Cisco ISG Design and Deployment Guide: ATM to ISG LNS Aggregation
Available Languages
Table Of Contents
Cisco ISG Design and Deployment Guide:
ATM to ISG LNS AggregationDesigning ATM to ISG LNS Aggregation
Deploying ATM to ISG LNS Aggregation
Verifying ATM to ISG LNS Aggregation
Verification of Default BOD256K Service
show Command Output for BOD1MTIME Service
show Command Output for History of Service Changes
Complete Running Configurations
Cisco ISG Design and Deployment Guide:
ATM to ISG LNS Aggregation
Version History
The Intelligent Service Architecture (ISA) is a Cisco IOS feature set that enables the provisioning and maintaining of broadband networks that have multiple types of edge devices, many subscribers, and many services. ISA combines real-time session and flow control with programmable, dynamic policy control to deliver flexible and highly scalable subscriber session management capabilities.
A Cisco device that is running a Cisco IOS image with ISA is called a Cisco Intelligent Service Gateway (ISG). A Cisco ISG is used to control subscriber access at the edge of an IP network. An ISG is deployed at network access control points, and subscribers access services through ISG. The role of ISA is to execute policies that identify and authenticate subscribers and provide access to the services that the subscriber is entitled to access.
This document describes how to leverage the capabilities of a Cisco ISG to simply network design and deployment. The network described in this document uses the Cisco 7206 and 7301 as ISGs, ATM as the aggregation technology, and L2TP tunnels to securely deliver traffic across the Internet. It enables ISPs to offer customers both basic Layer 3 VPN access and the advanced services known as Bandwidth on Demand and Prepaid Services.
This document contains the following sections:
•
Designing ATM to ISG LNS Aggregation
•
Deploying ATM to ISG LNS Aggregation
•
Verifying ATM to ISG LNS Aggregation
•
Complete Running Configurations
Designing ATM to ISG LNS Aggregation
The network described in this document uses the Cisco 7206 and 7301 as ISGs, ATM as the aggregation technology, and L2TP tunnels to securely deliver traffic across the Internet. The network involves two ISPs:
•
ISP-1 offers wholesale service to other ISPs.
•
ISP-2 contracts with ISP-1 to receive wholesale service, which it then offers to retail customers.
The motivation for deploying this network is an ISP's desire to broaden the flexibility of its digital subscriber line (DSL) deployments beyond traditional, static DSL service. Basic Layer 3 VPN access is established first. The following advanced ISA services are then deployed:
•
Bandwidth on Demand—Enables subscribers to temporarily increase their upstream and downstream bandwidths. This increased bandwidth can be charged to the subscriber's account on either a duration or a volume basis.
•
Prepaid Services—Enables subscribers to purchase short-term DSL access, using either time or volume limits.
The following sections describe the design of the network:
Network Topology
Figure 1 shows a high-level network topology.
Figure 1 High-Level Topology

Network Elements
The following elements play key roles in the network:
•
CPE
•
LAC
•
LNS
•
PE
•
SESM
CPE
The customer premises equipment (CPE) router is a small router (such as the Cisco 800 series) that is used to initiate PPP over Ethernet (PPPoE) connections from the customer PC to the L2TP Access Concentrator (LAC).
DSLAM
The Digital Subscriber Line Access Multiplexer (DSLAM) aggregates multiple incoming DSL connections into a single ATM line. It is maintained by ISP-1 at a point-of-presence (POP) separate from the ISP's central network.

Note
The configuration of the DSLAM will not be discussed in this document.
LAC
The L2TP Access Concentrator (LAC) is maintained by ISP-1 as part of its central network. It receives incoming sessions from the DSLAM and forwards them to the appropriate retail ISP (ISP-2 in this case) by establishing an L2TP tunnel with the ISG LNS. The LAC contacts ISP-1's AAA server to determine the forwarding information based on the domain name in the subscriber's username.
LNS
The ISG L2TP Network Server (LNS) terminates the L2TP tunnel from the LAC and the PPPoE session from the subscriber. It is maintained by ISP-2 on its central network. The ISG LNS authenticates the subscriber by contacting the AAA server for ISP-2 and assigns the subscriber a VPN routing/forwarding instance (VRF). The ISG LNS also communicates with the AAA server when the subscriber requests additional services.
PE
The provider edge (PE) router is responsible for maintaining VRF information. It is the final endpoint on the ISP's network that terminates the subscriber session. The ISP uses VRF to segment customers easily without having to specify different subnets for different classes of customers.
AAA Server for ISP-1
The AAA server for ISP-1 (known as AAA-1) maintains forwarding information for the retail ISPs. When queried by the LAC, it sends forwarding information based on the subscriber's domain name or username.
AAA Server for ISP-2
The AAA server for ISP-2 (known as AAA-2) maintains subscriber authentication information as well as information on the services available to subscribers. When the ISG LNS receives a subscriber's username and password, it forwards them to AAA-2 for authentication. When a subscriber activates a service, the ISG LNS contacts AAA-2. AAA-2 then replies with information about the service to the ISG LNS.
SESM
The Cisco Subscriber Edge Services Manager (SESM) provides service selection and connection management in broadband and mobile wireless networks. The Cisco SESM provides a web portal by which users access services. ISPs can customize the web portal to their needs.

Note
Configuring the Cisco SESM is beyond the scope of this document. A detailed Installation and Configuration Guide for the Cisco SESM is at the following URL: http://www.cisco.com/univercd/solution/sesm/sesm_320/index.htm
Billing Server
The billing server maintains subscriber account information, including the amount of credit remaining for prepaid services. When subscribers initiate services, the ISG LNS contacts the billing server to determine if the subscriber has credit available.
Network Design Options
The following sections describe the various options that the ISP must consider in deploying the network:
Aggregation Technology
ISA currently supports ATM for use as the aggregation technology.
Routing Technology
In all cases the DSLAM delivers traffic to the first ISG using an ATM permanent virtual circuit (PVC). When designing the network, you have three basic choices for how to deliver traffic from the ISG at the wholesale ISP to the retail ISP:
•
IP routed—Traffic is IP-routed from the ISG to the retail ISP.
•
PPP terminated—The DSLAM delivers traffic to the ISG using PPPoE. The ISG terminates the PPPoE and then IP routes traffic to the retail ISP.
•
L2TP tunneled—The DSLAM delivers traffic to the ISG using PPPoE. The ISG then establishes an L2TP tunnel with an LNS at the retail ISP. The LNS terminates the PPPoE, and IP is used to route the traffic in the retail ISP's network. Using an L2TP tunnel offers the advantage that it can support both ATM and Gigabit Ethernet as the aggregation technology.
The network deployed in this document uses the L2TP tunneled method.
QoS Strategy
Figure 2 shows all of the interfaces in the network where quality of service (QoS) could potentially be configured, where "Up" refers to the upstream interface between the two devices, and "Dw" refers to the downstream interface. The interfaces in bold are where QoS is configured for this deployment.
Figure 2 QoS Interfaces
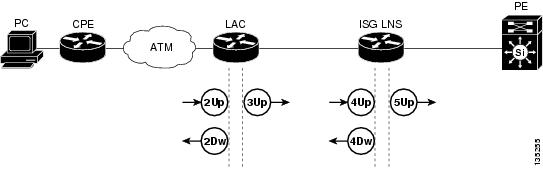
Table 1 describes the QoS strategy that is deployed on each of the interfaces shown in Figure 2.
Protocol Flow
PPP is tunneled from the LAC to the ISG LNS. At the ISG LNS, the PPP session is terminated, and the encapsulated IP session is routed on through the ISP's network. The identity of the customer is uniquely maintained only by the PPP session. Figure 3 shows how the PPP session is routed across the network.
Figure 3 Network Protocol Flow

Figure 4 shows all of the protocols that are active at each device in the network.
Figure 4 Network Protocol Stacks

Multiservice Service Bundle
Because of the large number of features available for ISA services, the design and deployment guides group the features into service bundles. For this deployment, the Multiservice service bundle will be deployed. It consists of the features described in the following section:
Layer 3 VPN Access
All ISPs that deploy ISA services begin with Layer 3 VPN access. In this network, this consists of basic DSL connectivity. Subscribers establish Layer 2 access connections over a Layer 3 VPN technology—in this case, an Multiprotocol Label Switching (MPLS) VPN. Subscriber bandwidth for basic Layer 3 VPN access is capped at 128 kbps upstream and 256 kbps downstream.
Bandwidth on Demand
The Bandwidth on Demand feature enables subscribers to temporarily increase their upstream and downstream bandwidths for either a set duration of time or volume of bandwidth. Subscribers first establish basic connectivity with a default cap on bandwidth and then access a website (maintained by the Cisco SESM) where they trigger a request for the Bandwidth on Demand. The ISP authorizes the subscriber for the service and bills the subscriber's account. The service remains active until either the subscriber deactivates the service or the subscriber terminates the session.
Prepaid Services
The Prepaid Services feature provides the same service to the subscriber as the Bandwidth on Demand feature. Subscribers access a website (maintained by the Cisco SESM) to increase their bandwidth. The difference between the two features is in how they are billed. The Bandwidth on Demand feature is charged against the subscriber account, which the subscriber pays later, after service is rendered. For Prepaid Services, subscribers pay into their accounts before the service is initiated. When a subscriber activates the service, the billing server charges the subscriber's account either for the time the service is active or for the bandwidth the subscriber uses. The service remains active until either the subscriber's account is depleted or the subscriber deactivates the service or terminates the session.
Deploying ATM to ISG LNS Aggregation
The following sections describe how to deploy the ATM to ISG LNS aggregation network:
•
Verifying ATM to ISG LNS Aggregation
Deployment Model
The following sections describe the deployment model on which the network is based:
In this deployment, the subscriber's PC connects to CPE, which initiates a PPPoE session to the LAC (maintained by ISP-1) across either an ATM or a DSL network. The LAC then establishes an L2TP tunnel with the ISG LNS (maintained by ISP-2), and forwards the PPPoE session to the LNS. The LNS assigns the subscriber a VRF and assigns the subscriber the default service, which is a capped bandwidth of 256 kbps. The following advanced ISA services are then available to the subscriber:
•
BOD1MVOLUME—1 Mbps downstream, 256 kbps upstream
•
BOD1MTIME—1 Mbps downstream, 256 kbps upstream
•
BOD2MVOLUME—2 Mpbs downstream, 512 kbps upstream
•
BOD2MTIME—2 Mbps downstream, 512 kbps upstream
For time-based service, subscribers are billed according to the length of time that the service is active. For volume-based service, subscribers are billed accordign to the amount of bandwidth they use.

Note
In this deployment, subscribers will not be able to switch from a time-based prepaid service to a volume-based prepaid service or vice versa. In this deployment, subscribers have access to both time-based and volume-based services. This is done to describe the full range of ISA services available. Typically, ISPs will only deploy either time-based or volume-based services for subscribers, but not both simultaneously.
Network Topology
Figure 5 shows the network topology of this deployment.
Figure 5 Network Topology

Call Flows
The following call flows describe the operation of the network:
•
Basic Layer 3 VPN Access Call Flow
Basic Layer 3 VPN Access Call Flow
Figure 6 shows the call flow process of establishing basic Layer 3 VPN access. Every subscriber session begins with this process before initiating advanced ISA services.
Figure 6 Layer 3 VPN Access Call Flow

The following describes the sequence of events in Figure 6:
1.
The subscriber initiates a PPPoE connection from the PC to the LAC by way of the CPE.
2.
The PC and the LAC establish a PPP connection.
3.
The LAC contacts the AAA-1 server to retrieve domain authentication information for L2TP.
4.
The LAC establishes an L2TP tunnel with the ISG LNS. This step is necessary only if an L2TP tunnel does not already exist.
5.
The LAC forwards the subscriber PPP session and associated information to the ISG LNS.
6.
The ISG LNS contacts the AAA-2 server to authenticate the subscriber. Once the subscriber is authenticated, the ISG LNS clones a virtual-access interface from the virtual template.
7.
The ISG LNS sends a CHAP response to the subscriber. The IP Control Protocol (IPCP) negotiation is performed, and the route to the ISG LNS is installed. The PPP session now runs between the subscriber and the ISG LNS, while the ISG forwards the PPP traffic over the L2TP tunnel.
8.
The ISG LNS sends an accounting start message to the AAA-2 server.
9.
The subscriber and the ISG LNS use IPCP to negotiate the link details, including the IP address. IPCP is responsible for configuring, enabling, and disabling the IP protocol modules on both ends of the PPP link. IPCP uses the same packet exchange mechanism as the Link Control Protocol (LCP). IPCP packets may not be exchanged until PPP has reached the Network-Layer Protocol phase.
Prepaid Service Call Flow
Figure 7 shows the call flow process that occurs when a subscriber initiates prepaid services.
Figure 7 Prepaid Services Call Flow

The following describes the sequence of events shown in Figure 7:
1.
The subscriber selects the BOD1MTIME service on the Cisco SESM web interface.
2.
The Cisco SESM sends an Access-Request message to the ISG LNS for the subscriber's information.
