Configure Umbrella SIG Tunnels for Active/Backup or Active/Active Scenarios
Available Languages
Download Options
Bias-Free Language
The documentation set for this product strives to use bias-free language. For the purposes of this documentation set, bias-free is defined as language that does not imply discrimination based on age, disability, gender, racial identity, ethnic identity, sexual orientation, socioeconomic status, and intersectionality. Exceptions may be present in the documentation due to language that is hardcoded in the user interfaces of the product software, language used based on RFP documentation, or language that is used by a referenced third-party product. Learn more about how Cisco is using Inclusive Language.
Contents
Introduction
This document describes how to configure Cisco Umbrella Secure Internet Gateway (SIG) tunnels with IPsec in both Active/Active and Active/Standby.
Prerequisites
Requirements
Cisco recommends knowledge of these topics:
- Cisco
Umbrella - IPsec negotiation
-
Cisco Software-defined Wide Area Network (SD-WAN)
Components Used
The information in this document is based on these software and hardware versions:
- Cisco vManage version 20.4.2
- Cisco WAN Edge Router C1117-4PW* version 17.4.2
The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, ensure that you understand the potential impact of any command.
Background Information
Cisco Umbrella SIG Overview
Cisco Umbrella is a cloud-delivered security service that brings essential functions together.
Umbrella unifies secure web gateway, DNS security, cloud-delivered firewall, cloud access security broker functionality, and threat intelligence.
Deep inspection and control ensure compliance with acceptable-use web policies and protect against internet threats.
SD-WAN routers can integrate with Secure Internet Gateways (SIG) which do the majority of the processing to secure enterprise traffic.
When the SIG is set up, all client traffic, based on routes or policy, is forwarded to the SIG.
Umbrella SIG Tunnel Bandwidth Limitation
Each IPsec IKEv2 tunnel to the Umbrella head-end is limited to approximately 250 Mbps, so if multiple tunnels are created and load balance the traffic, they overcome such limitations in case a higher bandwidth is required.
Up to four High Availability tunnel pairs can be created.
Get your Cisco Umbrella Portal Information
In order to proceed with the SIG integration, an Umbrella Account with SIG essentials package is needed.
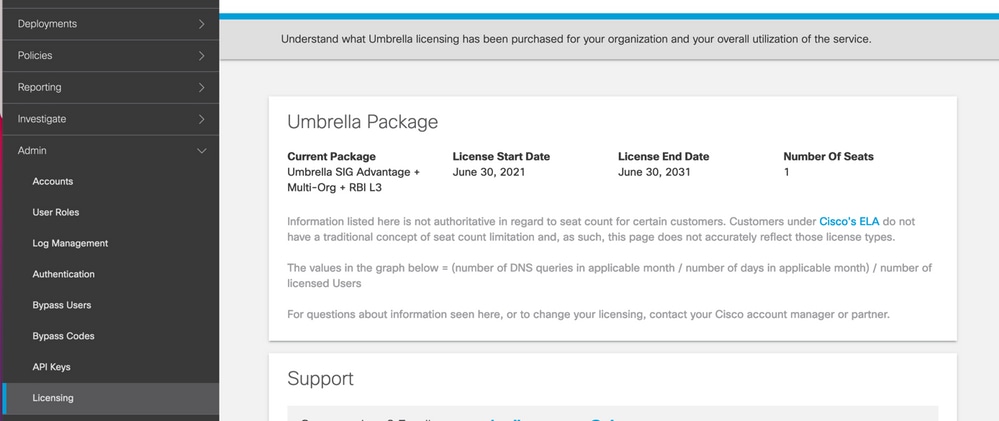
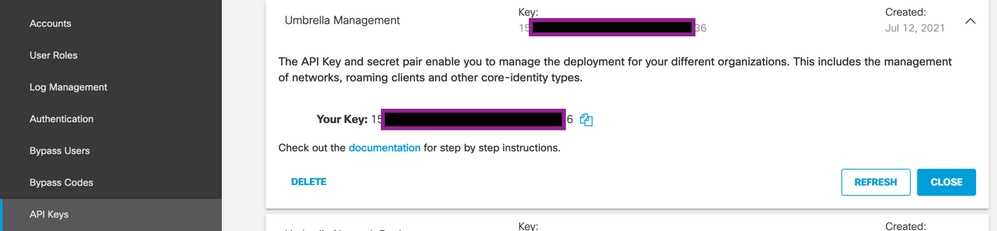
Get the Key and the Secret Key
The key and secret key can be generated at the moment you get the Umbrella Management API KEY (this key is under 'Legacy Keys'). If you do not remember or did not save the secret key, click refresh.
Caution: If the refresh button is clicked, an update for these keys on all devices is needed, the update is not recommended if there are devices in use.
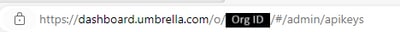
Get Your Organization ID
The organization ID can be easily obtained when you log in to Umbrella from the browser address bar.
Create Umbrella SIG Tunnels with Active/Backup Scenario
Note: IPsec/GRE Tunnel Routing and Load-Balancing Using ECMP: This feature is available in vManage 20.4.1 and onwards, it allows you to use the SIG template to steer application traffic to Cisco Umbrella or a Third-party SIG Provider
Note: Support for Zscaler Automatic Provisioning: This feature is available on vManage 20.5.1 and onwards, this automates the provisioning of tunnels from Cisco SD-WAN routers to Zscaler, with the use of Zscaler partner API credentials.
To configure the SIG automatic tunnels, it is required to create/update a few templates:
- Create a SIG Credentials feature template.
- Create two loopback interfaces in order to link the SIG tunnels (Only applicable with more than one
Activetunnel at the same time -Active/Activescenario). - Create a SIG feature template.
- Edit service-side VPN Template to inject a
Service Route.
Note: Make sure UDP 4500 and 500 ports are allowed from any upstream device.
The template configurations change with the Active/Backup and the Active/Active scenarios for which both scenarios are explained and exposed separately.
Step 1. Create a SIG Credentials Feature Template.
Go to the feature template and click Edit.
Under the section of Additional templates, click Cisco SIG Credentials. The option is shown in the image.
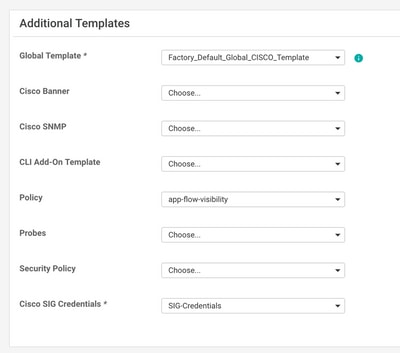
Give a name and description to the template.
