Implement CA Signed Certificates in a CCE Solution
Available Languages
Download Options
Bias-Free Language
The documentation set for this product strives to use bias-free language. For the purposes of this documentation set, bias-free is defined as language that does not imply discrimination based on age, disability, gender, racial identity, ethnic identity, sexual orientation, socioeconomic status, and intersectionality. Exceptions may be present in the documentation due to language that is hardcoded in the user interfaces of the product software, language used based on RFP documentation, or language that is used by a referenced third-party product. Learn more about how Cisco is using Inclusive Language.
Contents
Introduction
This document describes how to Implement Certificate Authority (CA) Signed certificates in Cisco Contact Center Enterprise (CCE) solution.
Contributed by Anuj Bhatia, Robert Rogier and Ramiro Amaya, Cisco TAC Engineers.
Prerequisites
Requirements
Cisco recommends that you have knowledge of these topics:
- Unified Contact Center Enterprise (UCCE) Release 12.5(1)
- Package Contact Center Enterprise Release 12.5(1)
- Customer Voice Portal (CVP) Release 12.5 (1)
- Cisco Virtualized Voice Browser (VVB)
- Cisco CVP Operations and Administration Console (OAMP)
-
Cisco Unified Intelligence Center (CUIC)
-
Cisco Unified Communication Manager (CUCM)
Components Used
The information in this document is based on these software versions:
- PCCE 12.5(1)
- CVP 12.5(1)
- Cisco VVB 12.5
- Finesss 12.5
- CUIC 12.5
- Windows 2016
The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, ensure that you understand the potential impact of any command.
Background
Certificates are used to ensure that communication is secure with the authentication between clients and servers.
Users can purchase certificates from a CA or they can use self-signed certificates.
Self-signed certificates (as the name implies) are signed by the same entity whose identity they certify, as opposed to be signed by a certificate authority. Self-signed certificates are not considered to be as secure as CA certificates, but they are used by default in many applications.
In the Package Contact Center Enterprise (PCCE) solution version 12.x all components of the solution are controlled by Single Pane of Glass (SPOG), which is hosted in the principal Admin Workstation (AW) server.
Due to Security Management Compliance (SRC) in the PCCE 12.5(1) version, all communication between SPOG and other components in the solution are done via secure HTTP protocol. In UCCE 12.5 communication between components is also done via secure HTTP protocol.
This document explains in details the steps needed to implement CA signed certificates in a CCE Solution for secure HTTP communication. For any other UCCE security considerations, refer to UCCE Security Guidelines. For any additional CVP secure communication different from secure HTTP, refer to the security guidelines in the CVP Configuration guide: CVP Security Guidelines.
Procedure
CCE Windows Based Servers
1. Generate CSR
This procedure explains how to generate a Certificate Signing Request (CSR) from Internet Information Services (IIS) Manager.
Step 1. Log in to Windows and choose Control Panel > Administrative Tools > Internet Information Services (IIS) Manager.
Step 2. In the Connections pane, click the server name. The server Home pane appears.
Step 3. In the IIS area, double-click Server Certificates.
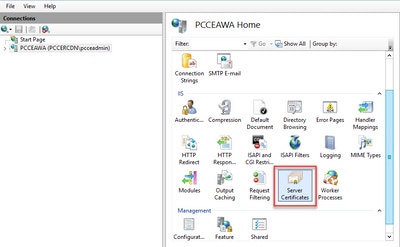
Step 4. In the Actions pane, click Create Certificate Request.
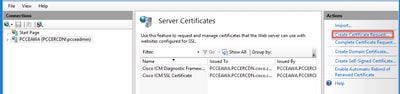
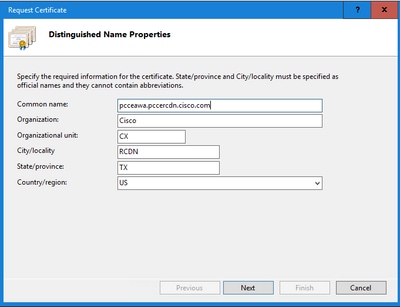
Step 5. In the Request Certificate dialog box, do this:
Specify the required information in the displayed fields and click Next.
