Introduction
This document describes the solutions for Certificate Expiry alert of Verisign certificate(VeriSign_Class_3_Secure_Server_CA_-_G3.der) provided for Smart Call Home which is set to expire on Feb 2020 in the following Cisco Unified Collaboration Products that are covered in this document.
| Cisco Unified Communications Manager (UCM) |
| Cisco Unified Communications Manager Session Management Edition |
| Cisco IM and Presence Service (CUPS) |
| Cisco Unity Connection |
| Cisco Finesse |
| Cisco SocialMiner |
| Cisco MediaSense |
| Cisco Unified Contact Center Express |
|
Cisco Unified Intelligence Center (CUIC)
|
| Cisco Virtualized Voice Browser |
| Cisco Prime License Manager |
Prerequisites
Requirements
There are no specific requirements for this document.
Components Used
The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, make sure that you understand the potential impact of any command.
Background Information
Smart Call Home is an automated support capability that monitors Cisco devices on your network. The Call Home feature allows you to communicate and send the diagnostic alerts, inventory, and other messages to the Smart Call Home backend server.
Use this section to verify if Smart Call Home is enabled
Step 1. From the Cisco Unified Serviceability page, choose CallHome > Configuration.
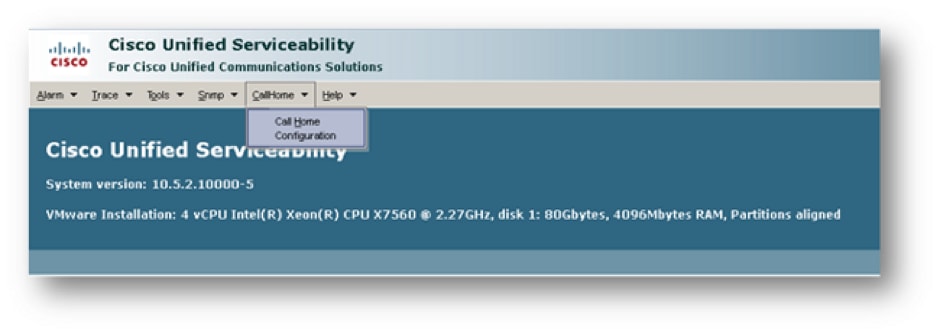
Step 2. Check if the Call Home field is set to Disabled or Enabled

Problem
The VeriSign certificate(VeriSign_Class_3_Secure_Server_CA_-_G3.der) provided by default as tomcat-trust certificate for Smart Call Home on Cisco Unified Collaboration Products is set to expire on Feb 2020. The following expiration alert may be seen below:
%UC_CERT-4-CertValidLessThanMonth: %[Message=Certificate expiration Notification.
Certificate name:VeriSign_Class_3_Secure_Server_CA_-_G3.der
Unit:tomcat-trust Type:own-cert ]
[AppID=Cisco Certificate Monitor][ClusterID=][NodeID=UCM-PUB.ciscolab.com]
Solution
This issue is documented by Cisco bug ID CSCvs64158 .
Workaround for 11.0(1) and higher versions
We need to perform below steps to Delete the expired certificate (VeriSign_Class_3_Secure_Server_CA_-_G3.der)
Step 1. Browse to the Cisco Unified OS Administration GUI on the Publisher and Click on Security > Certificate Management