3.
The ISG LNS replies to the Cisco SESM with an Access-Accept message containing the subscriber's information.
4.
The Cisco SESM sends an Access-Request message to the ISG LNS requesting information on the BOD1MTIME service.
5.
The ISG LNS sends an Access-Request message to the AAA-2 server requesting information on the BOD1MTIME service.
6.
The AAA-2 server replies to the ISG LNS with an Access-Accept message containing the traffic class, the BOD1MTIME profile, and the prepaid configuration.
7.
The ISG LNS sends an Access-Accept message to the AAA-2 server containing the details of the BOD1MTIME service.
8.
The ISG LNS sends an Access-Request message to the billing server, notifying it that the subscriber has initiated the BOD1MTIME service.
9.
The billing server replies with an Access-Accept message that authorizes the subscriber for a set quota of time.
10.
The ISG LNS sends an accounting request to the billing server with the subscriber's username and an event time stamp.
11.
When the subscriber quota is depleted, the ISG LNS sends a reauthorization request to renew the quota.
12.
The billing server reauthorizes the subscriber and sends a renewed quota to the ISG LNS.
Steps 8 through 12 are repeated until either the subscriber terminates the BOD1MTIME service or the subscriber runs out of quota on the billing server.
Device Characteristics Table
Table 2 describes details of the devices in the network.
Configuring the Network
The configuration of this deployment is divided into the following sections:
•
Service Bundle Configurations
Prerequisites
Before the ISA configuration begins, the following baseline network operations must be configured:
•
Basic IP connectivity must be established across the entire network
•
L2TP must be configured between the ISG LAC and LNS
•
Subscribers must be able to establish a PPPoE connection over the L2TP tunnel to the LNS.
Network administrators should be familiar with the following topics:
•
CAR configuration procedure: http://www.cisco.com/univercd/cc/td/doc/product/rtrmgmt/cnsar/3_5/install/config.htm
•
CNR configuration procedure: http://www.cisco.com/en/US/products/sw/netmgtsw/ps1982/products_user_guide_book09186a008022745c.html
•
Basic broadband (PPP and L2TP) configuration:
–
http://www.cisco.com/en/US/products/sw/iosswrel/ps1835/products_configuration_guide_chapter09186a00800ca72a.html
–
http://www.cisco.com/en/US/products/sw/iosswrel/ps1835/products_configuration_guide_chapter09186a00800ca724.html
–
http://www.cisco.com/en/US/partner/tech/tk801/tk703/technologies_configuration_example09186a0080093c2a.shtml
Baseline Configuration
The following devices are configured to enable baseline network operation. The baseline configuration establishes basic connectivity across the network and enables the subscriber to establish basic Layer 3 VPN access.
•
CPE
•
LAC
•
PE
CPE
The following baseline configuration tasks are performed on the CPE:
•
Configuring the Ethernet Interface and DHCP
•
Configuring the Outbound Interface
•
Configuring the Dialer Interface and NAT
Configuring the Ethernet Interface and DHCP
Interface Ethernet 0 is configured to connect to the subscriber PC, and DHCP is enabled for incoming sessions.
interface Ethernet0ip address 10.10.10.1 255.255.255.0ip nat insideload-interval 30no cdp enablehold-queue 100 out!ip dhcp excluded-address 10.10.10.1!! DHCP configuration for interface Ethernet 0 subscribersip dhcp pool CLIENTimport allnetwork 10.10.10.0 255.255.255.0default-router 10.10.10.1lease 0 2Configuring the Outbound Interface
ATM interface 0.6 is configured as a PVC. This is the outbound interface from the CPE to the DSLAM.
interface ATM0.6 point-to-point! This is the PVC which is going to the ATM DSLAMpvc 6/46encapsulation aal5snap! This associates the PVC with dialer 1pppoe-client dial-pool-number 1Configuring the Dialer Interface and NAT
Dialer interface 1 is configured to receive incoming connections from the subscriber. CHAP is used for the CPE's username and password, and NAT is enabled for outbound traffic.
interface Dialer1ip address negotiatedip nat outside! using PPPencapsulation pppip route-cache flowdialer pool 1no cdp enable!The username and password are set for CHAPppp chap hostname cpe6_1@isp.comppp chap password 7 060A0E23!! Enables subscribers on the inside of E0 to access outside using NATip nat inside source list 1 interface Dialer1 overload!ip classless! set the default gateway out the dialer 1 interfaceip route 0.0.0.0 0.0.0.0 Dialer1!! allow E0 subscribers to be NAT translatedaccess-list 1 permit 10.10.10.0 0.0.0.255! refers to ACL 1dialer-list 1 protocol ip permitno cdp runLAC
The following baseline configuration tasks are performed on the LAC:
•
Configuring AAA and the Connection to the RADIUS Server
•
Configuring the Connection to the ISG LNS and PPPoE
Configuring AAA and the Connection to the RADIUS Server
A basic AAA configuration is entered, and the connection to the RADIUS server is configured, including vendor specific attribute (VSA) accounting and authentication.
aaa new-model!aaa authentication login default none! setup RADIUS server for authenticationaaa authentication ppp default group radius localaaa authorization network default group radius localaaa accounting network default start-stop group radius!!aaa session-id common!interface Loopback0ip address 10.200.1.49 255.255.255.255!! Use Loopback 0 to communicate with radius serverip radius source-interface Loopback0!!radius-server host 10.100.1.35 auth-port 1812 acct-port 1813 key Ciscoradius-server vsa send accountingradius-server vsa send authenticationConfiguring the Connection to the ISG LNS and PPPoE
The connection to the ISG LNS is configured. The LAC uses VPDN to initiate L2TP tunnels to the ISG LNS, which are used to carry the subscriber PPPoE sessions. An ISA control policy map is used to instruct L2TP to authenticate on the basis domain name, and a BBA group is used to configure PPPoE.
no ip dhcp use vrf connected!subscriber policy recording rules limit 64subscriber access pppoe pre-authorize nas-port-id defaultsubscriber authorization enable! Enables VPDN globally, which is used for PPPoE.vpdn enablevpdn ip udp ignore checksumvpdn search-order domain!no mpls traffic-eng auto-bw timers frequency 0call rsvp-sync!!!! This control policy map instructs L2TP to authenticate based on domain name.policy-map type control RULE_L2TP_LM_ATM5class type control always event session-start1 collect identifier unauthenticated-domain2 authorize identifier unauthenticated-domain!!! The BBA group method is used to configure PPPoE (alternatively, the vpdn-group! method could be used).bba-group pppoe BBA_LM_ATM5virtual-template 5sessions auto cleanup!! This virtual circuit (VC) class is applied to the ATM PVC.vc-class atm VC_LM_ATM5! Associates the VC class with the above bba-group.protocol pppoe group BBA_LM_ATM5! Enables dynamic bandwidth selection.dbs enable maximumencapsulation aal5snap! Applies the L2TP rule above to the VC class.service-policy type control RULE_L2TP_LM_ATM5!! Interface Gigabit Ethernet 0/3 points to the LNS.interface GigabitEthernet0/3ip address 180.49.1.49 255.255.255.0! The port bundle host key (PBHK) feature is enabled on the interface.ip portbundle outsideip flow ingressload-interval 30duplex fullspeed 1000media-type gbicnegotiation auto!!interface ATM2/0.101 point-to-pointip flow ingressno atm enable-ilmi-trappvc 106/46! The VC class is associated with the PVC.class-vc VC_LM_ATM5! This can be changed to restrict PPPoE sessions on the PVC.pppoe max-sessions 1!!! The PPP CHAP configuration is entered on the virtual template.interface Virtual-Template5no ip addressno peer default ip addressno keepaliveppp authentication chapppp timeout aaaISG LNS
The following baseline configuration tasks are performed on the ISG LNS:
•
Configuring AAA and the Connection to the RADIUS Server
•
Configuring PPPoE and the Connection to the LAC
•
Configuring Inbound and Outbound Access Lists
Configuring AAA and the Connection to the RADIUS Server
In this AAA configuration, connections to the AAA server, the Cisco SESM, and two billing servers are configured. VSA accounting and authentication are enabled, and the loopback interface 0 is used for AAA communications.
aaa new-model!! Configures the AAA server group for the CAR AAA server.aaa group server radius CAR_SERVERserver 10.100.2.36 auth-port 1812 acct-port 1813!! Configures the AAA server group for the RSIM_SERVER billing server.aaa group server radius RSIM_SERVERserver 10.100.6.88 auth-port 1645 acct-port 1646!! Configures the AAA server group for the MIND_SERVER billing server.aaa group server radius MIND_SERVERserver 10.100.11.86 auth-port 1645 acct-port 1646! Configures AAA for the CAR AAA server.aaa authentication login default noneaaa authentication login IP_AUTHEN_LIST group CAR_SERVERaaa authentication ppp default group CAR_SERVER! The following commands configure authentication, authorization, and accounting for the! CAR AAA server and the two billing servers.aaa authentication ppp PREPAID_MIND group MIND_SERVERaaa authentication ppp PREPAID_AUTHEN_LIST group RSIM_SERVERaaa authorization network default group CAR_SERVERaaa authorization network PREPAID_MIND group MIND_SERVERaaa authorization network PREPAID_AUTHOR_LIST group RSIM_SERVERaaa authorization subscriber-service default local group radiusaaa accounting network default start-stop group CAR_SERVERaaa accounting network PREPAID_MIND start-stop group MIND_SERVERaaa accounting network PREPAID_ACCNT_LIST start-stop group RSIM_SERVER! Configures the connection to the Cisco SESMaaa server radius sesmclient 10.100.4.38key ciscoport 1812message-authenticator ignore!! Loopback 0 is used for communicating with AAA, the billing servers, and SESM.interface Loopback0ip address 10.200.1.55 255.255.255.255ip router isis Remote_ISP! Instructs the router to use loopback 0 to communicate with the AAA RADIUS servers.ip radius source-interface Loopback0!! These RADIUS attributes are required for prepaid services.radius-server attribute 44 include-in-access-reqradius-server attribute 8 include-in-access-reqradius-server attribute 55 include-in-acct-reqradius-server attribute 55 access-request includeradius-server attribute 25 access-request include! The CAR AAA server.radius-server host 10.100.2.36 auth-port 1812 acct-port 1813 key Cisco! The RSIM_SERVER billing server.radius-server host 10.100.6.88 auth-port 1645 acct-port 1646 key Cisco! The MIND_SERVER billing server.radius-server host 10.100.11.86 auth-port 1645 acct-port 1646 key Ciscoradius-server retransmit 5radius-server key ciscoradius-server vsa send accountingradius-server vsa send authenticationConfiguring PPPoE and the Connection to the LAC
VPDN is configured to receive L2TP tunnels from the LAC over which the PPPoE sessions are sent. A DHCP pool and MPLS virtual routing forwarding (VRF) tables are created for incoming subscribers.
no ip dhcp use vrf connected!! Globally enables MPLS VRFs for incoming subscribers.ip vrf VPN11006rd 200:6route-target export 200:6route-target import 200:6!!ip cef!vpdn enablevpdn ip udp ignore checksum!! VPDN group 1 terminates PPPoE clients that come in from the LAC over L2TP tunnels.vpdn-group 1accept-dialinprotocol l2tpvirtual-template 5terminate-from hostname sp_laclocal name sp_lnsl2tp tunnel password 0 lab!!interface Loopback1ip vrf forwarding VPN11006ip address 100.6.6.6 255.255.255.255!! Gigabit Ethernet interface 0/3 points to the ISG LNS.interface GigabitEthernet0/3ip address 22.22.1.55 255.255.255.0! The PBHK feature is enabled on this interface.ip portbundle outsideip flow ingressip router isis Remote_ISPload-interval 30duplex fullspeed 1000media-type gbicnegotiation autompls mtu 1522mpls label protocol ldpmpls ipno keepalive!! PPPoE subscribers terminated from L2TP tunnels use this virtual template.interface Virtual-Template5no ip addressload-interval 30no peer default ip addressno keepaliveppp mtu adaptiveppp authentication chap! Applies this policy map to PPPoE subscribers.service-policy type control RULE_PPP_ATM5!! The DHCP pool that is assigned to subscribers.ip local pool cpe6_pool-53 200.53.6.2 200.53.6.254!Configuring Baseline ISA Subscriber Services
Basic ISA subscriber services are configured, including Layer 4 redirect to the Cisco SESM and the PBHK feature. When the port bundle host key (PBHK) feature is enabled, TCP packets from subscribers are mapped to a local IP address for the ISA gateway and a range of ports. This mapping allows the portal to identify the ISA gateway from which the session originated. Also, the default service, BOD256K_CLASS is configured, which limits subscribers bandwidth to 256 kbps.