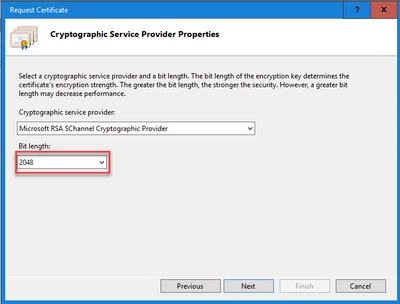
In the Cryptographic service provider drop-down list, leave the default setting.
From the Bit length drop-down list, select 2048.
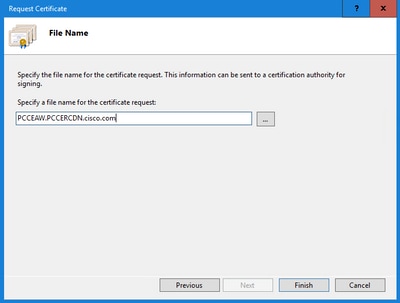
Step 6. Specify a file name for the certificate request and click Finish.
2. Obtain the CA Signed Certificates
Step 1. Sign the certificate on a CA.
Note: Ensure that the certificate template used by the CA includes client and server authentication.
Step 2. Obtain the CA Signed Certificates from your Certificate Authority (Root, Application and Intermediate if any ).
3. Upload the CA Signed Certificates
Step 1. Log in to Windows and choose Control Panel > Administrative Tools > Internet Information Services (IIS) Manager.
Step 2. In the Connections pane, click the server name.
Step 3. In the IIS area, double-click Server Certificates.
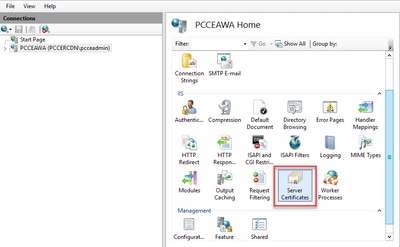
Step 4. In the Actions pane, click Complete Certificate Request.
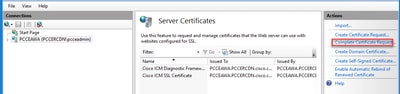
Step 5. In the Complete Certificate Request dialog box, complete these fields:
In the File name which contains the certification authority response field, click the ellipsis ( … ) button.
Browse to the location where signed application certificate is stored and then click Open.
Note: If this is a 2-tier CA implementation and the root certificate is not already in the server certificate store, then the root needs to be uploaded to the Windows store before you import the signed cert. Refer to this document if you need to upload the root CA to the windows store https://learn.microsoft.com/en-us/skype-sdk/sdn/articles/installing-the-trusted-root-certificate.
In the Friendly name field, enter the Fully Qualified Domain Name (FQDN) of the server or any significant name for you. Ensure that the Select a certificate store for the new certificate drop-down remains as Personal.
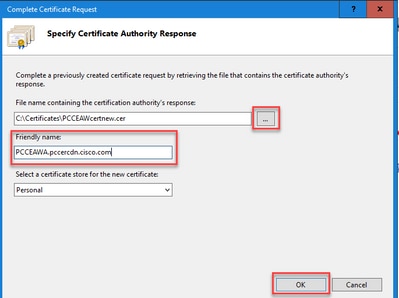
Step 6. Click OK to upload the certificate.
If the certificate upload is successful, the certificate appears in the Server Certificates pane.
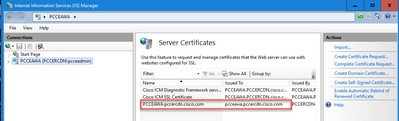
4. Bind the CA-Signed Certificate to IIS
This procedure explains how to bind a CA Signed certificate in the IIS Manager.
Step 1. Log in to Windows and choose Control Panel > Administrative Tools > Internet Information Services (IIS) Manager.
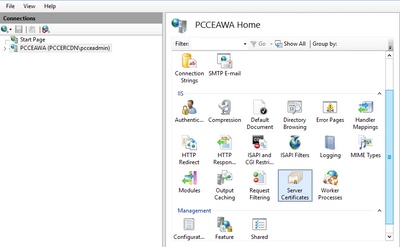
Step 2. In the Connections pane, choose <server_name> > Sites > Default Web Site.
