Packet Loss over a Dot1Q/L2P Tunnel
Available Languages
Contents
Introduction
This document discusses about troubleshooting the packet loss over a Dot1Q/L2P tunnel due to poor network design in Cisco IOS® with a case study.
Prerequisites
Requirements
Cisco recommends that you have knowledge of these topics:
-
Basic knowledge on Dot1Q Tunneling
-
Basic knowledge of OSPF
Components Used
This document is not restricted to specific software or hardware versions.
The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, make sure that you understand the potential impact of any command.
Conventions
Refer to Cisco Technical Tips Conventions for more information on document conventions.
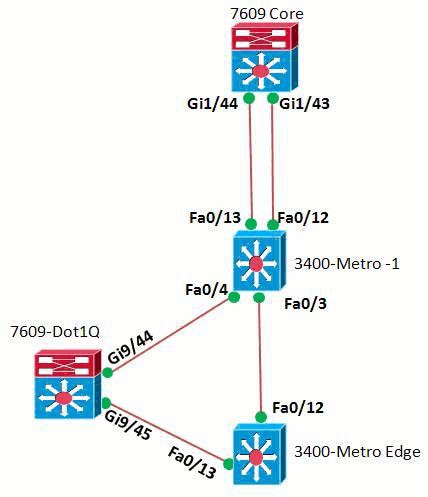
Network Diagram
In this network setup, the interface Gi1/44 and Gi 1/43 of the router 7600-Core has router on a stick setup with Fa0/13 and Fa0/12 of the router 3400-Metro-1 respectively. In 7600-Dot1Q switch the interface Gi9/44 and Gi 9/45 are enabled with Dot1q tunnel mode. SVI vlan interfaces are created on the 3400-Metro Edge and Fa0/13 and Fa0/12 are configured as trunk ports. The routers use OSPF to communicate with each other.
Configurations
| 7609 Core |
|---|
! version 15.0 hostname 7609-CORE interface GigabitEthernet1/43 mtu 9216 no ip address no ip redirects no ip proxy-arp load-interval 60 carrier-delay 2 flowcontrol send off storm-control broadcast level 1.00 ! interface GigabitEthernet1/43.3503 encapsulation dot1Q 3503 ip address 172.16.41.17 255.255.255.252 no ip redirects no ip proxy-arp ip mtu 1500 ip ospf authentication-key 7 072C0E6B6B272D ip ospf network point-to-point ip ospf hello-interval 3 ip ospf dead-interval 10 ! ! interface GigabitEthernet1/44 mtu 9216 no ip address no ip redirects no ip proxy-arp load-interval 60 carrier-delay 2 flowcontrol send off storm-control broadcast level 1.00 ! interface GigabitEthernet1/44.3803 encapsulation dot1Q 3803 ip address 172.16.73.137 255.255.255.248 secondary ip address 172.16.41.21 255.255.255.252 no ip redirects no ip proxy-arp ip mtu 1500 ip ospf authentication-key 7 072C0E6B6B272D ip ospf network point-to-point ip ospf cost 5 ip ospf hello-interval 3 ip ospf dead-interval 10 !--- Output omitted. ! end |
| 7609 DOT1Q |
|---|
! version 12.2 ! interface GigabitEthernet9/44 switchport switchport access vlan 24 switchport mode dot1q-tunnel mtu 9216 load-interval 60 carrier-delay 2 flowcontrol send off storm-control broadcast level 1.00 l2protocol-tunnel cdp l2protocol-tunnel stp l2protocol-tunnel vtp no cdp enable spanning-tree portfast disable spanning-tree bpdufilter enable ! ! interface GigabitEthernet9/45 switchport switchport access vlan 24 switchport mode dot1q-tunnel mtu 9216 load-interval 60 carrier-delay 2 flowcontrol send off storm-control broadcast level 1.00 l2protocol-tunnel cdp l2protocol-tunnel stp l2protocol-tunnel vtp no cdp enable spanning-tree portfast disable spanning-tree bpdufilter enable ! !--- Output omitted. ! end |
| 3400-Metro-1 |
|---|
