Cisco Security Manager Data Sheet
Available Languages
Cisco®Security Manager is an integrated end-to-end solution that helps administrators enforce consistent access policies, rapidly troubleshoot security events, and view summarized reports across the deployment.
Product Overview
Businesses are facing ever greater challenges in their security operations. The growing number and complexity of technologies, combined with the reduction of IT professionals once dedicated to security management, has dramatically increased the potential for human error, which can lead to exposures and breaches.
Cisco Security Manager counteracts these challenges. It provides scalable, centralized management for a wide range of devices. Administrators gain visibility across the network and can share highly secure information with other essential network services, such as compliance systems and advanced analysis systems. Designed for operational efficiency, Security Manager also includes a powerful suite of automated capabilities, such as health and performance monitoring, software image management, automatic conflict detection, and integration with ticketing systems.
Security Manager supports a wide range of Cisco security devices, including the Cisco ASA 5500 Series and ASA 5500-X Series appliances; and the Cisco AnyConnect® Secure Mobility Client.
From Cisco Security Manager 4.17 onwards, it does not support
● Cisco Catalyst 6500 and 7600 Series Firewall Services Modules (EOL8184)
● Cisco Catalyst 6500 Series Intrusion Detection System Services Module 2 (EOL8843)
● Cisco Intrusion Prevention System: IPS 4200, 4300, and 4500 Series Sensors (EOL9916)
● Cisco SR 500 Series Secure Routers (EOL7687, EOL7657)
Several features in Security Manager make for simplified and efficient management. The following sections describe these features.
Dashboard
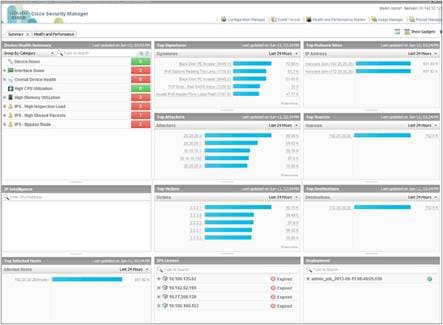
The manager’s dashboard (Figure 1) is a widget-based home screen that gives a bird’s-eye view of the health, functioning, and other major performance indicators of a network security setup. Several widgets, such as the Device Health Summary, Top Attackers, Top Victims, and Top Signatures, provide an excellent summary of priority security aspects. These widgets act as a starting point for any security readiness analysis. For example, in the Signatures widget, you can click the number of times a specific signature has been hit. Security Manager then takes you to the Event Viewer, where events corresponding to that signature can be analyzed. Similarly, you can click an IP address in the Top Attackers widget and look at value-added information related to that IP address. So, in summary, the dashboard screen is the starting point for security administrators. These dashboards can be personalized to suit each administrator’s needs.
Integrated Policy and Object Management
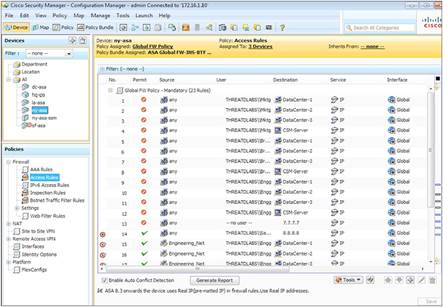
Security Manager helps enable the reuse of security rules and objects. It also enhances your ability to monitor threats throughout the deployment, reducing the potential for errors and improving efficiency. You can implement security deployments on either an on-demand or a scheduled basis and can roll back to a previous configuration if required. Role-based access control and deployment workflows help ensure that compliance processes are followed (Figure 2).
Event Management and Troubleshooting
Integrated event management helps enable the viewing of real-time and historical events for rapid incident analysis and troubleshooting. You can quickly navigate from events to source policies. In addition, you can identify and isolate interesting events by using the advanced filtering and search capabilities. Cross-linkages between the Event Manager and Configuration Manager shorten the troubleshooting time for firewall rules (Figure 3).
