- Index
- Preface
- Overview
- Using the Command-Line Interface
- Assigning the Switch IP Address and Default Gateway
- Configuring Cisco IOS Configuration Engine
- Administering the Switch
- Configuring Web-Based Authentication
- Clustering Switches
- Managing Switch Stacks
- Configuring SDM Templates
- Configuring Switch-Based Authentication
- Configuring IEEE 802.1x Port-Based Authentication
- Configuring Interface Characteristics
- Configuring VLANs
- Configuring VTP
- Configuring Voice VLAN
- Configuring STP
- Configuring MSTP
- Configuring Optional Spanning-Tree Features
- Configuring Flex Links and the MAC Address-Table Move Update Feature
- Configuring DHCP Features and IP Source Guard
- Configuring Dynamic ARP Inspection
- Configuring IGMP Snooping and MVR
- Configuring Port-Based Traffic Control
- Configuring UDLD
- Configuring CDP
- Configuring LLDP, LLDP-MED, and Wired Location Service
- Configuring SPAN and RSPAN
- Configuring RMON
- Configuring System Message Logging
- Configuring SNMP
- Configuring Cisco IOS IP SLAs Operations
- Configuring Network Security with ACLs
- Configuring QoS
- Configuring Static IP Unicast Routing
- Configuring IPv6 Host
- Configuring IPv6 MLD Snooping
- Configuring EtherChannels and Link-State Tracking
- Troubleshooting
- Configuring Online Diagnostics
- Working with the Cisco IOS File System, Configuration Files, and Software Images
- Supported MIBs
- Unsupported Commands in Cisco IOS Release 12.2(55)SE
- Recommendations for Upgrading a Catalyst 2950 Switch to a Catalyst 2960 Switch
- Understanding QoS
- Configuring Auto-QoS
- Displaying Auto-QoS Information
- Configuring Standard QoS
- Default Standard QoS Configuration
- Standard QoS Configuration Guidelines
- Enabling QoS Globally
- Configuring Classification Using Port Trust States
- Configuring a QoS Policy
- Configuring DSCP Maps
- Configuring Ingress Queue Characteristics
- Configuring Egress Queue Characteristics
- Configuration Guidelines
- Allocating Buffer Space to and Setting WTD Thresholds for an Egress Queue-Set
- Mapping DSCP or CoS Values to an Egress Queue and to a Threshold ID
- Configuring SRR Shaped Weights on Egress Queues
- Configuring SRR Shared Weights on Egress Queues
- Configuring the Egress Expedite Queue
- Limiting the Bandwidth on an Egress Interface
Configuring QoS
This chapter describes how to configure quality of service (QoS) by using automatic QoS (auto-QoS) commands or by using standard QoS commands on the Catalyst 2960 and 2960-S switches. With QoS, you can provide preferential treatment to certain types of traffic at the expense of others. Without QoS, the switch offers best-effort service to each packet, regardless of the packet contents or size. It sends the packets without any assurance of reliability, delay bounds, or throughput. Unless otherwise noted, the term switch refers to a standalone switch and a switch stack.

Note![]() Stacking is supported only on Catalyst 2960-S switches running the LAN base image.
Stacking is supported only on Catalyst 2960-S switches running the LAN base image.

Note![]() Catalyst 2960-S switches do not support ingress queueing.
Catalyst 2960-S switches do not support ingress queueing.
You can configure QoS only on physical ports. You configure the QoS settings, such as classification, queueing, and scheduling, and apply the policy map to a port.

Note![]() For complete syntax and usage information for the commands used in this chapter, see the command reference for this release.
For complete syntax and usage information for the commands used in this chapter, see the command reference for this release.
This chapter consists of these sections:

Note![]() To use auto-QoS, the switch must be running the LAN Base image.
To use auto-QoS, the switch must be running the LAN Base image.
The switch supports some of the modular QoS CLI (MQC) commands. For more information about the MQC commands, see the “Modular Quality of Service Command-Line Interface Overview”:
http://www.cisco.com/en/US/docs/ios/12_2/qos/configuration/guide/qcfmcli2.html
Understanding QoS
Typically, networks operate on a best-effort delivery basis, which means that all traffic has equal priority and an equal chance of being delivered in a timely manner. When congestion occurs, all traffic has an equal chance of being dropped.
When you configure the QoS feature, you can select specific network traffic, prioritize it according to its relative importance, and use congestion-management and congestion-avoidance techniques to provide preferential treatment. Implementing QoS in your network makes network performance more predictable and bandwidth utilization more effective.
The QoS implementation is based on the Differentiated Services (Diff-Serv) architecture, an emerging standard from the Internet Engineering Task Force (IETF). This architecture specifies that each packet is classified upon entry into the network.
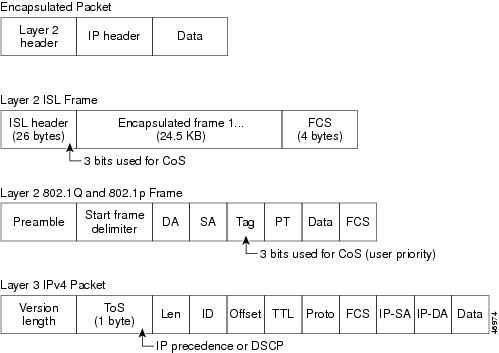
The classification is carried in the IP packet header, using 6 bits from the deprecated IP type of service (ToS) field to carry the classification ( class) information. Classification can also be carried in the Layer 2 frame. These special bits in the Layer 2 frame or a Layer 3 packet are described here and shown in Figure 1-1:
Layer 2 Inter-Switch Link (ISL) frame headers have a 1-byte User field that carries an IEEE 802.1p class of service (CoS) value in the three least-significant bits. On ports configured as Layer 2 ISL trunks, all traffic is in ISL frames.
Layer 2 IEEE 802.1Q frame headers have a 2-byte Tag Control Information field that carries the CoS value in the three most-significant bits, which are called the User Priority bits. On ports configured as Layer 2 IEEE 802.1Q trunks, all traffic is in IEEE 802.1Q frames except for traffic in the native VLAN.
Other frame types cannot carry Layer 2 CoS values.
Layer 2 CoS values range from 0 for low priority to 7 for high priority.

Note![]() To use DSCP, the switch must be running the LAN Base image.
To use DSCP, the switch must be running the LAN Base image.
Layer 3 IP packets can carry either an IP precedence value or a Differentiated Services Code Point (DSCP) value. QoS supports the use of either value because DSCP values are backward-compatible with IP precedence values.
IP precedence values range from 0 to 7.
DSCP values range from 0 to 63.

Note![]() IPv6 QoS is not supported in this release.
IPv6 QoS is not supported in this release.
Figure 1-1 QoS Classification Layers in Frames and Packets
All switches and routers that access the Internet rely on the class information to provide the same forwarding treatment to packets with the same class information and different treatment to packets with different class information. The class information in the packet can be assigned by end hosts or by switches or routers along the way, based on a configured policy, detailed examination of the packet, or both. Detailed examination of the packet is expected to happen closer to the edge of the network so that the core switches and routers are not overloaded with this task.
Switches and routers along the path can use the class information to limit the amount of resources allocated per traffic class. The behavior of an individual device when handling traffic in the DiffServ architecture is called per-hop behavior. If all devices along a path provide a consistent per-hop behavior, you can construct an end-to-end QoS solution.
Implementing QoS in your network can be a simple or complex task and depends on the QoS features offered by your internetworking devices, the traffic types and patterns in your network, and the granularity of control that you need over incoming and outgoing traffic.
Basic QoS Model
To implement QoS, the switch must distinguish packets or flow from one another (classify), assign a label to indicate the given quality of service as the packets move through the switch, make the packets comply with the configured resource usage limits (police and mark), and provide different treatment (queue and schedule) in all situations where resource contention exists. The switch also needs to ensure that traffic sent from it meets a specific traffic profile (shape).

Note![]() Catalyst 2960-S switches do not support ingress queueing.
Catalyst 2960-S switches do not support ingress queueing.
Figure 1-2 shows the basic QoS model. Actions at the ingress port include classifying traffic, policing, marking, queueing, and scheduling:
- Classifying a distinct path for a packet by associating it with a QoS label. The switch maps the CoS or DSCP in the packet to a QoS label to distinguish one kind of traffic from another. The QoS label that is generated identifies all future QoS actions to be performed on this packet. For more information, see the “Classification” section.
- Policing determines whether a packet is in or out of profile by comparing the rate of the incoming traffic to the configured policer. The policer limits the bandwidth consumed by a flow of traffic. The result is passed to the marker. For more information, see the “Policing and Marking” section.
- Marking evaluates the policer and configuration information for the action to be taken when a packet is out of profile and determines what to do with the packet (pass through a packet without modification, mark down the QoS label in the packet, or drop the packet). For more information, see the “Policing and Marking” section.
- Queueing evaluates the QoS label and the corresponding DSCP or CoS value to select into which of the two ingress queues to place a packet. Queueing is enhanced with the weighted tail-drop (WTD) algorithm, a congestion-avoidance mechanism. If the threshold is exceeded, the packet is dropped. For more information, see the “Queueing and Scheduling Overview” section.
- Scheduling services the queues based on their configured shaped round robin (SRR) weights. One of the ingress queues is the priority queue, and SRR services it for its configured share before servicing the other queue. For more information, see the “SRR Shaping and Sharing” section.
Actions at the egress port include queueing and scheduling:
- Queueing evaluates the QoS packet label and the corresponding DSCP or CoS value before selecting which of the four egress queues to use. Because congestion can occur when multiple ingress ports simultaneously send data to an egress port, WTD differentiates traffic classes and subjects the packets to different thresholds based on the QoS label. If the threshold is exceeded, the packet is dropped. For more information, see the “Queueing and Scheduling Overview” section.
- Scheduling services the four egress queues based on their configured SRR shared or shaped weights. One of the queues (queue 1) can be the expedited queue, which is serviced until empty before the other queues are serviced.

Note![]() Catalyst 2960-S switches do not support ingress queueing.
Catalyst 2960-S switches do not support ingress queueing.

Classification
Classification is the process of distinguishing one kind of traffic from another by examining the fields in the packet. Classification is enabled only if QoS is globally enabled on the switch. By default, QoS is globally disabled, so no classification occurs.
During classification, the switch performs a lookup and assigns a QoS label to the packet. The QoS label identifies all QoS actions to be performed on the packet and from which queue the packet is sent.
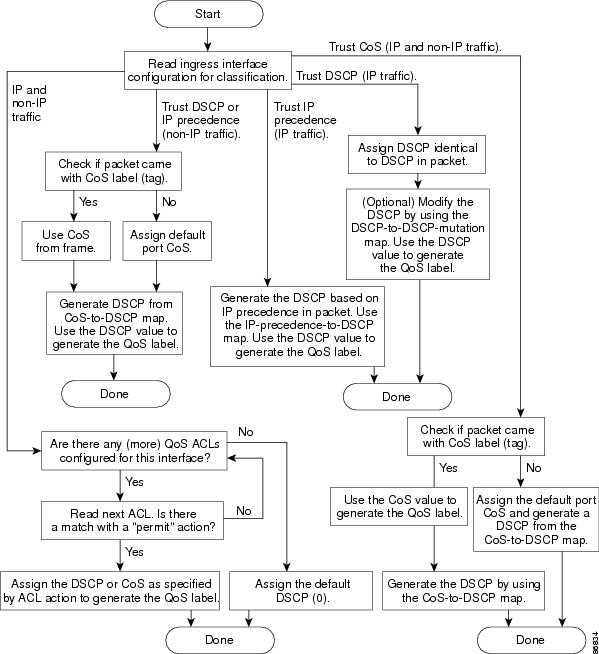
The QoS label is based on the DSCP or the CoS value in the packet and decides the queueing and scheduling actions to perform on the packet. The label is mapped according to the trust setting and the packet type as shown in Figure 1-3.
You specify which fields in the frame or packet that you want to use to classify incoming traffic. For non-IP traffic, you have these classification options as shown in Figure 1-3:
- Trust the CoS value in the incoming frame (configure the port to trust CoS). Then use the configurable CoS-to-DSCP map to generate a DSCP value for the packet. Layer 2 ISL frame headers carry the CoS value in the 3 least-significant bits of the 1-byte User field. Layer 2 IEEE 802.1Q frame headers carry the CoS value in the 3 most-significant bits of the Tag Control Information field. CoS values range from 0 for low priority to 7 for high priority.
- Trust the DSCP or trust IP precedence value in the incoming frame. These configurations are meaningless for non-IP traffic. If you configure a port with either of these options and non-IP traffic is received, the switch assigns a CoS value and generates an internal DSCP value from the CoS-to-DSCP map. The switch uses the internal DSCP value to generate a CoS value representing the priority of the traffic.
- Perform the classification based on a configured Layer 2 MAC access control list (ACL), which can examine the MAC source address, the MAC destination address, and other fields. If no ACL is configured, the packet is assigned 0 as the DSCP and CoS values, which means best-effort traffic. Otherwise, the policy-map action specifies a DSCP or CoS value to assign to the incoming frame.
For IP traffic, you have these classification options as shown in Figure 1-3:
- Trust the DSCP value in the incoming packet (configure the port to trust DSCP), and assign the same DSCP value to the packet. The IETF defines the 6 most-significant bits of the 1-byte ToS field as the DSCP. The priority represented by a particular DSCP value is configurable. DSCP values range from 0 to 63.
For ports that are on the boundary between two QoS administrative domains, you can modify the DSCP to another value by using the configurable DSCP-to-DSCP-mutation map.
- Trust the IP precedence value in the incoming packet (configure the port to trust IP precedence), and generate a DSCP value for the packet by using the configurable IP-precedence-to-DSCP map. The IP Version 4 specification defines the 3 most-significant bits of the 1-byte ToS field as the IP precedence. IP precedence values range from 0 for low priority to 7 for high priority.
- Trust the CoS value (if present) in the incoming packet, and generate a DSCP value for the packet by using the CoS-to-DSCP map. If the CoS value is not present, use the default port CoS value.
- Perform the classification based on a configured IP standard or an extended ACL, which examines various fields in the IP header. If no ACL is configured, the packet is assigned 0 as the DSCP and CoS values, which means best-effort traffic. Otherwise, the policy-map action specifies a DSCP or CoS value to assign to the incoming frame.
For information on the maps described in this section, see the “Mapping Tables” section. For configuration information on port trust states, see the “Configuring Classification Using Port Trust States” section.
After classification, the packet is sent to the policing, marking, and the ingress queueing and scheduling stages.

