Cisco Carrier Grade Services Engine Module Data Sheet
Available Languages
Do you want to scale your infrastructure to perform tens of millions of IPv4 to IPv6 address translations? Do you need to support a powerful distributed denial of service (DDoS) attack mitigation solution? The Cisco® Carrier-Grade Services Engine (CGSE) for the Cisco Carrier Routing System (CRS) is an ideal platform for these services. The Cisco CGSE is a single-slot module supported on all models of proven, high-end Cisco carrier-class routing system, including the Cisco CRS-1 Carrier Router and CRS-3 platform.
The Cisco CGSE for the Cisco CRS (Figure 1) is an integrated multi-CPU service module offering carrier-class performance and scale in support of both the Cisco Carrier-Grade IPv6 (CGv6) Solution and a DDoS mitigation solution. This data sheet provides detailed product specifications for the Cisco CGSE module and details about the Cisco CGv6 Solution and the DDoS mitigation software available on the Cisco CGSE.
Product Overview
The Cisco CGv6 Solution, running on one or more Cisco CGSE modules inside of a Cisco CRS, can scale to tens of millions of IP address translations with tens of gigabits of performance. It’s an effective way to address IPv4 depletion and facilitate IPv6 transition. Several modules can be populated within a chassis for a high-performance solution that can be deployed at places in the network where the best Cisco CGv6 coverage can be obtained.
The Cisco CGSE also supports the Arbor Peakflow SP Threat Management System (TMS) from Arbor Networks, which is licensed by Cisco to provide DDoS mitigation capabilities on Cisco CRS platforms. It provides service providers with the ability to offer:
● Managed DDoS mitigation services to enterprise clients
● Protection of the network backbone and services against attacks originating from both the outside and the inside of the service provider network
The module supports a highly available architecture with line-rate accounting and logging of translation information. Cisco IOS® XR Software on the module offers a flexible way to divert selected packets through the Cisco CGSE while allowing global IPv4 and IPv6 packets to traverse the Cisco CRS forwarding infrastructure as usual.

Powerful Performance
The Cisco CGSE housed inside a Cisco CRS offers carrier-class performance for Cisco CGv6 services, including:
● More than one million connection setups per second for stateful IPv4 and IPv6 Network Address Translation (NAT)
● Real-time off-device logging of NAT translation states using Cisco NetFlow 9
● Line-rate forwarding for IPv4 and IPv6
The powerful performance of the Cisco CGSE helps ensure that the experience of your end-users continues to be optimal for all services you provide.
Cisco CGSE DDoS Mitigation Software
As part of the Arbor Peakflow SP TMS software for DDoS mitigation, the Arbor Peakflow SP Collector Platform appliance monitors the network, performing an analysis of traffic in real-time to detect a comprehensive set of DDoS attack signatures. Upon detecting an attack, it redirects traffic to the threat management system on the Cisco CGSE module or to a bank of Cisco CGSE modules on the Cisco CRS, where the attack is surgically mitigated and clean traffic is re-injected into the network. Figure 2 illustrates how the DDoS mitigation process works.
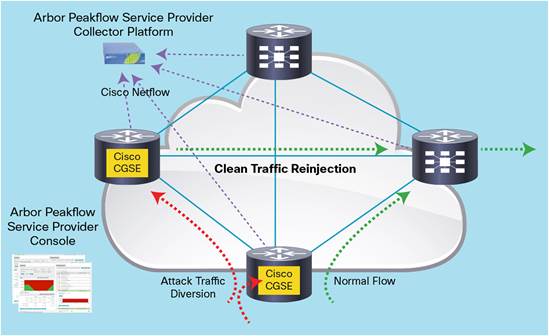
The main capabilities of the Cisco CGSE DDoS mitigation solution include:
● Throughput: Up to 10 Gbps of DDoS mitigation capability is provided per Cisco CGSE module
● Scalability: Up to 120 Gbps (12 Cisco CGSE modules), 60 Gbps (6 Cisco CGSE modules), and 30 Gbps (3 Cisco CGSE modules) are provided per Cisco CRS 16-slot, 8-slot, and 4-slot chassis, respectively
● Load balancing: Attack traffic can be load-balanced across multiple Cisco CRS routers with Cisco CGSE modules, or across multiple Cisco CGSE modules within a Cisco CRS. Additionally, the multi-CPU architecture of the Cisco CGSE module allows DDoS attack flows from multiple sources to be handled simultaneously, allowing greater mitigation performance
● Multiple configuration options: Traffic redirection and reinjection can be accomplished by IP redirect, using Layer 3 VPN (L3VPN) or generic routing encapsulation (GRE) tunnels
● Flexible deployment scenarios: Implement distributed deployment across multiple peering and provider-edge sites to offer mitigation at the point closest to the attack, or centralized deployment with a “scrubbing center” model using a cluster of Cisco CGSE modules in one more Cisco CRS routers
● Comprehensive DDoS mitigation capabilities: The solution addresses the full set of DDoS attack types and includes IPv6 support and an optional Atlas Fingerprints subscription to stay current with the latest attack signatures. For more information, please refer to the Arbor SP Peakflow TMS data sheet
Massive Scalability
As an increasing multitude of subscribers with their numerous applications traverse the network, the Cisco CGSE scales to support this growth:
● Up to 20 million stateful NAT translations per Cisco CGSE module
● Support for tens to hundreds of thousands of private IPv4 subscribers accessing the public IPv4 Internet
● Support for tens to hundreds of thousands of IPv6 subscribers accessing the IPv4 Internet
● Capability to add multiple Cisco CGSE modules in a chassis, increasing performance linearly
Integrated Services
The Cisco CGSE module is designed for the proven high-end routing platform of the Cisco CRS. It is supported on all the form factors of the Cisco CRS-1 and CRS-3 platforms, including 4-, 8-, and 16-slot and multichassis versions. This breadth of deployment options allows service providers to scale the Cisco CGSE to their appropriate needs. Also, the Cisco CGSE is integrated with the routing intelligence of the Cisco CRS, providing the significant operation efficiencies of a single OS. Because the Cisco CRS platform supports secure domain routers (SDRs), providers have the flexibility to integrate the Cisco CGSE on a virtualized network infrastructure.
