Installation und Upgrade von Firepower Threat Defense auf ASA 55xx-X Appliances
Download-Optionen
-
ePub (789.3 KB)
In verschiedenen Apps auf iPhone, iPad, Android, Sony Reader oder Windows Phone anzeigen
Inklusive Sprache
In dem Dokumentationssatz für dieses Produkt wird die Verwendung inklusiver Sprache angestrebt. Für die Zwecke dieses Dokumentationssatzes wird Sprache als „inklusiv“ verstanden, wenn sie keine Diskriminierung aufgrund von Alter, körperlicher und/oder geistiger Behinderung, Geschlechtszugehörigkeit und -identität, ethnischer Identität, sexueller Orientierung, sozioökonomischem Status und Intersektionalität impliziert. Dennoch können in der Dokumentation stilistische Abweichungen von diesem Bemühen auftreten, wenn Text verwendet wird, der in Benutzeroberflächen der Produktsoftware fest codiert ist, auf RFP-Dokumentation basiert oder von einem genannten Drittanbieterprodukt verwendet wird. Hier erfahren Sie mehr darüber, wie Cisco inklusive Sprache verwendet.
Informationen zu dieser Übersetzung
Cisco hat dieses Dokument maschinell übersetzen und von einem menschlichen Übersetzer editieren und korrigieren lassen, um unseren Benutzern auf der ganzen Welt Support-Inhalte in ihrer eigenen Sprache zu bieten. Bitte beachten Sie, dass selbst die beste maschinelle Übersetzung nicht so genau ist wie eine von einem professionellen Übersetzer angefertigte. Cisco Systems, Inc. übernimmt keine Haftung für die Richtigkeit dieser Übersetzungen und empfiehlt, immer das englische Originaldokument (siehe bereitgestellter Link) heranzuziehen.
Inhalt
Einführung
Dieses Dokument beschreibt die Installation, das Upgrade und die Registrierung von Firepower Threat Defense (FTD) auf ASA55xx-X-Appliances.
Voraussetzungen
Anforderungen
Für dieses Dokument bestehen keine speziellen Anforderungen.
Verwendete Komponenten
Die Informationen in diesem Dokument basieren auf den folgenden Software- und Hardwareversionen:
- ASA 5508-X
- ASA 5512-X
- FireSIGHT Management Center (FMC) mit 6.0.1 (Build 1213)
Die Informationen in diesem Dokument wurden von den Geräten in einer bestimmten Laborumgebung erstellt. Alle in diesem Dokument verwendeten Geräte haben mit einer leeren (Standard-)Konfiguration begonnen. Wenn Ihr Netzwerk in Betrieb ist, stellen Sie sicher, dass Sie die potenziellen Auswirkungen eines Befehls verstehen.
Hintergrundinformationen
FTD ist ein einheitliches Software-Image, das auf folgenden Plattformen installiert werden kann:
- ASA5506-X, ASA5506W-X, ASA5506H-X, ASA5508-X, ASA5516-X
- ASA5512-X, ASA5515-X, ASA5525-X, ASA5545-X, ASA555-X
- FPR4100, FPR9300
- VMware (ESXi)
- Amazon Web Services (AWS)
- KVM
- ISR Router-Modul
Dieses Dokument soll zeigen,
- Installation von FTD Version 6.0.0 auf den Plattformen ASA5508-X und ASA5512-X
- Das Upgrade-Verfahren für FTD von Version 6.0.0 auf 6.0.1
- Registrierung von FirePOWER Management Center (FMC) und grundlegende Lizenzierung
Konfigurieren
Netzwerkdiagramm

FTD-Software-Download
Navigieren Sie zu Next-Generation Firewalls (NGFW) > ASA mit FirePOWER Services > ASA 5508-X mit FirePOWER Services, und wählen Sie Firepower Threat Defense Software:

Ebenso für die ASA5512-X-Software.
Aufgabe 1: Überprüfen der Voraussetzungen
Überprüfen Sie die Voraussetzungen vor der FTD-Installation.
Lösung:
Für die FTD-Installation verwenden Sie zwei Images:
- Betriebssystem-Image (auch als Boot-Image bekannt) - Für Firepower Threat Defense auf ASA5506-X, ASA5506H-X, ASA5506W-X, ASA5508-X, ASA5516-X ist eine *.lfbff-Datei. Bei Firepower Threat Defense auf Saleen (ASA5512-X, ASA5515-X, ASA5525-X, ASA5545-X, ASA5555-X) handelt es sich um eine *.cdisk-Datei.
- Systemabbild - Dies ist eine .pkg-Datei.
Bevor Sie mit der FTD-Installation fortfahren, überprüfen Sie Folgendes:
- Der ASA-Flash-Speicher muss mindestens 3,1 GB freien Speicherplatz (3 GB + Größe des Boot-Image) aufweisen.
- Das Boot-Image wird auf einen TFTP-Server hochgeladen.
- Das System-Image wird auf einen HTTP- oder FTP-Server hochgeladen.
- Auf ASA5506/08/16 ist der ROMMON mindestens 1.1.8-Version
Überprüfen Sie den freien Speicherplatz:
FTD5508X# show flash | i free 7859437568 bytes total (4273819648 bytes free)
Überprüfen Sie diese Bilder:
| Dateiname |
Beschreibung |
| ftd-boot-9.6.1.0.lfbff |
v6.0.1 FirePOWER Threat Defense-Boot-Image für 5506/5508/5516. Dies ist das Boot-Image für die saubere Installation unter 5506/5508/5516. |
| ftd-boot-9.6.1.0.cdisk |
v6.0.1 Firepower Threat Defense-Boot-Image für ASA 5512/5515/5525/5545/5555. Dies ist das Boot-Image für die saubere Installation unter 5512/5515/5525/5545/5555 |
| ftd-6,0,0-1005,pkg |
v6.0.0 Firepower Threat Defense für alle unterstützten ASAs: 5506/5508/5512/5515/5516/5525/5545/5555. Dies ist das Systemabbild für die saubere Installation. |
Aufgabe 2: Aktualisieren Sie ASA5508-X ROMMON.
Wie in den erforderlichen Komponenten erwähnt, müssen ASA5506-X-, ASA5508-X- und ASA5516-X-Geräte sich auf ROMMON v1.1.8 befinden. Falls nicht, installieren Sie asa5500-firmware-1108.SPA (auf der Cisco ASA-Downloadseite verfügbar).
Aufgabenanforderung:
Aktualisieren Sie ASA5508 ROMMON von 1.1.1 auf 1.1.8.
Lösung:
Das Verfahren wird im ASA ROMMON Upgrade Guide beschrieben.
Schritt 1: Überprüfen Sie die vorhandene ROMMON-Version:
FTD5508X# show module Mod Card Type Model Serial No. ---- -------------------------------------------- ------------------ ----------- 1 ASA 5508-X with FirePOWER services, 8GE, AC, ASA5508 JAD192100SZ sfr FirePOWER Services Software Module ASA5508 JAD192100SZ Mod MAC Address Range Hw Version Fw Version Sw Version ---- --------------------------------- ------------ ------------ --------------- 1 188b.9d1e.ca7c to 188b.9d1e.ca84 1.0 1.1.1 9.5(2) sfr 188b.9d1e.ca7b to 188b.9d1e.ca7b N/A N/A 5.4.1-211
Schritt 2.Laden Sie die ROMMON-Firmware in den Flash-Speicher der ASA herunter:
FTD5508X# copy ftp://10.48.40.70/ANG/mzafeiro/asa5500-firmware-1108.SPA disk0:asa5500-firmware-1108.SPA
Address or name of remote host [10.48.40.70]?
Source filename [ANG/mzafeiro/asa5500-firmware-1108.SPA]?
Destination filename [asa5500-firmware-1108.SPA]?
