- About This Guide
-
- Introduction to the Security Appliance
- Getting Started
- Enabling Multiple Context Mode
- Configuring Interfaces for the Cisco ASA 5505 Adaptive Security Appliance
- Configuring Ethernet Settings and Subinterfaces
- Adding and Managing Security Contexts
- Configuring Interface Parameters
- Configuring Basic Settings
- Configuring IP Routing
- Configuring Multicast Routing
- Configuring DHCP, DDNS, and WCCP Services
- Configuring IPv6
- Configuring AAA Servers and the Local Database
- Configuring Failover
-
- Firewall Mode Overview
- Identifying Traffic With Access Lists
- Applying NAT
- Permitting or Denying Network Access
- Applying AAA for Network Access
- Applying Filtering Services
- Using Modular Policy Framework
- Managing AIP SSM and CSC SSM
- Preventing Network Attacks
- Applying QoS Policies
- Applying Application Layer Protocol Inspection
- Configuring ARP Inspection and Bridging Parameters
-
- Configuring IPSec and ISAKMP
- Configuring L2TP over IPSec
- Setting General VPN Parameters
- Configuring Tunnel Groups, Group Policies, and Users
- Configuring IP Addresses for VPN
- Configuring Remote Access VPNs
- Configuring Network Admission Control
- Configuring Easy VPN on the ASA 5505
- Configuring the PPPoE Client
- Configuring LAN-to-LAN VPNs
- Configuring WebVPN
- Configuring SSL VPN Client
- Configuring Certificates
- Glossary
- Index
Identifying Traffic with Access Lists
This chapter describes how to identify traffic with access lists. This chapter includes the following topics:
•![]() Adding an Extended Access List
Adding an Extended Access List
•![]() Adding an EtherType Access List
Adding an EtherType Access List
•![]() Adding a Standard Access List
Adding a Standard Access List
•![]() Simplifying Access Lists with Object Grouping
Simplifying Access Lists with Object Grouping
•![]() Adding Remarks to Access Lists
Adding Remarks to Access Lists
•![]() Scheduling Extended Access List Activation
Scheduling Extended Access List Activation
For information about IPv6 access lists, see the "Configuring IPv6 Access Lists" section on page 12-6.
Access List Overview
Access lists are made up of one or more Access Control Entries. An ACE is a single entry in an access list that specifies a permit or deny rule, and is applied to a protocol, a source and destination IP address or network, and optionally the source and destination ports.
Access lists are used in a variety of features. If your feature uses Modular Policy Framework, you can use an access list to identify traffic within a traffic class map. For more information on Modular Policy Framework, see Chapter 21, "Using Modular Policy Framework."
This section includes the following topics:
•![]() IP Addresses Used for Access Lists When You Use NAT
IP Addresses Used for Access Lists When You Use NAT
Access List Types
Table 16-1 lists the types of access lists and some common uses for them.
|
|
|
|
|---|---|---|
Control network access for IP traffic (routed and transparent mode) |
Extended |
The security appliance does not allow any traffic from a lower security interface to a higher security interface unless it is explicitly permitted by an extended access list. Note |
Identify traffic for AAA rules |
Extended |
AAA rules use access lists to identify traffic. |
Control network access for IP traffic for a given user |
Extended, downloaded from a AAA server per user |
You can configure the RADIUS server to download a dynamic access list to be applied to the user, or the server can send the name of an access list that you already configured on the security appliance. |
Identify addresses for NAT (policy NAT and NAT exemption) |
Extended |
Policy NAT lets you identify local traffic for address translation by specifying the source and destination addresses in an extended access list. |
Establish VPN access |
Extended |
You can use an extended access list in VPN commands. |
Identify traffic in a traffic class map for Modular Policy Framework |
Extended EtherType |
Access lists can be used to identify traffic in a class map, which is used for features that support Modular Policy Framework. Features that support Modular Policy Framework include TCP and general connection settings, and inspection. |
For transparent firewall mode, control network access for non-IP traffic |
EtherType |
You can configure an access list that controls traffic based on its EtherType. |
Identify OSPF route redistribution |
Standard |
Standard access lists include only the destination address. You can use a standard access list to control the redistribution of OSPF routes. |
Filtering for WebVPN |
Webtype |
You can configure a Webtype access list to filter URLs. |
Access Control Entry Order
An access list is made up of one or more Access Control Entries. Depending on the access list type, you can specify the source and destination addresses, the protocol, the ports (for TCP or UDP), the ICMP type (for ICMP), or the EtherType.
Each ACE that you enter for a given access list name is appended to the end of the access list.
The order of ACEs is important. When the security appliance decides whether to forward or drop a packet, the security appliance tests the packet against each ACE in the order in which the entries are listed. After a match is found, no more ACEs are checked. For example, if you create an ACE at the beginning of an access list that explicitly permits all traffic, no further statements are ever checked.
You can disable an ACE by specifying the keyword inactive in the access-list command.
Access Control Implicit Deny
Access lists have an implicit deny at the end of the list, so unless you explicitly permit it, traffic cannot pass. For example, if you want to allow all users to access a network through the security appliance except for particular addresses, then you need to deny the particular addresses and then permit all others.
For EtherType access lists, the implicit deny at the end of the access list does not affect IP traffic or ARPs; for example, if you allow EtherType 8037, the implicit deny at the end of the access list does not now block any IP traffic that you previously allowed with an extended access list (or implicitly allowed from a high security interface to a low security interface). However, if you explicitly deny all traffic with an EtherType ACE, then IP and ARP traffic is denied.
IP Addresses Used for Access Lists When You Use NAT
When you use NAT, the IP addresses you specify for an access list depend on the interface to which the access list is attached; you need to use addresses that are valid on the network connected to the interface. This guideline applies for both inbound and outbound access lists: the direction does not determine the address used, only the interface does.
