Field Notice: FN72552 - Identity Services Engine: Connections to Microsoft Endpoint Configuration Manager Might Fail After the March 14, 2023 Microsoft Security Patch Is Installed - Workaround Provided
Available Languages
Notice
THIS FIELD NOTICE IS PROVIDED ON AN "AS IS" BASIS AND DOES NOT IMPLY ANY KIND OF GUARANTEE OR WARRANTY, INCLUDING THE WARRANTY OF MERCHANTABILITY. YOUR USE OF THE INFORMATION ON THE FIELD NOTICE OR MATERIALS LINKED FROM THE FIELD NOTICE IS AT YOUR OWN RISK. CISCO RESERVES THE RIGHT TO CHANGE OR UPDATE THIS FIELD NOTICE AT ANY TIME.
Products Affected
| Affected Software Product | Affected Release | Affected Release Number | Comments |
|---|---|---|---|
| Identity Services Engine System Software | 2 | 2.0, 2.0.1, 2.1.0, 2.2.0, 2.2.1, 2.3.0, 2.4.0, 2.6.0, 2.7.0 | |
| Identity Services Engine System Software | 3 | 3.0, 3.0.0, 3.1.0, 3.2.0 |
Defect Information
| Defect ID | Headline |
| CSCwe57764 | MDM - Connection to Microsoft SCCM fails after Windows DCOM Server Hardening for CVE-2021-26414 |
Problem Description
For all wired, wireless, and VPN deployment scenarios, the Cisco Identity Services Engine (ISE) for Mobile Device Management (MDM) solution deployments might no longer be able to connect and obtain compliance information from the Microsoft Endpoint Configuration Manager (MECM) after the March 14, 2023 Microsoft security patch is installed.
Background
Cisco ISE uses a Windows Management Instrumentation (WMI) query to obtain endpoint registration and compliance status from the MECM server. This query requires authentication with the MECM server. Microsoft uses Distributed Component Object Model (DCOM) for communication between software components of networked devices.
As part of security hardening, the Microsoft security patch update released on March 14, 2023 will deprecate the low level authentication that is required by Cisco ISE. For MDM solution deployments only, this causes the connection to the MECM server to fail and compliance information will not be obtained. The security hardening changes are enabled by default and there is no ability to disable the security hardening changes after installation of the Microsoft security patch.
ISE posture functionality with the Cisco AnyConnect Secure Mobility Client is not affected by the issue described in this field notice.
Additional information for the March 14, 2023 Microsoft security patch update can be found in Manage changes for Windows DCOM Server Security Feature Bypass.
Note: MECM was previously known as System Center Configuration Manager (SCCM).
Problem Symptom
After the March 14, 2023 Microsoft security patch is installed, the Cisco ISE MDM solution will not be able to retrieve endpoint attributes and compliance information.
The integration status for on-prem MECM is shown as "Enabled" (ISE > Administration > Network Resources > External MDM). Alarms that state "External MDM Server Connection Failure" are shown in ISE.
Using "Test Connection" in the ISE MDM server settings results in an error that states "Connection to server failed with: MDM Server API error" and a message that indicates "Access is denied" and "Configure the Windows Machine for DCOM Access" is displayed.
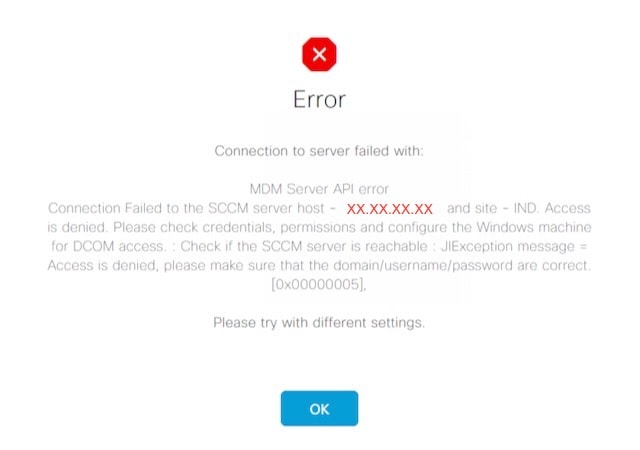
Note: This error message might appear for other conditions not related to the issue described in this field notice.
Workaround/Solution
Solution
To address this issue, Cisco strongly recommends upgrading to one of the following Cisco ISE releases:
- 3.0 Patch 8
- 3.1 Patch 7 or later
- 3.2 Patch 2 or later
Note: For Cisco ISE 2.x releases, there will not be a fixed release or Hot Patch. Upgrade to one of the appropriate 3.0, 3.1, or 3.2 releases.
Workaround
Cisco recommends to temporarily disable the March 14, 2023, Microsoft Windows Server update in order to maintain functionality of the Cisco ISE MECM integration for the MDM solution.
The Microsoft security update can be identified by this title.
“[MSRC] Cumulative Security for Windows xxxxxxx – KB####### - 2023.03 B”
Note: Microsoft Windows version and KB number will vary for each Microsoft OS version.
If the March 14, 2023, update is already installed on the Microsoft Windows Server, Cisco recommends to temporarily revert the update by uninstalling the March 14, 2023 update. Follow the Microsoft published procedure to revert the update.
If the Cisco ISE MECM integration for the MDM solution does not function after the Microsoft update is uninstalled, refer to the "Registry setting to enable or disable the hardening changes" section of the Microsoft article Manage changes for Windows DCOM Server Security Feature Bypass to disable the hardening changes. The registry setting must be set to 0x00000000 for the Cisco ISE MECM integration to function correctly.
Revision History
| Version | Description | Section | Date |
| 3.1 | Updated the list of fixed software releases. | Workaround/Solution | 2023-DEC-21 |
| 3.0 | Updated the title and the solution. | Title, Workaround/Solution | 2023-JUN-01 |
| 2.0 | Updated the Workaround/Solution Section | Workaround/Solution | 2023-MAR-15 |
| 1.0 | Initial Release | — | 2023-MAR-09 |
For More Information
For further assistance or for more information about this field notice, contact the Cisco Technical Assistance Center (TAC) using one of the following methods:
Receive Email Notification About New Field Notices
To receive email updates about Field Notices (reliability and safety issues), Security Advisories (network security issues), and end-of-life announcements for specific Cisco products, set up a profile in My Notifications
Contact Cisco
- Open a Support Case

- (Requires a Cisco Service Contract)
This Document Applies to These Products
Unleash the Power of TAC's Virtual Assistance
 Feedback
Feedback