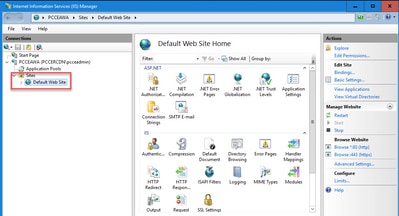
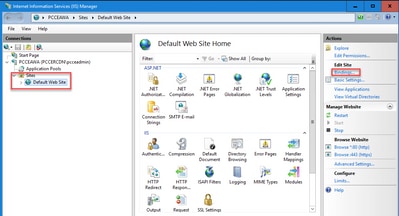
Step 3. In the Actions pane, click Bindings....
Step 4. Click the type https with port 443, and then click Edit....
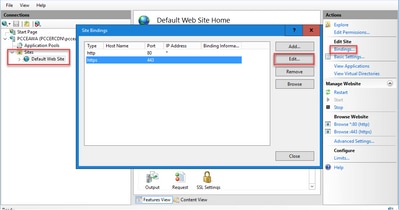
Step 5. From the SSL certificate drop-down list, select the certificate with the same friendly name as given in previous step.
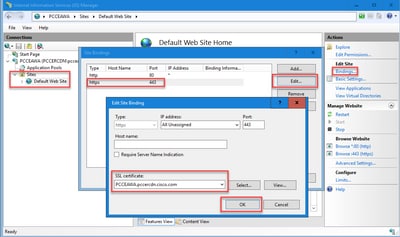
Step 6. Click OK.
Step 7. Navigate to Start > Run > services.msc and restart the IIS Admin Service.
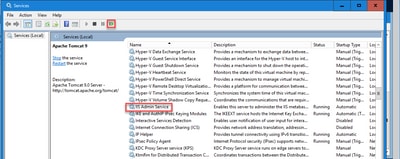
If IIS is restarted successfully, certificate error warnings do not appear when the application is launched.
5. Bind the CA-Signed Certificate to Diagnostic Portico
This procedure explains how to bind a CA Signed Certificate in the Diagnostic Portico.
Step 1. Open the command prompt (Run as Administrator).
Step 2. Navigate to the Diagnostic Portico home folder. Run this command:
cd c:\icm\serviceability\diagnostics\bin
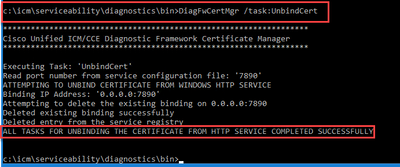
Step 3. Remove the current certificate binding to the Diagnostic Portico. Run this command:
DiagFwCertMgr /task:UnbindCert
Step 4. Open the signed certificate and copy the hash content (without spaces) of the Thumbprint field.
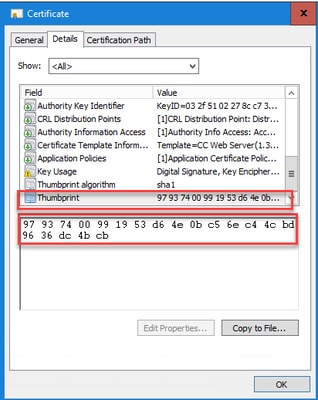
Step 5. Run this command and paste the hash content.
DiagFwCertMgr /task:BindCertFromStore /certhash:<hash_value>
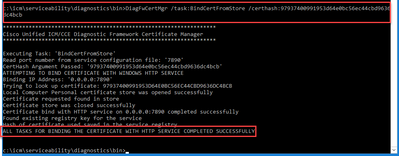
If certificate binding is successful, it displays The certificate binding is VALID message.
Step 6. Validate if the certificate binding was successful. Run this command:
DiagFwCertMgr /task:ValidateCertBinding
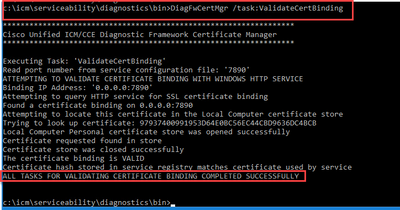
Note: DiagFwCertMgr uses port 7890 by default..
