Introduction
This document describes how to structure the configurations to set up Inter VLAN routing with the use of an external Cisco router.
Prerequisites
Requirements
Cisco recommends that you have knowledge of this topic:
Components Used
The information in this document is based on these software versions:
- Catalyst Switch Cisco IOS® 15.2E
- Cisco Router Cisco IOS XE 17.3
The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, ensure that you understand the potential impact of any command.
Conventions
For more information on document conventions, refer to the Cisco Technical Tips Conventions.
Background Information
This document describes the configurations to setup Inter VLAN routing with the use of an external Cisco router and explains it with sample configurations on 802.1Q trunking; the results of each command are displayed as they are executed. Different Cisco series routers, and any Catalyst switch can be used in the scenarios presented in this document to obtain the same results.
Trunking is a way to carry traffic from several VLANs over a point-to-point link between the two devices. Initially, there were two ways in which Ethernet trunking was implemented:
A trunk link is created and used to carry traffic from two or more VLANs, for example, VLAN1 and VLAN2 across a single link between Catalyst switches and/or a Cisco router.
The Cisco router is used to do the Inter VLAN routing between VLAN-X and VLAN-Y. This configuration can be useful when the Catalyst series switches are Layer 2 (L2) only and cannot route or communicate between VLANs.
For 802.1Q trunking, one VLAN is not tagged. This VLAN is called native VLAN. The native VLAN is used for untagged traffic when the port is in 802.1Q trunking mode. While you configure 802.1Q trunking, remember that the native VLAN must be configured the same on each side of the trunk link. It is a common mistake not to match the native VLANs when 802.1Q trunking between the router and the switch is configured.
In this sample configuration, the native VLAN is VLAN1, by default, on both the Cisco router and the Catalyst switch. Dependent on your network needs, you can use a native VLAN other than the default VLAN, VLAN1. Commands have been mentioned in the Configurations section of this document on how to change the native VLAN on these devices.
Sample configurations presented in this document can be used on different Cisco router series that supports 802.1Q VLAN trunking.
Note: The minimum supported release cannot necessarily be the recommended release. To determine the best maintenance release for your Cisco product, search for bugs listed by product component in the Bug Toolkit.
Note: Only registered Cisco users have access to internal documents, tools, and information.
Configure
In this section, you are presented with the information to configure the features described in this document.
Network Diagram
This document uses the network setup shown in this diagram.
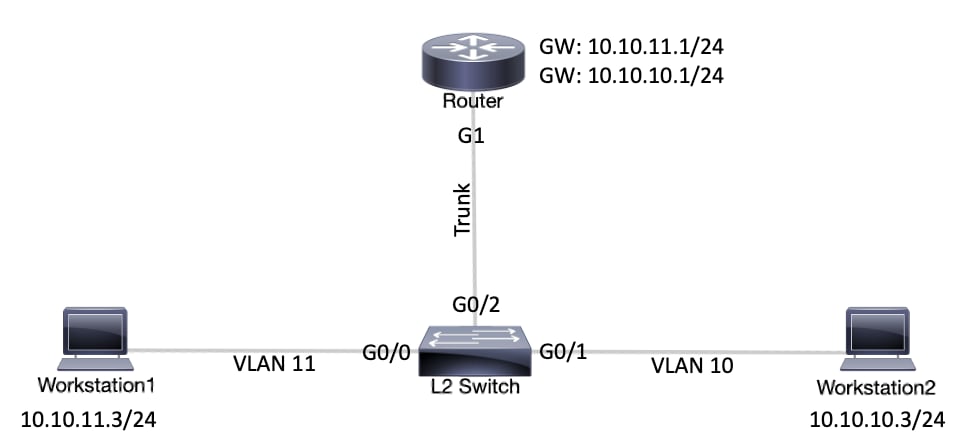 Network DiagramConfigurations
Network DiagramConfigurations
| Catalyst L2 Switch |
!-- (Optional) Set the IP address and default gateway for VLAN1 for management purposes.