For example, you want to apply an access list to the inbound direction of the inside interface. You configure the security appliance to perform NAT on the inside source addresses when they access outside addresses. Because the access list is applied to the inside interface, the source addresses are the original untranslated addresses. Because the outside addresses are not translated, the destination address used in the access list is the real address (see Figure 16-1).
Figure 16-1 IP Addresses in Access Lists: NAT Used for Source Addresses
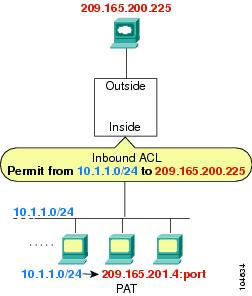
See the following commands for this example:
hostname(config)# access-list INSIDE extended permit ip 10.1.1.0 255.255.255.0 host 209.165.200.225
hostname(config)# access-group INSIDE in interface inside
If you want to allow an outside host to access an inside host, you can apply an inbound access list on the outside interface. You need to specify the translated address of the inside host in the access list because that address is the address that can be used on the outside network (see Figure 16-2).
Figure 16-2 IP Addresses in Access Lists: NAT used for Destination Addresses
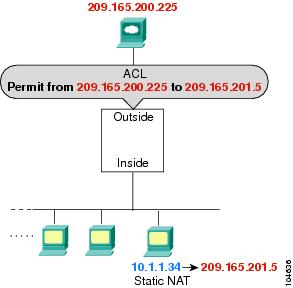
See the following commands for this example:
hostname(config)# access-list OUTSIDE extended permit ip host 209.165.200.225 host 209.165.201.5
hostname(config)# access-group OUTSIDE in interface outside
If you perform NAT on both interfaces, keep in mind the addresses that are visible to a given interface. In Figure 16-3, an outside server uses static NAT so that a translated address appears on the inside network.
Figure 16-3 IP Addresses in Access Lists: NAT used for Source and Destination Addresses
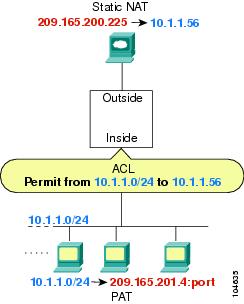
See the following commands for this example:
hostname(config)# access-list INSIDE extended permit ip 10.1.1.0 255.255.255.0 host 10.1.1.56
hostname(config)# access-group INSIDE in interface inside
Adding an Extended Access List
This section describes how to add an extended access list, and includes the following sections:
•![]() Extended Access List Overview
Extended Access List Overview
•![]() Allowing Broadcast and Multicast Traffic through the Transparent Firewall
Allowing Broadcast and Multicast Traffic through the Transparent Firewall
Extended Access List Overview
An extended access list is made up of one or more ACEs, in which you can specify the line number to insert the ACE, source and destination addresses, and, depending on the ACE type, the protocol, the ports (for TCP or UDP), or the ICMP type (for ICMP). You can identify all of these parameters within the access-list command, or you can use object groups for each parameter. This section describes how to identify the parameters within the command. To use object groups, see the "Simplifying Access Lists with Object Grouping" section.
For information about logging options that you can add to the end of the ACE, see the "Logging Access List Activity" section. For information about time range options, see "Scheduling Extended Access List Activation" section.
For TCP and UDP connections, you do not need an access list to allow returning traffic, because the ASA allows all returning traffic for established, bidirectional connections. For connectionless protocols such as ICMP, however, the security appliance establishes unidirectional sessions, so you either need access lists to allow ICMP in both directions (by applying access lists to the source and destination interfaces), or you need to enable the ICMP inspection engine. The ICMP inspection engine treats ICMP sessions as bidirectional connections.
You can apply only one access list of each type (extended and EtherType) to each direction of an interface. You can apply the same access lists on multiple interfaces. See Chapter 18, "Permitting or Denying Network Access," for more information about applying an access list to an interface.

Note ![]() If you change the access list configuration, and you do not want to wait for existing connections to time out before the new access list information is used, you can clear the connections using the clear local-host command.
If you change the access list configuration, and you do not want to wait for existing connections to time out before the new access list information is used, you can clear the connections using the clear local-host command.
Allowing Broadcast and Multicast Traffic through the Transparent Firewall
In routed firewall mode, broadcast and multicast traffic is blocked even if you allow it in an access list, including unsupported dynamic routing protocols and DHCP (unless you configure DHCP relay). Transparent firewall mode can allow any IP traffic through. This feature is especially useful in multiple context mode, which does not allow dynamic routing, for example.

Note ![]() Because these special types of traffic are connectionless, you need to apply an extended access list to both interfaces, so returning traffic is allowed through.
Because these special types of traffic are connectionless, you need to apply an extended access list to both interfaces, so returning traffic is allowed through.
Table 16-2 lists common traffic types that you can allow through the transparent firewall.
Adding an Extended ACE
When you enter the access-list command for a given access list name, the ACE is added to the end of the access list unless you specify the line number.
To add an ACE, enter the following command:
hostname(config)# access-list access_list_name [line line_number] [extended] {deny | permit} protocol source_address mask [operator port] dest_address mask [operator port | icmp_type] [inactive]

Tip ![]() Enter the access list name in upper case letters so the name is easy to see in the configuration. You might want to name the access list for the interface (for example, INSIDE), or for the purpose for which it is created (for example, NO_NAT or VPN).
Enter the access list name in upper case letters so the name is easy to see in the configuration. You might want to name the access list for the interface (for example, INSIDE), or for the purpose for which it is created (for example, NO_NAT or VPN).
Typically, you identify the ip keyword for the protocol, but other protocols are accepted. For a list of protocol names, see the "Protocols and Applications" section on page D-11.
Enter the host keyword before the IP address to specify a single address. In this case, do not enter a mask. Enter the any keyword instead of the address and mask to specify any address.