Note![]() Catalyst 2960-S switches do not support ingress queueing.
Catalyst 2960-S switches do not support ingress queueing.
Figure 1-3 Classification Flowchart
Classification Based on QoS ACLs

Note![]() If the switch is running the LAN Lite image, you can configure ACLs, but you cannot attach them to physical interfaces. You can attach them to VLAN interfaces to filter traffic to the CPU.
If the switch is running the LAN Lite image, you can configure ACLs, but you cannot attach them to physical interfaces. You can attach them to VLAN interfaces to filter traffic to the CPU.
You can use IP standard, IP extended, or Layer 2 MAC ACLs to define a group of packets with the same characteristics (class). In the QoS context, the permit and deny actions in the access control entries (ACEs) have different meanings than with security ACLs:
- If a match with a permit action is encountered (first-match principle), the specified QoS-related action is taken.
- If a match with a deny action is encountered, the ACL being processed is skipped, and the next ACL is processed.
- If no match with a permit action is encountered and all the ACEs have been examined, no QoS processing occurs on the packet, and the switch offers best-effort service to the packet.
- If multiple ACLs are configured on a port, the lookup stops after the packet matches the first ACL with a permit action, and QoS processing begins.

Note![]() When creating an access list, remember that, by default, the end of the access list contains an implicit deny statement for everything if it did not find a match before reaching the end.
When creating an access list, remember that, by default, the end of the access list contains an implicit deny statement for everything if it did not find a match before reaching the end.
After a traffic class has been defined with the ACL, you can attach a policy to it. A policy might contain multiple classes with actions specified for each one of them. A policy might include commands to classify the class as a particular aggregate (for example, assign a DSCP) or rate-limit the class. This policy is then attached to a particular port on which it becomes effective.
You implement IP ACLs to classify IP traffic by using the access-list global configuration command; you implement Layer 2 MAC ACLs to classify non-IP traffic by using the mac access-list extended global configuration command. For configuration information, see the “Configuring a QoS Policy” section.
Classification Based on Class Maps and Policy Maps

Note![]() To use policy maps, the switch must be running the LAN Base image.
To use policy maps, the switch must be running the LAN Base image.
A class map is a mechanism that you use to name a specific traffic flow (or class) and to isolate it from all other traffic. The class map defines the criteria used to match against a specific traffic flow to further classify it. The criteria can include matching the access group defined by the ACL or matching a specific list of DSCP or IP precedence values. If you have more than one type of traffic that you want to classify, you can create another class map and use a different name. After a packet is matched against the class-map criteria, you further classify it through the use of a policy map.
A policy map specifies which traffic class to act on. Actions can include trusting the CoS, DSCP, or IP precedence values in the traffic class; setting a specific DSCP or IP precedence value in the traffic class; or specifying the traffic bandwidth limitations and the action to take when the traffic is out of profile. Before a policy map can be effective, you must attach it to a port.
You create a class map by using the class-map global configuration command or the class policy-map configuration command. You should use the class-map command when the map is shared among many ports. When you enter the class-map command, the switch enters the class-map configuration mode. In this mode, you define the match criterion for the traffic by using the match class-map configuration command.
You can configure a default class by using the class class-default policy-map configuration command(not supported on Catalyst 2960-S). Unclassified traffic (traffic that does not meet the match criteria specified in the traffic classes) is treated as default traffic.
You create and name a policy map by using the policy-map global configuration command. When you enter this command, the switch enters the policy-map configuration mode. In this mode, you specify the actions to take on a specific traffic class by using the class, trust, or set policy-map configuration and policy-map class configuration commands.
The policy map can contain the police and police aggregate policy-map class configuration commands, which define the policer, the bandwidth limitations of the traffic, and the action to take if the limits are exceeded.
To enable the policy map, you attach it to a port by using the service-policy interface configuration command.
For more information, see the “Policing and Marking” section. For configuration information, see the “Configuring a QoS Policy” section.
Policing and Marking

Note![]() To use policing and marking, the switch must be running the LAN Base image.
To use policing and marking, the switch must be running the LAN Base image.
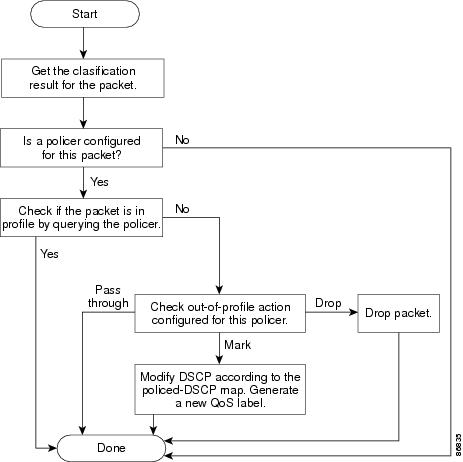
After a packet is classified and has a DSCP-based or CoS-based QoS label assigned to it, the policing and marking process can begin as shown in Figure 1-4.
Policing involves creating a policer that specifies the bandwidth limits for the traffic. Packets that exceed the limits are out of profile or nonconforming . Each policer decides on a packet-by-packet basis whether the packet is in or out of profile and specifies the actions on the packet. These actions, carried out by the marker, include passing through the packet without modification, dropping the packet, or modifying (marking down) the assigned DSCP of the packet and allowing the packet to pass through. The configurable policed-DSCP map provides the packet with a new DSCP-based QoS label. For information on the policed-DSCP map, see the “Mapping Tables” section. Marked-down packets use the same queues as the original QoS label to prevent packets in a flow from getting out of order.

Note![]() All traffic, regardless of whether it is bridged or routed, is subjected to a policer, if one is configured. As a result, bridged packets might be dropped or might have their DSCP or CoS fields modified when they are policed and marked.
All traffic, regardless of whether it is bridged or routed, is subjected to a policer, if one is configured. As a result, bridged packets might be dropped or might have their DSCP or CoS fields modified when they are policed and marked.
You can configure policing (either individual or aggregate policers) on a physical port or an SVI. For more information about configuring policing on physical ports, see the “Policing on Physical Ports” section.
After you configure the policy map and policing actions, attach the policy to an ingress port by using the service-policy interface configuration command. For configuration information, see the “Classifying, Policing, and Marking Traffic on Physical Ports by Using Policy Maps” section and the “Classifying, Policing, and Marking Traffic by Using Aggregate Policers” section.

Note![]() Catalyst 2960-S switches do not support ingress queueing.
Catalyst 2960-S switches do not support ingress queueing.
Policing on Physical Ports
In policy maps on physical ports, you can create these types of policers:
- Individual—QoS applies the bandwidth limits specified in the policer separately to each matched traffic class. You configure this type of policer within a policy map by using the police policy-map class configuration command.
- Aggregate—QoS applies the bandwidth limits specified in an aggregate policer cumulatively to all matched traffic flows. You configure this type of policer by specifying the aggregate policer name within a policy map by using the police aggregate policy-map class configuration command. You specify the bandwidth limits of the policer by using the mls qos aggregate-policer global configuration command. In this way, the aggregate policer is shared by multiple classes of traffic within a policy map.

Note![]() You can configure only individual policers on an SVI.
You can configure only individual policers on an SVI.
Policing uses a token-bucket algorithm. As each frame is received by the switch, a token is added to the bucket. The bucket has a hole in it and leaks at a rate that you specify as the average traffic rate in bits per second. Each time a token is added to the bucket, the switch verifies that there is enough room in the bucket. If there is not enough room, the packet is marked as nonconforming, and the specified policer action is taken (dropped or marked down).
How quickly the bucket fills is a function of the bucket depth (burst-byte), the rate at which the tokens are removed (rate-b/s), and the duration of the burst above the average rate. The size of the bucket imposes an upper limit on the burst length and limits the number of frames that can be transmitted back-to-back. If the burst is short, the bucket does not overflow, and no action is taken against the traffic flow. However, if a burst is long and at a higher rate, the bucket overflows, and the policing actions are taken against the frames in that burst.
You configure the bucket depth (the maximum burst that is tolerated before the bucket overflows) by using the burst-byte option of the police policy-map class configuration command or the mls qos aggregate-policer global configuration command. You configure how fast (the average rate) that the tokens are removed from the bucket by using the rate-bps option of the police policy-map class configuration command or the mls qos aggregate-policer global configuration command.
Figure 1-4 shows the policing and marking process.
Figure 1-4 Policing and Marking Flowchart on Physical Ports
Mapping Tables

Note![]() To use mapping tables, the switch must be running the LAN Base image.
To use mapping tables, the switch must be running the LAN Base image.
During QoS processing, the switch represents the priority of all traffic (including non-IP traffic) with an QoS label based on the DSCP or CoS value from the classification stage:
- During classification, QoS uses configurable mapping tables to derive a corresponding DSCP or CoS value from a received CoS, DSCP, or IP precedence value. These maps include the CoS-to-DSCP map and the IP-precedence-to-DSCP map. You configure these maps by using the mls qos map cos-dscp and the mls qos map ip-prec-dscp global configuration commands.
On an ingress port configured in the DSCP-trusted state, if the DSCP values are different between the QoS domains, you can apply the configurable DSCP-to-DSCP-mutation map to the port that is on the boundary between the two QoS domains. You configure this map by using the mls qos map dscp-mutation global configuration command.

Note![]() Catalyst 2960-S switches do not support ingress queueing.
Catalyst 2960-S switches do not support ingress queueing.
- During policing, QoS can assign another DSCP value to an IP or a non-IP packet (if the packet is out of profile and the policer specifies a marked-down value). This configurable map is called the policed-DSCP map. You configure this map by using the mls qos map policed-dscp global configuration command.
- Before the traffic reaches the scheduling stage, QoS stores the packet in an ingress and an egress queue according to the QoS label. The QoS label is based on the DSCP or the CoS value in the packet and selects the queue through the DSCP input and output queue threshold maps or through the CoS input and output queue threshold maps. In addition to an ingress or an egress queue, the QOS label also identifies the WTD threshold value. You configure these maps by using the mls qos srr-queue { input | output } dscp-map and the mls qos srr-queue { input | output } cos-map global configuration commands.
The CoS-to-DSCP, DSCP-to-CoS, and the IP-precedence-to-DSCP maps have default values that might or might not be appropriate for your network.
The default DSCP-to-DSCP-mutation map and the default policed-DSCP map are null maps; they map an incoming DSCP value to the same DSCP value. The DSCP-to-DSCP-mutation map is the only map you apply to a specific port. All other maps app ly to the entire switch.
For configuration information, see the “Configuring DSCP Maps” section.
For information about the DSCP and CoS input queue threshold maps, see the “Queueing and Scheduling on Ingress Queues” section. For information about the DSCP and CoS output queue threshold maps, see the “Queueing and Scheduling on Egress Queues” section.
Queueing and Scheduling Overview
The switch has queues at specific points to help prevent congestion as shown in Figure 1-5.
Figure 1-5 Ingress and Egress Queue Location
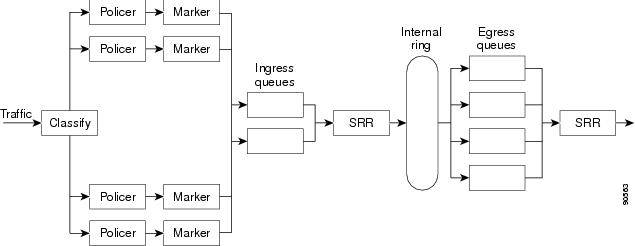
Because the total inbound bandwidth of all ports can exceed the bandwidth of the internal ring, ingress queues are located after the packet is classified, policed, and marked and before packets are forwarded into the switch fabric. Because multiple ingress ports can simultaneously send packets to an egress port and cause congestion, outbound queues are located after the internal ring.
Weighted Tail Drop

Note![]() To use WTD, the switch must be running the LAN Base image.
To use WTD, the switch must be running the LAN Base image.

