Configuration Example of MPLS L3VPNs with ISIS Remote LFA
Available Languages
Download Options
Bias-Free Language
The documentation set for this product strives to use bias-free language. For the purposes of this documentation set, bias-free is defined as language that does not imply discrimination based on age, disability, gender, racial identity, ethnic identity, sexual orientation, socioeconomic status, and intersectionality. Exceptions may be present in the documentation due to language that is hardcoded in the user interfaces of the product software, language used based on RFP documentation, or language that is used by a referenced third-party product. Learn more about how Cisco is using Inclusive Language.
Contents
Introduction
This document describes how to configure Multiprotocol Label Switching (MPLS) Layer 3 Vpns with ISIS Remote Loop Free Alternative (LFA) feature. It shows a sample network scenario and its configuration and outputs to understand better.
Prerequisites
Requirements
There are no specific requirements for this document. However, basic understanding of MPLS and working knowledge of ISIS protocol will definitely help.
Components Used
This document is not restricted to specific software and hardware versions.
The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, make sure that you understand the potential impact of any command.
Background Information
ISIS is widely deployed across ISPs worldwide and MPLS Layer 3 Vpn is the most common solution provided by the ISPs. Inside an ISP core infrastructure link failure directly impacts the performance, so sub-second convergence is highly desired. Features like MPLS tunnel Link Protection and Node Protection solve these issues but require manual configuration.
ISIS Remote LFA leverages the concept that for a given area, all the ISIS routers will have identical link State Database. If Router A needs to select a backup path to destination X, via Router B, then Router A can select Router B as the backup next hop provided that Router B does not use Router A as it next hop for destination X. This can be done as all the routers have identical database. This is the basic idea for the LFA feature. Now this backup path is directly programmed in Cisco Express Forwarding (CEF) entry and will be instantly used once the primary route fails. Then the routing protocol can converge as per traditional timers.
ISIS Remote LFA
To understand better how Remote LFA works, consider this diagram:
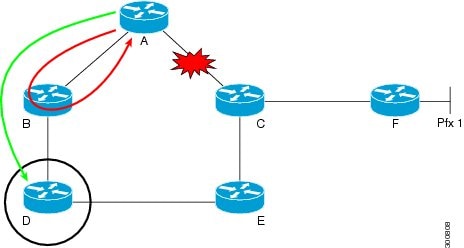
The traffic flows from Router A to F taking the path A--C--F. If the link between Router A and C goes down. Router A then can immediately send the packets destined to F, to router B, but this will not solve the problem. Since the link just got down and ISIS topology is unaware of the change. If the packets arrive at Router B, Router B will still have old routing information and will still have the entry to route to F via A. Hence packets will be looped between B and A till the point topology converges.
To solve this problem, tunnel the packets to Router D from Router A. Router D never used path via Router A to go to F. Now when the link between Router A and C fails, immediatey without any convergence the traffic destined to router F is sent to Router D via Tunnel. Now Router D is unaware of any such change in topology when it gets the tunnelled traffic from Router A destined to Router F, it forwards the packets via its normal routing logic. So traffic flow remains unaffected and meanwhile the topology can reconverge.
Configure
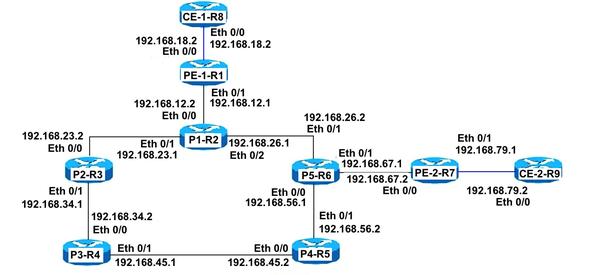
Network Diagram
The topology for the MPLS Layer 3 Vpn with Remote LFA:
Acronym
CE = Customer Edge Router
PE = Provider Edger Router
P = Provider Router
Loopback used is 192.168.255.X, where X Router Number. For example, if R1 is under consideration, then loopback is 192.168.255.1.
