تكوين Dynamic Multipoint VPN باستخدام GRE عبر IPsec مع OSPF و NAT وجدار حماية Cisco IOS
المحتويات
المقدمة
يزود هذا وثيقة عينة تشكيل ل Dynamic Multipoint VPN (DMVPN) يستعمل تحشد عام (GRE) عبر IPsec مع فتح أقصر مسار أولا (OSPF)، شبكة ترجمة عنوان (NAT)، و cisco IOS® جدار حماية.
المتطلبات الأساسية
المتطلبات
قبل إنشاء نفق GRE متعدد النقاط (mGRE) و IPsec، يجب تحديد سياسة تبادل مفتاح الإنترنت (IKE) باستخدام أمر سياسة التشفير isakmp.
ملاحظة: أستخدم أداة بحث الأوامر (للعملاء المسجلين فقط) للحصول على مزيد من المعلومات حول الأوامر المستخدمة في هذا القسم.
المكونات المستخدمة
تستند المعلومات الواردة في هذا المستند إلى إصدارات البرامج والمكونات المادية التالية:
-
برنامج Cisco IOS® الإصدار 12.2(15)T1 على الموجه الموجه الموجه وبرنامج Cisco IOS Software الإصدار 12.3(1.6) على الموجهات التي يتم التحدث بها
-
الموجه Cisco 3620 كموجه محوري، موجهات Cisco 1720 وموجه Cisco 3620 واحد كموجهات يتم التحدث بها
تم إنشاء المعلومات الواردة في هذا المستند من الأجهزة الموجودة في بيئة معملية خاصة. بدأت جميع الأجهزة المُستخدمة في هذا المستند بتكوين ممسوح (افتراضي). إذا كانت شبكتك مباشرة، فتأكد من فهمك للتأثير المحتمل لأي أمر.
الاصطلاحات
راجع اصطلاحات تلميحات Cisco التقنية للحصول على مزيد من المعلومات حول اصطلاحات المستندات.
التكوين
في هذا القسم، تُقدّم لك معلومات تكوين الميزات الموضحة في هذا المستند.
ملاحظة: أستخدم أداة بحث الأوامر (للعملاء المسجلين فقط) للحصول على مزيد من المعلومات حول الأوامر المستخدمة في هذا القسم.
الرسم التخطيطي للشبكة
يستخدم هذا المستند إعداد الشبكة التالي.
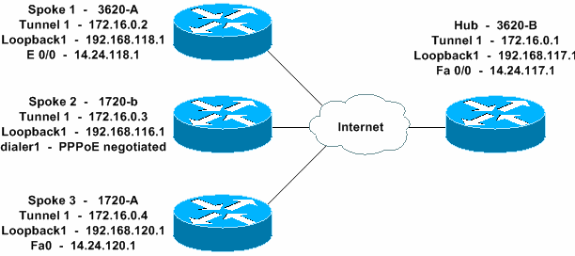
التكوينات
يستخدم هذا المستند هذه التكوينات.
| الموزع - 3620-B |
|---|
W2N-6.16-3620-B#write terminal Building configuration... Current configuration : 2613 bytes ! version 12.2 service timestamps debug datetime msec service timestamps log datetime msec no service password-encryption ! hostname W2N-6.16-3620-B ! logging queue-limit 100 ! memory-size iomem 10 ip subnet-zero ! ! ip cef no ip domain lookup ! !--- This is the Cisco IOS Firewall configuration and what to inspect. !--- This is applied outbound on the external interface. ip inspect name in2out rcmd ip inspect name in2out ftp ip inspect name in2out tftp ip inspect name in2out tcp timeout 43200 ip inspect name in2out http ip inspect name in2out udp ip audit po max-events 100 ! ! ! !--- Create an Internet Security Association and Key Management !--- Protocol (ISAKMP) policy for Phase 1 negotiations. crypto isakmp policy 5 authentication pre-share group 2 !--- Add dynamic pre-shared key. crypto isakmp key dmvpnkey address 0.0.0.0 0.0.0.0 crypto isakmp nat keepalive 20 ! ! !--- Create the Phase 2 policy for actual data encryption. crypto ipsec transform-set dmvpnset esp-3des esp-sha-hmac ! !--- Create an IPsec profile to be applied dynamically !--- to the GRE over IPsec tunnels. crypto ipsec profile dmvpnprof set transform-set dmvpnset ! ! ! ! ! ! ! ! ! ! ! no voice hpi capture buffer no voice hpi capture destination ! ! mta receive maximum-recipients 0 ! ! ! !--- This is the inbound interface. interface Loopback1 ip address 192.168.117.1 255.255.255.0 ip nat inside ! !--- Create a GRE tunnel template to be applied !--- to all the dynamically created GRE tunnels. interface Tunnel1 description MULTI-POINT GRE TUNNEL for BRANCHES bandwidth 1000 ip address 172.16.0.1 255.255.255.0 no ip redirects ip mtu 1416 ip nhrp authentication dmvpn ip nhrp map multicast dynamic ip nhrp network-id 99 ip nhrp holdtime 300 no ip route-cache ip ospf network broadcast no ip mroute-cache delay 1000 tunnel source FastEthernet0/0 tunnel mode gre multipoint tunnel key 100000 tunnel protection ipsec profile dmvpnprof ! !