Field Notice: FN74227 - Cisco Identity Services Engine: Authentication and Certificate-Based Logins Will Fail Due to Microsoft Intune Security Identifier Changes - Software Upgrade Recommended
Available Languages
Notice
THIS FIELD NOTICE IS PROVIDED ON AN "AS IS" BASIS AND DOES NOT IMPLY ANY KIND OF GUARANTEE OR WARRANTY, INCLUDING THE WARRANTY OF MERCHANTABILITY. YOUR USE OF THE INFORMATION ON THE FIELD NOTICE OR MATERIALS LINKED FROM THE FIELD NOTICE IS AT YOUR OWN RISK. CISCO RESERVES THE RIGHT TO CHANGE OR UPDATE THIS FIELD NOTICE AT ANY TIME.
Products Affected
| Affected Software Product | Affected Release | Affected Release Number | Comments |
|---|---|---|---|
| Identity Services Engine System Software | 3 | 3.1.0, 3.2.0, 3.3.0, 3.4.0 | 3.1.0: For ISE release 3.1 Patch 9 and earlier 3.2.0: For ISE release 3.2 Patch 6 and earlier 3.3.0: For ISE release 3.3 Patch 3 and earlier 3.4.0: For ISE release 3.4 unpatched |
Defect Information
| Defect ID | Headline |
| CSCwk73785 | Certificate Based Authentication with SID - Security Identifiers |
Problem Description
Cisco Identity Services Engine (ISE) supports certificate-based authentication with endpoints. Recent communication from Microsoft indicates that there have been changes in the Windows behavior that mitigates certificate spoofing. These changes will impact Cisco ISE authentication capabilities. Certificate-based logins will fail for users or devices on the local Active Directory and integration with Microsoft Intune Mobile Device Management (MDM) when Windows enforces strong mapping on February 11, 2025.
Background
As part of the Windows update on May 10, 2022 (KB5014754: Certificate-based authentication changes on Windows domain controllers), Active Directory Kerberos Key Distribution (KDC) behavior in Windows Server 2008 and later versions changed to prevent certificate spoofing vulnerabilities that could allow privilege escalation attacks. This change requires that a certificate for a user or computer object be strongly mapped to Active Directory.
To do this, Microsoft Intune adds security identifiers (SIDs) to the Subject Alternative Name (SAN) Uniform Resource Identifier (URI) field of certificates using the OnPremisesSecurityIdentifer variable. SIDs can be added to the certificate in formats that are mentioned in the Additional Information section of this field notice when users or devices sync from on-premises Active Directory in the following cases:
- To obtain a new certificate
- To go through certificate renewal
- When assigned a new "Network Device Enrollment Service (NDES)" / "Simple Certificate Enrollment Protocol (SCEP)" certificate configuration profile
If strong mapping is not configured, certificate-based logins for users or devices on the local Active Directory will fail when Windows enforces strong mapping on Feb 11, 2025.
For more information, see Support tip: Implementing strong mapping in Microsoft Intune certificates.
The change in Windows behavior will impact Cisco ISE customers in following use cases:
Certificate attribute lookups against external identity stores: When endpoints authenticate using certificate-based EAP authentication, Cisco ISE allows certificate attributes to be matched using Certificate Authentication Profiles. After the changes introduced by Microsoft (KB5014754), endpoint authentication may fail when SAN is used for identity lookups against Active Directory.
The following is an example of an affected configuration:
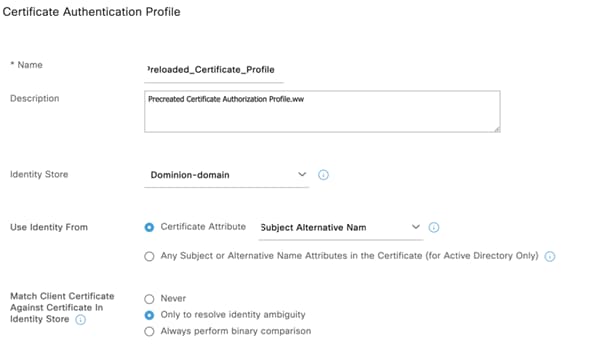
Cisco ISE and Intune Integration: When endpoints connect to a Wi-Fi or wired network through certificate-based authentication, Cisco ISE MDM API version 3 uses globally unique identifiers (GUIDs) under the Common Name or SAN URI of the certificate to obtain compliance information. If users and endpoints obtain new certificates with SIDs, this compliance retrieval may fail with the changes mentioned in Microsoft’s article KB5014754.
