IPSec Stateful Failover (VPN High Availability) Feature Module
Available Languages
Table Of Contents
IPSec Stateful Failover (VPN High Availability)
Hot Standby Router Protocol (HSRP)
Related Features and Technologies
Supported Standards, MIBs, and RFCs
Configuring HSRP Group Attributes
Configuring IKE Pre-Shared Key
Configuring an IPSec Transform Set
Defining an IPSec Transform Set
Selecting Appropriate Transforms
The Crypto Transform Configuration Mode
Configuring Crypto Access Lists for IPSec Traffic
Creating Crypto Access Lists for IPSec Traffic
Creating Crypto Access List Example
Ensuring That Access Lists Are Compatible with IPSec
Setting Global Lifetimes for IPSec Security Associations
Configuring Crypto Map Example
Configuring SSP Communications
Configuring SSP Communications Example
Applying Crypto Map Sets to Interfaces and Enabling Transferring IPSec State
Applying Crypto Map Sets to Interfaces Example
Show Configuration Tasks and Examples
Verifying IPSec Configurations
Verifying IPSec High Availability
Monitoring and Maintaining IPSec Stateful Failover (VPN High Availability)
Debug Configuration Tasks and Examples
Clearing Dormant SAs on Standby Routers
clear crypto isakmp ha standby
IPSec Stateful Failover (VPN High Availability)
Feature History
This document describes IPSec Stateful Failover (VPN High Availability) in Cisco IOS Release 12.2(14)SU2, 12.2(14)SU1, 12.2(14)SU, 12.2(11)YX1, and 12.2(11)YX, and contains the following sections:
•
Supported Standards, MIBs, and RFCs
•
Show Configuration Tasks and Examples
•
Debug Configuration Tasks and Examples
Feature Overview
IPSec Stateful Failover (VPN High Availability) is a feature that enables a router to continue processing and forwarding packets after a planned or unplanned outage. You can employ a backup (standby) router that automatically takes over the primary (active) router's tasks in the event of an active router failure. The process is transparent to users and to remote IPSec peers. The time that it takes for the standby router to take over depends on HSRP timers.
IPSec Stateful Failover (VPN High Availability) is designed to work in conjunction with Reverse Route Injection (RRI) and Hot Standby Router Protocol (HSRP) with IPSec. When used together, RRI and HSRP provide a more reliable network design for VPNs and reduce configuration complexity on remote peers.
RRI and HSRP are supported together with the restriction that the HSRP configuration on the outside interface uses equal priorities on both routers. As an option, when not using RRI, you can use an HSRP configuration on the LAN side of the network (equal HSRP priority restriction still applies).
Reverse Route Injection (RRI)
RRI is a feature designed to simplify network design for VPNs which require redundancy and routing. RRI works with both dynamic and static crypto maps. When routes are created, they are injected into any dynamic routing protocol and distributed to surrounding devices. This causes traffic flows requiring IPSec to be directed to the appropriate head-end VPN router for transport across the correct security associations (SAs) to avoid IPSec policy mismatches and possible packet loss.
Hot Standby Router Protocol (HSRP)
HSRP is designed to provide high network availability by routing IP traffic from hosts on Ethernet networks without relying on the availability of any single router. By providing network redundancy for IP networks, user traffic immediately and transparently recovers from first hop failures in network edge devices or access circuits.
A network administrator enables HSRP, assigns a virtual IP address, and enables IPSec Stateful Failover (VPN High Availability). After enabling both HSRP and IPSec Stateful Failover, the network administrator uses the show ssp, show crypto ipsec, and show crypto isakmp commands to verify that all processes are running properly. In the event of failover, the standby device takes over ownership of the standby IP address and begins to service remote VPN peers.
The information that the active router transmits to the standby router includes:
•
IKE cookies stamp
•
Session keys
•
Cisco Service Assurance (SA) Agent attributes
•
Sequence number counter and window state
•
Kilobyte (KB) lifetime expirations
•
Dead peer detection (DPD) sequence number updates
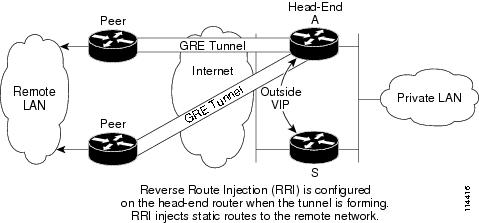
Figure 1 shows a sample topology for site-to-site configuration of IPSec Stateful Failover with generic routing encapsulation (GRE), a tunnel interface not tied to specific "passenger" or "transport" protocols. GRE supports multicast traffic, critical for V3PN applications.
Figure 1 Site-to-Site VPN Configuration
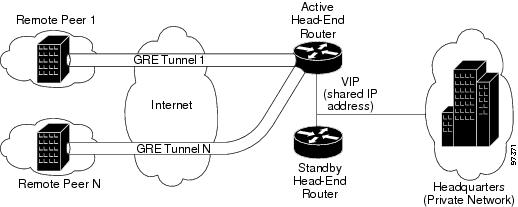
There are four possible configurations for the Cisco 7200 series routers using Cisco IOS Release 12.2(14)SU, 12.2(14)SU1, or 12.2(14)SU2:
•
non-GRE High Availability (HA) with a virtual IP (VIP), or redundancy groups, on the outside and a VIP on the inside (see Figure 2)
•
non-GRE HA with only VIPs on the outside. The route to the outside is provided by Reverse Route Injection (RRI) (see Figure 3)
•
GRE HA, with VIPs on the outside and tested inside faces (see Figure 4)
•
GRE HA, with only a VIP on the outside, using RRI to inject routes (see Figure 5)
Figure 2 HSRP VIP on Inside and Outside
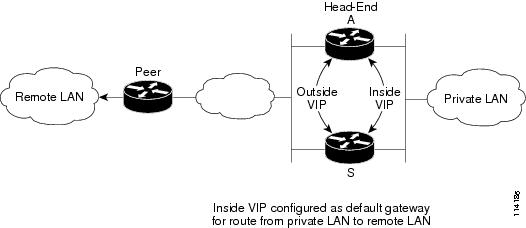
Figure 3 HSRP VIP on Outside, RRI Injected Routes on Inside
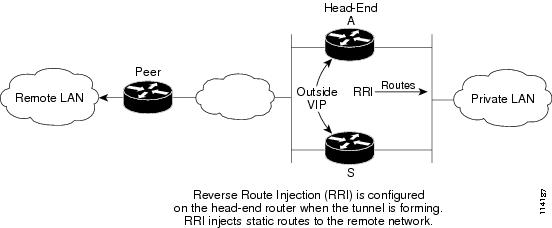
Figure 4 GRE HA with VIPs on the Outside and Inside Faces
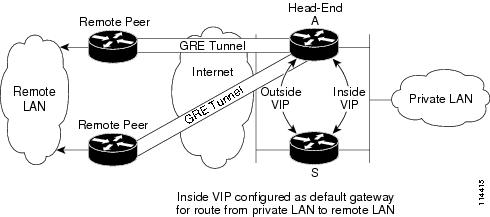
Figure 5 GRE HA with Only a VIP on the Outside, Using RRI to Inject Routes
Feature Summary
Table 1 provides a summary of features, by Cisco IOS software release.
Benefits
•
IPSec VPN tunnels assigned to an active router will automatically be transitioned to a standby router upon any active router failure. Any transition from an active router to a standby router is transparent to peers, and requires no remote peer adjustment or reconfiguration.