You can specify the source and destination ports only for the tcp or udp protocols. For a list of permitted keywords and well-known port assignments, see the "TCP and UDP Ports" section on page D-11. DNS, Discard, Echo, Ident, NTP, RPC, SUNRPC, and Talk each require one definition for TCP and one for UDP. TACACS+ requires one definition for port 49 on TCP.
Use an operator to match port numbers used by the source or destination. The permitted operators are as follows:
•![]() lt—less than
lt—less than
•![]() gt—greater than
gt—greater than
•![]() eq—equal to
eq—equal to
•![]() neq—not equal to
neq—not equal to
•![]() range—an inclusive range of values. When you use this operator, specify two port numbers, for example:
range—an inclusive range of values. When you use this operator, specify two port numbers, for example:
range 100 200
You can specify the ICMP type only for the icmp protocol. Because ICMP is a connectionless protocol, you either need access lists to allow ICMP in both directions (by applying access lists to the source and destination interfaces), or you need to enable the ICMP inspection engine (see the "Adding an ICMP Type Object Group" section). The ICMP inspection engine treats ICMP sessions as stateful connections. To control ping, specify echo-reply (0) (security appliance to host) or echo (8) (host to security appliance). See the "Adding an ICMP Type Object Group" section for a list of ICMP types.
When you specify a network mask, the method is different from the Cisco IOS software access-list command. The security appliance uses a network mask (for example, 255.255.255.0 for a Class C mask). The Cisco IOS mask uses wildcard bits (for example, 0.0.0.255).
To make an ACE inactive, use the inactive keyword. To reenable it, enter the entire ACE without the inactive keyword. This feature lets you keep a record of an inactive ACE in your configuration to make reenabling easier.
To remove an ACE, enter the no access-list command with the entire command syntax string as it appears in the configuration:
hostname(config)# no access-list access_list_name [line line_number] [extended] {deny | permit} protocol source_address mask [operator port] dest_address mask [operator port | icmp_type] [inactive]
If the entry that you are removing is the only entry in the access list, the entire access list is removed.
See the following examples:
The following access list allows all hosts (on the interface to which you apply the access list) to go through the security appliance:
hostname(config)# access-list ACL_IN extended permit ip any any
The following sample access list prevents hosts on 192.168.1.0/24 from accessing the 209.165.201.0/27 network. All other addresses are permitted.
hostname(config)# access-list ACL_IN extended deny tcp 192.168.1.0 255.255.255.0 209.165.201.0 255.255.255.224
hostname(config)# access-list ACL_IN extended permit ip any any
If you want to restrict access to only some hosts, then enter a limited permit ACE. By default, all other traffic is denied unless explicitly permitted.
hostname(config)# access-list ACL_IN extended permit ip 192.168.1.0 255.255.255.0 209.165.201.0 255.255.255.224
The following access list restricts all hosts (on the interface to which you apply the access list) from accessing a website at address 209.165.201.29. All other traffic is allowed.
hostname(config)# access-list ACL_IN extended deny tcp any host 209.165.201.29 eq www
hostname(config)# access-list ACL_IN extended permit ip any any
Adding an EtherType Access List
Transparent firewall mode only
This section describes how to add an EtherType access list, and includes the following sections:
•![]() EtherType Access List Overview
EtherType Access List Overview
EtherType Access List Overview
An EtherType access list is made up of one or more ACEs that specify an EtherType. This section includes the following topics:
•![]() Implicit Permit of IP and ARPs Only
Implicit Permit of IP and ARPs Only
•![]() Implicit and Explicit Deny ACE at the End of an Access List
Implicit and Explicit Deny ACE at the End of an Access List
•![]() Using Extended and EtherType Access Lists on the Same Interface
Using Extended and EtherType Access Lists on the Same Interface
Supported EtherTypes
An EtherType ACE controls any EtherType identified by a 16-bit hexadecimal number.
EtherType access lists support Ethernet V2 frames.
802.3-formatted frames are not handled by the access list because they use a length field as opposed to a type field.
BPDUs, which are handled by the access list, are the only exception: they are SNAP-encapsulated, and the security appliance is designed to specifically handle BPDUs.
The security appliance receives trunk port (Cisco proprietary) BPDUs. Trunk BPDUs have VLAN information inside the payload, so the security appliance modifies the payload with the outgoing VLAN if you allow BPDUs.
Implicit Permit of IP and ARPs Only
IPv4 traffic is allowed through the transparent firewall automatically from a higher security interface to a lower security interface, without an access list. ARPs are allowed through the transparent firewall in both directions without an access list. ARP traffic can be controlled by ARP inspection.
However, to allow any traffic with EtherTypes other than IPv4 and ARP, you need to apply an EtherType access list, even from a high security to a low security interface.
Because EtherTypes are connectionless, you need to apply the access list to both interfaces if you want traffic to pass in both directions.
Implicit and Explicit Deny ACE at the End of an Access List
For EtherType access lists, the implicit deny at the end of the access list does not affect IP traffic or ARPs; for example, if you allow EtherType 8037, the implicit deny at the end of the access list does not now block any IP traffic that you previously allowed with an extended access list (or implicitly allowed from a high security interface to a low security interface). However, if you explicitly deny all traffic with an EtherType ACE, then IP and ARP traffic is denied.
IPv6 Unsupported
EtherType ACEs do not allow IPv6 traffic, even if you specify the IPv6 EtherType.
Using Extended and EtherType Access Lists on the Same Interface
You can apply only one access list of each type (extended and EtherType) to each direction of an interface. You can also apply the same access lists on multiple interfaces.
Allowing MPLS
If you allow MPLS, ensure that Label Distribution Protocol and Tag Distribution Protocol TCP connections are established through the security appliance by configuring both MPLS routers connected to the security appliance to use the IP address on the security appliance interface as the router-id for LDP or TDP sessions. (LDP and TDP allow MPLS routers to negotiate the labels (addresses) used to forward packets.)
