What’s New in Stealthwatch Release 7.3.0 At-a-Glance
Available Languages
Bias-Free Language
The documentation set for this product strives to use bias-free language. For the purposes of this documentation set, bias-free is defined as language that does not imply discrimination based on age, disability, gender, racial identity, ethnic identity, sexual orientation, socioeconomic status, and intersectionality. Exceptions may be present in the documentation due to language that is hardcoded in the user interfaces of the product software, language used based on RFP documentation, or language that is used by a referenced third-party product. Learn more about how Cisco is using Inclusive Language.
Automated response, easier management, and enhanced security analytics
What’s new in Cisco Stealthwatch Release 7.3.0
A lot of things have fundamentally changed how users work today. Applications, data, and user identities have moved to the cloud, branch offices connect directly to the internet, and many users work off-premises. Although this has given users an unprecedented ability to access, create, and share information online, it has also increased the likelihood of them exposing sensitive information. Couple that with today’s evolving threats, and it comes as no surprise that security breaches continue to proliferate. You need comprehensive visibility into all network behavior both on and off premises to be able to detect any suspicious behavior. This is where a network detection and response (NDR) solution like Cisco Stealthwatch can help.
Stealthwatch collects telemetry from network traffic, applies behavioral based modeling analytics and machine learning, and incorporates threat intelligence from Cisco Talos to derive a baseline of what normal network behavior looks like to identify suspicious and anomalous behavior in your organization, alert you to its presence, and facilitate response efforts.
Stealthwatch release 7.3.0, introduces automated response capabilities to Stealthwatch, giving you new methods to share and respond to alarms, both through improvements to the response management module, and through SecureX threat response integration enhancements. In addition to that, we are announcing other exciting updates to the web UI to increase ease of use, and security analytics updates that offer more threat detection advancements.