•
Businesses employing IPSec Stateful Failover (VPN High Availability) are 100% redundant with regard to IPSec VPN traffic.
•
Utilizing IPSec Stateful Failover (VPN High Availability) does not appreciably affect overall router performance.
•
Generic routing encapsulation (GRE) supports multicast traffic, critical for V3PN applications.
Restrictions
•
Does not support failover of IKECFG attributes.
•
Does not support IKE XAUTH states.
•
Supports just a single VAM/VAM2 card in each active/standby router.
•
Requires identical security policy configurations on both active and standby routers.
•
Requires that IKE keepalives must not be used; enabling this feature will cause the connection to be torn down after the standby router assumes ownership control.
•
Supports keepalives only with dead peer detection (DPD).
•
Requires that priority values are equal on both active and standby routers for IP redundancy.
•
IPSec MIB statistics could be erroneous on the standby router after a failover.
•
Requires that active and standby routers be connected to an Ethernet interface.
•
Does not support Cisco VPN Client 3.X client.
•
Does not support PKI certificates.
Related Features and Technologies
•
Internet Key Exchange (IKE)
•
IP Security (IPSec)
•
Reverse Route Injection (RRI)
•
Hot Standby Router Protocol (HSRP)
•
State Synchronization Protocol (SSP)
Related Documents
Supported Platforms
•
Cisco 7200 series
Supported Standards, MIBs, and RFCs
Standards
•
None
MIBs
•
None
To obtain lists of supported MIBs by platform and Cisco IOS release, and to download MIB modules, go to the Cisco MIB web site at http://www.cisco.com/public/sw-center/netmgmt/cmtk/mibs.shtml.
RFCs
•
None
Prerequisites
You must configure IPSec and IKE on the router and a crypto map to all interfaces that require encryption service. See the "Configuration Tasks" section for configuration procedures.
•
Cisco IOS Release 12.2(14)SU2, 12.2(14)SU1, 12.2(14)SU, 12.2(11)YX1, or Cisco IOS Release 12.2(11)YX
•
Two Cisco 72xx routers configured with the same Cisco IOS release
•
HSRP running
Configuration Tasks
See Figure 6 and use the following commands to implement, maintain, and debug IPSec Stateful Failover (VPN High Availability).
•
Configuring HSRP (required)
•
Configuring an IKE Policy (required)
•
Configuring IKE Pre-Shared Key (required)
•
Configuring an IPSec Transform Set (required)
•
Configuring Crypto Access Lists for IPSec Traffic (required)
•
Configuring Crypto Maps (required)
•
Configuring SSP Communications (required)
•
Applying Crypto Map Sets to Interfaces and Enabling Transferring IPSec State (required)
Figure 6 Sample Configuration for IPSec Stateful Failover (VPN High Availability

Configuring HSRP
This section describes the Hot Standby Router Protocol (HSRP) Support for Virtual Private Networks (VPNs) and includes the following sections:
•
Configuring HSRP Group Attributes
The HSRP Support for VPNs feature ensures that the HSRP virtual IP address is added to the correct IP routing table and not to the default routing table.
Keep in mind the following when configuring HSRP:
•
Both the inside (private) and outside (public) interfaces must belong to separate HSRP groups. The interfaces then must track each other.
•
The HSRP state of the inside and outside interface of each must be the same, that is, both must be active or both must be standby, otherwise there will be a black hole - packets won't have a route out of the private network. To avoid having one interface on standby while another is on active, confirm the conditions below:
–
Standby priorities should be equal on active and standby routers. If they are not, IPSec Stateful failover may or may not occur automatically when the active router fails.
–
The IP addresses on the HSRP-tracked interfaces on the standby and active routers should both be either lower or higher on one router than the other. In the case of equal priorities (an HA requirement), HSRP will assign the active state based on IP address. If an addressing scheme exists so that the public IP address of router A is lower than the public IP address of router B, but the opposite is true for their private interfaces, an active/standby-standby/active split condition could happen, which will break IPSec connectivity.
Enabling HSRP
To enable the HSRP on an interface, use the following command in interface configuration mode:
Enables the HSRP.
Repeat this command to enable HSRP on each router.
Configuring HSRP Group Attributes
To configure other HSRP group attributes that affect how the local router participates in HSRP, use one or more of the following commands in interface configuration mode:
Configuring HSRP Examples
The following example shows how to configure the outside interface:
Router(config-if)# interface fastEthernet 0/1Router(config-if)# standby 1 ip 40.0.0.1Router(config-if)# standby 1 name ispRouter(config-if)# standby 1 timers msec 500 3Router(config-if)# standby delay minimum 30 reload 60Router(config-if)# standby 1 preemptRouter(config-if)# standby 1 track fastEthernet 0/0
Note
The standby delay command is not essential, but recommended. All other commands are required.
The following commands shows how to configure the HSRP inside interface:
Router(config-if)# interface fastEthernet 0/0Router(config-if)# standby 2 ip 172.16.31.1Router(config-if)# standby 2 name lanRouter(config-if)# standby 2 timers msec 500 3Router(config-if)# standby delay minimum 30 reload 60Router(config-if)# standby 2 preemptRouter(config-if)# standby 2 track fastEthernet 0/1
Note
Configure the same commands on Router 2, including the same HSRP priority values (the default is 100) as on Router 1.
Configuring an IKE Policy
If you do not specify a value for a parameter, the default value is assigned. For information on default values, refer to the "IP Security and Encryption" chapter of the Security Command Reference publication.
To configure an IKE policy, use the following commands beginning in global configuration mode:
For detailed information on creating IKE policies, refer to the "Configuring Internet Key Exchange Security Protocol" chapter in the Security Configuration Guide publication.
Configuring IKE Pre-Shared Key
To specify pre-shared keys with a peer, use the following commands in global configuration mode:
Remember to repeat these tasks at each peer that uses pre-shared in an IKE policy.
Configuring an IPSec Transform Set
This section includes the following topics:
•
Defining an IPSec Transform Set (required)
•
IPSec Protocols: AH and ESP (optional)
•
Selecting Appropriate Transforms (optional)
•
The Crypto Transform Configuration Mode (optional)
•
Changing Existing Transforms (optional)
•
Transform Example (optional)
A transform set is an acceptable combination of security protocols, algorithms, and other settings to apply to IPSec protected traffic. During the IPSec security association (SA) negotiation, the peers agree to use a particular transform set when protecting a particular data flow.
Defining an IPSec Transform Set
A transform set is a combination of security protocols and algorithms. During the IPSec security association negotiation, peers agree to use a specific transform set to protect a particular data flow.
To define a transform set, use the following commands, starting in global configuration mode:
Step 1
Router(config)# crypto ipsec transform-set transform-set-name transform1 [transform2 [transform3]]
transform-set-name
Specify the name of the transform set to create (or modify).transform1
transform2
transform3Specify up to three transforms (one is required) that define the IPSec security protocol(s) and algorithm(s). Accepted transform values are described in Table 2.
Step 2
Router(cfg-crypto-tran)# mode [tunnel | transport]
(Optional) Changes the mode associated with the transform set. The mode setting is only applicable to traffic whose source and destination addresses are the IPSec peer addresses; it is ignored for all other traffic. (All other traffic is in tunnel mode only.)