Accessing ftp://10.48.40.70/ANG/mzafeiro/asa5500-firmware-1108.SPA...!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!! Done!
Computed Hash SHA2: d824bdeecee1308fc64427367fa559e9
eefe8f182491652ee4c05e6e751f7a4f
5cdea28540cf60acde3ab9b65ff55a9f
4e0cfb84b9e2317a856580576612f4af
Embedded Hash SHA2: d824bdeecee1308fc64427367fa559e9
eefe8f182491652ee4c05e6e751f7a4f
5cdea28540cf60acde3ab9b65ff55a9f
4e0cfb84b9e2317a856580576612f4af
Digital signature successfully validated
Writing file disk0:/asa5500-firmware-1108.SPA...
!!!!!!!!!
9241408 bytes copied in 18.890 secs (513411 bytes/sec)
Schritt 3: Aktualisieren Sie das ASA ROMMON-Image:
FTD5508X# upgrade rommon disk0:asa5500-firmware-1108.SPA
Verifying file integrity of disk0:/asa5500-firmware-1108.SPA
Computed Hash SHA2: d824bdeecee1308fc64427367fa559e9
eefe8f182491652ee4c05e6e751f7a4f
5cdea28540cf60acde3ab9b65ff55a9f
4e0cfb84b9e2317a856580576612f4af
Embedded Hash SHA2: d824bdeecee1308fc64427367fa559e9
eefe8f182491652ee4c05e6e751f7a4f
5cdea28540cf60acde3ab9b65ff55a9f
4e0cfb84b9e2317a856580576612f4af
Digital signature successfully validated
File Name : disk0:/asa5500-firmware-1108.SPA
Image type : Release
Signer Information
Common Name : abraxas
Organization Unit : NCS_Kenton_ASA
Organization Name : CiscoSystems
Certificate Serial Number : 55831CF6
Hash Algorithm : SHA2 512
Signature Algorithm : 2048-bit RSA
Key Version : A
Verification successful.
System config has been modified. Save? [Y]es/[N]o: Y
Cryptochecksum: cb47de8a cad3b773 7fc07212 3e76ef4f
2804 bytes copied in 0.260 secs
Proceed with reload? [confirm]
***
*** --- START GRACEFUL SHUTDOWN ---
***
*** Message to all terminals:
***
*** Performing upgrade on rom-monitor.
Shutting down License Controller
Shutting down File system
***
*** --- SHUTDOWN NOW ---
***
*** Message to all terminals:
***
*** Performing upgrade on rom-monitor.
Process shutdown finished
Rebooting.....
INIT: Sending processes the TERM signal
Deconfiguring network interfaces... done.
Sending all processes the TERM signal...
Sending all processes the KILL signal...
Deactivating swap...
Unmounting local filesystems...
Rebooting...
Rom image verified correctly
Cisco Systems ROMMON, Version 1.1.01, RELEASE SOFTWARE
Copyright (c) 1994-2014 by Cisco Systems, Inc.
Compiled Mon 10/20/2014 15:59:12.05 by builder
Current image running: Boot ROM0
Last reset cause: PowerCycleRequest
DIMM Slot 0 : Present
DIMM Slot 1 : Present
INFO: Rommon upgrade state: ROMMON_UPG_START (1)
INFO: Reset code: 0x00002000
Firmware upgrade step 1... Looking for file 'disk0:asa5500-firmware-1108.SPA' Located 'asa5500-firmware-1108.SPA' @ cluster 856765.
###########################################################################################
Image base 0x77014018, size 9241408
LFBFF signature verified.
Objtype: lfbff_object_rommon (0x800000 bytes @ 0x77014238)
Objtype: lfbff_object_fpga (0xd0100 bytes @ 0x77814258)
INFO: FPGA version in upgrade image: 0x0202
INFO: FPGA version currently active: 0x0202
INFO: The FPGA image is up-to-date.
INFO: Rommon version currently active: 1.1.01. INFO: Rommon version in upgrade image: 1.1.08.
Active ROMMON: Preferred 0, selected 0, booted 0
Switching SPI access to standby rommon 1.
Please DO NOT reboot the unit, updating ROMMON................... INFO: Duplicating machine state...... Reloading now as step 1 of the rommon upgrade process... Toggling power on system board... Rom image verified correctly
Cisco Systems ROMMON, Version 1.1.01, RELEASE SOFTWARE
Copyright (c) 1994-2014 by Cisco Systems, Inc.
Compiled Mon 10/20/2014 15:59:12.05 by builder
Current image running: Boot ROM0
Last reset cause: RP-Reset
DIMM Slot 0 : Present
DIMM Slot 1 : Present
INFO: Rommon upgrade state: ROMMON_UPG_START (1)
INFO: Reset code: 0x00000008
Active ROMMON: Preferred 0, selected 0, booted 0
Firmware upgrade step 2...
Detected current rommon upgrade is available, continue rommon upgrade process
Rommon upgrade reset 0 in progress
Reloading now as step 2 of the rommon upgrade process...
Rom image verified correctly
Cisco Systems ROMMON, Version 1.1.8, RELEASE SOFTWARE
Copyright (c) 1994-2015 by Cisco Systems, Inc.
Compiled Thu 06/18/2015 12:15:56.43 by builders
Current image running: *Upgrade in progress* Boot ROM1
Last reset cause: BootRomUpgrade
DIMM Slot 0 : Present
DIMM Slot 1 : Present
INFO: Rommon upgrade state: ROMMON_UPG_START (1)
INFO: Reset code: 0x00000010
PROM B: stopping boot timer
Active ROMMON: Preferred 0, selected 0, booted 1
INFO: Rommon upgrade state: ROMMON_UPG_TEST
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
!! Please manually or auto boot ASAOS now to complete firmware upgrade !!
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
Platform ASA5508 with 8192 Mbytes of main memory
MAC Address: 18:8b:9d:1e:ca:7c
Use BREAK or ESC to interrupt boot.
Use SPACE to begin boot immediately.
Located '.boot_string' @ cluster 859024.
#
Attempt autoboot: "boot disk0:/asa952-lfbff-k8.SPA"
Located 'asa952-lfbff-k8.SPA' @ cluster 818273.
####################################################################################################################################################################################################################################################################################################################################################################################################################################################################################################################################################################################################################################################################################################################################################################################################################################
LFBFF signature verified.
INIT: version 2.88 booting
Starting udev
Configuring network interfaces... done.
Populating dev cache
dosfsck 2.11, 12 Mar 2005, FAT32, LFN
There are differences between boot sector and its backup.
Differences: (offset:original/backup)
65:01/00
Not automatically fixing this.
Starting check/repair pass.
/csco_config
"." is missing. Can't fix this yet.
/csco_config
".." is missing. Can't fix this yet.
Starting verification pass.
/csco_config
"." is missing. Can't fix this yet.
/csco_config
".." is missing. Can't fix this yet.
/dev/sdb1: 182 files, 849380/1918808 clusters
dosfsck(/dev/sdb1) returned 0
IO Memory Nodes: 1
IO Memory Per Node: 499122176 bytes
Global Reserve Memory Per Node: 314572800 bytes Nodes=1
Processor memory 3807834603
LCMB: got 499122176 bytes on numa-id=0, phys=0x1b8000000, virt=0x2aaaaae00000
LCMB: HEAP-CACHE POOL got 314572800 bytes on numa-id=0, virt=0x2aaac8a00000
Compiled on Sat 28-Nov-15 00:16 PST by builders
Total NICs found: 13
i354 rev03 Gigabit Ethernet @ irq255 dev 20 index 08 MAC: 188b.9d1e.ca7c
ivshmem rev03 Backplane Data Interface @ index 09 MAC: 0000.0001.0002
en_vtun rev00 Backplane Control Interface @ index 10 MAC: 0000.0001.0001
en_vtun rev00 Backplane Int-Mgmt Interface @ index 11 MAC: 0000.0001.0003
en_vtun rev00 Backplane Ext-Mgmt Interface @ index 12 MAC: 0000.0000.0000
Rom-monitor was successfully upgraded.
