- Index
- Preface
- Overview
- Using the Command-Line Interface
- Assigning the Switch IP Address and Default Gateway
- Configuring Cisco IOS CNS Agents
- Clustering Switches
- Administering the Switch
- Configuring SDM Templates
- Configuring Switch-Based Authentication
- Configuring IEEE 802.1x Port-Based Authentication
- Configuring Interface Characteristics
- Configuring Smartports Macros
- Configuring VLANs
- Configuring VTP
- Configuring Private VLANs
- Configuring Voice VLAN
- Configuring IEEE 802.1Q and Layer 2 Protocol Tunneling
- Configuring STP
- Configuring MSTP
- Configuring Optional Spanning-Tree Features
- Configuring Flex Links
- Configuring DHCP Features and IP Source Guard
- Configuring Dynamic ARP Inspection
- Configuring IGMP Snooping and MVR
- Configuring Port-Based Traffic Control
- Configuring CDP
- Configuring UDLD
- Configuring SPAN and RSPAN
- Configuring RMON
- Configuring System Message Logging
- Configuring SNMP
- Configuring Network Security with ACLs
- Configuring QoS
- Configuring EtherChannels
- Configuring IP Unicast Routing
- Configuring IPv6 Unicast Routing
- Configuring IPv6 MLD Snooping
- Configuring IPv6 ACLs
- Configuring HSRP
- Configuring IP Multicast Routing
- Configuring MSDP
- Configuring Fallback Bridging
- Troubleshooting
- Supported MIBs
- Working with the Cisco IOS File System, Configuration Files, and Software Images
- Unsupported Commands in Cisco IOS Release 12.2(25)SEE
- Understanding VLANs
- Configuring Normal-Range VLANs
- Configuring Extended-Range VLANs
- Displaying VLANs
- Configuring VLAN Trunks
Configuring VLANs
This chapter describes how to configure normal-range VLANs (VLAN IDs 1 to 1005) and extended-range VLANs (VLAN IDs 1006 to 4094) on the Catalyst 3560 switch. It includes information about VLAN membership modes, VLAN configuration modes, VLAN trunks, and dynamic VLAN assignment from a VLAN Membership Policy Server (VMPS).

Note ![]() For complete syntax and usage information for the commands used in this chapter, see the command reference for this release.
For complete syntax and usage information for the commands used in this chapter, see the command reference for this release.
The chapter consists of these sections:
•![]() Configuring Normal-Range VLANs
Configuring Normal-Range VLANs
•![]() Configuring Extended-Range VLANs
Configuring Extended-Range VLANs
Understanding VLANs
A VLAN is a switched network that is logically segmented by function, project team, or application, without regard to the physical locations of the users. VLANs have the same attributes as physical LANs, but you can group end stations even if they are not physically located on the same LAN segment. Any switch port can belong to a VLAN, and unicast, broadcast, and multicast packets are forwarded and flooded only to end stations in the VLAN. Each VLAN is considered a logical network, and packets destined for stations that do not belong to the VLAN must be forwarded through a router or a switch supporting fallback bridging, as shown in Figure 12-1. Because a VLAN is considered a separate logical network, it contains its own bridge Management Information Base (MIB) information and can support its own implementation of spanning tree. See "Configuring STP."

Note ![]() Before you create VLANs, you must decide whether to use VLAN Trunking Protocol (VTP) to maintain global VLAN configuration for your network. For more information on VTP, see "Configuring VTP."
Before you create VLANs, you must decide whether to use VLAN Trunking Protocol (VTP) to maintain global VLAN configuration for your network. For more information on VTP, see "Configuring VTP."
Figure 12-1 shows an example of VLANs segmented into logically defined networks.
Figure 12-1 VLANs as Logically Defined Networks

VLANs are often associated with IP subnetworks. For example, all the end stations in a particular IP subnet belong to the same VLAN. Interface VLAN membership on the switch is assigned manually on an interface-by-interface basis. When you assign switch interfaces to VLANs by using this method, it is known as interface-based, or static, VLAN membership.
Traffic between VLANs must be routed or fallback bridged. The switch can route traffic between VLANs by using switch virtual interfaces (SVIs). An SVI must be explicitly configured and assigned an IP address to route traffic between VLANs. For more information, see the "Switch Virtual Interfaces" section and the "Configuring Layer 3 Interfaces" section.

Note ![]() If you plan to configure many VLANs on the switch and to not enable routing, you can use the sdm prefer vlan global configuration command to set the Switch Database Management (sdm) feature to the VLAN template, which configures system resources to support the maximum number of unicast MAC addresses. For more information on the SDM templates, see "Configuring SDM Templates," or see the sdm prefer command in the command reference for this release.
If you plan to configure many VLANs on the switch and to not enable routing, you can use the sdm prefer vlan global configuration command to set the Switch Database Management (sdm) feature to the VLAN template, which configures system resources to support the maximum number of unicast MAC addresses. For more information on the SDM templates, see "Configuring SDM Templates," or see the sdm prefer command in the command reference for this release.
Supported VLANs
The switch supports VLANs in VTP client, server, and transparent modes. VLANs are identified by a number from 1 to 4094. VLAN IDs 1002 through 1005 are reserved for Token Ring and FDDI VLANs. VTP only learns normal-range VLANs, with VLAN IDs 1 to 1005; VLAN IDs greater than 1005 are extended-range VLANs and are not stored in the VLAN database. The switch must be in VTP transparent mode when you create VLAN IDs from 1006 to 4094.
Although the switch supports a total of 1005 (normal range and extended range) VLANs, the number of routed ports, SVIs, and other configured features affects the use of the switch hardware.
The switch supports per-VLAN spanning-tree plus (PVST+) or rapid PVST+ with a maximum of 128 spanning-tree instances. One spanning-tree instance is allowed per VLAN. See the "Normal-Range VLAN Configuration Guidelines" section for more information about the number of spanning-tree instances and the number of VLANs. The switch supports both Inter-Switch Link (ISL) and IEEE 802.1Q trunking methods for sending VLAN traffic over Ethernet ports.
VLAN Port Membership Modes
You configure a port to belong to a VLAN by assigning a membership mode that specifies the kind of traffic the port carries and the number of VLANs to which it can belong. Table 12-1 lists the membership modes and membership and VTP characteristics.
|
|
|
|
|---|---|---|
Static-access |
A static-access port can belong to one VLAN and is manually assigned to that VLAN. For more information, see the "Assigning Static-Access Ports to a VLAN" section. |
VTP is not required. If you do not want VTP to globally propagate information, set the VTP mode to transparent. To participate in VTP, there must be at least one trunk port on the switch connected to a trunk port of a second switch. |
Trunk (ISL or |
A trunk port is a member of all VLANs by default, including extended-range VLANs, but membership can be limited by configuring the allowed-VLAN list. You can also modify the pruning-eligible list to block flooded traffic to VLANs on trunk ports that are included in the list. For information about configuring trunk ports, see the "Configuring an Ethernet Interface as a Trunk Port" section. |
VTP is recommended but not required. VTP maintains VLAN configuration consistency by managing the addition, deletion, and renaming of VLANs on a network-wide basis. VTP exchanges VLAN configuration messages with other switches over trunk links. |
Dynamic access |
A dynamic-access port can belong to one VLAN (VLAN ID 1 to 4094) and is dynamically assigned by a VMPS. The VMPS can be a Catalyst 5000 or Catalyst 6500 series switch, for example, but never a Catalyst 3560 switch. The Catalyst 3560 switch is a VMPS client. You can have dynamic-access ports and trunk ports on the same switch, but you must connect the dynamic-access port to an end station or hub and not to another switch. For configuration information, see the "Configuring Dynamic-Access Ports on VMPS Clients" section. |
VTP is required. Configure the VMPS and the client with the same VTP domain name. To participate in VTP, at least one trunk port on the switch must be connected to a trunk port of a second switch. |
Voice VLAN |
A voice VLAN port is an access port attached to a Cisco IP Phone, configured to use one VLAN for voice traffic and another VLAN for data traffic from a device attached to the phone. For more information about voice VLAN ports, see "Configuring Voice VLAN." |
VTP is not required; it has no affect on a voice VLAN. |
Private VLAN |
A private VLAN port is a host or promiscuous port that belongs to a private VLAN primary or secondary VLAN. For information about private VLANs, see "Configuring Private VLANs." |
The switch must be in VTP transparent mode when you configure private VLANs. When private VLANs are configured on the switch, do not change VTP mode from transparent to client or server mode. |
Tunnel |
Tunnel ports are used for IEEE 802.1Q tunneling to maintain customer VLAN integrity across a service-provider network. You configure a tunnel port on an edge switch in the service-provider network and connect it to an IEEE 802.1Q trunk port on a customer interface, creating an asymetric link. A tunnel port belongs to a single VLAN that is dedicated to tunneling. For more information about tunnel ports, see Chapter 16, "Configuring IEEE 802.1Q and Layer 2 Protocol Tunneling." |
VTP is not required. You manually assign the tunnel port to a VLAN by using the switchport access vlan interface configuration command. |
For more detailed definitions of access and trunk modes and their functions, see Table 12-4.
When a port belongs to a VLAN, the switch learns and manages the addresses associated with the port on a per-VLAN basis. For more information, see the "Managing the MAC Address Table" section.
Configuring Normal-Range VLANs
Normal-range VLANs are VLANs with VLAN IDs 1 to 1005. If the switch is in VTP server or VTP transparent mode, you can add, modify or remove configurations for VLANs 2 to 1001 in the VLAN database. (VLAN IDs 1 and 1002 to 1005 are automatically created and cannot be removed.)

