Cisco Secure Firewall ASA and Secure Firewall Threat Defense Reimage Guide
This guide describes how to reimage between the Secure Firewall ASA and Secure Firewall Threat Defense (formerly Firepower Threat Defense), and also how to perform a reimage for the threat defense using a new image version; this method is distinct from an upgrade, and sets the threat defense to a factory default state. For ASA reimaging, see the ASA general operations configuration guide, where you can use multiple methods to reimage the ASA.
Supported Models
The following models support either ASA software or threat defense software. For ASA and threat defense version support, see the ASA compatibility guide or Cisco Secure Firewall Threat Defense Compatibility Guide.
-
Firepower 1000
-
Secure Firewall 1200
-
Firepower 2100 (threat defense 7.4 and earlier; ASA 9.20 and earlier)
-
Secure Firewall 3100
-
Secure Firewall 4200
-
ISA 3000
-
ASA 5506-X, 5506W-X, and 5506H-X (Threat Defense 6.2.3 and earlier; ASA 9.16 and earlier)
-
ASA 5508-X (threat defense 7.0 and earlier; ASA 9.16 and earlier)
-
ASA 5512-X (threat defense 6.2.3 and earlier; ASA 9.12 and earlier)
-
ASA 5515-X (threat defense 6.4 and earlier; ASA 9.12 and earlier)
-
ASA 5516-X (threat defense 7.0 and earlier; ASA 9.16 and earlier)
-
ASA 5525-X (threat defense 6.6 and earlier; ASA 9.14 and earlier)
-
ASA 5545-X (threat defense 6.6 and earlier; ASA 9.14 and earlier)
-
ASA 5555-X (threat defense 6.6 and earlier; ASA 9.14 and earlier)
 Note |
The Firepower 4100 and 9300 also support either the ASA or threat defense, but they are installed as logical devices; see the FXOS configuration guides for more information. |
 Note |
For the threat defense on the ASA 5512-X through 5555-X, you must install a Cisco solid state drive (SSD). For more information, see the ASA 5500-X hardware guide. For the ASA, the SSD is also required to use the ASA FirePOWER module. (The SSD is standard on the ASA 5506-X, 5508-X, and 5516-X.) |
Reimage the Firepower or Secure Firewall
The Firepower and Secure Firewall models support either threat defense or ASA software.
Download Software
Obtain the threat defense software or ASA software.
 Note |
A Cisco.com login and Cisco service contract are required. |
|
Threat Defense Model |
Download Location |
Packages |
|---|---|---|
|
Firepower 1000 |
||
|
Threat Defense package Choose your model > Firepower Threat Defense Software > version. |
The package has a filename like cisco-ftd-fp1k.7.4.1-172SPA. |
|
| Secure Firewall 1200 | ||
|
Threat Defense package Choose your model > Firepower Threat Defense Software > version. |
The package has a filename like Cisco_Secure_FW_TD_1200-7.6.0-01.sh.REL.tar |
|
|
Firepower 2100 |
||
|
Threat Defense package Choose your model > Firepower Threat Defense Software > version. |
The package has a filename like cisco-ftd-fp2k.7.4.1-172SPA. |
|
|
Secure Firewall 3100 |
||
|
Threat Defense package Choose your model > Firepower Threat Defense Software > version. |
|
|
|
Secure Firewall 4200 |
||
|
Threat Defense package Choose your model > Firepower Threat Defense Software > version. |
The package has a filename like Cisco_Secure_FW_TD_4200-7.4.1-172.sh.REL.tar |
|
ASA Model |
Download Location |
Packages |
|---|---|---|
|
Firepower 1000 |
||
|
ASA package Choose your model > Adaptive Security Appliance (ASA) Software > version. |
The package has a filename like cisco-asa-fp1k.9.20.2.2.SPA. This package includes ASA and ASDM. |
|
|
ASDM software (upgrade) To upgrade to a later version of ASDM using your current ASDM or the ASA CLI, choose your model > Adaptive Security Appliance (ASA) Device Manager > version. |
The ASDM software file has a filename like asdm-7202.bin. |
|
| Secure Firewall 1200 | ||
|
Firepower 2100 |
||
|
ASA package Choose your model > Adaptive Security Appliance (ASA) Software > version. |
The package has a filename like cisco-asa-fp2k.9.20.2.2.SPA. This package includes ASA, ASDM, FXOS, and the Secure Firewall chassis manager (formerly Firepower Chassis Manager) . |
|
|
ASDM software (upgrade) To upgrade to a later version of ASDM using your current ASDM or the ASA CLI, choose your model > Adaptive Security Appliance (ASA) Device Manager > version. |
The ASDM software file has a filename like asdm-7202.bin. |
|
|
Secure Firewall 3100 |
||
|
ASA package Choose your model > Adaptive Security Appliance (ASA) Software > version. |
The package has a filename like cisco-asa-fp3k.9.20.2.2.SPA. This package includes ASA and ASDM. |
|
|
ASDM software (upgrade) To upgrade to a later version of ASDM using your current ASDM or the ASA CLI, choose your model > Adaptive Security Appliance (ASA) Device Manager > version. |
The ASDM software file has a filename like asdm-7202.bin. |
|
|
Secure Firewall 4200 series |
||
|
ASA package Choose your model > Adaptive Security Appliance (ASA) Software > version. |
The package has a filename like cisco-asa-fp4200.9.20.2.2.SPA. This package includes ASA and ASDM. |
|
|
ASDM software (upgrade) To upgrade to a later version of ASDM using your current ASDM or the ASA CLI, choose your model > Adaptive Security Appliance (ASA) Device Manager > version. |
The ASDM software file has a filename like asdm-7202.bin. |
ASA→Threat Defense: Firepower or Secure Firewall
This task lets you reimage a Firepower or a Secure Firewall device from ASA to threat defense by booting the threat defense image from the ASA software.