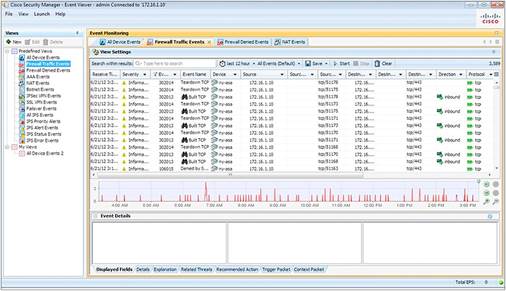
The Event Manager provides:
● Support for syslog messages created by Cisco ASA appliances, and Cisco Catalyst® 6500 Series ASA Services Module
● Real-time and historical event viewing
● Cross-linkages to firewall access rules for quick navigation to the source policies
● A pre-bundled set of views for firewall, and VPN
● Customizable views for monitoring select devices or a select time range
● Intuitive GUI controls for searching, sorting, and filtering events
● Administrative options to turn event collection on or off for select security devices
● Tools such as ping, traceroute, and packet tracer for further troubleshooting capabilities
Security Manager generates detailed system reports of events and other essential information gathered throughout the security deployment (Figure 4). Table 1 lists the available system reports. In addition, you can predefine and save reports to meet specific reporting needs. Whether system generated or predefined, all reports can be exported and scheduled for email delivery as PDF or CSV files. You can also find more detail from a specific chart if you want to view additional information for further analysis.
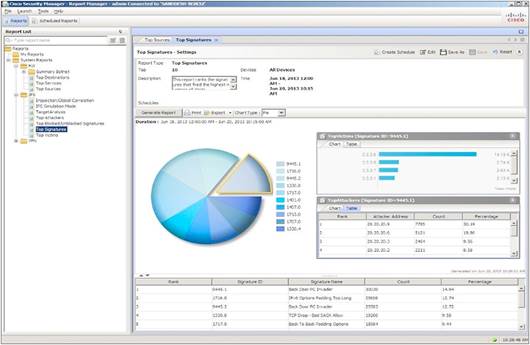
Table 1. System Reports
| Firewall |
VPN |
|
● Top Infected Hosts
|
● Top Bandwidth Users (SSL/IPsec)
● Top Duration Users (SSL/IPsec)
● Top Throughput Users (SSL/IPsec)
● User Report
● VPN Device Usage Report
|
Health and Performance Monitoring
The integrated Health and Performance Monitor can help you increase your productivity. It continuously analyzes the security environment and sends alerts when preset thresholds are reached. Customizable alert notifications can be set for such events as critical firewall failover, or excessive CPU or memory use.
With the monitor’s simple color-coded interface, you can immediately identify any devices that are in critical condition. You can view commonly monitored attributes (CPU or memory use, for example) to rapidly ascertain the general health and performance of all devices across the security deployment. Detailed charts give additional insights regarding the health, traffic, and performance metrics of each device, as desired. Figure 5 shows the primary monitoring interface.
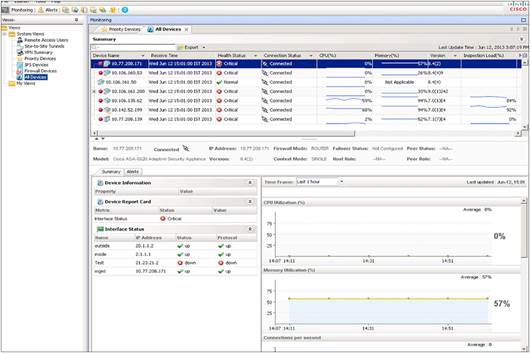
These health and monitoring features are available for the new Cisco ASA clustering features as well.
Software Image Upgrades
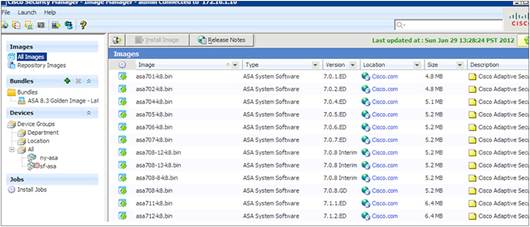
Firewall software images can be upgraded using an intuitive wizard. The wizard leads you through the steps required to download the images, create the image bundle, and verify that the image is appropriate for each device. The tool then performs the backup, takes the devices down, and performs the update. The updates can be performed on each firewall individually or run in groups for more speed and efficiency. The process is automated so it can be run overnight or during noncritical times to reduce disruption to the operating environment. Figure 6 shows the primary image-management interface of the solution.
API-Based Access to the Security Manager
With highly secure API-based access, Security Manager can share information with other essential network services, such as compliance and advanced security analysis systems, to streamline the security operations and compliance adherence. Using representational state transfer, external firewall compliance systems can directly request access to data from any security device that the Security Manager manages. These third-party client programs can also add, delete, or modify firewall-access policies and policy objects in the Security Manager through APIs. The APIs integrate transparently with the solution’s workflow, so administrators can enforce strict controls when the APIs automate the policy configuration.