Note ![]() When the switch is in VTP transparent mode, you can also create extended-range VLANs (VLANs with IDs from 1006 to 4094), but these VLANs are not saved in the VLAN database. See the "Configuring Extended-Range VLANs" section.
When the switch is in VTP transparent mode, you can also create extended-range VLANs (VLANs with IDs from 1006 to 4094), but these VLANs are not saved in the VLAN database. See the "Configuring Extended-Range VLANs" section.
Configurations for VLAN IDs 1 to 1005 are written to the file vlan.dat (VLAN database), and you can display them by entering the show vlan privileged EXEC command. The vlan.dat file is stored in flash memory.

You use the interface configuration mode to define the port membership mode and to add and remove ports from VLANs. The results of these commands are written to the running-configuration file, and you can display the file by entering the show running-config privileged EXEC command.
You can set these parameters when you create a new normal-range VLAN or modify an existing VLAN in the VLAN database:
•![]() VLAN ID
VLAN ID
•![]() VLAN name
VLAN name
•![]() VLAN type (Ethernet, Fiber Distributed Data Interface [FDDI], FDDI network entity title [NET], TrBRF, or TrCRF, Token Ring, Token Ring-Net)
VLAN type (Ethernet, Fiber Distributed Data Interface [FDDI], FDDI network entity title [NET], TrBRF, or TrCRF, Token Ring, Token Ring-Net)
•![]() VLAN state (active or suspended)
VLAN state (active or suspended)
•![]() Maximum transmission unit (MTU) for the VLAN
Maximum transmission unit (MTU) for the VLAN
•![]() Security Association Identifier (SAID)
Security Association Identifier (SAID)
•![]() Bridge identification number for TrBRF VLANs
Bridge identification number for TrBRF VLANs
•![]() Ring number for FDDI and TrCRF VLANs
Ring number for FDDI and TrCRF VLANs
•![]() Parent VLAN number for TrCRF VLANs
Parent VLAN number for TrCRF VLANs
•![]() Spanning Tree Protocol (STP) type for TrCRF VLANs
Spanning Tree Protocol (STP) type for TrCRF VLANs
•![]() VLAN number to use when translating from one VLAN type to another
VLAN number to use when translating from one VLAN type to another

Note ![]() This section does not provide configuration details for most of these parameters. For complete information on the commands and parameters that control VLAN configuration, see the command reference for this release.
This section does not provide configuration details for most of these parameters. For complete information on the commands and parameters that control VLAN configuration, see the command reference for this release.
These sections contain normal-range VLAN configuration information:
•![]() Normal-Range VLAN Configuration Guidelines
Normal-Range VLAN Configuration Guidelines
•![]() VLAN Configuration Mode Options
VLAN Configuration Mode Options
•![]() Default Ethernet VLAN Configuration
Default Ethernet VLAN Configuration
•![]() Creating or Modifying an Ethernet VLAN
Creating or Modifying an Ethernet VLAN
•![]() Assigning Static-Access Ports to a VLAN
Assigning Static-Access Ports to a VLAN
Token Ring VLANs
Although the switch does not support Token Ring connections, a remote device such as a Catalyst 5000 series switch with Token Ring connections could be managed from one of the supported switches. Switches running VTP Version 2 advertise information about these Token Ring VLANs:
•![]() Token Ring TrBRF VLANs
Token Ring TrBRF VLANs
•![]() Token Ring TrCRF VLANs
Token Ring TrCRF VLANs
For more information on configuring Token Ring VLANs, see the Catalyst 5000 Series Software Configuration Guide.
Normal-Range VLAN Configuration Guidelines
Follow these guidelines when creating and modifying normal-range VLANs in your network:
•![]() The switch supports 1005 VLANs in VTP client, server, and transparent modes.
The switch supports 1005 VLANs in VTP client, server, and transparent modes.
•![]() Normal-range VLANs are identified with a number between 1 and 1001. VLAN numbers 1002 through 1005 are reserved for Token Ring and FDDI VLANs.
Normal-range VLANs are identified with a number between 1 and 1001. VLAN numbers 1002 through 1005 are reserved for Token Ring and FDDI VLANs.
•![]() VLAN configuration for VLANs 1 to 1005 are always saved in the VLAN database. If the VTP mode is transparent, VTP and VLAN configuration are also saved in the switch running configuration file.
VLAN configuration for VLANs 1 to 1005 are always saved in the VLAN database. If the VTP mode is transparent, VTP and VLAN configuration are also saved in the switch running configuration file.
•![]() The switch also supports VLAN IDs 1006 through 4094 in VTP transparent mode (VTP disabled). These are extended-range VLANs and configuration options are limited. Extended-range VLANs are not saved in the VLAN database. See the "Configuring Extended-Range VLANs" section.
The switch also supports VLAN IDs 1006 through 4094 in VTP transparent mode (VTP disabled). These are extended-range VLANs and configuration options are limited. Extended-range VLANs are not saved in the VLAN database. See the "Configuring Extended-Range VLANs" section.
•![]() Before you can create a VLAN, the switch must be in VTP server mode or VTP transparent mode. If the switch is a VTP server, you must define a VTP domain or VTP will not function.
Before you can create a VLAN, the switch must be in VTP server mode or VTP transparent mode. If the switch is a VTP server, you must define a VTP domain or VTP will not function.
•![]() The switch does not support Token Ring or FDDI media. The switch does not forward FDDI, FDDI-Net, TrCRF, or TrBRF traffic, but it does propagate the VLAN configuration through VTP.
The switch does not support Token Ring or FDDI media. The switch does not forward FDDI, FDDI-Net, TrCRF, or TrBRF traffic, but it does propagate the VLAN configuration through VTP.
•![]() The switch supports 128 spanning-tree instances. If a switch has more active VLANs than supported spanning-tree instances, spanning tree can be enabled on 128 VLANs and is disabled on the remaining VLANs. If you have already used all available spanning-tree instances on a switch, adding another VLAN anywhere in the VTP domain creates a VLAN on that switch that is not running spanning-tree. If you have the default allowed list on the trunk ports of that switch (which is to allow all VLANs), the new VLAN is carried on all trunk ports. Depending on the topology of the network, this could create a loop in the new VLAN that would not be broken, particularly if there are several adjacent switches that all have run out of spanning-tree instances. You can prevent this possibility by setting allowed lists on the trunk ports of switches that have used up their allocation of spanning-tree instances.
The switch supports 128 spanning-tree instances. If a switch has more active VLANs than supported spanning-tree instances, spanning tree can be enabled on 128 VLANs and is disabled on the remaining VLANs. If you have already used all available spanning-tree instances on a switch, adding another VLAN anywhere in the VTP domain creates a VLAN on that switch that is not running spanning-tree. If you have the default allowed list on the trunk ports of that switch (which is to allow all VLANs), the new VLAN is carried on all trunk ports. Depending on the topology of the network, this could create a loop in the new VLAN that would not be broken, particularly if there are several adjacent switches that all have run out of spanning-tree instances. You can prevent this possibility by setting allowed lists on the trunk ports of switches that have used up their allocation of spanning-tree instances.
If the number of VLANs on the switch exceeds the number of supported spanning-tree instances, we recommend that you configure the IEEE 802.1s Multiple STP (MSTP) on your switch to map multiple VLANs to a single spanning-tree instance. For more information about MSTP, see "Configuring MSTP."
VLAN Configuration Mode Options
You can configure normal-range VLANs (with VLAN IDs 1 to 1005) by using these two configuration modes:
•![]() VLAN Configuration in config-vlan Mode
VLAN Configuration in config-vlan Mode
You access config-vlan mode by entering the vlan vlan-id global configuration command.
•![]() VLAN Configuration in VLAN Database Configuration Mode
VLAN Configuration in VLAN Database Configuration Mode
You access VLAN database configuration mode by entering the vlan database privileged EXEC command.
VLAN Configuration in config-vlan Mode
To access config-vlan mode, enter the vlan global configuration command with a VLAN ID. Enter a new VLAN ID to create a VLAN, or enter an existing VLAN ID to modify that VLAN. You can use the default VLAN configuration (Table 12-2) or enter multiple commands to configure the VLAN. For more information about commands available in this mode, see the vlan global configuration command description in the command reference for this release. When you have finished the configuration, you must exit config-vlan mode for the configuration to take effect. To display the VLAN configuration, enter the show vlan privileged EXEC command.
You must use this config-vlan mode when creating extended-range VLANs (VLAN IDs greater than 1005). See the "Configuring Extended-Range VLANs" section.
VLAN Configuration in VLAN Database Configuration Mode
To access VLAN database configuration mode, enter the vlan database privileged EXEC command. Then enter the vlan command with a new VLAN ID to create a VLAN, or enter an existing VLAN ID to modify the VLAN. You can use the default VLAN configuration (Table 12-2) or enter multiple commands to configure the VLAN. For more information about keywords available in this mode, see the vlan VLAN database configuration command description in the command reference for this release. When you have finished the configuration, you must enter apply or exit for the configuration to take effect. When you enter the exit command, it applies all commands and updates the VLAN database. VTP messages are sent to other switches in the VTP domain, and the privileged EXEC mode prompt appears.
Saving VLAN Configuration
The configurations of VLAN IDs 1 to 1005 are always saved in the VLAN database (vlan.dat file). If the VTP mode is transparent, they are also saved in the switch running configuration file. You can enter the copy running-config startup-config privileged EXEC command to save the configuration in the startup configuration file. To display the VLAN configuration, enter the show vlan privileged EXEC command.
When you save VLAN and VTP information (including extended-range VLAN configuration information) in the startup configuration file and reboot the switch, the switch configuration is selected as follows:
•![]() If the VTP mode is transparent in the startup configuration, and the VLAN database and the VTP domain name from the VLAN database matches that in the startup configuration file, the VLAN database is ignored (cleared), and the VTP and VLAN configurations in the startup configuration file are used. The VLAN database revision number remains unchanged in the VLAN database.
If the VTP mode is transparent in the startup configuration, and the VLAN database and the VTP domain name from the VLAN database matches that in the startup configuration file, the VLAN database is ignored (cleared), and the VTP and VLAN configurations in the startup configuration file are used. The VLAN database revision number remains unchanged in the VLAN database.
•![]() If the VTP mode or domain name in the startup configuration does not match the VLAN database, the domain name and VTP mode and configuration for the first 1005 VLANs use the VLAN database information.
If the VTP mode or domain name in the startup configuration does not match the VLAN database, the domain name and VTP mode and configuration for the first 1005 VLANs use the VLAN database information.
•![]() If VTP mode is server, the domain name and VLAN configuration for the first 1005 VLANs use the VLAN database information
If VTP mode is server, the domain name and VLAN configuration for the first 1005 VLANs use the VLAN database information