Before you begin
-
Make sure the image you want to upload is available on an FTP, HTTP(S), SCP, SMB, or TFTP server, or a USB drive formatted as EXT2/3/4 or VFAT/FAT32.
-
Make sure you can reach the server over an ASA interface. The default configuration includes:
-
Ethernet 1/2 (inside)—192.168.1.1
-
Management 1/1 (management)—1010/1210/1220: 192.168.45.1; Other models: DHCP and default route
-
Ethernet 1/1 (outside)—DHCP and default route
If you do not have a default route from DHCP and need to download from a remote server, set the route using the route command.
You can also use the configure factory-default command to set a static IP address for Management 1/1 (1010/1210/1220) or Ethernet 1/2 (other models).
-
-
To use copy to or from an SCP server, you have to:
-
Enable SSH access on the ASA for the SCP server subnet/host using the ssh command.
-
Generate a key pair using the crypto key generate command.
-
-
(Firepower 2100) In 9.12 and earlier, only Platform mode is available. In 9.13 and later, Appliance mode is the default. If you upgrade a Platform mode device to 9.13 or later, then the ASA remains in Platform mode. Check the mode by using the show fxos mode command at the ASA CLI. Other models only support Appliance mode.
If you have an ASA in Platform mode, you must use FXOS to reimage. See ASA→Threat Defense: Firepower 2100 Platform Mode.
-
(Secure Firewall 3100) To reimage from ASA to threat defense 7.3+ on the Secure Firewall 3100, you must first upgrade ASA to 9.19+ in order to update the ROMMON version to support the new image type introduced in 7.3. See the ASA upgrade guide.
Procedure
|
Step 1 |
Connect to the ASA CLI. |
||
|
Step 2 |
Unregister the ASA from the Smart Software Licensing server, either from the ASA CLI/ASDM or from the Smart Software Licensing server. license smart deregister Example: |
||
|
Step 3 |
Download the threat defense image to flash memory. This step shows an FTP copy. copy ftp://[[user@]server_ip[/path]/ftd_image_name diskn:/[path/]ftd_image_name To use the USB drive, specify disk1:// , except for the Firepower 2100, which uses disk2:// .
Example:Example: |
||
|
Step 4 |
Boot the threat defense image (the one you just uploaded). |
||
|
Step 5 |
Wait for the chassis to finish rebooting. FXOS comes up first, but you still need to wait for the threat defense to come up. After the application comes up and you connect to the application, you are prompted to accept the EULA and perform initial setup at the CLI. You can use either the Secure Firewall device manager (formerly Firepower Device Manager) or the Secure Firewall Management Center (formerly Firepower Management Center) to manage your device. See the Quick Start Guide for your model and your manager to continue setup: http://www.cisco.com/go/ftd-asa-quick Example: |
ASA→Threat Defense: Firepower 2100 Platform Mode
This task lets you reimage the Firepower 2100 in Platform mode to threat defense.
 Note |
After performing this procedure, the FXOS admin password is reset to Admin123. |
Before you begin
-
You must use the FXOS CLI for this procedure.
-
In 9.12 and earlier, only Platform mode is available. In 9.13 and later, Appliance mode is the default. If you upgrade a Platform mode device to 9.13 or later, then the ASA remains in Platform mode. Check the mode in 9.13 or later by using the show fxos mode command at the ASA CLI.