L2_Switch#configure terminal
Enter configuration commands, one per line. End with CNTL/Z.
L2_Switch(config)#interface vlan 1
L2_Switch(config-if)#ip address 10.10.0.2 255.255.255.0
L2_Switch(config-if)#no ip directed-broadcast
L2_Switch(config-if)#no ip route-cache
L2_Switch(config-if)#exit
L2_Switch(config-if)#ip default-gateway 10.10.0.1
!-- (Optional) Set the VTP Mode. In our example, we have set the mode to be transparent.
!-- Depending on your network, set the VTP Mode accordingly.
L2_Switch(config)#vtp mode transparent
Setting device to VTP Transparent mode for VLANS.
L2_Switch(config)#
!-- Adding VLAN10 and VLAN11.
L2_Switch(config)#vlan 10-11
L2_Switch(config-vlan)#exit
L2_Switch(config)#
!-- Enable trunking on the interface GigabitEthernet 0/2.
!-- Enter the trunking encapsulation as dot1q.
L2_Switch(config)#interface gigabitEthernet 0/2
L2_Switch(config-if)#switchport trunk encapsulation dot1q
L2_Switch(config-if)#switchport mode trunk
!-- In case of dot1q, you need to make sure that the native VLAN matches across the link.
!-- On Catalyst Switches, by default, the native VLAN is 1.
!-- It is very important that you change the native VLAN on the router accordingly.
!-- The following set of commands can place on the interfaces connecting to the workstations.
L2_Switch(config)#interface gigabitEthernet 0/0
L2_Switch(config-if)#switchport mode access
L2_Switch(config-if)#switchport access vlan 11
L2_Switch(config-if)#exit
L2_Switch(config)#interface gigabitEthernet 0/1
L2_Switch(config-if)#switchport mode access
L2_Switch(config-if)#switchport access vlan 10
L2_Switch(config-if)#exit
!-- Remember to save the configuration.
L2_Switch#write memory
Building configuration...
|
| Router |
|
Note: The next screen captures show the commands that were entered on the Cisco Router. Comments between the commands are added in italics to explain certain commands and steps.
Router#configure terminal
Enter configuration commands, one per line. End with CNTL/Z.
!-- Select GigabitEthernet 1 for the trunk configuration.
!-- No Layer 3 (L3) configuration is done here.
Router(config)#interface GigabitEthernet 1
Router(config-if)#no shut
Router(config-if)#exit
!-- Enable dot1q on the sub-interface one for each VLAN.
!-- Configure L3 information on the sub-interface for each gateway.
Router(config)#interface gigabitEthernet 1.10
Router(config-subif)#encapsulation dot1Q 10
Router(config-subif)#ip address 10.10.10.1 255.255.255.0
Router(config-subif)#exit
Router(config)#interface gigabitEthernet 1.11
Router(config-subif)#encapsulation dot1Q 11
Router(config-subif)#ip address 10.10.11.1 255.255.255.0
Router(config-subif)#exit
!-- (Optional) For the management VLAN 1 make sure that the native VLAN matches across the link.
!-- On the switch, by default, the native VLAN is 1.
!-- On the router, configure VLAN1 as the native VLAN.
Router(config)#interface gigabitEthernet 1.1
Router(config-subif)#encapsulation dot1Q 1 native
Router(config-subif)#ip address 10.10.0.1 255.255.255.0
Router(config-subif)#end
!-- Remember to save the configuration.
Router#write memory
Building configuration...
[OK]
Router#
Note: In order to make this setup work, and to successfully ping between workstation1 and workstation2, you need to make sure that the default gateways on the workstations are setup properly. For workstation1, the default gateway must be 10.10.11.1 and for workstation2, the default gateway must be 10.10.10.1.
|
Useful Commands
This section helps you confirm that your configuration works as expected.