Step 3
end
Exits the crypto transform configuration mode to enabled mode.
Step 4
clear crypto sa
or
clear crypto sa peer {ip-address | peer-name}
or
clear crypto sa map map-name
or
clear crypto sa spi destination-address protocol spiClears existing IPSec security associations so that any changes to a transform set take effect on subsequently established security associations (SAs). (Manually established SAs are reestablished immediately.)
Using the clear crypto sa command without parameters clears out the full SA database, which clears out active security sessions. You may also specify the peer, map, or entry keywords to clear out only a subset of the SA database.
Step 5
Repeat these steps to configure IPSec transform sets on each router.
Table 2 shows allowed transform combinations for the AH and ESP protocols.

Note
AES is not available with Cisco IOS Release 12.2(14)SU2, 12.2(14)SU1 or 12.2(14)SU.
Examples of acceptable transform combinations are as follows:
•
ah-md5-hmac
•
esp-des
•
esp-3des and esp-md5-hmac
•
ah-sha-hmac and esp-des and esp-sha-hmac
•
comp-lzs
The parser will prevent you from entering invalid combinations; for example, once you specify an AH transform it will not allow you to specify another AH transform for the current transform set.
IPSec Protocols: AH and ESP
Both the AH and ESP protocols implement security services for IPSec.
AH provides data authentication and antireplay services.
ESP provides packet encryption and optional data authentication and antireplay services.
ESP encapsulates the protected data—either a full IP datagram (or only the payload)—with an ESP header and an ESP trailer. AH is embedded in the protected data; it inserts an AH header immediately after the outer IP header and before the inner IP datagram or payload. Traffic that originates and terminates at the IPSec peers can be sent in either tunnel or transport mode; all other traffic is sent in tunnel mode. Tunnel mode encapsulates and protects a full IP datagram, while transport mode encapsulates/protects the payload of an IP datagram. For more information about modes, refer to the mode (IPSec) command description.
Selecting Appropriate Transforms
The following tips may help you select transforms that are appropriate for your situation:
•
If you want to provide data confidentiality, include an ESP encryption transform.
•
If you want to ensure data authentication for the outer IP header as well as the data, include an AH transform. (Some consider the benefits of outer IP header data integrity to be debatable.)
•
If you use an ESP encryption transform, also consider including an ESP authentication transform or an AH transform to provide authentication services for the transform set.
•
If you want data authentication (either using ESP or AH) you can choose from the MD5 or SHA (HMAC keyed hash variants) authentication algorithms. The SHA algorithm is generally considered stronger than MD5 but is slightly slower.
•
Note that some transforms might not be supported by the IPSec peer.

Note
If a user enters an IPSec transform that the hardware (the IPSec peer) does not support, a warning message will be displayed immediately after the crypto ipsec transform-set command is entered.
•
In cases where you need to specify an encryption transform but do not actually encrypt packets, you can use the esp-null transform.
Suggested transform combinations follow:
•
esp-aes and esp-sha-hmac
•
ah-sha-hmac and esp-aes and esp-sha-hmac
The Crypto Transform Configuration Mode
After you issue the crypto ipsec transform-set command, you are put into the crypto transform configuration mode. While in this mode, you can change the mode to tunnel or transport. (These are optional changes.) After you have made these changes, type exit to return to global configuration mode. For more information about these optional changes, refer to the match address (IPSec) and mode (IPSec) command descriptions.
Changing Existing Transforms
If one or more transforms are specified in the crypto ipsec transform-set command for an existing transform set, the specified transforms will replace the existing transforms for that transform set.
If you change a transform set definition, the change is only applied to crypto map entries that reference the transform set. The change will not be applied to existing SAs, but will be used in subsequent negotiations to establish new SAs. If you want the new settings to take effect sooner, you can clear all or part of the SA database by using the clear crypto sa command.
Transform Example
The following example defines two transform sets. The first transform set will be used with an IPSec peer that supports the newer ESP and AH protocols. The second transform set will be used with an IPSec peer that only supports the older transforms.
crypto ipsec transform-set SDM_TRASFORMSET_1 esp-3des esp-sha-hmacThe following example is a sample warning message that is displayed when a user enters an IPSec transform that the hardware does not support:
crypto ipsec transform transform-1 esp-aes 256 esp-md5WARNING:encryption hardware does not support transformesp-aes 256 within IPSec transform transform-1Configuring Crypto Access Lists for IPSec Traffic
This section includes the following topics:
•
Creating Crypto Access Lists for IPSec Traffic (required)
•
Creating Crypto Access List Example
•
Ensuring That Access Lists Are Compatible with IPSec (required)
•
Setting Global Lifetimes for IPSec Security Associations (optional)
Creating Crypto Access Lists for IPSec Traffic
Crypto access lists define which IP traffic will be protected by encryption. (These access lists are not the same as regular access lists, which determine what traffic to forward or block at an interface.) For example, access lists can be created to protect all IP traffic between Subnet A and Subnet Y or Telnet traffic between Host A and Host B.
To create crypto access lists, use the following command in global configuration mode:
Step 1
Router(config)# access-list access-list-number {permit | deny} protocol source source-wildcard destination destination-wildcard [log]
or
Router(config)# ip access-list extended name
access-list-number
Specify an integer from 100 to 199 that you select for the list.permit
Permits the frame.deny
Denies the frame.Specifies conditions to determine which IP packets will be protected.1 (Enable or disable crypto for traffic that matches these conditions.)
We recommend that you configure "mirror image" crypto access lists for use by IPSec and that you avoid using the any keyword.
Step 2
Add permit and deny statements as appropriate.
Adds permit or deny statements to access lists.
Step 3
End
Exits the configuration command mode.
Step 4
Repeat these steps to create access lists on each router.
1 You specify conditions using an IP access list designated by either a number or a name. The access-list command designates a numbered extended access list; the ip access-list extended command designates a named access list.
Creating Crypto Access List Example
The following example shows a typical example for creating an access list for IPSec traffic on both routers:
access-list 100 permit ip any 192.168.4.0.0.0.0.255Ensuring That Access Lists Are Compatible with IPSec
IKE uses UDP port 500. The IPSec Encapsulating Security Payload (ESP) and Authentication Header (AH) protocols use protocol numbers 50 and 51. Ensure that your interface access lists are configured so that protocol numbers 50, 51, and UDP port 500 traffic are not blocked at interfaces used by IPSec. In some cases, you might need to add a statement to your access lists to explicitly permit this traffic.
Setting Global Lifetimes for IPSec Security Associations
You can change the global lifetime values which are used when negotiating new IPSec security associations. (These global lifetime values can be overridden for a particular crypto map entry).
These lifetimes only apply to security associations established via IKE. Manually established security associations do not expire.
To change a global lifetime for IPSec security associations, use one or more of the following commands in global configuration mode:
Configuring Crypto Maps
You can apply only one crypto map set to a single interface. The crypto map set can include a combination of IPSec/IKE and IPSec/manual entries. Multiple interfaces can share the same crypto map set if you want to apply the same policy to multiple interfaces.