If certificate binding is successful, it displays The certificate binding is VALID message.
Step 7. Restart the Diagnostic Framework service. Run these commands:
net stop DiagFwSvc net start DiagFwSvc
If Diagnostic Framework restarts successfully, certificate error warnings do not appear when the application is launched.
6. Import the Root and Intermediate Certificate into Java Keystore
Caution: Before you begin, you must backup the keystore and run the commands from the java home as an Administrator.
Step 1. Know the java home path to ensure where the java keytool is hosted. There are couple of ways you can find the java home path.
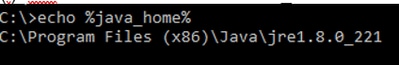
Option 1: CLI command: echo %JAVA_HOME%
Option 2: Manually via Advanced system setting, as shown in the image
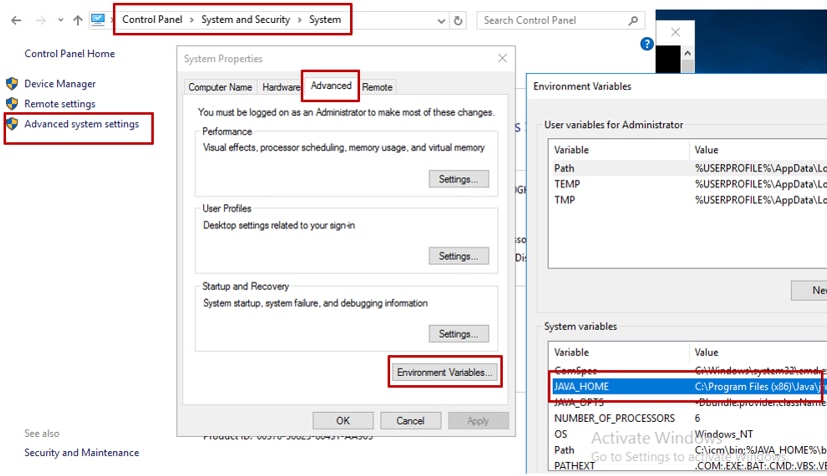
Note: On UCCE 12.5 default path is C:\Program Files (x86)\Java\jre1.8.0_221\bin. However, If you have used the 12.5(1a) installer or have 12.5 ES55 installed (mandatory OpenJDK ES), then use CCE_JAVA_HOME instead of JAVA_HOME since the datastore path has changed with OpenJDK.
Step 2. Backup the cacerts file from the folder C:\Program Files (x86)\Java\jre1.8.0_221\lib\security. You can copy it to another location.
Step 3. Open a command window as Administrator to run the command:
keytool.exe –keystore ./cacerts -import -file <path where the Root, or Intermediate certificate are stored> -alias <Root_name of your CA or Intermediate_name of your CA> -storepass changeit
Note: The specific certificates required depend on the CA that you use to sign your certificates. In a two tier CA, which is typical of public CAs and more secure than internal CAs, then you need to import both the root and intermediate certificates. In a standalone CA with no intermediates, which is generally seen in a lab or more simple internal CA, then you only need to import the root certificate.
CVP Solution
1. Generate Certificates with FQDN
This procedure explains how to generate certificates with FQDN for Web Service Manager (WSM), Voice XML (VXML), Call Server and Operations Management (OAMP) services.
Note: When you install CVP the certificate name only includes the name of the server and not the FQDN therefore, you need to regenerate the certificates.
Caution: Before you begin, you must do this:
1. Obtain the keystore password. Run the command: more %CVP_HOME%\conf\security.properties. You need this password when running the keytool commands.
2. Copy the %CVP_HOME%\conf\security folder to another folder.
3. Open a command window as Administrator to run the commands.
CVP Servers
Step 1. To delete the CVP servers certificates run these commands:
%CVP_HOME%\jre\bin\keytool.exe -storetype JCEKS -keystore %CVP_HOME%\conf\security\.keystore -delete -alias wsm_certificate %CVP_HOME%\jre\bin\keytool.exe -storetype JCEKS -keystore %CVP_HOME%\conf\security\.keystore -delete -alias vxml_certificate %CVP_HOME%\jre\bin\keytool.exe -storetype JCEKS -keystore %CVP_HOME%\conf\security\.keystore -delete -alias callserver_certificate
Enter the keystore password when prompted.