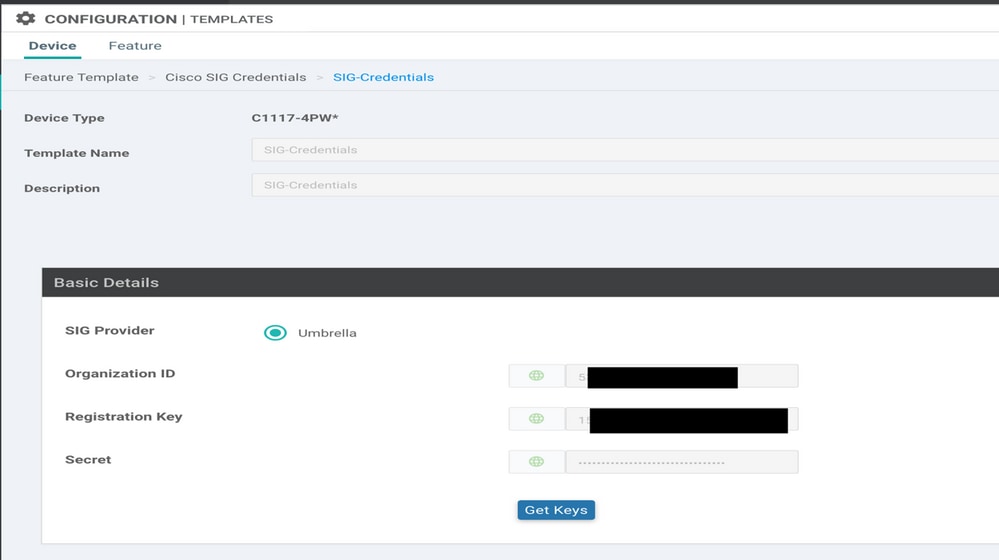
Step 2. Create a SIG Feature Template.
Navigate to the feature template and, under the section Transport & Management VPN select the Cisco Secure Internet Gateway feature template.
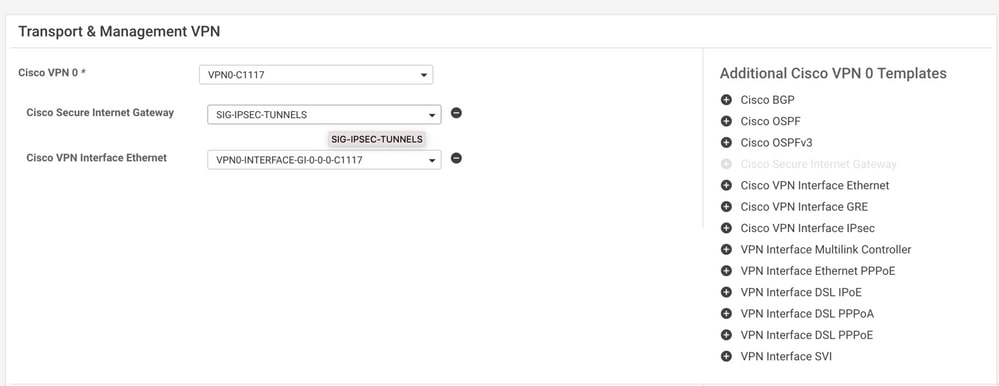
Give a name and description to the template.
Step 3. Select Your SIG Provider for Primary Tunnel.
Click Add Tunnel.
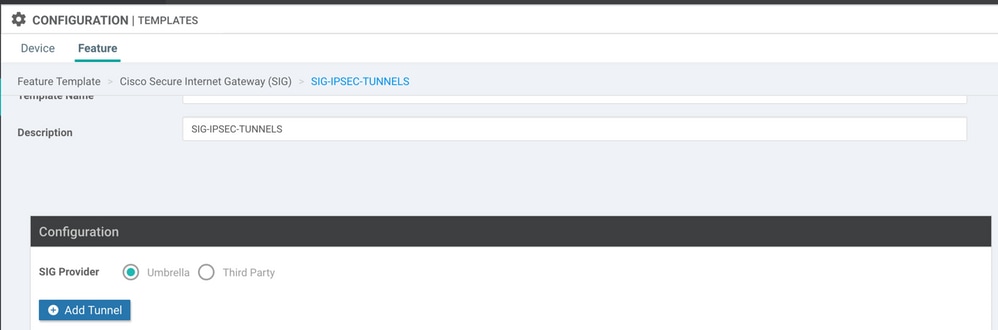
Configure the basic details and keep Data-Center as Primary, then click Add.
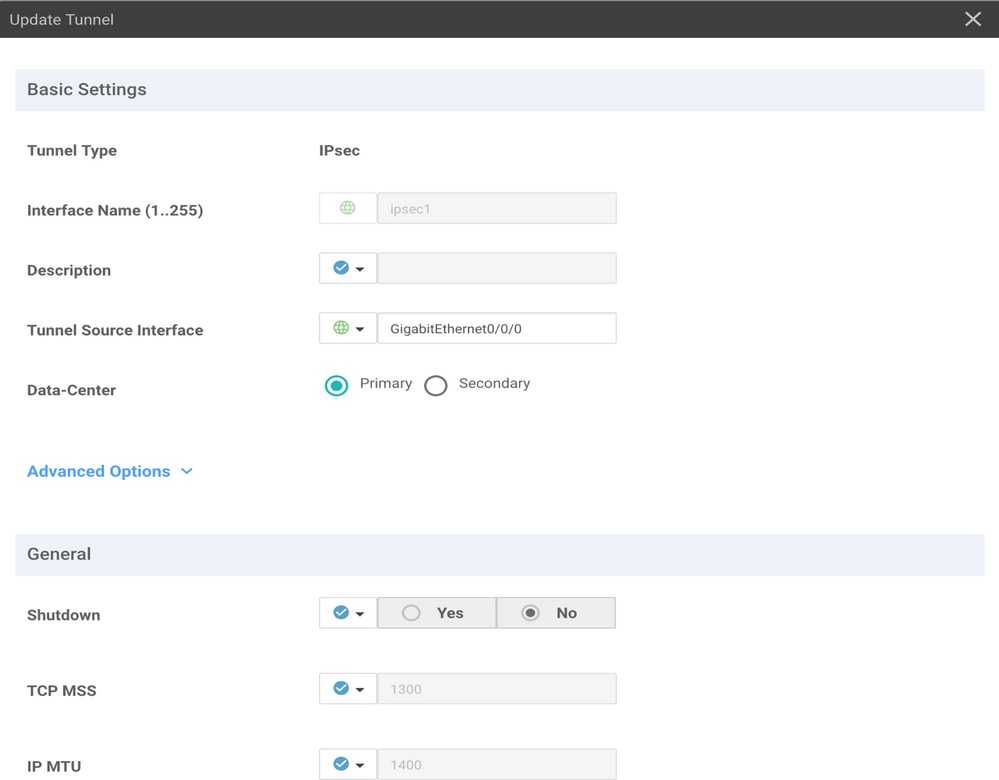
Step 4. Add the Secondary Tunnel.