Note![]() Catalyst 2960-S switches do not support ingress queueing.
Catalyst 2960-S switches do not support ingress queueing.
Both the ingress and egress queues use an enhanced version of the tail-drop congestion-avoidance mechanism called weighted tail drop (WTD). WTD is implemented on queues to manage the queue lengths and to provide drop precedences for different traffic classifications.
As a frame is enqueued to a particular queue, WTD uses the frame’s assigned QoS label to subject it to different thresholds. If the threshold is exceeded for that QoS label ( the space available in the destination queue is less than the size of the frame), the switch drops the frame.
Each queue has three threshold values. The QOS label is determines which of the three threshold values is subjected to the frame. Of the three thresholds, two are configurable (explicit) and one is not (implicit).
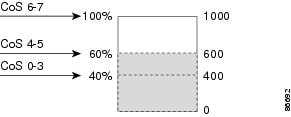
Figure 1-6 shows an example of WTD operating on a queue whose size is 1000 frames. Three drop percentages are configured: 40 percent (400 frames), 60 percent (600 frames), and 100 percent (1000 frames). These percentages mean that up to 400 frames can be queued at the 40-percent threshold, up to 600 frames at the 60-percent threshold, and up to 1000 frames at the 100-percent threshold.
In this example, CoS values 6 and 7 have a greater importance than the other CoS values, and they are assigned to the 100-percent drop threshold (queue-full state). CoS values 4 and 5 are assigned to the 60-percent threshold, and CoS values 0 to 3 are assigned to the 40-percent threshold.
Suppose the queue is already filled with 600 frames, and a new frame arrives. It contains CoS values 4 and 5 and is subjected to the 60-percent threshold. If this frame is added to the queue, the threshold will be exceeded, so the switch drops it.
Figure 1-6 WTD and Queue Operation
For more information, see the “Mapping DSCP or CoS Values to an Ingress Queue and Setting WTD Thresholds” section, the “Allocating Buffer Space to and Setting WTD Thresholds for an Egress Queue-Set” section, and the “Mapping DSCP or CoS Values to an Egress Queue and to a Threshold ID” section.
SRR Shaping and Sharing
Both the ingress and egress queues are serviced by SRR, which controls the rate at which packets are sent. On the ingress queues, SRR sends packets to the stack or internal ring. On the egress queues, SRR sends packets to the egress port.

Note![]() Catalyst 2960-S switches do not support ingress queueing.
Catalyst 2960-S switches do not support ingress queueing.
You can configure SRR on egress queues for sharing or for shaping. However, for ingress queues, sharing is the default mode, and it is the only mode supported.
In shaped mode, the egress queues are guaranteed a percentage of the bandwidth, and they are rate-limited to that amount. Shaped traffic does not use more than the allocated bandwidth even if the link is idle. Shaping provides a more even flow of traffic over time and reduces the peaks and valleys of bursty traffic. With shaping, the absolute value of each weight is used to compute the bandwidth available for the queues.
In shared mode, the queues share the bandwidth among them according to the configured weights. The bandwidth is guaranteed at this level but not limited to it. For example, if a queue is empty and no longer requires a share of the link, the remaining queues can expand into the unused bandwidth and share it among them. With sharing, the ratio of the weights controls the frequency of dequeuing; the absolute values are meaningless. Shaping and sharing is configured per interface. Each interface can be uniquely configured.
For more information, see the “Allocating Bandwidth Between the Ingress Queues” section, the “Configuring SRR Shaped Weights on Egress Queues” section, and the “Configuring SRR Shared Weights on Egress Queues” section.
Queueing and Scheduling on Ingress Queues

Note![]() Catalyst 2960-S switches do not support ingress queueing.
Catalyst 2960-S switches do not support ingress queueing.
Figure 1-7 shows the queueing and scheduling flowchart for ingress ports.
Figure 1-7 Queueing and Scheduling Flowchart for Ingress Ports
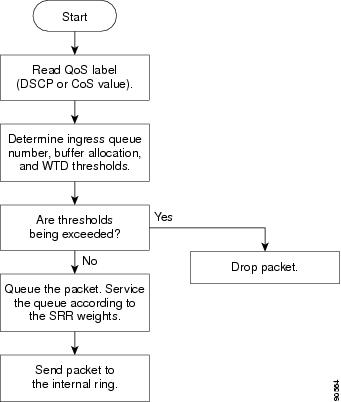

Note![]() SRR services the priority queue for its configured share before servicing the other queue.
SRR services the priority queue for its configured share before servicing the other queue.
The switch supports two configurable ingress queues, which are serviced by SRR in shared mode only. Table 1-1 describes the queues.

Note![]() Catalyst 2960-S switches do not support ingress queueing.
Catalyst 2960-S switches do not support ingress queueing.
|
|
|
|---|---|
User traffic that is considered to be normal priority. You can configure three different thresholds to differentiate among the flows. You can use the mls qos srr-queue input threshold, the mls qos srr-queue input dscp-map, and the mls qos srr-queue input cos-map global configuration commands. |
|
High-priority user traffic such as differentiated services (DF) expedited forwarding or voice traffic. You can configure the bandwidth required for this traffic as a percentage of the total stack traffic by using the mls qos srr-queue input priority-queue global configuration command. The expedite queue has guaranteed bandwidth. |
|
1.The switch uses two nonconfigurable queues for traffic that is essential for proper network and stack operation. |
You assign each packet that flows through the switch to a queue and to a threshold. Specifically, you map DSCP or CoS values to an ingress queue and map DSCP or CoS values to a threshold ID. You use the mls qos srr-queue input dscp-map queue queue-id { dscp1...dscp8 | threshold threshold-id dscp1...dscp8 } or the mls qos srr-queue input cos-map queue queue-id { cos1...cos8 | threshold threshold-id cos1...cos8 } global configuration command. You can display the DSCP input queue threshold map and the CoS input queue threshold map by using the show mls qos maps privileged EXEC command.
WTD Thresholds

Note![]() Catalyst 2960-S switches do not support ingress queueing.
Catalyst 2960-S switches do not support ingress queueing.
The queues use WTD to support distinct drop percentages for different traffic classes. Each queue has three drop thresholds: two configurable ( explicit) WTD thresholds and one nonconfigurable ( implicit) threshold preset to the queue-full state. You assign the two explicit WTD threshold percentages for threshold ID 1 and ID 2 to the ingress queues by using the mls qos srr-queue input threshold queue-id threshold-percentage1 threshold-percentage2 global configuration command. Each threshold value is a percentage of the total number of allocated buffers for the queue. The drop threshold for threshold ID 3 is preset to the queue-full state, and you cannot modify it. For more information about how WTD works, see the “Weighted Tail Drop” section.
Buffer and Bandwidth Allocation

Note![]() Catalyst 2960-S switches do not support ingress queueing.
Catalyst 2960-S switches do not support ingress queueing.
You define the ratio (allocate the amount of space) with which to divide the ingress buffers between the two queues by using the mls qos srr-queue input buffers percentage1 percentage2 global configuration command. The buffer allocation together with the bandwidth allocation control how much data can be buffered and sent before packets are dropped. You allocate bandwidth as a percentage by using the mls qos srr-queue input bandwidth weight1 weight2 global configuration command. The ratio of the weights is the ratio of the frequency in which the SRR scheduler sends packets from each queue.
Priority Queueing

Note![]() Catalyst 2960-S switches do not support ingress queueing.
Catalyst 2960-S switches do not support ingress queueing.
You can configure one ingress queue as the priority queue by using the mls qos srr-queue input priority-queue queue-id bandwidth weight global configuration command. The priority queue should be used for traffic (such as voice) that requires guaranteed delivery because this queue is guaranteed part of the bandwidth regardless of the load on the stack or internal ring.
SRR services the priority queue for its configured weight as specified by the bandwidth keyword in the mls qos srr-queue input priority-queue queue-id bandwidth weight global configuration command. Then, SRR shares the remaining bandwidth with both ingress queues and services them as specified by the weights configured with the mls qos srr-queue input bandwidth weight1 weight2 global configuration command.
You can combine the commands described in this section to prioritize traffic by placing packets with particular DSCPs or CoSs into certain queues, by allocating a large queue size or by servicing the queue more frequently, and by adjusting queue thresholds so that packets with lower priorities are dropped. For configuration information, see the “Configuring Ingress Queue Characteristics” section.
Queueing and Scheduling on Egress Queues
Figure 1-8 shows the queueing and scheduling flowchart for egress ports.

Note![]() If the expedite queue is enabled, SRR services it until it is empty before servicing the other three queues.
If the expedite queue is enabled, SRR services it until it is empty before servicing the other three queues.
Figure 1-8 Queueing and Scheduling Flowchart for Egress Ports
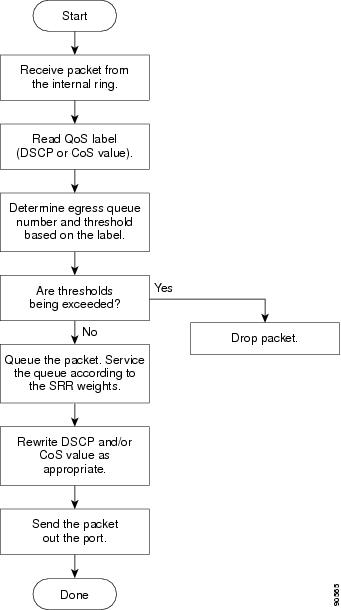
Each port supports four egress queues, one of which (queue 1) can be the egress expedite queue.These queues are configured by a queue-set. All traffic leaving an egress port flows through one of these four queues and is subjected to a threshold based on the QoS label assigned to the packet.
Figure 1-9 shows the egress queue buffer. The buffer space is divided between the common pool and the reserved pool. The switch uses a buffer allocation scheme to reserve a minimum amount of buffers for each egress queue, to prevent any queue or port from consuming all the buffers and depriving other queues, and to control whether to grant buffer space to a requesting queue. The switch detects whether the target queue has not consumed more buffers than its reserved amount (under-limit), whether it has consumed all of its maximum buffers (over limit), and whether the common pool is empty (no free buffers) or not empty (free buffers). If the queue is not over-limit, the switch can allocate buffer space from the reserved pool or from the common pool (if it is not empty). If there are no free buffers in the common pool or if the queue is over-limit, the switch drops the frame.
Figure 1-9 Egress Queue Buffer Allocation
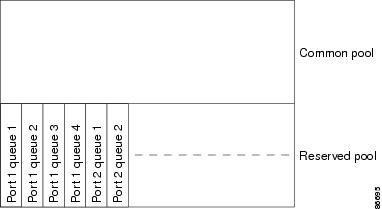
Buffer and Memory Allocation
You guarantee the availability of buffers, set drop thresholds, and configure the maximum memory allocation for a queue-set by using the mls qos queue-set output qset-id threshold queue-id drop-threshold1 drop-threshold2 reserved-threshold maximum-threshold global configuration command. Each threshold value is a percentage of the queue’s allocated memory, which you specify by using the mls qos queue-set output qset-id buffers allocation1... allocation4 global configuration command. The sum of all the allocated buffers represents the reserved pool, and the remaining buffers are part of the common pool.
Through buffer allocation, you can ensure that high-priority traffic is buffered. For example, if the buffer space is 400, you can allocate 70 percent of it to queue 1 and 10 percent to queues 2 through 4. Queue 1 then has 280 buffers allocated to it, and queues 2 through 4 each have 40 buffers allocated to them.
You can guarantee that the allocated buffers are reserved for a specific queue in a queue-set. For example, if there are 100 buffers for a queue, you can reserve 50 percent (50 buffers). The switch returns the remaining 50 buffers to the common pool. You also can enable a queue in the full condition to obtain more buffers than are reserved for it by setting a maximum threshold. The switch can allocate the needed buffers from the common pool if the common pool is not empty.
WTD Thresholds
You can assign each packet that flows through the switch to a queue and to a threshold. Specifically, you map DSCP or CoS values to an egress queue and map DSCP or CoS values to a threshold ID. You use the mls qos srr-queue output dscp-map queue queue-id { dscp1...dscp8 | threshold threshold-id dscp1...dscp8 } or the mls qos srr-queue output cos-map queue queue-id { cos1...cos8 | threshold threshold-id cos1...cos8 } global configuration command. You can display the DSCP output queue threshold map and the CoS output queue threshold map by using the show mls qos maps privileged EXEC command.
The queues use WTD to support distinct drop percentages for different traffic classes. Each queue has three drop thresholds: two configurable ( explicit) WTD thresholds and one nonconfigurable ( implicit) threshold preset to the queue-full state. You assign the two WTD threshold percentages for threshold ID 1 and ID 2. The drop threshold for threshold ID 3 is preset to the queue-full state, and you cannot modify it. You map a port to queue-set by using the queue-set qset-id interface configuration command. Modify the queue-set configuration to change the WTD threshold percentages. For more information about how WTD works, see the “Weighted Tail Drop” section.
Shaped or Shared Mode
SRR services each queue-set in shared or shaped mode. You assign shared or shaped weights to the port by using the srr-queue bandwidth share weight1 weight2 weight3 weight4 or the srr-queue bandwidth shape weight1 weight2 weight3 weight4 interface configuration commands. For an explanation of the differences between shaping and sharing, see the “SRR Shaping and Sharing” section.
The buffer allocation together with the SRR weight ratios control how much data can be buffered and sent before packets are dropped. The weight ratio is the ratio of the frequency in which the SRR scheduler sends packets from each queue.
All four queues participate in the SRR unless the expedite queue is enabled, in which case the first bandwidth weight is ignored and is not used in the ratio calculation. The expedite queue is a priority queue, and it is serviced until empty before the other queues are serviced. You enable the expedite queue by using the priority-queue out interface configuration command.
You can combine the commands described in this section to prioritize traffic by placing packets with particular DSCPs or CoSs into certain queues, by allocating a large queue size or by servicing the queue more frequently, and by adjusting queue thresholds so that packets with lower priorities are dropped. For configuration information, see the “Configuring Egress Queue Characteristics” section.