Step 2. Find Certificate List where Common Name contains VeriSign
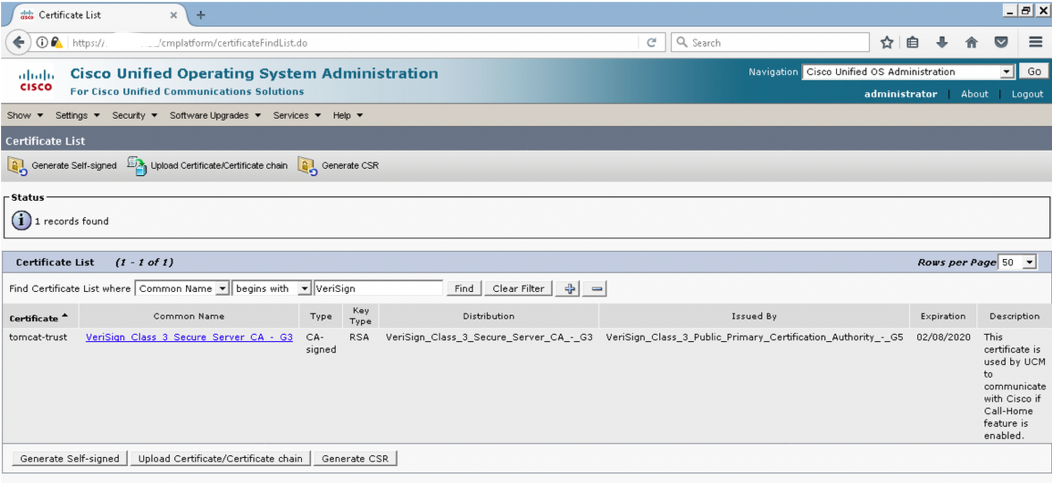
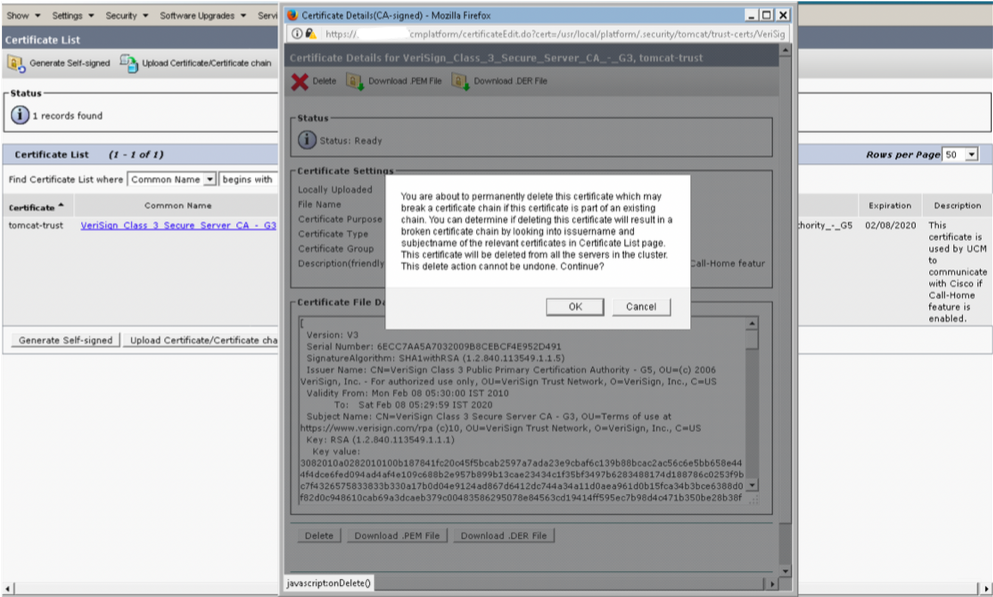
Step 3. Click on VeriSign_Class_3_Secure_Server_CA_-_G3 and you will see the pop-up window highlighting the details of the certificate

Step 4. Click on Delete button and warning prompted Click OK. The certificate should be deleted from all nodes in the cluster.

For all other versions
We need to perform below steps before we delete the certificate
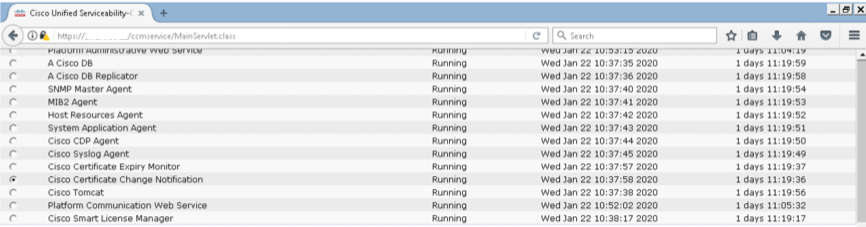
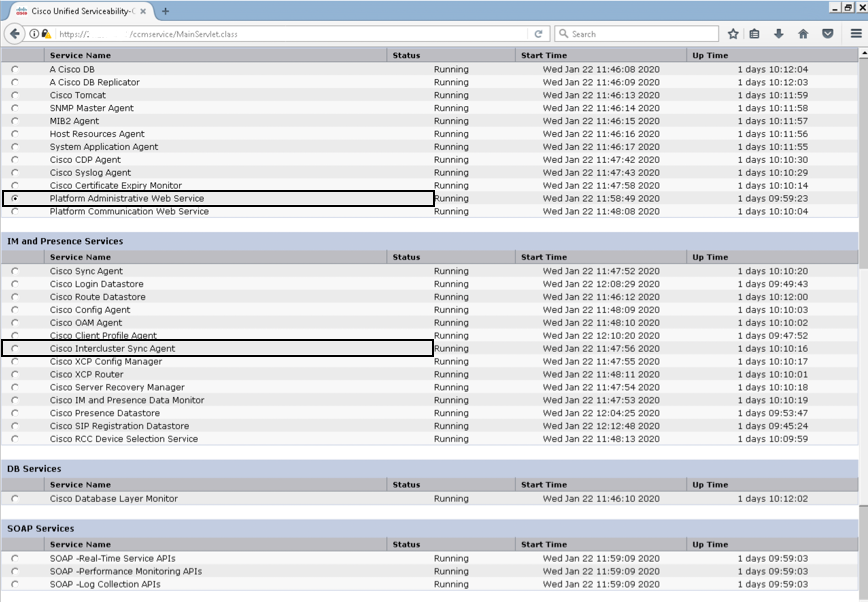
Step 1. Navigate to Cisco Unified Serviceability > Tools > Control Center - Network Services

