Configure SSH on Tty Lines with Menu Option on Terminal Server
Available Languages
Download Options
Bias-Free Language
The documentation set for this product strives to use bias-free language. For the purposes of this documentation set, bias-free is defined as language that does not imply discrimination based on age, disability, gender, racial identity, ethnic identity, sexual orientation, socioeconomic status, and intersectionality. Exceptions may be present in the documentation due to language that is hardcoded in the user interfaces of the product software, language used based on RFP documentation, or language that is used by a referenced third-party product. Learn more about how Cisco is using Inclusive Language.
Contents
Introduction
This document describes how to configure a Cisco router as a terminal server with the use of Secure Shell (SSH) for terminal line access with menu options.
Prerequisites
Requirements
Cisco recommends that you have knowledge of these topics:
- Terminal server usage and basic setup
- Octal cables to connect consoles
- SSH for remote access
Components Used
The information in this document is based on Cisco 2911 router with HWIC-16A module connected.
The information in this document is from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, make sure that you understand the potential impact of any command.
Configure
Network Diagram
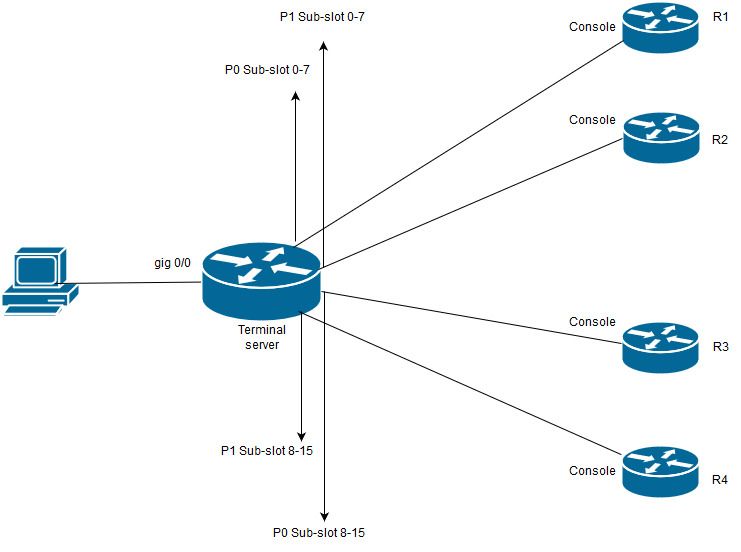
In this diagram, Cisco 2911 has HWIC-16A card is connected to slot 0 and two octal cable connect to total four devices consoles (2 each). From octal cable 1(0-7) port 0 goes to R1 and port 1 goes to R2. Likewise, from octal cable 2, port 0 goes to R3 and port 1 goes to R4. A test PC connects to the terminal sever for console access.
Step 1. Ensure that SSH is enabled on the router that you use as terminal server. In the configuration example, local database is used for authentication. Radius or TACACS authentication method can also be used.
Configure a loopback interface on the router which can be used later to open reverse telnet/SSH session to vty lines. Other physical interface IP can also be used for terminal line access. It’s recommended to use loopback for scalability purpose.
TS(config)#int lo 0
TS(config-if)#ip add 192.168.1.1 255.255.255.255
Step 2. Before you configure the terminal tty lines, it’s better to understand how these port mappings work. The number of tty lines can be verified with the use of this command:
TS#show line
Tty Line Typ Tx/Rx A Modem Roty AccO AccI Uses Noise Overruns Int
* 0 0 CTY - - - - - 4 0 0/0 -
1 1 AUX 9600/9600 - - - - - 0 0 0/0 -
2 2 TTY 9600/9600 - - - - - 0 0 0/0 -
0/0/0 3 TTY 9600/9600 - - - - - 18 249 0/0 -
0/0/1 4 TTY 9600/9600 - - - - - 6 257 1916/0 -
0/0/2 5 TTY 9600/9600 - - - - - 0 0 0/0 -
0/0/3 6 TTY 9600/9600 - - - - - 0 0 0/0 -
0/0/4 7 TTY 9600/9600 - - - - - 0 0 0/0 -
0/0/5 8 TTY 9600/9600 - - - - - 0 0 0/0 -
0/0/6 9 TTY 9600/9600 - - - - - 0 0 0/0 -
0/0/7 10 TTY 9600/9600 - - - - - 0 0 0/0 -
0/0/8 11 TTY 9600/9600 - - - - - 3 0 0/0 -
0/0/9 12 TTY 9600/9600 - - - - - 15 321 0/0 -
0/0/10 13 TTY 9600/9600 - - - - - 0 0 0/0 -
0/0/11 14 TTY 9600/9600 - - - - - 0 0 0/0 -
0/0/12 15 TTY 9600/9600 - - - - - 0 0 0/0 -
0/0/13 16 TTY 9600/9600 - - - - - 0 0 0/0 -
0/0/14 17 TTY 9600/9600 - - - - - 0 0 0/0 -
0/0/15 18 TTY 9600/9600 - - - - - 0 0 0/0 -
388 388 VTY - - - - - 50 0 0/0 -
389 389 VTY - - - - - 3 0 0/0 -
390 390 VTY - - - - - 0 0 0/0 -
Tty Line Typ Tx/Rx A Modem Roty AccO AccI Uses Noise Overruns Int
391 391 VTY - - - - - 0 0 0/0 -
392 392 VTY - - - - - 0 0 0/0 -
Line(s) not in async mode -or- with no hardware support:
19-387
It’s clearly seen from the output that, with the use of a HWIC-16A card, it can give up to 16 tty lines that range from 0/0/0-0/0/15 which allows to connect 16 devices.