Configurations
CPE-1-R8
#Basic CE configuration with the use of a default route:
interface Ethernet0/0
ip address 192.168.18.8 255.255.255.0
!
!
ip route 0.0.0.0 0.0.0.0 192.168.18.1
!
!
CPE-2-R8
#Basic CE configuration with the use of a default route.
interface Ethernet0/0
ip address 192.168.79.9 255.255.255.0
!
!
ip route 0.0.0.0 0.0.0.0 192.168.79.7
!
!
PE-1-R1
# PE Configuration
interface Loopback1
ip address 192.168.255.1 255.255.255.255
ip router isis TAC
!
interface Ethernet0/0
vrf forwarding A
ip address 192.168.18.1 255.255.255.0
!
# ISIS Interface must be point-to-point
interface Ethernet0/1
ip address 192.168.12.1 255.255.255.0
ip router isis TAC
mpls ip
isis circuit-type level-2-only
isis network point-to-point
!
!
# Configuring ISIS remote LFA
router isis TAC
net 49.0000.0000.0001.00
is-type level-2-only
metric-style wide
fast-reroute per-prefix level-2 all
fast-reroute remote-lfa level-2 mpls-ldp
mpls ldp autoconfig level-2
!
# BGP Vpnv4 peering with PE-2-R7
router bgp 65000
bgp log-neighbor-changes
no bgp default ipv4-unicast
neighbor 192.168.255.7 remote-as 65000
neighbor 192.168.255.7 update-source Loopback1
!
address-family ipv4
exit-address-family
!
address-family vpnv4
neighbor 192.168.255.7 activate
neighbor 192.168.255.7 send-community both
exit-address-family
!
address-family ipv4 vrf A
redistribute connected
exit-address-family
!
P1-R2
# P Configuration
interface Loopback1
ip address 192.168.255.2 255.255.255.255
ip router isis TAC
!
# ISIS Interface must be point-to-point
interface Ethernet0/0
ip address 192.168.12.2 255.255.255.0
ip router isis TAC
mpls ip
isis circuit-type level-2-only
isis network point-to-point
!
interface Ethernet0/1
ip address 192.168.23.2 255.255.255.0
ip router isis TAC
mpls ip
isis circuit-type level-2-only
isis network point-to-point
!
interface Ethernet0/2
ip address 192.168.26.2 255.255.255.0
ip router isis TAC
mpls ip
isis circuit-type level-2-only
isis network point-to-point
!
!
# Configuring ISIS remote LFA
router isis TAC
net 49.0000.0000.0002.00
is-type level-2-only
metric-style wide
fast-reroute per-prefix level-2 all
fast-reroute remote-lfa level-2 mpls-ldp
!
P2-R3
# P Configuration
interface Loopback1
ip address 192.168.255.3 255.255.255.255
ip router isis TAC
!
# ISIS Interface must be point-to-point
interface Ethernet0/0
ip address 192.168.23.3 255.255.255.0
ip router isis TAC
mpls ip
isis circuit-type level-2-only
isis network point-to-point
!
interface Ethernet0/1
ip address 192.168.34.3 255.255.255.0
ip router isis TAC
mpls ip
isis circuit-type level-2-only
isis network point-to-point
!
!
# Configuring ISIS remote LFA
router isis TAC
net 49.0000.0000.0003.00
is-type level-2-only
metric-style wide
fast-reroute per-prefix level-2 all
fast-reroute remote-lfa level-2 mpls-ldp
!
P3-R4
# P Configuration
interface Loopback1
ip address 192.168.255.4 255.255.255.255
ip router isis TAC
!
# ISIS Interface must be point-to-point
interface Ethernet0/0
ip address 192.168.34.4 255.255.255.0
ip router isis TAC
mpls ip
isis circuit-type level-2-only
isis network point-to-point
!
interface Ethernet0/1
ip address 192.168.45.4 255.255.255.0
ip router isis TAC
mpls ip
isis circuit-type level-2-only
isis network point-to-point
!
!
# Configuring ISIS remote LFA
router isis TAC
net 49.0000.0000.0004.00
is-type level-2-only
metric-style wide
fast-reroute per-prefix level-2 all
fast-reroute remote-lfa level-2 mpls-ldp
P4-R5
# P Configuration
interface Loopback1
ip address 192.168.255.5 255.255.255.255
ip router isis TAC
!