--- This is the outbound interface. interface FastEthernet0/0 ip address 14.24.117.1 255.255.0.0 ip nat outside ip access-group 100 in ip inspect in2out out no ip mroute-cache duplex auto speed auto ! interface Serial0/0 no ip address shutdown clockrate 2000000 no fair-queue ! interface FastEthernet0/1 no ip address no ip mroute-cache duplex auto speed auto ! !--- Enable a routing protocol to send/receive dynamic !--- updates about the private networks. router ospf 1 log-adjacency-changes network 172.16.0.0 0.0.0.255 area 0 network 192.168.117.0 0.0.0.255 area 0 ! !--- Except the private network traffic from the NAT process. ip nat inside source route-map nonat interface FastEthernet0/0 overload ip http server no ip http secure-server ip classless ip route 0.0.0.0 0.0.0.0 14.24.1.1 ip route 2.0.0.0 255.0.0.0 14.24.121.1 ! ! ! !--- Allow ISAKMP, ESP, and GRE traffic inbound. !--- Cisco IOS Firewall opens other inbound access as needed. access-list 100 permit udp any host 14.24.117.1 eq 500 access-list 100 premit esp any host 14.24.117.1 access-list 100 permit gre any host 14.24.117.1 access-list 100 deny ip any any !--- Except the private network traffic from the NAT process. access-list 110 deny ip 192.168.117.0 0.0.0.255 192.168.118.0 0.0.0.255 access-list 110 deny ip 192.168.117.0 0.0.0.255 192.168.116.0 0.0.0.255 access-list 110 deny ip 192.168.117.0 0.0.0.255 192.168.120.0 0.0.0.255 access-list 110 permit ip 192.168.117.0 0.0.0.255 any ! !--- Except the private network traffic from the NAT process. route-map nonat permit 10 match ip address 110 ! call rsvp-sync ! ! mgcp profile default ! dial-peer cor custom ! ! ! ! ! line con 0 exec-timeout 0 0 line aux 0 line vty 0 4 login ! ! end W2N-6.16-3620-B# |
| تحدث 1 - 3620 - ألف |
|---|
W2N-6.16-3620-A#write terminal Building configuration... Current configuration : 2678 bytes ! version 12.2 service timestamps debug uptime service timestamps log uptime no service password-encryption ! hostname W2N-6.16-3620-A ! boot system flash slot0:c3620-ik9o3s7-mz.122-15.T1.bin logging queue-limit 100 ! memory-size iomem 15 ip subnet-zero ! ! ip cef no ip domain lookup ! !--- This is the Cisco IOS Firewall configuration and what to inspect. !--- This is applied outbound on the external interface. ip inspect name in2out rcmd ip inspect name in2out tftp ip inspect name in2out udp ip inspect name in2out tcp timeout 43200 ip inspect name in2out realaudio ip inspect name in2out vdolive ip inspect name in2out netshow ip audit po max-events 100 ! ! ! !--- Create an ISAKMP policy for !--- Phase 1 negotiations. crypto isakmp policy 5 authentication pre-share group 2 !--- Add dynamic pre-shared key. crypto isakmp key dmvpnkey address 0.0.0.0 0.0.0.0 ! ! !--- Create the Phase 2 policy for actual data encryption. crypto ipsec transform-set dmvpnset esp-3des esp-sha-hmac ! !--- Create an IPsec profile to be applied dynamically !--- to the GRE over IPsec tunnels. crypto ipsec profile dmvpnprof set transform-set dmvpnset ! ! ! ! ! ! ! ! ! ! ! no voice hpi capture buffer no voice hpi capture destination ! ! mta receive maximum-recipients 0 ! ! ! !--- This is the inbound interface. interface Loopback1 ip address 192.168.118.1 255.255.255.0 ip nat inside ! !--- Create a GRE tunnel template to be applied to !