! version 12.2 ! interface FastEthernet0/3 port-type nni switchport trunk allowed vlan 1052,3503 switchport mode trunk load-interval 60 ! interface FastEthernet0/4 port-type nni switchport trunk allowed vlan 1052,3803 switchport mode trunk load-interval 60 ! ! interface FastEthernet0/12 port-type nni switchport trunk allowed vlan 2-4094 switchport mode trunk ! interface FastEthernet0/13 port-type nni switchport trunk allowed vlan 2-4094 switchport mode trunk ! end |
| 3400-Metro Edge |
|---|
! version 12.2 ! interface FastEthernet0/12 port-type nni switchport mode trunk load-interval 60 storm-control broadcast level 1.00 spanning-tree portfast disable spanning-tree bpdufilter disable ! interface FastEthernet0/13 port-type nni switchport mode trunk load-interval 60 storm-control broadcast level 1.00 spanning-tree portfast disable spanning-tree bpdufilter disable ! ! interface Vlan3503 ip address 172.16.41.18 255.255.255.252 no ip redirects no ip proxy-arp ip ospf authentication-key 7 072C0E6B6B272D ip ospf network point-to-point ip ospf hello-interval 3 ip ospf dead-interval 10 ! interface Vlan3803 ip address 172.16.73.139 255.255.255.248 secondary ip address 172.16.41.22 255.255.255.252 no ip redirects no ip proxy-arp ip ospf authentication-key 7 072C0E6B6B272D ip ospf network point-to-point ip ospf cost 5 ip ospf hello-interval 3 ip ospf dead-interval 10 ! !--- Output omitted. ! end |
Observation
Random Ping drops occur when the packet traverses through Dot1Q Tunnel. But, there are no input/output drops on the interfaces and also there are no symptoms of physical layer issues. Issue the show interface <interface > command in order to check the input/output drops on the interface:
7609-Dot1Q#show interface gi9/44
!--- Output omitted.
Input queue: 0/75/0/0 (size/max/drops/flushes); Total output drops: 0
0 input errors, 0 CRC, 1 frame, 0 overrun, 0 ignored
0 output errors, 0 collisions, 1 interface resets
0 lost carrier, 0 no carrier, 0 PAUSE output
!--- Output omitted.
When an ICMP traffic of about 100 Pings are sent out from the Metro-Edge, only 95 Echoes are received in the Core, which suggests that ICMP packets are getting dropped in the path.
Metro-Edge#ping 172.16.41.21 re 100 Type escape sequence to abort. Sending 100, 100-byte ICMP Echos to 172.16.41.21, timeout is 2 seconds: .....!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!! !!!!!!!!!!!!!!!!!!!!!!!!!!!!!! Success rate is 95 percent (95/100), round-trip min/avg/max = ½/9 ms
Note: The show ip traffic command in the 7609 shows that only 95 echos are received whereas in Metro-edge and it shows 100 Echos are sent out.
| show ip traffic |
|---|
In Metro-Edge ICMP statistics:
Rcvd: 0 format errors, 0 checksum errors, 0 redirects, 0 unreachable
0 echo, 95 echo reply, 0 mask requests, 0 mask replies, 0 quench
0 parameter, 0 timestamp, 0 info request, 0 other
0 irdp solicitations, 0 irdp advertisements
Sent: 0 redirects, 0 unreachable, 100 echo, 0 echo reply
0 mask requests, 0 mask replies, 0 quench, 0 timestamp
0 info reply, 0 time exceeded, 0 parameter problem
0 irdp solicitations, 0 irdp advertisements
!--- The above output shows that 100 echos are sent !--- but received 95 replies from 7609-Core.
