |
Previous Behavior: HTTP redirection was applied only on HTTP GET and not applied on other request methods such as HTTP POST. New Behavior: HTTP redirection will now be applied on all HTTP Request methods. |
|
Increase in QER Limit per PDR |
The QER limit per PDR is increased for the PTT (Push to Talk) feature. Previous Behavior: UPF supported a maximum number of two QERs per PDR association. New Behavior: The maximum number of QERs per PDR limit is increased to three in this release. |
|
Length Validation of OHC Description Field |
Previous Behavior: When the OHC (Outer Header Creation) description field was set to 768, length validation was not done. New Behavior: When the OHC IE receives the Outer Header Creation description field with both GTP-U/UDP/IPv4 and GTP-U/UDP/IPv6, the length of the OHC IE as 26 bytes is validated. If the length is not 26 bytes, then Sx message responds with the PFCP_CAUSE_MANDATORY_IE_INCORRECT cause code with Offending IE OUTER_HDR_CREATION. |
|
Maximum PDR Limit |
Previous Behavior: UPF did not enforce a maximum limit for installed PDRs per subscriber. New Behavior: UPF now enforces a maximum limit of 356 installed PDRs per subscriber. If the number of installed PDRs exceeds the maximum limit due to new Create PDRs in Modify Request, then Sx/N4 Modify Request is rejected. |
|
Message Handling during Inter-PLMN Handover |
Previous Behavior: When inter-PLMN handover was detected, UPF did not validate Create PDR for rulebase in Sx Modify Request. New Behavior: When inter-PLMN handover is detected, validation is enforced on UPF to reject Sx Modify Request without any Create PDR for the rulebase. |
|
OHC IE Validation on N4 Interface |
Previous Behavior: For N4 calls, the OHC (Outer Header Creation) IE in an uplink FAR led to validation failure and rejection of Sx Establishment/Modification Request. New Behavior: If an OHC IE is present in an uplink FAR for N4 calls, UPF establishes Sx Establishment/Modification Request without failure. Customer Impact: This behavior might impact the OHR and OHC functionality. |
|
Port Number Behavior in EDR Module Configuration |
After Cisco SSH or SSL upgrade, the port number behavior has changed for the EDR-module configuration. Previous Behavior: In the EDR-module configuration, the default SFTP port number "0" was selected automatically and connected to port 0 when colon was specified. For example: cdr transfer-mode push primary url sftp://root:starent@192.0.2.1:/root/EDR/ via local-context New Behavior: The EDR-module configuration is updated to allow the new default SFTP port number "22" or disallow the port number without specifying a colon. For example: cdr transfer-mode push primary url sftp://root:starent@192.0.2.1:22/root/EDR/ via local-context (with default SFTP port number) cdr transfer-mode push primary url sftp://root:starent@192.0.2.1/root/EDR/ via local-context (without colon) |
|
User Plane Advertisement through Created PDR IE or Traffic Endpoint IE |
Previous Behavior: The Local F-TEID in Create PDR or Create Traffic Endpoint IE was populated with the local GTP-U endpoint. This endpoint is allocated based on the configuration irrespective of Outer Header Removal received in the Create PDR IE. For example, if the GTP-U service configuration supported both IPv4 and IPv6 addresses, then both addresses are allocated and advertised in the Create PDR and Create Traffic Endpoint IEs. New Behavior: The Local F-TEID allocation process works as earlier. With this release, the User Plane advertises the allocated F-TEID to the Control Plane through Create PDR or Create Traffic Endpoint IE in the following scenarios:
Customer Impact: The behaviour of Local F-TEID in Create PDR or Create Traffic Endpoint IE is changed. |
Installation and Upgrade Notes
This Release Note does not contain general installation and upgrade instructions. Refer to the existing installation documentation for specific installation and upgrade considerations.
Software Integrity Verification
To verify the integrity of the software image you have from Cisco, you can validate the SHA512 checksum information against the checksum identified by Cisco for the software.
Image checksum information is available through Cisco.com Software Download Details. To find the checksum, hover the mouse pointer over the software image you have downloaded.
The following screenshot is an example of a UPF release posted in the Software Download page.