On Cisco IOS routers, enter the appropriate command for your protocol, LDP or TDP. The interface is the interface connected to the security appliance.
hostname(config)# mpls ldp router-id interface force
Or
hostname(config)# tag-switching tdp router-id interface force
Adding an EtherType ACE
To add an EtherType ACE, enter the following command:
hostname(config)# access-list access_list_name ethertype {permit | deny} {ipx | bpdu |
mpls-unicast | mpls-multicast | any | hex_number}
The hex_number is any EtherType that can be identified by a 16-bit hexadecimal number greater than or equal to 0x600. See RFC 1700, "Assigned Numbers," at http://www.ietf.org/rfc/rfc1700.txt for a list of EtherTypes.
To remove an ACE, enter the no access-list command with the entire command syntax string as it appears in the configuration:
hostname(config)# no access-list access_list_name [line line_number] [extended] {deny | permit} protocol source_address mask [operator port] dest_address mask [operator port | icmp_type] [inactive]
To remove an EtherType ACE, enter the no access-list command with the entire command syntax string as it appears in the configuration:
ehostname(config)# no access-list access_list_name ethertype {permit | deny} {ipx | bpdu |
mpls-unicast | mpls-multicast | any | hex_number}

Note ![]() If an EtherType access list is configured to deny all, all ethernet frames are discarded. Only physical protocol traffic, such as auto-negotiation, is still allowed.
If an EtherType access list is configured to deny all, all ethernet frames are discarded. Only physical protocol traffic, such as auto-negotiation, is still allowed.
When you enter the access-list command for a given access list name, the ACE is added to the end of the access list.

Tip ![]() Enter the access_list_name in upper case letters so the name is easy to see in the configuration. You might want to name the access list for the interface (for example, INSIDE), or for the purpose (for example, MPLS or IPX).
Enter the access_list_name in upper case letters so the name is easy to see in the configuration. You might want to name the access list for the interface (for example, INSIDE), or for the purpose (for example, MPLS or IPX).
For example, the following sample access list allows common EtherTypes originating on the inside interface:
hostname(config)# access-list ETHER ethertype permit ipx
hostname(config)# access-list ETHER ethertype permit bpdu
hostname(config)# access-list ETHER ethertype permit mpls-unicast
hostname(config)# access-group ETHER in interface inside
The following access list allows some EtherTypes through the security appliance, but denies IPX:
hostname(config)# access-list ETHER ethertype deny ipx
hostname(config)# access-list ETHER ethertype permit 0x1234
hostname(config)# access-list ETHER ethertype permit bpdu
hostname(config)# access-list ETHER ethertype permit mpls-unicast
hostname(config)# access-group ETHER in interface inside
hostname(config)# access-group ETHER in interface outside
The following access list denies traffic with EtherType 0x1256, but allows all others on both interfaces:
hostname(config)# access-list nonIP ethertype deny 1256
hostname(config)# access-list nonIP ethertype permit any
hostname(config)# access-group ETHER in interface inside
hostname(config)# access-group ETHER in interface outside
Adding a Standard Access List
Single context mode only
Standard access lists identify the destination IP addresses of OSPF routes, and can be used in a route map for OSPF redistribution. Standard access lists cannot be applied to interfaces to control traffic.
The following command adds a standard ACE. To add another ACE at the end of the access list, enter another access-list command specifying the same access list name. Apply the access list using the "Defining Route Maps" section on page 9-7.
To add an ACE, enter the following command:
hostname(config)# access-list access_list_name standard {deny | permit} {any | ip_address
mask}
To remove an ACE, enter the no access-list command with the entire command syntax string as it appears in the configuration:
hostname(config)# no access-list access_list_name standard {deny | permit} {any |
ip_address mask}
The following sample access list identifies routes to 192.168.1.0/24:
hostname(config)# access-list OSPF standard permit 192.168.1.0 255.255.255.0
Adding a Webtype Access List
To add an access list to the configuration that supports filtering for WebVPN, enter the following command:
hostname(config)# access-list access_list_name webtype {deny | permit} url [url_string | any]
To remove a Webtype access list, enter the no access-list command with the entire syntax string as it appears in the configuration:
hostname(config)# access-list access_list_name webtype {deny | permit} url [url_string | any]
For information about logging options that you can add to the end of the ACE, see the "Logging Access List Activity" section.
Simplifying Access Lists with Object Grouping
This section describes how to use object grouping to simplify access list creation and maintenance.
This section includes the following topics:
•![]() Using Object Groups with an Access List
Using Object Groups with an Access List
How Object Grouping Works
By grouping like-objects together, you can use the object group in an ACE instead of having to enter an ACE for each object separately. You can create the following types of object groups:
•![]() Protocol
Protocol
•![]() Network
Network
•![]() Service
Service
•![]() ICMP type
ICMP type
For example, consider the following three object groups:
•![]() MyServices—Includes the TCP and UDP port numbers of the service requests that are allowed access to the internal network
MyServices—Includes the TCP and UDP port numbers of the service requests that are allowed access to the internal network
•![]() TrustedHosts—Includes the host and network addresses allowed access to the greatest range of services and servers
TrustedHosts—Includes the host and network addresses allowed access to the greatest range of services and servers
•![]() PublicServers—Includes the host addresses of servers to which the greatest access is provided
PublicServers—Includes the host addresses of servers to which the greatest access is provided
After creating these groups, you could use a single ACE to allow trusted hosts to make specific service requests to a group of public servers.
You can also nest object groups in other object groups.

Note ![]() The ACE system limit applies to expanded access lists. If you use object groups in ACEs, the number of actual ACEs that you enter is fewer, but the number of expanded ACEs is the same as without object groups. In many cases, object groups create more ACEs than if you added them manually, because creating ACEs manually leads you to summarize addresses more than an object group does. To view the number of expanded ACEs in an access list, enter the show access-list access_list_name command.