...
Überprüfen:
Sie können den Befehl show module verwenden, um die ROMMON-Softwareversion zu überprüfen:
FTD5508X> enable Password: FTD5508X# show module Mod Card Type Model Serial No. ---- -------------------------------------------- ------------------ ----------- 1 ASA 5508-X with FirePOWER services, 8GE, AC, ASA5508 JAD192100SZ sfr FirePOWER Services Software Module ASA5508 JAD192100SZ Mod MAC Address Range Hw Version Fw Version Sw Version ---- --------------------------------- ------------ ------------ --------------- 1 188b.9d1e.ca7c to 188b.9d1e.ca84 1.0 1.1.8 9.5(2) sfr 188b.9d1e.ca7b to 188b.9d1e.ca7b N/A N/A 5.4.1-211
Aufgabe 3: Installieren Sie das FTD-Boot-Image auf ASA55xx-X.
Aufgabenanforderung:
Installieren Sie das FTD-Boot-Image ftd-boot-9.6.1.0.lfbff auf ASA5508-X.
Lösung:
Dafür gibt es mehrere Methoden. Dies ist die erste:
Methode 1. Von RUMON
Schritt 1: Laden Sie die ASA neu, und wechseln Sie in den ROMMON-Modus:
FTD5508X# reload Proceed with reload? [confirm] FTD5508X# *** *** --- START GRACEFUL SHUTDOWN --- Shutting down isakmp Shutting down webvpn Shutting down sw-module Shutting down License Controller Shutting down File system *** *** --- SHUTDOWN NOW --- Process shutdown finished Rebooting..... INIT: Sending processes the TERM signal Deconfiguring network interfaces... done. Sending all processes the TERM signal... Sending all processes the KILL signal... Deactivating swap... Unmounting local filesystems... Rebooting... ÿ Rom image verified correctly Cisco Systems ROMMON, Version 1.1.8, RELEASE SOFTWARE Copyright (c) 1994-2015 by Cisco Systems, Inc. Compiled Thu 06/18/2015 12:15:56.43 by builders Current image running: Boot ROM1 Last reset cause: PowerCycleRequest DIMM Slot 0 : Present DIMM Slot 1 : Present Platform ASA5508 with 8192 Mbytes of main memory MAC Address: 18:8b:9d:1e:ca:7c Use BREAK or ESC to interrupt boot. Use SPACE to begin boot immediately. Boot interrupted. rommon 1 >
Schritt 2: Konfigurieren Sie die grundlegenden Netzwerkeinstellungen:
rommon 1 > ADDRESS=10.62.148.29 rommon 2 > SERVER=10.229.22.42 rommon 3 > GATEWAY=10.62.148.1 rommon 4 > IMAGE=ftd-boot-9.6.1.0.lfbff rommon 5 > netmask 255.255.255.128 rommon 6 > ping 10.229.22.42 Sending 10, 32-byte ICMP Echoes to 10.229.22.42 timeout is 4 seconds ?!!!!!!!!! Success rate is 90 percent (9/10) rommon 7 > sync rommon 8 > tftpdnld ADDRESS: 10.62.148.29
NETMASK: 255.255.255.128
GATEWAY: 10.62.148.1
SERVER: 10.229.22.42
IMAGE: ftd-boot-9.6.1.0.lfbff
MACADDR: 18:8b:9d:1e:ca:7c
VERBOSITY: Progress
RETRY: 40
PKTTIMEOUT: 7200
BLKSIZE: 1460
CHECKSUM: Yes
PORT: GbE/1
PHYMODE: Auto Detect
Receiving ftd-boot-9.6.1.0.lfbff from 10.229.22.42!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!! .. output omitted ..
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
File reception completed.
Boot buffer bigbuf=348bd018
Boot image size = 100308208 (0x5fa94f0) bytes
[image size] 100308208
[MD5 signaure] 781dde41844d750f8c0db1cd1e1e164f
LFBFF signature verified.
INIT: version 2.88 booting
Starting udev
Configuring network interfaces... done.
Populating dev cache
Detected PID ASA5508.
Found device serial number JAD192100SZ.
Found USB flash drive /dev/sdb
Found hard drive(s): /dev/sda
fsck from util-linux 2.23.2
dosfsck 2.11, 12 Mar 2005, FAT32, LFN
/dev/sdb1: 47 files, 24618/1919063 clusters ============================================== Launching boot CLI ... Configuring network interface using static IP Bringing up network interface. Depending on your network, this might take a couple of minutes when using DHCP... ifup: interface lo already configured Using IPv4 address: 10.62.148.62
Using IPv6 address: fe80::1a8b:9dff:fe1e:ca7b
Using DNS server: 10.62.145.72
Using default gateway: 10.62.148.100
INIT: Starting system message bus: dbus.
Starting OpenBSD Secure Shell server: sshd
generating ssh RSA key...
generating ssh ECDSA key...
generating ssh DSA key...
done.
Starting Advanced Configuration and Power Interface daemon: acpid.
acpid: starting up
acpid: 1 rule loaded
acpid: waiting for events: event logging is off
Starting ntpd: done
Starting syslog-ng:.
Starting crond: OK
Cisco FTD Boot 6.0.0 (9.6.1.)
Type ? for list of commands
firepower-boot>
Bei ASA5512/15/25/45/55 ist die Vorgehensweise identisch, wobei der Boot-Image-Name nur vom Namen abweicht:
rommon #0> ADDRESS=10.62.148.10 rommon #1> SERVER=10.229.22.42 rommon #2> GATEWAY=10.62.148.1 rommon #3> IMAGE=ftd-boot-9.6.1.0.cdisk
Methode 2. Aus ASA-Modus
Schritt 1: Kopieren Sie das FTD-Boot-Image im ASA Exec-Modus (ohne ROMMON) in den ASA-Flash-Speicher:
ciscoasa# copy ftp://10.48.40.70/ANG/mzafeiro/ftd-boot-9.6.1.0.lfbff flash
Schritt 2: Löschen Sie alle ASA-Images von der Festplatte:
ciscoasa# delete flash:asa*
Der Flash-Inhalt nach dem Löschen von ASA-Images:
ciscoasa# show flash --#-- --length-- -----date/time------ path 131 33 May 20 2016 09:27:28 .boot_string 11 4096 Mar 03 2016 11:48:34 log 154 16767 May 20 2016 09:23:48 log/asa-appagent.log 155 465 Mar 03 2016 11:54:58 log/asa-ssp_ntp.log 21 4096 Jun 10 2015 06:45:42 crypto_archive 22 4096 Jun 10 2015 06:46:00 coredumpinfo 23 59 Jun 10 2015 06:46:00 coredumpinfo/coredump.cfg 134 25627616 Dec 01 2015 04:01:58 asdm-752.bin 135 52563 Feb 09 2016 02:49:58 system.cfg 136 25028660 Feb 09 2016 02:50:28 asdm-751-112.bin 137 38409858 Feb 09 2016 02:51:14 anyconnect-win-3.1.10010-k9.pkg 138 25629676 Feb 09 2016 04:38:10 asdm-752-153.bin 151 100308208 May 20 2016 09:39:57 ftd-boot-9.6.1.0.lfbff <--
Schritt 3: Laden Sie die ASA neu. Es wird vom FTD-Boot-Image gebootet:
Located 'ftd-boot-9.6.1.0.lfbff' @ cluster 45093.
#####################################################################
..
LFBFF signature verified.
INIT: version 2.88 booting
..
Cisco FTD Boot 6.0.0 (9.6.1.)