Step 2. To generate the WSM certificate run this command:
%CVP_HOME%\jre\bin\keytool.exe -storetype JCEKS -keystore %CVP_HOME%\conf\security\.keystore -genkeypair -alias wsm_certificate -keysize 2048 -keyalg RSA -validity XXXX
Enter the keystore password when prompted.
Note: By default, the certificates are generated for two years. Use -validity XXXX to set the expiry date when certificates are regenerated, otherwise certificates are valid for 90 days and need to be signed by a CA before this time. For most of these certificates, 3-5 years must be a reasonable validation time.
Here are some standard validity inputs:
|
One Year |
365 |
|
Two Years |
730 |
|
Three Years |
1095 |
|
Four Year |
1460 |
|
Five Years |
1895 |
|
Ten Years |
3650 |
Caution: In 12.5 certificates must be SHA 256, Key Size 2048, and encryption Algorithm RSA, use these parameters to set these values: -keyalg RSA and -keysize 2048. It is important that the CVP keystore commands include the -storetype JCEKS parameter. If this is not done, the certificate, the key, or worse the keystore can become corrupted.
Specify the FQDN of the server, on the question what is your fist and last name?
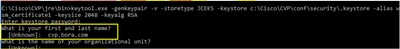
Complete these other questions:
What is the name of your organizational unit?
[Unknown]: <specify OU>
What is the name of your organization?
[Unknown]: <specify the name of the org>
What is the name of your City or Locality?
[Unknown]: <specify the name of the city/locality>
What is the name of your State or Province?
[Unknown]: <specify the name of the state/province>
What is the two-letter country code for this unit?
[Unknown]: <specify two-letter Country code>
Specify yes for the next two inputs.
Step 3. Perform the same steps for vxml_certificate and callserver_certificate:
%CVP_HOME%\jre\bin\keytool.exe -storetype JCEKS -keystore %CVP_HOME%\conf\security\.keystore -genkeypair -alias vxml_certificate -keysize 2048 -keyalg RSA -validity XXXX %CVP_HOME%\jre\bin\keytool.exe -storetype JCEKS -keystore %CVP_HOME%\conf\security\.keystore -genkeypair -alias callserver_certificate -keysize 2048 -keyalg RSA -validity XXXX
CVP Reporting server
Step 1. To delete the WSM and Reporting Server certificates run these commands:
%CVP_HOME%\jre\bin\keytool.exe -storetype JCEKS -keystore %CVP_HOME%\conf\security\.keystore -delete -alias wsm_certificate
%CVP_HOME%\jre\bin\keytool.exe -storetype JCEKS -keystore %CVP_HOME%\conf\security\.keystore -delete -alias callserver_certificate
Enter the keystore password when prompted.
Step 2. To generate the WSM certificate run this command:
%CVP_HOME%\jre\bin\keytool.exe -storetype JCEKS -keystore %CVP_HOME%\conf\security\.keystore -genkeypair -alias wsm_certificate -keysize 2048 -keyalg RSA -validity XXXX
Enter the keystore password when prompted.
Specify the FQDN of the server for the query what is your fist and last name? and continue with the same steps as done with CVP servers.
Step 3. Perform the same steps for callserver_certificate:
%CVP_HOME%\jre\bin\keytool.exe -storetype JCEKS -keystore %CVP_HOME%\conf\security\.keystore -genkeypair -alias callserver_certificate -keysize 2048 -keyalg RSA -validity XXXX
CVP OAMP (UCCE deployment)
Since In the PCCE solution version 12.x all components of the solution are controlled by the SPOG and OAMP is not installed, these steps are only required for a UCCE deployment solution.
Step 1. To delete the WSM and OAMP Server certificates run these commands:
%CVP_HOME%\jre\bin\keytool.exe -storetype JCEKS -keystore %CVP_HOME%\conf\security\.keystore -delete -alias wsm_certificate
%CVP_HOME%\jre\bin\keytool.exe -storetype JCEKS -keystore %CVP_HOME%\conf\security\.keystore -delete -alias oamp_certificate
Enter the keystore password when prompted.