Add a second tunnel configuration, use Data-Center as Secondary this time, and the interface name as ipsec2.
vManage configuration appears as shown here:
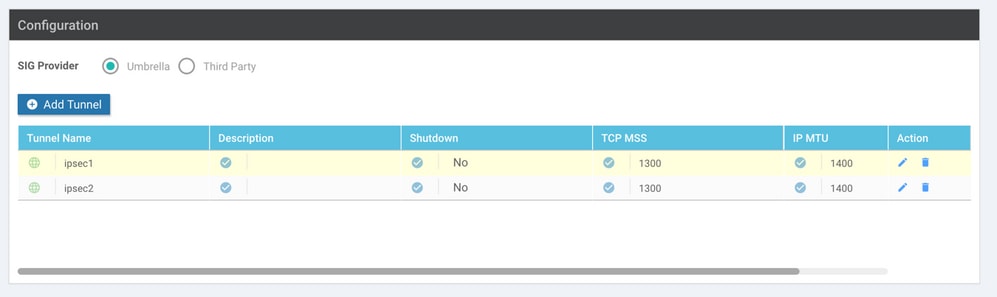
Step 5. Create One High Availability Pair.
Within the High Availability section, select the ipsec1 as Active and the ipsec2 tunnel as Backup.
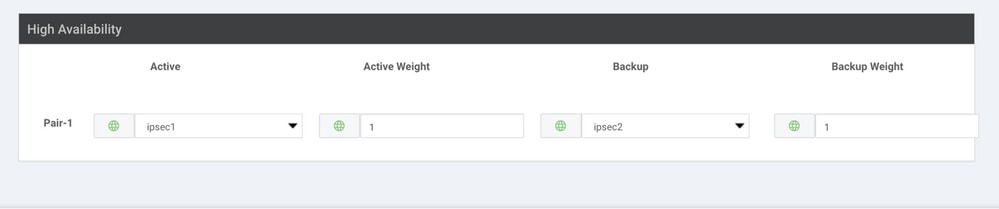
Note: Up to 4 High Availability tunnel pairs and a maximum of 4 active tunnels can be created at the same time.
Step 6. Edit Service-side VPN Template to Inject a Service Route.
Navigate to the Service VPN section and, within the Service VPN template, navigate to the section Service Route and add a 0.0.0.0 with SIG Service Route. For this document, the VRF/VPN 10 is used.
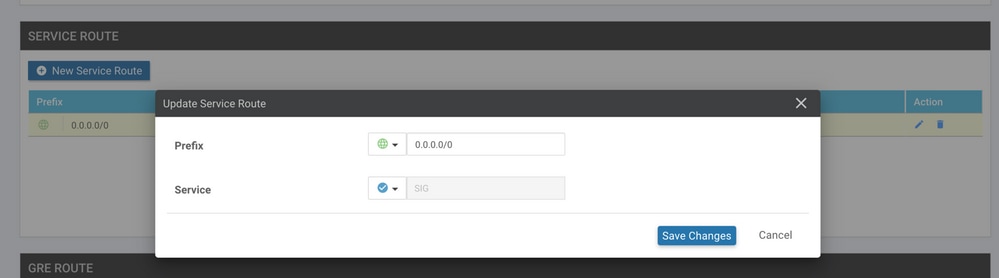
The 0.0.0.0 SIG route is displayed as shown here.
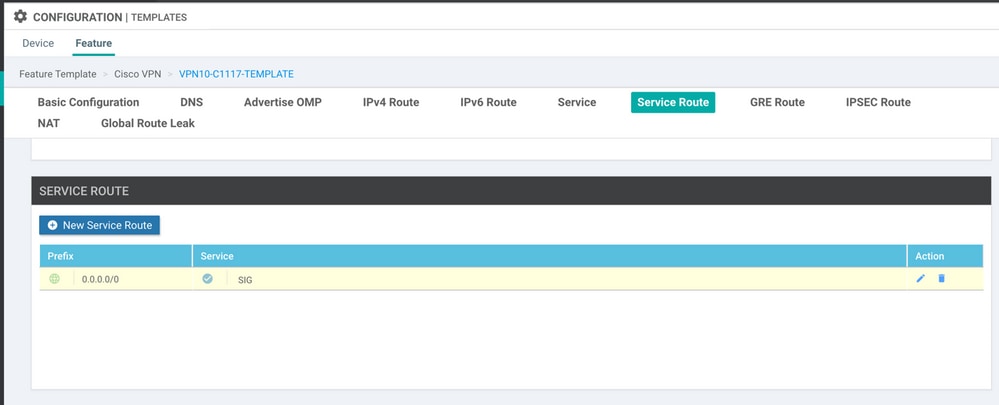
Note: For the Service traffic to actually go out, NAT has to be configured in the WAN interface.
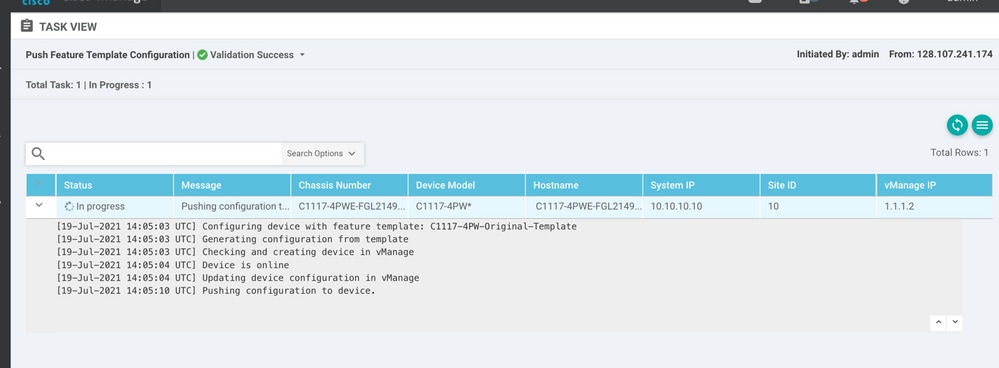
Attach this template to the device and push the configuration:
WAN Edge Router Configuration for Active/Backup Scenario
system
host-name <HOSTNAME>
system-ip <SYSTEM-IP>
overlay-id 1
site-id <SITE-ID>
sp-organization-name <ORG-NAME>
organization-name <SP-ORG-NAME>
vbond <VBOND-IP> port 12346
!
secure-internet-gateway
umbrella org-id <UMBRELLA-ORG-ID>
umbrella api-key <UMBRELLA-API-KEY-INFO>
umbrella api-secret <UMBRELLA-SECRET-INFO>
!
sdwan
service sig vrf global
ha-pairs
interface-pair Tunnel100001 active-interface-weight 1 Tunnel100002 backup-interface-weight 1
!