The following is an example of an affected configuration (found in External MDM > MDM/UEM Integrations within the ISE user interface):
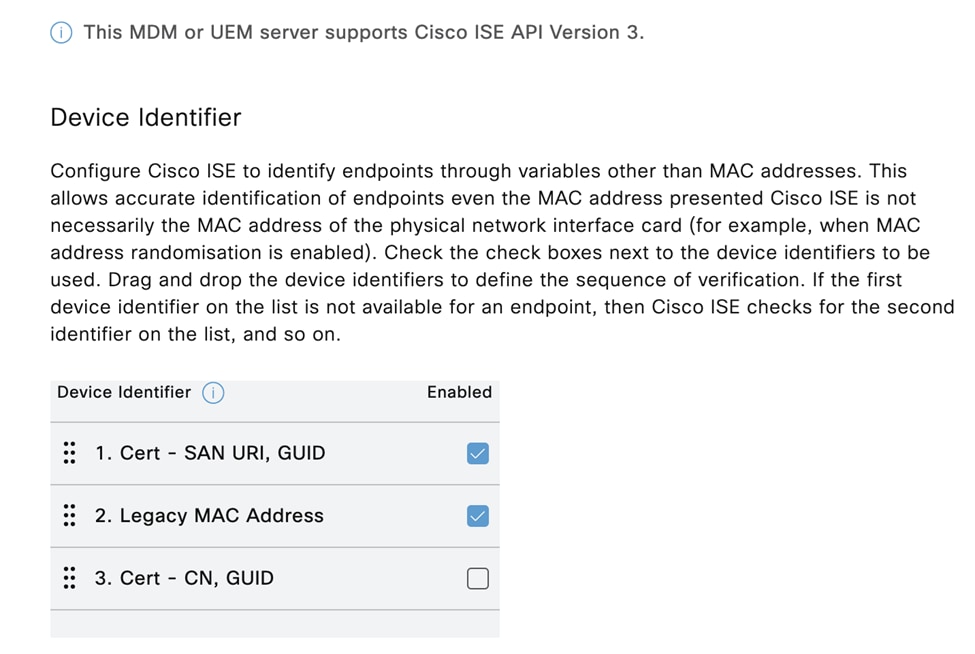
For more information on affected SAN formats, see the Additional Information section of this field notice.
Problem Symptom
The following error and log messages may be observed for Cisco ISE and Intune Integration:
SAN URI with SID from certificate:
2024-11-18 14:53:09,331 INFO [MdmEventHandler-63-thread-2][[]] cisco.cpm.mdm.pip.MdmEventHandler -:::::- CERT_GUID_KEY ==CertMdmGuid , deviceQueryIdenArr=[SAN_URI, ID:Meraki:GUID:673288144292101809,tag:microsoft.com,2022-09-14:sid:S-1-5-21-2942795583-2590601415-1333022741-66482]
Sending incorrect GUID to MDM server:
2024-11-18 14:53:09,039 INFO [MdmEventHandler-63-thread-2][[]] cisco.cpm.mdm.util.MdmRESTClient -:::::- GET: MDM Server URL: https://n196.meraki.com:443/ciscoise/v3/devices/?paging=0&querycriteria=guid&value=S-1-5-21-2942795583-2590601415-1333022741-66482&filter=all
Enrollment return from MDM:
2024-11-18 14:53:09,333 DEBUG [MdmEventHandler-63-thread-2][[]] cisco.cpm.mdm.util.MDMUtil -:::::- Existing device and checking the mdm attributes values 2024-11-18 14:53:09,333 DEBUG [MdmEventHandler-63-thread-2][[]] cisco.cpm.mdm.util.MDMUtil -:::::- updating device mdm attributes - MDM Enrolled value: false in endpoint
Workaround/Solution
Solution
For the affected use cases where authentication is performed using GUID-embedded certificates, Cisco ISE systems must be upgraded to one of the following releases:
- 3.2 P7 or later
- 3.3 P4 or later
- 3.4 P1 or later
- 3.1 P10 or later (3.1 P10 estimated release date: Jan 2025)
These Cisco ISE releases comply with the newer GUID format proposed by Microsoft Intune.