Step 2. To generate the WSM certificate run this command:
%CVP_HOME%\jre\bin\keytool.exe -storetype JCEKS -keystore %CVP_HOME%\conf\security\.keystore -genkeypair -alias wsm_certificate -keysize 2048 -keyalg RSA -validity XXXX
Enter the keystore password when prompted.
Specify the FQDN of the server for the query what is your fist and last name? and continue with the same steps as done with CVP servers.
Step 3. Perform the same steps for oamp_certificate:
%CVP_HOME%\jre\bin\keytool.exe -storetype JCEKS -keystore %CVP_HOME%\conf\security\.keystore -genkeypair -alias oamp_certificate -keysize 2048 -keyalg RSA -validity XXXX
Enter the keystore password when prompted.
2. Generate the CSR
Note: RFC5280 compliant browser requires Subject Alternative Name (SAN) to be included with each certificate. This can be accomplished using the -ext parameter with SAN when generating the CSR.
Subject Alternative Name
The -ext paramenter allows a user to specific extensions. The example shown adds a subject alternative name (SAN) with the fully qualified domain name (FQDN) of the server as well as localhost. Additional SAN fields can be added as comma separated values.
Valid SAN Types are:
ip:192.168.0.1
dns:myserver.mydomain.com
email:name@mydomain.com
For example: -ext san=dns:mycvp.mydomain.com,dns:localhost
CVP Servers
Step 1. Generate the certificate request for the alias. Run this command and save it to a file (for example, wsm_certificate):
%CVP_HOME%\jre\bin\keytool.exe -storetype JCEKS -keystore %CVP_HOME%\conf\security\.keystore -certreq -alias wsm_certificate -file %CVP_HOME%\conf\security\wsm_certificate.csr
Enter the keystore password when prompted.
Step 2. Perform the same steps for vxml_certificate and callserver_certificate:
%CVP_HOME%\jre\bin\keytool.exe -storetype JCEKS -keystore %CVP_HOME%\conf\security\.keystore -certreq -alias vxml_certificate -file %CVP_HOME%\conf\security\vxml_certificate.csr
%CVP_HOME%\jre\bin\keytool.exe -storetype JCEKS -keystore %CVP_HOME%\conf\security\.keystore -certreq -alias callserver_certificate -file %CVP_HOME%\conf\security\callserver_certificate.csr
Enter the keystore password when prompted.
CVP Reporting server
Step 1. Generate the certificate request for the alias. Run this command and save it to a file (for example, oampreport_certificate):
%CVP_HOME%\jre\bin\keytool.exe -storetype JCEKS -keystore %CVP_HOME%\conf\security\.keystore -certreq -alias wsm_certificate -file %CVP_HOME%\conf\security\wsmreport_certificate.csr
Enter the keystore password when prompted.
Step 2. Perform the same steps for the callserver_certificate:
%CVP_HOME%\jre\bin\keytool.exe -storetype JCEKS -keystore %CVP_HOME%\conf\security\.keystore -certreq -alias callserver_certificate -file %CVP_HOME%\conf\security\callserverreport_certificate.csr
Enter the keystore password when prompted.
CVP OAMP (UCCE deployment)
Step 1. Generate the certificate request for the alias. Run this command and save it to a file (for example, oamp_certificate):
%CVP_HOME%\jre\bin\keytool.exe -storetype JCEKS -keystore %CVP_HOME%\conf\security\.keystore -certreq -alias oamp_certificate -file %CVP_HOME%\conf\security\oamp_certificate.csr -ext san=dns:mycvp.mydomain.com,dns:localhost
Ensure to replace "mycvp.mydomain.com" with your OAMP FQDN.
Enter the keystore password when prompted.
Step 2. Perform the same steps for wsm_certificate:
%CVP_HOME%\jre\bin\keytool.exe -storetype JCEKS -keystore %CVP_HOME%\conf\security\.keystore -certreq -alias wsm_certificate -file %CVP_HOME%\conf\security\wsm_certificate.csr
Enter the keystore password when prompted.