Type ? for list of commands
firepower-boot>
Aufgabe 4: Installieren Sie das FTD-Systemabbild auf ASA55xx-X.
Installieren Sie FTD-Systemabbild auf ASA5508-X.
Lösung
firepower-boot> setup
Welcome to Cisco FTD Setup
[hit Ctrl-C to abort]
Default values are inside []
Enter a hostname [firepower]: FTD5508
Do you want to configure IPv4 address on management interface?(y/n) [Y]:
Do you want to enable DHCP for IPv4 address assignment on management interface?(y/n) [Y]: N
Enter an IPv4 address: 10.62.148.29
Enter the netmask: 255.255.255.128
Enter the gateway: 10.62.148.1
Do you want to enable DHCP for IPv4 address assignment on management interface?(y/n) [N]:
Enter an IPv4 address [10.62.148.29]:
Enter the netmask [255.255.255.128]:
Enter the gateway [10.62.148.1]:
Do you want to configure static IPv6 address on management interface?(y/n) [N]:
Stateless autoconfiguration will be enabled for IPv6 addresses.
Enter the primary DNS server IP address: 173.38.200.100
Do you want to configure Secondary DNS Server? (y/n) [n]: y
Enter the secondary DNS server IP address: 144.254.71.184
Do you want to configure Local Domain Name? (y/n) [n]:
Do you want to configure Search domains? (y/n) [n]:
Do you want to enable the NTP service? [Y]:
Enter the NTP servers separated by commas [203.0.113.126]: 171.68.38.65
Please review the final configuration:
Hostname: FTD5508
Management Interface Configuration
IPv4 Configuration: static
IP Address: 10.62.148.29
Netmask: 255.255.255.128
Gateway: 10.62.148.1
IPv6 Configuration: Stateless autoconfiguration
DNS Configuration:
DNS Server:
173.38.200.100
144.254.71.184
NTP configuration:
171.68.38.65
CAUTION:
You have selected IPv6 stateless autoconfiguration, which assigns a global address
based on network prefix and a device identifier. Although this address is unlikely
to change, if it does change, the system will stop functioning correctly.
We suggest you use static addressing instead.
Apply the changes?(y,n) [Y]:
Configuration saved successfully!
Applying...
Done.
Press ENTER to continue...
firepower-boot>
Überprüfen Sie die Verbindung mit dem FTP-Server:
firepower-boot> ping 10.229.22.42
PING 10.229.22.42 (10.229.22.42) 56(84) bytes of data.
64 bytes from 10.229.22.42: icmp_seq=1 ttl=124 time=1.30 ms
64 bytes from 10.229.22.42: icmp_seq=2 ttl=124 time=1.32 ms
64 bytes from 10.229.22.42: icmp_seq=3 ttl=124 time=1.45 ms
^C
--- 10.229.22.42 ping statistics ---
3 packets transmitted, 3 received, 0% packet loss, time 2002ms
rtt min/avg/max/mdev = 1.302/1.360/1.458/0.075 ms
Installieren Sie das Systempaket:
firepower-boot> system install ftp://10.229.22.42/ftd-6.0.0-1005.pkg
######################## WARNING ############################
# The content of disk0: will be erased during installation! #
#############################################################
Do you want to continue? [y/N] y
Erasing disk0 ...
Verifying
Enter credentials to authenticate with ftp server
Username: ftp
Password:
Verifying Downloading Extracting <-- Here give it some time (~10 min)
Package Detail
Description: Cisco ASA-NGFW 6.0.0-1005 System Install
Requires reboot: Yes
Do you want to continue with upgrade? [y]: <-- Press Enter
Warning: Please do not interrupt the process or turn off the system.
Doing so might leave system in unusable state.
Starting upgrade process ...
Populating new system image <-- Here give it some time (~5 min)
Reboot is required to complete the upgrade. Press 'Enter' to reboot the system. <-- Press Enter
Broadcast message from root@firepowStopping OpenBSD Secure Shell server: sshdstopped /usr/sbin/sshd (pid 1963)
.
Stopping Advanced Configuration and Power Interface daemon: stopped /usr/sbin/acpid (pid 1967)
acpid: exiting
acpid.
Stopping system message bus: dbus.
Stopping ntpd: stopped process in pidfile '/var/run/ntp.pid' (pid 2055)
done
Stopping crond: OK
Deconfiguring network interfaces... done.
Sending all processes the TERM signal...
Sending all processes the KILL signal...
Deactivating swap...
Unmounting local filesystems...
Rebooting... ÿ
Rom image verified correctly
Cisco Systems ROMMON, Version 1.1.8, RELEASE SOFTWARE
Copyright (c) 1994-2015 by Cisco Systems, Inc.
Compiled Thu 06/18/2015 12:15:56.43 by builders
Current image running: Boot ROM1
Last reset cause: PowerCycleRequest
DIMM Slot 0 : Present
DIMM Slot 1 : Present
Platform ASA5508 with 8192 Mbytes of main memory
MAC Address: 18:8b:9d:1e:ca:7c
Use BREAK or ESC to interrupt boot.
Use SPACE to begin boot immediately.
Located '.boot_string' @ cluster 186016.
#
Attempt autoboot: "boot disk0:os.img"
Located 'os.img' @ cluster 160001.
########################################
LFBFF signature verified.
INIT: version 2.88 booting
Starting udev
Configuring network interfaces... done.
Populating dev cache
Detected PID ASA5508.
Found device serial number JAD192100SZ.
Found USB flash drive /dev/sdb
Found hard drive(s): /dev/sda
fsck from util-linux 2.23.2
dosfsck 2.11, 12 Mar 2005, FAT32, LFN
/dev/sdb1: 7 files, 26064/1919063 clusters
==============================================
Use ESC to interrupt boot and launch boot CLI.
Use SPACE to launch Cisco FTD immediately.
Cisco FTD launch in 20 seconds ...
Running on kenton
Mounting disk partitions ...
Initializing Threat Defense ... [ OK ]
Starting system log daemon... [ OK ]
Flushing all current IPv4 rules and user defined chains: ...success
Clearing all current IPv4 rules and user defined chains: ...success
Applying iptables firewall rules:
Flushing chain `PREROUTING'
Flushing chain `INPUT'
Flushing chain `FORWARD'
Flushing chain `OUTPUT'
Flushing chain `POSTROUTING'
Flushing chain `INPUT'
Flushing chain `FORWARD'
Flushing chain `OUTPUT'
Applying rules successed
Flushing all current IPv6 rules and user defined chains: ...success
Clearing all current IPv6 rules and user defined chains: ...success
Applying ip6tables firewall rules:
Flushing chain `PREROUTING'
Flushing chain `INPUT'
Flushing chain `FORWARD'
Flushing chain `OUTPUT'
Flushing chain `POSTROUTING'
Flushing chain `INPUT'
Flushing chain `FORWARD'
Flushing chain `OUTPUT'
Applying rules successed
Starting nscd...
mkdir: created directory '/var/run/nscd' [ OK ]
Starting , please wait...grep: /ngfw/etc/motd: No such file or directory
...complete.
Firstboot detected, executing scripts
Executing S01reset_failopen_if [ OK ]
Executing S04fix-httpd.sh [ OK ]
Executing S05set-mgmnt-port [ OK ]
Executing S06addusers [ OK ]
Executing S07uuid-init [ OK ]
Executing S09configure_mysql [ OK ]
************ Attention *********
Initializing the configuration database. Depending on available
system resources (CPU, memory, and disk), this may take 30 minutes
or more to complete.