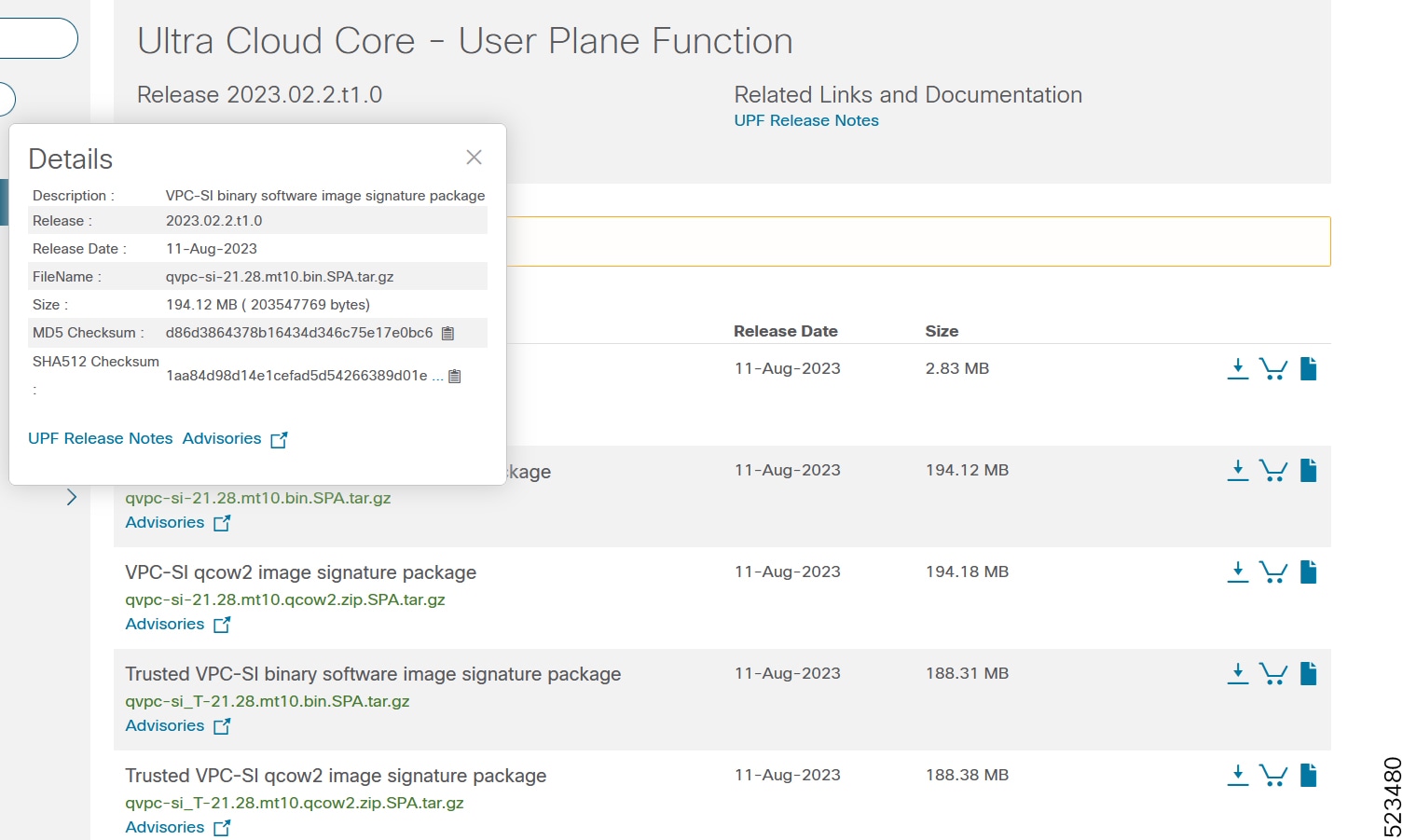
At the bottom you find the SHA512 checksum, if you do not see the whole checksum you can expand it by pressing the "..." at the end.
To validate the information, calculate a SHA512 checksum using the information in Table 1 and verify that it matches either the one provided on the software download page.