Each octal cable has 8 wires. On a HWIC-16A card, two octal cables can be connected. The numbering schema can be seen on each wire of octal cable as well as on the card. A couple of simple diagrams will help to understand this better.

A close look at the cables indicates a number in a pattern of P0, P2,….P7 and on the card for the top port the number is from 8 - 15 and the bottom one is from 0 - 7. Based on the diagram mentioned, you can say that, for R1 you use line 0/0/0, for R2 line 0/0/1, for R3 line 0/0/8 and for R4 0/0/9.
Step 3. For SSH access, the tty lines do not listen to the same ports as telnet does. So you need to define the ports manually with the use of the rotary group.
- Configure SSH to listen to a range of ports and map them to rotary group.
TS(config)#ip ssh port 2001 rotary 1 127
This command maps each rotary group to a port in a sequential manner. For example; rotary 1 will be mapped to port 2001, rotary 2-2002, rotary 3-2003,……etc.
- Now, you will define the rotary groups under the tty lines. When you configure, you can either use the tty or the line number, like line 0/0/0 or line 3. Regardless of what you configure, it will show up as tty. Here is the configuration:
line 0/0/0
login local
rotary 1
no exec
transport input ssh
line 0/0/1
login local
rotary 2
no exec
transport input ssh
line 0/0/8
login local
rotary 11
no exec
transport input ssh
line 0/0/9
login local
rotary 12
no exec
transport input ssh
In this configuration example, rotary 1 is defined under line 0/0/0 and rotary 1 has been mapped to port 2001. So, the line will listen to SSH port 2001. Likewise, line 0/0/1 will listen to port 2002.
Step 4. Configure your vty lines for SSH as outgoing protocol. Since you open reverse connections to the lines, it comes from vty line and hence SSH should be allowed.
TS(config)#line vty 0 4
TS(config-line)#transport output ssh
TS(config-line)#login local
Step 5. Ensure that you have configured the usernames correctly based on the authentication criteria that is used. In this configuration example, you have configured a local username cisco with password cisco123.
Now, you are ready to access the devices. Multiple methods can be used to accomplish the same and all will be checked here.
Use Terminal Application
With the use of SSH client software, you can connect through SSH with the use of the port based on the mapping on terminal lines.
Access Directly from Terminal Server
TS#ssh -l cisco -p 2012 192.168.1.1
Password:
Password OK
R4#
In this example, 1.1.1.1 is the loopback address of terminal server. To come back to terminal server, you need to use Ctrl + Shift + 6, release the buttons and instantly press X.
The sessions from terminal server can be verified with the show sessions command.
TS#show sessions
Conn Host Address Byte Idle Conn Name
* 192.168.1.1 192.168.1.1 0 2 192.168.1.1
*Indicates an active session and to clear it you can either use clear line <line number; 12 in this case > or disconnect <conn number next to *>
TS#disconnect 1
Closing connection to 192.168.1.1 [confirm]
Access Devices through Menu Options:
This is another method to access the devices. It gives a set of options when someone logs in to the terminal server and makes it easy to access the devices.
Note: For easy access, you can bind the IP to a host name which allows the name to be used instead of IP. This is optional.
Step 1. Bind the terminal server IP address to a name.
ip host R 192.168.1.1
Step 2. Menu option provides an option to use a set of commands based on user input.
- Configure a banner or title for the menu:.
TS(config)#menu nodes title $
Enter TEXT message. End with the character '$'.