● Modernized response management module now in the web UI with customizable settings to facilitate automated data sharing and remediation
● Configurable rules and actions to offer numerous possibilities on how to share or respond to alarms
● SecureX platform integration enhancements
● Optimized installation process through full configuration in the web UI
● Flow Sensor deployment configuration and visibility improvements
● Enhanced security analytics
New methods for sharing and responding to alarms
With release 7.3.0, Stealthwatch’s response management module has been moved to the web-based UI and modernized to facilitate data-sharing with 3rd party event gathering and ticketing systems. It now offers numerous ways to share and respond to alarms through a range of customizable action and rule options to aid in streamlining remediation operations and accelerating containment. You can also reduce noise and accelerate incident investigations with flexible rule configurations that allow you to specify which alarms from Stealthwatch are shared with SecureX threat response and improve operational efficiency by automating responses with pre-built workflows through the SecureX platform’s orchestration capabilities.
1. Automate remediation by limiting the compromised device’s network access when detections occur, through automated and customizable quarantine policies that leverage Identity Services Engine (ISE) and Adaptive Network Control (ANC)
2. Webhooks to enhance data-sharing with third-party tools add unparalleled flexibility in response management and save time
3. Streamline and accelerate incident investigation and remediation efforts by specifying which malware detections to send to SecureX threat response as well as associated response actions
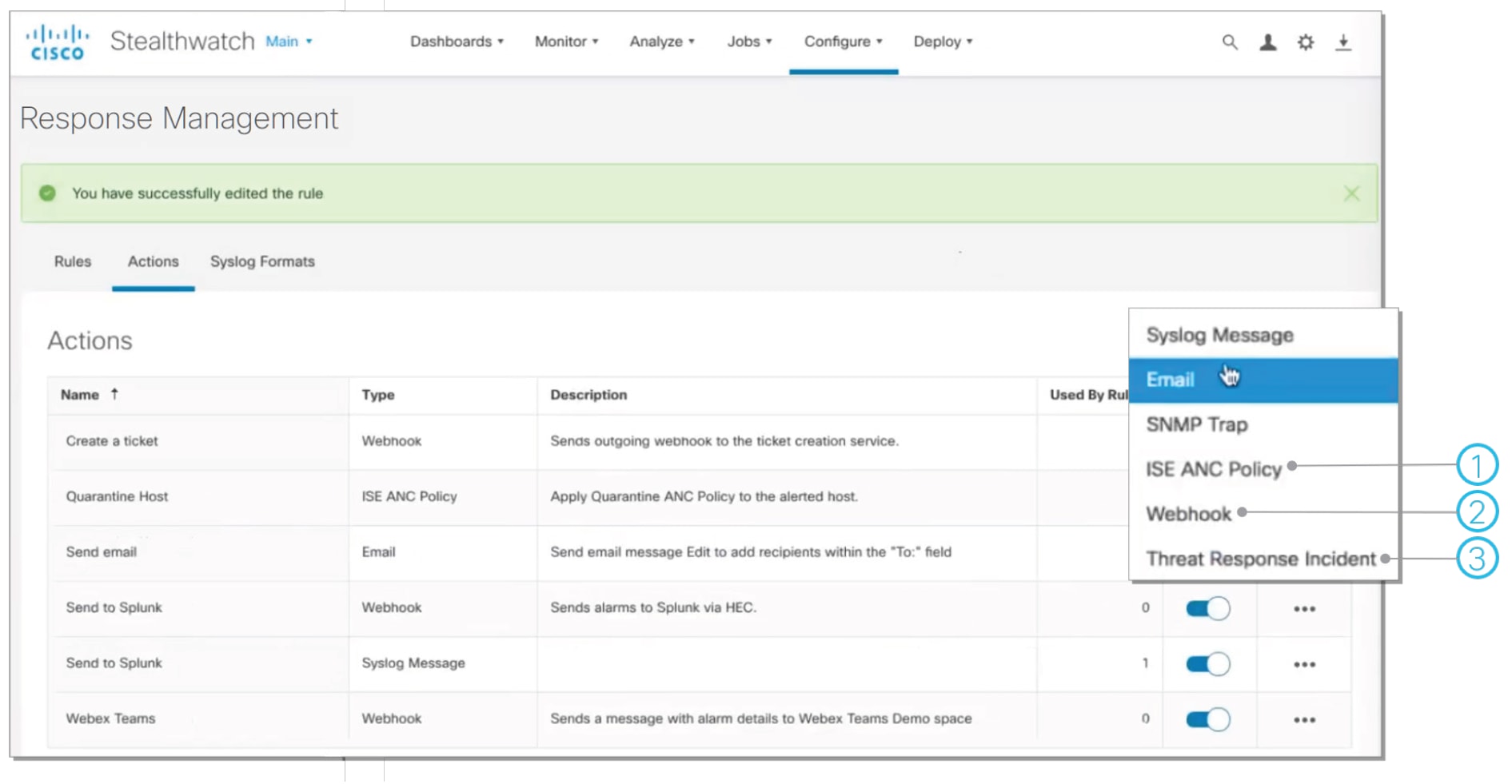
1. Set up rules to trigger when an alarm fires
2. Configure specific actions or responses that will take place once the above rule is triggered


Response Automation updates with SecureX
Cisco’s SecureX platform unifies visibility, centralizes alerts, and enables automation across your entire security infrastructure on a single dashboard. Reduce noise and accelerate investigations with flexible rule configurations to define which alarms from Stealthwatch are shared with SecureX threat response. Maximize operational efficiency and eliminate repetitive tasks by automating responses with pre-built workflows through SecureX’s orchestration capabilities.