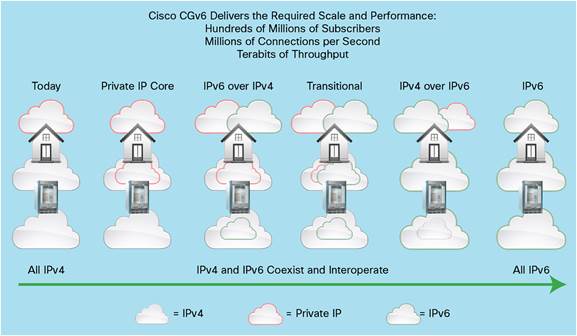
The following services are available on the Cisco CGSE (Figure 3):
● Full IPv4 and IPv6 routing and forwarding on the Cisco CRS platform
● Service provider-class NAT44 to address IPv4 depletion based on IETF NAT behaviors as described in RFCs 4787, 5382, and 5508
● IPv6 Rapid Deployment Border Relay (6rd BR, described in RFC 5969)
● Stateful and stateless IPv4 and IPv6 translation based on IETF BEHAVE specifications
● Service provider-class NAT64 translations based on IETF NAT behavior as described in RFC 6146
● Service provider-class Dual-Stack Lite (DSLite) translations based on existing IETF behavior as described in RFCs 6333 and 6334
● Network Positioning System (NPS)
The Cisco CGSE interface module on the Cisco CRS offers service providers a near-term solution to address IPv4 depletion and preserve a service provider’s present mode of operation (PMO). At the same time, it provides one or more methods to offer a low-risk, cost-effective means to activate IPv6 tunneling and translation functions.
Product Specifications
Table 1 lists the specifications of the Cisco CGSE module.
Table 1. Product Specifications
| Feature |
Description |
| Chassis compatibility |
Compatible with all current Cisco CRS-1 and CRS-3 line-card chassis |
| Forwarding-engine compatibility |
Compatible with the following forwarding engines: CRS-MSC-40G-B, CRS-MSC-20G-B, and CRS-MSC |
| Software compatibility |
Cisco IOS XR Software Release 3.9.1 |
| Protocols |
● NAT44 (RFCs 4787, 5382, and 5508)
● NAT64 (RFC 6146)
● DSLite AFTR (RFC 6334)
● Cisco NetFlowv9
● Port Control Protocol
|
| Feature summary |
● Stateful IPv4 NAT (NAT44)
● Stateful IPv6 to v4 NAT (NAT64)
● Stateless IPv6 to v4 NAT (NAT64 SL)
● Stateful DSLite translation AFTR function
● 6RD BR
|
| Performance |
● 20 Gbps of throughput
● Maximum number of physical layer interface modules (PLIMs) per chassis: 4 slots: 3; 8 slots: 7; and 16 slots: 12
● Max subscribers per stateful NAT session blade: 1 million
|
| Reliability and availability |
● Online insertion and removal (OIR) without affecting system traffic
|
| Network management |
● Cisco IOS XR Software command-line interface (CLI)
● XML interface
● Cisco Active Network Abstraction (ANA)
|
| Physical dimensions |
● Occupies one PLIM slot on a Cisco CRS chassis
● Weight: 7.85 lb (3.55 kg)
● Height: 20.6 in. (52.2 cm)
● Depth: 11.2 in. (28.4 cm)
● Width: 1.8 in. (4.49 cm)
|
| Power |
135 watts (-5 °C) to 165 watts (55 °C) |
| Environmental conditions |
● Storage temperature: -40 to 158°F (-40 to 70°C)
● Operating temperature:
◦ Normal: 41 to 104°F (5 to 40°C)
◦ Short-term: 23 to 122°F (-5 to 50°C)
● Relative humidity:
◦ Normal: 5 to 85%
◦ Short-term: 5 to 90% but not to exceed 0.024 kg water per kg of dry air
Note: Short-term refers to a period of not more than 96 consecutive hours and a total of 360 hours but not more than 15 instances in 1 year. |
Approvals and Compliance
Table 2 provides standards-compliance information for the Cisco CRS Carrier-Grade Services Engine PLIM.
