Introduction
This document describes how PfRv3 (Performance Routing) discovers the external interfaces for spoke locations. This process varies in PfRv2 where the external interfaces at spoke location are manually configured on the Master Controller (MC) router on respective site. In PfRv3 manual configuration is not required on any of the spoke site routers as these are automatically discovered through Smart Probes.
Smart Probes are UDP probes being sent by Hub Master Controller (MC) destined for Master Router as spoke location . Therse are not be confused with IP SLA probes. Smart probes uses 18000 as source port and 19000 as destination port.
Prerequisites
Requirements
Cisco recommends that you have basic knowledge of Performance Routing version 3 (PfRv3).
Components Used
This document is not restricted to specific software and hardware versions.
The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, make sure that you understand the potential impact of any command.
Background Information
One of the main applications of PfR is WAN load balancing and to achieve this PfR needs to identify all the available external links(WAN). In PfRv2 a site's WAN links are manually defined on site's Master Controller router. This approach works fine if there are few sites to be configured but the complexity increases as the number of sites to be monitored increases as this configuration will then be required to be done on each site. Even managing every site configuration in time becomes difficult .
One of the features that have been introduced, to tackle this challegnge, in the next generation of the PfR is the ability to automate this discovery process. In PfRv3 this automation is done with the help of Smart Probes which performs autodiscovery of the interfaces on all spoke sites.
There are four different roles a device can play in PfRv3 configuration:
- Hub-master controller — The master controller at the hub site, which can be either a data center or a head quarter. All policies are configured on hub-master controller. It acts as master controller for the site and makes optimization decision.
- Hub-border router — The border controller at the hub site. PfRv3 is enabled on the WAN interfaces of the hub-border routers. You can configure more than one WAN interface on the same device. You can have multiple hub border devices. On the hub-border router, PfRv3 must be configured with the address of the local hub-master controller, path names, and path-ids of the external interfaces. You can use the global routing table (default VRF) or define specific VRFs for the hub-border routers.
-
Branch-master controller — The branch-master controller is the master controller at the branch site. There is no policy configuration on this device. It receives policy from the hub-master controller. This device acts as master controller for the branch site and makes optimization decision.
-
Branch- border router — The border device at the branch-site. There is no configuration other than enabling of PfRv3 border-master controller on the device. The WAN interface that terminates on the device is detected automatically.
Configure
Network Diagram
This document would refer following image as a sample topolgy for rest of the document.
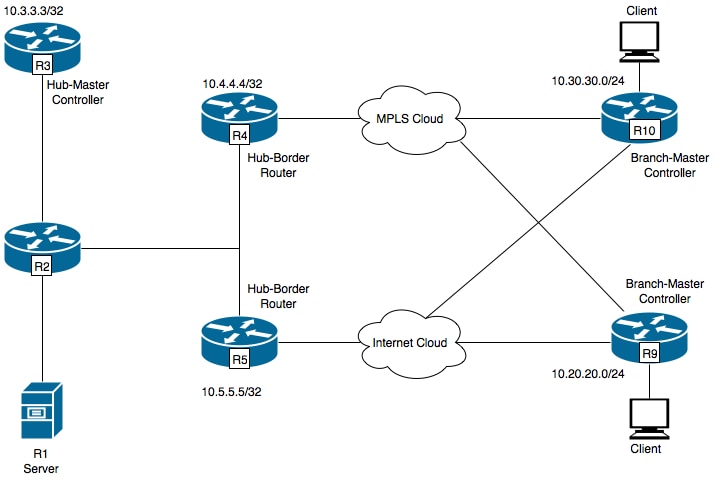
Devices shown in the diagram:
R1- Server, Initiating traffic.
R3- Hub-Master Controller.
R4- Hub-Border Router.
R5- Hub-Border Router.
R9- Branch-Master Controller for Spoke Location
R10- Branch-Master Controller for Spoke Location
R9 has two DMVPN tunnels i.e. Tunnel 100 and Tunnel 200. Tunnel 100 is terminating on R4 and Tunnel 200 is termintaing on R5.
Configurations
R3: HUB Master Controller Configuraton
domain one
vrf default
master hub
source-interface Loopback0
load-balance
class test1 sequence 1
class TEST sequence 10
match dscp ef policy custom
priority 1 one-way-delay threshold 25
path-preference INET1 fallback INET2
R4: Hub Border Router Configuration
vrf default
border
source-interface Loopback0
master 10.3.3.3
R4#sh run int tu 100
Building configuration...