--- all the dynamically created GRE tunnels. interface Tunnel1 description HOST DYNAMIC TUNNEL bandwidth 1000 ip address 172.16.0.2 255.255.255.0 no ip redirects ip mtu 1416 ip nhrp authentication dmvpn ip nhrp map multicast dynamic ip nhrp map 172.16.0.1 14.24.117.1 ip nhrp map multicast 14.24.117.1 ip nhrp network-id 99 ip nhrp holdtime 300 ip nhrp nhs 172.16.0.1 no ip route-cache ip ospf network broadcast no ip mroute-cache delay 1000 tunnel source Ethernet0/0 tunnel mode gre multipoint tunnel key 100000 tunnel protection ipsec profile dmvpnprof ! !--- This is the outbound interface. interface Ethernet0/0 ip address 14.24.118.1 255.255.0.0 ip nat outside ip access-group 100 in ip inspect in2out out no ip mroute-cache half-duplex ! interface Ethernet0/1 no ip address half-duplex ! interface Ethernet0/2 no ip address shutdown half-duplex ! interface Ethernet0/3 no ip address shutdown half-duplex ! !--- Enable a routing protocol to send/receive dynamic !--- updates about the private networks. router ospf 1 log-adjacency-changes redistribute connected network 172.16.0.0 0.0.0.255 area 0 network 192.168.118.0 0.0.0.255 area 0 ! !--- Except the private network traffic from the NAT process. ip nat inside source route-map nonat interface Ethernet0/0 overload ip http server no ip http secure-server ip classless ip route 0.0.0.0 0.0.0.0 14.24.1.1 ip route 2.0.0.0 255.0.0.0 14.24.121.1 ! ! ! !--- Allow ISAKMP, ESP, and GRE traffic inbound. !--- Cisco IOS Firewall opens inbound access as needed. access-list 100 permit udp any host 14.24.118.1 eq 500 access-list 100 premit esp any host 14.24.118.1 access-list 100 permit gre any host 14.24.118.1 access-list 100 deny ip any any !--- Except the private network traffic from the NAT process. access-list 110 deny ip 192.168.118.0 0.0.0.255 192.168.117.0 0.0.0.255 access-list 110 deny ip 192.168.118.0 0.0.0.255 192.168.116.0 0.0.0.255 access-list 110 deny ip 192.168.118.0 0.0.0.255 192.168.120.0 0.0.0.255 access-list 110 permit ip 192.168.118.0 0.0.0.255 any ! !--- Except the private network traffic from the NAT process. route-map nonat permit 10 match ip address 110 ! call rsvp-sync ! ! mgcp profile default ! dial-peer cor custom ! ! ! ! ! line con 0 exec-timeout 0 0 line aux 0 line vty 0 4 login ! ! end W2N-6.16-3620-A# |
| تكلم 2 - 1720-ب |
|---|
1720-b#write terminal Building configuration... Current configuration : 2623 bytes ! version 12.2 service timestamps debug uptime service timestamps log uptime no service password-encryption ! hostname 1720-b ! logging queue-limit 100 enable password cisco ! username 7206-B password 0 cisco ip subnet-zero ! ! no ip domain lookup ! ip cef !--- This is the Cisco IOS Firewall configuration and what to inspect. !--- This is applied outbound on the external interface. ip inspect name in2out rcmd ip inspect name in2out tftp ip inspect name in2out udp ip inspect name in2out tcp timeout 43200 ip inspect name in2out realaudio ip inspect name in2out vdolive ip inspect name in2out netshow ip audit po max-events 100 vpdn-group 1 request-dialin protocol pppoe ! ! ! ! ! !--- Create an ISAKMP policy for !--- Phase 1 negotiations. crypto isakmp policy 5 authentication pre-share group 2 !--- Add dynamic pre-shared key. crypto isakmp key dmvpnkey address 0.0.0.0 0.0.0.0 ! ! !--- Create the Phase 2 policy for actual data encryption. crypto ipsec transform-set dmvpnset esp-3des esp-sha-hmac ! !--- Create an IPsec profile to be applied dynamically !--- to the GRE over IPsec tunnels. crypto ipsec profile dmvpnprof set transform-set dmvpnset ! ! ! ! ! !--- This is the inbound interface. interface Loopback1 ip address 192.168.116.1 255.255.255.0 ip nat inside ! !--- Create a GRE tunnel template to be applied to !