************ Attention *********
Executing S10database [ OK ]
Executing S12install_infodb [ OK ]
Executing S15set-locale.sh [ OK ]
Executing S16update-sensor.pl [ OK ]
Executing S19cert-tun-init [ OK ]
Executing S20cert-init [ OK ]
Executing S21disable_estreamer [ OK ]
Executing S25create_default_des.pl [ OK ]
Executing S30init_lights_out_mgmt.pl [ OK ]
Executing S40install_default_filters.pl [ OK ]
Executing S42install_default_dashboards.pl [ OK ]
Executing S43install_default_report_templates.pl [ OK ]
Executing S44install_default_app_filters.pl [ OK ]
Executing S45install_default_realms.pl [ OK ]
Executing S47install_default_sandbox_EO.pl [ OK ]
Executing S50install-remediation-modules [ OK ]
Executing S51install_health_policy.pl [ OK ]
Executing S52install_system_policy.pl [ OK ]
Executing S53change_reconciliation_baseline.pl [ OK ]
Executing S70update_sensor_objects.sh [ OK ]
Executing S85patch_history-init [ OK ]
Executing S90banner-init [ OK ]
Executing S95copy-crontab [ OK ]
Executing S96grow_var.sh [ OK ]
********** Attention **********
Initializing the system's localization settings. Depending on available
system resources (CPU, memory, and disk), this may take 10 minutes
or more to complete.
********** Attention **********
Executing S96localize-templates [ OK ]
Executing S96ovf-data.pl [ OK ]
Executing S97compress-client-resources [ OK ]
Executing S97create_platinum_forms.pl [ OK ]
Executing S97install_cloud_support.pl [ OK ]
Executing S97install_geolocation.pl [ OK ]
Executing S97install_ssl_inspection.pl [ OK ]
Executing S97update_modprobe.pl [ OK ]
Executing S98check-db-integrity.sh [ OK ]
Executing S98htaccess-init [ OK ]
Executing S99correct_ipmi.pl [ OK ]
Executing S99start-system [ OK ]
Executing S99z_db_restore [ OK ]
Firstboot scripts finished.
Configuring NTP... [ OK ]
Model reconfigure detected, executing scripts
Pinging mysql
Found mysql is running
Executing 45update-sensor.pl [ OK ]
Executing 55recalculate_arc.pl [ OK ]
Starting xinetd:
Mon Mar 14 18:28:11 UTC 2016
Starting MySQL...
Pinging mysql
Pinging mysql, try 1
Found mysql is running
Running initializeObjects...
Stopping MySQL...
Killing mysqld with pid 10993
Wait for mysqld to exit\c
done
Mon Mar 14 18:28:21 UTC 2016
Starting sfifd... [ OK ]
Starting Cisco ASA5508-X Threat Defense, please wait...No PM running!
...started.
INIT: Starting system message bus: dbus.
Starting OpenBSD Secure Shell server: sshd
generating ssh RSA key...
generating ssh ECDSA key...
generating ssh DSA key...
done.
Starting Advanced Configuration and Power Interface daemon: acpid.
Starting crond: OK
Mar 14 18:28:26 ciscoasa SF-IMS[11490]: [11490] init script:system [INFO] pmmon Setting affinity to 5-7...
pid 11486's current affinity list: 0-7
pid 11486's new affinity list: 5-7
Mar 14 18:28:26 ciscoasa SF-IMS[11492]: [11492] init script:system [INFO] pmmon The Process Manager is not running...
Mar 14 18:28:26 ciscoasa SF-IMS[11493]: [11493] init script:system [INFO] pmmon Starting the Process Manager...
Mar 14 18:28:26 ciscoasa SF-IMS[11494]: [11494] pm:pm [INFO] Using model number 75K
Cisco ASA5508-X Threat Defense v6.0.0 (build 1005)
ciscoasa login:
Compiled on Sat 07-Nov-15 16:13 PST by builders
Total NICs found: 13
i354 rev03 Gigabit Ethernet @ irq255 dev 20 index 08 MAC: 188b.9d1e.ca7c
ivshmem rev03 Backplane Data Interface @ index 09 MAC: 0000.0001.0002
en_vtun rev00 Backplane Control Interface @ index 10 MAC: 0000.0001.0001
en_vtun rev00 Backplane Int-Mgmt Interface @ index 11 MAC: 0000.0001.0003
en_vtun rev00 Backplane Ext-Mgmt Interface @ index 12 MAC: 0000.0000.0000
INFO: Unable to read firewall mode from flash
Writing default firewall mode (single) to flash
INFO: Unable to read cluster interface-mode from flash
Writing default mode "None" to flash
Verify the activation-key, it might take a while...
Failed to retrieve permanent activation key.
Running Permanent Activation Key: 0x00000000 0x00000000 0x00000000 0x00000000 0x00000000
The Running Activation Key is not valid, using default settings:
Licensed features for this platform:
Maximum Physical Interfaces : Unlimited perpetual
Maximum VLANs : 50 perpetual
Inside Hosts : Unlimited perpetual
Failover : Active/Active perpetual
Encryption-DES : Enabled perpetual
Encryption-3DES-AES : Disabled perpetual
Security Contexts : 2 perpetual
GTP/GPRS : Disabled perpetual
AnyConnect Premium Peers : 4 perpetual
AnyConnect Essentials : Disabled perpetual
Other VPN Peers : 100 perpetual
Total VPN Peers : 100 perpetual
Shared License : Disabled perpetual
AnyConnect for Mobile : Disabled perpetual
AnyConnect for Cisco VPN Phone : Disabled perpetual
Advanced Endpoint Assessment : Disabled perpetual
Total UC Proxy Sessions : 320 perpetual
Botnet Traffic Filter : Disabled perpetual
Cluster : Disabled perpetual
VPN Load Balancing : Enabled perpetual
Encryption hardware device : Cisco ASA Crypto on-board accelerator (revision 0x1)
Cisco Adaptive Security Appliance Software Version 99.1(3)194
****************************** Warning *******************************
This product contains cryptographic features and is
subject to United States and local country laws
governing, import, export, transfer, and use.
Delivery of Cisco cryptographic products does not
imply third-party authority to import, export,
distribute, or use encryption. Importers, exporters,
distributors and users are responsible for compliance
with U.S. and local country laws. By using this
product you agree to comply with applicable laws and
regulations. If you are unable to comply with U.S.
and local laws, return the enclosed items immediately.
A summary of U.S. laws governing Cisco cryptographic
products may be found at:
http://www.cisco.com/wwl/export/crypto/tool/stqrg.html
If you require further assistance please contact us by
sending email to export@cisco.com.
******************************* Warning *******************************
... output omitted ...
Reading from flash...
!
Cryptochecksum (changed): 6129864f 6298b553 75f279ea e547792b
INFO: Power-On Self-Test in process.
.......................
INFO: Power-On Self-Test complete.
INFO: Starting HW-DRBG health test...
INFO: HW-DRBG health test passed.
INFO: Starting SW-DRBG health test...
INFO: SW-DRBG health test passed.
Cisco ASA5508-X Threat Defense v6.0.0 (build 1005)
firepower login: admin
Password: <-- Admin123
You must accept the EULA to continue.
Press
to display the EULA:
... EULA is displayed - output is omitted
END USER LICENSE AGREEMENT
Please enter 'YES' or press to AGREE to the EULA:
System initialization in progress. Please stand by.
You must change the password for 'admin' to continue.
Enter new password:
Confirm new password:
You must configure the network to continue.
You must configure at least one of IPv4 or IPv6.
Do you want to configure IPv4? (y/n) [y]: Do you want to configure IPv6? (y/n) [n]:
Configure IPv4 via DHCP or manually? (dhcp/manual) [manual]:
Enter an IPv4 address for the management interface [192.168.45.45]: 10.62.148.29
Enter an IPv4 netmask for the management interface [255.255.255.0]: 255.255.255.128
Enter the IPv4 default gateway for the management interface []: 10.62.148.1
Enter a fully qualified hostname for this system [firepower]: FTD5508
Enter a comma-separated list of DNS servers or 'none' []: 173.38.200.100,144.254.71.184
Enter a comma-separated list of search domains or 'none' []:
If your networking information has changed, you will need to reconnect.