If you have an ASA in Appliance mode, you cannot access these FXOS commands; reimaging to the threat defense takes place in the ASA OS. See ASA→Threat Defense: Firepower or Secure Firewall.
Procedure
|
Step 1 |
Make sure the image you want to upload is available on an FTP, SCP, SFTP, or TFTP server connected to the FXOS Management 1/1 interface, or a USB drive formatted as EXT2/3/4 or VFAT/FAT32. To verify or change the FXOS Management 1/1 IP address, see the Firepower 2100 getting started guide. |
|
Step 2 |
Unregister the ASA from the Smart Software Licensing server, either from the ASA CLI/ASDM or from the Smart Software Licensing server. |
|
Step 3 |
Connect to the FXOS CLI, either the console port (preferred) or using SSH to the Management 1/1 interface. If you connect at the console port, you access the FXOS CLI immediately. Enter the FXOS login credentials. The default username is admin and the default password is Admin123. If you connect to the ASA management IP address using SSH, enter connect fxos to access FXOS. You can also SSH directly to the FXOS management IP address. |
|
Step 4 |
Download the package to the chassis. |
|
Step 5 |
When the new package finishes downloading (Downloaded state), boot the package. |
|
Step 6 |
Wait for the chassis to finish rebooting. FXOS comes up first, but you still need to wait for the threat defense to come up. After the application comes up and you connect to the application, you are prompted to accept the EULA and perform initial setup at the CLI. You can use either the device manager or the management center to manage your device. See the Quick Start Guide for your model and your manager to continue setup: http://www.cisco.com/go/ftd-asa-quick Example: |
Threat Defense→ASA: Firepower or Secure Firewall
This task lets you reimage the Firepower or the Secure Firewall device from threat defense to ASA. For the Firepower 2100 by default, the ASA is in Appliance mode. After you reimage, you can change it to Platform mode.
 Note |
After performing this procedure, the FXOS admin password is reset to Admin123. |
Procedure
|
Step 1 |
Make sure the image you want to upload is available on an FTP, HTTP(S), SCP, SFTP, or TFTP server connected to the Management 1/1 interface, or for the Secure Firewall 4200, Management 1/1 or 1/2, or a USB drive formatted as EXT2/3/4 or VFAT/FAT32. For more information about the Management interface settings, see the threat defense show network and configure network commands in Cisco Secure Firewall Threat Defense Command Reference. |
|
Step 2 |
Unlicense the threat defense.
|
|
Step 3 |
Connect to the FXOS CLI, either the console port (preferred) or using SSH to the Management interface. If you connect at the console port, you access the FXOS CLI immediately. Enter the FXOS login credentials. The default username is admin and the default password is Admin123. If you connect to the threat defense management IP address using SSH, enter connect fxos to access FXOS. |
|
Step 4 |
Download the package to the chassis. |
|
Step 5 |
When the new package finishes downloading (Downloaded state), boot the package. |
|
Step 6 |
Wait for the chassis to finish rebooting. ASA 9.13 and later (defaults to Appliance mode) The ASA starts up, and you access user EXEC mode at the CLI. Example:ASA 9.12 and earlier (defaults to Platform mode) FXOS comes up first, but you still need to wait for the ASA to come up. After the application comes up and you connect to the application, you access user EXEC mode at the CLI. Example: |
Threat Defense→Threat Defense: Firepower or Secure Firewall
For the Secure Firewall 3100 only, the reimage method depends on your current version.
Threat Defense→Threat Defense: Firepower or Secure Firewall (Except 3100)
These models offer multiple levels of reimaging, from erasing the configuration only, to replacing the image, to restoring the device to a factory default condition.
Procedure
|
Step 1 |
For reimaging procedures, see the troubleshooting guide. |
|
Step 2 |
If you want to load a new version, use the "Reimage the System with a New Software Version" procedure. Use the other reimaging methods for troubleshooting purposes, such as an inability to boot up or resetting the password. |
Threat Defense→Threat Defense: Secure Firewall 3100
The Secure Firewall 3100 offers multiple levels of reimaging, from erasing the configuration only, to replacing the image, to restoring the device to a factory default condition. See the following options for reimaging depending on your starting and ending version.