--- all the dynamically created GRE tunnels. interface Tunnel1 description HOST DYNAMIC TUNNEL bandwidth 1000 ip address 172.16.0.3 255.255.255.0 no ip redirects ip mtu 1416 ip nhrp authentication dmvpn ip nhrp map multicast dynamic ip nhrp map 172.16.0.1 14.24.117.1 ip nhrp map multicast 14.24.117.1 ip nhrp network-id 99 ip nhrp holdtime 300 ip nhrp nhs 172.16.0.1 no ip route-cache ip ospf network broadcast no ip mroute-cache delay 1000 tunnel source Dialer1 tunnel mode gre multipoint tunnel key 100000 tunnel protection ipsec profile dmvpnprof ! interface Ethernet0 no ip address half-duplex ! interface FastEthernet0 no ip address no ip mroute-cache speed auto pppoe enable pppoe-client dial-pool-number 1 ! !--- This is the outbound interface. interface Dialer1 ip address 2.2.2.10 255.255.255.0 ip inspect in2out out ip access-group 100 in encapsulation ppp dialer pool 1 dialer-group 1 ppp authentication pap chap callin ! !--- Enable a routing protocol to send/receive dynamic !--- updates about the private networks. router ospf 1 log-adjacency-changes redistribute connected network 172.16.0.0 0.0.0.255 area 0 network 192.168.116.0 0.0.0.255 area 0 ! !--- Except the private network traffic from the NAT process. ip nat inside source route-map nonat interface Dialer1 overload ip classless ip route 0.0.0.0 0.0.0.0 14.24.1.1 ip route 0.0.0.0 0.0.0.0 Dialer1 no ip http server no ip http secure-server ! ! ! !--- Allow ISAKMP, ESP, and GRE traffic inbound. !--- Cisco IOS Firewall opens inbound access as needed. access-list 100 permit udp any host 14.24.116.1 eq 500 access-list 100 premit esp any host 14.24.116.1 access-list 100 permit gre any host 14.24.116.1 access-list 100 deny ip any any !--- Except the private network traffic from the NAT process. access-list 110 deny ip 192.168.116.0 0.0.0.255 192.168.117.0 0.0.0.255 access-list 110 deny ip 192.168.116.0 0.0.0.255 192.168.118.0 0.0.0.255 access-list 110 deny ip 192.168.116.0 0.0.0.255 192.168.120.0 0.0.0.255 access-list 110 permit ip 192.168.116.0 0.0.0.255 any dialer-list 1 protocol ip permit ! !--- Except the private network traffic from the NAT process. route-map nonat permit 10 match ip address 110 ! ! line con 0 exec-timeout 0 0 line aux 0 line vty 0 4 login ! no scheduler allocate end 1720-b# |
| تكلم 3 - 1720 - ألف |
|---|
W2N-6.16-1720-A#write terminal Building configuration... Current configuration : 2303 bytes ! version 12.2 service timestamps debug datetime msec service timestamps log datetime msec no service password-encryption ! hostname W2N-6.16-1720-A ! logging queue-limit 100 ! memory-size iomem 25 ip subnet-zero ! ! no ip domain lookup ! ip cef !--- This is the Cisco IOS Firewall configuration and what to inspect. !--- This is applied outbound on the external interface. ip inspect name in2out rcmd ip inspect name in2out tftp ip inspect name in2out udp ip inspect name in2out tcp timeout 43200 ip inspect name in2out realaudio ip inspect name in2out vdolive ip inspect name in2out netshow ip audit notify log ip audit po max-events 100 ! ! ! ! !--- Create an ISAKMP policy for !--- Phase 1 negotiations. crypto isakmp policy 5 authentication pre-share group 2 !--- Add dynamic pre-shared key. crypto isakmp key dmvpnkey address 0.0.0.0 0.0.0.0 ! ! !--- Create the Phase 2 policy for actual data encryption. crypto ipsec transform-set dmvpnset esp-3des esp-sha-hmac ! !--- Create an IPsec profile to be applied dynamically !--- to the GRE over IPsec tunnels. crypto ipsec profile dmvpnprof set transform-set dmvpnset ! ! ! ! ! !--- This is the inbound interface. interface Loopback1 ip address 192.168.120.1 255.255.255.0 ip nat inside ! !