In 7609-Core ICMP statistics:
Rcvd: 0 format errors, 0 checksum errors, 0 redirects, 0 unreachable
95 echo, 0 echo reply, 0 mask requests, 0 mask replies, 0 quench
0 parameter, 0 timestamp, 0 info request, 0 other
0 irdp solicitations, 0 irdp advertisements
Sent: 0 redirects, 0 unreachable, 0 echo, 95 echo reply
0 mask requests, 0 mask replies, 0 quench, 0 timestamp
0 info reply, 0 time exceeded, 0 parameter problem
0 irdp solicitations, 0 irdp advertisements |
Troubleshooting
Verify whether the MAC addresses are learnt properly in order to troubleshoot the drop in packets.
Use show mac address table command in order to verify the MAC address entries.
For Successful Ping
7609-DOT1q#sh mac-address-table address E05F.B972.1F00 all Legend: * - primary entry age - seconds since last seen n/a - not available vlan mac address type learn age ports ------+----------------+--------+-----+----------+-------------------------- Active Supervisor: * 24 e05f.b972.1f00 dynamic Yes 0 Gi9/44 !--- This output displays the MAC address learnt !--- and its associated port, in this case the associated !--- port for successful ping is Gi9/44.
For Failure Ping
7609-DOT1q#sh mac-address-table address E05F.B972.1F00 all Legend: * - primary entry age - seconds since last seen n/a - not available vlan mac address type learn age ports ------+----------------+--------+-----+----------+-------------------------- Active Supervisor: * 24 e05f.b972.1f00 dynamic Yes 5 Gi9/45 !--- This output displays the MAC address learnt !--- and its associated port, in this case, !--- the port number is Gi9/45.
In order to see the detailed MAC Index Programming , use the show mac-address-table command.
7609-DOT1q#sh mac-address-table address E05F.B972.1F00 det MAC Table shown in details ======================================== PI_E RM RMA Type Alw-Lrn Trap Modified Notify Capture Flood Mac Address Age Pvlan SWbits Index XTag ----+---+---+----+-------+----+--------+------+-------+------+--------------+----+------+------+---- Active Supervisor: Yes No No DY No No Yes No No No e05f.b972.1f00 0xE0 24 0 0x22C 0
Issue the Remote login switch and test mcast ltl-info index <Index number> commands in order to know which port number that the previous HEX value denoted.
7609-DOT1q-sp#test mcast ltl-info index 22B index 0x22B contain ports 9/44 7609-DOT1q-sp#test mcast ltl-info index 22C index 0x22C contain ports 9/45 !--- The output shows that hex number 22B !--- points to 9/44 port and hex 22C points to 9/45.
For the failed ping the source and destination index are the same port and hence the drop. When enabled Mac-move with the mac-address-table notification mac-move command on the 7600 it shows MAC flaps between two different ports and this is the error message:
Note: Since 6500/7600 uses one common MAC address for the switch., the same MAC address assigned between different ports. The show catalyst 6000 chassis-mac-address command shows the reserved switch MAC address.
* Jul 2 10:29:44.011: %MAC_MOVE-SP-4-NOTIF: Host e05f.b972.1f00 in vlan 24 is flapping between port Gi9/45 and port Gi9/44 !--- The previous error message indicates !--- that the same MAC address is assigned between !--- two different ports: Gi9/45 and port Gi9/44.
Solution
The previous network is a full mesh network setup that has DOT1Q tunnel endpoints on the same switch. In this kind of network setup MAC-flaps are expected. In order to avoid MAC-flapping, one of these solutions can be implemented.
-
Move the tunnel endpoint to a different switch, for example, encapsulation and decapsulation should happen in different switch.
-
VLAN Pruning can be done so as to regulate the VLANS in any of the trunk ports.
Related Information
Revision History
| Revision | Publish Date | Comments |
|---|---|---|
1.0 |
06-Nov-2012 |
Initial Release |
 Feedback
Feedback