Introduction
This document describes how to block ICMP (ping) responses from Cent7_NAT router.
Prerequisites
Requirements
Root access to the NAT router

Warning: Keep in mind that disabling ICMP renders traceroute (from Linux) and tracert (from windows) unusable.
Components Used
- CSPC (tested version: Cent7_NAT_V3.ova )
- (Optional) Access to ESXI (in case connectivity to the VM is lost)
The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, ensure that you understand the potential impact of any command.
Configure
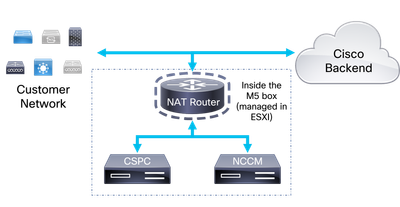
Network Diagram
Configurations
1. Log in to the NAT router by using the IP of your collector and port 1022 on your SSH client.
2. Change your user to root.
su -
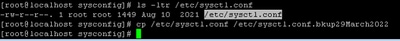
3. Backup the /etc/sysctl.conf file:
cp /etc/sysctl.conf /etc/sysctl.conf.bkup<date>
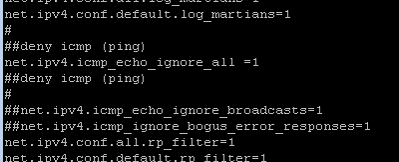
4. Once backed up, modify the /etc/sysctl.conf file and add the line:
net.ipv4.icmp_echo_ignore_all = 1
5. Comment out all lines matching net.ipv4.icmp.
6. Save your changes.
Warning: SSH access to CSPC, NCCM and AFM is lost after step 7
7. Load the new variables with the command.
sysctl -p
Warning: Connection from CSPC, NCCM, and AFM is interrupted after step 8. This can affect ongoing collections and changes being applied from NCCM to the devices.
8. Reboot the NAT router.
9. Verify connectivity to CSPC, NCCM and AFM (if applicable) by opening a SSH session to them.
Verify
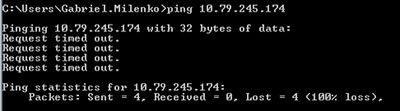
After step 7, ping to the Cent7_NAT router IP address stops responding.
Before:
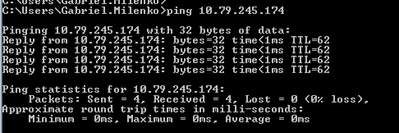
After:
Troubleshoot
If connectivity to the CSPC, NCCM or AFM boxes is not recovered upon reboot of the Cent7_NAT router, log into the Cent7_NAT router and revert the changes using the backup from step 3.
cp /etc/sysctl.conf.bkup<date> /etc/sysctl.conf







 Feedback
Feedback