! Configures the connection to the Cisco SESM for Layer 4 Redirect functionality.redirect server-group SESM-Serverserver ip 10.100.4.38 port 8080!!! Creates the class map BOD256K_CLASS, which is the default service applied to all! subscribers.class-map type control match-any BOD256K_CLASSmatch service-name BOD256K!class type control BOD256K_CLASS event service-start1 service-policy type service identifier service-name!! Applies PBHK to all subscribers so they can access the Cisco SESM.class type control always event session-start1 service local2 service-policy type service name PBHK_SERVICE!! If both the quota from the billing server and idle time equal zero, the connection is! dropped.class type control always event quota-depleted1 set-param drop-traffic FALSE!! If the quota from the billing server equals zero, but the idle time is greater than! zero, Layer 4 redirect is activated.class type control always event credit-exhausted1 service-policy type service name L4REDIRECT_SERVICE!! Enables port bundle host key (PBHK) access to the Cisco SESM.ip portbundlematch access-list 110! The Loopback 0 interface is used to communicate with the Cisco SESM.source Loopback0Configuring Inbound and Outbound Access Lists
Basic access lists are configured to govern subscribers' Internet access, and an access list is created for the PBHK feature.
! This access list is referenced in the AAA subscriber profile. It governs incoming! Internet traffic.ip access-list extended Internet-in-acldeny ip any 223.0.0.0 0.255.255.255deny ip any 20.0.0.0 0.255.255.255deny ip any 40.0.0.0 0.255.255.255deny ip any 21.0.0.0 0.255.255.255deny ip any 22.0.0.0 0.255.255.255deny ip any 41.0.0.0 0.255.255.255deny ip any 80.0.0.0 0.255.255.255deny ip any 81.0.0.0 0.255.255.255deny ip any 82.0.0.0 0.255.255.255deny ip any 10.200.0.0 0.0.255.255permit ip any any! This access list is called out in the AAA subscriber profile. It governs outgoing! Internet traffic.ip access-list extended Internet-out-acldeny ip 223.0.0.0 0.255.255.255 anydeny ip 10.200.0.0 0.0.255.255 anydeny ip 20.0.0.0 0.255.255.255 anydeny ip 40.0.0.0 0.255.255.255 anydeny ip 21.0.0.0 0.255.255.255 anydeny ip 22.0.0.0 0.255.255.255 anydeny ip 41.0.0.0 0.255.255.255 anydeny ip 80.0.0.0 0.255.255.255 anydeny ip 81.0.0.0 0.255.255.255 anydeny ip 82.0.0.0 0.255.255.255 anypermit ip any any!access-list 101 permit ip any any! This access list is used in the ip portbundle configuration above.access-list 110 permit ip any anyaccess-list 111 deny tcp any host 10.100.4.38 eq wwwaccess-list 111 deny tcp any host 10.100.4.38 eq 8080access-list 111 permit tcp any any eq wwwPE
The PE is configured to assign subscribers to a VRF and to allow subscribers to access the Cisco SESM.
! The VRF that subscribers are assigned to.ip vrf VPN11006rd 200:6route-target export 200:6route-target import 200:6!!router bgp 200no synchronizationbgp router-id 10.200.1.43bgp log-neighbor-changesnetwork 10.100.2.0 mask 255.255.255.0network 10.200.1.43 mask 255.255.255.255network 24.7.1.0 mask 255.255.255.0network 83.83.1.0 mask 255.255.255.0network 84.1.1.0 mask 255.255.255.0network 84.2.1.0 mask 255.255.255.0network 84.3.1.0 mask 255.255.255.0network 84.4.1.0 mask 255.255.255.0neighbor 10.200.1.47 remote-as 200neighbor 10.200.1.47 ebgp-multihop 10neighbor 10.200.1.47 update-source Loopback0no auto-summary!! Enables BGP VPNv4 neighborsaddress-family vpnv4neighbor 10.200.1.47 activateneighbor 10.200.1.47 send-community extendedexit-address-family!!! Allows VRF routes into the BGP routing table.address-family ipv4 vrf VPN11006redistribute connectedredistribute staticno auto-summaryno synchronizationexit-address-family!!! Creates an IP route for subscribers in VRF VPN11006 to access the Cisco SESM.ip route vrf VPN11006 10.100.4.38 255.255.255.255 Vlan6 10.100.4.38AAA Server for ISP-1
The following baseline configuration tasks are performed on the AAA server for ISP-1:
•
Configuring the Connection to the LAC
•
Configuring L2TP Forwarding from the LAC to the ISG LNS
Configuring the Connection to the LAC
This profile allows the LAC router access to the AAA CAR server. The IP address 10.200.1.49 is the address of the loopback interface on the LAC.
--> cd ie2-c7206-ge[ //localhost/Radius/Clients/ie2-C7206-GE ]Name = ie2-C7206-GEDescription =IPAddress = 10.200.1.49SharedSecret = ciscoType = NASVendor =IncomingScript~ =OutgoingScript~ =EnablePOD = FALSEConfiguring L2TP Forwarding from the LAC to the ISG LNS
This profile and the corresponding attributes instruct the LAC to establish an L2TP tunnel to the ISG LNS, based on the "@isp.com" portion of the username. The IP address 10.200.1.55 is the address of the loopback interface on the ISG LNS.
--> cd isp.com[ //localhost/Radius/UserLists/SESMServices/isp.com ]Name = isp.comDescription =Password = <encrypted>Enabled = TRUEGroup~ =BaseProfile~ =AuthenticationScript~ =AuthorizationScript~ =UserDefined1 =AllowNullPassword = FALSEAttributes/CheckItems/--> ls attributes/[ Attributes ]Cisco-AVpair = vpdn:tunnel-id=sp_lacCisco-AVpair = vpdn:l2tp-tunnel-password=labCisco-AVpair = vpdn:tunnel-type=l2tpCisco-AVpair = vpdn:ip-addresses=10.200.1.55Cisco-AVpair = atm:peak-cell-rate=3000Cisco-AVpair = atm:sustainable-cell-rate=3000idle-timeout = 86400AAA Server for ISP-2
The following baseline configuration tasks are performed on the AAA server for ISP-2:
•
Configuring the Connection to the ISG LNS
•
Configuring the Connection to the Cisco SESM
•
Configuring the Subscriber's Default PPP Profile
Configuring the Connection to the ISG LNS
This profile allows the ISG LNS to have access to the AAA CAR server.
--> cd ie2-c7206-lns[ //localhost/Radius/Clients/ie2-C7206-LNS ]Name = ie2-C7206-LNSDescription =IPAddress = 10.200.1.55SharedSecret = ciscoType = NASVendor =IncomingScript~ =OutgoingScript~ =EnablePOD = FALSEConfiguring the Connection to the Cisco SESM
This profile connects the AAA CAR server to the Cisco SESM.
--> cd ie2-sesm-1b[ //localhost/Radius/Clients/ie2-SESM-1b ]Name = ie2-SESM-1bDescription =IPAddress = 10.100.4.38SharedSecret = ciscoType = NASVendor =IncomingScript~ =OutgoingScript~ =EnablePOD = FALSEConfiguring the Baseline ISA Subscriber Services
This profile and the following attributes specify the ISA subscriber services that are allowed.
--> cd cpe6_1@isp.com[ //localhost/Radius/UserLists/SESMSubscribers/cpe6_1@isp.com ]! Specifies the username that the CPE uses.Name = cpe6_1@isp.comDescription =! This password must match the one configured on the CPE.Password = <encrypted>Enabled = TRUEGroup~ =! Specifies the name of the PPP profile.BaseProfile~ = Default-PPP-UsersAuthenticationScript~ =AuthorizationScript~ =UserDefined1 =AllowNullPassword = FALSEAttributes/CheckItems/--> ls attributes/[ Attributes ]! Assigns subscribers to vrf VPN11006.Cisco-AVpair = "lcp:interface-config=ip vrf forwarding VPN11006"Cisco-AVpair = "lcp:interface-config=ip unnumbered loopback 1"! Assigns an address to this DHCP pool on the LNS.Cisco-AVpair = ip:addr-pool=cpe6_pool-53! The "A" in front of BOD256K designates autologin, which means that the default service! is BOD256k.Cisco-SSG-Account-Info = ABOD256KCisco-SSG-Account-Info = NBOD256K! Specifies the other services that the subscriber is allowed to access.Cisco-SSG-Account-Info = NBOD1MTIMECisco-SSG-Account-Info = NBOD2MTIMECisco-SSG-Account-Info = NBOD1MVOLUMECisco-SSG-Account-Info = NBOD2MVOLUME! Specifies the total session timeout value (optional).Session-Timeout = 86400This profile and the following attributes configure the default service, BOD256K.
--> cd bod256k[ //localhost/Radius/UserLists/SESMServices/BOD256K ]! This service is not a prepaid service because there is no "prepaid-config" line.Name = BOD256KDescription =Password = <encrypted>Enabled = TRUEGroup~ =BaseProfile~ =AuthenticationScript~ =AuthorizationScript~ =UserDefined1 =AllowNullPassword = FALSEAttributes/CheckItems/--> ls attributes/[ Attributes ]Cisco-AVPair = "ip:traffic-class=in access-group name Internet-in-acl"Cisco-AVPair = "ip:traffic-class=in default drop"Cisco-AVPair = "ip:traffic-class=out access-group name Internet-out-acl"Cisco-AVPair = "ip:traffic-class=out default drop"Cisco-SSG-Service-Info = IBOD256KCisco-SSG-Service-Info = QU;128000;8000;8000;D;256000;16000;16000Cisco-SSG-Service-Info = R42.1.1.0;255.255.255.0Configuring Layer 4 Redirect
This attribute enables the Layer 4 Redirect feature.
[ Attributes ]! Instructs Layer 4 redirect to send traffic to ACL 111 on the ISG LNS.Cisco-AVPair = "ip:l4redirect=redirect list 111 to group SESM-Server duration 30 frequency 180"Configuring PBHK
This profile and the following attribute enable the PBHK feature on the AAA server, which enables access to the SESM by way of the PBHK feature.
--> cd pbhk_service[ //localhost/Radius/UserLists/SESMServices/PBHK_SERVICE ]Name = PBHK_SERVICEDescription =Password = <encrypted>Enabled = TRUEGroup~ =BaseProfile~ =AuthenticationScript~ =AuthorizationScript~ =UserDefined1 =AllowNullPassword = FALSEAttributes/CheckItems/--> ls attributes/[ Attributes ]Cisco-AVPair = ip:portbundle=enableConfiguring the Subscriber's Default PPP Profile
This profile and the following attributes configure the PPP profile that is used in the subscriber's base profile.
--> cd default-ppP-users/[ //localhost/Radius/Profiles/default-PPP-users ]Name = default-PPP-usersDescription =Attributes/--> ls attributes/[ Attributes ]Ascend-Idle-Limit = 1800Framed-MTU = 1500Framed-Protocol = PPPFramed-Routing = None! Configures the length of the idle timeout on PPP sessions, after which the session is! dropped.Idle-timeout = 180Service-Type = FramedService Bundle Configurations
The following devices are configured to enable the advanced ISA subscriber services:
ISG LNS
The following configuration tasks are performed on the ISG LNS to enable the advanced ISA subscriber services:
•
Configuring the Global Prepaid Services Configuration
•
Reconfiguring the BOD256K Service
•
Configuring the BOD1MTIME Service
•
Configuring the BOD2MTIME Service
•
Configuring the BOD1MVOLUME Service
•
Configuring the BOD2MVOLUME Service
Configuring the Global Prepaid Services Configuration
The global attributes of the prepaid services are configured for each of the two billing servers.
! This is the global configuration for the PREPAID_RSIM prepaid billing server.subscriber feature prepaid PREPAID_RSIMthreshold time 10 secondsthreshold volume 1000 bytesinterim-interval 3 minutes! References the authorization list in the above AAA configuration.method-list author PREPAID_AUTHOR_LIST! References the accounting list in the above AAA configuration.method-list accounting PREPAID_ACCNT_LIST! This is the prepaid password that is configured on the billing servers.password prepaidcisco! This is the global configuration for the PREPAID_MIND prepaid billing server.subscriber feature prepaid PREPAID_MINDthreshold time 10 secondsthreshold volume 1000 bytesinterim-interval 3 minutesmethod-list author PREPAID_MINDmethod-list accounting PREPAID_MINDpassword prepaidcisco!subscriber policy recording rules limit 64Reconfiguring the BOD256K Service
The control class for the BOD256K service is reconfigured, so that when it is initiated, the other services are unapplied.
class type control BOD256K_CLASS event service-start1 service-policy type service unapply name BOD1MVOLUME2 service-policy type service unapply name BOD2MVOLUME3 service-policy type service unapply name BOD1MTIME4 service-policy type service unapply name BOD2MTIME5 service-policy type service identifier service-nameConfiguring the BOD1MTIME Service
To configure the additional services, each service is first defined by creating a control class map. Then instructions on how to start and stop the service are configured as class controls.
