Configuring PPTP Through PAT to a Microsoft PPTP Server
Available Languages
Contents
Introduction
Microsoft (MS) Point-to-Point Tunneling Protocol (PPTP) is used to enable remote users to connect back to their corporate network in a secured manner across the public Internet. You can allocate a single IP address to a remote location to conserve your public IP addresses. Then, you can allow multiple users to establish PPTP connections simultaneously to the same or to different locations. PPTP was added in Cisco IOS® Software Release 12.1(4)T.
For more information, refer to the NAT - Support for PPTP in an Overload (Port Address Translation) Configuration section in the Cisco IOS Software 12.1 T Early Deployment Release Series.
Prerequisites
Requirements
There are no specific requirements for this document.
Components Used
The information in this document is based on these software and hardware versions:
-
Cisco 3600 Routers that run Cisco IOS Software Releases 12.1.5(9)T and 12.2.3
-
All Windows Operating System platforms with PPTP native clients built-in
-
MS Windows 2000 Advanced Server with a built-in PPTP server
The information presented in this document was created from devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If you are working in a live network, ensure that you understand the potential impact of any command before using it.
Conventions
Refer to the Cisco Technical Tips Conventions for more information on document conventions.
Configure
In this section, you are presented with the information to configure the features described in this document.
Note: Use the Command Lookup Tool (registered customers only) to find more information on the commands used in this document.
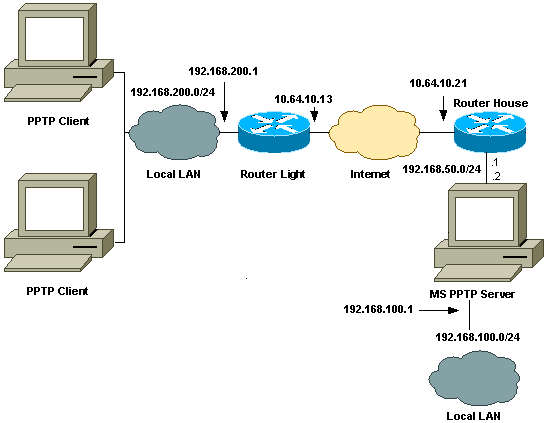
Network Diagram
This document uses this network setup:
Configurations
This document uses these configurations:
| Router Light |
|---|
Current configuration : 1136 bytes ! version 12.2 service timestamps debug upti service timestamps log uptime no service password-encryption ! hostname light ! boot system tftp c3660-jk9o3s-mz.122-3.bin 255.255.255.255 ! ip subnet-zero ! ! no ip domain-lookup ! ip audit notify log ip audit po max-events 100 ip ssh time-out 120 ip ssh authentication-retries 3 ! call rsvp-sync cns event-service server ! ! ! ! ! fax interface-type modem mta receive maximum-recipients 0 ! controller E1 2/0 ! ! ! interface FastEthernet0/0 ip address 10.64.10.13 255.255.255.224 !--- Defines the interface as external for NAT. ip nat outside duplex auto speed auto ! interface FastEthernet0/1 ip address 192.168.200.1 255.255.255.0 !--- Defines the interface as internal for NAT. ip nat inside duplex auto speed auto ! interface Serial1/0 no ip address shutdown no fair-queue ! interface Serial1/1 no ip address shutdown ! interface Serial1/2 no ip address shutdown ! interface Serial1/3 no ip address shutdown ! !--- Indicates that any packets received on the inside interface permitted !--- by access list 101 share one public IP address (the address on Fa0/0). ip nat inside source list 101 interface FastEthernet0/0 overload ip classless ip route 0.0.0.0 0.0.0.0 10.64.10.1 no ip http server ! access-list 101 permit ip any any ! ! dial-peer cor custom ! ! ! ! ! line con 0 line aux 0 line vty 0 4 login ! end |