!
interface GigabitEthernet0/0/0
tunnel-interface
encapsulation ipsec weight 1
no border
color biz-internet
no last-resort-circuit
no low-bandwidth-link
no vbond-as-stun-server
vmanage-connection-preference 5
port-hop
carrier default
nat-refresh-interval 5
hello-interval 1000
hello-tolerance 12
allow-service all
no allow-service bgp
allow-service dhcp
allow-service dns
allow-service icmp
no allow-service sshd
no allow-service netconf
no allow-service ntp
no allow-service ospf
no allow-service stun
allow-service https
no allow-service snmp
no allow-service bfd
exit
exit
interface Tunnel100001
tunnel-options tunnel-set secure-internet-gateway-umbrella tunnel-dc-preference primary-dc source-interface GigabitEthernet0/0/0
exit
interface Tunnel100002
tunnel-options tunnel-set secure-internet-gateway-umbrella tunnel-dc-preference secondary-dc source-interface GigabitEthernet0/0/0
exit
appqoe
no tcpopt enable
!
security
ipsec
rekey 86400
replay-window 512
authentication-type sha1-hmac ah-sha1-hmac
!
!
service tcp-keepalives-in
service tcp-keepalives-out
no service tcp-small-servers
no service udp-small-servers
hostname <DEVICE-HOSTNAME>
username admin privilege 15 secret 9 <SECRET-PASSWORD>
vrf definition 10
rd 1:10
address-family ipv4
route-target export 1:10
route-target import 1:10
exit-address-family
!
address-family ipv6
exit-address-family
!
!
vrf definition Mgmt-intf
description Transport VPN
rd 1:512
address-family ipv4
route-target export 1:512
route-target import 1:512
exit-address-family
!
address-family ipv6
exit-address-family
!
!
ip sdwan route vrf 10 0.0.0.0/0 service sig
no ip http server
no ip http secure-server
no ip http ctc authentication
ip nat settings central-policy
vlan 10
exit
interface GigabitEthernet0/0/0
no shutdown
arp timeout 1200
ip address dhcp client-id GigabitEthernet0/0/0
no ip redirects
ip dhcp client default-router distance 1
ip mtu 1500
load-interval 30
mtu 1500
exit
interface GigabitEthernet0/1/0
switchport access vlan 10
switchport mode access
no shutdown
exit
interface GigabitEthernet0/1/1
switchport mode access
no shutdown
exit
interface Vlan10
no shutdown
arp timeout 1200
vrf forwarding 10
ip address <VLAN-IP-ADDRESS> <MASK>
ip mtu 1500
ip nbar protocol-discovery
exit
interface Tunnel0
no shutdown
ip unnumbered GigabitEthernet0/0/0
no ip redirects
ipv6 unnumbered GigabitEthernet0/0/0
no ipv6 redirects
tunnel source GigabitEthernet0/0/0
tunnel mode sdwan
exit
interface Tunnel100001
no shutdown
ip unnumbered GigabitEthernet0/0/0
ip mtu 1400
tunnel source GigabitEthernet0/0/0
tunnel destination dynamic
tunnel mode ipsec ipv4
tunnel protection ipsec profile if-ipsec1-ipsec-profile
tunnel vrf multiplexing
exit
interface Tunnel100002
no shutdown
ip unnumbered GigabitEthernet0/0/0
ip mtu 1400
tunnel source GigabitEthernet0/0/0
tunnel destination dynamic
tunnel mode ipsec ipv4
tunnel protection ipsec profile if-ipsec2-ipsec-profile
tunnel vrf multiplexing
exit
clock timezone UTC 0 0
logging persistent size 104857600 filesize 10485760
logging buffered 512000
logging console
no logging rate-limit
aaa authentication log in default local
aaa authorization exec default local
aaa session-id common
mac address-table aging-time 300
no crypto ikev2 diagnose error
crypto ikev2 policy policy1-global
proposal p1-global
!
crypto ikev2 profile if-ipsec1-ikev2-profile
no config-exchange request
dpd 10 3 on-demand
dynamic
lifetime 86400
!
crypto ikev2 profile if-ipsec2-ikev2-profile
no config-exchange request
dpd 10 3 on-demand
dynamic
lifetime 86400
!
crypto ikev2 proposal p1-global
encryption aes-cbc-128 aes-cbc-256
group 14 15 16
integrity sha1 sha256 sha384 sha512
!
crypto ipsec transform-set if-ipsec1-ikev2-transform esp-gcm 256
mode tunnel
!
crypto ipsec transform-set if-ipsec2-ikev2-transform esp-gcm 256
mode tunnel
!
crypto ipsec profile if-ipsec1-ipsec-profile
set ikev2-profile if-ipsec1-ikev2-profile
set transform-set if-ipsec1-ikev2-transform
set security-association lifetime kilobytes disable
set security-association lifetime seconds 3600
set security-association replay window-size 512
!
crypto ipsec profile if-ipsec2-ipsec-profile
set ikev2-profile if-ipsec2-ikev2-profile
set transform-set if-ipsec2-ikev2-transform
set security-association lifetime kilobytes disable
set security-association lifetime seconds 3600
set security-association replay window-size 512
!