Current configuration : 542 bytes
!
interface Tunnel100
description -- TO BORDER ROUTERS --
bandwidth 1000
ip address 10.0.100.84 255.255.255.0
no ip redirects
ip mtu 1400
ip flow monitor MONITOR-STATS input
ip flow monitor MONITOR-STATS output
ip nhrp authentication cisco
ip nhrp map multicast dynamic
ip nhrp network-id 1
ip nhrp holdtime 600
ip tcp adjust-mss 1360
load-interval 30
delay 5100
tunnel source Ethernet0/1
tunnel mode gre multipoint
tunnel key 100
tunnel vrf INET1
tunnel protection ipsec profile DMVPN-PROFILE1
domain one path INET1 -----> INET1 is the name defined for the external interface.
R5: Hub Border Router Configuration
vrf default
border
source-interface Loopback0
master 10.3.3.3
R5#sh run int tu 200
Building configuration...
Current configuration : 542 bytes
!
interface Tunnel200
description -- TO BORDER ROUTERS --
bandwidth 1000
ip address 10.0.200.85 255.255.255.0
no ip redirects
ip mtu 1400
ip flow monitor MONITOR-STATS input
ip flow monitor MONITOR-STATS output
ip nhrp authentication cisco
ip nhrp map multicast dynamic
ip nhrp network-id 2
ip nhrp holdtime 600
ip tcp adjust-mss 1360
load-interval 30
delay 5100
tunnel source Ethernet0/1
tunnel mode gre multipoint
tunnel key 200
tunnel vrf INET2
tunnel protection ipsec profile DMVPN-PROFILE2
domain one path INET2 -----> INET2 is the name defined for the external interface.
R9: Spoke Master Controller Configuration
domain one
vrf default
border
source-interface Loopback0
master local
master branch
source-interface Loopback0
hub 10.3.3.3
R9#show run int tun100
Building configuration...
Current configuration : 548 bytes
!
interface Tunnel100
bandwidth 400
ip address 10.0.100.10 255.255.255.0
no ip redirects
ip mtu 1400
ip flow monitor MONITOR-STATS input
ip flow monitor MONITOR-STATS output
ip nhrp authentication cisco
ip nhrp map 10.0.100.84 10.4.81.4
ip nhrp map multicast 10.4.81.4
ip nhrp network-id 1
ip nhrp holdtime 600
ip nhrp nhs 10.0.100.84
ip nhrp registration timeout 60
ip tcp adjust-mss 1360
tunnel source Ethernet0/1
tunnel mode gre multipoint
tunnel key 100
tunnel vrf INET1
tunnel protection ipsec profile DMVPN-PROFILE1
end
R9#show run int tun200
Building configuration...
Current configuration : 588 bytes
!
interface Tunnel200
bandwidth 400
ip address 10.0.200.10 255.255.255.0
no ip redirects
ip mtu 1400
ip flow monitor MONITOR-STATS input
ip flow monitor MONITOR-STATS output
ip nhrp authentication cisco
ip nhrp map 10.0.200.85 10.5.82.5
ip nhrp map multicast 10.5.82.5
ip nhrp network-id 2
ip nhrp holdtime 600
ip nhrp nhs 10.0.200.85
ip nhrp nhs cluster 0 max-connections 2
ip nhrp registration no-unique
ip tcp adjust-mss 1360
tunnel source Ethernet0/2
tunnel mode gre multipoint
tunnel key 200
tunnel vrf INET2
tunnel protection ipsec profile DMVPN-PROFILE2
end
Note: On R9 spoke site there is no explicit configuration required to identify external interfaces as they will be autodiscovered from Hub Master controller router using smart probes as discussed earlier.