Step 2. Stop Cisco Certificate Change Notification on all node in the cluster
Step 3. Incase of IM and Presence Server Stop Platform Administration Web Services and Cisco Intercluster Sync Agent
Step 4. Delete the certificate on all the nodes including IM and Presence as described in Section Workaround for 11.0(1) and higher in this document
Step 5. Start the service which were stopped in Step 2. and Step 3.
Note: If you delete the certificate and you do an upgrade prior to 7 Feb 2020, the certificate will reappear after the upgrade and which has to be removed again. Any upgrades after 7 Feb 2020 will not re-add the certificate
Smart Call Home Certificates Renewal Procedure
If Smart Call Home is disabled, no further action is required after deleting the certificate. If Smart Call Home is enabled, follow the steps
Step 1. Copy the certificate content from UCM Administration Guide Section Information for Smart Call Home Certificates

Note: Same certificate is valid for 10.5 and higher version
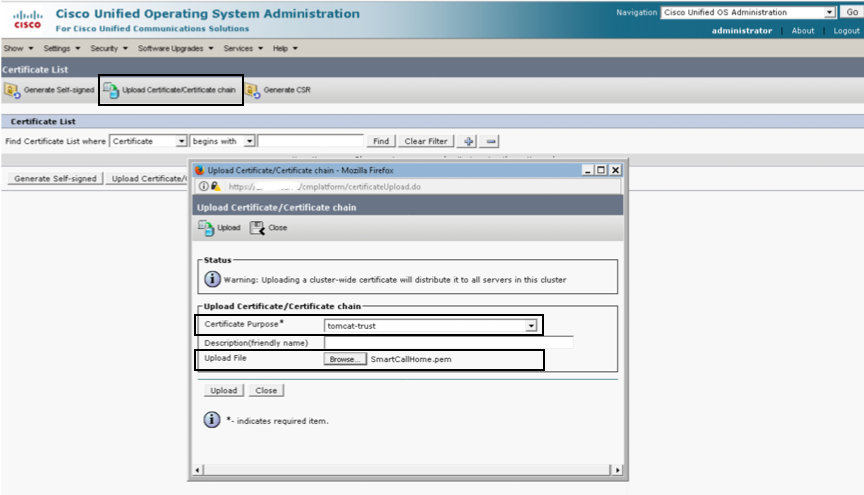
Step 2. Upload the .pem file as tomcat-trust in Cisco Unified OS Administration GUI Certificate Management Page per the screenshot
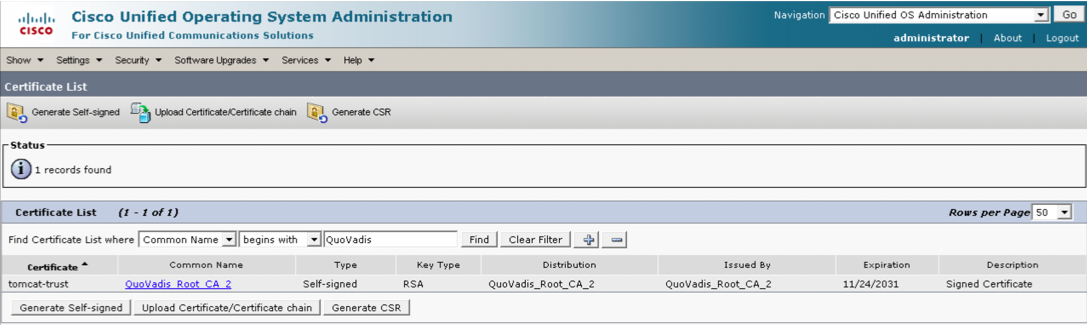
Step 3. Verify QuoVadis_Root_CA_2 is listed as tomcat-trust by finding Certificate where Common Name contains QuoVadis
For Cisco Prime License Manager
For Prime License Manager 10.5
The expired certificate (VeriSign_Class_3_Secure_Server_CA_-_G3) can be deleted from system by applying this COP file (ciscocm.plm-CSCvs64158_remove_sch_cert_C0050-1.k3.cop.sgn). Please review the Readme file for installation instructions.
For Prime License Manager 11.5
The expired certificate (VeriSign_Class_3_Secure_Server_CA_-_G3) can be deleted from system by applying this COP file (ciscocm.plm-CSCvs64158_remove_sch_cert_C0050-1.k3.cop.sgn). Please review the Readme file for installation instructions.