no crypto isakmp diagnose error
no network-clock revertive
Create Umbrella SIG Tunnels with Active/Active Scenario
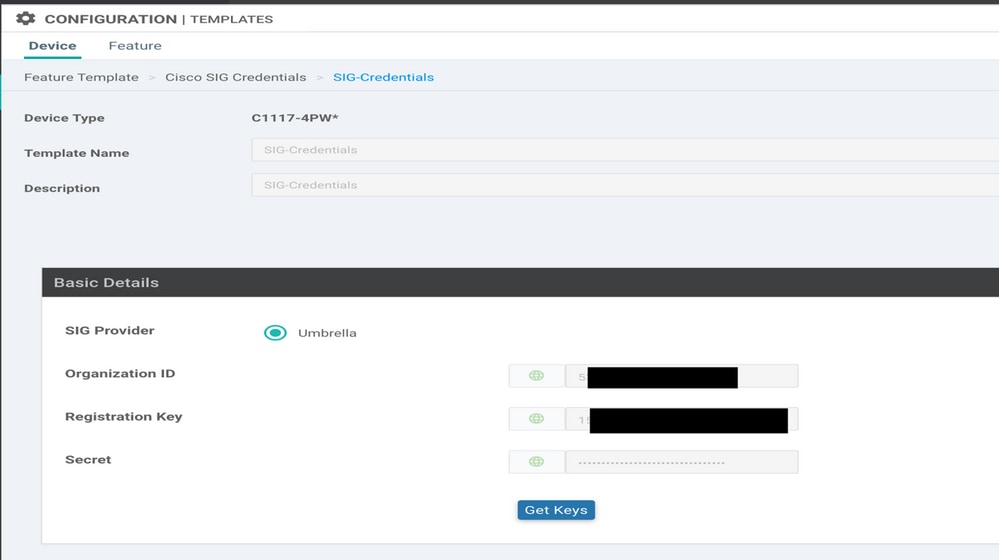
Step 1. Create a SIG Credentials Feature Template.
Navigate to the feature template and click Edit
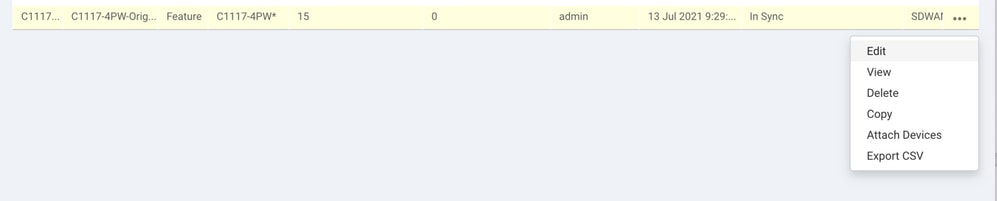
Under the section of Additional templates, select Cisco SIG Credentials. The option is shown on the image.
Give a name and description to the template.
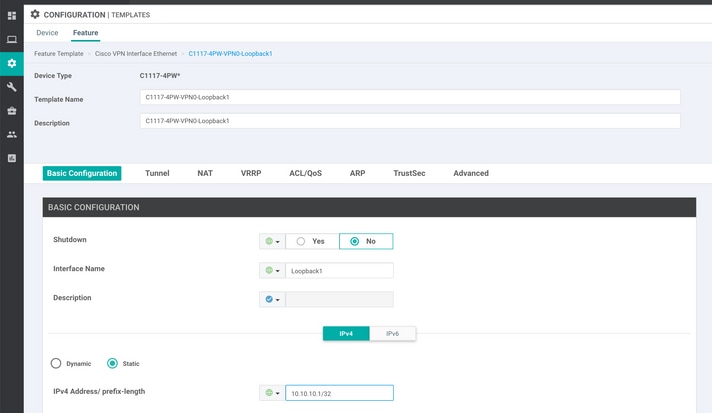
Step 2. Create Two Loopback Interfaces to Link the SIG Tunnels.
Note: Create a Loopback interface for each SIG tunnel configured in active mode, this is needed because each tunnel needs a unique IKE ID.
Note: This scenario is Active/Active, therefore two Loopbacks are created.
Configure the interface name and IPv4 address for the Loopback.
Note: The IP address configured for the loopback is a dummy address.
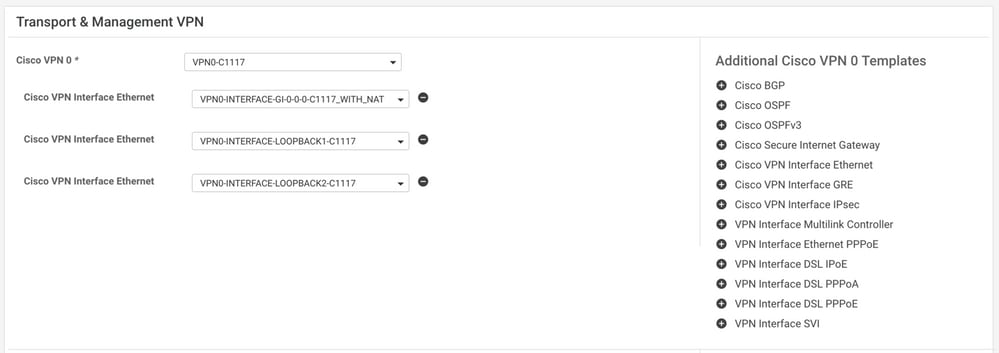
Create the second Loopback template and attach it to the device template. The device template must have two Loopback templates attached:
Step 3. Create a SIG Feature Template.
Navigate to the SIG feature template and, under the section Transport & Management VPN select Cisco Secure Internet Gateway
Step 4. Select the SIG Provider for the Primary Tunnel.
Click Add Tunnel.
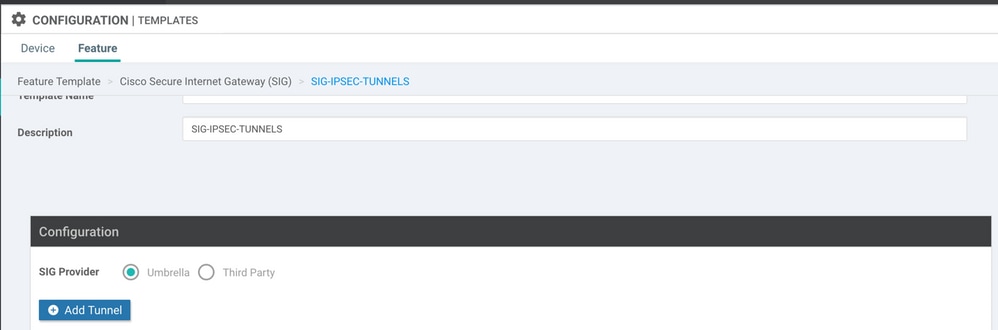
Configure the basic details and keep Data-Center as Primary.
Note: The Tunnel Source Interface parameter is the Loopback (for this document Loopback1) and as Tunnel Route-via Interface the physical interface (for this document GigabitEthernet0/0/0)
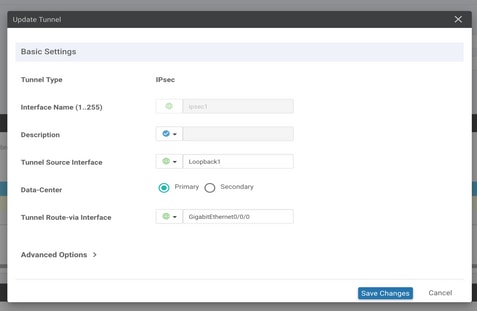
Step 5. Add the Secondary Tunnel.