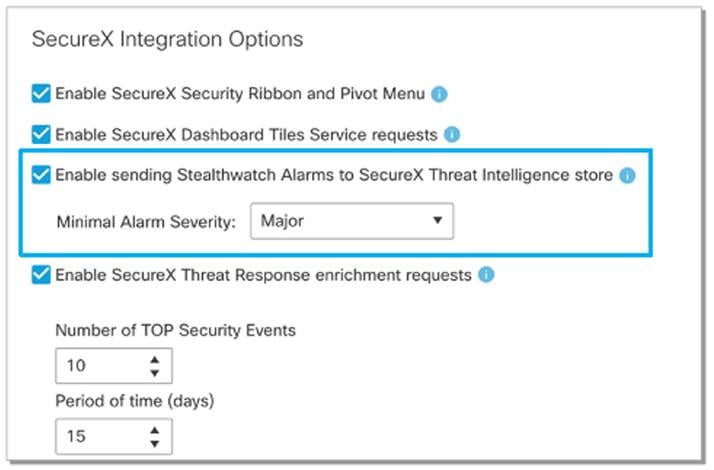

1. Automate responses with pre-built workflows through SecureX’s orchestration capabilities
2. Create your own playbooks by leveraging SecureX’s intuitive interface and all of your integrated security tools

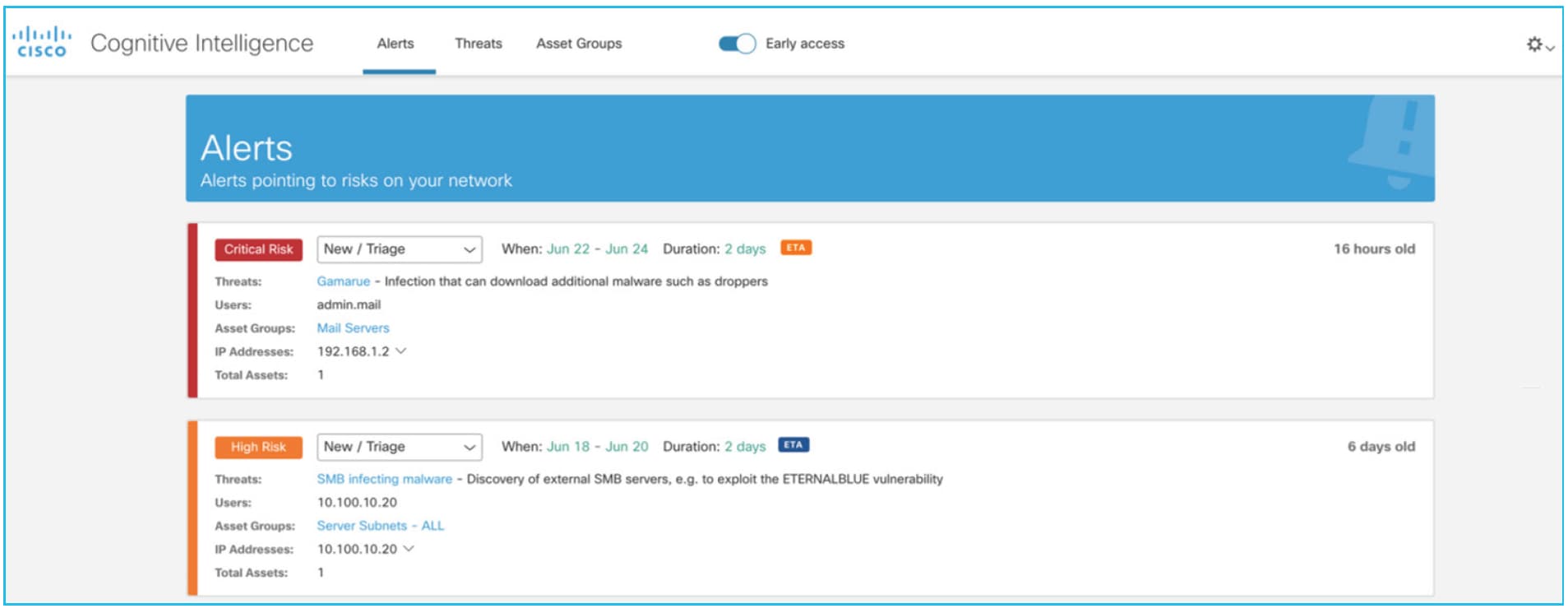
We continue to update and improve Stealthwatch analytics to stay ahead of evolving threats and deliver fast and high-fidelity detections. The cloud-based machine learning engine (Cognitive Intelligence) has been updated to include enhanced detections, new classifiers, smart alert fusion in the new GUI, and new Stealthwatch use cases including Remote Access Trojan and Emotet malware detections.

Save time and optimize the installation process with web UI enhancements that support full appliance configuration.