The ACE system limit applies to expanded access lists. If you use object groups in ACEs, the number of actual ACEs that you enter is fewer, but the number of expanded ACEs is the same as without object groups. In many cases, object groups create more ACEs than if you added them manually, because creating ACEs manually leads you to summarize addresses more than an object group does. To view the number of expanded ACEs in an access list, enter the show access-list access_list_name command.
Adding Object Groups
This section describes how to add object groups.
This section includes the following topics:
•![]() Adding a Protocol Object Group
Adding a Protocol Object Group
•![]() Adding a Network Object Group
Adding a Network Object Group
•![]() Adding a Service Object Group
Adding a Service Object Group
•![]() Adding an ICMP Type Object Group
Adding an ICMP Type Object Group
Adding a Protocol Object Group
To add or change a protocol object group, follow these steps. After you add the group, you can add more objects as required by following this procedure again for the same group name and specifying additional objects. You do not need to reenter existing objects; the commands you already set remain in place unless you remove them with the no form of the command.
To add a protocol group, follow these steps:
Step 1 ![]() To add a protocol group, enter the following command:
To add a protocol group, enter the following command:
hostname(config)# object-group protocol grp_id
The grp_id is a text string up to 64 characters in length.
The prompt changes to protocol configuration mode.
Step 2 ![]() (Optional) To add a description, enter the following command:
(Optional) To add a description, enter the following command:
hostname(config-protocol)# description text
The description can be up to 200 characters.
Step 3 ![]() To define the protocols in the group, enter the following command for each protocol:
To define the protocols in the group, enter the following command for each protocol:
hostname(config-protocol)# protocol-object protocol
The protocol is the numeric identifier of the specific IP protocol (1 to 254) or a keyword identifier (for example, icmp, tcp, or udp). To include all IP protocols, use the keyword ip. For a list of protocols you can specify, see the "Protocols and Applications" section on page D-11.
For example, to create a protocol group for TCP, UDP, and ICMP, enter the following commands:
hostname(config)# object-group protocol tcp_udp_icmp
hostname(config-protocol)# protocol-object tcp
hostname(config-protocol)# protocol-object udp
hostname(config-protocol)# protocol-object icmp
Adding a Network Object Group
To add or change a network object group, follow these steps. After you add the group, you can add more objects as required by following this procedure again for the same group name and specifying additional objects. You do not need to reenter existing objects; the commands you already set remain in place unless you remove them with the no form of the command.

Note ![]() A network object group supports IPv4 and IPv6 addresses, depending on the type of access list. For more information about IPv6 access lists, see "Configuring IPv6 Access Lists" section on page 12-6.
A network object group supports IPv4 and IPv6 addresses, depending on the type of access list. For more information about IPv6 access lists, see "Configuring IPv6 Access Lists" section on page 12-6.
To add a network group, follow these steps:
Step 1 ![]() To add a network group, enter the following command:
To add a network group, enter the following command:
hostname(config)# object-group network grp_id
The grp_id is a text string up to 64 characters in length.
The prompt changes to network configuration mode.
Step 2 ![]() (Optional) To add a description, enter the following command:
(Optional) To add a description, enter the following command:
hostname(config-network)# description text
The description can be up to 200 characters.
Step 3 ![]() To define the networks in the group, enter the following command for each network or address:
To define the networks in the group, enter the following command for each network or address:
hostname(config-network)# network-object {host ip_address | ip_address mask}
For example, to create network group that includes the IP addresses of three administrators, enter the following commands:
hostname(config)# object-group network admins
hostname(config-network)# description Administrator Addresses
hostname(config-network)# network-object host 10.1.1.4
hostname(config-network)# network-object host 10.1.1.78
hostname(config-network)# network-object host 10.1.1.34
Adding a Service Object Group
To add or change a service object group, follow these steps. After you add the group, you can add more objects as required by following this procedure again for the same group name and specifying additional objects. You do not need to reenter existing objects; the commands you already set remain in place unless you remove them with the no form of the command.
To add a service group, follow these steps:
Step 1 ![]() To add a service group, enter the following command:
To add a service group, enter the following command:
hostname(config)# object-group service grp_id {tcp | udp | tcp-udp}
The grp_id is a text string up to 64 characters in length.
Specify the protocol for the services (ports) you want to add, either tcp, udp, or tcp-udp keywords. Enter tcp-udp keyword if your service uses both TCP and UDP with the same port number, for example, DNS (port 53).
The prompt changes to service configuration mode.
Step 2 ![]() (Optional) To add a description, enter the following command:
(Optional) To add a description, enter the following command:
hostname(config-service)# description text
The description can be up to 200 characters.
Step 3 ![]() To define the ports in the group, enter the following command for each port or range of ports:
To define the ports in the group, enter the following command for each port or range of ports:
hostname(config-service)# port-object {eq port | range begin_port end_port}
For a list of permitted keywords and well-known port assignments, see the "Protocols and Applications" section on page D-11.
For example, to create service groups that include DNS (TCP/UDP), LDAP (TCP), and RADIUS (UDP), enter the following commands:
hostname(config)# object-group service services1 tcp-udp
hostname(config-service)# description DNS Group
hostname(config-service)# port-object eq domain
hostname(config-service)# object-group service services2 udp
hostname(config-service)# description RADIUS Group
hostname(config-service)# port-object eq radius
hostname(config-service)# port-object eq radius-acct
hostname(config-service)# object-group service services3 tcp
hostname(config-service)# description LDAP Group
hostname(config-service)# port-object eq ldap
Adding an ICMP Type Object Group
To add or change an ICMP type object group, follow these steps. After you add the group, you can add more objects as required by following this procedure again for the same group name and specifying additional objects. You do not need to reenter existing objects; the commands you already set remain in place unless you remove them with the no form of the command.
To add an ICMP type group, follow these steps:
Step 1 ![]() To add an ICMP type group, enter the following command:
To add an ICMP type group, enter the following command:
hostname(config)# object-group icmp-type grp_id
The grp_id is a text string up to 64 characters in length.