This section includes the following topics:
•
Creating Crypto Map Entries (required)
•
Configuring Crypto Map Example
•
Creating Dynamic Crypto Maps (optional)
Creating Crypto Map Entries
To create crypto map entries that use IKE to establish the security associations, use the following commands, starting in global configuration mode:
Configuring Crypto Map Example
The following example shows an example of configuring a crypto map:
crypto map SDM_CMAP_1 1 ipsec-isakmpdescription Tunnel to 192.168.3.1set peer 192.168.3.1set transform-set SDM_TRASNFORMSET_1match address 100Creating Dynamic Crypto Maps
A dynamic crypto map entry is a crypto map entry with some parameters not configured.The missing parameters are later dynamically configured (as the result of an IPSec negotiation). Dynamic crypto maps are only available for use with ISAKMP.
Dynamic crypto map entries are grouped into sets. A set is a group of dynamic crypto map entries all with the same dynamic-map-name, each with a different dynamic-seq-num.
To create a dynamic crypto map entry, use the following commands starting in global configuration mode:
To add a dynamic crypto map set into a crypto map set, use the following command in global configuration mode:
Router(config)# crypto map map-name seq-num ipsec-isakmp dynamic dynamic-map-name
Adds a dynamic crypto map set to a static crypto map set.
Configuring SSP Communications
Perform the following commands to enable and debug SSP:
Configuring SSP Communications Example
The following example shows an SSP communications configuration on each HA router:
Router 1:
ssp group 1remote 172.16.31.6redundancy ISPredundancy LANRouter 2:
ssp group 1remote 172.16.31.100redundancy ISPredundancy LANTransferring ISAKMP State
Perform the following commands, starting in configuration mode to enable SSP communication state transfers for ISAKMP:
Transferring IPSec State
Perform the following command in global mode to transfer IPSec state from the active router to the standby router:
Global Mode
Applying Crypto Map Sets to Interfaces and Enabling Transferring IPSec State
Apply a crypto map set to each interface through which IPSec traffic will flow. Crypto maps instruct the router to evaluate the interface traffic against the crypto map set and use the specified policy during connection or security association negotiation on behalf of traffic to be protected by crypto.
To apply a crypto map set to an interface, use the following commands, starting in global configuration mode:
Applying Crypto Map Sets to Interfaces Example
The following example shows the application of a crypto map:
interface FastEthernet0/1crypto map SDM_CMAP_1 ssp 1Configuration Examples
The following examples show sample output for IPSec HA configurations:
Example 1
hostname 7200-1!ssp group 1remote 172.16.31.6redundancy ISPredundancy LAN!crypto isakmp policy 1encr 3desauthentication pre-sharegroup 2crypto isakmp key cisco address 192.168.3.1crypto isakmp ssp 1!!!crypto ipsec transform-set TRANSFORMSET_1 esp-3des esp-sha-hmac!crypto map CMAP_1 1 ipsec-isakmpdescription Tunnel to 192.168.3.1set peer 192.168.3.1set transform-set TRANSFORMSET_1match address 100!interface FastEthernet0/0description INSIDE_INTERFACEip address 172.16.31.100 255.255.255.0standby delay minimum 30 reload 60standby 1 ip 172.16.31.1standby 1 timers msec 500 3standby 1 preemptstandby 1 name LANstandby 1 track FastEthernet0/1!interface FastEthernet0/1description OUTSIDE_INTERFACEip address 40.0.0.100 255.255.255.0standby delay minimum 30 reload 60standby 2 ip 40.0.0.1standby 2 timers msec 500 3standby 2 preemptstandby 2 name ISPstandby 2 track FastEthernet0/0crypto map CMAP_1 ssp 1!access-list 100 remark IPSec Ruleaccess-list 100 permit ip any 192.168.4.0 0.0.0.255!endExample 2
hostname 7200-2!ssp group 1remote 172.16.31.100redundancy ISPredundancy LAN!crypto isakmp policy 1encr 3desauthentication pre-sharegroup 2crypto isakmp key cisco address 192.168.3.1crypto isakmp ssp 1!!!crypto ipsec transform-set TRANSFORMSET_1 esp-3des esp-sha-hmac!crypto map CMAP_1 1 ipsec-isakmpdescription Tunnel to 192.168.3.1set peer 192.168.3.1set transform-set TRANSFORMSET_1match address 100!interface FastEthernet0/0description INSIDE_INTERFACEip address 172.16.31.6 255.255.255.0standby delay minimum 30 reload 60standby 1 ip 172.16.31.1standby 1 timers msec 500 3standby 1 preemptstandby 1 name LANstandby 1 track FastEthernet0/1!interface FastEthernet0/1description OUTSIDE_INTERFACEip address 40.0.0.6 255.255.255.0standby delay minimum 30 reload 60standby 2 ip 40.0.0.1standby 2 timers msec 500 3standby 2 preemptstandby 2 name ISPstandby 2 track FastEthernet0/0crypto map CMAP_1 ssp 1!access-list 100 remark IPSec Ruleaccess-list 100 permit ip any 192.168.4.0 0.0.0.255!endShow Configuration Tasks and Examples
This section provides the following configuration tasks and examples:
•
Verifying IPSec Configurations
•
Verifying IPSec High Availability
•
Monitoring and Maintaining IPSec Stateful Failover (VPN High Availability)
Verifying IKE Configurations
To view information about your IKE configurations, use show crypto isakmp policy EXEC command. The following is sample output from that command:
Router# show crypto isakmp policy 1encr 3desauthentication pre-sharegroup 2crypto isakmp key cisco address 192.168.3.1
Note
If a user enters an IKE encryption method that the hardware does not support, a warning message will be displayed in the show crypto isakmp policy output.
The following sample output from the show crypto isakmp policy command displays a warning message after a user tries to configure an IKE encryption method that the hardware does not support:
Protection suite of priority 1encryption algorithm: AES - Advanced Encryption Standard (256 bit keys).WARNING:encryption hardware does not support the configuredencryption method for ISAKMP policy 1hash algorithm: Secure Hash Standardauthentication method: Pre-Shared KeyDiffie-Hellman group: #1 (768 bit)lifetime: 3600 seconds, no volume limit
Verifying IPSec Configurations
Some configuration changes take effect only after subsequent security associations are negotiated. For the new settings to take effect immediately, clear the existing security associations.
To clear (and reinitialize) IPSec security associations, use one of the commands in Table 3 in global configuration mode:
The following steps provide information on verifying your configurations:
Step 1
Enter the show crypto ipsec transform-set command to view your transform set configuration:
Router# show crypto ipsec transform-setTransform set combined-des-md5: {esp-des esp-md5-hmac}will negotiate = {Tunnel,},Transform set t1: {esp-des esp-md5-hmac}will negotiate = {Tunnel,},Transform set t100: {ah-sha-hmac}will negotiate = {Transport,},Transform set t2: {ah-sha-hmac}will negotiate = {Tunnel,},{esp-des}will negotiate = {Tunnel,},
Note
If a user enters an IPSec transform that the hardware (the IPSec peer) does not support, a warning message will be displayed in the show crypto ipsec transform-set command output.