Procedure
|
Step 1 |
Reimage to 7.2, or 7.3+ to 7.3+: For reimaging procedures, see the troubleshooting guide. If you want to load a new version, use the "Reimage the System with a New Software Version" procedure. Use the other reimaging methods for troubleshooting purposes, such as an inability to boot up or resetting the password. |
||
|
Step 2 |
Reimage from 7.1/7.2 to 7.3+: If you want to reimage from 7.1/7.2 to 7.3+, you must first reimage to ASA 9.19+, then reimage to 7.3+. 7.3+ uses a new type of image file. Before you can use this image file, you need to update ROMMON, which is why you need to reimage to ASA 9.19+ (which is supported with the old ROMMON, but which also upgrades to the new ROMMON) before you can reimage to 7.3+. There is no separate ROMMON updater.
|
ASA→ASA: Firepower and Secure Firewall
Reimaging an ASA may be required to troubleshoot bootup issues and perform password recovery. For normal upgrading, you do not need to perform a reimage.
Procedure
|
Step 1 |
For reimaging procedures, see the troubleshooting guide. |
|
Step 2 |
To load a new software image, see the ASA Upgrade Guide instead of reimaging. |
Reimage the ASA 5500-X or ISA 3000
Many models in the ASA 5500-X or ISA 3000 series support either threat defense or ASA software.
Console Port Access Required
To perform the reimage, you must connect your computer to the console port.
For the ASA 5512-X, 5515-X, 5525-X, 5545-X, and 5555-X, you might need to use a third party serial-to-USB cable to make the connection. Other models include a Mini USB Type B console port, so you can use any mini USB cable. For Windows, you may need to install a USB-serial driver from software.cisco.com. See the hardware guide for more information about console port options and driver requirements: http://www.cisco.com/go/asa5500x-install
Use a terminal emulator set for 9600 baud, 8 data bits, no parity, 1 stop bit, no flow control.
Download Software
Obtain the threat defense software, or ASA, ASDM, and ASA FirePOWER module software. The procedures in this document require you to put software on a TFTP server for the initial download. Other images can be downloaded from other server types, such as HTTP or FTP. For the exact software package and server type, see the procedures.
 Note |
A Cisco.com login and Cisco service contract are required. |
 Attention |
The threat defense boot image and system package are version-specific and model-specific. Verify that you have the correct boot image and system package for your platform. A mismatch between the boot image and system package can cause boot failure. A mismatch would be using an older boot image with a newer system package. |
|
Threat Defense Model |
Download Location |
Packages |
||
|---|---|---|---|---|
|
ASA 5506-X, ASA 5508-X, and ASA 5516-X |
|
|||
|
Boot image Choose your model > Firepower Threat Defense Software > version. |
The boot image has a filename like ftd-boot-9.6.2.0.lfbff. |
|||
|
System software install package Choose your model > Firepower Threat Defense Software > version. |
The system software install package has a filename like ftd-6.1.0-330.pkg. |
|||
|
ASA 5512-X through ASA 5555-X |
|
|||
|
Boot image Choose your model > Firepower Threat Defense Software > version. |
The boot image has a filename like ftd-boot-9.6.2.0.cdisk. |
|||
|
System software install package Choose your model > Firepower Threat Defense Software > version. |
The system software install package has a filename like ftd-6.1.0-330.pkg. |
|||
|
ISA 3000 |
|
|||
|
Boot image Choose your model > Firepower Threat Defense Software > version. |
The boot image has a filename like ftd-boot-9.9.2.0.lfbff. |
|||
|
System software install package Choose your model > Firepower Threat Defense Software > version. |
The system software install package has a filename like ftd-6.2.3-330.pkg. |
|
ASA Model |
Download Location |
Packages |
|---|---|---|
|
ASA 5506-X, ASA 5508-X, and ASA 5516-X |
||
|
ASA Software Choose your model > Adaptive Security Appliance (ASA) Software > version. |
The ASA software file has a filename like asa962-lfbff-k8.SPA. |
|
|
ASDM Software Choose your model > Adaptive Security Appliance (ASA) Device Manager > version. |
The ASDM software file has a filename like asdm-762.bin. |
|
|
REST API Software Choose your model > Adaptive Security Appliance REST API Plugin > version. |
The API software file has a filename like asa-restapi-132-lfbff-k8.SPA. To install the REST API, see the API quick start guide |
|
|
ROMMON Software Choose your model > ASA Rommon Software > version. |
The ROMMON software file has a filename like asa5500-firmware-1108.SPA. |
|
|
ASA 5512-X through ASA 5555-X |
||
|
ASA Software Choose your model > Software on Chassis > Adaptive Security Appliance (ASA) Software > version. |
The ASA software file has a filename like asa962-smp-k8.bin. |