--- Create a GRE tunnel template to be applied to !--- all the dynamically created GRE tunnels. interface Tunnel1 description HOST DYNAMIC TUNNEL bandwidth 1000 ip address 172.16.0.4 255.255.255.0 no ip redirects ip mtu 1416 ip nhrp authentication dmvpn ip nhrp map multicast dynamic ip nhrp map 172.16.0.1 14.24.117.1 ip nhrp map multicast 14.24.117.1 ip nhrp network-id 99 ip nhrp holdtime 300 ip nhrp nhs 172.16.0.1 ip ospf network broadcast no ip mroute-cache delay 1000 tunnel source FastEthernet0 tunnel mode gre multipoint tunnel key 100000 tunnel protection ipsec profile dmvpnprof ! interface Ethernet0 no ip address no ip mroute-cache half-duplex ! !--- This is the outbound interface. interface FastEthernet0 ip address 14.24.120.1 255.255.0.0 ip nat outside ip inspect in2out out ip access-group 100 in no ip mroute-cache speed auto ! !--- Enable a routing protocol to send/receive dynamic !--- updates about the private networks. router ospf 1 log-adjacency-changes redistribute connected network 172.16.0.0 0.0.0.255 area 0 network 192.168.120.0 0.0.0.255 area 0 ! !--- Except the private network traffic from the NAT process. ip nat inside source route-map nonat interface FastEthernet0 overload ip classless ip route 0.0.0.0 0.0.0.0 14.24.1.1 ip route 2.0.0.0 255.0.0.0 14.24.121.1 no ip http server no ip http secure-server ! ! ! !--- Allow ISAKMP, ESP, and GRE traffic inbound. !--- Cisco IOS Firewall opens inbound access as needed. access-list 100 permit udp any host 14.24.116.1 eq 500 access-list 100 premit esp any host 14.24.116.1 access-list 100 permit gre any host 14.24.116.1 access-list 100 deny ip any any access-list 110 permit ip 192.168.120.0 0.0.0.255 any !--- Except the private network traffic from the NAT process. access-list 110 deny ip 192.168.120.0 0.0.0.255 192.168.116.0 0.0.0.255 access-list 110 deny ip 192.168.120.0 0.0.0.255 192.168.117.0 0.0.0.255 access-list 110 deny ip 192.168.120.0 0.0.0.255 192.168.118.0 0.0.0.255 access-list 110 permit ip 192.168.120.0 0.0.0.255 any ! !--- Except the private network traffic from the NAT process. route-map nonat permit 10 match ip address 110 ! ! line con 0 exec-timeout 0 0 line aux 0 line vty 0 4 login ! end W2N-6.16-1720-A# |
التحقق من الصحة
استخدم هذا القسم لتأكيد عمل التكوين بشكل صحيح.
تدعم أداة مترجم الإخراج (للعملاءالمسجلين فقط) بعض أوامر show. استخدم أداة مترجم الإخراج (OIT) لعرض تحليل مُخرَج الأمر show .
-
show crypto isakmp sa— يعرض حالة اقتران أمان ISAKMP (SA).
-
show crypto engine connections active—يعرض إجمالي التشفيرات/فك التشفير لكل SA.
-
show crypto ipsSA— يعرض الإحصائيات على الأنفاق النشطة.
-
show ip route—يعرض جدول التوجيه.
-
show ip ospf neighbor— يعرض معلومات منفذ OSPF المجاور على أساس كل واجهة.
-
show ip nhrp—يعرض ذاكرة التخزين المؤقت لبروتوكول تحليل الخطوة التالية (NHRP) ل IP، والتي تقتصر إختياريا على إدخالات ذاكرة التخزين المؤقت الديناميكية أو الثابتة لواجهة معينة.
استكشاف الأخطاء وإصلاحها
يوفر هذا القسم معلومات يمكنك استخدامها لاستكشاف أخطاء التكوين وإصلاحها.
أوامر استكشاف الأخطاء وإصلاحها
ملاحظة: ارجع إلى معلومات مهمة حول أوامر التصحيح قبل إصدار أوامر debug.
-
debug crypto ipSec—يعرض أحداث IPsec.
-
debug crypto isakmp—يعرض الرسائل المتعلقة بأحداث IKE.
-
debug crypto engine—يعرض معلومات من محرك التشفير.
يمكن العثور على معلومات إضافية حول أستكشاف أخطاء IPsec وإصلاحها في أستكشاف أخطاء أمان IP وإصلاحها - فهم أوامر تصحيح الأخطاء واستخدامها.
معلومات ذات صلة
محفوظات المراجعة
| المراجعة | تاريخ النشر | التعليقات |
|---|---|---|
1.0 |
28-May-2003 |
الإصدار الأولي |
 التعليقات
التعليقات