3. Obtain the CA Signed Certificates
Step 1. Sign the certificates on a CA (WSM, Callserver and VXML server for he CVP server; WSM and OAMP for the CVP OAMP server, and WSM and Callserver for the Reporting server).
Step 2. Download the application certificates and the root certificate from the CA authority.
Step 3. Copy the root certificate and the CA signed certificates in to the folder %CVP_HOME%\conf\security\ of each server.
4. Import the CA Signed Certificates
Apply these steps to all servers of the CVP solution. Only the certificates for components on that server need to have the CA signed certificate imported.
Step 1. Import the root certificate. Run this command:
%CVP_HOME%\jre\bin\keytool.exe -storetype JCEKS -keystore %CVP_HOME%\conf\security\.keystore -import -v -trustcacerts -alias root -file %CVP_HOME%\conf\security\<filename_of_root_cer>
Enter the keystore password when prompted. At Trust this certificate prompt, type Yes.
If there is an intermediate certificate, run this command:
%CVP_HOME%\jre\bin\keytool.exe -storetype JCEKS -keystore %CVP_HOME%\conf\security\.keystore -import -v -trustcacerts -alias intermediate_ca -file %CVP_HOME%\conf\security\<filename_of_intermediate_cer>
Enter the keystore password when prompted. At Trust this certificate prompt, type Yes.
Step 2. Import the CA Signed WSM for that server certificate ( CVP, Reporting and OAMP). Run this command:
%CVP_HOME%\jre\bin\keytool.exe -storetype JCEKS -keystore %CVP_HOME%\conf\security\.keystore -import -v -trustcacerts -alias wsm_certificate -file %CVP_HOME%\conf\security\<filename_of_wsm_CA_cer>.
Enter the keystore password when prompted. At Trust this certificate prompt, type Yes.
Step 3. In the CVP Servers and the Reporting servers import the Callserver CA Signed certificate. Run this command:
%CVP_HOME%\jre\bin\keytool.exe -storetype JCEKS -keystore %CVP_HOME%\conf\security\.keystore -import -v -trustcacerts -alias callserver_certificate -file %CVP_HOME%\conf\security\<filename_of_callserver_CA_cer>.
Enter the keystore password when prompted. At Trust this certificate prompt, type Yes.
Step 4. In the CVP Servers import the VXML server CA Signed certificate. Run this command:
%CVP_HOME%\jre\bin\keytool.exe -storetype JCEKS -keystore %CVP_HOME%\conf\security\.keystore -import -v -trustcacerts -alias vxml_certificate -file %CVP_HOME%\conf\security\<filename_of_vxml_CA_cer>.
Step 5. In the CVP OAMP server ( for UCCE only) import the OAMP server CA Signed certificate. Run this command:
%CVP_HOME%\jre\bin\keytool.exe -storetype JCEKS -keystore %CVP_HOME%\conf\security\.keystore -import -v -trustcacerts -alias oamp_certificate -file %CVP_HOME%\conf\security\<filename_of_oamp_CA_cer>.
Step 6. Reboot the servers.
Note: In UCCE deployment, ensure to add the servers ( Reporting, CVP Server, and so on.) in CVP OAMP with the FQDN that you provided when you genarated the CSR.
VOS Servers
1. Generate CSR Certificate
This procedure explains how to generate Tomcat CSR certificate from a Cisco Voice Operating System (VOS) based platforms. This process is applicable for all VOS based applications such as:
- CUCM
- Finesse
- CUIC \ Live Data (LD) \Identity Server(IDS)
- Cloud Connect
- Cisco VVB
Step 1. Navigate to Cisco Unified Communications Operating System Administration page: https://FQDN:<8443 or 443>/cmplatform.
Step 2. Navigate to Security > Certificate Management and select Generate CSR.
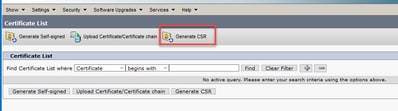
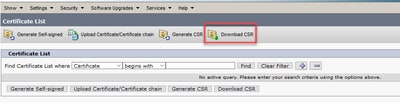
Step 3. After the CSR certificate is generated, close the window and select Download CSR.