! This control class map defines the BOD1MTIME_CLASS service.class-map type control match-any BOD1MTIME_CLASSmatch service-name BOD1MTIME!! When subscribers start the service, the other services are unapplied.class type control BOD1MTIME_CLASS event service-start1 service-policy type service unapply name BOD256K2 service-policy type service unapply name BOD2MTIME3 service-policy type service identifier service-name!! When subscribers stop the service, it is unapplied, and the default BOD256K service is! reapplied.class type control BOD1MTIME_CLASS event service-stop1 service-policy type service unapply identifier service-name2 service-policy type service name BOD256KConfiguring the BOD2MTIME Service
The same method is used to configure the BOD2MTIME service.
class-map type control match-any BOD2MTIME_CLASSmatch service-name BOD2MTIME!
class type control BOD2MTIME_CLASS event service-start1 service-policy type service unapply name BOD256K2 service-policy type service unapply name BOD1MTIME3 service-policy type service identifier service-name!class type control BOD2MTIME_CLASS event service-stop1 service-policy type service unapply identifier service-name2 service-policy type service name BOD256KConfiguring the BOD1MVOLUME Service
The same method is used to configure the BOD1MVOLUME service.
class-map type control match-any BOD1MVOLUME_CLASSmatch service-name BOD1MVOLUMEclass type control BOD1MVOLUME_CLASS event service-start1 service-policy type service unapply name BOD256K2 service-policy type service unapply name BOD2MVOLUME3 service-policy type service identifier service-name!class type control BOD1MVOLUME_CLASS event service-stop1 service-policy type service unapply identifier service-name2 service-policy type service name BOD256KConfiguring the BOD2MVOLUME Service
The same method is used to configure the BOD2MVOLUME service.
class-map type control match-any BOD2MVOLUME_CLASSmatch service-name BOD2MVOLUME!class type control BOD2MVOLUME_CLASS event service-start1 service-policy type service unapply name BOD256K2 service-policy type service unapply name BOD1MVOLUME3 service-policy type service identifier service-name!class type control BOD2MVOLUME_CLASS event service-stop1 service-policy type service unapply identifier service-name2 service-policy type service name BOD256KAAA Server for ISP-2
The following configuration tasks are performed on the AAA server for ISP-2 to enable the advanced ISA subscriber services:
•
Configuring the BOD1MTIME Service
•
Configuring the BOD2MTIME Services
•
Configuring the BOD1MVOLUME Service
•
Configuring the BOD2MVOLUME Service
•
Configuring Layer 4 Redirect for when Quotas Run Out
Configuring the BOD1MTIME Service
The following profile and attributes configure the BOD1MTIME service.
--> cd bod1mtime[ //localhost/Radius/UserLists/SESMServices/BOD1MTIME ]Name = BOD1MTIMEDescription =Password = <encrypted>Enabled = TRUEGroup~ =BaseProfile~ =AuthenticationScript~ =AuthorizationScript~ =UserDefined1 =AllowNullPassword = FALSEAttributes/CheckItems/--> ls attributes/[ Attributes ]Cisco-AVPair = "ip:traffic-class=in access-group name Internet-in-acl"Cisco-AVPair = "ip:traffic-class=in default drop"Cisco-AVPair = "ip:traffic-class=out access-group name Internet-out-acl"Cisco-AVPair = "ip:traffic-class=out default drop"! Identifies the service as a prepaid service and references the PREPAID_RSIM global! configuration on the ISG LNS.Cisco-AVPair = prepaid-config=PREPAID_RSIM! The name of the service on the SESM is BOD1MTIME. The "I" instructs RADIUS that this! attribute is specifying a service named "BOD1MTIME."Cisco-SSG-Service-Info = IBOD1MTIME! Configures QoS policing, where Q indicates that QoS is applied, U is the upstream rates,! and D is the downstream rates. Three rates are configured for both upstream and! downstream rates: the committed rate, the normal burst rate, and the excess burst rate! respectively.Cisco-SSG-Service-Info = QU;256000;16000;16000;D;1000000;64000;64000Cisco-SSG-Service-Info = R42.1.1.0;255.255.255.0Configuring the BOD2MTIME Services
The following profile and attributes configure the BOD2MTIME service.
--> cd bod2mtime[ //localhost/Radius/UserLists/SESMServices/BOD2MTIME ]Name = BOD2MTIMEDescription =Password = <encrypted>Enabled = TRUEGroup~ =BaseProfile~ =AuthenticationScript~ =AuthorizationScript~ =UserDefined1 =AllowNullPassword = FALSEAttributes/CheckItems/--> ls attributes/[ Attributes ]Cisco-AVPair = "ip:traffic-class=in access-group name Internet-in-acl"Cisco-AVPair = "ip:traffic-class=in default drop"Cisco-AVPair = "ip:traffic-class=out access-group name Internet-out-acl"Cisco-AVPair = "ip:traffic-class=out default drop"Cisco-AVPair = prepaid-config=PREPAID_RSIMCisco-SSG-Service-Info = IBOD2MTIMECisco-SSG-Service-Info = QU;512000;32000;32000;D;2000000;128000;128000Cisco-SSG-Service-Info = R42.1.1.0;255.255.255.0Configuring the BOD1MVOLUME Service
The following profile and attributes configure the BOD1MVOLUME service.
--> cd bod1mvolUME/[ //localhost/Radius/UserLists/SESMServices/BOD1MVOLUME ]Name = BOD1MVOLUMEDescription =Password = <encrypted>Enabled = TRUEGroup~ =BaseProfile~ =AuthenticationScript~ =AuthorizationScript~ =UserDefined1 =AllowNullPassword = FALSEAttributes/CheckItems/--> ls attributes/[ Attributes ]Cisco-AVPair = "ip:traffic-class=in access-group name Internet-in-acl"Cisco-AVPair = "ip:traffic-class=in default drop"Cisco-AVPair = "ip:traffic-class=out access-group name Internet-out-acl"Cisco-AVPair = "ip:traffic-class=out default drop"Cisco-AVPair = prepaid-config=PREPAID_RSIMCisco-SSG-Service-Info = IBOD1MVOLUMECisco-SSG-Service-Info = QU;256000;16000;16000;D;1000000;64000;64000Cisco-SSG-Service-Info = R42.1.1.0;255.255.255.0Configuring the BOD2MVOLUME Service
The following profile and attributes configure the BOD2MVOLUME service.
--> cd bod2mvolUME/[ //localhost/Radius/UserLists/SESMServices/BOD2MVOLUME ]Name = BOD2MVOLUMEDescription =Password = <encrypted>Enabled = TRUEGroup~ =BaseProfile~ =AuthenticationScript~ =AuthorizationScript~ =UserDefined1 =AllowNullPassword = FALSEAttributes/CheckItems/--> ls attributes/[ Attributes ]Cisco-AVPair = "ip:traffic-class=in access-group name Internet-in-acl"Cisco-AVPair = "ip:traffic-class=in default drop"Cisco-AVPair = "ip:traffic-class=out access-group name Internet-out-acl"Cisco-AVPair = "ip:traffic-class=out default drop"Cisco-AVPair = prepaid-config=PREPAID_RSIMCisco-SSG-Service-Info = IBOD2MVOLUMECisco-SSG-Service-Info = QU;512000;32000;32000;D;2000000;128000;128000Cisco-SSG-Service-Info = R42.1.1.0;255.255.255.0Configuring Layer 4 Redirect for when Quotas Run Out
The following profile enables Layer 4 Redirect when the subscriber's quota or funds from the billing server run out.
--> cd l4redirECT_SERVICE/[ //localhost/Radius/UserLists/SESMServices/L4REDIRECT_SERVICE ]Name = L4REDIRECT_SERVICEDescription =Password = <encrypted>Enabled = TRUEGroup~ =BaseProfile~ =AuthenticationScript~ =AuthorizationScript~ =UserDefined1 =AllowNullPassword = FALSEAttributes/CheckItems/Verifying ATM to ISG LNS Aggregation
The following sections provide sample show command output:
•
Verification of Default BOD256K Service
•
show Command Output for BOD1MTIME Service
•
show Command Output for History of Service Changes
Basic Verification
The show subscriber session command shows basic information for all active subscribers. In the following output, there is one active subscriber session.
ie2-C7206-LNS# show subscriber sessionCurrent Subscriber Information: Total sessions 1Uniq ID Interface State Service Identifier Up-time! This is the VID for the subscriber520 Vi3 authen Local Term cpe6_1@isp.com 00:12:03! This is the VID for the subscriber's traffic class521 Traffic-Cl unauthen Ltm Internal 00:12:03The show ip route vrf VPN11006 command shows routing table information for the VRF. In the following output, there is one active subscriber session.
ie2-C7206-LNS# show ip route vrf VPN11006Routing Table: VPN11006Codes: C - connected, S - static, R - RIP, M - mobile, B - BGPD - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter areaN1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2E1 - OSPF external type 1, E2 - OSPF external type 2, E - EGPi - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2ia - IS-IS inter area, * - candidate default, U - per-user static routeo - ODR, P - periodic downloaded static routeGateway of last resort is not set84.0.0.0/24 is subnetted, 1 subnetsB 84.1.206.0 [200/0] via 10.200.1.43, 4d19h100.0.0.0/32 is subnetted, 1 subnetsC 100.6.6.6 is directly connected, Loopback1200.53.6.0/32 is subnetted, 1 subnets! This shows that the subscriber is connected and part of vrf VPN11006C 200.53.6.2 is directly connected, Virtual-Access3200.6.6.0/32 is subnetted, 1 subnetsB 200.6.6.6 [200/0] via 10.200.1.56, 4d19h10.0.0.0/32 is subnetted, 1 subnetsB 10.100.4.38 [200/0] via 10.200.1.43, 4d19hie2-C7206-LNS#Verification of Default BOD256K Service
The show subscriber session uid 520 command shows detailed information for the subscriber with UID 520. The following output is for a subscriber with the default BOD256K service.
ie2-C7206-LNS# show subscriber session uid 520Unique Session ID: 520Identifier: cpe6_1@isp.comSIP subscriber access type(s): VPDN/PPPCurrent SIP options: Req Fwding/Req FwdedSession Up-time: 00:12:10, Last Changed: 00:12:10AAA unique ID: 472Interface: Virtual-Access3Policy information:Context 212C1F2C: Handle 41000819Authentication status: authenUser profile, excluding services:service-type 2 [Framed]Framed-Protocol 1 [PPP]routing FalseFramed-MTU 1500 (0x5DC)timeout 86400 (0x15180)idletime 180 (0xB4)! The "A" stands for auto-login, which indicates that BOD256K is the default service.ssg-account-info "ABOD256K"! The "N" indicates that the subscriber is allowed access to these services based on the! user's AAA profile.ssg-account-info "NBOD256K"ssg-account-info "NBOD1MTIME"ssg-account-info "NBOD2MTIME"ssg-account-info "NBOD1MVOLUME"ssg-account-info "NBOD2MVOLUME"idletime 1800 (0x708)interface-config "ip"interface-config "ip"addr-pool "cpe6_pool-53"! Indicates the current active services.Active services associated with session:name "BOD256K"! PBHK was applied when the session was started, as configured in the policy-map.name "PBHK_SERVICE", applied outwith active session! Because BOD256K is not a prepaid service, prepaid is not active.Prepaid context: not presentRules, actions and conditions executed:subscriber rule-map RULE_PPP_ATM5condition always event session-start1 service-policy type service service PBHK_SERVICEsubscriber rule-map RULE_PPP_ATM5condition BOD1MTIME_CLASS event service-startsubscriber condition-map match-any BOD1MTIME_CLASSmatch identifier service-name BOD1MTIME [FALSE]subscriber rule-map RULE_PPP_ATM5condition BOD2MTIME_CLASS event service-startsubscriber condition-map match-any BOD2MTIME_CLASSmatch identifier service-name BOD2MTIME [FALSE]subscriber rule-map RULE_PPP_ATM5condition BOD256K_CLASS event service-startsubscriber condition-map match-any BOD256K_CLASSmatch identifier service-name BOD256K [FALSE]subscriber rule-map RULE_PPP_ATM5condition BOD1MVOLUME_CLASS event service-startsubscriber condition-map match-any BOD1MVOLUME_CLASSmatch identifier service-name BOD1MVOLUME [FALSE]subscriber rule-map RULE_PPP_ATM5condition BOD2MVOLUME_CLASS event service-startsubscriber condition-map match-any BOD2MVOLUME_CLASSmatch identifier service-name BOD2MVOLUME [FALSE]subscriber rule-map RULE_PPP_ATM5condition BOD1MTIME_CLASS event service-startsubscriber condition-map match-any BOD1MTIME_CLASSmatch identifier service-name BOD1MTIME [FALSE]subscriber rule-map RULE_PPP_ATM5condition BOD2MTIME_CLASS event service-startsubscriber condition-map match-any BOD2MTIME_CLASSmatch identifier service-name BOD2MTIME [FALSE]subscriber rule-map RULE_PPP_ATM5condition BOD256K_CLASS event service-startsubscriber condition-map match-any BOD256K_CLASS! Services that are active are identified as "TRUE."match identifier service-name BOD256K [TRUE]subscriber rule-map RULE_PPP_ATM5condition BOD256K_CLASS event service-start1 service-policy service unapply service BOD1MTIME2 service-policy service unapply service BOD2MTIME3 service-policy service unapply service BOD1MVOLUME4 service-policy service unapply service BOD2MVOLUME5 service-policy service identifier service-nameSession inbound features:Traffic classes:Traffic class session ID: 521! Identifies the ACL that restricts inbound traffic. The ACL is configured on the ISG LNS,! and it is applied to the subscriber based on the subscriber profile on the AAA server.ACL Name: Internet-in-acl, Packets = 4, Bytes = 368Default traffic is droppedUnmatched Packets (dropped) = 0, Re-classified packets (redirected) = 0Feature: Portbundle Hostkey! Identifies the PBHK IP address and the bundle number. This information can be used to! troubleshoot PBHK with the show ip portbundle command.Portbundle IP = 10.200.1.55 Bundle Number = 761Session outbound features:Feature: PPP Idle TimeoutTimeout value is 1800! The current elapsed idle time.Idle time is 00:12:11Traffic classes:Traffic class session ID: 521ACL Name: Internet-out-acl, Packets = 0, Bytes = 0Default traffic is droppedUnmatched Packets (dropped) = 0, Re-classified packets (redirected) = 0Non-datapath features:Feature: Interface-ConfigFeature: Session TimeoutTimeout value is 86400 secondsTime remaining is 23:47:48Feature: IP ConfigAddress Pool: cpe6_pool-53Unnumbered Intf: [None]Configuration sources associated with this session:Service: BOD256K, Active Time = 00:12:11Service: PBHK_SERVICE, Active Time = 00:12:11Interface: Virtual-Template5, Active Time = 00:12:11The show subscriber session uid 521 command shows detailed information for the subscriber with UID 521. The following output is for a subscriber with the default BOD256K service.
