Field Notice: FN - 64080 - IPS Sensors - Software Upgrade Required in Order to Enable SHA-2 Support For IPS Signature Updates - Software Upgrade Recommended
Available Languages
Notice
THIS FIELD NOTICE IS PROVIDED ON AN "AS IS" BASIS AND DOES NOT IMPLY ANY KIND OF GUARANTEE OR WARRANTY, INCLUDING THE WARRANTY OF MERCHANTABILITY. YOUR USE OF THE INFORMATION ON THE FIELD NOTICE OR MATERIALS LINKED FROM THE FIELD NOTICE IS AT YOUR OWN RISK. CISCO RESERVES THE RIGHT TO CHANGE OR UPDATE THIS FIELD NOTICE AT ANY TIME.
Revision History
| Revision | Publish Date | Comments |
|---|---|---|
1.0 |
01-Mar-16 |
Initial Release |
10.0 |
11-Oct-17 |
Migration to new field notice system |
10.1 |
22-Jan-21 |
Updated the Defect Information Table |
Products Affected
| Affected OS Type | Affected Software Product | Affected Release | Affected Release Number | Comments |
|---|---|---|---|---|
NON-IOS |
Intrusion Prevention System (IPS) System Software |
E4 |
7.0(2)E4,7.0(3)E4,7.0(4)E4,7.0(5)E4,7.0(5a)E4,7.0(6)E4,7.0(7)E4,7.0(8)E4,7.0(9)E4,7.2(1)E4,7.2(2)E4,7.3(1)E4,7.3(2)E4,7.3(3)E4,7.3(4)E4,7.3(5)E4,7.1(1)E4,7.1(10)E4,7.1(11)E4,7.1(2)E4,7.1(3)E4,7.1(4)E4,7.1(5)E4,7.1(6)E4,7.1(7)E4,7.1(8)E4,7.1(9)E4 |
|
NON-IOS |
Intrusion Prevention System (IPS) System Software |
E3 |
6.2(1)E3,6.2(2)E3 |
Defect Information
| Defect ID | Headline |
|---|---|
| CSCvf34445 | There were no defects filed with this field notice at the time of publication. |
Problem Description
Customers that subscribe to automatic Intrusion Prevention System (IPS) signature/sensor updates are required to upgrade their IPS software. This upgrade is required in order to provide compatibility with the SHA-2 certificate that is deployed on the Cisco update servers.
Customers that use Cisco Security Manager (CSM) in order to provide automatic IPS signature/sensor updates might need to replace their SHA-1 Contact URL certificate with the new SHA-2 certificate from the same Contact URL as used previously.
Background
Customers that use IPS depend on continuous signature updates from Cisco for up-to-date protection of their network.
Customers that subscribe to automatic IPS signature/sensor updates are required to upgrade their IPS software in order to provide compatibility with the SHA-2 certificates that are deployed on the Cisco update servers. This change affects IPS sensors that run 6.2, 7.0, 7.1, 7.2, and 7.3 code versions configured for the Auto Update feature. IPS software versions 7.1(11)E4 or 7.3(5)E4 provide compatibility with the SHA-2 certificates on the Cisco update servers.
Customers that use any IPS software versions earlier than 7.3(4)E4 must upgrade before February 12, 2016 in order to provide compatibility with the previous Cisco update servers.
Customers that use IPS software version 7.3(4)E4 must upgrade before March 18, 2016 in order to provide compatibility with the new Cisco update servers.
This change only affects downloads from the Cisco server. Customers who use Auto Update with a remote server instead of the Cisco server will continue to receive updates as usual. Customers that download signature update packages with a web browser are also unaffected by this change.
Problem Symptom
Customers that do not upgrade their IPS software might not receive automatic IPS signature updates and could potentially be vulnerable to security threats.
Workaround/Solution
Use one of these procedures in order to upgrade the IPS software.
Note: The latest versions of IPS software require a DNS server or HTTP proxy configured in order to support automatic signature updates from Cisco.
For customers that use IPS 6.2 or IPS 7.0 - Manually download signature update packages with CSM or a web browser. The Cisco server auto-updates for these older versions will no longer work once the SHA-2 certificates are deployed.
For customers that use IPS 7.1 - Upgrade to version 7.1(11)E4 or later (see the upgrade procedures in this section).
For customers that use IPS 7.2 or IPS 7.3 - Upgrade to version 7.3(4)E4 or later (see the upgrade procedures in this section).
Procedure #1: Upgrade the IPS Software with the CLI
For example, in order to install the 7.1(11)E4 release for the IPS 4510 with the CLI, complete these steps:
- Download the model appropriate package file (for example, IPS-4510-K9-7.1-11-E4.pkg) to a local server.
- Log into the CLI with an account that has administrator privileges.
- Type this command in order to enter Configuration mode:
configure terminal
- Type this command in order to upgrade the sensor:
sensor(config)# upgrade [URL]/IPS-4510-K9-7.1-11-E4.pkg
In this example, [URL] is a uniform resource locator that points to where the package is located. For example, in order to retrieve the IPS 4510 update via FTP, type this command:
sensor(config)# upgrade ftp://username@ip-address//directory/IPS-4510-K9-7.1-11-E4.pkg
The available transport methods are SCP, FTP, HTTP, or HTTPS.
- Enter the sensor password when prompted.
- In order to complete the upgrade, type yes when prompted. The sensor reboots and applies the changes.
In order to determine if 7.1(11)E4 has successfully been installed on the sensor, log into the CLI and type show version at the command prompt. The sensor reports the version as 7.1(11)E4 and the Upgrade History should include IPS-4510-K9-7.1-11-E4.pkg.
Note: You must run these versions in order to upgrade these platforms to IPS 7.1(11)E4:
- For the IPS 42XX and SSM series sensors, you must run IPS 6.0(6) or later.