Add a second tunnel configuration, use Data-Center as Primary as well, and the interface name as ipsec2.
vManage configuration appears as shown here:
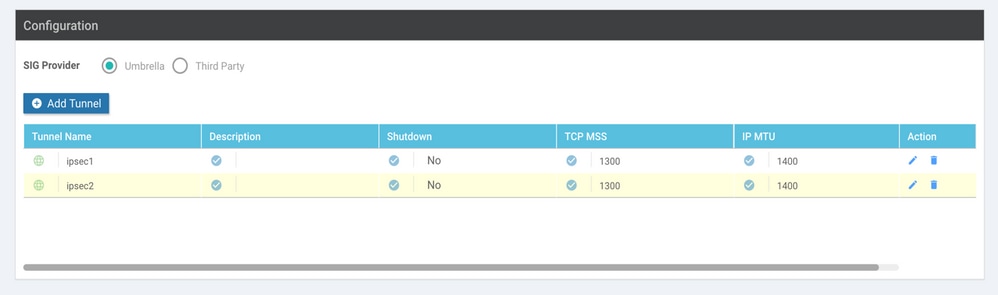
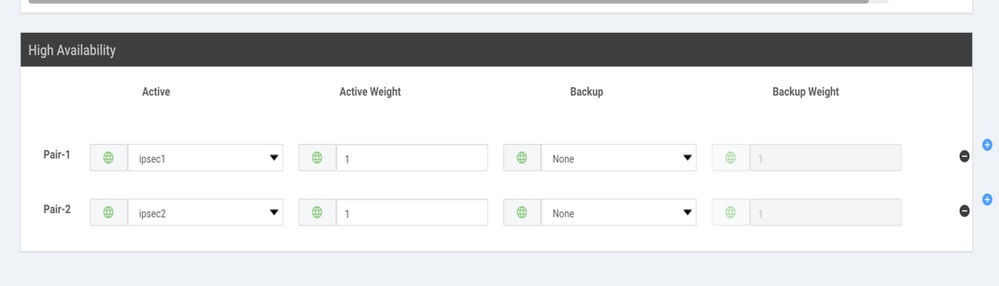
Step 6. Create Two High Availability Pairs.
Within the High Availability section, create two High Availability pairs.
- In the first HA pair, select the ipsec1 as Active and select
Nonefor backup. - In the second HA pair, select the ipsec2 as Active select
Noneand for backup.
The vManage configuration for High Availability appears as shown:
The device template has the two Loopback templates and the SIG feature template attached as well.
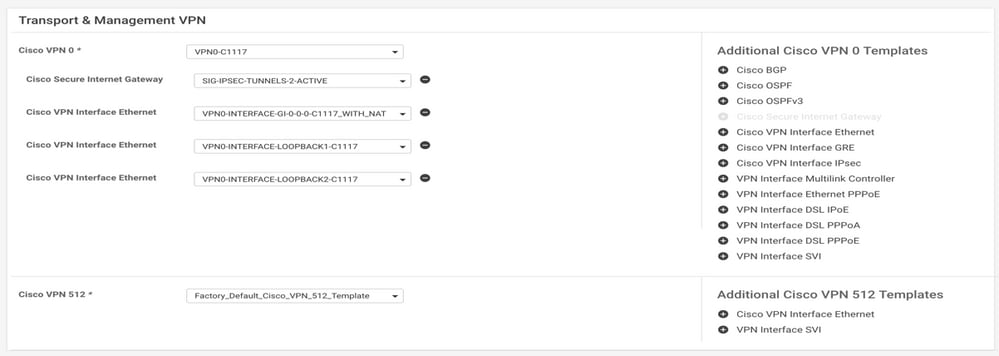
Step 7. Edit Service-side VPN Template to Inject a Service Route.
Navigate to the Service VPN section and within the VPN of service template, navigate to the section Service Route and add a 0.0.0.0 with SIGService Route
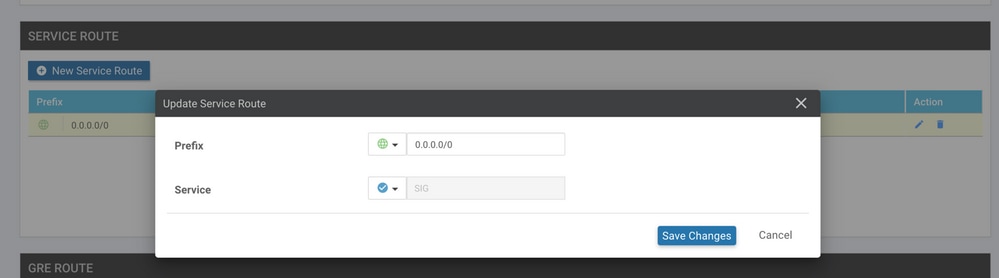
The 0.0.0.0 SIG route appears as shown here.
Note: For the Service traffic to actually go out, NAT has to be configured in the WAN interface.
Attach this template to the device and push the configuration.
WAN Edge Router Configuration for Active/Active Scenario
system
host-name <HOSTNAME>
system-ip <SYSTEM-IP>
overlay-id 1
site-id <SITE-ID>
sp-organization-name <ORG-NAME>
organization-name <SP-ORG-NAME>
vbond <VBOND-IP> port 12346
!
secure-internet-gateway
umbrella org-id <UMBRELLA-ORG-ID>
umbrella api-key <UMBRELLA-API-KEY-INFO>
umbrella api-secret <UMBRELLA-SECRET-INFO>
!
sdwan
service sig vrf global
ha-pairs
interface-pair Tunnel100001 active-interface-weight 1 None backup-interface-weight 1
interface-pair Tunnel100002 active-interface-weight 1 None backup-interface-weight 1
!
interface GigabitEthernet0/0/0
tunnel-interface
encapsulation ipsec weight 1
no border
color biz-internet
no last-resort-circuit
no low-bandwidth-link
no vbond-as-stun-server
vmanage-connection-preference 5
port-hop
carrier default
nat-refresh-interval 5
hello-interval 1000
hello-tolerance 12
allow-service all
no allow-service bgp
allow-service dhcp
allow-service dns
allow-service icmp
no allow-service sshd
no allow-service netconf
no allow-service ntp
no allow-service ospf
no allow-service stun
allow-service https
no allow-service snmp
no allow-service bfd
exit
exit
interface Tunnel100001
tunnel-options tunnel-set secure-internet-gateway-umbrella tunnel-dc-preference primary-dc source-interface Loopback1
exit
interface Tunnel100002
tunnel-options tunnel-set secure-internet-gateway-umbrella tunnel-dc-preference primary-dc source-interface Loopback2
exit
appqoe
no tcpopt enable
!
security
ipsec
rekey 86400
replay-window 512
authentication-type sha1-hmac ah-sha1-hmac
!