# ISIS Interface must be point-to-point
interface Ethernet0/0
ip address 192.168.45.5 255.255.255.0
ip router isis TAC
mpls ip
isis circuit-type level-2-only
isis network point-to-point
!
interface Ethernet0/1
ip address 192.168.56.5 255.255.255.0
ip router isis TAC
mpls ip
isis circuit-type level-2-only
isis network point-to-point
!
!
# Configuring ISIS remote LFA
router isis TAC
net 49.0000.0000.0005.00
is-type level-2-only
metric-style wide
fast-reroute per-prefix level-2 all
fast-reroute remote-lfa level-2 mpls-ldp
P5-R6
# P Configuration
interface Loopback1
ip address 192.168.255.6 255.255.255.255
ip router isis TAC
!
# ISIS Interface must be point-to-point
interface Ethernet0/0
ip address 192.168.56.6 255.255.255.0
ip router isis TAC
mpls ip
isis circuit-type level-2-only
isis network point-to-point
!
interface Ethernet0/1
ip address 192.168.26.6 255.255.255.0
ip router isis TAC
mpls ip
isis circuit-type level-2-only
isis network point-to-point
!
interface Ethernet0/2
ip address 192.168.67.6 255.255.255.0
ip router isis TAC
mpls ip
isis circuit-type level-2-only
isis network point-to-point
!
!
# Configuring ISIS remote LFA
router isis TAC
net 49.0000.0000.0006.00
is-type level-2-only
metric-style wide
fast-reroute per-prefix level-2 all
fast-reroute remote-lfa level-2 mpls-ldp
!
PE-2-R7
# PE Configuration
interface Loopback1
ip address 192.168.255.7 255.255.255.255
ip router isis TAC
!
# ISIS Interface must be point-to-point
interface Ethernet0/0
ip address 192.168.67.7 255.255.255.0
ip router isis TAC
mpls ip
isis circuit-type level-2-only
isis network point-to-point
!
interface Ethernet0/1
vrf forwarding A
ip address 192.168.79.7 255.255.255.0
!
!
# Configuring ISIS remote LFA
router isis TAC
net 49.0000.0000.0007.00
is-type level-2-only
metric-style wide
fast-reroute per-prefix level-2 all
fast-reroute remote-lfa level-2 mpls-ldp
!
!
# BGP Vpnv4 peering with PE-1-R1
router bgp 65000
bgp log-neighbor-changes
no bgp default ipv4-unicast
neighbor 192.168.255.1 remote-as 65000
neighbor 192.168.255.1 update-source Loopback1
!
address-family ipv4
exit-address-family
!
address-family vpnv4
neighbor 192.168.255.1 activate
neighbor 192.168.255.1 send-community both
exit-address-family
!
address-family ipv4 vrf A
redistribute connected
exit-address-family
!
Verify
Use this section in order to confirm that your configuration works properly.
P1-R2
The command show isis fast-reroute remote-lfa tunnels displays the remote LFA tunnels built on the router:
P1-R2#show isis fast-reroute remote-lfa tunnels
Tag TAC - Fast-Reroute Remote-LFA Tunnels: MPLS-Remote-Lfa1: use Et0/2, nexthop 192.168.26.6, end point 192.168.255.5
MPLS-Remote-Lfa2: use Et0/1, nexthop 192.168.23.3, end point 192.168.255.4
P2-R3
P2-R3#show isis fast-reroute remote-lfa tunnels
Tag TAC - Fast-Reroute Remote-LFA Tunnels: MPLS-Remote-Lfa1: use Et0/1, nexthop 192.168.34.4, end point 192.168.255.5
MPLS-Remote-Lfa2: use Et0/0, nexthop 192.168.23.2, end point 192.168.255.6
P3-R4
P3-R4#show isis fast-reroute remote-lfa tunnels
Tag TAC - Fast-Reroute Remote-LFA Tunnels: MPLS-Remote-Lfa1: use Et0/1, nexthop 192.168.45.5, end point 192.168.255.6
MPLS-Remote-Lfa2: use Et0/0, nexthop 192.168.34.3, end point 192.168.255.2
P4-R5
P4-R5#show isis fast-reroute remote-lfa tunnels
Tag TAC - Fast-Reroute Remote-LFA Tunnels: MPLS-Remote-Lfa1: use Et0/0, nexthop 192.168.45.4, end point 192.168.255.3
MPLS-Remote-Lfa2: use Et0/1, nexthop 192.168.56.6, end point 192.168.255.2
P5-R6
P5-R6#show isis fast-reroute remote-lfa tunnels
Tag TAC - Fast-Reroute Remote-LFA Tunnels: MPLS-Remote-Lfa1: use Et0/0, nexthop 192.168.56.5, end point 192.168.255.4
MPLS-Remote-Lfa2: use Et0/1, nexthop 192.168.26.2, end point 192.168.255.3
Failure in core scenario, traffic flow in core when LFA is configured.