| IP NAT Translation Table |
|---|
light#show ip nat translations Pro Inside global Inside local Outside local Outside global gre 10.64.10.13:50150 192.168.200.253:50150 10.64.10.21:50150 10.64.10.21:50150 gre 10.64.10.13:50151 192.168.200.254:50151 10.64.10.21:50151 10.64.10.21:50151 gre 10.64.10.13:0 192.168.200.254:0 10.64.10.21:0 10.64.10.21:0 gre 10.64.10.13:32768 192.168.200.253:32768 10.64.10.21:32768 10.64.10.21:32768 tcp 10.64.10.13:2643 192.168.200.253:2643 10.64.10.21:1723 10.64.10.21:1723 tcp 10.64.10.13:3546 192.168.200.254:3546 10.64.10.21:1723 10.64.10.21:1723 |
| Router House |
|---|
Building configuration... Current configuration : 2281 bytes ! version 12.2 service timestamps debug uptime service timestamps log uptime no service password-encryption ! hostname house ! enable password cisco ! ip subnet-zero ! ! ! fax interface-type modem mta receive maximum-recipients 0 ! ! interface FastEthernet0/0 ip address 10.64.10.21 255.255.255.224 !--- Defines the interface as external for NAT. ip nat outside duplex auto speed auto ! interface FastEthernet0/1 ip address 192.168.50.1 255.255.255.0 !--- Defines the interface as internal for NAT. ip nat inside duplex auto speed auto ! ! interface FastEthernet4/0 no ip address shutdown duplex auto speed auto ! !--- Indicates that any packets received on the inside interface permitted by !--- access list 101 share one public IP address (the address on Fa0/0). ip nat inside source list 101 interface FastEthernet0/0 overload !--- Static port translation for the Microsoft PPTP server on TCP port 1723 !--- share one public IP address (the address on Fa0/0). ip nat inside source static tcp 192.168.50.2 1723 interface FastEthernet0/0 1723 ip classless ip route 0.0.0.0 0.0.0.0 10.64.10.1 ip http server ip pim bidir-enable ! access-list 101 permit ip any any ! ! snmp-server manager ! call rsvp-sync ! ! mgcp profile default ! dial-peer cor custom ! ! line con 0 line aux 0 line vty 0 4 password cisco login ! ! end |
| IP NAT Translation Table |
|---|
house#show ip nat translations Pro Inside global Inside local Outside local Outside global gre 10.64.10.21:50150 192.168.50.2:50150 10.64.10.13:50150 10.64.10.13:50150 gre 10.64.10.21:50151 192.168.50.2:50151 10.64.10.13:50151 10.64.10.13:50151 gre 10.64.10.21:0 192.168.50.2:0 10.64.10.13:0 10.64.10.13:0 gre 10.64.10.21:32768 192.168.50.2:32768 10.64.10.13:32768 10.64.10.13:32768 tcp 10.64.10.21:1723 192.168.50.2:1723 10.64.10.13:2643 10.64.10.13:2643 tcp 10.64.10.21:1723 192.168.50.2:1723 --- --- tcp 10.64.10.21:80 192.168.50.2:80 --- --- tcp 10.64.10.21:1723 192.168.50.2:1723 10.64.10.13:3546 10.64.10.13:3546 |
Configure the MS PPTP Server
Complete these steps in order to configure the MS PPTP Server:
-
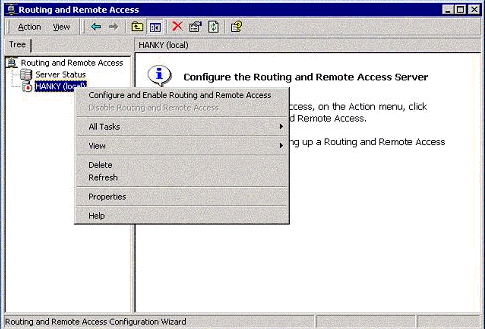
Go to Routing and Remote Access and choose Configure and Enable Routing and Remote Access.