The following sample output from the show crypto ipsec transform-set command displays a warning message after a user tries to configure an IPSec transform that the hardware does not support:
Router# show crypto ipsec transform-setTransform set transform-1:{esp-256-aes esp-md5-hmac}will negotiate = {Tunnel, },WARNING:encryption hardware does not support transformesp-aes 256 within IPSec transform transform-1
Step 2
Enter the show crypto map [interface interface | tag map-name] command to view your crypto map configuration:
Router# show crypto mapCrypto Map: "router-alice" idb: Ethernet0 local address: 172.21.114.123Crypto Map "router-alice" 10 ipsec-isakmpPeer = 172.21.114.67Extended IP access list 141access-list 141 permit ipsource: addr = 172.21.114.123/0.0.0.0dest: addr = 172.21.114.67/0.0.0.0Current peer: 172.21.114.67Security-association lifetime: 4608000 kilobytes/120 secondsPFS (Y/N): NTransform sets={t1,}Step 3
Enter the show crypto ipsec sa [map map-name | address | identity | detail | interface] command to view information about IPSec security associations:
Router# show crypto ipsec sainterface: Ethernet0Crypto map tag: router-alice, local addr. 172.21.114.123local ident (addr/mask/prot/port): (172.21.114.123/255.255.255.255/0/0)remote ident (addr/mask/prot/port): (172.21.114.67/255.255.255.255/0/0)current_peer: 172.21.114.67PERMIT, flags={origin_is_acl,}#pkts encaps: 10, #pkts encrypt: 10, #pkts digest 10#pkts decaps: 10, #pkts decrypt: 10, #pkts verify 10#send errors 10, #recv errors 0local crypto endpt.: 172.21.114.123, remote crypto endpt.: 172.21.114.67path mtu 1500, media mtu 1500current outbound spi: 20890A6Finbound esp sas:spi: 0x257A1039(628756537)transform: esp-des esp-md5-hmac,in use settings ={Tunnel,}slot: 0, conn id: 26, crypto map: router-alicesa timing: remaining key lifetime (k/sec): (4607999/90)IV size: 8 bytesreplay detection support: Yinbound ah sas:outbound esp sas:spi: 0x20890A6F(545852015)transform: esp-des esp-md5-hmac,in use settings ={Tunnel,}slot: 0, conn id: 27, crypto map: router-alicesa timing: remaining key lifetime (k/sec): (4607999/90)IV size: 8 bytesreplay detection support: Youtbound ah sas:interface: Tunnel0Crypto map tag: router-alice, local addr. 172.21.114.123local ident (addr/mask/prot/port): (172.21.114.123/255.255.255.255/0/0)remote ident (addr/mask/prot/port): (172.21.114.67/255.255.255.255/0/0)current_peer: 172.21.114.67PERMIT, flags={origin_is_acl,}#pkts encaps: 10, #pkts encrypt: 10, #pkts digest 10#pkts decaps: 10, #pkts decrypt: 10, #pkts verify 10#send errors 10, #recv errors 0local crypto endpt.: 172.21.114.123, remote crypto endpt.: 172.21.114.67path mtu 1500, media mtu 1500current outbound spi: 20890A6Finbound esp sas:spi: 0x257A1039(628756537)transform: esp-des esp-md5-hmac,in use settings ={Tunnel,}slot: 0, conn id: 26, crypto map: router-alicesa timing: remaining key lifetime (k/sec): (4607999/90)IV size: 8 bytesreplay detection support: Yinbound ah sas:outbound esp sas:spi: 0x20890A6F(545852015)transform: esp-des esp-md5-hmac,in use settings ={Tunnel,}slot: 0, conn id: 27, crypto map: router-alicesa timing: remaining key lifetime (k/sec): (4607999/90)IV size: 8 bytesreplay detection support: Youtbound ah sas:
For a detailed description of the information displayed by the show commands, refer to the "IP Security and Encryption" chapter of the Security Command Reference publication.
Verifying IPSec High Availability
Perform the following commands to verify and display IPSec High Availability information:
Step 1
Enter the show crypto isakmp ha standby command to view your ISAKMP standby or active SAs.
dst src state I-Cookie R-Cookie172.16.31.100 20.3.113.1 QM_IDLE 796885F3 62C3295E FFAFBACDEED41AFF172.16.31.100 20.2.148.1 QM_IDLE 5B78D70F 3D80ED01 FFA03C6D09FC50BE172.16.31.100 20.4.124.1 QM_IDLE B077D0A1 0C8EB3A0 FF5B152CD233A1E0172.16.31.100 20.3.88.1 QM_IDLE 55A9F85E 48CC14DE FF20F9AEDE37B913172.16.31.100 20.1.95.1 QM_IDLE 3881DE75 3CF384AE FF192CABStep 2
Enter the show crypto ipsec ha command to view your IPSec High Availability HA Manager state.
Router# show crypto ipsec haInterface VIP SAs IPSec HA StateFastEthernet0/0 172.16.31.100 1800 Active since 13:00:16 EDT Tue Oct 1 2002Step 3
Enter the show crypto ipsec sa command to view HA status of the IPSec SA (standby or active).
Router# show crypto ipsec sainterface: FastEthernet0/0Crypto map tag: mymap, local addr. 172.168.3.100local ident (addr/mask/prot/port): (192.168.1.0/255.255.255.0/0/0)remote ident (addr/mask/prot/port): (5.6.0.0/255.255.0.0/0/0)current_peer: 172.168.3.1PERMIT, flags={}#pkts encaps: 0, #pkts encrypt: 0, #pkts digest 0#pkts decaps: 0, #pkts decrypt: 0, #pkts verify 0#pkts compressed: 0, #pkts decompressed: 0#pkts not compressed: 0, #pkts compr. failed: 0, #pkts decompress failed: 0#send errors 0, #recv errors 0local crypto endpt.: 172.168.3.100, remote crypto endpt.: 172.168.3.1path mtu 1500, media mtu 1500current outbound spi: 132ED6ABinbound esp sas:spi: 0xD8C8635F(3637011295)transform: esp-des esp-md5-hmac ,in use settings ={Tunnel, }slot: 0, conn id: 2006, flow_id: 3, crypto map: mymapsa timing: remaining key lifetime (k/sec): (4499/59957)IV size: 8 bytesreplay detection support: YHA Status: STANDBYinbound ah sas:spi: 0xAAF10A60(2867923552)transform: ah-sha-hmac ,in use settings ={Tunnel, }slot: 0, conn id: 2004, flow_id: 3, crypto map: mymapsa timing: remaining key lifetime (k/sec): (4499/59957)replay detection support: YHA Status: STANDBYinbound pcp sas:outbound esp sas:spi: 0x132ED6AB(321836715)transform: esp-des esp-md5-hmac ,in use settings ={Tunnel, }slot: 0, conn id: 2007, flow_id: 4, crypto map: mymapsa timing: remaining key lifetime (k/sec): (4499/59957)IV size: 8 bytesreplay detection support: YHA Status: STANDBYoutbound ah sas:spi: 0x1951D78(26549624)transform: ah-sha-hmac ,in use settings ={Tunnel, }slot: 0, conn id: 2005, flow_id: 4, crypto map: mymapsa timing: remaining key lifetime (k/sec): (4499/59957)replay detection support: YHA Status: STANDBYoutbound pcp sas:Step 4
Enter the show crypto ipsec sa standby command to view your standby SAs:
Router# show crypto ipsec sa standbyinterface: FastEthernet0/0Crypto map tag: mymap, local addr. 172.168.3.100local ident (addr/mask/prot/port): (192.168.1.0/255.255.255.0/0/0)remote ident (addr/mask/prot/port): (5.6.0.0/255.255.0.0/0/0)current_peer: 172.168.3.1PERMIT, flags={}#pkts encaps: 0, #pkts encrypt: 0, #pkts digest 0#pkts decaps: 0, #pkts decrypt: 0, #pkts verify 0#pkts compressed: 0, #pkts decompressed: 0#pkts not compressed: 0, #pkts compr. failed: 0, #pkts decompress failed: 0#send errors 0, #recv errors 0local crypto endpt.: 172.168.3.100, remote crypto endpt.: 172.168.3.1path mtu 1500, media mtu 1500current outbound spi: 132ED6ABinbound esp sas:spi: 0xD8C8635F(3637011295)transform: esp-des esp-md5-hmac ,in use settings ={Tunnel, }slot: 0, conn id: 2006, flow_id: 3, crypto map: mymapsa timing: remaining key lifetime (k/sec): (4499/59957)IV size: 8 bytesreplay detection support: YHA Status: STANDBYinbound ah sas:spi: 0xAAF10A60(2867923552)transform: ah-sha-hmac ,in use settings ={Tunnel, }slot: 0, conn id: 2004, flow_id: 3, crypto map: mymapsa timing: remaining key lifetime (k/sec): (4499/59957)replay detection support: YHA Status: STANDBYinbound pcp sas:outbound esp sas:spi: 0x132ED6AB(321836715)transform: esp-des esp-md5-hmac ,in use settings ={Tunnel, }slot: 0, conn id: 2007, flow_id: 4, crypto map: mymapsa timing: remaining key lifetime (k/sec): (4499/59957)IV size: 8 bytesreplay detection support: YHA Status: STANDBYoutbound ah sas:spi: 0x1951D78(26549624)transform: ah-sha-hmac ,in use settings ={Tunnel, }slot: 0, conn id: 2005, flow_id: 4, crypto map: mymapsa timing: remaining key lifetime (k/sec): (4499/59957)replay detection support: YHA Status: STANDBYoutbound pcp sas:Step 5
This example is baselined on a previous synchronization command. Every time a clear crypto isakmp ha standby resync command on the standby router is run, the delete and add metrics will return to zero. This example assumes some number of SAs have been created.