!
service tcp-keepalives-in
service tcp-keepalives-out
no service tcp-small-servers
no service udp-small-servers
hostname <DEVICE HOSTNAME>
username admin privilege 15 secret 9 <secret-password>
vrf definition 10
rd 1:10
address-family ipv4
route-target export 1:10
route-target import 1:10
exit-address-family
!
address-family ipv6
exit-address-family
!
!
vrf definition Mgmt-intf
description Transport VPN
rd 1:512
address-family ipv4
route-target export 1:512
route-target import 1:512
exit-address-family
!
address-family ipv6
exit-address-family
!
no ip source-route
ip sdwan route vrf 10 0.0.0.0/0 service sig
ip nat inside source list nat-dia-vpn-hop-access-list interface GigabitEthernet0/0/0 overload
ip nat translation tcp-timeout 3600
ip nat translation udp-timeout 60
ip nat settings central-policy
vlan 10
exit
interface GigabitEthernet0/0/0
no shutdown
arp timeout 1200
ip address dhcp client-id GigabitEthernet0/0/0
no ip redirects
ip dhcp client default-router distance 1
ip mtu 1500
ip nat outside
load-interval 30
mtu 1500
exit
interface GigabitEthernet0/1/0
switchport access vlan 10
switchport mode access
no shutdown
exit
interface Loopback1
no shutdown
arp timeout 1200
ip address 10.20.20.1 255.255.255.255
ip mtu 1500
exit
interface Loopback2
no shutdown
arp timeout 1200
ip address 10.10.10.1 255.255.255.255
ip mtu 1500
exit
interface Vlan10
no shutdown
arp timeout 1200
vrf forwarding 10
ip address 10.1.1.1 255.255.255.252
ip mtu 1500
ip nbar protocol-discovery
exit
interface Tunnel0
no shutdown
ip unnumbered GigabitEthernet0/0/0
no ip redirects
ipv6 unnumbered GigabitEthernet0/0/0
no ipv6 redirects
tunnel source GigabitEthernet0/0/0
tunnel mode sdwan
exit
interface Tunnel100001
no shutdown
ip unnumbered Loopback1
ip mtu 1400
tunnel source Loopback1
tunnel destination dynamic
tunnel mode ipsec ipv4
tunnel protection ipsec profile if-ipsec1-ipsec-profile
tunnel vrf multiplexing
tunnel route-via GigabitEthernet0/0/0 mandatory
exit
interface Tunnel100002
no shutdown
ip unnumbered Loopback2
ip mtu 1400
tunnel source Loopback2
tunnel destination dynamic
tunnel mode ipsec ipv4
tunnel protection ipsec profile if-ipsec2-ipsec-profile
tunnel vrf multiplexing
tunnel route-via GigabitEthernet0/0/0 mandatory
exit
clock timezone UTC 0 0
logging persistent size 104857600 filesize 10485760
logging buffered 512000
logging console
no logging rate-limit
aaa authentication log in default local
aaa authorization exec default local
aaa session-id common
mac address-table aging-time 300
no crypto ikev2 diagnose error
crypto ikev2 policy policy1-global
proposal p1-global
!
crypto ikev2 profile if-ipsec1-ikev2-profile
no config-exchange request
dpd 10 3 on-demand
dynamic
lifetime 86400
!
crypto ikev2 profile if-ipsec2-ikev2-profile
no config-exchange request
dpd 10 3 on-demand
dynamic
lifetime 86400
!
crypto ikev2 proposal p1-global
encryption aes-cbc-128 aes-cbc-256
group 14 15 16
integrity sha1 sha256 sha384 sha512
!
crypto ipsec transform-set if-ipsec1-ikev2-transform esp-gcm 256
mode tunnel
!
crypto ipsec transform-set if-ipsec2-ikev2-transform esp-gcm 256
mode tunnel
!
crypto ipsec profile if-ipsec1-ipsec-profile
set ikev2-profile if-ipsec1-ikev2-profile
set transform-set if-ipsec1-ikev2-transform
set security-association lifetime kilobytes disable
set security-association lifetime seconds 3600
set security-association replay window-size 512
!
crypto ipsec profile if-ipsec2-ipsec-profile
set ikev2-profile if-ipsec2-ikev2-profile
set transform-set if-ipsec2-ikev2-transform
set security-association lifetime kilobytes disable
set security-association lifetime seconds 3600
set security-association replay window-size 512
!
Note: Although this document is Umbrella focused, the same scenarios apply for Azure and Third-party SIG tunnels.
Verify
Verify Active/Backup Scenario
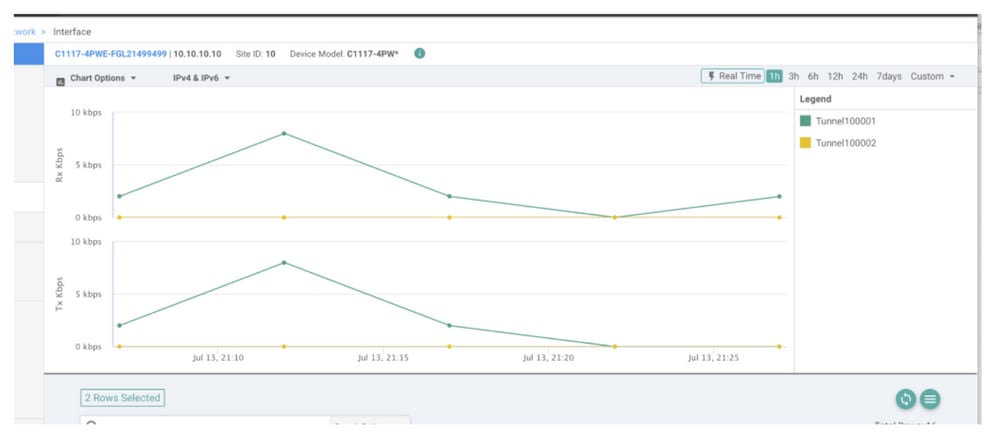
In the vManage, is possible to monitor the status of the SIG IPSec tunnels. Navigate to Monitor > Network, select the WAN edge device desired.
Click the Interfaces tab on the left side; a list of all interfaces in the device is displayed. This includes the ipsec1 and ipsec2 interfaces.
The image shows that the ipsec1 tunnel forwards all the traffic and the ipsec2 does not pass traffic.