Note![]() The egress queue default settings are suitable for most situations. You should change them only when you have a thorough understanding of the egress queues and if these settings do not meet your QoS solution.
The egress queue default settings are suitable for most situations. You should change them only when you have a thorough understanding of the egress queues and if these settings do not meet your QoS solution.
Packet Modification
A packet is classified, policed, and queued to provide QoS. Packet modifications can occur during this process:
- For IP and non-IP packets, classification involves assigning a QoS label to a packet based on the DSCP or CoS of the received packet. However, the packet is not modified at this stage; only an indication of the assigned DSCP or CoS value is carried along. The reason for this is that QoS classification and forwarding lookups occur in parallel, and it is possible that the packet is forwarded with its original DSCP to the CPU where it is again processed through software.
- During policing, IP and non-IP packets can have another DSCP assigned to them (if they are out of profile and the policer specifies a markdown DSCP). Once again, the DSCP in the packet is not modified, but an indication of the marked-down value is carried along. For IP packets, the packet modification occurs at a later stage; for non-IP packets the DSCP is converted to CoS and used for queueing and scheduling decisions.
- Depending on the QoS label assigned to a frame and the mutation chosen, the DSCP and CoS values of the frame are rewritten. If you do not configure the mutation map and if you configure the port to trust the DSCP of the incoming frame, the DSCP value in the frame is not changed, but the CoS is rewritten according to the DSCP-to-CoS map. If you configure the port to trust the CoS of the incoming frame and it is an IP packet, the CoS value in the frame is not changed, but the DSCP might be changed according to the CoS-to-DSCP map.
The input mutation causes the DSCP to be rewritten depending on the new value of DSCP chosen. The set action in a policy map also causes the DSCP to be rewritten.
Configuring Auto-QoS

Note![]() To use auto-QoS, the switch must be running the LAN Base image.
To use auto-QoS, the switch must be running the LAN Base image.

Note![]() Catalyst 2960-S switches do not support ingress queueing.
Catalyst 2960-S switches do not support ingress queueing.
You can use the auto-QoS feature to simplify the deployment of QoS features. Auto-QoS determines the network design and enables QoS configurations so that the switch can prioritize different traffic flows. It uses the ingress and egress queues instead of using the default (disabled) QoS behavior. The switch offers best-effort service to each packet, regardless of the packet contents or size, and sends it from a single queue.
When you enable auto-QoS, it automatically classifies traffic based on the traffic type and ingress packet label. The switch uses the classification results to choose the appropriate egress queue.
You use auto-QoS commands to identify ports connected to these Cisco devices:
You also use the commands to identify ports that receive trusted traffic through an uplink. Auto-QoS then performs these functions:
- Detects the presence or absence of auto-QoS devices through conditional trusted interfaces.
- Configures QoS classification
- Configures egress queues
These sections contain this configuration information:
- Generated Auto-QoS Configuration
- Effects of Auto-QoS on the Configuration
- Auto-QoS Configuration Guidelines
- Enabling Auto-QoS
Generated Auto-QoS Configuration
By default, auto-QoS is disabled on all ports. Packets are not modified--the CoS, DSCP and IP precedence values in the packet are not changed.

Note![]() Catalyst 2960-S switches do not support ingress queueing.
Catalyst 2960-S switches do not support ingress queueing.
When you enable the auto-QoS feature on the first port of the interface:
- Ingress packet label is used to categorize traffic, to assign packet labels, and to configure the ingress and egress queues.
- QoS is globally enabled ( mls qos global configuration command), and other global configuration commands are automatically generated. (See Table 1-5 .)
- Switch enables the trusted boundary feature and uses the Cisco Discovery Protocol (CDP) to detect the presence of a supported device.
- Policing is used to determine whether a packet is in or out of profile and specifies the action on the packet.
VOIP Device Specifics
- When you enter the auto qos voip cisco-phone command on a port at the network edge connected to a Cisco IP Phone, the switch enables the trusted boundary feature. If the packet does not have a DSCP value of 24, 26, or 46 or is out of profile, the switch changes the DSCP value to 0. When there is no Cisco IP Phone, the ingress classification is set to not trust the QoS label in the packet. The policing is applied to the traffic matching the policy-map classification before the switch enables the trust boundary feature.
- When you enter the auto qos voip cisco-softphone interface configuration command on a port at the network edge that is connected to a device running the Cisco SoftPhone, the switch uses policing to determine whether a packet is in or out of profile and to specify the action on the packet. If the packet does not have a DSCP value of 24, 26, or 46 or is out of profile, the switch changes the DSCP value to 0.
- When you enter the auto qos voip trust interface configuration command on a port connected to the network interior, the switch trusts the CoS value for nonrouted ports or the DSCP value for routed ports in ingress packets (the assumption is that traffic has already been classified by other edge devices).
The switch configures ingress and egress queues on the port according to the settings in Table 1-2 and Table 1-3 .
|
|
Traffic |
|
|
|
|
||
|---|---|---|---|---|---|---|---|
|
|
|
|
|
|
|
|
|---|---|---|---|---|
|
|
|
|
|
|
|
|---|---|---|---|---|---|
For information about the trusted boundary feature, see the “Configuring a Trusted Boundary to Ensure Port Security” section on page 39-42.
When you enable auto-QoS by using the auto qos voip cisco-phone, the auto qos voip cisco-softphone, or the auto qos voip trust interface configuration command, the switch automatically generates a QoS configuration based on the traffic type and ingress packet label and applies the commands listed in Table 1-5 to the port.
Enhanced Auto-QoS for Video, Trust, and Classification

Note![]() The enhanced auto-QoS feature is not supported on switches running LAN Lite images.
The enhanced auto-QoS feature is not supported on switches running LAN Lite images.
In Cisco IOS Release 12.2(55)SE, auto-QoS is enhanced to support video. Automatic configurations are generated that classify and trust traffic from Cisco TelePresence systems and Cisco IP cameras.
When you configure the auto qos { video | classify | trust } enhanced commands on a switch port, this behavior occurs:
- Auto qos voip generated commands that you configured on the interface before Cisco IOS Release 12.2(55)SE migrate to the enhanced commands.
- Global values change with the migration of enhanced commands. For a complete list of the generated commands that are applied to the running configuration see Table 1-5 .
Auto-QoS Configuration Migration
Auto-QoS configuration migration from legacy auto-QoS to enhanced auto-QoS occurs when:
Any video or voice trust configuration on the interface automatically generates enhanced auto-QoS commands.
–![]() If you configure the interface for conditional trust on a voice device, only the legacy auto-QoS VoIP configuration is generated.
If you configure the interface for conditional trust on a voice device, only the legacy auto-QoS VoIP configuration is generated.
–![]() If you configure the interface for conditional trust on a video device, the enhanced auto-QoS configuration is generated.
If you configure the interface for conditional trust on a video device, the enhanced auto-QoS configuration is generated.
–![]() If you configure the interface with classification or conditional trust based on the new interface auto-QoS commands, enhanced auto-QoS configuration is generated.
If you configure the interface with classification or conditional trust based on the new interface auto-QoS commands, enhanced auto-QoS configuration is generated.
- Auto-QoS migration happens after a new device is connected when the auto qos srnd4 global configuration command is enabled.

Note![]() If an interface previously configured with legacy auto-QoS migrates to enhanced auto-QoS, voice commands and configuration are updated to match the new global QoS commands.
If an interface previously configured with legacy auto-QoS migrates to enhanced auto-QoS, voice commands and configuration are updated to match the new global QoS commands.
Auto-QoS configuration migration from enhanced auto-QoS to legacy auto-QoS can occur only when you disable all existing auto-QoS configurations from the interface.

Note![]() Catalyst 2960-S switches do not support ingress queueing.
Catalyst 2960-S switches do not support ingress queueing.
Global Auto-QoS Configuration
Auto-QoS Generated Configuration For VoIP Devices
If you entered the auto qos voip cisco-phone command, the switch automatically enables the trusted boundary feature, which uses the CDP to detect the presence or absence of a Cisco IP Phone.
If you entered the auto qos voip cisco-softphone command, the switch automatically creates class maps and policy maps.
Switch(config-pmap-c)# police 32000 8000 exceed-action policed-dscp-transmit
After creating the class maps and policy maps, the switch automatically applies the policy map called AutoQoS-Police-SoftPhone to an ingress interface on which auto-QoS with the Cisco SoftPhone feature is enabled.
Switch(config-if)# service-policy input AutoQoS-Police-SoftPhone
If you entered the auto qos voip cisco-phone command, the switch automatically creates class maps and policy maps.
Switch(config-if)# mls qos trust device cisco-phone
If you entered the auto qos voip cisco-softphone command, the switch automatically creates class maps and policy maps.
Switch(config-pmap-c)# police 32000 8000 exceed-action policed-dscp-transmit
After creating the class maps and policy maps, the switch automatically applies the policy map called AutoQoS-Police-SoftPhone to an ingress interface on which auto-QoS with the Cisco SoftPhone feature is enabled.
Switch(config-if)# service-policy input AutoQoS-Police-SoftPhone
Auto-QoS Generated Configuration For Enhanced Video, Trust, and Classify Devices
If you entered these enhanced auto-QoS commands, the switch automatically configures the CoS-to-DSCP map (maps CoS values in incoming packets to a DSCP value).
Switch(config)# mls qos map cos-dscp 0 8 16 24 32 46 48 56

Note![]() No class maps and policy maps are configured.
No class maps and policy maps are configured.
If you entered the auto qos classify command, the switch automatically creates class maps and policy maps.
If you entered the auto qos classify police command, the switch automatically creates class maps and policy maps.
This is the enhanced configuration for the auto qos voip cisco-phone command:
This is the enhanced configuration for the auto qos voip cisco-softphone command:
Effects of Auto-QoS on the Configuration
When auto-QoS is enabled, the auto qos interface configuration commands and the generated global configuration are added to the running configuration.
The switch applies the auto-QoS-generated commands as if the commands were entered from the CLI. An existing user configuration can cause the application of the generated commands to fail or to be overridden by the generated commands. These actions occur without warning. If all the generated commands are successfully applied, any user-entered configuration that was not overridden remains in the running configuration. Any user-entered configuration that was overridden can be retrieved by reloading the switch without saving the current configuration to memory. If the generated commands are not applied, the previous running configuration is restored.
Auto-QoS Configuration Guidelines
Before configuring auto-QoS, you should be aware of this information:
- Auto-QoS configures the switch for VoIP with Cisco IP Phones on nonrouted and routed ports. Auto-QoS also configures the switch for VoIP with devices running the Cisco SoftPhone application.
- When a device running Cisco SoftPhone is connected to a nonrouted or routed port, the switch supports only one Cisco SoftPhone application per port.
- Beginning with Cisco IOS Release 12.2(40)SE, Auto-Qos VoIP uses the priority-queue interface configuration command for an egress interface. You can also configure a policy-map and trust device on the same interface for Cisco IP phones.
- If the switch port was configure by using the auto qos voip cisco-phone interface configuration command in Cisco IOS Release 12.2(37)SE or earlier, the auto-QoS generated commands new to Cisco IOS Release 12.2(40)SE are not applied to the port. To have these commands automatically applied, you must remove and then reapply the configuration to the port.
- To take advantage of the auto-QoS defaults, you should enable auto-QoS before you configure other QoS commands. If necessary, you can fine-tune the QoS configuration, but we recommend that you do so only after the auto-QoS configuration is completed. For more information, see the Effects of Auto-QoS on the Configuration.
- After auto-QoS is enabled, do not modify a policy map or aggregate policer that includes AutoQoS in its name. If you need to modify the policy map or aggregate policer, make a copy of it, and change the copied policy map or policer. To use this new policy map instead of the generated one, remove the generated policy map from the interface, and apply the new policy map to the interface.
- You can enable auto-QoS on static, dynamic-access, voice VLAN access, and trunk ports.