Router# show crypto isakmp sspVIP ADDS DELETES REQUESTS REPLIES172.16.31.100 538 33 0 0After a clear cryp isa ha standby resync:Router# show crypto isakmp sspVIP ADDS DELETES REQUESTS REPLIES172.16.31.100 0 0 514 514
Monitoring and Maintaining IPSec Stateful Failover (VPN High Availability)
Perform the following commands in EXEC mode to monitor and maintain IPSec Stateful Failover (VPN High Availability) information:
Displaying SSP Information
The following example uses the show ssp client command:
router# show ssp clientSSP Client InformationDOI Client Name Version Running Ver1 IPSec HA Manager 1.0 1.02 IKE HA Manager 1.0 1.0The following example uses the show ssp packet command:
router# show ssp packetSSP packet InformationSocket creation time: 01:01:06Local port: 3249 Server port: 3249Packets Sent = 38559, Bytes Sent = 2285020Packets Received = 910, Bytes Received = 61472The following example uses the show ssp peers command:
router# show ssp peersSSP Peer InformationIP Address Connection State Local Interface40.0.0.1 Connected FastEthernet0/1The following example uses the show ssp redundancy command:
router# show ssp redundancySSP Redundancy InformationDevice has been ACTIVE for 02:55:34Virtual IP Redundancy Name Interface172.16.31.100 KNIGHTSOFNI FastEthernet0/0Debug Configuration Tasks and Examples
This section provides the following debug configuration tasks and examples:
•
Clearing Dormant SAs on Standby Routers
Clearing Dormant SAs on Standby Routers
Perform the following commands in EXEC mode to clear associated SA entries:
Debugging
Perform the following commands in EXEC mode to enable debugging:
To prevent debug messages from flooding the console, disable the console log and enable the buffer log as follows:
Router# configure terminalRouter(config)# logging bufferedRouter(config)# no logging consoleTroubleshooting Tips
Enabling IPSec Stateful Failover (VPN High Availability) is dependent on the proper operation of HSRP, and includes the virtual IP address that is specified during HSRP setup.
To enable IPSec Stateful Failover (VPN High Availability), a network administrator should perform the following procedures:
•
Enable HSRP.
•
Enable IPSec Stateful Failover (VPN High Availability).
•
Verify processes are working properly.
If you follow the above procedures, but find that either the active or standby IPSec Stateful Failover (VPN High Availability) processes are dysfunctional, you can perform the following checks:
•
Use the show ssp command to verify the SSP process is running.
•
Make sure that both routers share identical IPSec configurations. This is critical. If routers are configured differently, IPSec Stateful Failover (VPN High Availability) will not work.
•
Verify that an IPSec connection can be formed with existing maps, transforms, and access lists.
•
Configure HSRP on the inside and outside interfaces and make the HSRP groups track one another. Verify this works properly by performing a shut command on either of the interfaces, then observe that the HSRP standby router takes active control from the active router.
•
Verify that SSP peers can see each other by performing a show ssp peer command on both the active and standby router.
•
Bind the IKE and IPSec to SSP and send traffic over the tunnels. A user can view HA messages on the standby router as both the active and standby routers synchronize.
HSRP settings may require adjustments depending on the interface employed, such as Fast Ethernet or Gigabit Ethernet. To tune HSRP settings, perform the following steps:
Step 1
Ensure that the interfaces are synchronized by using the show standby brief command.
Router# show standby briefInterface group priority p state active address standby address group addressFA 0/0 1 100 Active local 172.16.31.6 172.16.31.100FA 0/1 2 100 Active local 40.0.0.6 40.0.0.0.100Step 2
Leave the delay timers at their default settings by using the no standby delay timer command.
Router# no standby delay timerStep 3
When the other router comes online, issue the show standby brief command once again. If you see the following output, you must set the standby router's delay timer.
Router# show standby briefinterface group priority p state active address standby address group addressFA 0/0 1 100 Standby 172.16.31.6 local 172.16.31.100FA 0/1 2 100 Active local 40.0.0.6 40.0.0.100Command Reference
This section documents new commands. All other commands used with this feature are documented in the Cisco IOS Release12.2(2) command reference publications.
•
clear crypto isakmp ha standby
•
port
clear crypto isakmp ha standby
To clear dormant entries from the router, use the clear crypto isakmp ha standby command.
clear crypto isakmp ha standby [resync]
Syntax Description
Defaults
No default behavior or values.
Command Modes
Privileged EXEC
Command History
Examples
None
Related Commands
clear crypto sa ha standby
To clear SAs, use the clear crypto sa ha standby command.
clear crypto sa ha standby [peer ip address | resync]
Syntax Description
peer
Clears SAs associated with peer.
ip address
Specifies peer IP address.
resync
Resynchronizes SA state entries between active and standby routers.
Defaults
No default behavior or values.
Command Modes
Privileged EXEC
Command History
Examples
None
Related Commands
crypto isakmp ssp
To enable ISAKMP state to be transferred by the SSP channel identified by the ID, use the crypto isakmp ssp command. To disable this feature, use the no form of this command.
crypto isakmp ssp id
[no] crypto isakmp ssp id
Syntax Description
Defaults
No default behavior or values.
Command Modes
Configuration
Command History
Usage Guidelines
If this feature is disabled, all dormant SA entries bound to that ID will be removed.
