Introduction
This document describes about the latest Security enhancements added with Unified Contact Center Enterprise (UCCE) 12.5.
Prerequisites
- UCCE
- Open Secure Sockets Layer (SSL)
Requirements
Cisco recommends that you have knowledge of these topics:
Components Used
The information in this document is based on these software and hardware versions:
- UCCE 12.5
- OpenSSL (64 bit) for windows
The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, ensure that you understand the potential impact of any command.
Background Information
Cisco Security Control Framework (SCF) : The Collaboration Security Control Framework provides the design and implementation guidelines for building secure and reliable collaboration infrastructures. These infrastructures are resilient to both well-known and new forms of attacks. Reference Security Guide for Cisco Unified ICM/Contact Center Enterprise, Release 12.5 .
As part of Cisco's SCF effort additional security enhancements are added for UCCE 12.5. This document outlines these enhancements.
Verification of Downloaded ISO
In order to validate the downloaded ISO signed by Cisco as well as ensure that it is authorized, steps are:
1. Download and Install the OpenSSL. Search for software "openssl softpedia".

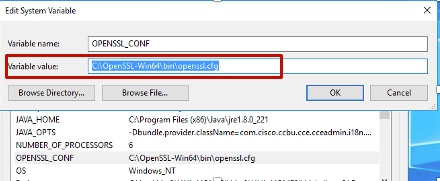
2. Confirm the path (this is set by default , but still good to verify). In Windows 10, goto System Propeties, select Environment Variables.
3. Files needed for ISO verification

4. Run the OpenSSL tool from command line.
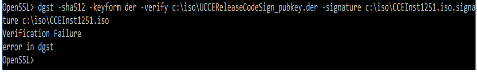
5. Run the command
dgst -sha512 -keyform der -verify <public Key.der> -signature <ISO image.iso.signature> <ISO Image>
6. In the event of failure, command line shows error as shown in the image
Use Certificates with SHA-256 and Key Size 2048 Bits
Logs report error in the event of identifying non-complaint certificates (i.e not meeting the SHA-256 and/or keysize 2048 bits requirement.)
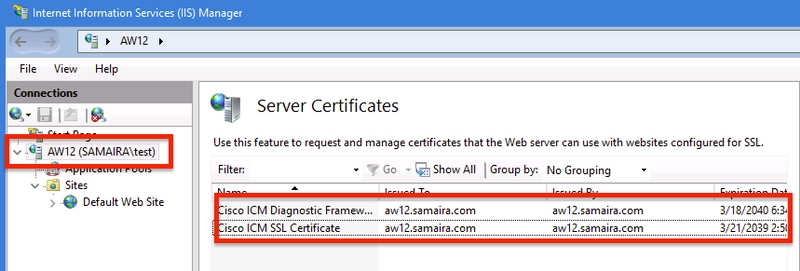
There are two important certificates from UCCE's perspective:
- Cisco ICM Diagnostic Framework service certificate
- Cisco ICM SSL Certificate
The certificates can be reviewed in the Internet Information Services (IIS) Manager option of windows server.
For Self-signed certificates (either for Diagnose Portico or Web Setup) , error line reported is:
Re-generating Cisco ICM SSL Certificate with SHA-256 and key size '2048' and will be binded with port 443.
SSLUtil Tool
a. In order to regenerate self-signed certificates (for WebSetup/CCEAdmin page) use SSLUtil tool (from location C:\icm\bin).
b. Select Uninstall to delete the current "Cisco ICM SSL Certificate".
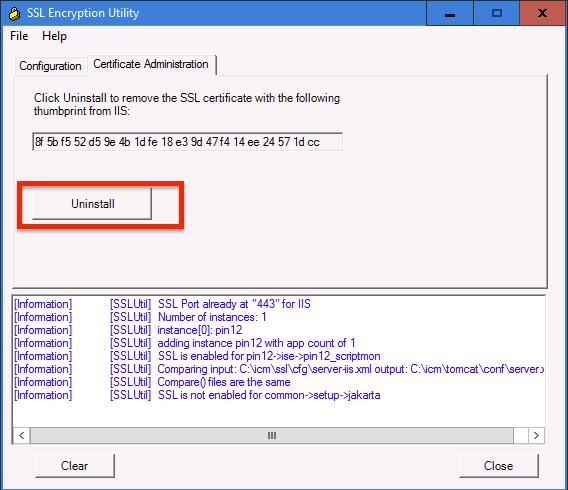
c. Next select Install in SSLUtil tool and once the process completes , notice the certificate created now include SHA-256 and keysize '2048' bits.