Note![]() VLAN-based QoS is not supported on Catalyst 2960-S switches.
VLAN-based QoS is not supported on Catalyst 2960-S switches.
- By default, the CDP is enabled on all ports. For auto-QoS to function properly, do not disable the CDP.
- When enabling auto-QoS with a Cisco IP Phone on a routed port, you must assign a static IP address to the IP phone.
- This release supports only Cisco IP SoftPhone Version 1.3(3) or later.
- Connected devices must use Cisco Call Manager Version 4 or later.
Auto-QoS Enhanced Considerations
- The auto qos srnd4 global configuration command is generated as a result of enhanced auto-QoS configuration.
- If the legacy auto qos voip commands are executed on the switch and the mls qos command is disabled, the enhanced auto-QoS configuration is generated. Otherwise, legacy auto-QoS commands are executed.
Enabling Auto-QoS
For optimum QoS performance, enable auto-QoS on all the devices in your network.
Beginning in privileged EXEC mode, follow these steps to enable auto-QoS devices within a QoS domain:
Troubleshooting Auto QoS Commands
To display the QoS commands that are automatically generated when auto-QoS is enabled or disabled, enter the debug auto qos privileged EXEC command before you enable auto-QoS. For more information, see the debug autoqos command in the command reference for this release.
To disable auto-QoS on a port, use the no form of the auto qos command interface configuration command, such as no auto qos voip. Only the auto-QoS-generated interface configuration commands for this port are removed. If this is the last port on which auto-QoS is enabled and you enter the no auto qos voip command, auto-QoS is considered disabled even though the auto-QoS-generated global configuration commands remain (to avoid disrupting traffic on other ports affected by the global configuration).
You can use the no mls qos global configuration command to disable the auto-QoS-generated global configuration commands. With QoS disabled, there is no concept of trusted or untrusted ports because the packets are not modified (the CoS, DSCP, and IP precedence values in the packet are not changed). Traffic is switched in pass-through mode (packets are switched without any rewrites and classified as best effort without any policing).
Displaying Auto-QoS Information
To display the initial auto-QoS configuration, use the show auto qos [ interface [ interface-id ]] privileged EXEC command. To d isplay any user changes to that configuration, use the show running-config privileged EXEC command. You can compare the show auto qos and the show running-config command output to identify the user-defined QoS settings.
To display information about the QoS configuration that might be affected by auto-QoS, use one of these commands:
- show mls qos
- show mls qos maps cos-dscp
- show mls qos interface [ interface-id ] [ buffers | queueing ]
- show mls qos maps [ cos-dscp | cos-input-q | cos-output-q | dscp-cos | dscp-input-q | dscp-output-q ]
- show mls qos input-queue
- show running-config

Note![]() Catalyst 2960-S switches do not support ingress queueing.
Catalyst 2960-S switches do not support ingress queueing.
Configuring Standard QoS
Before configuring standard QoS, you must have a thorough understanding of these items:
- The types of applications used and the traffic patterns on your network.
- Traffic characteristics and needs of your network. Is the traffic bursty? Do you need to reserve bandwidth for voice and video streams?
- Bandwidth requirements and speed of the network.
- Location of congestion points in the network.
These sections contain this configuration information:
- Default Standard QoS Configuration
- Standard QoS Configuration Guidelines
- Enabling QoS Globally (required)
- Configuring Classification Using Port Trust States (required
- Configuring a QoS Policy (required)
- Configuring DSCP Maps (optional, unless you need to use the DSCP-to-DSCP-mutation map or the policed-DSCP map)
- Configuring Ingress Queue Characteristics (optional)
- Configuring Egress Queue Characteristics (optional)
Default Standard QoS Configuration

Note![]() Catalyst 2960-S switches do not support ingress queueing.
Catalyst 2960-S switches do not support ingress queueing.
QoS is disabled. There is no concept of trusted or untrusted ports because the packets are not modified (the CoS, DSCP, and IP precedence values in the packet are not changed). Traffic is switched in pass-through mode (packets are switched without any rewrites and classified as best effort without any policing).
When QoS is enabled with the mls qos global configuration command and all other QoS settings are at their defaults, traffic is classified as best effort (the DSCP and CoS value is set to 0) without any policing. No policy maps are configured. The default port trust state on all ports is untrusted. The default ingress and egress queue settings are described in the “Default Ingress Queue Configuration” section and the “Default Egress Queue Configuration” section.
Default Ingress Queue Configuration
Note Catalyst 2960-S switches do not support ingress queueing.
Table 1-6 shows the default ingress queue configuration when QoS is enabled.
|
|
|
|
|---|---|---|
Bandwidth allocation 3 |
||
Priority queue bandwidth 4 |
||
Table 1-7 shows the default CoS input queue threshold map when QoS is enabled.
|
|
|
|---|---|
Table 1-8 shows the default DSCP input queue threshold map when QoS is enabled.
|
|
|
|---|---|
Default Egress Queue Configuration
Table 1-9 shows the default egress queue configuration for each queue-set when QoS is enabled. All ports are mapped to queue-set 1. The port bandwidth limit is set to 100 percent and rate unlimited.
|
|
|
|
|
|
|---|---|---|---|---|
SRR shaped weights (absolute) 5 |
||||
SRR shared weights 6 |
|
5.A shaped weight of zero means that this queue is operating in shared mode. |
Table 1-10 shows the default CoS output queue threshold map when QoS is enabled.
|
|
|
|---|---|
Table 1-11 shows the default DSCP output queue threshold map when QoS is enabled.
|
|
|
|---|---|
Default Mapping Table Configuration
The default CoS-to-DSCP map is shown in Table 1-12.
The default IP-precedence-to-DSCP map is shown in Table 1-13.
The default DSCP-to-CoS map is shown in Table 1-14.
The default DSCP-to-DSCP-mutation map is a null map, which maps an incoming DSCP value to the same DSCP value.
The default policed-DSCP map is a null map, which maps an incoming DSCP value to the same DSCP value (no markdown).
Standard QoS Configuration Guidelines
Before beginning the QoS configuration, you should be aware of this information in these sections:
QoS ACL Guidelines
- If you use QoS ACLs for classification, you can use the sdm prefer qos global configuration command to set the Switch Database Management (SDM) feature to the QoS template. SDM configures system resources to support the maximum number of access control entries (ACEs). For more information on the SDM templates, see Chapter1, “Configuring SDM Templates”
- It is not possible to match IP fragments against configured IP extended ACLs to enforce QoS. IP fragments are sent as best-effort. IP fragments are denoted by fields in the IP header.
- Only one ACL per class map and only one match class-map configuration command per class map are supported. The ACL can have multiple ACEs, which match fields against the contents of the packet.
- A trust statement in a policy map requires multiple TCAM entries per ACL line. If an input service policy map contains a trust statement in an ACL, the access-list might be too large to fit into the available QoS TCAM and an error can occur when you apply the policy map to a port. Whenever possible, you should minimize the number of lines in a QoS ACL.
Policing Guidelines

Note![]() To use policing, the switch must be running the LAN Base image.
To use policing, the switch must be running the LAN Base image.
- The port ASIC device, which controls more than one physical port, supports 256 policers (255 user-configurable policers plus 1 policer reserved for system internal use). The maximum number of user-configurable policers supported per port is 63. Policers are allocated on demand by the software and are constrained by the hardware and ASIC boundaries. You cannot reserve policers per port; there is no guarantee that a port will be assigned to any policer.
- Only one policer is applied to a packet on an ingress port. Only the average rate and committed burst parameters are configurable.

Note![]() Catalyst 2960-S switches do not support ingress queueing.
Catalyst 2960-S switches do not support ingress queueing.
- On a port configured for QoS, all traffic received through the port is classified, policed, and marked according to the policy map attached to the port. On a trunk port configured for QoS, traffic in all VLANs received through the port is classified, policed, and marked according to the policy map attached to the port.
- If you have EtherChannel ports configured on your switch, you must configure QoS classification, policing, mapping, and queueing on the individual physical ports that comprise the EtherChannel. You must decide whether the QoS configuration should match on all ports in the EtherChannel.
- If you need to modify a policy map of an existing QoS policy, first remove the policy map from all interfaces, and then modify or copy the policy map. After you finish the modification, apply the modified policy map to the interfaces. If you do not first remove the policy map from all interfaces, high CPU usage can occur, which, in turn, can cause the console to pause for a very long time.
General QoS Guidelines
These are general QoS guidelines:
- You configure QoS only on physical ports; there is no support for it at the VLAN level.
- Control traffic (such as spanning-tree bridge protocol data units [BPDUs] and routing update packets) received by the switch are subject to all ingress QoS processing.

Note![]() Catalyst 2960-S switches do not support ingress queueing.
Catalyst 2960-S switches do not support ingress queueing.
Enabling QoS Globally
By default, QoS is disabled on the switch.
Beginning in privileged EXEC mode, follow these steps to enable QoS. This procedure is required.
|
|
|
|
|---|---|---|
| QoS runs with the default settings described in the “Default Standard QoS Configuration” section, the “Queueing and Scheduling on Ingress Queues” section, and the “Queueing and Scheduling on Egress Queues” section. |
||
To disable QoS, use the no mls qos global configuration command.
Configuring Classification Using Port Trust States
These sections describe how to classify incoming traffic by using port trust states. Depending on your network configuration, you must perform one or more of these tasks or one or more of the tasks in the “Configuring a QoS Policy” section:
Configuring the Trust State on Ports within the QoS Domain

Note![]() Catalyst 2960-S switches do not support ingress queueing.
Catalyst 2960-S switches do not support ingress queueing.
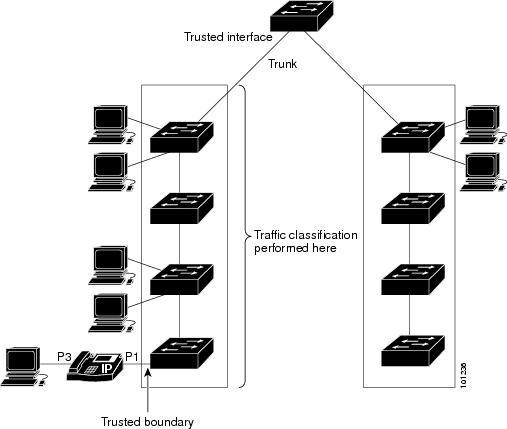
Packets entering a QoS domain are classified at the edge of the QoS domain. When the packets are classified at the edge, the switch port within the QoS domain can be configured to one of the trusted states because there is no need to classify the packets at every switch within the QoS domain. Figure 1-10 shows a sample network topology.
Figure 1-10 Port Trusted States within the QoS Domain
Beginning in privileged EXEC mode, follow these steps to configure the port to trust the classification of the traffic that it receives:
To return a port to its untrusted state, use the no mls qos trust interface configuration command.
For information on how to change the default CoS value, see the “Configuring the CoS Value for an Interface” section. For information on how to configure the CoS-to-DSCP map, see the “Configuring the CoS-to-DSCP Map” section.
Configuring the CoS Value for an Interface