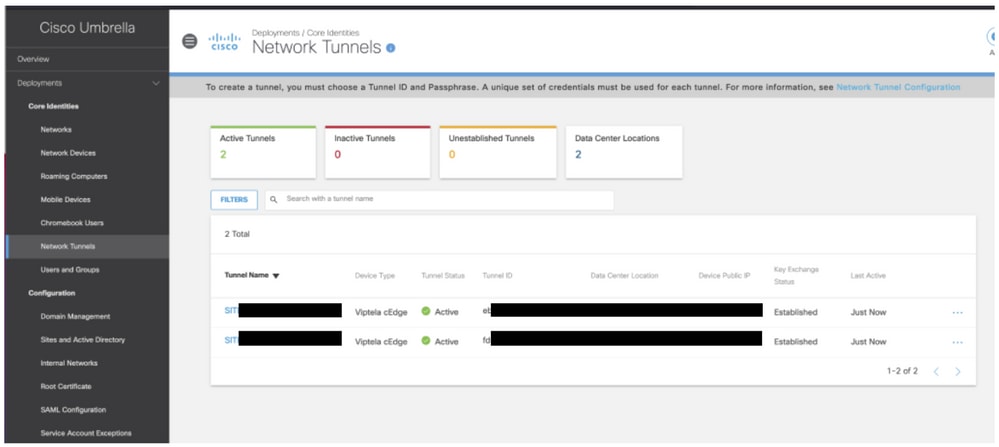
It is also possible to verify the Tunnels on the Cisco Umbrella portal s shown in the image.
Use the show sdwan secure-internet-gateway tunnels command on the CLI in order to display the Tunnels information.
C1117-4PWE-FGL21499499#show sdwan secure-internet-gateway tunnels
API LAST
TUNNEL IF HTTP SUCCESSFUL TUNNEL
NAME TUNNEL ID TUNNEL NAME FSM STATE CODE REQ STATE
---------------------------------------------------------------------------------------------------------------
Tunnel100001 540798313 SITE10SYS10x10x10x10IFTunnel100001 st-tun-create-notif 200 create-tunnel -
Tunnel100002 540798314 SITE10SYS10x10x10x10IFTunnel100002 st-tun-create-notif 200 create-tunnel -
Use the show endpoint-tracker and show ip sla summary commands on the CLI in order to display information on the auto-generated trackers and SLAs.
cEdge_Site1_East_01#show endpoint-tracker
Interface Record Name Status RTT in msecs Probe ID Next Hop
Tunnel100001 #SIGL7#AUTO#TRACKER Up 8 14 None
Tunnel100002 #SIGL7#AUTO#TRACKER Up 2 12 None
cEdge_Site1_East_01#show ip sla summary
IPSLAs Latest Operation Summary
Codes: * active, ^ inactive, ~ pending
All Stats are in milliseconds. Stats with u are in microseconds
ID Type Destination Stats Return Last
Code Run
-----------------------------------------------------------------------
*12 http 10.10.10.10 RTT=6 OK 8 seconds ago
*14 http 10.10.10.10 RTT=17 OK 3 seconds ago Verify Active/Active Scenario
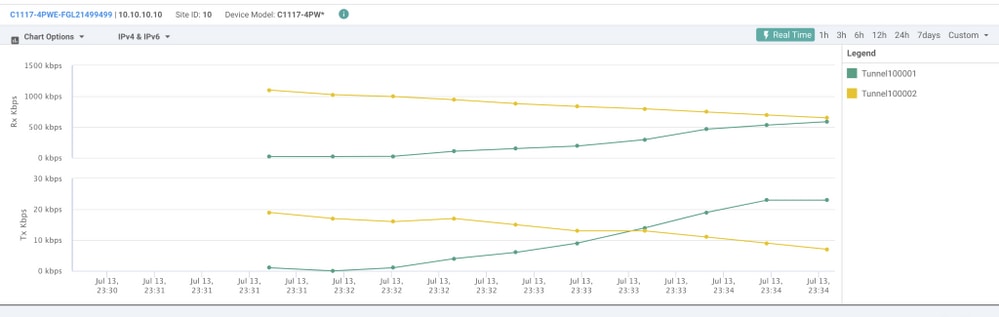
In the vManage is possible to monitor the status of the SIG IPSec tunnels. Navigate to Monitor > Network, select the WAN edge device desired.
Click the Interfaces tab on the left side - and a list of all interfaces in the device is displayed. This includes the ipsec1 and ipsec2 interfaces.
The image shows that both ipsec1 and ipsec2 tunnels forward traffic.
Use the show sdwan secure-internet-gateway tunnels command on the CLI in order to display the Tunnels information.
C1117-4PWE-FGL21499499#show sdwan secure-internet-gateway tunnels
API LAST
TUNNEL IF HTTP SUCCESSFUL TUNNEL
NAME TUNNEL ID TUNNEL NAME FSM STATE CODE REQ STATE
---------------------------------------------------------------------------------------------------------------
Tunnel100001 540798313 SITE10SYS10x10x10x10IFTunnel100001 st-tun-create-notif 200 create-tunnel -
Tunnel100002 540798314 SITE10SYS10x10x10x10IFTunnel100002 st-tun-create-notif 200 create-tunnel -
Use the show endpoint-tracker and show ip sla summary commands on the CLI in order to display information on the auto-generated trackers and SLAs.
cEdge_Site1_East_01#show endpoint-tracker
Interface Record Name Status RTT in msecs Probe ID Next Hop
Tunnel100001 #SIGL7#AUTO#TRACKER Up 8 14 None
Tunnel100002 #SIGL7#AUTO#TRACKER Up 2 12 None
cEdge_Site1_East_01#show ip sla summary
IPSLAs Latest Operation Summary
Codes: * active, ^ inactive, ~ pending
All Stats are in milliseconds. Stats with u are in microseconds
ID Type Destination Stats Return Last
Code Run
-----------------------------------------------------------------------
*12 http 10.10.10.10 RTT=6 OK 8 seconds ago
*14 http 10.10.10.10 RTT=17 OK 3 seconds ago Related Information
Revision History
| Revision | Publish Date | Comments |
|---|---|---|
6.0 |
22-Nov-2023 |
Recertification |
4.0 |
30-Dec-2021 |
Minor changes |
3.0 |
23-Dec-2021 |
Adding extra info |
2.0 |
16-Nov-2021 |
Initial Release |
1.0 |
16-Nov-2021 |
Initial Release |
Contributed by Cisco Engineers
- Diana Laura SerranoCisco TAC Engineer
- Edited by Amanda Nava ZarateCisco TAC Engineer
Contact Cisco
- Open a Support Case

- (Requires a Cisco Service Contract)
 Feedback
Feedback