On the Catalyst switch, you can use the next commands to help with the verification:
On the Cisco Router, use the next commands:
-
show ip route
-
show interface
Sample Command Output
Catalyst Switch
The next command is used to check the administrative and operational status of the port. It is also used to make sure that the native VLAN matches on both sides of the trunk. The native VLAN is used for untagged traffic when the port is in 802.1Q trunking mode.
For 802.1Q trunking, the output command shows:
L2_Switch#show interfaces gigabitEthernet 0/2 switchport
Name: Gi0/2
Switchport: Enabled
Administrative Mode: trunk
Operational Mode: trunk
Administrative Trunking Encapsulation: dot1q
Operational Trunking Encapsulation: dot1q
Negotiation of Trunking: On
Access Mode VLAN: 1 (default)
Trunking Native Mode VLAN: 1 (default)
Administrative Native VLAN tagging: enabled
Voice VLAN: none
Administrative private-vlan host-association: none
Administrative private-vlan mapping: none
Administrative private-vlan trunk native VLAN: none
Administrative private-vlan trunk Native VLAN tagging: enabled
Administrative private-vlan trunk encapsulation: dot1q
Administrative private-vlan trunk normal VLANs: none
Administrative private-vlan trunk associations: none
Administrative private-vlan trunk mappings: none
Operational private-vlan: none
Trunking VLANs Enabled: ALL
Pruning VLANs Enabled: 2-1001
Capture Mode Disabled
Capture VLANs Allowed: ALL
Protected: false
Appliance trust: none
The next command is used to verify that the interfaces (ports) belong to the correct VLAN. In this example, interface Gi0/1 belongs to VLAN10 and Gi0/0 belongs to VLAN11. The rest are members of VLAN1.
L2_Switch#show vlan brief
VLAN Name Status Ports
---- -------------------------------- --------- -------------------------------
1 default active Gi0/3
10 VLAN0010 active Gi0/1
11 VLAN0011 active Gi0/0
1002 fddi-default act/unsup
1003 token-ring-default act/unsup
1004 fddinet-default act/unsup
1005 trnet-default act/unsup
L2_Switch#
The next command is used to check the VLAN trunking protocol (VTP) configuration on the switch. In this example, the transparent mode is used. The correct VTP mode depends on the topology of your network.
L2_Switch#show vtp status
VTP Version capable : 1 to 3
VTP version running : 1
VTP Domain Name :
VTP Pruning Mode : Disabled
VTP Traps Generation : Disabled
Device ID : 5254.0000.8000
Configuration last modified by 0.0.0.0 at 3-1-24 15:21:18
Feature VLAN:
--------------
VTP Operating Mode : Transparent
Maximum VLANs supported locally : 1005
Number of existing VLANs : 7
Configuration Revision : 0
MD5 digest : 0x9F 0x7D 0x8D 0x10 0xB1 0x22 0x2F 0xE7
0x29 0x77 0x42 0xA7 0x95 0xE7 0x68 0x1C
Cisco Router
The next command tells the L3 routing information about the sub-interfaces configured on the router.