Note![]() Catalyst 2960-S switches do not support ingress queueing.
Catalyst 2960-S switches do not support ingress queueing.
QoS assigns the CoS value specified with the mls qos cos interface configuration command to untagged frames received on trusted and untrusted ports.
Beginning in privileged EXEC mode, follow these steps to define the default CoS value of a port or to assign the default CoS to all incoming packets on the port:
To return to the default setting, use the no mls qos cos { default-cos | override } interface configuration command.
Configuring a Trusted Boundary to Ensure Port Security
In a typical network, you connect a Cisco IP Phone to a switch port, as shown in Figure 1-10, and cascade devices that generate data packets from the back of the telephone. The Cisco IP Phone guarantees the voice quality through a shared data link by marking the CoS level of the voice packets as high priority (CoS = 5) and by marking the data packets as low priority (CoS = 0). Traffic sent from the telephone to the switch is typically marked with a tag that uses the IEEE 802.1Q header. The header contains the VLAN information and the class of service (CoS) 3-bit field, which is the priority of the packet.
For most Cisco IP Phone configurations, the traffic sent from the telephone to the switch should be trusted to ensure that voice traffic is properly prioritized over other types of traffic in the network. By using the mls qos trust cos interface configuration command, you configure the switch port to which the telephone is connected to trust the CoS labels of all traffic received on that port. Use the mls qos trust dscp interface configuration command to configure a routed port to which the telephone is connected to trust the DSCP labels of all traffic received on that port.
With the trusted setting, you also can use the trusted boundary feature to prevent misuse of a high-priority queue if a user bypasses the telephone and connects the PC directly to the switch. Without trusted boundary, the CoS labels generated by the PC are trusted by the switch (because of the trusted CoS setting). By contrast, trusted boundary uses CDP to detect the presence of a Cisco IP Phone (such as the Cisco IP Phone 7910, 7935, 7940, and 7960) on a switch port. If the telephone is not detected, the trusted boundary feature disables the trusted setting on the switch port and prevents misuse of a high-priority queue. Note that the trusted boundary feature is not effective if the PC and Cisco IP Phone are connected to a hub that is connected to the switch.
In some situations, you can prevent a PC connected to the Cisco IP Phone from taking advantage of a high-priority data queue. You can use the switchport priority extend cos interface configuration command to configure the telephone through the switch CLI to override the priority of the traffic received from the PC.
Beginning in privileged EXEC mode, follow these steps to enable trusted boundary on a port:
To disable the trusted boundary feature, use the no mls qos trust device interface configuration command.
Enabling DSCP Transparency Mode
The switch supports the DSCP transparency feature. It affects only the DSCP field of a packet at egress. By default, DSCP transparency is disabled. The switch modifies the DSCP field in an incoming packet, and the DSCP field in the outgoing packet is based on the quality of service (QoS) configuration, including the port trust setting, policing and marking, and the DSCP-to-DSCP mutation map.
If DSCP transparency is enabled by using the no mls qos rewrite ip dscp command, the switch does not modify the DSCP field in the incoming packet, and the DSCP field in the outgoing packet is the same as that in the incoming packet.
Regardless of the DSCP transparency configuration, the switch modifies the internal DSCP value of the packet, which the switch uses to generate a class of service (CoS) value that represents the priority of the traffic. The switch also uses the internal DSCP value to select an egress queue and threshold.
Beginning in privileged EXEC mode, follow these steps to enable DSCP transparency on a switch:
|
|
|
|
|---|---|---|
Enable DSCP transparency. The switch is configured to not modify the DSCP field of the IP packet. |
||
To configure the switch to modify the DSCP value based on the trust setting or on an ACL by disabling DSCP transparency, use the mls qos rewrite ip dscp global configuration command.
If you disable QoS by using the no mls qos global configuration command, the CoS and DSCP values are not changed (the default QoS setting).
If you enter the no mls qos rewrite ip dscp global configuration command to enable DSCP transparency and then enter the mls qos trust [ cos | dscp ] interface configuration command, DSCP transparency is still enabled.
Configuring the DSCP Trust State on a Port Bordering Another QoS Domain
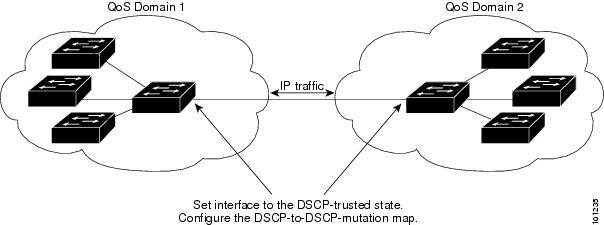
If you are administering two separate QoS domains between which you want to implement QoS features for IP traffic, you can configure the switch ports bordering the domains to a DSCP-trusted state as shown in Figure 1-11. Then the receiving port accepts the DSCP-trusted value and avoids the classification stage of QoS. If the two domains use different DSCP values, you can configure the DSCP-to-DSCP-mutation map to translate a set of DSCP values to match the definition in the other domain.
Figure 1-11 DSCP-Trusted State on a Port Bordering Another QoS Domain

Note![]() Catalyst 2960-S switches do not support ingress queueing.
Catalyst 2960-S switches do not support ingress queueing.
Beginning in privileged EXEC mode, follow these steps to configure the DSCP-trusted state on a port and modify the DSCP-to-DSCP-mutation map. To ensure a consistent mapping strategy across both QoS domains, you must perform this procedure on the ports in both domains:
To return a port to its non-trusted state, use the no mls qos trust interface configuration command. To return to the default DSCP-to-DSCP-mutation map values, use the no mls qos map dscp-mutation dscp-mutation-name global configuration command.
This example shows how to configure a port to the DSCP-trusted state and to modify the DSCP-to-DSCP-mutation map (named gi0/2-mutation) so that incoming DSCP values 10 to 13 are mapped to DSCP 30:
Configuring a QoS Policy
Configuring a QoS policy typically requires classifying traffic into classes, configuring policies applied to those traffic classes, and attaching policies to ports.

Note![]() To use policing and marking, the switch must be running the LAN Base image.
To use policing and marking, the switch must be running the LAN Base image.
For background information, see the “Classification” section and the “Policing and Marking” section. For configuration guidelines, see the “Standard QoS Configuration Guidelines” section.
These sections describe how to classify, police, and mark traffic. Depending on your network configuration, you must perform one or more of these tasks:
Classifying Traffic by Using ACLs
You can classify IP traffic by using IP standard or IP extended ACLs; you can classify non-IP traffic by using Layer 2 MAC ACLs.
Beginning in privileged EXEC mode, follow these steps to create an IP standard ACL for IP traffic:
To delete an access list, use the no access-list access-list-number global configuration command.
This example shows how to allow access for only those hosts on the three specified networks. The wildcard bits apply to the host portions of the network addresses. Any host with a source address that does not match the access list statements is rejected.
Beginning in privileged EXEC mode, follow these steps to create an IP extended ACL for IP traffic:
To delete an access list, use the no access-list access-list-number global configuration command.
This example shows how to create an ACL that permits IP traffic from any source to any destination that has the DSCP value set to 32:
This example shows how to create an ACL that permits IP traffic from a source host at 10.1.1.1 to a destination host at 10.1.1.2 with a precedence value of 5:
This example shows how to create an ACL that permits PIM traffic from any source to a destination group address of 224.0.0.2 with a DSCP set to 32:
Beginning in privileged EXEC mode, follow these steps to create a Layer 2 MAC ACL for non-IP traffic:
To delete an access list, use the no mac access-list extended access-list-name global configuration command.
This example shows how to create a Layer 2 MAC ACL with two permit statements. The first statement allows traffic from the host with MAC address 0001.0000.0001 to the host with MAC address 0002.0000.0001. The second statement allows only Ethertype XNS-IDP traffic from the host with MAC address 0001.0000.0002 to the host with MAC address 0002.0000.0002.
Classifying Traffic by Using Class Maps
You use the class-map global configuration command to name and to isolate a specific traffic flow (or class) from all other traffic. The class map defines the criteria to use to match against a specific traffic flow to further classify it. Match statements can include criteria such as an ACL, IP precedence values, or DSCP values. The match criterion is defined with one match statement entered within the class-map configuration mode.

Note![]() You can also create class-maps during policy map creation by using the class policy-map configuration command. For more information, see the “Classifying, Policing, and Marking Traffic on Physical Ports by Using Policy Maps” section.
You can also create class-maps during policy map creation by using the class policy-map configuration command. For more information, see the “Classifying, Policing, and Marking Traffic on Physical Ports by Using Policy Maps” section.
Beginning in privileged EXEC mode, follow these steps to create a class map and to define the match criterion to classify traffic:
|
|
|
|
|---|---|---|
access-list access-list-number { deny | permit } source [ source-wildcard ] access-list access-list-number { deny | permit } protocol source [ source-wildcard ] destination [ destination-wildcard ] { permit | deny } { host src-MAC-addr mask | any | host dst-MAC-addr | dst-MAC-addr mask } [ type mask ] |
Create an IP standard or extended ACL for IP traffic or a Layer 2 MAC ACL for non-IP traffic, repeating the command as many times as necessary. For more information, see the “Classifying Traffic by Using ACLs” section. Note When creating an access list, remember that, by default, the end of the access list contains an implicit deny statement for everything if it did not find a match before reaching the end. |
|
Create a class map, and enter class-map configuration mode. By default, no class maps are defined.
If neither the match-all or match-any keyword is specified, the default is match-all. Note Because only one match command per class map is supported, the match-all and match-any keywords function the same. |
||
match { access-group acl-index-or-name | ip dscp dscp-list | ip precedence ip-precedence-list } |
Define the match criterion to classify traffic. By default, no match criterion is defined. Only one match criterion per class map is supported, and only one ACL per class map is supported.
|
|
To delete an existing policy map, use the no policy-map policy-map-name global configuration command. To delete an existing class map, use the no class-map [ match-all | match-any ] class-map-name global configuration command. To remove a match criterion, use the no match { access-group acl-index-or-name | ip dscp | ip precedence } class-map configuration command.
This example shows how to configure the class map called class1. The class1 has one match criterion, which is access list 103. It permits traffic from any host to any destination that matches a DSCP value of 10.
This example shows how to create a class map called class2, which matches incoming traffic with DSCP values of 10, 11, and 12.
This example shows how to create a class map called class3, which matches incoming traffic with IP-precedence values of 5, 6, and 7:
Classifying, Policing, and Marking Traffic on Physical Ports by Using Policy Maps