Additional Features and Benefits
Table 2 summarizes the additional features and benefits of Security Manager.
Table 2. Additional Features and Benefits
| Feature |
Benefit |
| Firewall Configuration |
|
| Manages the Cisco security deployment |
Facilitates the centralized management of the Cisco security environment, including:
● ASA 5500 Series and 5500-X Series appliances
● ASA on Firepower 2100, 4100 and 9300 Series appliances
● ASAv on VMware and KVM
● AnyConnect
® Secure Mobility Client
● Cisco Catalyst 6500 Series ASA Services Modules
● Integrated Services Router (ISR) platforms running a Cisco IOS
® Software security image
|
| Zone-based policies |
Sets zone-based firewall policies on supported device platforms if desired. |
| Botnet Traffic Filter |
Supports the Cisco Botnet Traffic Filter on the ASA platform, for application-layer inspection and blockage of “phone-home” activity by botnets. |
| Integration with Cisco TrustSec security group tags |
Provides integration with Cisco TrustSec security group tags, so that Security Manager users can configure detailed and highly relevant policies across deployments. |
| ASA clustering |
Offers advanced failover capabilities to support multiple ASA appliances and load-sharing mechanisms to reduce downtime and improve availability. |
| Content filtering |
Supports content filtering on Cisco IOS Software–based device platforms to filter traffic based on deep content inspection. Supports the management of multiple device platforms using a single rule table. |
| Efficient policy definition |
Increases the efficiency with which administrators can define policies by clearly displaying which rules match a specific source, destination, and service flow, including wildcards. |
| Syslog forwarding |
Supports forwarding logs generated by ASA firewalls to two remote collectors in addition to the in-built Event Viewer. |
| Simplified setup |
Streamlines configuration and simplifies the initial security management setup by making it possible for device information to be imported from a device repository or configuration file, added in the software, or discovered from the device itself. |
| Streamlined operations |
Significantly reduces manual tasks while reducing errors and optimizing the security environment, through:
● Rule-conflict detection, hit-count analysis, rule combiner, and other powerful tools to analyze and optimize rule sets.
● Role-based access control and workflow to help ensure error-free deployments and process compliance.
|
| Interface roles |
Can apply rule policies to groups of interfaces and centrally manages them to increase flexibility and scalability. |
| VPN Configuration |
|
| VPN wizard |
Provides easy configuration of site-to-site, hub-and-spoke, full-mesh, and extranet VPNs. |
| Support for common VPN deployment scenarios |
Supports common VPN deployment scenarios with support for Group Encrypted Transport VPN (GET VPN), Dynamic Multipoint VPN (DMVPN), and generic routing encapsulation (GRE) IP Security (IPsec), both with dynamic IP and hierarchical certificates. |
| Multiple context configurations |
Supports policy segmentation and flexibility with security configurations between branch offices spanning multiple locations. |
| Remote configuration |
Centralizes the management of VPNs. |
| Efficiency and Usability Features |
|
| Ticketing integration |
Can tag changes made in multiple ticketing systems with a single ticket identifier, making them easily queried for audit. |
| Global search |
Can find all devices, policies, and policy objects in the configuration database that use a particular IP address or service. |
| Find usage |
Helps administrators quickly find usage information about objects by pointing to the exact rules that use a particular policy object, in addition to providing details about all the policies that use the object. |
| Automatic conflict detection |
Provides a clear picture about rule conflicts to simplify rule optimization and troubleshooting. |
| IPv4 and IPv6 cross-compatibility |
Supports the configuration of unified IPv4 and IPv6 policies and rules to help speed deployments and improve compatibility between policy configurations. |
| Integrated event management |
Helps enable administrators to monitor status and to troubleshoot security information, by providing:
● Receipts of syslog messages from Cisco ASA appliances
● Real-time and historical event views
● Cross-linkages to firewall access rules for quick navigation to the source policies
● Prebundled sets of views for firewall, and VPN monitoring
● Customizable views for monitoring select devices or a select time range
● Intuitive GUI controls for searching, sorting, and filtering events
● Administrative options to turn event collection on or off for select security devices
● Launch of the Cisco Prime
™ Security Manager when an ASA CX deployment is detected in the environment; this provides a way to manage CX through the Security Manager
|
| Report Manager |
Supports system reports and the creation of predefined reports, all of which can be:
● Viewed as charts and grids
● Exported as PDF or Excel files
● Scheduled for delivery by email
● Scanned for more detail
|
| Bulk operations |
Reduces administrative overhead in networks that have a large number of devices. The feature includes:
● Bulk import and export of policy objects
● Bulk addition for offline devices
● Bulk import of device-level overrides