ie2-C7206-LNS# show subscriber session uid 521Unique Session ID: 521Identifier:SIP subscriber access type(s): Traffic-ClassCurrent SIP options: NoneSession Up-time: 00:12:14, Last Changed: 00:12:14AAA unique ID: 0Policy information:Context 212C1B18: Handle 5A00081CAuthentication status: unauthenPrepaid context: not presentSession inbound features:Feature: Policing! Identifies the upstream policing rates for the BOD256K service. These rates are defined! on the AAA server in the BOD256K service profile.Upstream Params:Average rate = 128000, Normal burst = 8000, Excess burst = 8000Config level = ServiceSession outbound features:Feature: Policing! Identifies the downstream policing rates for the BOD256K service. These rates are! defined on the AAA server in the BOD256K service profile.Dnstream Params:Average rate = 256000, Normal burst = 16000, Excess burst = 16000Config level = ServiceConfiguration sources associated with this session:Service: BOD256K, Active Time = 00:12:14ie2-C7206-LNS#show Command Output for BOD1MTIME Service
The following output is for subscribers who have activated the BOD1MTIME service.
ie2-C7206-LNS# show subscriber sessionCurrent Subscriber Information: Total sessions 1Uniq ID Interface State Service Identifier Up-time520 Vi3 authen Local Term cpe6_1@isp.com 00:14:17522 Traffic-Cl unauthen Ltm Internal cpe6_1@isp.com 00:00:11ie2-C7206-LNS# show subscriber session uid 520Unique Session ID: 520Identifier: cpe6_1@isp.comSIP subscriber access type(s): VPDN/PPPCurrent SIP options: Req Fwding/Req FwdedSession Up-time: 00:14:29, Last Changed: 00:00:23AAA unique ID: 472Interface: Virtual-Access3Policy information:Context 212C1F2C: Handle 41000819Authentication status: authenUser profile, excluding services:service-type 2 [Framed]Framed-Protocol 1 [PPP]routing FalseFramed-MTU 1500 (0x5DC)timeout 86400 (0x15180)idletime 180 (0xB4)ssg-account-info "ABOD256K"ssg-account-info "NBOD256K"ssg-account-info "NBOD1MTIME"ssg-account-info "NBOD2MTIME"ssg-account-info "NBOD1MVOLUME"ssg-account-info "NBOD2MVOLUME"idletime 1800 (0x708)interface-config "ip"interface-config "ip"addr-pool "cpe6_pool-53"Active services associated with session:! Indicates that the BOD1MTIME service is active.name "BOD1MTIME"name "PBHK_SERVICE", applied outwith active sessionPrepaid context: not presentRules, actions and conditions executed:subscriber rule-map RULE_PPP_ATM5condition always event session-start1 service-policy service service PBHK_SERVICEsubscriber rule-map RULE_PPP_ATM5condition BOD1MTIME_CLASS event service-startsubscriber condition-map match-any BOD1MTIME_CLASSmatch identifier service-name BOD1MTIME [FALSE]subscriber rule-map RULE_PPP_ATM5condition BOD2MTIME_CLASS event service-startsubscriber condition-map match-any BOD2MTIME_CLASSmatch identifier service-name BOD2MTIME [FALSE]subscriber rule-map RULE_PPP_ATM5condition BOD256K_CLASS event service-startsubscriber condition-map match-any BOD256K_CLASSmatch identifier service-name BOD256K [FALSE]subscriber rule-map RULE_PPP_ATM5condition BOD1MVOLUME_CLASS event service-startsubscriber condition-map match-any BOD1MVOLUME_CLASSmatch identifier service-name BOD1MVOLUME [FALSE]subscriber rule-map RULE_PPP_ATM5condition BOD2MVOLUME_CLASS event service-startsubscriber condition-map match-any BOD2MVOLUME_CLASSmatch identifier service-name BOD2MVOLUME [FALSE]subscriber rule-map RULE_PPP_ATM5condition BOD1MTIME_CLASS event service-startsubscriber condition-map match-any BOD1MTIME_CLASSmatch identifier service-name BOD1MTIME [FALSE]subscriber rule-map RULE_PPP_ATM5condition BOD2MTIME_CLASS event service-startsubscriber condition-map match-any BOD2MTIME_CLASSmatch identifier service-name BOD2MTIME [FALSE]subscriber rule-map RULE_PPP_ATM5condition BOD256K_CLASS event service-startsubscriber condition-map match-any BOD256K_CLASSmatch identifier service-name BOD256K [TRUE]subscriber rule-map RULE_PPP_ATM5condition BOD256K_CLASS event service-start1 service-policy service unapply service BOD1MTIME2 service-policy service unapply service BOD2MTIME3 service-policy service unapply service BOD1MVOLUME4 service-policy service unapply service BOD2MVOLUME5 service-policy service identifier service-namesubscriber rule-map RULE_PPP_ATM5condition BOD1MTIME_CLASS event service-startsubscriber condition-map match-any BOD1MTIME_CLASSmatch identifier service-name BOD1MTIME [FALSE]subscriber rule-map RULE_PPP_ATM5condition BOD2MTIME_CLASS event service-startsubscriber condition-map match-any BOD2MTIME_CLASSmatch identifier service-name BOD2MTIME [FALSE]subscriber rule-map RULE_PPP_ATM5condition BOD256K_CLASS event service-startsubscriber condition-map match-any BOD256K_CLASSmatch identifier service-name BOD256K [TRUE]subscriber rule-map RULE_PPP_ATM5condition BOD256K_CLASS event service-start1 service-policy service unapply service BOD1MTIME2 service-policy service unapply service BOD2MTIME3 service-policy service unapply service BOD1MVOLUME4 service-policy service unapply service BOD2MVOLUME5 service-policy service identifier service-namesubscriber rule-map RULE_PPP_ATM5condition BOD1MTIME_CLASS event service-startsubscriber condition-map match-any BOD1MTIME_CLASS! Indicates that the BOD1MTIME service is active.match identifier service-name BOD1MTIME [TRUE]subscriber rule-map RULE_PPP_ATM5condition BOD1MTIME_CLASS event service-start1 service-policy service unapply service BOD256K2 service-policy service unapply service BoD2MTIME3 service-policy service unapply service BOD1MVOLUME4 service-policy service unapply service BOD2MVOLUME5 service-policy service identifier service-nameSession inbound features:Traffic classes:Traffic class session ID: 522ACL Name: Internet-in-acl, Packets = 17, Bytes = 1157Default traffic is droppedUnmatched Packets (dropped) = 0, Re-classified packets (redirected) = 0Feature: Portbundle HostkeyPortbundle IP = 10.200.1.55 Bundle Number = 761Session outbound features:Feature: PPP Idle TimeoutTimeout value is 1800Idle time is 00:00:24Traffic classes:Traffic class session ID: 522ACL Name: Internet-out-acl, Packets = 26, Bytes = 28894Default traffic is droppedUnmatched Packets (dropped) = 0, Re-classified packets (redirected) = 0Non-datapath features:Feature: Interface-ConfigFeature: Session TimeoutTimeout value is 86400 secondsTime remaining is 23:45:28Feature: IP ConfigAddress Pool: cpe6_pool-53Unnumbered Intf: [None]Configuration sources associated with this session:Service: BOD1MTIME, Active Time = 00:00:25Service: PBHK_SERVICE, Active Time = 00:14:31Interface: Virtual-Template5, Active Time = 00:14:31ie2-C7206-LNS# show subscriber session uid 522Unique Session ID: 522Identifier: cpe6_1@isp.comSIP subscriber access type(s): Traffic-ClassCurrent SIP options: NoneSession Up-time: 00:00:27, Last Changed: 00:00:21AAA unique ID: 0Policy information:Context 212C1C74: Handle 40000821Authentication status: unauthen! Indicates that prepaid is now active to PREPAID_RSIM.Prepaid context: PREPAID_RSIMthreshold time 10 secondsthreshold volume 1000 bytesmethod-list author PREPAID_AUTHOR_LISTmethod-list accounting PREPAID_ACCNT_LISTpassword prepaidciscoInterim 3State PREPAID_FEATURE_RUNNINGFlow idle ? NOAcct start sent ? YESSession inbound features:Feature: PolicingUpstream Params:! Identifies the upstream policing rates for the BOD1MTIME service.Average rate = 256000, Normal burst = 16000, Excess burst = 16000Config level = ServiceFeature: Prepaid Volume MonitorThreshold:4294967295 - Quota:4294967295Usage(since last update):0 - Total:0Current states: StartSession outbound features:Feature: PolicingDnstream Params:! Identifies the downstream policing rates for the BOD1MTIME service.Average rate = 1000000, Normal burst = 64000, Excess burst = 64000Config level = ServiceFeature: Prepaid Volume MonitorThreshold:4294967295 - Quota:4294967295Usage(since last update):0 - Total:0Current states: StartNon-datapath features:! Shows the time statistics for the prepaid services.Feature: Time MonitorThreshold: 90 (seconds) - Quota: 100 (seconds)Session time: 21 (seconds)Configuration sources associated with this session:Service: BOD1MTIME, Active Time = 00:00:27ie2-C7206-LNS#show Command Output for History of Service Changes
The show subscriber policy conditions command shows the history of subscriber service changes.
