Making previously unimaginable outcomes a reality
A fundamentally new approach to address today's realities
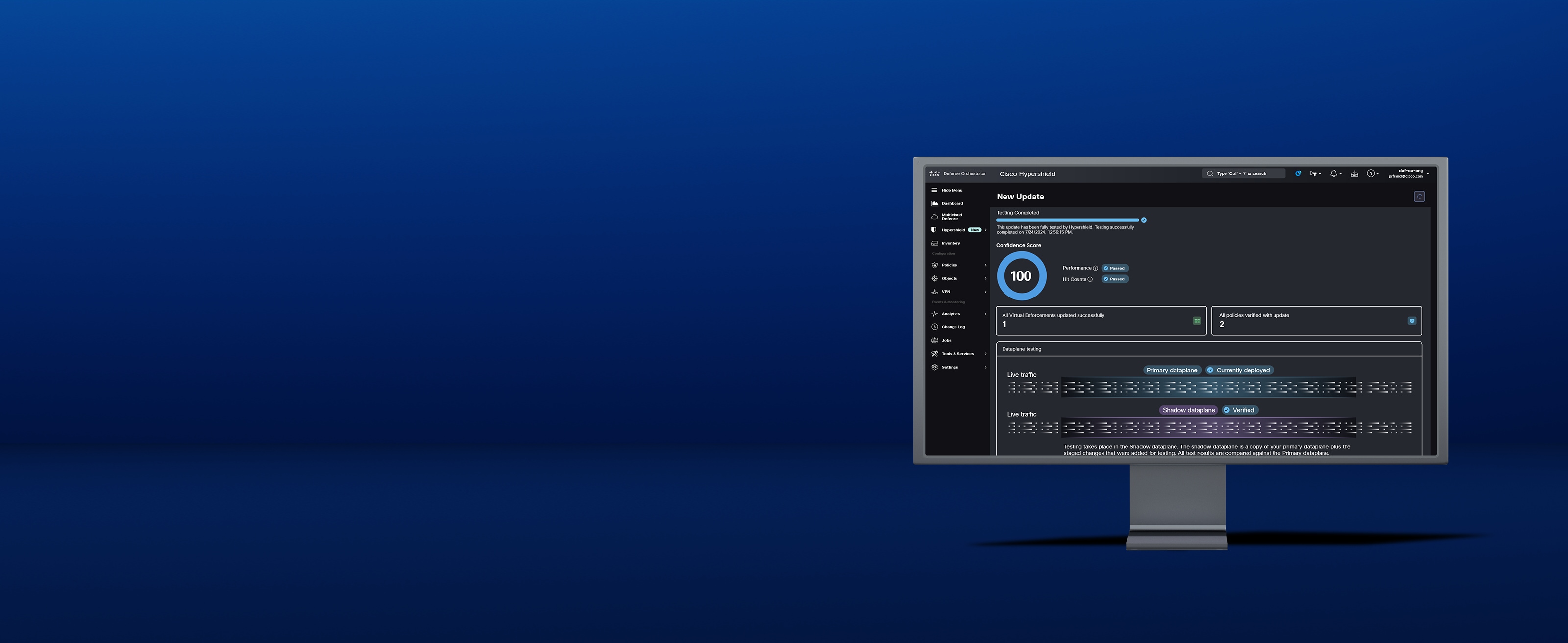
An AI-native security architecture that's rewriting the rules
Network and security leaders from Goldman Sachs, The Ohio State University Medical Center, and Cisco discuss how to tackle AI-scale attacks, automated updates, and how Cisco Hypershield can address their needs.