For HTTP Proxy configuration, run 'configure network http-proxy'
Configure firewall mode? (routed/transparent) [routed]:
Configuring firewall mode ...
Update policy deployment information
- add device configuration
You can register the sensor to a Firepower Management Center and use the
Firepower Management Center to manage it. Note that registering the sensor
to a Firepower Management Center disables on-sensor Firepower Services
management capabilities.
When registering the sensor to a Firepower Management Center, a unique
alphanumeric registration key is always required. In most cases, to register
a sensor to a Firepower Management Center, you must provide the hostname or
the IP address along with the registration key.
'configure manager add [hostname | ip address ] [registration key ]'
However, if the sensor and the Firepower Management Center are separated by a
NAT device, you must enter a unique NAT ID, along with the unique registration
key.
'configure manager add DONTRESOLVE [registration key ] [ NAT ID ]'
Later, using the web interface on the Firepower Management Center, you must
use the same registration key and, if necessary, the same NAT ID when you add
this sensor to the Firepower Management Center.
>
Tipp: Sie können die Option noconfirm verwenden, um das Bild zu installieren. In diesem Fall werden Sie während der Installation nicht dazu aufgefordert.
firepower-boot>system install noconfirm ftp://10.229.22.42/ftd-6.0.0-1005.pkg
Bei FTD 6.1.x und höher werden Sie aufgefordert, den Verwaltungsmodus (lokal oder remote) einzustellen.
For HTTP Proxy configuration, run 'configure network http-proxy' Manage the device locally? (yes/no) [yes]: no Configure firewall mode? (routed/transparent) [routed]:
Lokaler Modus = Gilt nur für ASA55xx-X-Geräte. Sie verwalten das FTD über den FirePOWER Device Manager (FDM).
Remote-Modus = Sie verwalten FTD über FMC.
Überprüfung
> show version -------------------[ FTD5508 ]-------------------- Model : Cisco ASA5508-X Threat Defense (75) Version 6.0.0 (Build 1005) UUID : 8c3f4b7e-ea11-11e5-94f1-f3a55afb51a3 Rules update version : 2015-10-01-001-vrt VDB version : 252 ---------------------------------------------------- >
Die Installation des Systemabbilds auf ASA5512/15/25/45/55 ist mit der oben beschriebenen identisch.
Aufgabe 5: Registrierung des FTD beim FMC
FTD auf FMC-Server registrieren Verwenden Sie die folgenden Einstellungen:
| Host | 10.62.148.29 |
| Anzeigename | FTD5508 |
| Registrierungsschlüssel | Cisco |
| Gruppe Keine | |
| Zugriffskontrollrichtlinie | FTD5508 |
| Grundlegende Richtlinie für Zugriffskontrolle | Keine |
| Standardaktion für Zugriffskontrollrichtlinie | Blockieren des gesamten Datenverkehrs |
Lösung
Schritt 1:Geben Sie in FTD den FMC-Server an:
> configure manager add 10.62.148.73 cisco Manager successfully configured. Please make note of reg_key as this will be required while adding Device in FMC. > show managers Host : 10.62.148.73 Registration Key : **** Registration : pending RPC Status : Type : Manager Host : 10.62.148.73 Registration : Pending >
Schritt 2:Bevor Sie die FTD hinzufügen, müssen Sie das FMC beim Smart Licensing Server registrieren. Wenn Sie versuchen, ein FTD-Gerät ohne Smart License hinzuzufügen, erhalten Sie die folgende Fehlermeldung:

Sie können den Evaluierungsmodus auswählen. So können Sie FTD 90 Tage lang ohne Funktionen verwenden, die eine starke Verschlüsselung erfordern (z. B. VPN).

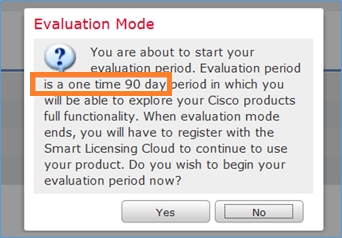

Schritt 3: Erstellen Sie auf FMC zunächst die Zugriffskontrollrichtlinie, die von FTD verwendet wird. Navigieren Sie zu Richtlinien > Zugriffskontrolle, und wählen Sie Neue Richtlinie aus:



Fügen Sie dann das FTD-Gerät hinzu:


Am Ende des FTD-Dokuments wird eine Richtlinie bereitgestellt:

Um zu überprüfen, was im Hintergrund passiert, während das FTD-Gerät hinzugefügt wird, aktivieren Sie Pigtail auf FMC und FTD.
Auf FMC:
admin@fs4k:~$ sudo pigtail ***************************************************************************************************************************** ** Displaying logs: ACTQ HTTP DCSM VMSS MOJO NGFW NGUI VMSB TCAT DEPL MSGS USMS *****************************************************************************************************************************
FTD:
> pigtail ******************************************************************************** ** Displaying logs: HTTP ACTQ DCSM VMSS MOJO NGUI NGFW TCAT VMSB DEPL USMS MSGS ********************************************************************************
Hinweis: Wenn der Status der FTD-Verwaltungsschnittstelle ausgefallen ist, stellen Sie sicher, dass der Wert für die Konvertierung 0x1 lautet.
Aufgabe 6: FTD-Upgrade
Aktualisieren Sie FTD bei dieser Aufgabe von 6.0.0 auf 6.0.1.
|
|
Version |
Dateiname |
| Anfängliches FTD-Image |
Version 6.0.0 (Build 1005) |
ftd-6,0,0-1005,pkg |
| FTD-Zielbild |
Version 6.0.1 (Build 1213) |
Cisco_FTD_Upgrade-6.0.1-1213.sh |
Lösung
Schritt 1: FTD-Image in FMC hochladen:


Schritt 2: Installieren Sie das FTD-Image:


Eine Warnung zum FTD-Neuladen wird angezeigt:

Das Upgrade dauerte in diesem Fall etwa 35 Minuten. Wie unten gezeigt, muss die Richtlinie erneut angewendet werden:

Bereitstellen der Richtlinien:

Überprüfung
Nach FTD-Upgrade:
> show version
-------------------[ FTD5508 ]--------------------
Model : Cisco ASA5508-X Threat Defense (75) Version 6.0.1 (Build 1213)
UUID : 53b44806-f0f4-11e5-88cc-c72c24d24877
Rules update version : 2016-03-04-001-vrt
VDB version : 259
----------------------------------------------------
>
Aufgabe 7. Verbinden und Trennen des CLI-Modus der LINA-Engine
Wechseln Sie in den LINA-CLI-Modus, und trennen Sie dann die Verbindung.
Lösung
Geben Sie im FTD CLISH-Modus den folgenden Befehl ein:
> system support diagnostic-cli Attaching to ASA console ... Press 'Ctrl+a then d' to detach. Type help or '?' for a list of available commands. firepower>
firepower> enable Password: <-- by default empty (null) firepower#
Wie in der obigen Meldung erwähnt, um die Verbindung von der FTD LINA-Konsole zu trennen (trennen), drücken Sie STRG + a und dann d:
firepower# <- 'Ctrl+a then d' Console connection detached. admin@FTD5508:~$
Aufgabe 8: Neu erstellen einer vorhandenen FTD-Installation
Anforderung
Aktualisieren Sie das vorhandene FTD-Image, und installieren Sie die Version 6.1.0-330.
Lösung
Bei dieser Aufgabe wird davon ausgegangen, dass eine FTD-Appliance mit Code 6.0.1.x vorhanden ist und dass aus welchen Gründen ein neues Image erforderlich ist (z. B. nicht behebbare Datenbankbeschädigung, katastrophaler Fehler, der kein Software-Upgrade erlaubt usw.).