The prompt changes to ICMP type configuration mode.
Step 2 ![]() (Optional) To add a description, enter the following command:
(Optional) To add a description, enter the following command:
hostname(config-icmp-type)# description text
The description can be up to 200 characters.
Step 3 ![]() To define the ICMP types in the group, enter the following command for each type:
To define the ICMP types in the group, enter the following command for each type:
hostname(config-icmp-type)# icmp-object icmp_type
See the "ICMP Types" section on page D-15 for a list of ICMP types.
For example, to create an ICMP type group that includes echo-reply and echo (for controlling ping), enter the following commands:
hostname(config)# object-group icmp-type ping
hostname(config-service)# description Ping Group
hostname(config-icmp-type)# icmp-object echo
hostname(config-icmp-type)# icmp-object echo-reply
Nesting Object Groups
To nest an object group within another object group of the same type, first create the group that you want to nest according to the "Adding Object Groups" section. Then follow these steps:
Step 1 ![]() To add or edit an object group under which you want to nest another object group, enter the following command:
To add or edit an object group under which you want to nest another object group, enter the following command:
hostname(config)# object-group {{protocol | network | icmp-type} grp_id | service grp_id
{tcp | udp | tcp-udp}}
Step 2 ![]() To add the specified group under the object group you specified in Step 1, enter the following command:
To add the specified group under the object group you specified in Step 1, enter the following command:
hostname(config-group_type)# group-object grp_id
The nested group must be of the same type.
You can mix and match nested group objects and regular objects within an object group.
For example, you create network object groups for privileged users from various departments:
hostname(config)# object-group network eng
hostname(config-network)# network-object host 10.1.1.5
hostname(config-network)# network-object host 10.1.1.9
hostname(config-network)# network-object host 10.1.1.89
hostname(config-network)# object-group network hr
hostname(config-network)# network-object host 10.1.2.8
hostname(config-network)# network-object host 10.1.2.12
hostname(config-network)# object-group network finance
hostname(config-network)# network-object host 10.1.4.89
hostname(config-network)# network-object host 10.1.4.100
You then nest all three groups together as follows:
hostname(config)# object-group network admin
hostname(config-network)# group-object eng
hostname(config-network)# group-object hr
hostname(config-network)# group-object finance
You only need to specify the admin object group in your ACE as follows:
hostname(config)# access-list ACL_IN extended permit ip object-group admin host 209.165.201.29
Using Object Groups with an Access List
To use object groups in an access list, replace the normal protocol (protocol), network (source_address mask, etc.), service (operator port), or ICMP type (icmp_type) parameter with object-group grp_id parameter.
For example, to use object groups for all available parameters in the access-list {tcp | udp} command, enter the following command:
hostname(config)# access-list access_list_name [line line_number] [extended] {deny | permit} {tcp | udp} object-group nw_grp_id [object-group svc_grp_id] object-group nw_grp_id [object-group svc_grp_id] [log [[level] [interval secs] | disable | default]] [inactive | time-range time_range_name]
You do not have to use object groups for all parameters; for example, you can use an object group for the source address, but identify the destination address with an address and mask.
The following normal access list that does not use object groups restricts several hosts on the inside network from accessing several web servers. All other traffic is allowed.
hostname(config)# access-list ACL_IN extended deny tcp host 10.1.1.4 host 209.165.201.29 eq www
hostname(config)# access-list ACL_IN extended deny tcp host 10.1.1.78 host 209.165.201.29 eq www
hostname(config)# access-list ACL_IN extended deny tcp host 10.1.1.89 host 209.165.201.29 eq www
hostname(config)# access-list ACL_IN extended deny tcp host 10.1.1.4 host 209.165.201.16 eq www
hostname(config)# access-list ACL_IN extended deny tcp host 10.1.1.78 host 209.165.201.16 eq www
hostname(config)# access-list ACL_IN extended deny tcp host 10.1.1.89 host 209.165.201.16 eq www
hostname(config)# access-list ACL_IN extended deny tcp host 10.1.1.4 host 209.165.201.78 eq www
hostname(config)# access-list ACL_IN extended deny tcp host 10.1.1.78 host 209.165.201.78 eq www
hostname(config)# access-list ACL_IN extended deny tcp host 10.1.1.89 host 209.165.201.78 eq www
hostname(config)# access-list ACL_IN extended permit ip any any
hostname(config)# access-group ACL_IN in interface inside
If you make two network object groups, one for the inside hosts, and one for the web servers, then the configuration can be simplified and can be easily modified to add more hosts:
hostname(config)# object-group network denied
hostname(config-network)# network-object host 10.1.1.4
hostname(config-network)# network-object host 10.1.1.78
hostname(config-network)# network-object host 10.1.1.89
hostname(config-network)# object-group network web
hostname(config-network)# network-object host 209.165.201.29
hostname(config-network)# network-object host 209.165.201.16
hostname(config-network)# network-object host 209.165.201.78
hostname(config-network)# access-list ACL_IN extended deny tcp object-group denied object-group web eq www
hostname(config)# access-list ACL_IN extended permit ip any any
hostname(config)# access-group ACL_IN in interface inside
Displaying Object Groups
To display a list of the currently configured object groups, enter the following command:
hostname(config)# show object-group [protocol | network | service | icmp-type | id grp_id]
If you enter the command without any parameters, the system displays all configured object groups.
The following is sample output from the show object-group command:
hostname# show object-group
object-group network ftp_servers
description: This is a group of FTP servers
network-object host 209.165.201.3
network-object host 209.165.201.4
object-group network TrustedHosts
network-object host 209.165.201.1
network-object 192.168.1.0 255.255.255.0
group-object ftp_servers
Removing Object Groups
To remove an object group, enter one of the following commands.

Note ![]() You cannot remove an object group or make an object group empty if it is used in an access list.