ie2-C7206-LNS# show subscriber policy conditionsClass-map Action Exec Hit Miss Comp--------- ------ ---- --- ---- ----match-any BOD2MVOLUME_CLASS match identifier service-name B 256 7 249 7match-any BOD1MVOLUME_CLASS match identifier service-name B 257 9 248 9match-any BOD2MTIME_CLASS match identifier service-name B 534 4 530 4match-any BOD256K_CLASS match identifier service-name B 505 259 246 259match-any BOD1MTIME_CLASS match identifier service-name B 548 37 511 37Key:"Exec" - The number of times this line was executed"Hit" - The number of times this line evaluated to TRUE"Miss" - The number of times this line evaluated to FALSE"Comp" - The number of times this line completed the execution of itscondition without a need to continue on to the endie2-C7206-LNS# show subscriber policy profileCurrent policy profile DB contents are:Profile name: PBHK_SERVICE, 4 referencesportbundle "enable"Profile name: apply-config-only, 3 referencesservice-type 2 [Framed]Framed-Protocol 1 [PPP]routing FalseFramed-MTU 1500 (0x5DC)timeout 86400 (0x15180)idletime 180 (0xB4)ssg-account-info "ABOD256K"ssg-account-info "NBOD256K"ssg-account-info "NBOD1MTIME"ssg-account-info "NBOD2MTIME"ssg-account-info "NBOD1MVOLUME"ssg-account-info "NBOD2MVOLUME"idletime 1800 (0x708)interface-config "ip"interface-config "ip"addr-pool "cpe6_pool-53"Profile name: BOD256K, 4 referencestraffic-class "in access-group name Internet-in-acl"traffic-class "in default drop"traffic-class "out access-group name Internet-out-acl"traffic-class "out default drop"ssg-service-info "IBOD256K"ssg-service-info "QU;128000;8000;8000;D;256000;16000;16000"ssg-service-info "R42.1.1.0;255.255.255.0"policy-handle 1509951516 (0x5A00081C)Profile name: BOD1MTIME, 5 referencestraffic-class "in access-group name Internet-in-acl"traffic-class "in default drop"traffic-class "out access-group name Internet-out-acl"traffic-class "out default drop"ssg-service-info "IBOD1MTIME"ssg-service-info "QU;256000;16000;16000;D;1000000;64000;64000"ssg-service-info "R42.1.1.0;255.255.255.0"policy-handle 1073743905 (0x40000821)Profile name: BOD1MTIME, 3 referencestraffic-class "in access-group name Internet-in-acl"traffic-class "in default drop"traffic-class "out access-group name Internet-out-acl"traffic-class "out default drop"ssg-service-info "IBOD1MTIME"ssg-service-info "QU;256000;16000;16000;D;1000000;64000;64000"ssg-service-info "R42.1.1.0;255.255.255.0"policy-handle 889194527 (0x3500081F)----------------------------------------------------------Entries in Profile dB subscribers for exact match----------------------------------------------------------No entries found in Profile dBie2-C7206-LNS# show subscriber policy rulesRule Class-map Action Exec---- --------- ------ ----internal-rule always event account-logon 1 authenticate aaa list default 0RULE_PPP_ATM5 BOD1MTIME_CLASS event service 1 service-policy service unapply 21RULE_PPP_ATM5 BOD1MTIME_CLASS event service 2 service-policy service unapply 21RULE_PPP_ATM5 BOD1MTIME_CLASS event service 3 service-policy service unapply 21RULE_PPP_ATM5 BOD1MTIME_CLASS event service 4 service-policy service unapply 21RULE_PPP_ATM5 BOD1MTIME_CLASS event service 5 service-policy service identif 21RULE_PPP_ATM5 BOD2MTIME_CLASS event service 1 service-policy service unapply 3RULE_PPP_ATM5 BOD2MTIME_CLASS event service 2 service-policy service unapply 3RULE_PPP_ATM5 BOD2MTIME_CLASS event service 3 service-policy service unapply 3RULE_PPP_ATM5 BOD2MTIME_CLASS event service 4 service-policy service unapply 3RULE_PPP_ATM5 BOD2MTIME_CLASS event service 5 service-policy service identif 3RULE_PPP_ATM5 BOD256K_CLASS event service-s 1 service-policy service unapply 259RULE_PPP_ATM5 BOD256K_CLASS event service-s 2 service-policy service unapply 259RULE_PPP_ATM5 BOD256K_CLASS event service-s 3 service-policy service unapply 259RULE_PPP_ATM5 BOD256K_CLASS event service-s 4 service-policy service unapply 259RULE_PPP_ATM5 BOD256K_CLASS event service-s 5 service-policy service identif 259RULE_PPP_ATM5 BOD1MVOLUME_CLASS event servi 1 service-policy service unapply 5RULE_PPP_ATM5 BOD1MVOLUME_CLASS event servi 2 service-policy service unapply 5RULE_PPP_ATM5 BOD1MVOLUME_CLASS event servi 3 service-policy service unapply 5RULE_PPP_ATM5 BOD1MVOLUME_CLASS event servi 4 service-policy service unapply 5RULE_PPP_ATM5 BOD1MVOLUME_CLASS event servi 5 service-policy service identif 5RULE_PPP_ATM5 BOD2MVOLUME_CLASS event servi 1 service-policy service unapply 4RULE_PPP_ATM5 BOD2MVOLUME_CLASS event servi 2 service-policy service unapply 4RULE_PPP_ATM5 BOD2MVOLUME_CLASS event servi 3 service-policy service unapply 4RULE_PPP_ATM5 BOD2MVOLUME_CLASS event servi 4 service-policy service unapply 4RULE_PPP_ATM5 BOD2MVOLUME_CLASS event servi 5 service-policy service identif 4RULE_PPP_ATM5 BOD2MTIME_CLASS event service 1 service-policy service unapply 1RULE_PPP_ATM5 BOD2MTIME_CLASS event service 2 service-policy service service 1RULE_PPP_ATM5 BOD1MTIME_CLASS event service 1 service-policy service unapply 16RULE_PPP_ATM5 BOD1MTIME_CLASS event service 2 service-policy service service 16RULE_PPP_ATM5 BOD2MVOLUME_CLASS event servi 1 service-policy service unapply 3RULE_PPP_ATM5 BOD2MVOLUME_CLASS event servi 2 service-policy service service 3RULE_PPP_ATM5 BOD1MVOLUME_CLASS event servi 1 service-policy service unapply 4RULE_PPP_ATM5 BOD1MVOLUME_CLASS event servi 2 service-policy service service 4RULE_PPP_ATM5 always event session-start 1 service-policy service service 233RULE_PPP_ATM5 always event quota-depleted 1 set-param drop-traffic FALSE 0RULE_PPP_ATM5 always event credit-exhausted 1 service-policy service service 0RULE_PPP_ATM5 always event internal-event-c 1 service-policy service unapply 0Key:"Exec" - The number of times this rule action line was executedie2-C7206-LNS#Clearing Statistics
The clear subscriber policy conditions command can be used to clear the statistics of subscriber policy changes.
ie2-C7206-LNS# clear subscriber policy conditionsie2-C7206-LNS#ie2-C7206-LNS# show subscriber policy conditionsClass-map Action Exec Hit Miss Comp--------- ------ ---- --- ---- ----match-any BOD2MVOLUME_CLASS match identifier service-name B 0 0 0 0match-any BOD1MVOLUME_CLASS match identifier service-name B 0 0 0 0match-any BOD2MTIME_CLASS match identifier service-name B 0 0 0 0match-any BOD256K_CLASS match identifier service-name B 0 0 0 0match-any BOD1MTIME_CLASS match identifier service-name B 0 0 0 0Key:"Exec" - The number of times this line was executed"Hit" - The number of times this line evaluated to TRUE"Miss" - The number of times this line evaluated to FALSE"Comp" - The number of times this line completed the execution of itscondition without a need to continue on to the endie2-C7206-LNS#Complete Running Configurations
The following sections contain complete running configurations for the devices in the network:
•
CPE
•
LAC

Note
Lines preceded by an exclamation marks (!) are comments about the configuration.
CPE
version 12.3no service padservice timestamps debug uptimeservice timestamps log uptimeservice password-encryption!hostname ie2-C837-CPE6!enable password 7 13091610!no aaa new-modelip subnet-zeroip dhcp excluded-address 10.10.10.1!! DHCP config for interface E0 subscribersip dhcp pool CLIENTimport allnetwork 10.10.10.0 255.255.255.0default-router 10.10.10.1lease 0 2!!ip cefip audit notify logip audit po max-events 100!!no ftp-server write-enable!!!!!!!interface Ethernet0ip address 10.10.10.1 255.255.255.0ip nat insideload-interval 30no cdp enablehold-queue 100 out!interface ATM0bandwidth 864no ip addressip route-cache flowload-interval 30no atm ilmi-keepalivedsl operating-mode auto!interface ATM0.6 point-to-point! This is the PVC which is going to the ATM DSLAMpvc 6/46encapsulation aal5snap! Refers to dialer 1pppoe-client dial-pool-number 1!!interface FastEthernet1no ip addressduplex autospeed auto!interface FastEthernet2no ip addressduplex autospeed auto!interface FastEthernet3no ip addressduplex autospeed auto!interface FastEthernet4no ip addressduplex autospeed auto!interface Dialer1ip address negotiated! NAT outside interfaceip nat outside! using pppencapsulation pppip route-cache flowdialer pool 1dialer-group 1no cdp enable! here we set the username via CHAPppp chap hostname cpe6_1@isp.com! set the password for CHAPppp chap password 7 060A0E23!! This allows the subscribers on the inside E0 interface access to the outside via NATip nat inside source list 1 interface Dialer1 overload!ip classless! set the default gateway out the dialer 1 interfaceip route 0.0.0.0 0.0.0.0 Dialer1ip http serverno ip http secure-server!! allow E0 subscribers to be NAT translatedaccess-list 1 permit 10.10.10.0 0.0.0.255! refers to ACL 1dialer-list 1 protocol ip permitno cdp run!line con 0exec-timeout 120 0no modem enablestopbits 1line aux 0line vty 0 4access-class 23 inexec-timeout 120 0password 7 11051807no loginlength 0!scheduler max-task-time 5000!endLAC
version 12.2no service padservice timestamps debug datetime msec localtimeservice timestamps log datetime msecno service password-encryption!hostname ie2-C7206-ATM2!boot-start-markerboot system disk2:c7200-js-mz.122-27.1.11.SIE7boot-end-marker!no logging consoleenable password lab!! enable AAA globallyaaa new-model!!aaa authentication login default none! setup RADIUS server for authenticationaaa authentication ppp default group radius localaaa authorization network default group radius localaaa accounting network default start-stop group radius!!aaa session-id commonclock timezone Pacific -8ip subnet-zero!!ip ftp username rootip ftp password labno ip dhcp use vrf connected!!ip cef!!subscriber policy recording rules limit 64subscriber access pppoe pre-authorize nas-port-id defaultsubscriber authorization enable! enable VPDN globally used for PPPoEvpdn enablevpdn ip udp ignore checksumvpdn search-order domain!no mpls traffic-eng auto-bw timers frequency 0call rsvp-sync!!!!!username all!!! rule to look at L2TP @domainpolicy-map control RULE_L2TP_LM_ATM5class control always event session-start1 collect identifier unauthenticated-domain2 authorize identifier unauthenticated-domain!!!! bba PPPoE group (another method is vpdn-group)bba-group pppoe BBA_LM_ATM5virtual-template 5sessions auto cleanup!!! This is applied to ATM pvcvc-class atm VC_LM_ATM5! refers to bba-group aboveprotocol pppoe group BBA_LM_ATM5! allow dynamic bandwidth selectiondbs enable maximumencapsulation aal5snap! apply L2TP ruleservice-policy control RULE_L2TP_LM_ATM5!interface Loopback0ip address 10.200.1.49 255.255.255.255!interface GigabitEthernet0/1ip address 223.255.12.49 255.255.255.0duplex autospeed automedia-type rj45no negotiation auto!interface GigabitEthernet0/2ip address 160.49.1.49 255.255.255.0load-interval 30duplex fullspeed 1000media-type gbicnegotiation auto!interface GigabitEthernet0/3ip address 180.49.1.49 255.255.255.0ip portbundle outsideip flow ingressload-interval 30duplex fullspeed 1000media-type gbicnegotiation auto!interface ATM1/0no ip addressno ip redirectsno ip unreachablesno ip proxy-arpip flow ingressload-interval 30no atm auto-configurationno atm ilmi-keepaliveno atm address-registration!interface ATM2/0no ip addressno ip redirectsno ip unreachablesno ip proxy-arpip flow ingressload-interval 30no atm auto-configurationno atm ilmi-keepaliveno atm address-registrationno atm ilmi-enableno atm enable-ilmi-trapbundle-enablentp disable!!interface ATM2/0.101 point-to-pointip flow ingressno atm enable-ilmi-trappvc 106/46! VC classclass-vc VC_LM_ATM5! this can be changed to restrict PPPoE sessions on the PVCpppoe max-sessions 1!!interface ATM2/0.108 point-to-pointip flow ingressno atm enable-ilmi-trappvc 108/48class-vc VC_LM_ATM5pppoe max-sessions 1!!interface FastEthernet4/0no ip addressshutdownduplex autospeed auto!interface FastEthernet4/1no ip addressshutdownduplex autospeed auto!! PPP CHAP configs hereinterface Virtual-Template5no ip addressno peer default ip addressno keepaliveppp authentication chapppp timeout aaa!router ospf 10log-adjacency-changesnetwork 10.200.1.49 0.0.0.0 area 200network 160.49.1.0 0.0.0.255 area 200network 180.49.1.0 0.0.0.255 area 200network 201.53.6.1 0.0.0.0 area 200!router bgp 100no synchronizationbgp router-id 10.200.1.49bgp log-neighbor-changesredistribute connectedneighbor 10.200.1.41 remote-as 100neighbor 10.200.1.41 update-source Loopback0no auto-summary!ip classless!no ip http server!!! Use Loopback 0 to communicate with radius serverip radius source-interface Loopback0!!! use this as radius server and specified ports and passwordsradius-server host 10.100.1.35 auth-port 1812 acct-port 1813 key Cisco! set up accounting VSA (vendor specific attributes)radius-server vsa send accounting! set up authentication VSAradius-server vsa send authentication!control-plane!!dial-peer cor custom!!!!gatekeepershutdown!!line con 0exec-timeout 0 0stopbits 1line aux 0stopbits 1line vty 0 4exec-timeout 3600 0!ntp clock-period 17179700ntp server 10.200.1.41 prefer!endISG LNS