Flow Sensor versatility and visibility enhancements
ERSPAN (Encapsulated Remote Switch Port Analyzer) support has been added to the Flow Sensor to increase versatility. Now, it also offers visibility improvements through the ability to see within VMware’s NSX-T data centers to facilitate Flow Sensor deployment and network configuration.
Introducing the Stealthwatch Data Store!
The Data Store will be supported by versions 7.3 and above and offers an improved database architecture design for Stealthwatch that enables new ways of storing and interacting with data more efficiently.
Each individual Data Store appliance includes a 3-node database cluster that sits between the Stealthwatch Management Console and Flow Collectors. One or more Flow Collectors ingest and de-duplicate flow data, perform analyses, and then send the flow data and its results directly to the Data Store. This flow data is then distributed equally across a Data Store, which is comprised of a minimum of three Data Node appliances. The Data Store facilitates flow data storage and keeps all your network telemetry in one centralized location as opposed to having it spread across multiple Flow Collectors in a distributed model.
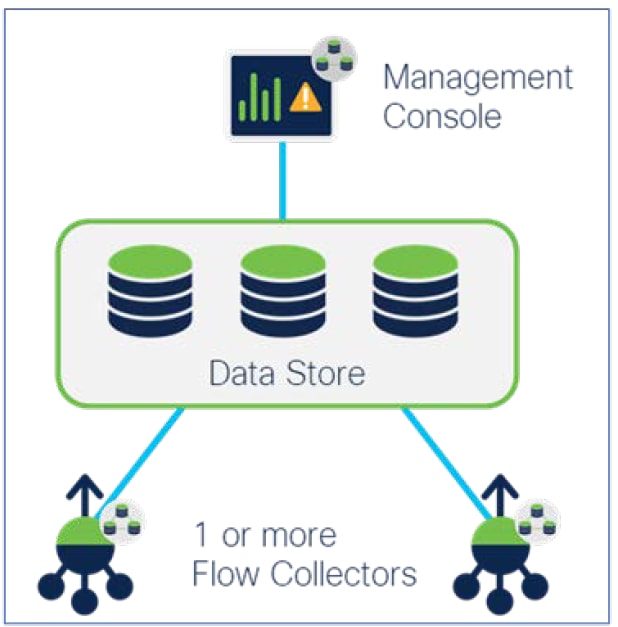
This new centralized model with flow ingest by Flow Collectors decoupled from data storage offers the following benefits:
● Increased ingest capacity: Data Stores can be combined to create a single cluster that is capable of monitoring over 3 million flows per second to aid in relieving ingestion bandwidth challenges for organizations with high flow volumes.
● Query and reporting response times improved by a significant magnitude: The Data Store provides drastically improved query performance and reporting response times of at least 10x faster than those offered by other standard deployment models and can also perform an increased number of concurrent queries to deliver substantial operational efficiency gains. Through the ability to run reports and get answers more quickly, the Data Store enables practitioners to pinpoint and respond to threats more quickly to expedite triage, investigation, and remediation workflows.
● Enterprise-class data resiliency: Telemetry data is stored redundantly across nodes to allow for seamless data availability during single node failures helping to ensure against loss of telemetry data.
● Storage scalability: The Data Store offers organizations with growing networks enhanced flexibility around data storage scalability through the ability to add additional database clusters.
To learn more, check out the Stealthwatch Data Store Solution Overview.
● Streamline remediation operations by customizing rules and actions to automate data sharing with 3rd party event gathering and ticketing systems
● Maximize operational efficiency and eliminate repetitive tasks by automating responses with pre-built workflows through SecureX’s orchestration capabilities
● Reduce noise and accelerate incident investigations with flexible rule configurations to define which alarms from Stealthwatch are shared with SecureX threat response
● Stay ahead of emerging threats with machine learning detection enhancements
● We continue to deliver new use cases that cover new Stealthwatch functionalities and new malware detections
● Save time with Web UI enhancements that optimize the installation process and support full appliance configuration
For further details about this release, please refer to the release notes.
To learn more about Stealthwatch, visit https://www.cisco.com/go/secure-network-analytics.
or contact your local Cisco account representative.