|
|
ASDM Software Choose your model > Software on Chassis > Adaptive Security Appliance (ASA) Device Manager > version. |
The ASDM software file has a filename like asdm-762.bin. |
|
|
REST API Software Choose your model > Software on Chassis > Adaptive Security Appliance REST API Plugin > version. |
The API software file has a filename like asa-restapi-132-lfbff-k8.SPA. To install the REST API, see the API quick start guide |
|
|
ASA Device Package for Cisco Application Policy Infrastructure Controller (APIC) Choose your model > Software on Chassis > ASA for Application Centric Infrastructure (ACI) Device Packages > version. |
For APIC 1.2(7) and later, choose either the Policy Orchestration with Fabric Insertion, or the Fabric Insertion-only package. The device package software file has a filename like asa-device-pkg-1.2.7.10.zip. To install the ASA device package, see the “Importing a Device Package” chapter of the Cisco APIC Layer 4 to Layer 7 Services Deployment Guide. |
|
|
ISA 3000 |
||
|
ASA Software Choose your model > Adaptive Security Appliance (ASA) Software > version. |
The ASA software file has a filename like asa962-lfbff-k8.SPA. |
|
|
ASDM Software Choose your model > Adaptive Security Appliance (ASA) Device Manager > version. |
The ASDM software file has a filename like asdm-762.bin. |
|
|
REST API Software Choose your model > Adaptive Security Appliance REST API Plugin > version. |
The API software file has a filename like asa-restapi-132-lfbff-k8.SPA. To install the REST API, see the API quick start guide. |
Upgrade the ROMMON Image (ASA 5506-X, 5508-X, and 5516-X, ISA 3000)
Follow these steps to upgrade the ROMMON image for the ASA 5506-X series, ASA 5508-X, ASA 5516-X, and ISA 3000. For the ASA models, the ROMMON version on your system must be 1.1.8 or greater. We recommend that you upgrade to the latest version.
You can only upgrade to a new version; you cannot downgrade.
 Caution |
The ASA 5506-X, 5508-X, and 5516-X ROMMON upgrade for 1.1.15 and the ISA 3000 ROMMON upgrade for 1.0.5 takes twice as long as previous ROMMON versions, approximately 15 minutes. Do not power cycle the device during the upgrade. If the upgrade is not complete within 30 minutes or it fails, contact Cisco technical support; do not power cycle or reset the device. |
Before you begin
Obtain the new ROMMON image from Cisco.com, and put it on a server to copy to the ASA. The ASA supports FTP, TFTP, SCP, HTTP(S), and SMB servers. Download the image from:
-
ASA 5506-X, 5508-X, 5516-X: https://software.cisco.com/download/home/286283326/type
-
ISA 3000: https://software.cisco.com/download/home/286288493/type
Procedure
|
Step 1 |
For threat defense software, enter the Diagnostic CLI, and then enter enable mode. system support diagnostic-cli enable Press enter without entering a password when prompted for a password. Example: |
|
Step 2 |
Copy the ROMMON image to the ASA flash memory. This procedure shows an FTP copy; enter copy ? for the syntax for other server types. copy ftp://[username:password@]server_ip/asa5500-firmware-xxxx.SPA disk0:asa5500-firmware-xxxx.SPA For threat defense software, make sure you have a data interface configured; the diagnostic CLI does not have access to the dedicated Management interface. Also due to CSCvn57678, the copy command may not work in the regular threat defense CLI for your threat defense version, so you cannot access the dedicated Management interface with that method. |
|
Step 3 |
To see your current version, enter the show module command and look at the Fw Version in the output for Mod 1 in the MAC Address Range table: |
|
Step 4 |
Upgrade the ROMMON image: upgrade rommon disk0:asa5500-firmware-xxxx.SPA Example: |
|
Step 5 |
Confirm to reload the ASA when you are prompted. The ASA upgrades the ROMMON image, and then reloads the operating system. |
ASA→Threat Defense: ASA 5500-X or ISA 3000
To reimage the ASA to threat defense software, you must access the ROMMON prompt. In ROMMON, you must use TFTP on the Management interface to download the threat defense boot image; only TFTP is supported. The boot image can then download the threat defense system software install package using HTTP or FTP. The TFTP download can take a long time; ensure that you have a stable connection between the ASA and the TFTP server to avoid packet loss.
Before you begin
To ease the process of reimaging back to an ASA, do the following:
-
Perform a complete system backup using the backup command.
See the configuration guide for more information, and other backup techniques.
-
Copy and save the current activation key(s) so you can reinstall your licenses using the show activation-key command.
-
For the ISA 3000, disable hardware bypass when using the management center; this feature is only available using the device manager in version 6.3 and later.