Default Ethernet VLAN Configuration
Table 12-2 shows the default configuration for Ethernet VLANs.

Note ![]() The switch supports Ethernet interfaces exclusively. Because FDDI and Token Ring VLANs are not locally supported, you only configure FDDI and Token Ring media-specific characteristics for VTP global advertisements to other switches.
The switch supports Ethernet interfaces exclusively. Because FDDI and Token Ring VLANs are not locally supported, you only configure FDDI and Token Ring media-specific characteristics for VTP global advertisements to other switches.
Creating or Modifying an Ethernet VLAN
Each Ethernet VLAN in the VLAN database has a unique, 4-digit ID that can be a number from 1 to 1001. VLAN IDs 1002 to 1005 are reserved for Token Ring and FDDI VLANs. To create a normal-range VLAN to be added to the VLAN database, assign a number and name to the VLAN.

Note ![]() When the switch is in VTP transparent mode, you can assign VLAN IDs greater than 1006, but they are not added to the VLAN database. See the "Configuring Extended-Range VLANs" section.
When the switch is in VTP transparent mode, you can assign VLAN IDs greater than 1006, but they are not added to the VLAN database. See the "Configuring Extended-Range VLANs" section.
For the list of default parameters that are assigned when you add a VLAN, see the "Configuring Normal-Range VLANs" section.
Beginning in privileged EXEC mode, follow these steps to use config-vlan mode to create or modify an Ethernet VLAN:
|
|
|
|
|---|---|---|
Step 1 |
configure terminal |
Enter global configuration mode. |
Step 2 |
vlan vlan-id |
Enter a VLAN ID, and enter config-vlan mode. Enter a new VLAN ID to create a VLAN, or enter an existing VLAN ID to modify that VLAN. Note |
Step 3 |
name vlan-name |
(Optional) Enter a name for the VLAN. If no name is entered for the VLAN, the default is to append the vlan-id with leading zeros to the word VLAN. For example, VLAN0004 is a default VLAN name for VLAN 4. |
Step 4 |
mtu mtu-size |
(Optional) Change the MTU size (or other VLAN characteristic). |
Step 5 |
remote-span |
(Optional) Configure the VLAN as the RSPAN VLAN for a remote SPAN session. For more information on remote SPAN, see "Configuring SPAN and RSPAN." |
Step 6 |
end |
Return to privileged EXEC mode. |
Step 7 |
show vlan {name vlan-name | id vlan-id} |
Verify your entries. |
Step 8 |
copy running-config startup config |
(Optional) If the switch is in VTP transparent mode, the VLAN configuration is saved in the running configuration file as well as in the VLAN database. This saves the configuration in the switch startup configuration file. |
To return the VLAN name to the default settings, use the no name, no mtu, or no remote-span config-vlan commands.
This example shows how to use config-vlan mode to create Ethernet VLAN 20, name it test20, and add it to the VLAN database:
Switch# configure terminal
Switch(config)# vlan 20
Switch(config-vlan)# name test20
Switch(config-vlan)# end
You can also create or modify Ethernet VLANs by using the VLAN database configuration mode.

Note ![]() VLAN database configuration mode does not support RSPAN VLAN configuration or extended-range VLANs.
VLAN database configuration mode does not support RSPAN VLAN configuration or extended-range VLANs.
Beginning in privileged EXEC mode, follow these steps to use VLAN database configuration mode to create or modify an Ethernet VLAN:
To return the VLAN name to the default settings, use the no vlan vlan-id name or no vlan vlan-id mtu VLAN database configuration command.
This example shows how to use VLAN configuration mode to create Ethernet VLAN 20, name it test20, and add it to the VLAN database:
Switch# vlan database
Switch(vlan)# vlan 20 name test20
Switch(vlan)# exit
APPLY completed.
Exiting....
Deleting a VLAN
When you delete a VLAN from a switch that is in VTP server mode, the VLAN is removed from the VLAN database for all switches in the VTP domain. When you delete a VLAN from a switch that is in VTP transparent mode, the VLAN is deleted only on that specific switch.
You cannot delete the default VLANs for the different media types: Ethernet VLAN 1 and FDDI or Token Ring VLANs 1002 to 1005.

Beginning in privileged EXEC mode, follow these steps to delete a VLAN on the switch:
To delete a VLAN by using VLAN database configuration mode, use the vlan database privileged EXEC command to enter VLAN database configuration mode and the no vlan vlan-id VLAN database configuration command.
Assigning Static-Access Ports to a VLAN
You can assign a static-access port to a VLAN without having VTP globally propagate VLAN configuration information by disabling VTP (VTP transparent mode).
If you are assigning a port on a cluster member switch to a VLAN, first use the rcommand privileged EXEC command to log in to the cluster member switch.

Note ![]() If you assign an interface to a VLAN that does not exist, the new VLAN is created. (See the "Creating or Modifying an Ethernet VLAN" section.)
If you assign an interface to a VLAN that does not exist, the new VLAN is created. (See the "Creating or Modifying an Ethernet VLAN" section.)
Beginning in privileged EXEC mode, follow these steps to assign a port to a VLAN in the VLAN database:
To return an interface to its default configuration, use the default interface interface-id interface configuration command.
This example shows how to configure a port as an access port in VLAN 2:
Switch# configure terminal
Enter configuration commands, one per line. End with CNTL/Z.
Switch(config)# interface gigabitethernet0/1
Switch(config-if)# switchport mode access
Switch(config-if)# switchport access vlan 2
Switch(config-if)# end
Configuring Extended-Range VLANs
When the switch is in VTP transparent mode (VTP disabled), you can create extended-range VLANs (in the range 1006 to 4094). Extended-range VLANs enable service providers to extend their infrastructure to a greater number of customers. The extended-range VLAN IDs are allowed for any switchport commands that allow VLAN IDs. You always use config-vlan mode (accessed by entering the vlan vlan-id global configuration command) to configure extended-range VLANs. The extended range is not supported in VLAN database configuration mode (accessed by entering the vlan database privileged EXEC command).
Extended-range VLAN configurations are not stored in the VLAN database, but because VTP mode is transparent, they are stored in the switch running configuration file, and you can save the configuration in the startup configuration file by using the copy running-config startup-config privileged EXEC command.