Additional Information
Affected SAN Formats
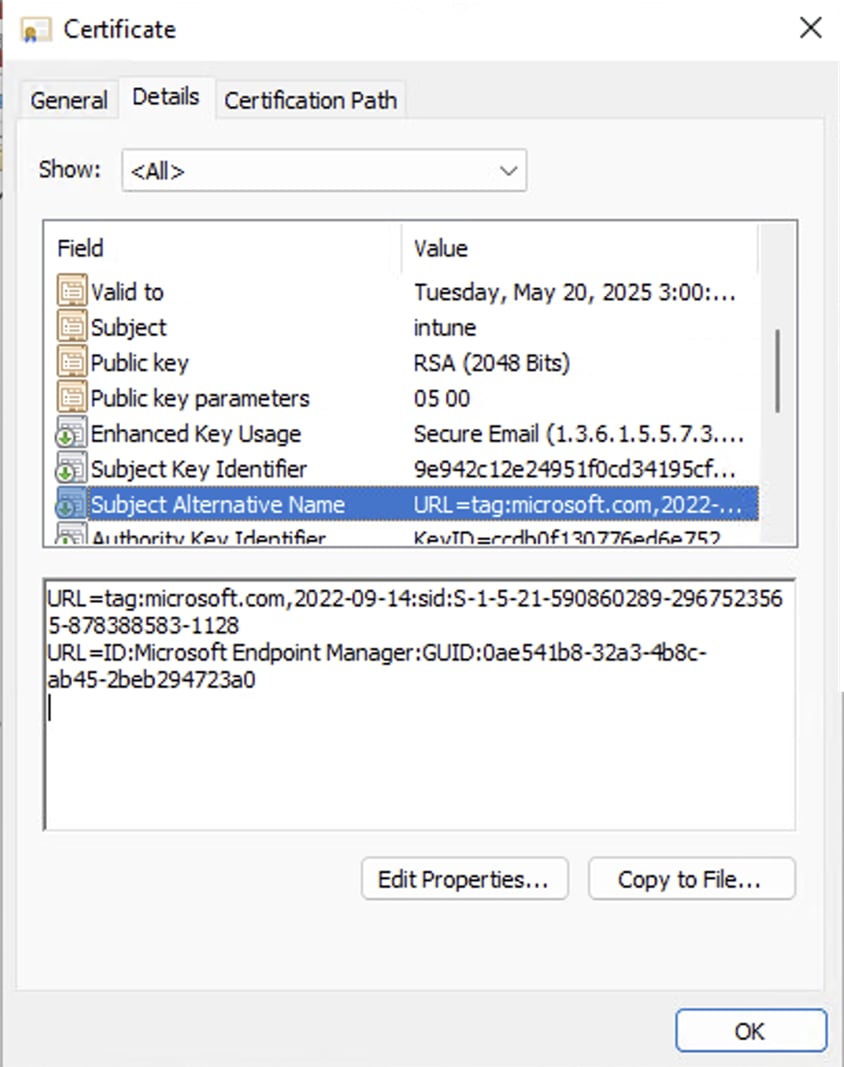
Format #1
URL=tag:microsoft.com,2022-09-14:sid:xxxxx
URL=ID:Microsoft Endpoint Manager:GUID:{{DeviceId}}
Policy definition in Microsoft Intune:

SAN in certificate issued:
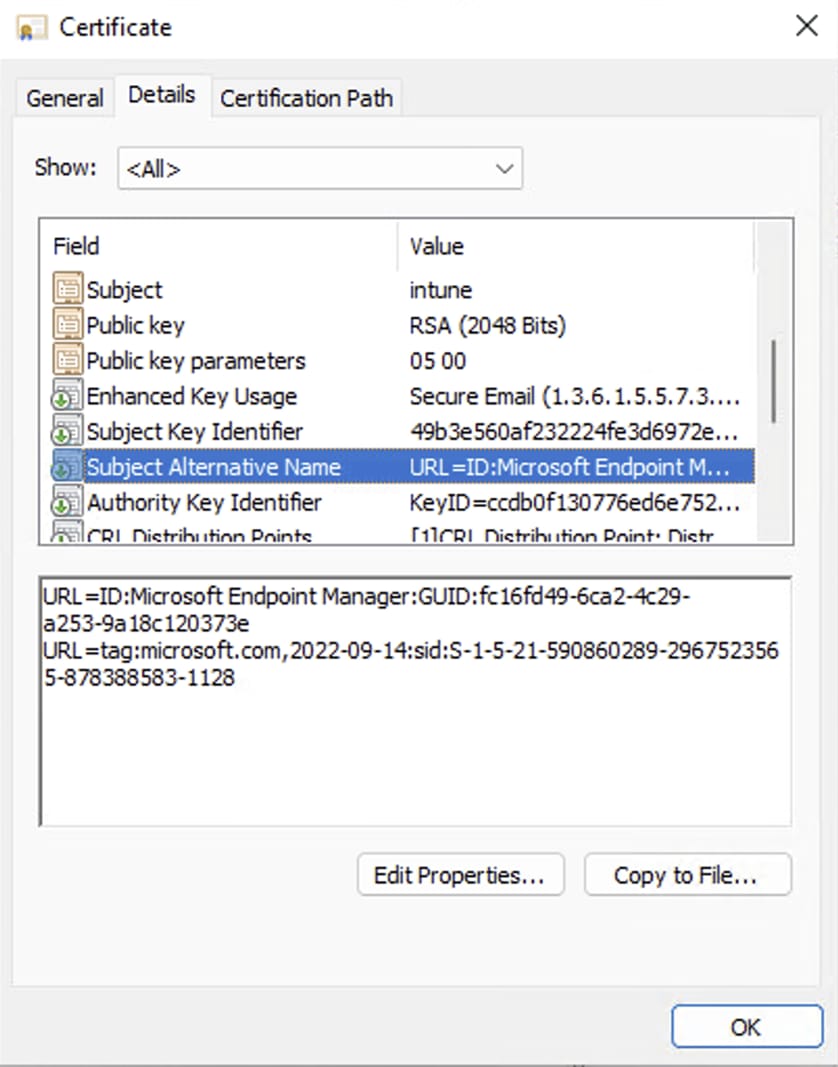
Format #2
URL=ID:Microsoft Endpoint Manager:GUID:{{DeviceId}}
URL=tag:microsoft.com,2022-09-14:sid:xxxxx
Policy definition in Microsoft Intune:

SAN in certificate issued:
Format #3
URL=tag:microsoft.com,2022-09-14:sid:xxxxx, ID:Microsoft Endpoint Manager:GUID:{{DeviceId}} – applicable for iOS. Notice that both URIs are combined into one URL in the certificate.
Policy definition in Microsoft Intune:

SAN in certificate issued:
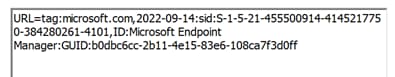
Format #4
URL= ID:Microsoft Endpoint Manager:GUID:{{DeviceId}},tag:microsoft.com,2022-09-14:sid:xxxxx – applicable for iOS. Notice that both URIs are combined into one URL in the certificate.
Policy definition in Microsoft Intune:

SAN in certificate issued:
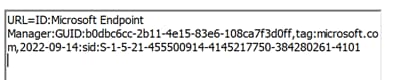
Format #5