Procedure
|
Step 1 |
Download the threat defense boot image (see Download Software) to a TFTP server accessible by the ASA on the Management interface. For the ASA 5506-X, 5508-X, 5516-X, ISA 3000: You must use the Management 1/1 port to download the image. For the other models, you can use any interface. |
||
|
Step 2 |
Download the threat defense system software install package (see Download Software) to an HTTP or FTP server accessible by the ASA on the Management interface. |
||
|
Step 3 |
From the console port, reload the ASA: reload Example: |
||
|
Step 4 |
Press Esc during the bootup when prompted to reach the ROMMON prompt. Pay close attention to the monitor. Example:Press Esc at this point. If you see the following message, then you waited too long, and must reload the ASA again after it finishes booting: |
||
|
Step 5 |
Set the network settings, and load the boot image using the following ROMMON commands: interface interface_id address management_ip_address netmask subnet_mask server tftp_ip_address gateway gateway_ip_address filepath/filename set sync tftpdnld The threat defense boot image downloads and boots up to the boot CLI. See the following information:
Example:Example for the ASA 5555-X: Example for the ASA 5506-X: Ping to troubleshoot connectivity to the server: |
||
|
Step 6 |
Enter setup , and configure network settings for the Management interface to establish temporary connectivity to the HTTP or FTP server so that you can download and install the system software package.
Example: |
||
|
Step 7 |
Download the threat defense system software install package. This step shows an HTTP installation. system install [noconfirm] url Include the noconfirm option if you do not want to respond to confirmation messages. Example:You are prompted to erase the internal flash drive. Enter y. The installation process erases the flash drive and downloads the system image. You are prompted to continue with the installation. Enter y. When the installation finishes, press Enter to reboot the device. The reboot takes upwards of 30 minutes, and could take much longer. Upon reboot, you will be in the threat defense CLI. |
||
|
Step 8 |
To troubleshoot network connectivity, see the following examples. Example:View the network interface configuration: Ping a server: Traceroute to test network connectivity: |
||
|
Step 9 |
To troubleshoot installation failures, see the following examples. Example:"Timed out" error At the downloading stage, if the file server is not reachable, it will fail due to a time out. In this case, make sure the file server is reachable from the ASA. You can verify by pinging the file server. "Package not found" error If the file server is reachable, but the file path or name is wrong, the installation fails with a "Package not found" error: In this case, make sure the threat defense package file path and name is correct. Installation failed with unknown error When the installation occurs after the system software has been downloaded, the cause is generally displayed as "Installation failed with unknown error". When this error happens, you can troubleshoot the failure by viewing the installation log: You can also view the upgrade.log, pyos.log, and commandd.log under /var/log/cisco with the same command for boot CLI related issues. |
||
|
Step 10 |
You can use either the device manager or the management center to manage your device. See the Quick Start Guide for your model and your manager to continue setup: http://www.cisco.com/go/ftd-asa-quick |
Threat Defense→ASA: ASA 5500-X or ISA 3000
To reimage the threat defense to ASA software, you must access the ROMMON prompt. In ROMMON, you must erase the disks, and then use TFTP on the Management interface to download the ASA image; only TFTP is supported. After you reload the ASA, you can configure basic settings and then load the FirePOWER module software.
Before you begin
-
Ensure that you have a stable connection between the ASA and the TFTP server to avoid packet loss.