- For the IPS 43XX series sensors and the ASA 5500-X IPS SSP series, you must run IPS 7.1(3)E4 or later.
- For the IPS 45XX series sensors, you must run IPS 7.1(4)E4 or later.
- For the ASA 5585-X IPS SSP series, you must run IPS 7.1(1)E4 or later.
Procedure #2: Update the IPS Software with IDM/IME
- Choose Configuration > Sensor Management > Update Sensor.
- Click the appropriate upgrade package location and transfer method, if needed. For example, if you will install the upgrade package from the system where you run IDM/IME, click the Update is located on this client radio button and choose the Local File Path of the upgrade package as shown here:
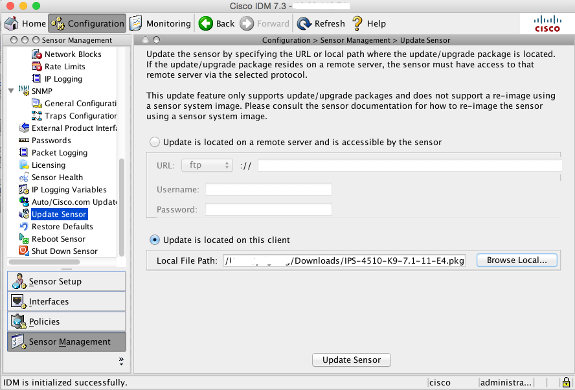
- Click Update Sensor in order to apply the update to the sensor.
Procedure #3: Update the IPS Signatures from a Local Server
You can configure automatic signature updates for an IPS device from a local FTP or SCP server.
Configuration of automatic signature updates from a local server requires:
- A local server that runs an FTP or SCP server in order to host the signature update files.
- The management interface on the IPS device must be able to use an FTP or SCP connection to the server.
- A directory on the server to contain signature update files.
- A user account on the server with read access to the signature update files.
This example shows how to use the CLI in order to configure signature updates from an SCP server.
Note: In this example, the server that hosts the signature update files is at 10.89.143.198. A user named 'service' has access to the update files on the server. The update files are located in the /home/service/signature_updates directory.
- Add the server that will host the signature update files as an SSH trusted host. From the CLI on the sensor, enter these commands:
sensor# configure terminal sensor(config)# ssh host-key 10.89.143.198 RSA Key: RSA Bubble Babble is xitoz-pimiz-nyrus-sarun-nekup-hufot-lirom-nitek-sipib-nukyz-noxox RSA public key modulus length: 2048 Would you like to add this to the known hosts table for this host?[yes]: sensor(config)# exit
- Enable automatic signature updates from the local server from the sensor's CLI, as follows:
sensor# configure terminal sensor(config)# service host sensor(config-hos)# auto-upgrade sensor(config-hos-aut)# user-server enabled sensor(config-hos-aut-ena)# directory /home/service/signature_updates sensor(config-hos-aut-ena)# file-copy-protocol scp sensor(config-hos-aut-ena)# ip-address 10.89.143.198 sensor(config-hos-aut-ena)# user-name service sensor(config-hos-aut-ena)# password Enter password[]: ******** Re-enter password: ******** sensor(config-hos-aut-ena)# show settings enabled ----------------------------------------------- schedule-option ----------------------------------------------- periodic-schedule ----------------------------------------------- start-time: 00:00:00 <defaulted> interval: 24 hours <defaulted> ----------------------------------------------- ----------------------------------------------- ip-address: 10.89.143.198 directory: /home/service/signature_updates user-name: service password: <hidden> file-copy-protocol: scp default: scp ---------------------------------------------- sensor(config-hos-aut-ena)# sensor(config-hos-aut-ena)# exit sensor(config-hos-aut)# exit sensor(config-hos)# exit Apply Changes?[yes]: yes sensor(config)# exit
- The sensor checks the server for a new update file in accordance with the configured schedule. If the sensor runs IPS version 7.3 or later, enter the autoupdatenow command in order to initiate the signature update process as follows:
sensor# autoupdatenow Warning: Executing this command will perform an auto-upgrade on the sensor immediately. Before executing this command, you must have a valid license to apply the Signature AutoUpdates and auto-upgrade settings configured. After executing this command please disable user-server/cisco-server inside 'auto-upgrade' settings, if you don't want scheduled auto-updates Continue? []: yes Automatic Update for the sensor has been executed. Use 'show statistics host' command to check the result of auto-update. Please disable user-server/cisco-server in auto-upgrade settings, if you don't want scheduled auto-updates - Verify the update. From the CLI, enter the show statistics host command as shown in this example:
sensor# show statistics host | begin Auto Auto Update Statistics lastDirectoryReadAttempt = 20:13:02 UTC Thu Jan 07 2016 = Read directory: scp://service@10.89.143.198//./home/service/signature_updates/ = Success lastDownloadAttempt = 20:13:06 UTC Thu Jan 07 2016 = Download: scp://service@10.89.143.198//./home/service/signature_updates/IPS-sig-S879-req-E4.pkg = Success lastInstallAttempt = 20:14:49 UTC Thu Jan 07 2016 = IPS-sig-S879-req-E4: Update completed successfully = Success nextAttempt = 00:00:01 UTC Fri Jan 08 2016 Auxiliary Processors Installed
For More Information
If you require further assistance, or if you have any further questions regarding this field notice, please contact the Cisco Systems Technical Assistance Center (TAC) by one of the following methods:
Receive Email Notification For New Field Notices
Cisco Notification Service—Set up a profile to receive email updates about reliability, safety, network security, and end-of-sale issues for the Cisco products you specify.
Unleash the Power of TAC's Virtual Assistance
 Feedback
Feedback