Zusammenfassung der Schritte
- Kompatibilitätsprüfung.
- FTD von FMC abmelden
- Laden Sie die FTD-Appliance neu, und geben Sie die BootCLI ein.
- Führen Sie den Setup-Assistenten aus.
- Installieren Sie das FTD-System-Image.
- Registrierung von FTD bei FMC
Detaillierte Schritte
Schritt 1: Überprüfen Sie die FirePOWER-Versionshinweise, und stellen Sie sicher, dass das FTD-Image, das Sie verwenden möchten, mit dem FMC kompatibel ist. Wenn das FMC nicht zuerst aktualisiert wird.
Schritt 2: Die Registrierung (Löschung) von FTD vom FMC aufheben. Dieser Schritt ist erforderlich, da die UUID-Änderungen nach dem FTD-Reimage nicht erneut registriert werden können, sondern von Grund auf neu hinzugefügt werden muss.
Schritt 3: Laden Sie die FTD-Appliance neu, und geben Sie die BootCLI ein. Da bereits ein FTD-Image installiert ist, kann die FTD-Boot-Image-Installation übersprungen werden:
> reboot
This command will reboot the system. Continue?
Please enter 'YES' or 'NO': YES
Broadcast messagStopping Cisco ASA5506-X Threat Defense......ok
Shutting down sfifd... [ OK ]
Clearing static routes
Unconfiguring default route [ OK ]
Unconfiguring address on br1 [ OK ]
Unconfiguring IPv6 [ OK ]
Downing interface [ OK ]
Stopping nscd... [ OK ]
Stopping system log daemon... [ OK ]
Stopping Threat Defense ...
cp: cannot stat '/etc/ssh': No such file or directory
Stopping system message bus: dbus.
rmdir: failed to remove directory '/etc': Directory not empty [ OK ]
Un-mounting disk partitions ...
…
Device root is still in use.
mdadm: Cannot get exclusive access to /dev/md0:Perhaps a running process, mounted filesystem or active volume group?
Stopping OpenBSD Secure Shell server: sshdstopped /usr/sbin/sshd (pid 4209)
.
Stopping Advanced Configuration and Power Interface daemon: stopped /usr/sbin/acpid (pid 4213)
acpid: exiting
acpid.
Stopping system message bus: dbus.
Deconfiguring network interfaces... ifdown: interface br1 not configured
done.
Sending all processes the TERM signal...
Sending all processes the KILL signal...
Deactivating swap...
Unmounting local filesystems...
Rebooting... ÿ
Rom image verified correctly
Cisco Systems ROMMON, Version 1.1.8, RELEASE SOFTWARE
Copyright (c) 1994-2015 by Cisco Systems, Inc.
Compiled Thu 06/18/2015 12:15:56.43 by builders
Current image running: Boot ROM0
Last reset cause: PowerCycleRequest
DIMM Slot 0 : Present
Platform ASA5506 with 4096 Mbytes of main memory
MAC Address: 84:3d:c6:1a:cf:39
Use BREAK or ESC to interrupt boot.
Use SPACE to begin boot immediately.
Located '.boot_string' @ cluster 260275.
#
Attempt autoboot: "boot disk0:"
Located 'os.img' @ cluster 235457.
#########################################################################################################################################################################################################################################################################################################################################################################################################################################################################################################################################################################################################################################################################################################################################################################################################################################################################################################################################################################################################################
LFBFF signature verified.
INIT: version 2.88 booting
Starting udev
Configuring network interfaces... done.
Populating dev cache
Detected PID ASA5506.
Found device serial number JAD2034008E.
Found USB flash drive /dev/sdb
Found hard drive(s): /dev/sda
fsck from util-linux 2.23.2
dosfsck 2.11, 12 Mar 2005, FAT32, LFN
/dev/sdb1: 42 files, 24805/1798467 clusters
==============================================
Use ESC to interrupt boot and launch boot CLI.
Use SPACE to launch Cisco FTD immediately.
Cisco FTD launch in 23 seconds ... < Press ESC to enter BootCLI
Launching boot CLI ...
Configuring network interface using DHCP
Bringing up network interface.
Depending on your network, this might take a couple of minutes when using DHCP...
ifup: interface lo already configured
Using IPv6 address: fe80::863d:c6ff:fe1a:cf38
IPv4 address not assigned. Run 'setup' before installation.
INIT: Starting system message bus: dbus.
Starting OpenBSD Secure Shell server: sshd
generating ssh RSA key...
generating ssh ECDSA key...
generating ssh DSA key...
done.
Starting Advanced Configuration and Power Interface daemon: acpid.
acpid: starting up
acpid: 1 rule loaded
acpid: waiting for events: event logging is off
Starting ntpd: done
Starting syslog-ng:[2017-01-14T11:20:33.699619] Connection failed; fd='15', server='AF_INET(127.128.254.1:514)', local='AF_INET(0.0.0.0:0)', error='Network is unreachable (101)'
[2017-01-14T11:20:33.699704] Initiating connection failed, reconnecting; time_reopen='60'
.
Starting crond: OK
Cisco FTD Boot 6.0.0 (9.6.2.)
Type ? for list of commands
firepower-boot>
Schritt 4:Führen Sie den Setup-Assistenten aus, und legen Sie die grundlegenden Netzwerkparameter fest:
firepower-boot>setup
Welcome to Cisco FTD Setup
[hit Ctrl-C to abort]
Default values are inside []
Enter a hostname [firepower]: FTD5506
Do you want to configure IPv4 address on management interface?(y/n) [Y]: Y
Do you want to enable DHCP for IPv4 address assignment on management interface?(y/n) [Y]: n
Enter an IPv4 address: 10.48.66.83
Enter the netmask: 255.255.255.128
Enter the gateway: 10.48.66.1
Do you want to configure static IPv6 address on management interface?(y/n) [N]: N
Stateless autoconfiguration will be enabled for IPv6 addresses.
Enter the primary DNS server IP address: 192.168.0.1
Do you want to configure Secondary DNS Server? (y/n) [n]: n
Do you want to configure Local Domain Name? (y/n) [n]: n
Do you want to configure Search domains? (y/n) [n]: n
Do you want to enable the NTP service? [Y]: n
Please review the final configuration:
Hostname: FTD5506
Management Interface Configuration
IPv4 Configuration: static
IP Address: 10.48.66.83
Netmask: 255.255.255.128
Gateway: 10.48.66.1
IPv6 Configuration: Stateless autoconfiguration
DNS Configuration:
DNS Server: 192.168.0.1
NTP configuration: Disabled
CAUTION:
You have selected IPv6 stateless autoconfiguration, which assigns a global address
based on network prefix and a device identifier. Although this address is unlikely
to change, if it does change, the system will stop functioning correctly.
We suggest you use static addressing instead.
Apply the changes?(y,n) [Y]: Y
Configuration saved successfully!
Applying...
Restarting network services...
Done.
Press ENTER to continue...
firepower-boot>
Schritt 5:Überprüfen Sie die Verbindung mit dem Server (FTP, HTTP usw.), der das FTD-Systemabbild enthält, und starten Sie die Installation:
firepower-boot>ping 10.48.40.70
PING 10.48.40.70 (10.48.40.70) 56(84) bytes of data.
64 bytes from 10.48.40.70: icmp_seq=1 ttl=64 time=555 ms
64 bytes from 10.48.40.70: icmp_seq=2 ttl=64 time=0.465 ms
64 bytes from 10.48.40.70: icmp_seq=3 ttl=64 time=0.511 ms
--- 10.48.40.70 ping statistics ---
3 packets transmitted, 3 received, 0% packet loss, time 2000ms
rtt min/avg/max/mdev = 0.465/185.466/555.424/261.599 ms
firepower-boot > system install noconfirm ftp://anonymous:cisco@10.48.40.70/ftd-6. 1.0-330.pkg
######################## WARNING ############################
# The content of disk0: will be erased during installation! #
#############################################################
Do you want to continue? [y/N] y
Erasing disk0 ...