Procedure
|
Step 1 |
If you are managing the threat defense from the management center, delete the device from the management center. |
|
Step 2 |
If you are managing the threat defense using the device manager, be sure to unregister the device from the Smart Software Licensing server, either from the device manager or from the Smart Software Licensing server. |
|
Step 3 |
Download the ASA image (see Download Software) to a TFTP server accessible by the threat defense on the Management interface. For the ASA 5506-X, 5508-X, 5516-X, ISA 3000: You must use the Management 1/1 port to download the image. For the other models, you can use any interface. |
|
Step 4 |
At the console port, reboot the threat defense device. reboot Enter yes to reboot. Example: |
|
Step 5 |
Press Esc during the bootup when prompted to reach the ROMMON prompt. Pay close attention to the monitor. Example:Press Esc at this point. If you see the following message, then you waited too long, and must reboot the threat defense again after it finishes booting: |
|
Step 6 |
Erase all disk(s) on the threat defense. The internal flash is called disk0. If you have an external USB drive, it is disk1. Example:This step erases the threat defense files so that the ASA does not try to load an incorrect configuration file, which causes numerous errors. |
|
Step 7 |
Set the network settings, and load the ASA image using the following ROMMON commands. interface interface_id address management_ip_address netmask subnet_mask server tftp_ip_address gateway gateway_ip_address filepath/filename set sync tftpdnld The ASA image downloads and boots up to the CLI. See the following information:
Example:Example for the ASA 5555-X: Example for the ASA 5506-X: Example:Ping to troubleshoot connectivity to the server: |
|
Step 8 |
Configure network settings and prepare the disks. When the ASA first boots up, it does not have any configuration on it. you can either follow the interactive prompts to configure the Management interface for ASDM access, or you can paste a saved configuration or, if you do not have a saved configuration, the recommended configuration (below). If you do not have a saved configuration, we suggest pasting the recommended configuration if you are planning to use the ASA FirePOWER module. The ASA FirePOWER module is managed on the Management interface and needs to reach the internet for updates. The simple, recommended network deployment includes an inside switch that lets you connect Management (for FirePOWER management only), an inside interface (for ASA management and inside traffic), and your management PC to the same inside network. See the quick start guide for more information about the network deployment: |
|
Step 9 |
Install the ASA and ASDM images. Booting the ASA from ROMMON mode does not preserve the system image across reloads; you must still download the image to flash memory. You also need to download ASDM to flash memory. |
|
Step 10 |
(Optional) Install the ASA FirePOWER module software. You need to install the ASA FirePOWER boot image, partition the SSD, and install the system software according to this procedure.
|
|
Step 11 |
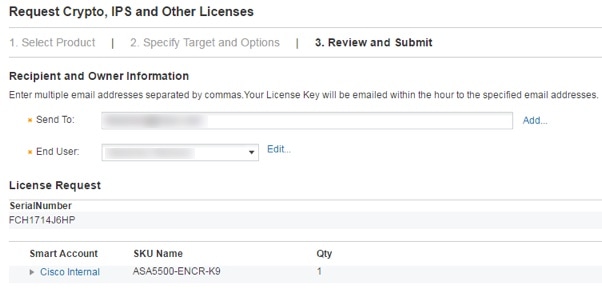
Obtain a Strong Encryption license and other licenses for an existing ASA for which you did not save the activation key: see http://www.cisco.com/go/license. In the section you can re-download your licenses. To use ASDM (and many other features), you need to install the Strong Encryption (3DES/AES) license. If you saved your license activation key from this ASA before you previously reimaged to the threat defense device, you can re-install the activation key. If you did not save the activation key but own licenses for this ASA, you can re-download the license. For a new ASA, you will need to request new ASA licenses. |
|
Step 12 |
Obtain licenses for a new ASA. |
|
Step 13 |
Apply the activation key. activation-key key Example:Because this ASA did not yet have an activation key installed, you see the “Failed to retrieve permanent activation key.” message. You can ignore this message. You can only install one permanent key, and multiple time-based keys. If you enter a new permanent key, it overwrites the already installed one. If you ordered additional licenses after you installed the 3DES/AES license, the combined activation key includes all licenses plus the 3DES/AES license, so you can overwrite the 3DES/AES-only key. |
|
Step 14 |
The ASA FirePOWER module uses a separate licensing mechanism from the ASA. No licenses are pre-installed, but depending on your order, the box might include a PAK on a printout that lets you obtain a license activation key for the following licenses:
If you did not buy an ASA 5500-X that included the ASA FirePOWER services, then you can purchase an upgrade bundle to obtain the necessary licenses. See the Cisco ASA with FirePOWER Services Ordering Guide for more information. Other licenses that you can purchase include the following:
These licenses do generate a PAK/license activation key for the ASA FirePOWER module. See the Cisco ASA with FirePOWER Services Ordering Guide for ordering information. See also the Cisco Secure Firewall Management Center Feature Licenses. To install the Control and Protection licenses and other optional licenses, see the ASA quick start guide for your model. |
Threat Defense→Threat Defense: ASA 5500-X or ISA 3000
This procedure describes how to use ROMMON to reimage an existing threat defense to a new version of threat defense software. This procedure restores the device to a factory default condition. If you want to perform a regular upgrade, see the upgrade guide instead.
In ROMMON, you must use TFTP on the management interface to download the new threat defense boot image; only TFTP is supported. The boot image can then download the threat defense system software install package using HTTP or FTP. The TFTP download can take a long time; ensure that you have a stable connection between the threat defense and the TFTP server to avoid packet loss.