version 12.2no service padservice timestamps debug datetime msec localtimeservice timestamps log datetime msecno service password-encryption!hostname ie2-C7206-LNS!boot-start-markerboot system disk2:c7200-js-mz.122-27.1.11.SIE7boot-end-marker!logging buffered 2000000 debuggingno logging consoleenable password lab!! enable AAA globallyaaa new-model!!! set up AAA server group for CARaaa group server radius CAR_SERVERserver 10.100.2.36 auth-port 1812 acct-port 1813!! set up AAA server for billing server 1aaa group server radius RSIM_SERVERserver 10.100.6.88 auth-port 1645 acct-port 1646!! set up AAA server group for billing server 2aaa group server radius MIND_SERVERserver 10.100.11.86 auth-port 1645 acct-port 1646! the following sets up the server groups for the 3 phases of AAAaaa authentication login default noneaaa authentication login IP_AUTHEN_LIST group CAR_SERVERaaa authentication ppp default group CAR_SERVERaaa authentication ppp PREPAID_MIND group MIND_SERVERaaa authentication ppp PREPAID_AUTHEN_LIST group RSIM_SERVERaaa authorization network default group CAR_SERVERaaa authorization network PREPAID_MIND group MIND_SERVERaaa authorization network PREPAID_AUTHOR_LIST group RSIM_SERVERaaa authorization subscriber-service default local group radiusaaa accounting network default start-stop group CAR_SERVERaaa accounting network PREPAID_MIND start-stop group MIND_SERVERaaa accounting network PREPAID_ACCNT_LIST start-stop group RSIM_SERVER! SESM access port, passwordaaa server radius sesm! IP address of SESMclient 10.100.4.38key ciscoport 1812message-authenticator ignore!!aaa session-id commonclock timezone Pacific -8ip subnet-zero!!ip ftp username rootip ftp password labno ip dhcp use vrf connected!!! Set up MPLS VRF for subscribers globally on routerip vrf VPN11006rd 200:6route-target export 200:6route-target import 200:6!!ip cef!! This is the prepaid server global config PREPAID_RSIM will be referred to on AAA server! for each service profilesubscriber feature prepaid PREPAID_RSIMthreshold time 10 secondsthreshold volume 1000 bytesinterim-interval 3 minutes! This refers to authorization list in AAA configuration abovemethod-list author PREPAID_AUTHOR_LIST! accounting method listmethod-list accounting PREPAID_ACCNT_LIST! prepaid password on billing serverpassword prepaidcisco! This is a 2nd billing server prepaid global setupsubscriber feature prepaid PREPAID_MINDthreshold time 10 secondsthreshold volume 1000 bytesinterim-interval 3 minutesmethod-list author PREPAID_MINDmethod-list accounting PREPAID_MINDpassword prepaidcisco!subscriber policy recording rules limit 64! enable VPDN for PPPoE/L2TPvpdn enablevpdn ip udp ignore checksum!! terminate PPPoE client here via L2TP tunnelvpdn-group 1accept-dialinprotocol l2tpvirtual-template 5terminate-from hostname sp_laclocal name sp_lnsl2tp tunnel password 0 lab!!! L4 Redirect server configurationredirect server-group SESM-Serverserver ip 10.100.4.38 port 8080!clns routingno mpls traffic-eng auto-bw timers frequency 0mpls label protocol ldpcall rsvp-sync!!class-map type control match-any BOD1MTIME_CLASS<-- following is the class-map configuration for the services available which is applied in the policy map belowmatch service-name BOD1MTIME!class-map type control match-any BOD256K_CLASSmatch service-name BOD256K!class-map type control match-any BOD2MTIME_CLASSmatch service-name BOD2MTIME!class-map type control match-any BOD1MVOLUME_CLASSmatch service-name BOD1MVOLUME!class-map type control match-any BOD2MVOLUME_CLASSmatch service-name BOD2MVOLUME!!! Rule which is applied to virtual-templatepolicy-map type control RULE_PPP_ATM5class type control BOD1MTIME_CLASS event service-start1 service-policy type service unapply name BOD256K2 service-policy type service unapply name BoD2MTIME3 service-policy type service identifier service-name!class type control BOD2MTIME_CLASS event service-start1 service-policy type service unapply name BOD256K2 service-policy type service unapply name BOD1MTIME3 service-policy type service identifier service-name!class type control BOD256K_CLASS event service-start1 service-policy type service unapply name BOD1MTIME2 service-policy type service unapply name BOD2MTIME3 service-policy type service unapply name BOD1MVOLUME4 service-policy type service unapply name BOD2MVOLUME5 service-policy type service identifier service-name!! If a subscriber selects this service class we follow the steps belowclass type control BOD1MVOLUME_CLASS event service-start! unapply these services first before we apply the selected BOD1MVOLUME service1 service-policy type service unapply name BOD256K2 service-policy type service unapply name BOD2MVOLUME3 service-policy type service identifier service-name!class type control BOD2MVOLUME_CLASS event service-start1 service-policy type service unapply name BOD256K2 service-policy type service unapply name BOD1MVOLUME3 service-policy type service identifier service-name!! if the subscriber stops this service then we unapply it and then apply the default! BOD256K serviceclass type control BOD2MTIME_CLASS event service-stop1 service-policy type service unapply identifier service-name2 service-policy type service name BOD256K!class type control BOD1MTIME_CLASS event service-stop1 service-policy type service unapply identifier service-name2 service-policy type service name BOD256K!class type control BOD2MVOLUME_CLASS event service-stop1 service-policy type service unapply identifier service-name2 service-policy type service name BOD256K!class type control BOD1MVOLUME_CLASS event service-stop1 service-policy type service unapply identifier service-name2 service-policy type service name BOD256K!class type control always event session-start! always apply PBHK so subscriber can access SESM1 service-policy type service name PBHK_SERVICE!class type control always event quota-depleted! If quota from billing server and idle time equal zero then drop traffic1 set-param drop-traffic FALSE!! If quota from billing server equal zero, but idle time is greater than zero L4 redirectclass type control always event credit-exhausted1 service-policy type service name L4REDIRECT_SERVICE!!!!! address we communicate with AAA, billing servers, SESMinterface Loopback0ip address 10.200.1.55 255.255.255.255ip router isis Remote_ISP!interface Loopback1ip vrf forwarding VPN11006ip address 100.6.6.6 255.255.255.255!interface GigabitEthernet0/1ip address 223.255.12.55 255.255.255.0duplex autospeed automedia-type rj45no negotiation auto!interface GigabitEthernet0/2ip address 21.21.1.55 255.255.255.0ip portbundle outsideip flow ingressip router isis Remote_ISPload-interval 30duplex autospeed automedia-type gbicnegotiation autompls mtu 1522mpls label protocol ldpmpls ip!interface GigabitEthernet0/3ip address 22.22.1.55 255.255.255.0ip portbundle outsideip flow ingressip router isis Remote_ISPload-interval 30duplex fullspeed 1000media-type gbicnegotiation autompls mtu 1522mpls label protocol ldpmpls ipno keepalive!interface FastEthernet1/0ip address 199.1.1.1 255.255.255.0load-interval 30shutdownduplex fullspeed 100!interface FastEthernet1/1no ip addressshutdownduplex autospeed auto!! PPPoE subscribers terminate from L2TP hereinterface Virtual-Template5no ip addressload-interval 30no peer default ip addressno keepaliveppp mtu adaptiveppp authentication chap! apply this rule to subscribersservice-policy control RULE_PPP_ATM5!router isis Remote_ISPnet 02.000c.cffe.c81b.00redistribute connected!router bgp 200no synchronizationbgp router-id 10.200.1.55bgp log-neighbor-changesnetwork 10.100.4.0 mask 255.255.255.0network 10.200.1.47 mask 255.255.255.255network 10.200.1.55 mask 255.255.255.255network 10.200.1.62 mask 255.255.255.255network 21.21.1.55 mask 255.255.255.0network 22.22.1.55 mask 255.255.255.0network 23.0.0.0network 24.0.0.0 mask 255.255.0.0network 24.5.0.0 mask 255.255.0.0neighbor 10.200.1.41 remote-as 100neighbor 10.200.1.41 ebgp-multihop 2neighbor 10.200.1.41 update-source Loopback0neighbor 10.200.1.47 remote-as 200neighbor 10.200.1.47 update-source Loopback0neighbor 10.200.1.47 next-hop-selfno auto-summary!address-family vpnv4neighbor 10.200.1.47 activateneighbor 10.200.1.47 send-community extendedexit-address-family!address-family ipv4 vrf VPN11006redistribute connectedno auto-summaryno synchronizationexit-address-family!! DHCP pool assigned to subscribersip local pool cpe6_pool-53 200.53.6.2 200.53.6.254!! for PBHK SESM accessip portbundlematch access-list 110! communicate with SESM via router Loopback 0source Loopback0!ip classlessip route 10.200.1.41 255.255.255.255 21.21.1.41!no ip http server!!!! This ACL is called out in the AAA subscriber profile and allows or denies access to! destinations for subscribers based on this ACLip access-list extended Internet-in-acldeny ip any 223.0.0.0 0.255.255.255deny ip any 20.0.0.0 0.255.255.255deny ip any 40.0.0.0 0.255.255.255deny ip any 21.0.0.0 0.255.255.255deny ip any 22.0.0.0 0.255.255.255deny ip any 41.0.0.0 0.255.255.255deny ip any 80.0.0.0 0.255.255.255deny ip any 81.0.0.0 0.255.255.255deny ip any 82.0.0.0 0.255.255.255deny ip any 10.200.0.0 0.0.255.255permit ip any any! This ACL is called out in the AAA subscriber profile and allows or denies access to! destinations for subscribers based on this ACLip access-list extended Internet-out-acldeny ip 223.0.0.0 0.255.255.255 anydeny ip 10.200.0.0 0.0.255.255 anydeny ip 20.0.0.0 0.255.255.255 anydeny ip 40.0.0.0 0.255.255.255 anydeny ip 21.0.0.0 0.255.255.255 anydeny ip 22.0.0.0 0.255.255.255 anydeny ip 41.0.0.0 0.255.255.255 anydeny ip 80.0.0.0 0.255.255.255 anydeny ip 81.0.0.0 0.255.255.255 anydeny ip 82.0.0.0 0.255.255.255 anypermit ip any any! sets up router to communicate AAA RADIUS via loopback 0 address as sourceip radius source-interface Loopback0access-list 101 permit ip any any! deny SESMaccess-list 110 permit ip any host 10.100.4.38! called out in "ip portbundle" config aboveaccess-list 110 permit ip any anyaccess-list 111 deny tcp any host 10.100.4.38 eq wwwaccess-list 111 deny tcp any host 10.100.4.38 eq 8080access-list 111 permit tcp any any eq www!!radius-server attribute 44 include-in-access-reqradius-server attribute 8 include-in-access-reqradius-server attribute 55 include-in-acct-reqradius-server attribute 55 access-request includeradius-server attribute 25 access-request include! AAA/CAR serverradius-server host 10.100.2.36 auth-port 1812 acct-port 1813 key Cisco! billing server 1radius-server host 10.100.6.88 auth-port 1645 acct-port 1646 key Cisco! billing server 2radius-server host 10.100.11.86 auth-port 1645 acct-port 1646 key Ciscoradius-server retransmit 5radius-server key ciscoradius-server vsa send accountingradius-server vsa send authentication!control-plane!!dial-peer cor custom!!!!gatekeepershutdown!!line con 0exec-timeout 0 0stopbits 1line aux 0stopbits 1line vty 0 4exec-timeout 0 0!ntp clock-period 17180035ntp server 10.200.1.41 prefer!endPE at ISP-2
version 12.2service timestamps debug datetime msecservice timestamps log datetime msecno service password-encryptionservice counters max age 10!hostname ie2-C6509-PE2!boot system disk0:s72033-pk9sv-mz.122-18.SXD1.binlogging snmp-authfailno logging consoleenable password lab!no aaa new-modelclock timezone PST -8vtp mode transparentip subnet-zero!!ip ftp username rootip ftp password labno ip domain-lookup!!ip vrf VPN11006rd 200:6route-target export 200:6route-target import 200:6!!mls ip multicast flow-stat-timer 9no mls flow ipno mls flow ipv6mls cef error action freeze!!!!spanning-tree mode pvstno spanning-tree optimize bpdu transmissiondiagnostic cns publish cisco.cns.device.diag_resultsdiagnostic cns subscribe cisco.cns.device.diag_commands!redundancymode ssomain-cpuauto-sync running-configauto-sync standard!controller T1 7/1/0framing esflinecode b8zs!controller T1 7/1/1framing esflinecode b8zs!controller T1 7/1/2framing esflinecode b8zs!controller T1 7/1/3framing esflinecode b8zs!vlan internal allocation policy ascendingvlan access-log ratelimit 2000!vlan 6,10!!interface Loopback0ip address 10.200.1.43 255.255.255.255ip router isis Area10!interface FastEthernet1/1description FE link to C7206-PE-FE1/0no ip addressswitchport!interface FastEthernet1/2description FE-LINK to ie2-SNMP-1Aip address 10.100.2.43 255.255.255.0ip router isis Area10!interface FastEthernet1/3description FE LINK to ie2-SESM-1Bno ip addressswitchportswitchport access vlan 6!interface FastEthernet1/4description link to SESM1b on non-vrf for Mindip address 10.100.5.1 255.255.255.0ip router isis Area10!interface FastEthernet1/5no ip addressswitchportswitchport access vlan 10!interface FastEthernet1/6no ip address!interface FastEthernet1/7ip address 10.100.6.43 255.255.255.0!interface FastEthernet1/47no ip addressspeed 100duplex full!interface FastEthernet1/48ip address 223.255.12.43 255.255.255.0ip router isis Area10speed 100duplex full!interface GigabitEthernet2/1no ip addressshutdown!interface GigabitEthernet2/2no ip addressshutdown!interface GE-WAN2/1no ip addressshutdownnegotiation automls qos trust dscp!interface GE-WAN2/2no ip addressshutdownnegotiation automls qos trust dscp!interface GE-WAN2/3no ip addressshutdownnegotiation automls qos trust dscp!interface GE-WAN2/4no ip addressshutdownnegotiation automls qos trust dscp!interface GigabitEthernet3/1no ip addressshutdown!interface GigabitEthernet3/2no ip addressshutdown!interface GigabitEthernet3/3no ip addressshutdown!interface GigabitEthernet3/4no ip addressshutdown!interface POS3/1no ip addressshutdownmls qos trust dscp!interface POS3/2no ip addressshutdownmls qos trust dscp!interface GigabitEthernet4/1ip address 83.83.1.43 255.255.255.0ip router isis Area10load-interval 30mpls label protocol ldptag-switching ip!interface GigabitEthernet4/2no ip addressshutdown!interface GigabitEthernet4/3no ip addressshutdown!interface GigabitEthernet4/4no ip addressshutdown!interface GigabitEthernet4/5no ip address!interface GigabitEthernet4/6no ip addressload-interval 30!interface GigabitEthernet4/6.206encapsulation dot1Q 206ip vrf forwarding VPN11006ip address 84.1.206.43 255.255.255.0!!interface GigabitEthernet4/7no ip addressshutdown!interface GigabitEthernet4/8no ip addressshutdown!interface GigabitEthernet5/1no ip addressshutdown!interface GigabitEthernet5/2no ip addressshutdown!interface Hssi7/0/0no ip addressshutdown!interface Hssi7/0/1no ip addressshutdown!interface Serial8/0/0no ip addressshutdownno fair-queue!interface Serial8/0/1no ip addressshutdownno fair-queue!interface Serial8/0/2no ip addressshutdownno fair-queue!interface Serial8/0/3no ip addressshutdownno fair-queue!interface Serial8/1/0no ip addressshutdowndsu bandwidth 44210framing c-bitcablelength 10!interface Serial8/1/1no ip addressshutdowndsu bandwidth 44210framing c-bitcablelength 10!interface Vlan1no ip addressshutdown!interface Vlan6ip address 10.100.4.43 255.255.255.0ip router isis Area10!interface Vlan10ip address 10.100.10.1 255.255.255.0ip router isis Area10!router isis Area10net 10.000e.d6aa.5000.00redistribute connected!router bgp 200no synchronizationbgp router-id 10.200.1.43bgp log-neighbor-changesnetwork 10.100.2.0 mask 255.255.255.0network 10.200.1.43 mask 255.255.255.255network 24.7.1.0 mask 255.255.255.0network 83.83.1.0 mask 255.255.255.0network 84.1.1.0 mask 255.255.255.0network 84.2.1.0 mask 255.255.255.0network 84.3.1.0 mask 255.255.255.0network 84.4.1.0 mask 255.255.255.0neighbor 10.200.1.47 remote-as 200neighbor 10.200.1.47 ebgp-multihop 10neighbor 10.200.1.47 update-source Loopback0no auto-summary!address-family vpnv4neighbor 10.200.1.47 activateneighbor 10.200.1.47 send-community extendedexit-address-family!!address-family ipv4 vrf VPN11006redistribute connectedredistribute staticno auto-summaryno synchronizationexit-address-family!!ip classlessip route vrf VPN11006 10.100.4.38 255.255.255.255 Vlan6 10.100.4.38ip http server!!!!!!control-plane!!!line con 0exec-timeout 0 0line vty 0 4exec-timeout 0 0no login!endAAA Server for ISP-1
This profile allows the LAC access to AAA-1. 10.200.1.49 is the loopback address on the LAC.