Verifying
Downloading
Extracting
Package Detail
Description: Cisco ASA-FTD 6.1.0-330 System Install
Requires reboot: Yes
Warning: Please do not interrupt the process or turn off the system.
Doing so might leave system in unusable state.
Starting upgrade process ...
Populating new system image
... output omitted ...
Firstboot detected, executing scripts
Executing S01reset_failopen_if [ OK ]
Executing S01virtual-machine-reconfigure [ OK ]
Executing S02aws-pull-cfg [ OK ]
Executing S02configure_onbox [ OK ]
Executing S04fix-httpd.sh [ OK ]
Executing S05set-mgmnt-port [ OK ]
Executing S06addusers [ OK ]
Executing S07uuid-init [ OK ]
Executing S08configure_mysql [ OK ]
************ Attention *********
Initializing the configuration database. Depending on available
system resources (CPU, memory, and disk), this may take 30 minutes
or more to complete.
************ Attention *********
Executing S09database-init [ OK ]
Executing S11database-populate [ OK ]
Executing S12install_infodb [ OK ]
Executing S15set-locale.sh [ OK ]
Executing S16update-sensor.pl [ OK ]
Executing S19cert-tun-init [ OK ]
Executing S20cert-init [ OK ]
Executing S21disable_estreamer [ OK ]
Executing S25create_default_des.pl [ OK ]
Executing S30init_lights_out_mgmt.pl [ OK ]
Executing S40install_default_filters.pl [ OK ]
Executing S42install_default_dashboards.pl [ OK ]
Executing S43install_default_report_templates.pl [ OK ]
Executing S44install_default_app_filters.pl [ OK ]
Executing S45install_default_realms.pl [ OK ]
Executing S47install_default_sandbox_EO.pl [ OK ]
Executing S50install-remediation-modules [ OK ]
Executing S51install_health_policy.pl [ OK ]
Executing S52install_system_policy.pl [ OK ]
Executing S53change_reconciliation_baseline.pl [ OK ]
Executing S70remove_casuser.pl [ OK ]
Executing S70update_sensor_objects.sh [ OK ]
Executing S85patch_history-init [ OK ]
Executing S90banner-init [ OK ]
Executing S95copy-crontab [ OK ]
Executing S96grow_var.sh [ OK ]
Executing S96install_vmware_tools.pl [ OK ]
********** Attention **********
Initializing the system's localization settings. Depending on available
system resources (CPU, memory, and disk), this may take 10 minutes
or more to complete.
********** Attention **********
Executing S96localize-templates [ OK ]
Executing S96ovf-data.pl [ OK ]
Executing S97compress-client-resources [ OK ]
Executing S97create_platinum_forms.pl [ OK ]
Executing S97install_cas [ OK ]
Executing S97install_cloud_support.pl [ OK ]
Executing S97install_geolocation.pl [ OK ]
Executing S97install_ssl_inspection.pl [ OK ]
Executing S97update_modprobe.pl [ OK ]
Executing S98check-db-integrity.sh [ OK ]
Executing S98htaccess-init [ OK ]
Executing S98is-sru-finished.sh [ OK ]
Executing S99correct_ipmi.pl [ OK ]
Executing S99start-system [ OK ]
Executing S99z_db_restore [ OK ]
Executing S99_z_cc-integrity.sh [ OK ]
Firstboot scripts finished.
Configuring NTP... [ OK ]
fatattr: can't open '/mnt/disk0/.private2': No such file or directory
fatattr: can't open '/mnt/disk0/.ngfw': No such file or directory
Model reconfigure detected, executing scripts
Pinging mysql
Found mysql is running
Executing 45update-sensor.pl [ OK ]
Executing 55recalculate_arc.pl [ OK ]
Starting xinetd:
Sat Jan 14 12:07:35 UTC 2017
Starting MySQL...
Pinging mysql
Pinging mysql, try 1
Pinging mysql, try 2
Found mysql is running
Running initializeObjects...
Stopping MySQL...
Killing mysqld with pid 22354
Wait for mysqld to exit\c
done
Sat Jan 14 12:07:57 UTC 2017
Starting sfifd... [ OK ]
Starting Cisco ASA5506-X Threat Defense, please wait...No PM running!
...started.
... output omitted ...
firepower login: admin
Password: < Admin123
You must accept the EULA to continue.
Press <ENTER> to display the EULA:
END USER LICENSE AGREEMENT
…
Please enter 'YES' or press <ENTER> to AGREE to the EULA:
System initialization in progress. Please stand by.
You must change the password for 'admin' to continue.
Enter new password:
Confirm new password:
You must configure the network to continue.
You must configure at least one of IPv4 or IPv6.
Do you want to configure IPv4? (y/n) [y]:
Do you want to configure IPv6? (y/n) [n]:
Configure IPv4 via DHCP or manually? (dhcp/manual) [manual]:
Enter an IPv4 address for the management interface [192.168.45.45]: 10.48.66.83
Enter an IPv4 netmask for the management interface [255.255.255.0]: 255.255.255.128
Enter the IPv4 default gateway for the management interface [192.168.45.1]: 10.48.66.1
Enter a fully qualified hostname for this system [firepower]: FTD5506
Enter a comma-separated list of DNS servers or 'none' []: 192.168.0.1
Enter a comma-separated list of search domains or 'none' []:
If your networking information has changed, you will need to reconnect.
For HTTP Proxy configuration, run 'configure network http-proxy'
Manage the device locally? (yes/no) [yes]: no
Configure firewall mode? (routed/transparent) [routed]:
Configuring firewall mode ...
Update policy deployment information
- add device configuration
- add network discovery
- add system policy
You can register the sensor to a Firepower Management Center and use the
Firepower Management Center to manage it. Note that registering the sensor
to a Firepower Management Center disables on-sensor Firepower Services
management capabilities.
When registering the sensor to a Firepower Management Center, a unique
alphanumeric registration key is always required. In most cases, to register
a sensor to a Firepower Management Center, you must provide the hostname or
the IP address along with the registration key.
'configure manager add [hostname | ip address ] [registration key ]'
However, if the sensor and the Firepower Management Center are separated by a
NAT device, you must enter a unique NAT ID, along with the unique registration
key.
'configure manager add DONTRESOLVE [registration key ] [ NAT ID ]'
Later, using the web interface on the Firepower Management Center, you must
use the same registration key and, if necessary, the same NAT ID when you add
this sensor to the Firepower Management Center.
Schritt 6: FTD im FMC registrieren
> configure manager add 10.62.148.50 cisco Manager successfully configured. Please make note of reg_key as this will be required while adding Device in FMC. > show managers Host : 10.62.148.50 Registration Key : **** Registration : pending RPC Status :
Navigieren Sie auf dem FMC zu Geräte > Gerätemanagement, um das FTD-Gerät hinzuzufügen.
Nachdem Sie FTD zu FMC hinzugefügt haben, müssen Sie:
- Konfigurieren Sie die Geräteeinstellungen wie Schnittstellen und Routing neu.
- Neukonfiguration von Richtlinien wie VPN und QoS
- Anwenden zuvor angewendeter Richtlinien und Einstellungen wie Zugriffskontrollrichtlinie, NAT und Plattformeinstellungen
Zugehörige Informationen
Beiträge von Cisco Ingenieuren
- Mikis ZafeiroudisCisco TAC-Techniker
- Dinkar SharmaCisco TAC-Techniker
- Olha YakovenkoCisco TAC-Techniker
Cisco kontaktieren
- Eine Supportanfrage öffnen

- (Erfordert einen Cisco Servicevertrag)
 Feedback
Feedback