Procedure
|
Step 1 |
If you are managing the threat defense using the management center, delete the device from the management center. |
||
|
Step 2 |
If you are managing the threat defense using device manager, be sure to unregister the device in the Smart Software Licensing server, either from the device manager or from the Smart Software Licensing server. |
||
|
Step 3 |
Download the threat defense boot image (see Download Software) to a TFTP server accessible by the threat defense on the Management interface. For the ASA 5506-X, 5508-X, 5516-X, ISA 3000: You must use the Management 1/1 port to download the image. For the other models, you can use any interface. |
||
|
Step 4 |
Download the threat defense system software install package (see Download Software) to an HTTP or FTP server accessible by the threat defense on the management interface. |
||
|
Step 5 |
At the console port, reboot the threat defense device. reboot Example:Enter yes to reboot. Example: |
||
|
Step 6 |
Press Esc during the bootup when prompted to reach the ROMMON prompt. Pay close attention to the monitor. Example:Press Esc at this point. If you see the following message, then you waited too long, and must reload the threat defense again after it finishes booting: |
||
|
Step 7 |
Erase all disk(s) on the threat defense. The internal flash is called disk0. If you have an external USB drive, it is disk1. Example:This step erases the old threat defense boot and system images. If you do not erase the system image, you must remember to escape out of the boot process after you load the boot image in the next step; if you miss the escape window, the threat defense will continue to load the old threat defense system image, which can take a long time, and you will have to start the procedure over again. |
||
|
Step 8 |
Set the network settings, and load the new boot image using the following ROMMON commands: interface interface_id address management_ip_address netmask subnet_mask server tftp_ip_address gateway gateway_ip_address file path/filename set sync tftpdnld The threat defense boot image downloads and boots up to the boot CLI.
See the following information:
Example:Example for the ASA 5508-X: Example for the ASA 5555-X: Ping to troubleshoot connectivity to the server: |
||
|
Step 9 |
Enter setup , and configure network settings for the Management interface to establish temporary connectivity to the HTTP or FTP server so that you can download and install the system software package.
Example: |
||
|
Step 10 |
Download the threat defense system software install package. This step shows an HTTP installation. system install [noconfirm] url Include the noconfirm option if you do not want to respond to confirmation messages. Example:You are prompted to erase the internal flash drive. Enter y. The installation process erases the flash drive and downloads the system image. You are prompted to continue with the installation. Enter y. When the installation finishes, press Enter to reboot the device. The reboot takes upwards of 30 minutes, and could take much longer. Upon reboot, you will be in the threat defense CLI. |
||
|
Step 11 |
To troubleshoot network connectivity, see the following examples. Example:View the network interface configuration: Ping a server: Traceroute to test network connectivity: |
||
|
Step 12 |
To troubleshoot installation failures, see the following examples. Example:"Timed out" error At the downloading stage, if the file server is not reachable, it will fail due to a time out. In this case, make sure the file server is reachable from the ASA. You can verify by pinging the file server. "Package not found" error If the file server is reachable, but the file path or name is wrong, the installation fails with a "Package not found" error: In this case, make sure the threat defense package file path and name is correct. Installation failed with unknown error When the installation occurs after the system software has been downloaded, the cause is generally displayed as "Installation failed with unknown error". When this error happens, you can troubleshoot the failure by viewing the installation log: You can also view the upgrade.log, pyos.log, and commandd.log under /var/log/cisco with the same command for boot CLI related issues. |
||
|
Step 13 |
You can use either the device manager or the management center to manage your device. See the Quick Start Guide for your model and your manager to continue setup: http://www.cisco.com/go/ftd-asa-quick |
ASA→ASA: ASA 5500-X or ISA 3000
If you cannot boot up, you can boot an image using ROMMON. You can then download a new image file to flash memory from the ASA OS.
Procedure
|
Step 1 |
Power off the ASA, then power it on. |
||
|
Step 2 |
During startup, press the Escape key when you are prompted to enter ROMMON mode. |
||
|
Step 3 |
In ROMMOM mode, define the interface settings to the ASA, including the IP address, TFTP server address, gateway address, software image file, and port, as follows:
|
||
|
Step 4 |
Validate your settings: |
||
|
Step 5 |
Ping the TFTP server: |
||
|
Step 6 |
Save the network settings for future use: |
||
|
Step 7 |
Load the software image: After the software image is successfully loaded, the ASA automatically exits ROMMON mode. |
||
|
Step 8 |
Booting the ASA from ROMMON mode does not preserve the system image across reloads; you must still download the image to flash memory. See the Cisco ASA Upgrade Guide for full upgrade procedures. |
What’s Next?
See the quick start guide for your model and management application:
-
ASA 5506-X
-
ASA 5512-X through ASA 5555-X
 Feedback
Feedback