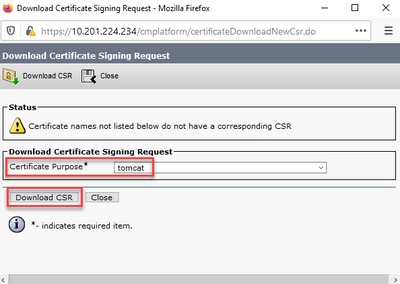
Step 4. Ensure that the Certificate purpose is tomcat and click Download CSR.
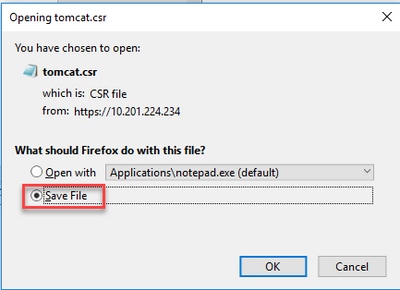
Step 5. Click Save File. The file is saved on the Download folder.
2. Obtain the CA Signed Certificates
Step 1. Sign the tomcat certificate exported on a CA.
Step 2. Download the application and the root certificated from the CA authority.
3. Upload the Application and Root Certificates
Step 1. Navigate to Cisco Unified Communications Operating System Administration page: https://FQDN:<8443 or 443>/cmplatform.
Step 2. Navigate to Security > Certificate Management and select Upload Certificate/Certificate chain.
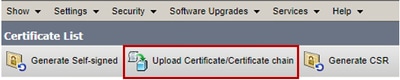
Step 3. On the Upload certificate/Certificate chain window select tomcat-trust in certificate purpose field and upload the Root certificate.
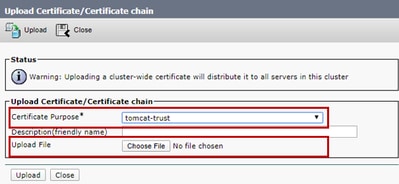
Step 4. Upload an intermediate certificate (if any ) as a tomcat-trust.
Step 5. On the Upload certificate/Certificate chain window select now tomcat in the Certificate Purpose field and upload the application CA signed certificate.
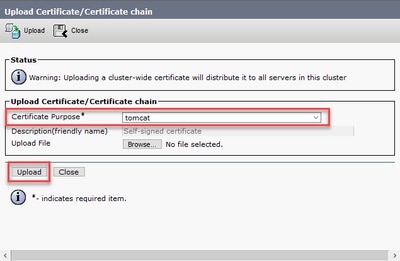
Step 6. Reboot the server.
Verify
After you reboot the server, execute these steps to verify the CA signed implementation:
Step 1. Open a Web Browser and clear the cache.
Step 2. Close and Open the browser again.
Now you must see the certificate switch to begin the CA signed certificate and the indication in the browser window that the certificate is self-signed and therefore not trusted, must go away.
Troubleshoot
There are no steps to troubleshoot the implementation of the CA Signed certificates in this guide.
Related Information
- CVP Configuration Guide: CVP Configuration Guide - Security
- UCCE Configuration Guide: UCCE Configuration Guide - Security
- PCCE Administration Guide: PCE Administration Guide - Security
- UCCE Self-Signed Certificates: Exchange UCCE Self-Signed Certificates
- PCCE Self-Signed Certificates: Exchange PCCE Self-Signed Certificates
- Install and Migrate to OpenJDK in CCE 12.5(1): CCE OpenJDK Migration
- Install and Migrate to OpenJDK in CVP 12.5(1): CVP OpenJDK Migration
Revision History
| Revision | Publish Date | Comments |
|---|---|---|
3.0 |
27-Jul-2023 |
Revision 13 |
2.0 |
21-Sep-2022 |
Revision 12 |
1.0 |
30-Aug-2021 |
Initial Release |
Contributed by Cisco Engineers
- Anuj BhatiaCisco TAC Engineer
- Robert RogierCisco TAC Engineer
- Ramiro AmayaCisco TAC Engineer
Contact Cisco
- Open a Support Case

- (Requires a Cisco Service Contract)
 Feedback
Feedback