==================================================
Welcome to my access server.
==================================================
$
Step 3. This gives an interface to select an option from menu.
TS(config)#menu cisco prompt $
Enter TEXT message. End with the character '$'.
enter your selection here :
$
Step 4. To connect to a device console, follow options are used from global configuration mode.
menu nodes text 1 1800 P1/0
menu nodes command 1 ssh -l cisco -p 2001 R
menu nodes text 2 1800 P1/1
menu nodes command 2 ssh -l cisco -p 2002 R
menu nodes text 3 3825 P2/0
menu nodes command 3 ssh -l cisco -p 2011 R
menu nodes text 4 3850 P2/1
menu nodes command 4 ssh -l cisco -p 2012 R
Step 5. Use this command to enable user to hit enter after you make a selection. By default when user selects an option, it executes automatically.
TS#(config)menu nodes line-mode
Step 6. Configure these options to disconnect the sessions.
menu nodes text d disconnect last session
menu nodes command d disconnect
menu nodes text d<no> clear session by number ie: d1
menu nodes command d1 disconnect 1
menu nodes command d2 disconnect 2
menu nodes command d3 disconnect 3
menu nodes command d4 disconnect 4
Step 7. Ensure to configure the option to exit from menu.
menu nodes text exit menu-exit
menu nodes command exit menu-exit
Step 8. Some additional options might also be configured under menu.
menu nodes single-space
! single-space menu entries on display
menu nodes status-line
! Display user status at top of screen
menu nodes text q Quit terminal server session
menu nodes command q exit
menu nodes text s show all established sessions
menu nodes command s show sessions
menu nodes options s pause
! pause after command, before redrawing menu
Step 9. You won't see any change in the menu untilyou apply it. So, apply it to the vty lines so that, when user opens a remote session to the terminal server, it gives the menu prompt.
TS(config)#line vty 0 4
TS(config-line)#autocommand menu nodes
Caution: If you access the terminal server remotely and want to do some modification to the menu, it’s recommended to remove the autocommand from vty lines and do the changes. Since you remove one line from the menu, it removes the entire menu configuration and if you only have banner configured under the menu, once the router enters into the menu option, there is no way to break it unless the autocommand is removed from the vty lines by taking a console access to the terminal server.
Any changes needed to be done for the menu, add the menu commands without removing anything, which will override previous configuration. Alternatively, take a backup of the menu configuration, do the changes. Then remove the entire menu and reapply the modified complete menu configuration again.
Verify
Use this section in order to confirm that your configuration works properly.
If you access the terminal server through console, this is how you will enter into the menu option.
TS#menu nodes
For remote access, the connection will land into menu option directly.
login as: cisco
Using keyboard-interactive authentication.
Password:
Server "TS" Line 388 Terminal-type xterm
==================================================
Welcome to my access server.
==================================================
1 1800 P1/0
2 1800 P1/1
3 3825 P2/0
4 3850 P2/1
exit menu-exit
q Quit terminal server session
s show all established sessions
d disconnect last session
d<no> clear session by number ie: d1
enter your selection here :4
Password:
Password OK
R4>
Press CTRL + Shift + 6 then X in order to return to the terminal server.
Check and disconnect sessions:
==================================================
Welcome to my access server.
==================================================
1 1800 P1/0
2 1800 P1/1
3 3825 P2/0
4 3850 P2/1
exit menu-exit
q Quit terminal server session
s show all established sessions
d disconnect last session
d<no> clear session by number ie: d1
enter your selection here :s
Conn Host Address Byte Idle Conn Name
1 R 192.168.1.1 0 0 R
* 2 R 192.168.1.1 0 0
It’s seen that, there are two sessions and session 2 is currently active. To disconnect:
enter your selection here :d1
Closing connection to R [confirm]
Server "TS" Line 388 Terminal-type xterm
enter your selection here :d2
Closing connection to R [confirm]
Server "TS" Line 388 Terminal-type xterm
Exiting from menu options:
enter your selection here :exit
TS>
Which brings us back to the terminal server CLI.
Note: You might have observed that sometimes the connection is refused by remote host when you connect to resolve this, disconnect any active connection from menu option or from cli exec mode use the command clear line <line number> and try to connect to the device again.
Troubleshoot
There is currently no specific troubleshooting information available for this configuration.
Contributed by Cisco Engineers
- Dibyajyoti PandaCisco TAC Engineer
Contact Cisco
- Open a Support Case

- (Requires a Cisco Service Contract)
 Feedback
Feedback