Note ![]() Although the switch supports 4094 VLAN IDs, see the "Supported VLANs" section for the actual number of VLANs supported.
Although the switch supports 4094 VLAN IDs, see the "Supported VLANs" section for the actual number of VLANs supported.
These sections contain extended-range VLAN configuration information:
•![]() Extended-Range VLAN Configuration Guidelines
Extended-Range VLAN Configuration Guidelines
•![]() Creating an Extended-Range VLAN
Creating an Extended-Range VLAN
•![]() Creating an Extended-Range VLAN with an Internal VLAN ID
Creating an Extended-Range VLAN with an Internal VLAN ID
Default VLAN Configuration
See Table 12-2 for the default configuration for Ethernet VLANs. You can change only the MTU size, private VLAN, and the remote SPAN configuration state on extended-range VLANs; all other characteristics must remain at the default state.
Extended-Range VLAN Configuration Guidelines
Follow these guidelines when creating extended-range VLANs:
•![]() To add an extended-range VLAN, you must use the vlan vlan-id global configuration command and access config-vlan mode. You cannot add extended-range VLANs in VLAN database configuration mode (accessed by entering the vlan database privileged EXEC command).
To add an extended-range VLAN, you must use the vlan vlan-id global configuration command and access config-vlan mode. You cannot add extended-range VLANs in VLAN database configuration mode (accessed by entering the vlan database privileged EXEC command).
•![]() VLAN IDs in the extended range are not saved in the VLAN database and are not recognized by VTP.
VLAN IDs in the extended range are not saved in the VLAN database and are not recognized by VTP.
•![]() You cannot include extended-range VLANs in the pruning eligible range.
You cannot include extended-range VLANs in the pruning eligible range.
•![]() The switch must be in VTP transparent mode when you create extended-range VLANs. If VTP mode is server or client, an error message is generated, and the extended-range VLAN is rejected.
The switch must be in VTP transparent mode when you create extended-range VLANs. If VTP mode is server or client, an error message is generated, and the extended-range VLAN is rejected.
•![]() You can set the VTP mode to transparent in global configuration mode or in VLAN database configuration mode. See the "Disabling VTP (VTP Transparent Mode)" section. You should save this configuration to the startup configuration so that the switch boots up in VTP transparent mode. Otherwise, you lose the extended-range VLAN configuration if the switch resets.
You can set the VTP mode to transparent in global configuration mode or in VLAN database configuration mode. See the "Disabling VTP (VTP Transparent Mode)" section. You should save this configuration to the startup configuration so that the switch boots up in VTP transparent mode. Otherwise, you lose the extended-range VLAN configuration if the switch resets.
•![]() STP is enabled by default on extended-range VLANs, but you can disable it by using the no spanning-tree vlan vlan-id global configuration command. When the maximum number of spanning-tree instances are on the switch, spanning tree is disabled on any newly created VLANs. If the number of VLANs on the switch exceeds the maximum number of spanning-tree instances, we recommend that you configure the IEEE 802.1s Multiple STP (MSTP) on your switch to map multiple VLANs to a single spanning-tree instance. For more information about MSTP, see "Configuring MSTP."
STP is enabled by default on extended-range VLANs, but you can disable it by using the no spanning-tree vlan vlan-id global configuration command. When the maximum number of spanning-tree instances are on the switch, spanning tree is disabled on any newly created VLANs. If the number of VLANs on the switch exceeds the maximum number of spanning-tree instances, we recommend that you configure the IEEE 802.1s Multiple STP (MSTP) on your switch to map multiple VLANs to a single spanning-tree instance. For more information about MSTP, see "Configuring MSTP."
•![]() Each routed port on the switch creates an internal VLAN for its use. These internal VLANs use extended-range VLAN numbers, and the internal VLAN ID cannot be used for an extended-range VLAN. If you try to create an extended-range VLAN with a VLAN ID that is already allocated as an internal VLAN, an error message is generated, and the command is rejected.
Each routed port on the switch creates an internal VLAN for its use. These internal VLANs use extended-range VLAN numbers, and the internal VLAN ID cannot be used for an extended-range VLAN. If you try to create an extended-range VLAN with a VLAN ID that is already allocated as an internal VLAN, an error message is generated, and the command is rejected.
–![]() Because internal VLAN IDs are in the lower part of the extended range, we recommend that you create extended-range VLANs beginning from the highest number (4094) and moving to the lowest (1006) to reduce the possibility of using an internal VLAN ID.
Because internal VLAN IDs are in the lower part of the extended range, we recommend that you create extended-range VLANs beginning from the highest number (4094) and moving to the lowest (1006) to reduce the possibility of using an internal VLAN ID.
–![]() Before configuring extended-range VLANs, enter the show vlan internal usage privileged EXEC command to see which VLANs have been allocated as internal VLANs.
Before configuring extended-range VLANs, enter the show vlan internal usage privileged EXEC command to see which VLANs have been allocated as internal VLANs.
–![]() If necessary, you can shut down the routed port assigned to the internal VLAN, which frees up the internal VLAN, and then create the extended-range VLAN and re-enable the port, which then uses another VLAN as its internal VLAN. See the "Creating an Extended-Range VLAN with an Internal VLAN ID" section.
If necessary, you can shut down the routed port assigned to the internal VLAN, which frees up the internal VLAN, and then create the extended-range VLAN and re-enable the port, which then uses another VLAN as its internal VLAN. See the "Creating an Extended-Range VLAN with an Internal VLAN ID" section.
•![]() Although the switch supports a total of 1005 (normal-range and extended-range) VLANs, the number of routed ports, SVIs, and other configured features affects the use of the switch hardware. If you try to create an extended-range VLAN and there are not enough hardware resources available, an error message is generated, and the extended-range VLAN is rejected.
Although the switch supports a total of 1005 (normal-range and extended-range) VLANs, the number of routed ports, SVIs, and other configured features affects the use of the switch hardware. If you try to create an extended-range VLAN and there are not enough hardware resources available, an error message is generated, and the extended-range VLAN is rejected.
Creating an Extended-Range VLAN
You create an extended-range VLAN in global configuration mode by entering the vlan global configuration command with a VLAN ID from 1006 to 4094. This command accesses the config-vlan mode. The extended-range VLAN has the default Ethernet VLAN characteristics (see Table 12-2) and the MTU size, private VLAN, and RSPAN configuration are the only parameters you can change. See the description of the vlan global configuration command in the command reference for the default settings of all parameters. If you enter an extended-range VLAN ID when the switch is not in VTP transparent mode, an error message is generated when you exit from config-vlan mode, and the extended-range VLAN is not created.
Extended-range VLANs are not saved in the VLAN database; they are saved in the switch running configuration file. You can save the extended-range VLAN configuration in the switch startup configuration file by using the copy running-config startup-config privileged EXEC command.

Note ![]() Before you create an extended-range VLAN, you can verify that the VLAN ID is not used internally by entering the show vlan internal usage privileged EXEC command. If the VLAN ID is used internally and you want to free it up, go to the"Creating an Extended-Range VLAN with an Internal VLAN ID" section before creating the extended-range VLAN.
Before you create an extended-range VLAN, you can verify that the VLAN ID is not used internally by entering the show vlan internal usage privileged EXEC command. If the VLAN ID is used internally and you want to free it up, go to the"Creating an Extended-Range VLAN with an Internal VLAN ID" section before creating the extended-range VLAN.
Beginning in privileged EXEC mode, follow these steps to create an extended-range VLAN:
|
|
|
|
|---|---|---|
Step 1 |
configure terminal |
Enter global configuration mode. |
Step 2 |
vtp mode transparent |
Configure the switch for VTP transparent mode, disabling VTP. |
Step 3 |
vlan vlan-id |
Enter an extended-range VLAN ID and enter config-vlan mode. The range is 1006 to 4094. |
Step 4 |
mtu mtu-size |
(Optional) Modify the VLAN by changing the MTU size. Note |
Step 5 |
remote-span |
(Optional) Configure the VLAN as the RSPAN VLAN. See the "Configuring a VLAN as an RSPAN VLAN" section. |
Step 6 |
end |
Return to privileged EXEC mode. |
Step 7 |
show vlan id vlan-id |
Verify that the VLAN has been created. |
Step 8 |
copy running-config startup config |
Save your entries in the switch startup configuration file. To save extended-range VLAN configurations, you need to save the VTP transparent mode configuration and the extended-range VLAN configuration in the switch startup configuration file. Otherwise, if the switch resets, it will default to VTP server mode, and the extended-range VLAN IDs will not be saved. |
To delete an extended-range VLAN, use the no vlan vlan-id global configuration command.
The procedure for assigning static-access ports to an extended-range VLAN is the same as for normal-range VLANs. See the "Assigning Static-Access Ports to a VLAN" section.
This example shows how to create a new extended-range VLAN with all default characteristics, enter config-vlan mode, and save the new VLAN in the switch startup configuration file:
Switch(config)# vtp mode transparent
Switch(config)# vlan 2000
Switch(config-vlan)# end
Switch# copy running-config startup config
Creating an Extended-Range VLAN with an Internal VLAN ID
If you enter an extended-range VLAN ID that is already assigned to an internal VLAN, an error message is generated, and the extended-range VLAN is rejected. To manually free an internal VLAN ID, you must temporarily shut down the routed port that is using the internal VLAN ID.
Beginning in privileged EXEC mode, follow these steps to release a VLAN ID that is assigned to an internal VLAN and to create an extended-range VLAN with that ID:
Displaying VLANs
Use the show vlan privileged EXEC command to display a list of all VLANs on the switch, including extended-range VLANs. The display includes VLAN status, ports, and configuration information. To view normal-range VLANs in the VLAN database (1 to 1005), use the show VLAN database configuration command (accessed by entering the vlan database privileged EXEC command).
Table 12-3 lists the commands for monitoring VLANs.
For more details about the show command options and explanations of output fields, see the command reference for this release.
Configuring VLAN Trunks
These sections contain this conceptual information:
•![]() Default Layer 2 Ethernet Interface VLAN Configuration
Default Layer 2 Ethernet Interface VLAN Configuration
•![]() Configuring an Ethernet Interface as a Trunk Port
Configuring an Ethernet Interface as a Trunk Port
•![]() Configuring Trunk Ports for Load Sharing
Configuring Trunk Ports for Load Sharing
Trunking Overview
A trunk is a point-to-point link between one or more Ethernet switch interfaces and another networking device such as a router or a switch. Ethernet trunks carry the traffic of multiple VLANs over a single link, and you can extend the VLANs across an entire network.
Two trunking encapsulations are available on all Ethernet interfaces:
•![]() Inter-Switch Link (ISL)—Cisco-proprietary trunking encapsulation.
Inter-Switch Link (ISL)—Cisco-proprietary trunking encapsulation.
•![]() IEEE 802.1Q— industry-standard trunking encapsulation.
IEEE 802.1Q— industry-standard trunking encapsulation.
Figure 12-2 shows a network of switches that are connected by ISL trunks.
Figure 12-2 Switches in an ISL Trunking Environment