To calculate a SHA512 checksum on your local desktop, refer to the following table.
|
Operating System |
SHA512 checksum calculation command examples |
|---|---|
|
Microsoft Windows |
Open a command line window and type the following command: |
|
Apple MAC |
Open a terminal window and type the following command: |
|
Linux |
Open a terminal window and type the following command: OR |
|
NOTES: filename is the name of the file. extension is the file extension (for example, .zip or .tgz). |
|
If the SHA512 checksum matches, you can be sure that no one has tampered with the software image or the image has not been corrupted during download.
If the SHA512 checksum does not match, we advise you to not attempt upgrading any systems with the corrupted software image. Download the software again and verify the SHA512 checksum again. If there is a constant mismatch, please open a case with the Cisco Technical Assistance Center.
Certificate Validation
UPF software images are signed via x509 certificates. Please view the .README file packaged with the software for information and instructions on how to validate the certificates.
Open Bugs for this Release
The following table lists the open bugs in this specific software release.
 Note |
This software release may contain open bugs first identified in other releases. Additional information for all open bugs for this release are available in the Cisco Bug Search Tool. |
|
Bug ID |
Headline |
|---|---|
|
Observed Update FAR not found with FAR ID |
|
|
4g converged and non converged calls getting drop with echo req/res on MPLS over N9 |
|
|
[UPF] VUPF doesn't update proper counts in show user-plane-service statistics for RA packet |
|
|
restart seen for the func /pC :libc.so.6/__strlen_sse2_bsf |
|
|
Sessmgr restart at function sessmgr_uplane_process_sx_sess_modify_request() |
|
|
UPF GTPU statictis displays incorrect Downlink Packets / Bytes counters |
|
|
[UPF]:First-Packet-Time is wrongly set for RB URR whn recal measmnt IE is receivd & data sent again |
|
|
[UPF]SN-Charge volume parameter in EDR is wrongly pegged in case of flow redirect and delay charging |
|
|
OHR not displayed post sessctrl/sessmgr recovery for Sxa Access PDR created midsession |
|
|
[UPF] : Data drop is seen on UPF, when Pure p call (using cnPGW) attached with Dual stack cli. |
|
|
sessmgr is in over state post sessmgr task kill |
Resolved Bugs for this Release
The following table lists the resolved bugs in this specific software release.
 Note |
This software release may contain bug fixes first introduced in other releases. Additional information for all resolved bugs for this release are available in the Cisco Bug Search Tool. |
|
Bug ID |
Headline |
Behavior Change |
|---|---|---|
|
CUPS-UP: hatsystem crash due to VPP timeout, Assertion failure at hat/hatsystem_fail.c:2115 |
No |
|
|
[CUPS-UP] Some UP does not activate VPP correctly after upgrade or reload |
No |
|
|
CUPS,VPP restart in vlan_ip4_qos_mark_node_fn_avx2 |
No |
|
|
SSD collection may cause BFD timeout with 16 vpp workers due to show memory main-heap |
No |
|
|
CLI controlled rcm vpnmgr message to clear the contextpoolinfo in rcm controller |
Yes |
|
|
[UPF LI TLS] Intercept ID is not populated on lawfull intercept all cli |
Yes |
|
|
CP fails to push ECS config after Sx interface restarts |
No |
|
|
Charging ID inside correlation number is showing 00 00 when using SGW-Service |
No |
|
|
Unable to send IMS-Signaling data from UP to LMISF server when pfd push is disabled on CUPS |
No |
|
|
[UPF] Sx peers are in associated state when configured CPGROUP is not associated with user-plane-ser |
Yes |
|
|
UPF show gtpu statistics peer-address should display bytes and pks for gtpu peer (umbrella Stats) |
No |
|
|
Need to disable OHC validation for N4 interface on uplink FAR |
Yes |
|
|
[UPF] SFW stats incorrectly getting reconciled from VPP to sessmgr |
No |
|
|
[UPF] Discrepancies in stat counters and disconnect reasons during gtpu path failure |
No |
|
|
hd raid CF2 disk is not used or available when CF1 is down |
No |
|
|
Sessmgr crashed with function ld-linux.so.2/_dl_sysinfo_int80() |
No |
|
| x
Need a fix on SxDemux for the IP chunk issue reported in BEMS01626426 |
Yes |
|
|
[UPF]HTTP Redirect not working for HTTP method as POST. |
Yes |
|
|