Examples
None
Related Commands
crypto map
To enable IPSec state information to be transferred by the SSP channel identified, use the crypto map command. To disable this feature, use the no form of this command.
crypto map name ssp id
[no] crypto map name ssp id
Syntax Description
Defaults
No default behavior or values.
Command Modes
Interface configuration
Command History
Examples
None
Related Commands
crypto map ha
To specify the intervals that the active router should update the standby router with anti-replay sequence numbers, use the crypto map ha command. To disable this feature, use the no form of this command.
crypto map name ha replay-interval inbound inbound interval outbound outbound interval
[no] crypto map name ha replay-interval inbound inbound interval outbound outbound interval
Syntax Description
Defaults
The default for inbound is 1000. The default for outbound is one (indicating 1,000,000).
Command Modes
Privileged EXEC
Command History
Usage Guidelines
This feature protects against anti-replay attacks. Suppose an errant user was planning an anti-replay attack. If the active router goes down, the standby will assume control and ownership. If the standby router does not have a current anti-replay counter, it cannot know what packets have already be sent to the active router because it will not have a current updated anti-replay window. So in theory, the errant user would be able to send packets that have already be sent. If the network administer employs the crypto map ha command, this will force the active router to update at constant intervals the anti-replay counter to the standby router. If the active would fail, the standby would assume control, and also be in possession of an updated anti-replay window, so anti-replay attacks would be difficult to undertake.
Examples
None
Related Commands
debug crypto isakmp ha
To enable IKE HA Manager debugging, use the debug crypto isakmp ha command. To disable debugging, use the no form of this command.
debug crypto isakmp ha ?
[no] debug crypto isakmp ha [detail | fsm | update ]
Syntax Description
detail
Enables detailed IKE HA Manager debugging.
fsm
Enables finite state machine debugging.
update
Enables updates for IKE HA Manager debugging.
Defaults
Disabled
Command Modes
Privileged EXEC
Command History
Examples
None
Related Commands
debug crypto ipsec ha
To enable IPSec HA debugging, use the debug crypto ipsec ha command. To disable debugging, use the no form of this command.
debug crypto ipsec ha [detail | fsm | update]
[no] debug crypto ipsec ha [detail | fsm | update]
Syntax Description
detail
Enables detailed IPSec HA debugging.
fsm
Enables finite state machine debugging.
update
Enables debugging for SSP updates.
Defaults
No default behavior or values.
Command Modes
Privileged EXEC
Command History
Examples
None
Related Commands
debug ssp
To enable ssp debugging, use the debug ssp command. To disable ssp debugging, use the no form of this command.
debug ssp [fsm | socket | packet | peers | redundancy | config]
[no] debug ssp [fsm | socket | packet | peers | redundancy | config]
Syntax Description
Defaults
No default behavior or values.
Command Modes
SSP configuration
Command History
Examples
None
Related Commands
port
To define the TCP port that SSP will use for communications, use the port command. To disable this feature, use the no form of this command.
port tcp-port
[no] port tcp-port
Syntax Description
Defaults
Default tcp-port is 3249
Command Modes
SSP configuration
Command History
Examples
None
Related Commands
remote
To define the channel that the active router communicates SA states to the standby router, use the remote command. To disable this feature, use the no form of this command.
remote ipaddr
[no] remote ipaddr
Syntax Description
Defaults
None
Command Modes
SSP configuration
Command History
Examples
None
Related Commands
redundancy
To define the HSRP group, use the redundancy command. To disable this feature, use the no form of this command.
redundancy name
[no] redundancy name
Syntax Description
Defaults
None
Command Modes
SSP configuration
Command History
Examples
None
Related Commands
show crypto ipsec ha
To display IPSec HA information, use the show crypto ipsec ha command.
show crypto ipsec
Syntax Description
This command has no arguments or keywords.
Defaults
No default behavior or values.
Command Modes
Privileged EXEC
Command History
Examples
The following example is output from the show crypto ipsec ha command:
router# show crypto ipsec haInterface VIP SAs IPSec HA StateFastEthernet0/0 172.16.31.100 1800 Active since 13:00:16 EDT Tue Oct 1 2002Related Commands
show crypto isakmp ha
To show the ISAKMP standby or active SAs, use the show crypto isakmp ha command.
show crypto isakmp ha [standby | active]
Syntax Description
Defaults
No default behavior or values.
Command Modes
Configuration
Command History
Examples
The following example is output from the show crypto isakmp ha standby command:
router# show crypto isakmp ha standbydst src state I-Cookie R-Cookie172.16.31.100 20.3.113.1 QM_IDLE 796885F3 62C3295E FFAFBACDEED41AFF172.16.31.100 20.2.148.1 QM_IDLE 5B78D70F 3D80ED01 FFA03C6D09FC50BE172.16.31.100 20.4.124.1 QM_IDLE B077D0A1 0C8EB3A0 FF5B152CD233A1E0172.16.31.100 20.3.88.1 QM_IDLE 55A9F85E 48CC14DE FF20F9AEDE37B913172.16.31.100 20.1.95.1 QM_IDLE 3881DE75 3CF384AE FF192CAB795019ABThe following example is output from the show crypto isakmp ha command:
router# show crypto isakmp haVIP SAs Stamp HA State172.16.31.100 902 72C28872 Active since 13:03:21 EDT Tue Oct 1 2002dstRelated Commands
show crypto ipsec sa
To display IPSec HA status, use the show crypto ipsec sa command.
show crypto ipsec sa [addr | standby]
Syntax Description
Defaults
No default behavior or values.