You can configure a trunk on a single Ethernet interface or on an EtherChannel bundle. For more information about EtherChannel, see "Configuring EtherChannels and Link-State Tracking."
Ethernet trunk interfaces support different trunking modes (see Table 12-4). You can set an interface as trunking or nontrunking or to negotiate trunking with the neighboring interface. To autonegotiate trunking, the interfaces must be in the same VTP domain.
Trunk negotiation is managed by the Dynamic Trunking Protocol (DTP), which is a Point-to-Point Protocol. However, some internetworking devices might forward DTP frames improperly, which could cause misconfigurations.
To avoid this, you should configure interfaces connected to devices that do not support DTP to not forward DTP frames, that is, to turn off DTP.
•![]() If you do not intend to trunk across those links, use the switchport mode access interface configuration command to disable trunking.
If you do not intend to trunk across those links, use the switchport mode access interface configuration command to disable trunking.
•![]() To enable trunking to a device that does not support DTP, use the switchport mode trunk and switchport nonegotiate interface configuration commands to cause the interface to become a trunk but to not generate DTP frames. Use the switchport trunk encapsulation isl or switchport trunk encapsulation dot1q interface to select the encapsulation type on the trunk port.
To enable trunking to a device that does not support DTP, use the switchport mode trunk and switchport nonegotiate interface configuration commands to cause the interface to become a trunk but to not generate DTP frames. Use the switchport trunk encapsulation isl or switchport trunk encapsulation dot1q interface to select the encapsulation type on the trunk port.
You can also specify on DTP interfaces whether the trunk uses ISL or IEEE 802.1Q encapsulation or if the encapsulation type is autonegotiated. The DTP supports autonegotiation of both ISL and IEEE 802.1Q trunks.

Note ![]() DTP is not supported on private-VLAN ports or tunnel ports.
DTP is not supported on private-VLAN ports or tunnel ports.
|
|
|
|---|---|
switchport mode access |
Puts the interface (access port) into permanent nontrunking mode and negotiates to convert the link into a nontrunk link. The interface becomes a nontrunk interface regardless of whether or not the neighboring interface is a trunk interface. |
switchport mode dynamic auto |
Makes the interface able to convert the link to a trunk link. The interface becomes a trunk interface if the neighboring interface is set to trunk or desirable mode. The default switchport mode for all Ethernet interfaces is dynamic auto. |
switchport mode dynamic desirable |
Makes the interface actively attempt to convert the link to a trunk link. The interface becomes a trunk interface if the neighboring interface is set to trunk, desirable, or auto mode. |
switchport mode trunk |
Puts the interface into permanent trunking mode and negotiates to convert the neighboring link into a trunk link. The interface becomes a trunk interface even if the neighboring interface is not a trunk interface. |
switchport nonegotiate |
Prevents the interface from generating DTP frames. You can use this command only when the interface switchport mode is access or trunk. You must manually configure the neighboring interface as a trunk interface to establish a trunk link. |
switchport mode dot1q-tunnel |
Configures the interface as a tunnel (nontrunking) port to be connected in an asymmetric link with an IEEE 802.1Q trunk port. The IEEE 802.1Q tunneling is used to maintain customer VLAN integrity across a service provider network. See Chapter 16, "Configuring IEEE 802.1Q and Layer 2 Protocol Tunneling," for more information on tunnel ports. |
Encapsulation Types
Table 12-5 lists the Ethernet trunk encapsulation types and keywords.

Note ![]() The switch does not support Layer 3 trunks; you cannot configure subinterfaces or use the encapsulation keyword on Layer 3 interfaces. The switch does support Layer 2 trunks and Layer 3 VLAN interfaces, which provide equivalent capabilities.
The switch does not support Layer 3 trunks; you cannot configure subinterfaces or use the encapsulation keyword on Layer 3 interfaces. The switch does support Layer 2 trunks and Layer 3 VLAN interfaces, which provide equivalent capabilities.
The trunking mode, the trunk encapsulation type, and the hardware capabilities of the two connected interfaces decide whether a link becomes an ISL or IEEE 802.1Q trunk.
IEEE 802.1Q Configuration Considerations
The IEEE 802.1Q trunks impose these limitations on the trunking strategy for a network:
•![]() In a network of Cisco switches connected through IEEE 802.1Q trunks, the switches maintain one spanning-tree instance for each VLAN allowed on the trunks. Non-Cisco devices might support one spanning-tree instance for all VLANs.
In a network of Cisco switches connected through IEEE 802.1Q trunks, the switches maintain one spanning-tree instance for each VLAN allowed on the trunks. Non-Cisco devices might support one spanning-tree instance for all VLANs.
When you connect a Cisco switch to a non-Cisco device through an IEEE 802.1Q trunk, the Cisco switch combines the spanning-tree instance of the VLAN of the trunk with the spanning-tree instance of the non-Cisco IEEE 802.1Q switch. However, spanning-tree information for each VLAN is maintained by Cisco switches separated by a cloud of non-Cisco IEEE 802.1Q switches. The non-Cisco IEEE 802.1Q cloud separating the Cisco switches is treated as a single trunk link between the switches.
•![]() Make sure the native VLAN for an IEEE 802.1Q trunk is the same on both ends of the trunk link. If the native VLAN on one end of the trunk is different from the native VLAN on the other end, spanning-tree loops might result.
Make sure the native VLAN for an IEEE 802.1Q trunk is the same on both ends of the trunk link. If the native VLAN on one end of the trunk is different from the native VLAN on the other end, spanning-tree loops might result.
•![]() Disabling spanning tree on the native VLAN of an IEEE 802.1Q trunk without disabling spanning tree on every VLAN in the network can potentially cause spanning-tree loops. We recommend that you leave spanning tree enabled on the native VLAN of an IEEE 802.1Q trunk or disable spanning tree on every VLAN in the network. Make sure your network is loop-free before disabling spanning tree.
Disabling spanning tree on the native VLAN of an IEEE 802.1Q trunk without disabling spanning tree on every VLAN in the network can potentially cause spanning-tree loops. We recommend that you leave spanning tree enabled on the native VLAN of an IEEE 802.1Q trunk or disable spanning tree on every VLAN in the network. Make sure your network is loop-free before disabling spanning tree.
Default Layer 2 Ethernet Interface VLAN Configuration
Table 12-6 shows the default Layer 2 Ethernet interface VLAN configuration.
Configuring an Ethernet Interface as a Trunk Port
Because trunk ports send and receive VTP advertisements, to use VTP you must ensure that at least one trunk port is configured on the switch and that this trunk port is connected to the trunk port of a second switch. Otherwise, the switch cannot receive any VTP advertisements.
These sections contain this configuration information:
•![]() Interaction with Other Features
Interaction with Other Features
•![]() Defining the Allowed VLANs on a Trunk
Defining the Allowed VLANs on a Trunk
•![]() Changing the Pruning-Eligible List
Changing the Pruning-Eligible List
•![]() Configuring the Native VLAN for Untagged Traffic
Configuring the Native VLAN for Untagged Traffic