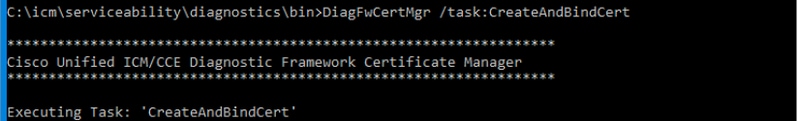
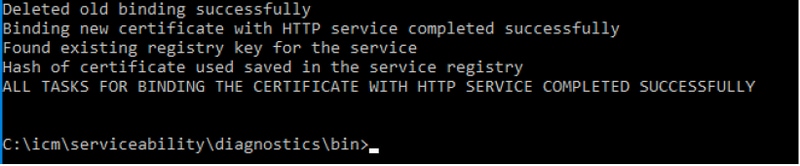
DiagFwCertMgr Command
In order to regenerate a self-signed certificate for Cisco ICM Diagnostic Framework service certificate, use command line "DiagFwCertMgr", as shown in the image:
Data Protection Tool
1. CCEDataProtectTool is used to encrypt and decrypt sensitive information that the Windows registry stores in it. Post upgrade to SQL 12.5 , value store in the SQLLogin registry need to be reconfigured with CCEDataProtectTool. Only administrator,domain user with administrattive rights,or a local administrator can run this tool.
2. This tool can be used to view,configure,edit,remove encrypted value store in SQLLogin registry.
3. Tool is found in location;
<Install Directory>:\icm\bin\CCEDataProtectTool.exe
4. Navigate to location and double click CCEDataProtectTool.exe.
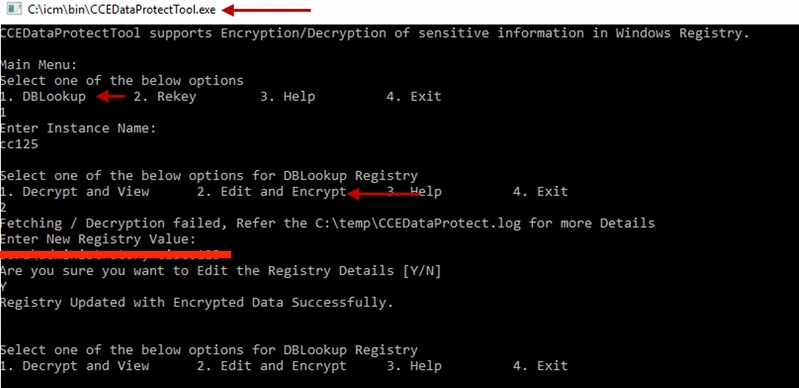
5. In order to encrypt , press 1 for DBLookup, enter Instance Name. Next, press 2 to select "Edit and Encrypt"
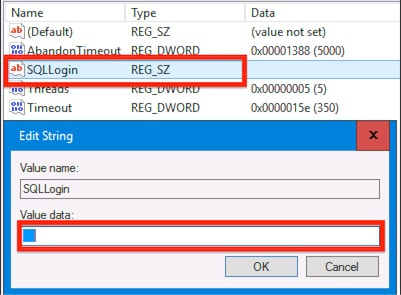
6. Navigate to registry location and review String Value SQLLogin looks blank , as shown in the image :
HKEY_LOCAL_MACHINE\SOFTWARE\Cisco Systems, Inc.\ICM\pin12\RouterA\Router\CurrentVersion\Configuration\Database
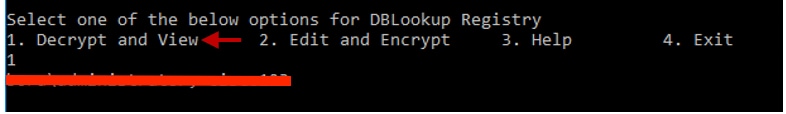
7. In case of need to review the encrypted value; while command line of CCEDataProtectTool , select press 1 for "Decrypt and View", as shown in the image;
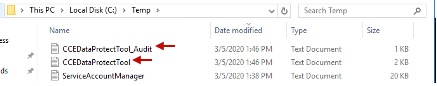
8. Any logs for this tool can be found in location;
<Install Directory>:\temp
Audit logs filename : CCEDataProtectTool_Audit
CCEDataProtectTool logs : CCEDataProtectTool