Verify
Following shows the status of the PfR on Hub Master Controller:
R3#show domain one master status
*** Domain MC Status ***
Master VRF: Global
Instance Type: Hub
Instance id: 0
Operational status: Up
Configured status: Up
Loopback IP Address: 10.3.3.3
Load Balancing:
Admin Status: Disabled
Operational Status: Down
Enterprise top level prefixes configured: 0
Route Control: Enabled
Mitigation mode Aggressive: Disabled
Policy threshold variance: 20
Minimum Mask Length: 28
Sampling: off
Borders:
IP address: 10.4.4.4
Connection status: CONNECTED (Last Updated 00:20:50 ago )
Interfaces configured:
Name: Tunnel100 | type: external | Service Provider: INET1 | Status: UP
Number of default Channels: 0
Tunnel if: Tunnel0
IP address: 10.5.5.5
Connection status: CONNECTED (Last Updated 00:20:50 ago )
Interfaces configured:
Name: Tunnel200 | type: external | Service Provider: INET2 | Status: UP
Number of default Channels: 0
Tunnel if: Tunnel0
Note: Above output shows that Tunnel100 on Border R4 shows External interface is INET1 and on Border R5 (10.5.5.5) External interface is Tunnel200 as marked as INET2.
Following command on the R9 shows the interfaces auto-discovered.
R9#show domain one master status
*** Domain MC Status ***
Master VRF: Global
Instance Type: Branch
Instance id: 0
Operational status: Up
Configured status: Up
Loopback IP Address: 10.9.9.9
Load Balancing:
Operational Status: Down
Route Control: Enabled
Mitigation mode Aggressive: Disabled
Policy threshold variance: 20
Minimum Mask Length: 28
Sampling: off
Minimum Requirement: Met
Borders:
IP address: 10.9.9.9
Connection status: CONNECTED (Last Updated 00:25:58 ago )
Interfaces configured:
Name: Tunnel200 | type: external | Service Provider: INET2 | Status: UP
Number of default Channels: 0
Name: Tunnel100 | type: external | Service Provider: INET1 | Status: UP
Number of default Channels: 0
Tunnel if: Tunnel0
Note: Above output shows that Tunnel 200 and Tunnel 100 on R9 ( 10.9.9.9 ) as external interfaces, have been discovered as INET1 and INET2 respectively .
These interfaces have been discovered by help of smart probes . Netflow was configured to show the source and destination ports for these probes.
R9#show flow monitor MONITOR-STATS cache format table
Cache type: Normal
Cache size: 4096
Current entries: 5
High Watermark: 5
Flows added: 5
Flows aged: 0
- Active timeout ( 60 secs) 0
- Inactive timeout ( 60 secs) 0
- Event aged 0
- Watermark aged 0
- Emergency aged 0
IPV4 SRC ADDR IPV4 DST ADDR TRNS SRC PORT TRNS DST PORT INTF INPUT FLOW DIRN IP DSCP IP PROT
=============== =============== ============= ============= ==================== ========= ======= =======
10.3.3.3 10.9.9.9 18000 19000 Tu100 Input 0x00 17
10.3.3.3 10.9.9.9 18000 19000 Tu200 Input 0x00 17
If there is no traffic then external interface are being discovered on channel associated with dscp 0 . Default channels are created from Hub to Branch site even though there may not be any traffic . This is to assist the interface discovery on Branch. However interface can be discovered on a non-default channel as well . Below output shows that channel 17 and channel 16 is automatically created for dscp value 0 , since there is no active traffic as of now so discovery packet will be sent on dscp 0.
R9#show domain one master channels dscp 0
Legend: * (Value obtained from Network delay:)
Channel Id: 17 Dst Site-Id: 10.3.3.3 Link Name: INET2 DSCP: default [0] TCs: 0
Channel Created: 05:08:04 ago
Provisional State: Discovered and open
Operational state: Available
Interface Id: 12
Estimated Channel Egress Bandwidth: 0 Kbps
Immitigable Events Summary:
Total Performance Count: 0, Total BW Count: 0
TCA Statitics:
Received:0 ; Processed:0 ; Unreach_rcvd:0
Channel Id: 16 Dst Site-Id: 10.3.3.3 Link Name: INET1 DSCP: default [0] TCs: 0
Channel Created: 05:08:34 ago
Provisional State: Discovered and open
Operational state: Available
Interface Id: 11
Estimated Channel Egress Bandwidth: 0 Kbps
Immitigable Events Summary:
Total Performance Count: 0, Total BW Count: 0
TCA Statitics:
Received:1 ; Processed:0 ; Unreach_rcvd:1
Troubleshoot
There is currently no specific troubleshooting information available for this configuration.

 Feedback
Feedback