Note ![]() By default, an interface is in Layer 2 mode. The default mode for Layer 2 interfaces is switchport mode dynamic auto. If the neighboring interface supports trunking and is configured to allow trunking, the link is a Layer 2 trunk or, if the interface is in Layer 3 mode, it becomes a Layer 2 trunk when you enter the switchport interface configuration command. By default, trunks negotiate encapsulation. If the neighboring interface supports ISL and IEEE 802.1Q encapsulation and both interfaces are set to negotiate the encapsulation type, the trunk uses ISL encapsulation.
By default, an interface is in Layer 2 mode. The default mode for Layer 2 interfaces is switchport mode dynamic auto. If the neighboring interface supports trunking and is configured to allow trunking, the link is a Layer 2 trunk or, if the interface is in Layer 3 mode, it becomes a Layer 2 trunk when you enter the switchport interface configuration command. By default, trunks negotiate encapsulation. If the neighboring interface supports ISL and IEEE 802.1Q encapsulation and both interfaces are set to negotiate the encapsulation type, the trunk uses ISL encapsulation.
Interaction with Other Features
Trunking interacts with other features in these ways:
•![]() A trunk port cannot be a secure port.
A trunk port cannot be a secure port.
•![]() A trunk port cannot be a tunnel port.
A trunk port cannot be a tunnel port.
•![]() Trunk ports can be grouped into EtherChannel port groups, but all trunks in the group must have the same configuration. When a group is first created, all ports follow the parameters set for the first port to be added to the group. If you change the configuration of one of these parameters, the switch propagates the setting you entered to all ports in the group:
Trunk ports can be grouped into EtherChannel port groups, but all trunks in the group must have the same configuration. When a group is first created, all ports follow the parameters set for the first port to be added to the group. If you change the configuration of one of these parameters, the switch propagates the setting you entered to all ports in the group:
–![]() allowed-VLAN list.
allowed-VLAN list.
–![]() STP port priority for each VLAN.
STP port priority for each VLAN.
–![]() STP Port Fast setting.
STP Port Fast setting.
–![]() trunk status: if one port in a port group ceases to be a trunk, all ports cease to be trunks.
trunk status: if one port in a port group ceases to be a trunk, all ports cease to be trunks.
•![]() We recommend that you configure no more than 24 trunk ports in PVST mode and no more than 40 trunk ports in MST mode.
We recommend that you configure no more than 24 trunk ports in PVST mode and no more than 40 trunk ports in MST mode.
•![]() If you try to enable IEEE 802.1x on a trunk port, an error message appears, and IEEE 802.1x is not enabled. If you try to change the mode of an IEEE 802.1x-enabled port to trunk, the port mode is not changed.
If you try to enable IEEE 802.1x on a trunk port, an error message appears, and IEEE 802.1x is not enabled. If you try to change the mode of an IEEE 802.1x-enabled port to trunk, the port mode is not changed.
•![]() A port in dynamic mode can negotiate with its neighbor to become a trunk port. If you try to enable IEEE 802.1x on a dynamic port, an error message appears, and IEEE 802.1x is not enabled. If you try to change the mode of an IEEE 802.1x-enabled port to dynamic, the port mode is not changed.
A port in dynamic mode can negotiate with its neighbor to become a trunk port. If you try to enable IEEE 802.1x on a dynamic port, an error message appears, and IEEE 802.1x is not enabled. If you try to change the mode of an IEEE 802.1x-enabled port to dynamic, the port mode is not changed.
Configuring a Trunk Port
Beginning in privileged EXEC mode, follow these steps to configure a port as a trunk port:
To return an interface to its default configuration, use the default interface interface-id interface configuration command. To reset all trunking characteristics of a trunking interface to the defaults, use the no switchport trunk interface configuration command. To disable trunking, use the switchport mode access interface configuration command to configure the port as a static-access port.
This example shows how to configure a port as an IEEE 802.1Q trunk. The example assumes that the neighbor interface is configured to support IEEE 802.1Q trunking.
Switch# configure terminal
Enter configuration commands, one per line. End with CNTL/Z.
Switch(config)# interface gigabitethernet0/2
Switch(config-if)# switchport mode dynamic desirable
Switch(config-if)# switchport trunk encapsulation dot1q
Switch(config-if)# end
Defining the Allowed VLANs on a Trunk
By default, a trunk port sends traffic to and receives traffic from all VLANs. All VLAN IDs, 1 to 4094, are allowed on each trunk. However, you can remove VLANs from the allowed list, preventing traffic from those VLANs from passing over the trunk. To restrict the traffic a trunk carries, use the switchport trunk allowed vlan remove vlan-list interface configuration command to remove specific VLANs from the allowed list.

Note ![]() VLAN 1 is the default VLAN on all trunk ports in all Cisco switches, and it has previously been a requirement that VLAN 1 always be enabled on every trunk link. You can use the VLAN 1 minimization feature to disable VLAN 1 on any individual VLAN trunk link so that no user traffic (including spanning-tree advertisements) is sent or received on VLAN 1.
VLAN 1 is the default VLAN on all trunk ports in all Cisco switches, and it has previously been a requirement that VLAN 1 always be enabled on every trunk link. You can use the VLAN 1 minimization feature to disable VLAN 1 on any individual VLAN trunk link so that no user traffic (including spanning-tree advertisements) is sent or received on VLAN 1.
To reduce the risk of spanning-tree loops or storms, you can disable VLAN 1 on any individual VLAN trunk port by removing VLAN 1 from the allowed list. When you remove VLAN 1 from a trunk port, the interface continues to sent and receive management traffic, for example, Cisco Discovery Protocol (CDP), Port Aggregation Protocol (PAgP), Link Aggregation Control Protocol (LACP), DTP, and VTP in VLAN 1.
If a trunk port with VLAN 1 disabled is converted to a nontrunk port, it is added to the access VLAN. If the access VLAN is set to 1, the port will be added to VLAN 1, regardless of the switchport trunk allowed setting. The same is true for any VLAN that has been disabled on the port.
A trunk port can become a member of a VLAN if the VLAN is enabled, if VTP knows of the VLAN, and if the VLAN is in the allowed list for the port. When VTP detects a newly enabled VLAN and the VLAN is in the allowed list for a trunk port, the trunk port automatically becomes a member of the enabled VLAN. When VTP detects a new VLAN and the VLAN is not in the allowed list for a trunk port, the trunk port does not become a member of the new VLAN.
Beginning in privileged EXEC mode, follow these steps to modify the allowed list of a trunk:
To return to the default allowed VLAN list of all VLANs, use the no switchport trunk allowed vlan interface configuration command.
This example shows how to remove VLAN 2 from the allowed VLAN list on a port:
Switch(config)# interface gigabitethernet0/1
Switch(config-if)# switchport trunk allowed vlan remove 2
Switch(config-if)# end
Changing the Pruning-Eligible List
The pruning-eligible list applies only to trunk ports. Each trunk port has its own eligibility list. VTP pruning must be enabled for this procedure to take effect. The "Enabling VTP Pruning" section describes how to enable VTP pruning.
Beginning in privileged EXEC mode, follow these steps to remove VLANs from the pruning-eligible list on a trunk port:
|
|
|
|
|---|---|---|
Step 1 |
configure terminal |
Enter global configuration mode. |
Step 2 |
interface interface-id |
Select the trunk port for which VLANs should be pruned, and enter interface configuration mode. |
Step 3 |
switchport trunk pruning vlan {add | except | none | remove} vlan-list [,vlan[,vlan[,,,]] |
Configure the list of VLANs allowed to be pruned from the trunk. (See the "VTP Pruning" section). For explanations about using the add, except, none, and remove keywords, see the command reference for this release. Separate nonconsecutive VLAN IDs with a comma and no spaces; use a hyphen to designate a range of IDs. Valid IDs are 2 to 1001. Extended-range VLANs (VLAN IDs 1006 to 4094) cannot be pruned. VLANs that are pruning-ineligible receive flooded traffic. The default list of VLANs allowed to be pruned contains VLANs 2 to 1001. |
Step 4 |
end |
Return to privileged EXEC mode. |
Step 5 |
show interfaces interface-id switchport |
Verify your entries in the Pruning VLANs Enabled field of the display. |
Step 6 |
copy running-config startup-config |
(Optional) Save your entries in the configuration file. |
To return to the default pruning-eligible list of all VLANs, use the no switchport trunk pruning vlan interface configuration command.
Configuring the Native VLAN for Untagged Traffic
A trunk port configured with IEEE 802.1Q tagging can receive both tagged and untagged traffic. By default, the switch forwards untagged traffic in the native VLAN configured for the port. The native VLAN is VLAN 1 by default.