Command Modes
Privileged EXEC
Command History
Examples
The following example is output from the show crypto ipsec sa command:
router# show crypto ipsec sainterface: FastEthernet0/0Crypto map tag: mymap, local addr. 172.168.3.100local ident (addr/mask/prot/port): (192.168.1.0/255.255.255.0/0/0)remote ident (addr/mask/prot/port): (5.6.0.0/255.255.0.0/0/0)current_peer: 172.168.3.1PERMIT, flags={}#pkts encaps: 0, #pkts encrypt: 0, #pkts digest 0#pkts decaps: 0, #pkts decrypt: 0, #pkts verify 0#pkts compressed: 0, #pkts decompressed: 0#pkts not compressed: 0, #pkts compr. failed: 0, #pkts decompress failed: 0#send errors 0, #recv errors 0local crypto endpt.: 172.168.3.100, remote crypto endpt.: 172.168.3.1path mtu 1500, media mtu 1500current outbound spi: 132ED6ABinbound esp sas:spi: 0xD8C8635F(3637011295)transform: esp-des esp-md5-hmac ,in use settings ={Tunnel, }slot: 0, conn id: 2006, flow_id: 3, crypto map: mymapsa timing: remaining key lifetime (k/sec): (4499/59957)IV size: 8 bytesreplay detection support: YHA Status: STANDBYinbound ah sas:spi: 0xAAF10A60(2867923552)transform: ah-sha-hmac ,in use settings ={Tunnel, }slot: 0, conn id: 2004, flow_id: 3, crypto map: mymapsa timing: remaining key lifetime (k/sec): (4499/59957)replay detection support: YHA Status: STANDBYinbound pcp sas:outbound esp sas:spi: 0x132ED6AB(321836715)transform: esp-des esp-md5-hmac ,in use settings ={Tunnel, }slot: 0, conn id: 2007, flow_id: 4, crypto map: mymapsa timing: remaining key lifetime (k/sec): (4499/59957)IV size: 8 bytesreplay detection support: YHA Status: STANDBYoutbound ah sas:spi: 0x1951D78(26549624)transform: ah-sha-hmac ,in use settings ={Tunnel, }slot: 0, conn id: 2005, flow_id: 4, crypto map: mymapsa timing: remaining key lifetime (k/sec): (4499/59957)replay detection support: YHA Status: STANDBYoutbound pcp sas:------------------------------------------------------------------------------------------The following example is output from the show crypto ipsec sa addr command:
router# show crypto ipsec sa addrdest address: 172.168.3.100protocol: AHspi: 0xAAF10A60(2867923552)transform: ah-sha-hmac ,in use settings ={Tunnel, }slot: 0, conn id: 2004, flow_id: 3, crypto map: mymapsa timing: remaining key lifetime (k/sec): (4499/59957)replay detection support: YHA Status: STANDBYprotocol: ESPspi: 0xD8C8635F(3637011295)transform: esp-des esp-md5-hmac ,in use settings ={Tunnel, }slot: 0, conn id: 2006, flow_id: 3, crypto map: mymapsa timing: remaining key lifetime (k/sec): (4499/59957)IV size: 8 bytesreplay detection support: YHA Status: STANDBYdest address: 172.168.3.1protocol: AHspi: 0x1951D78(26549624)transform: ah-sha-hmac ,in use settings ={Tunnel, }slot: 0, conn id: 2005, flow_id: 4, crypto map: mymapsa timing: remaining key lifetime (k/sec): (4499/59957)replay detection support: YHA Status: STANDBYprotocol: ESPspi: 0x132ED6AB(321836715)transform: esp-des esp-md5-hmac ,in use settings ={Tunnel, }slot: 0, conn id: 2007, flow_id: 4, crypto map: mymapsa timing: remaining key lifetime (k/sec): (4499/59957)IV size: 8 bytesreplay detection support: YHA Status: STANDBY------------------------------------------------------------------------------------------The following example is output from the show crypto ipsec sa standby command:
router# show crypto ipsec sa standbyinterface: FastEthernet0/0Crypto map tag: mymap, local addr. 172.168.3.100local ident (addr/mask/prot/port): (192.168.1.0/255.255.255.0/0/0)remote ident (addr/mask/prot/port): (5.6.0.0/255.255.0.0/0/0)current_peer: 172.168.3.1PERMIT, flags={}#pkts encaps: 0, #pkts encrypt: 0, #pkts digest 0#pkts decaps: 0, #pkts decrypt: 0, #pkts verify 0#pkts compressed: 0, #pkts decompressed: 0#pkts not compressed: 0, #pkts compr. failed: 0, #pkts decompress failed: 0#send errors 0, #recv errors 0local crypto endpt.: 172.168.3.100, remote crypto endpt.: 172.168.3.1path mtu 1500, media mtu 1500current outbound spi: 132ED6ABinbound esp sas:spi: 0xD8C8635F(3637011295)transform: esp-des esp-md5-hmac ,in use settings ={Tunnel, }slot: 0, conn id: 2006, flow_id: 3, crypto map: mymapsa timing: remaining key lifetime (k/sec): (4499/59957)IV size: 8 bytesreplay detection support: YHA Status: STANDBYinbound ah sas:spi: 0xAAF10A60(2867923552)transform: ah-sha-hmac ,in use settings ={Tunnel, }slot: 0, conn id: 2004, flow_id: 3, crypto map: mymapsa timing: remaining key lifetime (k/sec): (4499/59957)replay detection support: YHA Status: STANDBYinbound pcp sas:outbound esp sas:spi: 0x132ED6AB(321836715)transform: esp-des esp-md5-hmac ,in use settings ={Tunnel, }slot: 0, conn id: 2007, flow_id: 4, crypto map: mymapsa timing: remaining key lifetime (k/sec): (4499/59957)IV size: 8 bytesreplay detection support: YHA Status: STANDBYoutbound ah sas:spi: 0x1951D78(26549624)transform: ah-sha-hmac ,in use settings ={Tunnel, }slot: 0, conn id: 2005, flow_id: 4, crypto map: mymapsa timing: remaining key lifetime (k/sec): (4499/59957)replay detection support: YHA Status: STANDBYoutbound pcp sas:Related Commands
show ssp
To show the SSP state information, use the show ssp command.
show ssp [packet | peers | redundancy | clients]
Syntax Description
Defaults
No default behavior or values.
Command Modes
SSP configuration
Command History
Examples
The following example is output from the show ssp command:
router# show ssp clientSSP Client InformationDOI Client Name Version Running Ver1 IPSec HA Manager 1.0 1.02 IKE HA Manager 1.0 1.0router# show ssp packetSSP packet InformationSocket creation time: 01:01:06Local port: 3249 Server port: 3249Packets Sent = 38559, Bytes Sent = 2285020Packets Received = 910, Bytes Received = 61472router# show ssp peersSSP Peer InformationIP Address Connection State Local Interface40.0.0.1 Connected FastEthernet0/1router# show ssp redundancySSP Redundancy InformationDevice has been ACTIVE for 02:55:34Virtual IP Redundancy Name Interface172.16.31.100 KNIGHTSOFNI FastEthernet0/0Related Commands
ssp group
To enter into the CLI ssp sub-mode, use the ssp group command. To disable this feature, use the no form of this command.
ssp group group
[no] ssp group group
Syntax Description
Defaults
No default behavior or values.
Command Modes
SSP configuration
Command History
Examples
None
Related Commands
Glossary
Active—Active IPSec High Availability router.
DPD—Dead peer detection. DPD allows two IPSec peers to determine if the other is still "alive" during the lifetime of a VPN connection.
GRE—Generic Routing Encapsulation. Tunneling protocol developed by Cisco that can encapsulate a wide variety of protocol packet types inside IP tunnels, creating a virtual point-to-point link to Cisco routers at remote points over an IP internetwork.
HSRP—Hot Standby Routing Protocol. HSRP provides network redundancy for IP networks, ensuring that user traffic immediately and transparently recovers from first hop failures in network edge devices or access circuits.
IKE—Internet Key Exchange. IKE establishes a shared security policy and authenticates keys for services (such as IPSec) that require keys. Before any IPSec traffic can be passed, each router/firewall/host must verify the identity of its peer. This can be done by manually entering pre-shared keys into both hosts or by a CA service.
IPSec—IP Security. A framework of open standards that provides data confidentiality, data integrity, and data authentication between participating peers. IPSec provides these security services at the IP layer. IPSec uses IKE to handle the negotiation of protocols and algorithms based on local policy and to generate the encryption and authentication keys to be used by IPSec. IPSec can protect one or more data flows between a pair of hosts, between a pair of security gateways, or between a security gateway and a host.
SA—security association. An instance of security policy and keying material applied to a data flow. Both IKE and IPSec use SAs, although SAs are independent of one another. IPSec SAs are unidirectional and they are unique in each security protocol.
SSP—State Synchronization Protocol (SSP) is a protocol developed to transfer state information between the active and standby routers.
Standby—Standby IPSec High Availability router.
Stateful Failover—Feature that enables a backup (standby) router to automatically take over the primary (active) router's tasks in the event of a active router failure with minimal or no loss of traffic. The remote peer sees no difference between the two routers since it is connected to a virtual end point (VEP), owned by either headend router that shares the same IPSec information.
 Feedback
Feedback