-
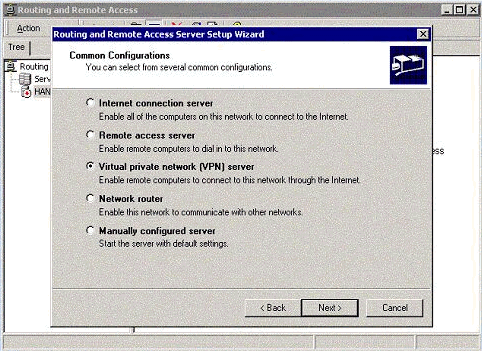
In the Routing and Remote Access Server Setup Wizard, choose Virtual private network (VPN) server.
-
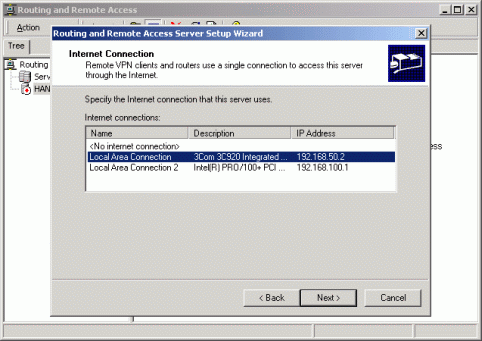
Define the outside and inside network IP addresses for the server network interface card (NIC).
-
Assign an IP pool to the remote PPTP clients.
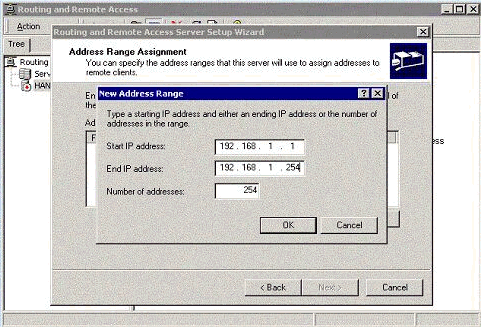
-
You can use the MS RADIUS authentication server or you can use local authentication.
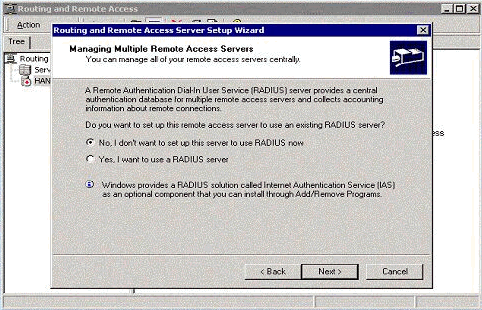
-
Create the local user database for local authentication.
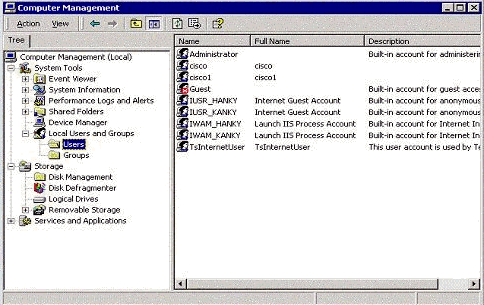
-
Two PPTP clients behind the Port Address Translation (PAT) router are connected to the MS PPTP server.
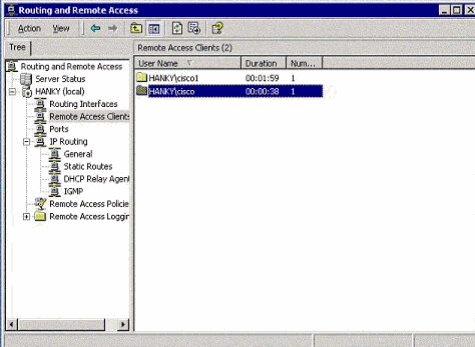
Verify
Use this section to confirm that your configuration works properly.
The Output Interpreter Tool (registered customers only) (OIT) supports certain show commands. Use the OIT to view an analysis of show command output.
-
show ip nat translations—Shows the contents of the translation table.
Troubleshoot
This section provides information you can use to troubleshoot your configuration.
Troubleshooting Resources
Related Information
Revision History
| Revision | Publish Date | Comments |
|---|---|---|
1.0 |
19-Oct-2006 |
Initial Release |







 Feedback
Feedback