Note ![]() The native VLAN can be assigned any VLAN ID.
The native VLAN can be assigned any VLAN ID.
For information about IEEE 802.1Q configuration issues, see the "IEEE 802.1Q Configuration Considerations" section.
Beginning in privileged EXEC mode, follow these steps to configure the native VLAN on an IEEE 802.1Q trunk:
To return to the default native VLAN, VLAN 1, use the no switchport trunk native vlan interface configuration command.
If a packet has a VLAN ID that is the same as the outgoing port native VLAN ID, the packet is sent untagged; otherwise, the switch sends the packet with a tag.
Configuring Trunk Ports for Load Sharing
Load sharing divides the bandwidth supplied by parallel trunks connecting switches. To avoid loops, STP normally blocks all but one parallel link between switches. Using load sharing, you divide the traffic between the links according to which VLAN the traffic belongs.
You configure load sharing on trunk ports by using STP port priorities or STP path costs. For load sharing using STP port priorities, both load-sharing links must be connected to the same switch. For load sharing using STP path costs, each load-sharing link can be connected to the same switch or to two different switches. For more information about STP, see "Configuring STP."
Load Sharing Using STP Port Priorities
When two ports on the same switch form a loop, the switch uses the STP port priority to decide which port is enabled and which port is in a blocking state. You can set the priorities on a parallel trunk port so that the port carries all the traffic for a given VLAN. The trunk port with the higher priority (lower values) for a VLAN is forwarding traffic for that VLAN. The trunk port with the lower priority (higher values) for the same VLAN remains in a blocking state for that VLAN. One trunk port sends or receives all traffic for the VLAN.
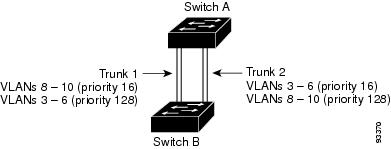
Figure 12-3 shows two trunks connecting supported switches. In this example, the switches are configured as follows:
•![]() VLANs 8 through 10 are assigned a port priority of 16 on Trunk 1.
VLANs 8 through 10 are assigned a port priority of 16 on Trunk 1.
•![]() VLANs 3 through 6 retain the default port priority of 128 on Trunk 1.
VLANs 3 through 6 retain the default port priority of 128 on Trunk 1.
•![]() VLANs 3 through 6 are assigned a port priority of 16 on Trunk 2.
VLANs 3 through 6 are assigned a port priority of 16 on Trunk 2.
•![]() VLANs 8 through 10 retain the default port priority of 128 on Trunk 2.
VLANs 8 through 10 retain the default port priority of 128 on Trunk 2.
In this way, Trunk 1 carries traffic for VLANs 8 through 10, and Trunk 2 carries traffic for VLANs 3 through 6. If the active trunk fails, the trunk with the lower priority takes over and carries the traffic for all of the VLANs. No duplication of traffic occurs over any trunk port.
Figure 12-3 Load Sharing by Using STP Port Priorities
Beginning in privileged EXEC mode, follow these steps to configure the network shown in Figure 12-3.
Load Sharing Using STP Path Cost
You can configure parallel trunks to share VLAN traffic by setting different path costs on a trunk and associating the path costs with different sets of VLANs, blocking different ports for different VLANs. The VLANs keep the traffic separate and maintain redundancy in the event of a lost link.
In Figure 12-4, Trunk ports 1 and 2 are configured as 100BASE-T ports. These VLAN path costs are assigned:
•![]() VLANs 2 through 4 are assigned a path cost of 30 on Trunk port 1.
VLANs 2 through 4 are assigned a path cost of 30 on Trunk port 1.
•![]() VLANs 8 through 10 retain the default 100BASE-T path cost on Trunk port 1 of 19.
VLANs 8 through 10 retain the default 100BASE-T path cost on Trunk port 1 of 19.
•![]() VLANs 8 through 10 are assigned a path cost of 30 on Trunk port 2.
VLANs 8 through 10 are assigned a path cost of 30 on Trunk port 2.
•![]() VLANs 2 through 4 retain the default 100BASE-T path cost on Trunk port 2 of 19.
VLANs 2 through 4 retain the default 100BASE-T path cost on Trunk port 2 of 19.
Figure 12-4 Load-Sharing Trunks with Traffic Distributed by Path Cost

Beginning in privileged EXEC mode, follow these steps to configure the network shown in Figure 12-4:
Configuring VMPS
The VLAN Query Protocol (VQP) is used to support dynamic-access ports, which are not permanently assigned to a VLAN, but give VLAN assignments based on the MAC source addresses seen on the port. Each time an unknown MAC address is seen, the switch sends a VQP query to a remote VMPS; the query includes the newly seen MAC address and the port on which it was seen. The VMPS responds with a VLAN assignment for the port. The switch cannot be a VMPS server but can act as a client to the VMPS and communicate with it through VQP.
These sections contain this information:
•![]() "Default VMPS Client Configuration" section
"Default VMPS Client Configuration" section
•![]() "VMPS Configuration Guidelines" section
"VMPS Configuration Guidelines" section
•![]() "Configuring the VMPS Client" section
"Configuring the VMPS Client" section
•![]() "Monitoring the VMPS" section
"Monitoring the VMPS" section
•![]() "Troubleshooting Dynamic-Access Port VLAN Membership" section
"Troubleshooting Dynamic-Access Port VLAN Membership" section
•![]() "VMPS Configuration Example" section
"VMPS Configuration Example" section
Understanding VMPS
Each time the client switch receives the MAC address of a new host, it sends a VQP query to the VMPS. When the VMPS receives this query, it searches its database for a MAC-address-to-VLAN mapping. The server response is based on this mapping and whether or not the server is in open or secure mode. In secure mode, the server shuts down the port when an illegal host is detected. In open mode, the server simply denies the host access to the port.
If the port is currently unassigned (that is, it does not yet have a VLAN assignment), the VMPS provides one of these responses:
•![]() If the host is allowed on the port, the VMPS sends the client a vlan-assignment response containing the assigned VLAN name and allowing access to the host.
If the host is allowed on the port, the VMPS sends the client a vlan-assignment response containing the assigned VLAN name and allowing access to the host.
•![]() If the host is not allowed on the port and the VMPS is in open mode, the VMPS sends an access-denied response.
If the host is not allowed on the port and the VMPS is in open mode, the VMPS sends an access-denied response.
•![]() If the VLAN is not allowed on the port and the VMPS is in secure mode, the VMPS sends a port-shutdown response.
If the VLAN is not allowed on the port and the VMPS is in secure mode, the VMPS sends a port-shutdown response.
If the port already has a VLAN assignment, the VMPS provides one of these responses:
•![]() If the VLAN in the database matches the current VLAN on the port, the VMPS sends an success response, allowing access to the host.
If the VLAN in the database matches the current VLAN on the port, the VMPS sends an success response, allowing access to the host.
•![]() If the VLAN in the database does not match the current VLAN on the port and active hosts exist on the port, the VMPS sends an access-denied or a port-shutdown response, depending on the secure mode of the VMPS.
If the VLAN in the database does not match the current VLAN on the port and active hosts exist on the port, the VMPS sends an access-denied or a port-shutdown response, depending on the secure mode of the VMPS.
If the switch receives an access-denied response from the VMPS, it continues to block traffic to and from the host MAC address. The switch continues to monitor the packets directed to the port and sends a query to the VMPS when it identifies a new host address. If the switch receives a port-shutdown response from the VMPS, it disables the port. The port must be manually re-enabled by using Network Assistant, the CLI, or SNMP.
Dynamic-Access Port VLAN Membership
A dynamic-access port can belong to only one VLAN with an ID from 1 to 4094. When the link comes up, the switch does not forward traffic to or from this port until the VMPS provides the VLAN assignment. The VMPS receives the source MAC address from the first packet of a new host connected to the dynamic-access port and attempts to match the MAC address to a VLAN in the VMPS database.
If there is a match, the VMPS sends the VLAN number for that port. If the client switch was not previously configured, it uses the domain name from the first VTP packet it receives on its trunk port from the VMPS. If the client switch was previously configured, it includes its domain name in the query packet to the VMPS to obtain its VLAN number. The VMPS verifies that the domain name in the packet matches its own domain name before accepting the request and responds to the client with the assigned VLAN number for the client. If there is no match, the VMPS either denies the request or shuts down the port (depending on the VMPS secure mode setting).
Multiple hosts (MAC addresses) can be active on a dynamic-access port if they are all in the same VLAN; however, the VMPS shuts down a dynamic-access port if more than 20 hosts are active on the port.
If the link goes down on a dynamic-access port, the port returns to an isolated state and does not belong to a VLAN. Any hosts that come online through the port are checked again through the VQP with the VMPS before the port is assigned to a VLAN.
Dynamic-access ports can be used for direct host connections, or they can connect to a network. A maximum of 20 MAC addresses are allowed per port on the switch. A dynamic-access port can belong to only one VLAN at a time, but the VLAN can change over time, depending on the MAC addresses seen.
Default VMPS Client Configuration
Table 12-7 shows the default VMPS and dynamic-access port configuration on client switches.
VMPS Configuration Guidelines
These guidelines and restrictions apply to dynamic-access port VLAN membership:
•![]() You should configure the VMPS before you configure ports as dynamic-access ports.
You should configure the VMPS before you configure ports as dynamic-access ports.
•![]() When you configure a port as a dynamic-access port, the spanning-tree Port Fast feature is automatically enabled for that port. The Port Fast mode accelerates the process of bringing the port into the forwarding state.
When you configure a port as a dynamic-access port, the spanning-tree Port Fast feature is automatically enabled for that port. The Port Fast mode accelerates the process of bringing the port into the forwarding state.
•![]() IEEE 802.1x ports cannot be configured as dynamic-access ports. If you try to enable IEEE 802.1x on a dynamic-access (VQP) port, an error message appears, and IEEE 802.1x is not enabled. If you try to change an IEEE 802.1x-enabled port to dynamic VLAN assignment, an error message appears, and the VLAN configuration is not changed.
IEEE 802.1x ports cannot be configured as dynamic-access ports. If you try to enable IEEE 802.1x on a dynamic-access (VQP) port, an error message appears, and IEEE 802.1x is not enabled. If you try to change an IEEE 802.1x-enabled port to dynamic VLAN assignment, an error message appears, and the VLAN configuration is not changed.
•![]() Trunk ports cannot be dynamic-access ports, but you can enter the switchport access vlan dynamic interface configuration command for a trunk port. In this case, the switch retains the setting and applies it if the port is later configured as an access port.
Trunk ports cannot be dynamic-access ports, but you can enter the switchport access vlan dynamic interface configuration command for a trunk port. In this case, the switch retains the setting and applies it if the port is later configured as an access port.
You must turn off trunking on the port before the dynamic-access setting takes effect.
•![]() Dynamic-access ports cannot be monitor ports.
Dynamic-access ports cannot be monitor ports.
•![]() Secure ports cannot be dynamic-access ports. You must disable port security on a port before it becomes dynamic.
Secure ports cannot be dynamic-access ports. You must disable port security on a port before it becomes dynamic.
•![]() Private VLAN ports cannot be dynamic-access ports.
Private VLAN ports cannot be dynamic-access ports.
•![]() Dynamic-access ports cannot be members of an EtherChannel group.
Dynamic-access ports cannot be members of an EtherChannel group.
•![]() Port channels cannot be configured as dynamic-access ports.
Port channels cannot be configured as dynamic-access ports.
•![]() A dynamic-access port can participate in fallback bridging.
A dynamic-access port can participate in fallback bridging.
•![]() The VTP management domain of the VMPS client and the VMPS server must be the same.
The VTP management domain of the VMPS client and the VMPS server must be the same.
•![]() The VLAN configured on the VMPS server should not be a voice VLAN.
The VLAN configured on the VMPS server should not be a voice VLAN.
Configuring the VMPS Client
You configure dynamic VLANs by using the VMPS (server). The switch can be a VMPS client; it cannot be a VMPS server.
Entering the IP Address of the VMPS
You must first enter the IP address of the server to configure the switch as a client.