Note![]() To use policing and marking, the switch must be running the LAN Base image.
To use policing and marking, the switch must be running the LAN Base image.
You can configure a policy map on a physical port that specifies which traffic class to act on. Actions can include trusting the CoS, DSCP, or IP precedence values in the traffic class; setting a specific DSCP or IP precedence value in the traffic class; and specifying the traffic bandwidth limitations for each matched traffic class (policer) and the action to take when the traffic is out of profile (marking).
A policy map also has these characteristics:
- A policy map can contain multiple class statements, each with different match criteria and policers.
- A policy map can contain a predefined default traffic class explicitly placed at the end of the map.
- A separate policy-map class can exist for each type of traffic received through a port.
- A policy-map trust state and a port trust state are mutually exclusive, and whichever is configured last takes affect.
Follow these guidelines when configuring policy maps on physical ports:
- You can attach only one policy map per ingress port.
- If you configure the IP-precedence-to-DSCP map by using the mls qos map ip-prec-dscp dscp1...dscp8 global configuration command, the settings only affect packets on ingress interfaces that are configured to trust the IP precedence value. In a policy map, if you set the packet IP precedence value to a new value by using the set ip precedence new-precedence policy-map class configuration command, the egress DSCP value is not affected by the IP-precedence-to-DSCP map. If you want the egress DSCP value to be different than the ingress value, use the set dscp new-dscp policy-map class configuration command.
- If you enter or have used the set ip dscp command, the switch changes this command to set dscp in its configuration.
- You can use the set ip precedence or the set precedence policy-map class configuration command to change the packet IP precedence value. This setting appears as set ip precedence in the switch configuration.
- A policy-map and a port trust state can both run on a physical interface. The policy-map is applied before the port trust state.
- When you configure a default traffic class by using the class class-default policy-map configuration command, unclassified traffic (traffic that does not meet the match criteria specified in the traffic classes) is treated as the default traffic class ( class-default). Class default is not supported on Catalyst 2960-S switches.
Beginning in privileged EXEC mode, follow these steps to create a policy map:
|
|
|
|
|---|---|---|
Create a class map, and enter class-map configuration mode. By default, no class maps are defined.
If neither the match-all or match-any keyword is specified, the default is match-all. Note Because only one match command per class map is supported, the match-all and match-any keywords function the same. |
||
Create a policy map by entering the policy map name, and enter policy-map configuration mode. By default, no policy maps are defined. The default behavior of a policy map is to set the DSCP to 0 if the packet is an IP packet and to set the CoS to 0 if the packet is tagged. No policing is performed. |
||
Defines a traffic classification, and enter policy-map class configuration mode. By default, no policy map class-maps are defined. If a traffic class has already been defined by using the class-map global configuration command, specify its name for class-map-name in this command. A class-default traffic class is pre-defined and can be added to any policy. It is always placed at the end of a policy map. With an implied match any included in the class-default class, all packets that have not already matched the other traffic classes will match class-default. |
||
Configure the trust state, which QoS uses to generate a CoS-based or DSCP-based QoS label. Note This command is mutually exclusive with the set command within the same policy map. If you enter the trust command, go to Step 6. By default, the port is not trusted. If no keyword is specified when the command is entered, the default is dscp. The keywords have these meanings:
For more information, see the “Configuring the CoS-to-DSCP Map” section. |
||
police rate-bps burst-byte [ exceed-action { drop | policed-dscp-transmit }] |
Define a policer for the classified traffic. By default, no policer is defined. For information on the number of policers supported, see the “Standard QoS Configuration Guidelines” section.
For burst-byte, specify the normal burst size in bytes. The range is 8000 to 1000000. On Catalyst 2960-S switches, although you can configure a rate of 8000, the minimum rate granularity is actually 16000.
|
|
Specify the port to attach to the policy map, and enter interface configuration mode. |
||
Specify the policy-map name, and apply it to an ingress port. |
||
To delete an existing policy map, use the no policy-map policy-map-name global configuration command. To delete an existing class map, use the no class class-map-name policy-map configuration command. To return to the untrusted state, use the no trust policy-map configuration command. To remove an assigned DSCP or IP precedence value, use the no set { dscp new-dscp | ip precedence new-precedence } policy-map configuration command. To remove an existing policer, use the no police rate-bps burst-byte [ exceed-action { drop | policed-dscp-transmit }] policy-map configuration command. To remove the policy map and port association, use the no service-policy input policy-map-name interface configuration command.
This example shows how to create a policy map and attach it to an ingress port. In the configuration, the IP standard ACL permits traffic from network 10.1.0.0. For traffic matching this classification, the DSCP value in the incoming packet is trusted. If the matched traffic exceeds an average traffic rate of 48000 b/s and a normal burst size of 8000 bytes, its DSCP is marked down (based on the policed-DSCP map) and sent:
This example shows how to create a Layer 2 MAC ACL with two permit statements and attach it to an ingress port. The first permit statement allows traffic from the host with MAC address 0001.0000.0001 destined for the host with MAC address 0002.0000.0001. The second permit statement allows only Ethertype XNS-IDP traffic from the host with MAC address 0001.0000.0002 destined for the host with MAC address 0002.0000.0002.
This example shows how to create a class map that applies to both IPv4 and IPv6 traffic with the default class applied to unclassified traffic:
This example shows how to configure default traffic class to a policy map:
This example shows how the default traffic class is automatically placed at the end of policy-map pm3 even though class-default was configured first:
Classifying, Policing, and Marking Traffic by Using Aggregate Policers

Note![]() To use policing and marking, the switch must be running the LAN Base image.
To use policing and marking, the switch must be running the LAN Base image.
By using an aggregate policer, you can create a policer that is shared by multiple traffic classes within the same policy map. However, you cannot use the aggregate policer across different policy maps or ports.
Beginning in privileged EXEC mode, follow these steps to create an aggregate policer:
|
|
|
|
|---|---|---|
mls qos aggregate-policer aggregate-policer-name rate-bps burst-byte exceed-action { drop | policed-dscp-transmit } |
Define the policer parameters that can be applied to multiple traffic classes within the same policy map. By default, no aggregate policer is defined. For information on the number of policers supported, see the “Standard QoS Configuration Guidelines” section. For rate-bps, specify average traffic rate in bits per second (b/s). The range is 8000 to 10000000000. (On Catalyst 2960-S switches, although you can configure a rate of 8000, the minimum rate granularity is actually 16000.)
|
|
Create a class map to classify traffic as necessary. For more information, see the “Classifying Traffic by Using Class Maps” section. |
||
Create a policy map by entering the policy map name, and enter policy-map configuration mode. For more information, see the “Classifying, Policing, and Marking Traffic on Physical Ports by Using Policy Maps” section. |
||
Define a traffic classification, and enter policy-map class configuration mode. The class-default keyword is not supported on Catalyst 2960-S switches. For more information, see the “Classifying, Policing, and Marking Traffic on Physical Ports by Using Policy Maps” section. |
||
Apply an aggregate policer to multiple classes in the same policy map. For aggregate-policer-name, enter the name specified in Step 2. |
||
Specify the port to attach to the policy map, and enter interface configuration mode. |
||
Specify the policy-map name, and apply it to an ingress port. |
||
To remove the specified aggregate policer from a policy map, use the no police aggregate aggregate-policer-name policy map configuration mode. To delete an aggregate policer and its parameters, use the no mls qos aggregate-policer aggregate-policer-name global configuration command.
This example shows how to create an aggregate policer and attach it to multiple classes within a policy map. In the configuration, the IP ACLs permit traffic from network 10.1.0.0 and from host 11.3.1.1. For traffic coming from network 10.1.0.0, the DSCP in the incoming packets is trusted. For traffic coming from host 11.3.1.1, the DSCP in the packet is changed to 56. The traffic rate from the 10.1.0.0 network and from host 11.3.1.1 is policed. If the traffic exceeds an average rate of 48000 b/s and a normal burst size of 8000 bytes, its DSCP is marked down (based on the policed-DSCP map) and sent. The policy map is attached to an ingress port.
Configuring DSCP Maps
These sections contain this configuration information:
- Configuring the CoS-to-DSCP Map (optional)
- Configuring the IP-Precedence-to-DSCP Map (optional)
- Configuring the Policed-DSCP Map (optional, unless the null settings in the map are not appropriate)
- Configuring the DSCP-to-CoS Map (optional)
- Configuring the DSCP-to-DSCP-Mutation Map (optional, unless the null settings in the map are not appropriate)
All the maps, except the DSCP-to-DSCP-mutation map, are globally defined and are applied to all ports.
Configuring the CoS-to-DSCP Map
You use the CoS-to-DSCP map to map CoS values in incoming packets to a DSCP value that QoS uses internally to represent the priority of the traffic.
Table 1-12 shows the default CoS-to-DSCP map.
|
|
|
|---|---|
If these values are not appropriate for your network, you need to modify them.
Beginning in privileged EXEC mode, follow these steps to modify the CoS-to-DSCP map. This procedure is optional.
|
|
|
|
|---|---|---|
| For dscp1...dscp8, enter eight DSCP values that correspond to CoS values 0 to 7. Separate each DSCP value with a space. |
||
To return to the default map, use the no mls qos cos-dscp global configuration command.
This example shows how to modify and display the CoS-to-DSCP map:
Configuring the IP-Precedence-to-DSCP Map
You use the IP-precedence-to-DSCP map to map IP precedence values in incoming packets to a DSCP value that QoS uses internally to represent the priority of the traffic.
Table 1-13 shows the default IP-precedence-to-DSCP map:
|
|
|
|---|---|
If these values are not appropriate for your network, you need to modify them.
Beginning in privileged EXEC mode, follow these steps to modify the IP-precedence-to-DSCP map. This procedure is optional.
|
|
|
|
|---|---|---|
Modify the IP-precedence-to-DSCP map. For dscp1...dscp8, enter eight DSCP values that correspond to the IP precedence values 0 to 7. Separate each DSCP value with a space. |
||
To return to the default map, use the no mls qos ip-prec-dscp global configuration command.
This example shows how to modify and display the IP-precedence-to-DSCP map:
Configuring the Policed-DSCP Map
You use the policed-DSCP map to mark down a DSCP value to a new value as the result of a policing and marking action.
The default policed-DSCP map is a null map, which maps an incoming DSCP value to the same DSCP value.
Beginning in privileged EXEC mode, follow these steps to modify the policed-DSCP map. This procedure is optional.
|
|
|
|
|---|---|---|
To return to the default map, use the no mls qos policed-dscp global configuration command.
This example shows how to map DSCP 50 to 57 to a marked-down DSCP value of 0:

Note![]() In this policed-DSCP map, the marked-down DSCP values are shown in the body of the matrix. The d1 column specifies the most-significant digit of the original DSCP; the d2 row specifies the least-significant digit of the original DSCP. The intersection of the d1 and d2 values provides the marked-down value. For example, an original DSCP value of 53 corresponds to a marked-down DSCP value of 0.
In this policed-DSCP map, the marked-down DSCP values are shown in the body of the matrix. The d1 column specifies the most-significant digit of the original DSCP; the d2 row specifies the least-significant digit of the original DSCP. The intersection of the d1 and d2 values provides the marked-down value. For example, an original DSCP value of 53 corresponds to a marked-down DSCP value of 0.
Configuring the DSCP-to-CoS Map
You use the DSCP-to-CoS map to generate a CoS value, which is used to select one of the four egress queues.
Table 1-14 shows the default DSCP-to-CoS map.
|
|
|
|---|---|
If these values are not appropriate for your network, you need to modify them.
Beginning in privileged EXEC mode, follow these steps to modify the DSCP-to-CoS map. This procedure is optional.
|
|
|
|
|---|---|---|
To return to the default map, use the no mls qos dscp-cos global configuration command.
This example shows how to map DSCP values 0, 8, 16, 24, 32, 40, 48, and 50 to CoS value 0 and to display the map:

Note![]() In the above DSCP-to-CoS map, the CoS values are shown in the body of the matrix. The d1 column specifies the most-significant digit of the DSCP; the d2 row specifies the least-significant digit of the DSCP. The intersection of the d1 and d2 values provides the CoS value. For example, in the DSCP-to-CoS map, a DSCP value of 08 corresponds to a CoS value of 0.
In the above DSCP-to-CoS map, the CoS values are shown in the body of the matrix. The d1 column specifies the most-significant digit of the DSCP; the d2 row specifies the least-significant digit of the DSCP. The intersection of the d1 and d2 values provides the CoS value. For example, in the DSCP-to-CoS map, a DSCP value of 08 corresponds to a CoS value of 0.
Configuring the DSCP-to-DSCP-Mutation Map

Note![]() Catalyst 2960-S switches do not support ingress queueing.
Catalyst 2960-S switches do not support ingress queueing.
If two QoS domains have different DSCP definitions, use the DSCP-to-DSCP-mutation map to translate one set of DSCP values to match the definition of another domain. You apply the DSCP-to-DSCP-mutation map to the receiving port (ingress mutation) at the boundary of a QoS administrative domain.
With ingress mutation, the new DSCP value overwrites the one in the packet, and QoS treats the packet with this new value. The switch sends the packet out the port with the new DSCP value.
You can configure multiple DSCP-to-DSCP-mutation maps on an ingress port. The default DSCP-to-DSCP-mutation map is a null map, which maps an incoming DSCP value to the same DSCP value.
Beginning in privileged EXEC mode, follow these steps to modify the DSCP-to-DSCP-mutation map. This procedure is optional.
To return to the default map, use the no mls qos dscp-mutation dscp-mutation-name global configuration command.
This example shows how to define the DSCP-to-DSCP-mutation map. All the entries that are not explicitly configured are not modified (remains as specified in the null map):

Note![]() In the above DSCP-to-DSCP-mutation map, the mutated values are shown in the body of the matrix. The d1 column specifies the most-significant digit of the original DSCP; the d2 row specifies the least-significant digit of the original DSCP. The intersection of the d1 and d2 values provides the mutated value. For example, a DSCP value of 12 corresponds to a mutated value of 10.
In the above DSCP-to-DSCP-mutation map, the mutated values are shown in the body of the matrix. The d1 column specifies the most-significant digit of the original DSCP; the d2 row specifies the least-significant digit of the original DSCP. The intersection of the d1 and d2 values provides the mutated value. For example, a DSCP value of 12 corresponds to a mutated value of 10.
Configuring Ingress Queue Characteristics

Note![]() Catalyst 2960-S switches do not support ingress queueing.
Catalyst 2960-S switches do not support ingress queueing.
Depending on the complexity of your network and your QoS solution, you might need to perform all of the tasks in the next sections. You will need to make decisions about these characteristics:
- Which packets are assigned (by DSCP or CoS value) to each queue?
- What drop percentage thresholds apply to each queue, and which CoS or DSCP values map to each threshold?
- How much of the available buffer space is allocated between the queues?
- How much of the available bandwidth is allocated between the queues?
- Is there traffic (such as voice) that should be given high priority?
Mapping DSCP or CoS Values to an Ingress Queue and Setting WTD Thresholds