You cannot remove an object group or make an object group empty if it is used in an access list.
•![]() To remove a specific object group, enter the following command:
To remove a specific object group, enter the following command:
hostname(config)# no object-group grp_id
•![]() To remove all object groups of the specified type, enter the following command:
To remove all object groups of the specified type, enter the following command:
hostname(config)# clear object-group [protocol | network | services | icmp-type]
If you do not enter a type, all object groups are removed.
Adding Remarks to Access Lists
You can include remarks about entries in any access list, including extended, EtherType, and standard access lists. The remarks make the access list easier to understand.
To add a remark after the last access-list command you entered, enter the following command:
hostname(config)# access-list access_list_name remark text
If you enter the remark before any access-list command, then the remark is the first line in the access list.
If you delete an access list using the no access-list access_list_name command, then all the remarks are also removed.
The text can be up to 100 characters in length. You can enter leading spaces at the beginning of the text. Trailing spaces are ignored.
For example, you can add remarks before each ACE, and the remark appears in the access list in this location. Entering a dash (-) at the beginning of the remark helps set it apart from ACEs.
hostname(config)# access-list OUT remark - this is the inside admin address
hostname(config)# access-list OUT extended permit ip host 209.168.200.3 any
hostname(config)# access-list OUT remark - this is the hr admin address
hostname(config)# access-list OUT extended permit ip host 209.168.200.4 any
Scheduling Extended Access List Activation
You can schedule each ACE to be activated at specific times of the day and week by applying a time range to the ACE. This section includes the following topics:
•![]() Applying the Time Range to an ACE
Applying the Time Range to an ACE
Adding a Time Range
To add a time range to implement a time-based access list, perform the following steps:
Step 1 ![]() Identify the time-range name by entering the following command:
Identify the time-range name by entering the following command:
hostname(config)# time-range name
Step 2 ![]() Specify the time range as either a recurring time range or an absolute time range.
Specify the time range as either a recurring time range or an absolute time range.

Note ![]() Users could experience a delay of approximately 80 to 100 seconds after the specified end time for the ACL to become inactive. For example, if the specified end time is 3:50, because the end time is inclusive, the command is picked up anywhere between 3:51:00 and 3:51:59. After the command is picked up, the security appliance finishes any currently running task and then services the command to deactivate the ACL.
Users could experience a delay of approximately 80 to 100 seconds after the specified end time for the ACL to become inactive. For example, if the specified end time is 3:50, because the end time is inclusive, the command is picked up anywhere between 3:51:00 and 3:51:59. After the command is picked up, the security appliance finishes any currently running task and then services the command to deactivate the ACL.
Multiple periodic entries are allowed per time-range command. If a time-range command has both absolute and periodic values specified, then the periodic commands are evaluated only after the absolute start time is reached, and are not further evaluated after the absolute end time is reached.
•![]() Recurring time range:
Recurring time range:
hostname(config-time-range)# periodic days-of-the-week time to [days-of-the-week] time
You can specify the following values for days-of-the-week:
–![]() monday, tuesday, wednesday, thursday, friday, saturday, and sunday.
monday, tuesday, wednesday, thursday, friday, saturday, and sunday.
–![]() daily
daily
–![]() weekdays
weekdays
–![]() weekend
weekend
The time is in the format hh:mm. For example, 8:00 is 8:00 a.m. and 20:00 is 8:00 p.m.
•![]() Absolute time range:
Absolute time range:
hostname(config-time-range)# absolute start time date [end time date]
The time is in the format hh:mm. For example, 8:00 is 8:00 a.m. and 20:00 is 8:00 p.m.
The date is in the format day month year; for example, 1 january 2006.
The following is an example of an absolute time range beginning at 8:00 a.m. on January 1, 2006. Because no end time and date are specified, the time range is in effect indefinitely.
hostname(config)# time-range for2006
hostname(config-time-range)# absolute start 8:00 1 january 2006
The following is an example of a weekly periodic time range from 8:00 a.m. to 6:00 p.m on weekdays.:
hostname(config)# time-range workinghours
hostname(config-time-range)# periodic weekdays 8:00 to 18:00
Applying the Time Range to an ACE
To apply the time range to an ACE, use the following command:
hostname(config)# access-list access_list_name [extended] {deny | permit}...[time-range name]
See the "Adding an Extended Access List" section for complete access-list command syntax.

Note ![]() If you also enable logging for the ACE, use the log keyword before the time-range keyword. If you disable the ACE using the inactive keyword, use the inactive keyword as the last keyword.
If you also enable logging for the ACE, use the log keyword before the time-range keyword. If you disable the ACE using the inactive keyword, use the inactive keyword as the last keyword.
The following example binds an access list named "Sales" to a time range named "New_York_Minute."
hostname(config)# access-list Sales line 1 extended deny tcp host 209.165.200.225 host
209.165.201.1 time-range New_York_Minute
Logging Access List Activity
This section describes how to configure access list logging for extended access lists and Webtype access lists.
This section includes the following topics:
•![]() Configuring Logging for an Access Control Entry
Configuring Logging for an Access Control Entry
Access List Logging Overview
By default, when traffic is denied by an extended ACE or a Webtype ACE, the security appliance generates system message 106023 for each denied packet, in the following form:
%ASA|PIX-4-106023: Deny protocol src [interface_name:source_address/source_port] dst
interface_name:dest_address/dest_port [type {string}, code {code}] by access_group acl_id
If the security appliance is attacked, the number of system messages for denied packets can be very large. We recommend that you instead enable logging using system message 106100, which provides statistics for each ACE and lets you limit the number of system messages produced. Alternatively, you can disable all logging.

Note ![]() Only ACEs in the access list generate logging messages; the implicit deny at the end of the access list does not generate a message. If you want all denied traffic to generate messages, add the implicit ACE manually to the end of the access list, as follows.