Note ![]() If the VMPS is being defined for a cluster of switches, enter the address on the command switch.
If the VMPS is being defined for a cluster of switches, enter the address on the command switch.
Beginning in privileged EXEC mode, follow these steps to enter the IP address of the VMPS:

Note ![]() You must have IP connectivity to the VMPS for dynamic-access ports to work. You can test for IP connectivity by pinging the IP address of the VMPS and verifying that you get a response.
You must have IP connectivity to the VMPS for dynamic-access ports to work. You can test for IP connectivity by pinging the IP address of the VMPS and verifying that you get a response.
Configuring Dynamic-Access Ports on VMPS Clients
If you are configuring a port on a cluster member switch as a dynamic-access port, first use the rcommand privileged EXEC command to log in to the cluster member switch.

Beginning in privileged EXEC mode, follow these steps to configure a dynamic-access port on a VMPS client switch:
To return an interface to its default configuration, use the default interface interface-id interface configuration command. To return an interface to its default switchport mode (dynamic auto), use the no switchport mode interface configuration command. To reset the access mode to the default VLAN for the switch, use the no switchport access vlan interface configuration command.
Reconfirming VLAN Memberships
Beginning in privileged EXEC mode, follow these steps to confirm the dynamic-access port VLAN membership assignments that the switch has received from the VMPS:
|
|
|
|
|---|---|---|
Step 1 |
vmps reconfirm |
Reconfirm dynamic-access port VLAN membership. |
Step 2 |
show vmps |
Verify the dynamic VLAN reconfirmation status. |
Changing the Reconfirmation Interval
VMPS clients periodically reconfirm the VLAN membership information received from the VMPS.You can set the number of minutes after which reconfirmation occurs.
If you are configuring a member switch in a cluster, this parameter must be equal to or greater than the reconfirmation setting on the command switch. You must also first use the rcommand privileged EXEC command to log in to the member switch.
Beginning in privileged EXEC mode, follow these steps to change the reconfirmation interval:
To return the switch to its default setting, use the no vmps reconfirm global configuration command.
Changing the Retry Count
Beginning in privileged EXEC mode, follow these steps to change the number of times that the switch attempts to contact the VMPS before querying the next server:
To return the switch to its default setting, use the no vmps retry global configuration command.
Monitoring the VMPS
You can display information about the VMPS by using the show vmps privileged EXEC command. The switch displays this information about the VMPS:
•![]() VMPS VQP Version—the version of VQP used to communicate with the VMPS. The switch queries the VMPS that is using VQP Version 1.
VMPS VQP Version—the version of VQP used to communicate with the VMPS. The switch queries the VMPS that is using VQP Version 1.
•![]() Reconfirm Interval—the number of minutes the switch waits before reconfirming the VLAN-to-MAC-address assignments.
Reconfirm Interval—the number of minutes the switch waits before reconfirming the VLAN-to-MAC-address assignments.
•![]() Server Retry Count—the number of times VQP resends a query to the VMPS. If no response is received after this many tries, the switch starts to query the secondary VMPS.
Server Retry Count—the number of times VQP resends a query to the VMPS. If no response is received after this many tries, the switch starts to query the secondary VMPS.
•![]() VMPS domain server—the IP address of the configured VLAN membership policy servers. The switch sends queries to the one marked current. The one marked primary is the primary server.
VMPS domain server—the IP address of the configured VLAN membership policy servers. The switch sends queries to the one marked current. The one marked primary is the primary server.
•![]() VMPS Action—the result of the most recent reconfirmation attempt. A reconfirmation attempt can occur automatically when the reconfirmation interval expires, or you can force it by entering the vmps reconfirm privileged EXEC command or its Network Assistant or SNMP equivalent.
VMPS Action—the result of the most recent reconfirmation attempt. A reconfirmation attempt can occur automatically when the reconfirmation interval expires, or you can force it by entering the vmps reconfirm privileged EXEC command or its Network Assistant or SNMP equivalent.
This is an example of output for the show vmps privileged EXEC command:
Switch# show vmps
VQP Client Status:
--------------------
VMPS VQP Version: 1
Reconfirm Interval: 60 min
Server Retry Count: 3
VMPS domain server: 172.20.128.86 (primary, current)
172.20.128.87
Reconfirmation status
---------------------
VMPS Action: other
Troubleshooting Dynamic-Access Port VLAN Membership
The VMPS shuts down a dynamic-access port under these conditions:
•![]() The VMPS is in secure mode, and it does not allow the host to connect to the port. The VMPS shuts down the port to prevent the host from connecting to the network.
The VMPS is in secure mode, and it does not allow the host to connect to the port. The VMPS shuts down the port to prevent the host from connecting to the network.
•![]() More than 20 active hosts reside on a dynamic-access port.
More than 20 active hosts reside on a dynamic-access port.
To re-enable a disabled dynamic-access port, enter the shutdown interface configuration command followed by the no shutdown interface configuration command.
VMPS Configuration Example
Figure 12-5 shows a network with a VMPS server switch and VMPS client switches with dynamic-access ports. In this example, these assumptions apply:
•![]() The VMPS server and the VMPS client are separate switches.
The VMPS server and the VMPS client are separate switches.
•![]() The Catalyst 6500 series Switch A is the primary VMPS server.
The Catalyst 6500 series Switch A is the primary VMPS server.
•![]() The Catalyst 6500 series Switch C and Switch J are secondary VMPS servers.
The Catalyst 6500 series Switch C and Switch J are secondary VMPS servers.
•![]() End stations are connected to the clients, Switch B and Switch I.
End stations are connected to the clients, Switch B and Switch I.
•![]() The database configuration file is stored on the TFTP server with the IP address 172.20.22.7.
The database configuration file is stored on the TFTP server with the IP address 172.20.22.7.
Figure 12-5 Dynamic Port VLAN Membership Configuration
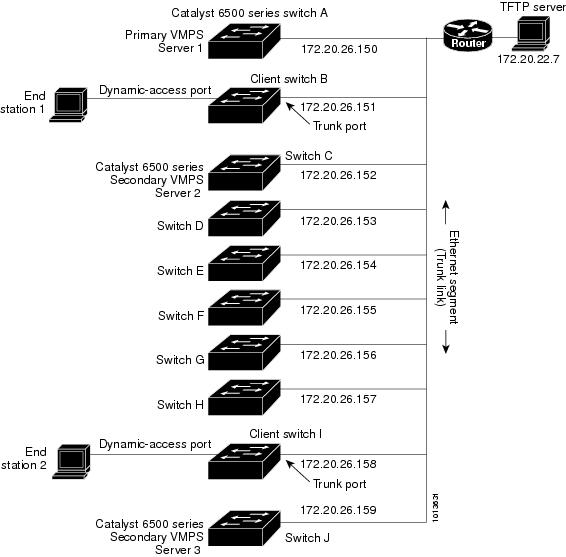
 Feedback
Feedback