● Bulk automatic software image updates for all Cisco ASA appliances deployed throughout the network, providing a flexible, consistent, and faster way of deploying updates at scale
|
| Device grouping |
Allows administrators to create and define device groups based on business function or location, and then manage all devices in a group as a single device. |
| Policy Object Manager |
Defines objects such as network addresses, services, device settings, time ranges, or VPN parameters once and then uses them any number of times to avoid manual entry of values. |
| Other Capabilities |
|
| Third-party device support |
Supports “unmanaged” endpoints and third-party devices. |
| Security services management |
Manages integrated security services, including quality of service (QoS) for VPN, routing, and Cisco Network Admission Control. |
| Multiple application views |
Provides multiple views into the application to support different use cases and experience levels. |
| Flexible deployment options |
Can implement security deployments on either an on-demand or a scheduled basis. |
| Rollback |
Can roll back deployments to a previous configuration if required. |
| Role-based access control |
Defines and enforces up to five administrator roles; additional roles are available with the optional Cisco Secure Access Control Server. |
| Workflow |
Can assign specific tasks to each administrator during the deployment of a policy, with formal change control and tracking. |
| Distributed deployment |
Includes the Auto Update Server and the Cisco Network Services Configuration Engine to simplify updates to large numbers of remote firewalls, which may have dynamic addresses or NAT addresses. |
| Integration with Cisco Cloud Web Security |
Allows users to define rules on firewalls by means of the Security Manager and gives an option to forward web traffic to Cloud Web Security. |
| Health and performance monitoring |
Continuously analyzes normal and clustered security environments and sends alerts when preset thresholds are reached. |
| IP intelligence |
Has embedded IP intelligence in several features. Users can look at value-added information such as FQDN and location information for an IP address from several widgets (for example, Top Attackers) in the home screen, in the Report Manager while analyzing a specific chart, and in the Health and Performance Monitor. IP Intelligence also exists as a separate widget in itself that can be added to a dashboard. |
Technical Specifications
Detailed hardware specifications and sizing guidelines for Security Manager are available at: http://www.cisco.com/go/csmanager.
Device Support
Table 3 summarizes the device product families supported by Security Manager. For a detailed list, including supported device software versions, see “Supported Devices and OS Versions for Cisco Security Manager” at: http://www.cisco.com/en/US/products/ps6498/products_device_support_tables_list.html.
Table 3. Overview of Supported Cisco Devices
Ordering Information
For ordering details, please refer to the Licensing chapter of the Installation Guide for Cisco Security Manager.
Cisco Services
Cisco offers a wide range of service programs to accelerate customer success. These innovative services programs are delivered through a unique combination of people, processes, tools, and partners, resulting in high levels of customer satisfaction. Cisco services help you protect your network investment, optimize network operations, and prepare your network for new applications to extend network intelligence and the power of your business. For more information about Cisco services for security, visit https://www.cisco.com/go/services/security.
Security Manager software is eligible for technical support service coverage under the Cisco Software Application Support service agreement, which features:
● Unlimited access to the Cisco Technical Assistance Center for award-winning support. Technical assistance is provided by Cisco software application experts trained in Cisco security software applications. Support is available 24 hours a day, 7 days a week, 365 days a year, worldwide.
● Registered access to Cisco.com, a robust repository of application tools and technical documents to assist in diagnosing network security problems, understanding new technologies, and staying current with innovative software enhancements. Utilities, white papers, application design data sheets, configuration documents, and case management tools help expand your in-house technical capabilities.
● Access to application software bug fixes and maintenance, and minor software releases.
Cisco Capital
Financing to Help You Achieve Your Objectives
Cisco Capital® financing can help you acquire the technology you need to achieve your objectives and stay competitive. We can help you reduce CapEx. Accelerate your growth. Optimize your investment dollars and ROI. Cisco Capital financing gives you flexibility in acquiring hardware, software, services, and complementary third-party equipment. And there’s just one predictable payment. Cisco Capital is available in more than 100 countries. Learn more.
For More Information
For more information about Cisco Security Manager, visit http://www.cisco.com/c/en/us/products/security/security-manager/index.html or contact your account manager or a Cisco Authorized Technology Provider. You may also send an email to ask‑csmanager@cisco.com.
 Feedback
Feedback