Note![]() Catalyst 2960-S switches do not support ingress queueing.
Catalyst 2960-S switches do not support ingress queueing.
You can prioritize traffic by placing packets with particular DSCPs or CoSs into certain queues and adjusting the queue thresholds so that packets with lower priorities are dropped.
Beginning in privileged EXEC mode, follow these steps to map DSCP or CoS values to an ingress queue and to set WTD thresholds. This procedure is optional.
To return to the default CoS input queue threshold map or the default DSCP input queue threshold map, use the no mls qos srr-queue input cos-map or the no mls qos srr-queue input dscp-map global configuration command. To return to the default WTD threshold percentages, use the no mls qos srr-queue input threshold queue-id global configuration command.
This example shows how to map DSCP values 0 to 6 to ingress queue 1 and to threshold 1 with a drop threshold of 50 percent. It maps DSCP values 20 to 26 to ingress queue 1 and to threshold 2 with a drop threshold of 70 percent:
In this example, the DSCP values (0 to 6) are assigned the WTD threshold of 50 percent and will be dropped sooner than the DSCP values (20 to 26) assigned to the WTD threshold of 70 percent.
Allocating Buffer Space Between the Ingress Queues

Note![]() Catalyst 2960-S switches do not support ingress queueing.
Catalyst 2960-S switches do not support ingress queueing.
You define the ratio (allocate the amount of space) with which to divide the ingress buffers between the two queues. The buffer and the bandwidth allocation control how much data can be buffered before packets are dropped.
Beginning in privileged EXEC mode, follow these steps to allocate the buffers between the ingress queues. This procedure is optional.
To return to the default setting, use the no mls qos srr-queue input buffers global configuration command.
This example shows how to allocate 60 percent of the buffer space to ingress queue 1 and 40 percent of the buffer space to ingress queue 2:
Allocating Bandwidth Between the Ingress Queues

Note![]() Catalyst 2960-S switches do not support ingress queueing.
Catalyst 2960-S switches do not support ingress queueing.
You need to specify how much of the available bandwidth is allocated between the ingress queues. The ratio of the weights is the ratio of the frequency in which the SRR scheduler sends packets from each queue. The bandwidth and the buffer allocation control how much data can be buffered before packets are dropped. On ingress queues, SRR operates only in shared mode.
Beginning in privileged EXEC mode, follow these steps to allocate bandwidth between the ingress queues. This procedure is optional.
|
|
|
|
|---|---|---|
Assign shared round robin weights to the ingress queues. The default setting for weight1 and weight2 is 4 (1/2 of the bandwidth is equally shared between the two queues). For weight1 and weight2 , t he range is 1 to 100. Separate each value with a space. SRR services the priority queue for its configured weight as specified by the bandwidth keyword in the mls qos srr-queue input priority-queue queue-id bandwidth weight global configuration command. Then, SRR shares the remaining bandwidth with both ingress queues and services them as specified by the weights configured with the mls qos srr-queue input bandwidth weight1 weight2 global configuration command. For more information, see the “Configuring the Ingress Priority Queue” section. |
||
To return to the default setting, use the no mls qos srr-queue input bandwidth global configuration command.
This example shows how to assign the ingress bandwidth to the queues. Priority queueing is disabled, and the shared bandwidth ratio allocated to queue 1 is 25/(25+75) and to queue 2 is 75/(25+75):
Configuring the Ingress Priority Queue

Note![]() Catalyst 2960-S switches do not support ingress queueing.
Catalyst 2960-S switches do not support ingress queueing.
You should use the priority queue only for traffic that needs to be expedited (for example, voice traffic, which needs minimum delay and jitter).
The priority queue is guaranteed part of the bandwidth to reduce the delay and jitter under heavy network traffic on an oversubscribed ring (when there is more traffic than the backplane can carry, and the queues are full and dropping frames).
SRR services the priority queue for its configured weight as specified by the bandwidth keyword in the mls qos srr-queue input priority-queue queue-id bandwidth weight global configuration command. Then, SRR shares the remaining bandwidth with both ingress queues and services them as specified by the weights configured with the mls qos srr-queue input bandwidth weight1 weight2 global configuration command.
Beginning in privileged EXEC mode, follow these steps to configure the priority queue. This procedure is optional.
To return to the default setting, use the no mls qos srr-queue input priority-queue queue-id global configuration command. To disable priority queueing, set the bandwidth weight to 0, for example, mls qos srr-queue input priority-queue queue-id bandwidth 0 .
This example shows how to assign the ingress bandwidths to the queues. Queue 1 is the priority queue with 10 percent of the bandwidth allocated to it. The bandwidth ratios allocated to queues 1 and 2 is 4/(4+4). SRR services queue 1 (the priority queue) first for its configured 10 percent bandwidth. Then SRR equally shares the remaining 90 percent of the bandwidth between queues 1 and 2 by allocating 45 percent to each queue:
Configuring Egress Queue Characteristics
Depending on the complexity of your network and your QoS solution, you might need to perform all of the tasks in the next sections. You will need to make decisions about these characteristics:
- Which packets are mapped by DSCP or CoS value to each queue and threshold ID?
- What drop percentage thresholds apply to the queue-set (four egress queues per port), and how much reserved and maximum memory is needed for the traffic type?
- How much of the fixed buffer space is allocated to the queue-set?
- Does the bandwidth of the port need to be rate limited?
- How often should the egress queues be serviced and which technique (shaped, shared, or both) should be used?
These sections contain this configuration information:
- Configuration Guidelines
- Allocating Buffer Space to and Setting WTD Thresholds for an Egress Queue-Set (optional)
- Mapping DSCP or CoS Values to an Egress Queue and to a Threshold ID (optional)
- Configuring SRR Shaped Weights on Egress Queues (optional)
- Configuring SRR Shared Weights on Egress Queues (optional)
- Configuring the Egress Expedite Queue (optional)
- Limiting the Bandwidth on an Egress Interface (optional)
Configuration Guidelines
Follow these guidelines when the expedite queue is enabled or the egress queues are serviced based on their SRR weights:
- If the egress expedite queue is enabled, it overrides the SRR shaped and shared weights for queue 1.
- If the egress expedite queue is disabled and the SRR shaped and shared weights are configured, the shaped mode overrides the shared mode for queue 1, and SRR services this queue in shaped mode.
- If the egress expedite queue is disabled and the SRR shaped weights are not configured, SRR services this queue in shared mode.
Allocating Buffer Space to and Setting WTD Thresholds for an Egress Queue-Set
You can guarantee the availability of buffers, set WTD thresholds, and configure the maximum allocation for a queue-set by using the mls qos queue-set output qset-id threshold queue-id drop-threshold1 drop-threshold2 reserved-threshold maximum-threshold global configuration commands.
Each threshold value is a percentage of the queues allocated buffers, which you specify by using the mls qos queue-set output qset-id buffers allocation1... allocation4 global configuration command. The queues use WTD to support distinct drop percentages for different traffic classes.

Note![]() The egress queue default settings are suitable for most situations. You should change them only when you have a thorough understanding of the egress queues and if these settings do not meet your QoS solution.
The egress queue default settings are suitable for most situations. You should change them only when you have a thorough understanding of the egress queues and if these settings do not meet your QoS solution.
Beginning in privileged EXEC mode, follow these steps to configure the memory allocation and to drop thresholds for a queue-set. This procedure is optional.
To return to the default setting, use the no mls qos queue-set output qset-id buffers global configuration command. To return to the default WTD threshold percentages, use the no mls qos queue-set output qset-id threshold [ queue-id ] global configuration command.
This example shows how to map a port to queue-set 2. It allocates 40 percent of the buffer space to egress queue 1 and 20 percent to egress queues 2, 3, and 4. It configures the drop thresholds for queue 2 to 40 and 60 percent of the allocated memory, guarantees (reserves) 100 percent of the allocated memory, and configures 200 percent as the maximum memory that this queue can have before packets are dropped:
Mapping DSCP or CoS Values to an Egress Queue and to a Threshold ID
You can prioritize traffic by placing packets with particular DSCPs or costs of service into certain queues and adjusting the queue thresholds so that packets with lower priorities are dropped.

Note![]() The egress queue default settings are suitable for most situations. You should change them only when you have a thorough understanding of the egress queues and if these settings do not meet your QoS solution.
The egress queue default settings are suitable for most situations. You should change them only when you have a thorough understanding of the egress queues and if these settings do not meet your QoS solution.
Beginning in privileged EXEC mode, follow these steps to map DSCP or CoS values to an egress queue and to a threshold ID. This procedure is optional.
To return to the default DSCP output queue threshold map or the default CoS output queue threshold map, use the no mls qos srr-queue output dscp-map or the no mls qos srr-queue output cos-map global configuration command.
This example shows how to map DSCP values 10 and 11 to egress queue 1 and to threshold 2:
Configuring SRR Shaped Weights on Egress Queues
You can specify how much of the available bandwidth is allocated to each queue. The ratio of the weights is the ratio of frequency in which the SRR scheduler sends packets from each queue.
You can configure the egress queues for shaped or shared weights, or both. Use shaping to smooth bursty traffic or to provide a smoother output over time. For information about shaped weights, see the “SRR Shaping and Sharing” section. For information about shared weights, see the “Configuring SRR Shared Weights on Egress Queues” section.
Beginning in privileged EXEC mode, follow these steps to assign the shaped weights and to enable bandwidth shaping on the four egress queues mapped to a port. This procedure is optional.
To return to the default setting, use the no srr-queue bandwidth shape interface configuration command.
This example shows how to configure bandwidth shaping on queue 1. Because the weight ratios for queues 2, 3, and 4 are set to 0, these queues operate in shared mode. The bandwidth weight for queue 1 is 1/8, which is 12.5 percent:
Configuring SRR Shared Weights on Egress Queues
In shared mode, the queues share the bandwidth among them according to the configured weights. The bandwidth is guaranteed at this level but not limited to it. For example, if a queue empties and does not require a share of the link, the remaining queues can expand into the unused bandwidth and share it among them. With sharing, the ratio of the weights controls the frequency of dequeuing; the absolute values are meaningless.

Note![]() The egress queue default settings are suitable for most situations. You should change them only when you have a thorough understanding of the egress queues and if these settings do not meet your QoS solution.
The egress queue default settings are suitable for most situations. You should change them only when you have a thorough understanding of the egress queues and if these settings do not meet your QoS solution.
Beginning in privileged EXEC mode, follow these steps to assign the shared weights and to enable bandwidth sharing on the four egress queues mapped to a port. This procedure is optional.
To return to the default setting, use the no srr-queue bandwidth share interface configuration command.
This example shows how to configure the weight ratio of the SRR scheduler running on an egress port. Four queues are used, and the bandwidth ratio allocated for each queue in shared mode is 1/(1+2+3+4), 2/(1+2+3+4), 3/(1+2+3+4), and 4/(1+2+3+4), which is 10 percent, 20 percent, 30 percent, and 40 percent for queues 1, 2, 3, and 4. This means that queue 4 has four times the bandwidth of queue 1, twice the bandwidth of queue 2, and one-and-a-third times the bandwidth of queue 3.
Configuring the Egress Expedite Queue
You can ensure that certain packets have priority over all others by queuing them in the egress expedite queue. SRR services this queue until it is empty before servicing the other queues.
Beginning in privileged EXEC mode, follow these steps to enable the egress expedite queue. This procedure is optional.
To disable the egress expedite queue, use the no priority-queue out interface configuration command.
This example shows how to enable the egress expedite queue when the SRR weights are configured. The egress expedite queue overrides the configured SRR weights.
Limiting the Bandwidth on an Egress Interface
You can limit the bandwidth on an egress port. For example, if a customer pays only for a small percentage of a high-speed link, you can limit the bandwidth to that amount.

Note![]() The egress queue default settings are suitable for most situations. You should change them only when you have a thorough understanding of the egress queues and if these settings do not meet your QoS solution.
The egress queue default settings are suitable for most situations. You should change them only when you have a thorough understanding of the egress queues and if these settings do not meet your QoS solution.
Beginning in privileged EXEC mode, follow these steps to limit the bandwidth on an egress port. This procedure is optional.
To return to the default setting, use the no srr-queue bandwidth limit interface configuration command.
This example shows how to limit the bandwidth on a port to 80 percent:
When you configure this command to 80 percent, the port is idle 20 percent of the time. The line rate drops to 80 percent of the connected speed, which is 800 Mb/s. These values are not exact because the hardware adjusts the line rate in increments of six.
Displaying Standard QoS Information
To display standard QoS information, use one or more of the privileged EXEC commands in Table 1-15 :
 Feedback
Feedback