Table 2. Compliance and Agency Approvals
| Feature |
Description |
| Safety standards |
● UL/CSA/IEC/EN 60950-1
● IEC/EN 60825 Laser Safety
● ACA TS001
● AS/NZS 60950
● FDA - Code of Federal Regulations Laser Safety
|
| EMI |
● FCC Class A
● ICES 003 Class A
● AS/NZS 3548 Class A
● CISPR 22 (EN55022) Class A
● VCCI Class A
● BSMI Class A
● IEC/EN 61000-3-2: Power Line Harmonics
● IEC/EN 61000-3-3: Voltage Fluctuations and Flicker
|
| Immunity (basic standards) |
● IEC/EN-61000-4-2: Electrostatic Discharge Immunity (8-kV contact, 15-kV air)
● IEC/EN-61000-4-3: Radiated Immunity (10V/m)
● IEC/EN-61000-4-4: Electrical Fast Transient Immunity (2-kV power, 1-kV signal)
● IEC/EN-61000-4-5: Surge AC Port (4-kV CM, 2-kV DM)
● IEC/EN-61000-4-5: Signal Ports (1 kV)
● IEC/EN-61000-4-5: Surge DC Port (1 kV)
● IEC/EN-61000-4-6: Immunity to Conducted Disturbances (10 Vrms)
IEC/EN-61000-4-8: Power Frequency Magnetic Field Immunity (30A/m)
● IEC/EN-61000-4-11: Voltage Dips, Short Interruptions, and Voltage Variations
|
| ETSI and EN |
● EN300 386: Telecommunications Network Equipment (EMC)
EN55022: Information Technology Equipment (Emissions) EN55024: Information Technology Equipment (Immunity)
● EN50082-1/EN-61000-6-1: Generic Immunity Standard
|
| Network Equipment Building Standards (NEBS) |
This product is designed to meet the following requirements (qualification in progress):
● SR-3580: NEBS Criteria Levels (Level 3)
● GR-1089-CORE: NEBS EMC and Safety
● GR-63-CORE: NEBS Physical Protection
|
Ordering Information
To place an order, contact your local Cisco representative or visit the Ordering page on Cisco.com. Use the ordering information in Table 3.
Table 3. Ordering Information for Carrier-Class NAT Licenses and Cisco CGSE License
| Product Part Number |
Product Name |
| CRS-CGSE-PLIM(=) |
Cisco CRS Carrier Grade Services Engine (CGSE) PLIM |
| XC-XLAT44-5M |
SW license for 5M NAT44 translations |
| XC-XLAT44-10M |
SW license for 10M NAT44 translations |
| XC-XLAT44-20M |
SW license for 20M NAT44 translations |
| XC-XLAT64-5M |
SW license for 5M NAT64 translations |
| XC-XLAT64-10M |
SW license for 10M NAT64 translations |
| XC-XLAT64-15M |
SW license for 15M NAT64 translations |
| XC-XLAT64-SL |
SW license for Stateless NAT64 translations |
| XC-6RD-BR |
SW license for 6RD translations |
| XC-XLAT-ANY-10M |
SW license for flexible NAT44 or NAT64 translations |
| XC-XLAT-DSLITE-5M |
SW license for 5M DSLITE translations |
| XC-XLAT-DSLITE-15M |
SW license for 15M DSLITE translations |
| CRS-CGSE-PLIM(=) |
Cisco CRS Carrier Grade Services Engine (CGSE) PLIM |
| XC-DDOS-BASE(=) |
SW license for 10Gbps TMS software on CGSE |
Service and Support
Cisco delivers innovative services programs through a unique combination of people, processes, tools, and partners, resulting in high levels of customer satisfaction. Cisco Services helps you protect your network investment, optimize network operations, and prepare your network for new applications to extend network intelligence and the power of your business. For more information about Cisco Services, contact your local Cisco representative or visit http://www.cisco.com.
For More Information
For more information about the Cisco CRS, other interfaces available for Cisco CRS, or cisco CRS Carrier-Grade Services Engine PLIM, contact your local Cisco representative or visit http://www.cisco.com/go/crs.
 Feedback
Feedback