--> cd ie2-c7206-ge[ //localhost/Radius/Clients/ie2-C7206-GE ]Name = ie2-C7206-GEDescription =IPAddress = 10.200.1.49SharedSecret = ciscoType = NASVendor =IncomingScript~ =OutgoingScript~ =EnablePOD = FALSE-->This profile allows the @isp.com portion of the username to bring up the L2TP tunnel to ISP-2. 10.200.1.55 is the loopback address of the ISG LNS.
--> cd isp.com[ //localhost/Radius/UserLists/SESMServices/isp.com ]Name = isp.comDescription =Password = <encrypted>Enabled = TRUEGroup~ =BaseProfile~ =AuthenticationScript~ =AuthorizationScript~ =UserDefined1 =AllowNullPassword = FALSEAttributes/CheckItems/--> ls attributes/[ Attributes ]Cisco-AVpair = vpdn:tunnel-id=sp_lacCisco-AVpair = vpdn:l2tp-tunnel-password=labCisco-AVpair = vpdn:tunnel-type=l2tpCisco-AVpair = vpdn:ip-addresses=10.200.1.55Cisco-AVpair = atm:peak-cell-rate=3000Cisco-AVpair = atm:sustainable-cell-rate=3000idle-timeout = 86400AAA Server for ISP-2
This profile allows the ISG LNS to access to AAA-2.
--> cd ie2-c7206-lns[ //localhost/Radius/Clients/ie2-C7206-LNS ]Name = ie2-C7206-LNSDescription =IPAddress = 10.200.1.55SharedSecret = ciscoType = NASVendor =IncomingScript~ =OutgoingScript~ =EnablePOD = FALSE-->--> cd ie2-sesm-1b[ //localhost/Radius/Clients/ie2-SESM-1b ]Name = ie2-SESM-1bDescription =IPAddress = 10.100.4.38SharedSecret = ciscoType = NASVendor =IncomingScript~ =OutgoingScript~ =EnablePOD = FALSE-->This is the subscriber profile, which specifies the services that are allowed.
--> cd cpe6_1@isp.com[ //localhost/Radius/UserLists/SESMSubscribers/cpe6_1@isp.com ]Name = cpe6_1@isp.comDescription =Password = <encrypted>Enabled = TRUEGroup~ =BaseProfile~ = Default-PPP-UsersAuthenticationScript~ =AuthorizationScript~ =UserDefined1 =AllowNullPassword = FALSEAttributes/CheckItems/--> ls attributes/[ Attributes ]Cisco-AVpair = "lcp:interface-config=ip vrf forwarding VPN11006"Cisco-AVpair = "lcp:interface-config=ip unnumbered loopback 1"Cisco-AVpair = ip:addr-pool=cpe6_pool-53Cisco-SSG-Account-Info = ABOD256KCisco-SSG-Account-Info = NBOD256KCisco-SSG-Account-Info = NBOD1MTIMECisco-SSG-Account-Info = NBOD2MTIMECisco-SSG-Account-Info = NBOD1MVOLUMECisco-SSG-Account-Info = NBOD2MVOLUMESession-Timeout = 86400-->These profiles define the prepaid services.
--> cd bod256k[ //localhost/Radius/UserLists/SESMServices/BOD256K ]Name = BOD256KDescription =Password = <encrypted>Enabled = TRUEGroup~ =BaseProfile~ =AuthenticationScript~ =AuthorizationScript~ =UserDefined1 =AllowNullPassword = FALSEAttributes/CheckItems/--> ls attributes/[ Attributes ]Cisco-AVPair = "ip:traffic-class=in access-group name Internet-in-acl"Cisco-AVPair = "ip:traffic-class=in default drop"Cisco-AVPair = "ip:traffic-class=out access-group name Internet-out-acl"Cisco-AVPair = "ip:traffic-class=out default drop"Cisco-SSG-Service-Info = IBOD256KCisco-SSG-Service-Info = QU;128000;8000;8000;D;256000;16000;16000Cisco-SSG-Service-Info = R42.1.1.0;255.255.255.0-->--> cd bod1mtime[ //localhost/Radius/UserLists/SESMServices/BOD1MTIME ]Name = BOD1MTIMEDescription =Password = <encrypted>Enabled = TRUEGroup~ =BaseProfile~ =AuthenticationScript~ =AuthorizationScript~ =UserDefined1 =AllowNullPassword = FALSEAttributes/CheckItems/--> ls attributes/[ Attributes ]Cisco-AVPair = "ip:traffic-class=in access-group name Internet-in-acl"Cisco-AVPair = "ip:traffic-class=in default drop"Cisco-AVPair = "ip:traffic-class=out access-group name Internet-out-acl"Cisco-AVPair = "ip:traffic-class=out default drop"Cisco-AVPair = prepaid-config=PREPAID_RSIMCisco-SSG-Service-Info = IBOD1MTIMECisco-SSG-Service-Info = QU;256000;16000;16000;D;1000000;64000;64000Cisco-SSG-Service-Info = R42.1.1.0;255.255.255.0-->--> cd bod2mtime[ //localhost/Radius/UserLists/SESMServices/BOD2MTIME ]Name = BOD2MTIMEDescription =Password = <encrypted>Enabled = TRUEGroup~ =BaseProfile~ =AuthenticationScript~ =AuthorizationScript~ =UserDefined1 =AllowNullPassword = FALSEAttributes/CheckItems/--> ls attributes/[ Attributes ]Cisco-AVPair = "ip:traffic-class=in access-group name Internet-in-acl"Cisco-AVPair = "ip:traffic-class=in default drop"Cisco-AVPair = "ip:traffic-class=out access-group name Internet-out-acl"Cisco-AVPair = "ip:traffic-class=out default drop"Cisco-AVPair = prepaid-config=PREPAID_RSIMCisco-SSG-Service-Info = IBOD2MTIMECisco-SSG-Service-Info = QU;512000;32000;32000;D;2000000;128000;128000Cisco-SSG-Service-Info = R42.1.1.0;255.255.255.0-->--> cd bod1mvolUME/[ //localhost/Radius/UserLists/SESMServices/BOD1MVOLUME ]Name = BOD1MVOLUMEDescription =Password = <encrypted>Enabled = TRUEGroup~ =BaseProfile~ =AuthenticationScript~ =AuthorizationScript~ =UserDefined1 =AllowNullPassword = FALSEAttributes/CheckItems/--> ls attributes/[ Attributes ]Cisco-AVPair = "ip:traffic-class=in access-group name Internet-in-acl"Cisco-AVPair = "ip:traffic-class=in default drop"Cisco-AVPair = "ip:traffic-class=out access-group name Internet-out-acl"Cisco-AVPair = "ip:traffic-class=out default drop"Cisco-AVPair = prepaid-config=PREPAID_RSIMCisco-SSG-Service-Info = IBOD1MVOLUMECisco-SSG-Service-Info = QU;256000;16000;16000;D;1000000;64000;64000Cisco-SSG-Service-Info = R42.1.1.0;255.255.255.0-->--> cd bod2mvolUME/[ //localhost/Radius/UserLists/SESMServices/BOD2MVOLUME ]Name = BOD2MVOLUMEDescription =Password = <encrypted>Enabled = TRUEGroup~ =BaseProfile~ =AuthenticationScript~ =AuthorizationScript~ =UserDefined1 =AllowNullPassword = FALSEAttributes/CheckItems/--> ls attributes/[ Attributes ]Cisco-AVPair = "ip:traffic-class=in access-group name Internet-in-acl"Cisco-AVPair = "ip:traffic-class=in default drop"Cisco-AVPair = "ip:traffic-class=out access-group name Internet-out-acl"Cisco-AVPair = "ip:traffic-class=out default drop"Cisco-AVPair = prepaid-config=PREPAID_RSIMCisco-SSG-Service-Info = IBOD2MVOLUMECisco-SSG-Service-Info = QU;512000;32000;32000;D;2000000;128000;128000Cisco-SSG-Service-Info = R42.1.1.0;255.255.255.0-->These are the other profiles that are required for the services to function properly.
--> cd l4redirECT_SERVICE/[ //localhost/Radius/UserLists/SESMServices/L4REDIRECT_SERVICE ]Name = L4REDIRECT_SERVICEDescription =Password = <encrypted>Enabled = TRUEGroup~ =BaseProfile~ =AuthenticationScript~ =AuthorizationScript~ =UserDefined1 =AllowNullPassword = FALSEAttributes/CheckItems/--> ls attributes/[ Attributes ]Cisco-AVPair = "ip:l4redirect=redirect list 111 to group SESM-Server duration 30 frequency 180"-->--> cd pbhk_service[ //localhost/Radius/UserLists/SESMServices/PBHK_SERVICE ]Name = PBHK_SERVICEDescription =Password = <encrypted>Enabled = TRUEGroup~ =BaseProfile~ =AuthenticationScript~ =AuthorizationScript~ =UserDefined1 =AllowNullPassword = FALSEAttributes/CheckItems/--> ls attributes/[ Attributes ]Cisco-AVPair = ip:portbundle=enable-->--> cd default-ppP-users/[ //localhost/Radius/Profiles/default-PPP-users ]Name = default-PPP-usersDescription =Attributes/--> ls attributes/[ Attributes ]Ascend-Idle-Limit = 1800Framed-MTU = 1500Framed-Protocol = PPPFramed-Routing = NoneIdle-timeout = 180Service-Type = Framed

Copyright © 2005 Cisco Systems, Inc. All rights reserved.
 Feedback
Feedback