Only ACEs in the access list generate logging messages; the implicit deny at the end of the access list does not generate a message. If you want all denied traffic to generate messages, add the implicit ACE manually to the end of the access list, as follows.
hostname(config)# access-list TEST deny ip any any log
The log options at the end of the extended access-list command lets you to set the following behavior:
•![]() Enable message 106100 instead of message 106023
Enable message 106100 instead of message 106023
•![]() Disable all logging
Disable all logging
•![]() Return to the default logging using message 106023
Return to the default logging using message 106023
System message 106100 is in the following form:
%ASA|PIX-n-106100: access-list acl_id {permitted | denied} protocol
interface_name/source_address(source_port) -> interface_name/dest_address(dest_port)
hit-cnt number ({first hit | number-second interval})
When you enable logging for message 106100, if a packet matches an ACE, the security appliance creates a flow entry to track the number of packets received within a specific interval. The security appliance generates a system message at the first hit and at the end of each interval, identifying the total number of hits during the interval. At the end of each interval, the security appliance resets the hit count to 0. If no packets match the ACE during an interval, the security appliance deletes the flow entry.
A flow is defined by the source and destination IP addresses, protocols, and ports. Because the source port might differ for a new connection between the same two hosts, you might not see the same flow increment because a new flow was created for the connection. See the "Managing Deny Flows" section to limit the number of logging flows.
Permitted packets that belong to established connections do not need to be checked against access lists; only the initial packet is logged and included in the hit count. For connectionless protocols, such as ICMP, all packets are logged even if they are permitted, and all denied packets are logged.
See the Cisco Security Appliance Logging Configuration and System Log Messages for detailed information about this system message.
Configuring Logging for an Access Control Entry
To configure logging for an ACE, see the following information about the log option:
hostname(config)# access-list access_list_name [extended] {deny | permit}...[log [[level] [interval secs] | disable | default]]
See the "Adding an Extended Access List" section and "Adding a Webtype Access List" section for complete access-list command syntax.
If you enter the log option without any arguments, you enable system log message 106100 at the default level (6) and for the default interval (300 seconds). See the following options:
•![]() level—A severity level between 0 and 7. The default is 6.
level—A severity level between 0 and 7. The default is 6.
•![]() interval secs—The time interval in seconds between system messages, from 1 to 600. The default is 300. This value is also used as the timeout value for deleting an inactive flow.
interval secs—The time interval in seconds between system messages, from 1 to 600. The default is 300. This value is also used as the timeout value for deleting an inactive flow.
•![]() disable—Disables all access list logging.
disable—Disables all access list logging.
•![]() default—Enables logging to message 106023. This setting is the same as having no log option.
default—Enables logging to message 106023. This setting is the same as having no log option.
For example, you configure the following access list:
hostname(config)# access-list outside-acl permit ip host 1.1.1.1 any log 7 interval 600
hostname(config)# access-list outside-acl permit ip host 2.2.2.2 any
hostname(config)# access-list outside-acl deny ip any any log 2
hostname(config)# access-group outside-acl in interface outside
When a packet is permitted by the first ACE of outside-acl, the security appliance generates the following system message:
%ASA|PIX-7-106100: access-list outside-acl permitted tcp outside/1.1.1.1(12345) -> inside/192.168.1.1(1357) hit-cnt 1 (first hit)
Although 20 additional packets for this connection arrive on the outside interface, the traffic does not have to be checked against the access list, and the hit count does not increase.
If one more connection by the same host is initiated within the specified 10 minute interval (and the source and destination ports remain the same), then the hit count is incremented by 1 and the following message is displayed at the end of the 10 minute interval:
%ASA|PIX-7-106100: access-list outside-acl permitted tcp outside/1.1.1.1(12345)-> inside/192.168.1.1(1357) hit-cnt 2 (600-second interval)
When a packet is denied by the third ACE, the security appliance generates the following system message:
%ASA|PIX-2-106100: access-list outside-acl denied ip outside/3.3.3.3(12345) -> inside/192.168.1.1(1357) hit-cnt 1 (first hit)
20 additional attempts within a 5 minute interval (the default) result in the following message at the end of 5 minutes:
%ASA|PIX-2-106100: access-list outside-acl denied ip outside/3.3.3.3(12345) -> inside/192.168.1.1(1357) hit-cnt 21 (300-second interval)
Managing Deny Flows
When you enable logging for message 106100, if a packet matches an ACE, the security appliance creates a flow entry to track the number of packets received within a specific interval. The security appliance has a maximum of 32 K logging flows for ACEs. A large number of flows can exist concurrently at any point of time. To prevent unlimited consumption of memory and CPU resources, the security appliance places a limit on the number of concurrent deny flows; the limit is placed only on deny flows (and not permit flows) because they can indicate an attack. When the limit is reached, the security appliance does not create a new deny flow for logging until the existing flows expire.
For example, if someone initiates a DoS attack, the security appliance can create a large number of deny flows in a short period of time. Restricting the number of deny flows prevents unlimited consumption of memory and CPU resources.
When you reach the maximum number of deny flows, the security appliance issues system message 106100:
%ASA|PIX-1-106101: The number of ACL log deny-flows has reached limit (number).
To configure the maximum number of deny flows and to set the interval between deny flow alert messages (106101), enter the following commands:
•![]() To set the maximum number of deny flows permitted per context before the security appliance stops logging, enter the following command:
To set the maximum number of deny flows permitted per context before the security appliance stops logging, enter the following command:
hostname(config)# access-list deny-flow-max number
The number is between 1 and 4096. 4096 is the default.
•![]() To set the amount of time between system messages (number 106101) that identify that the maximum number of deny flows was reached, enter the following command:
To set the amount of time between system messages (number 106101) that identify that the maximum number of deny flows was reached, enter the following command:
hostname(config)# access-list alert-interval secs
The seconds are between 1 and 3600. 300 is the default.
 Feedback
Feedback