Before inducing a link failure, If you check on P-1-R2 you would see already there is a targeted LDP session formed between P-1-R2 and P-5-R4 as a backup path due to RLFA. Without RLFA the routing protocol has to detect the failure and needs to reconverge.
P-1-R2#show ip route repair-paths 192.168.255.7 Routing entry for 192.168.255.7/32 Known via "isis", distance 115, metric 30, type level-c Redistributing via isis TAC Last update from 192.168.26.6 on Ethernet0/2, 02:23:31 ago Routing Descriptor Blocks: * 192.168.26.6, from 192.168.255.7, 02:23:31 ago, via Ethernet0/2 Route metric is 30, traffic share count is 1 Repair Path: 192.168.255.4, via MPLS-Remote-Lfa6 [RPR]192.168.255.4, from 192.168.255.7, 02:23:31 ago, via MPLS-Remote-Lfa6 Route metric is 20, traffic share count is 1
P-1-R2#show mpls ldp neighbor 192.168.255.4 Peer LDP Ident: 192.168.255.4:0; Local LDP Ident 192.168.255.2:0 TCP connection: 192.168.255.4.32391 - 192.168.255.2.646 State: Oper; Msgs sent/rcvd: 184/183; Downstream Up time: 02:26:09 LDP discovery sources: Targeted Hello 192.168.255.2 -> 192.168.255.4, active, passive Addresses bound to peer LDP Ident: 192.168.255.4 192.168.34.4 192.168.45.4
It can be observed here that repair path to PE2-R7 in routing table is via 192.168.255.4 (P3-R4). As a part of Remote LFA logic a tunnel is prebuilt to P3-R4. Hence, whenever the primary link fails, immediately packets are tunnelled to P3-R4 and this happens at line card level as the entry is pre-built. So there is no traffic disruption and forwarding is seamless. The ISIS protocol then can converge based upon it's configured timers.
P1-R2 router does not need to look for backup path, as already there is a CEF entry formed ie via P2-R3 prior to the failure.
P1-R2#show ip cef 192.168.255.7
nexthop 192.168.26.6 Ethernet0/2 label [25|26]
repair: attached-nexthop 192.168.255.4 MPLS-Remote-Lfa6
This diagram demostrates the exact behaviour explained previously:

P1-R2
For verification, a continuous ping is done from CE-1-R8 to CE-2-R9 after it recreates a failure scenario by shutting down the core link (Eth 0/2) between P1-R2 and P5-R6, not even a single drop is observed in the test environment.
CE-1-R8#ping 192.168.79.9
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.79.9, timeout is 2 seconds:
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!! <Ouput Snipped> !!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
!!!!!!!!!!
Success rate is 100 percent (149320/149320), round-trip min/avg/max = 1/1/18 ms
Troubleshoot
There is currently no specific troubleshooting information available for this configuration.
Contributed by Cisco Engineers
- Lijesh N CCisco TAC Engineer
- Lalit VermaCisco TAC Engineer
Contact Cisco
- Open a Support Case

- (Requires a Cisco Service Contract)
 Feedback
Feedback