URL=tag:microsoft.com,2022-09-14:sid:xxxxx, ID:Microsoft Endpoint Manager:GUID:{{DeviceId}},SampleURI – applicable for iOS. Notice that both URIs are combined into one URL in the certificate
Policy definition in Microsoft Intune:
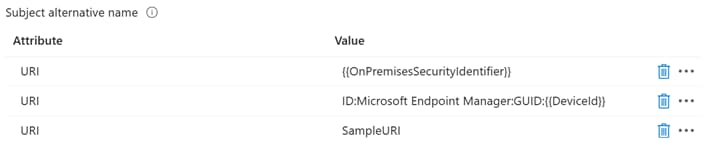
SAN in certificate issued:
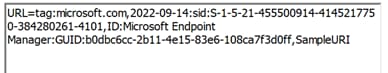
Revision History
| Version | Description | Section | Date |
| 1.0 | Initial Release | — | 2025-JAN-08 |
For More Information
For further assistance or for more information about this field notice, contact the Cisco Technical Assistance Center (TAC) using one of the following methods:
Receive Email Notification About New Field Notices
To receive email updates about Field Notices (reliability and safety issues), Security Advisories (network security issues), and end-of-life announcements for specific Cisco products, set up a profile in My Notifications.
Contact Cisco
- Open a Support Case

- (Requires a Cisco Service Contract)
This Document Applies to These Products
Unleash the Power of TAC's Virtual Assistance
 Feedback
Feedback