Router#show ip route
Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2, m - OMP
n - NAT, Ni - NAT inside, No - NAT outside, Nd - NAT DIA
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
H - NHRP, G - NHRP registered, g - NHRP registration summary
o - ODR, P - periodic downloaded static route, l - LISP
a - application route
+ - replicated route, % - next hop override, p - overrides from PfR
& - replicated local route overrides by connected
Gateway of last resort is not set
10.0.0.0/8 is variably subnetted, 6 subnets, 2 masks
C 10.10.0.0/24 is directly connected, GigabitEthernet1.1
L 10.10.0.1/32 is directly connected, GigabitEthernet1.1
C 10.10.10.0/24 is directly connected, GigabitEthernet1.10
L 10.10.10.1/32 is directly connected, GigabitEthernet1.10
C 10.10.11.0/24 is directly connected, GigabitEthernet1.11
L 10.10.11.1/32 is directly connected, GigabitEthernet1.11
The next command is used to check the administrative and operational status of the interface. For the router interface status, the output command shows:
Router#show interfaces
GigabitEthernet1 is up, line protocol is up
Hardware is CSR vNIC, address is 5254.0000.004d (bia 5254.0000.004d)
MTU 1500 bytes, BW 1000000 Kbit/sec, DLY 10 usec,
reliability 255/255, txload 1/255, rxload 1/255
Encapsulation ARPA, loopback not set
Keepalive set (10 sec)
Full Duplex, 1000Mbps, link type is auto, media type is Virtual
output flow-control is unsupported, input flow-control is unsupported
ARP type: ARPA, ARP Timeout 04:00:00
Last input 00:00:00, output 00:14:10, output hang never
Last clearing of "show interface" counters never
Input queue: 0/375/0/0 (size/max/drops/flushes); Total output drops: 0
Queueing strategy: fifo
Output queue: 0/40 (size/max)
5 minute input rate 0 bits/sec, 0 packets/sec
5 minute output rate 0 bits/sec, 0 packets/sec
5338 packets input, 361563 bytes, 0 no buffer
Received 0 broadcasts (0 IP multicasts)
0 runts, 0 giants, 0 throttles
0 input errors, 0 CRC, 0 frame, 0 overrun, 0 ignored
0 watchdog, 0 multicast, 0 pause input
13 packets output, 1248 bytes, 0 underruns
Output 0 broadcasts (0 IP multicasts)
0 output errors, 0 collisions, 2 interface resets
57 unknown protocol drops
0 babbles, 0 late collision, 0 deferred
1 lost carrier, 0 no carrier, 0 pause output
0 output buffer failures, 0 output buffers swapped out
GigabitEthernet1.1 is up, line protocol is up
Hardware is CSR vNIC, address is 5254.0000.004d (bia 5254.0000.004d)
Internet address is 10.10.0.1/24
MTU 1500 bytes, BW 1000000 Kbit/sec, DLY 10 usec,
reliability 255/255, txload 1/255, rxload 1/255
Encapsulation 802.1Q Virtual LAN, Vlan ID 1.
ARP type: ARPA, ARP Timeout 04:00:00
Keepalive set (10 sec)
Last clearing of "show interface" counters never
GigabitEthernet1.10 is up, line protocol is up
Hardware is CSR vNIC, address is 5254.0000.004d (bia 5254.0000.004d)
Internet address is 10.10.10.1/24
MTU 1500 bytes, BW 1000000 Kbit/sec, DLY 10 usec,
reliability 255/255, txload 1/255, rxload 1/255
Encapsulation 802.1Q Virtual LAN, Vlan ID 10.
ARP type: ARPA, ARP Timeout 04:00:00
Keepalive set (10 sec)
Last clearing of "show interface" counters never
GigabitEthernet1.11 is up, line protocol is up
Hardware is CSR vNIC, address is 5254.0000.004d (bia 5254.0000.004d)
Internet address is 10.10.11.1/24
MTU 1500 bytes, BW 1000000 Kbit/sec, DLY 10 usec,
reliability 255/255, txload 1/255, rxload 1/255
Encapsulation 802.1Q Virtual LAN, Vlan ID 11.
ARP type: ARPA, ARP Timeout 04:00:00
Keepalive set (10 sec)
Last clearing of "show interface" counters never
GigabitEthernet2 is administratively down, line protocol is down
Hardware is CSR vNIC, address is 5254.0000.004e (bia 5254.0000.004e)
MTU 1500 bytes, BW 1000000 Kbit/sec, DLY 10 usec,
reliability 255/255, txload 1/255, rxload 1/255
Encapsulation ARPA, loopback not set
Keepalive set (10 sec)
Full Duplex, 1000Mbps, link type is auto, media type is Virtual
output flow-control is unsupported, input flow-control is unsupported
ARP type: ARPA, ARP Timeout 04:00:00
Last input never, output never, output hang never
Last clearing of "show interface" counters never
Input queue: 0/375/0/0 (size/max/drops/flushes); Total output drops: 0
Queueing strategy: fifo
Related Information

 Feedback
Feedback