UPF displays Port bits for OHC for 5G Attach with GNB having IPv4v6 transport |
Yes |
|
|
VPP issues with 21.28.m14 |
No |
|
|
[UPF] - Handle exception when SMF does not remove the PDR for 5g-4g HO collision with IM exit |
Yes |
|
|
VPP Buffers reach 100% utilization with Mellanox NICs and NSH-Traffic-Steering |
No |
|
|
sessmgr restart at egtpu_process_update_req_evt() with inter/intra plmn HO calls |
Yes |
|
|
When redirect url length exceeds 512 then appended attributes sent incomplete in 302 |
Yes |
|
|
Incorrect handling when gnodeB is dual-stack and SMF is not configured to be dual stack |
Yes |
|
|
VPP restart as /usr/sbin64/vpp(sn_assert_signal_handler |
No |
|
|
[UPF]Post switchover pfcp flow with port 8805 is getting deleted, leading to call failures. |
No |
|
|
[UPF]QER limit needs to be increased to 3 per PDR, for PTT feature. |
Yes |
|
|
VPP restart observed in CUPS-UP |
No |
|
|
[CUPS-UP] vpp restarted - vlib_worker_thread_barrier_sync_int() |
No |
|
|
[BP-CUPS]: sesmgr restart at sessmgr_med_data_process_memif_pri() |
No |
|
|
Multiple vpp crashes with 21.25.0.82232 |
No |
Operator Notes
StarOS Version Numbering System
The output of the show version command displays detailed information about the version of StarOS currently running on the ASR 5x00 or Cisco Virtualized Packet Core platform.
The Version Build Number for releases 21.1 and later include a major and emergency release number, for example, "21.1.1".

The appropriate version number field increments after a version has been released. The new version numbering format is a contiguous sequential number that represents incremental changes between releases. This format facilitates identifying the changes between releases when using Bug Search Tool to research software releases.
 Note |
The 5G UPF software is based on StarOS and implements the version numbering system described in this section. However, as a 5G network function (NF), it is posted to Cisco.com under the Cloud Native Product Numbering System as described in Cloud Native Product Version Numbering System. |
Cloud Native Product Version Numbering System
The show helm list command displays detailed information about the version of the cloud native product currently deployed.

The appropriate version number field increments after a version has been released. The new version numbering format is a contiguous sequential number that represents incremental changes between releases. This format facilitates identifying the changes between releases when using Bug Search Tool to research software releases.
Release Package Descriptions
The following table provides descriptions for the packages that are available with this release.
|
Software Packages |
Description |
|---|---|
|
companion-vpc-<staros_version>.zip.SPA.tar.gz |
Contains files pertaining to VPC, including SNMP MIBs, RADIUS dictionaries, ORBEM clients, etc. These files pertain to both trusted and non-trusted build variants. The VPC companion package also includes the release signature file, a verification script, the x.509 certificate, and a README file containing information on how to use the script to validate the certificate. |
|
qvpc-si-<staros_version>.bin.SPA.tar.gz |
The UPF release signature package. This package contains the VPC-SI deployment software for the UPF as well as the release signature, certificate, and verification information. Files within this package are nested under a top-level folder pertaining to the corresponding StarOS build. |
|
qvpc-si-<staros_version>.qcow2.zip.SPA.tar.gz |
The UPF release signature package. This package contains the VPC-SI deployment software for the UPF as well as the release signature, certificate, and verification information. Files within this package are nested under a top-level folder pertaining to the corresponding StarOS build. |
|
ncs-<nso_version>-cisco-staros-<version>.signed.bin |
The NETCONF NED package. This package includes all the files that are used for NF configuration. Note that NSO is used for NED file creation. |
Obtaining Documentation and Submitting a Service Request
For information on obtaining documentation, using the Cisco Bug Search Tool (BST), submitting a service request, and gathering additional information, refer to https://www.cisco.com/c/en/us/support/index.html.
 Feedback
Feedback