FireAMP Private Cloud 3.0.1 upgrade procedure
Available Languages
Download Options
Bias-Free Language
The documentation set for this product strives to use bias-free language. For the purposes of this documentation set, bias-free is defined as language that does not imply discrimination based on age, disability, gender, racial identity, ethnic identity, sexual orientation, socioeconomic status, and intersectionality. Exceptions may be present in the documentation due to language that is hardcoded in the user interfaces of the product software, language used based on RFP documentation, or language that is used by a referenced third-party product. Learn more about how Cisco is using Inclusive Language.
Contents
Introduction
This document describes how to upgrade a FireAMP Private Cloud (vPC) version 2.4.4 to version 3.0.1. Please note that upgrade procedure requires a new Virtual Machine instance for 3.0.1 version.
Prerequisites
Requirements
Cisco recommends that you have knowledge of these topics:
- Installation an Open Virtual Appliance (OVA) Template in the VMWare ESXi
- Basic knowledge of how Virtual AMP Cloud works and operates
Hardware Requirements
Below are the minimum hardware requirements for the FireAMP Private Cloud:
- vSphere ESX 5 or higher
- 8 CPUs
- 64 GB RAM
- 1 TB free disk space on the VMWare datastore
- Type of drives: SSD required
- RAID Type: One RAID 10 group (stripe of mirrors)
- Minimum VMware data store size: 1TB
- Minimum Data Store Random Reads for the RAID 10 Group (4K): 60K IOPS
- Minimum Data Store Random Writes for the RAID 10 Group (4K): 30K IOPS
Caution: The Private Cloud OVA creates the drive partitions, so there is no need to specify them in VMWare.
Note: Refer to the FireAMP Private Cloud User Guide for more information about Hardware Requirements.
Components Used
The information in this document is based on these hardware and software versions:
- FireAMP Private Cloud 2.4.4
- FireAMP Private Cloud 3.0.1
- VMWare ESXi 5.0 or greater
The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, make sure that you understand the potential impact of any command.
Upgrade process
This section provides step by step instructions on how to collect the backup from the FireAMP Private Cloud 2.4.4 version and how to properly restore it on FireAMP Private Cloud 3.0.1 version.
Caution: Upgrade process can introduce a downtime in your environment. Connectors (includes AMP for Networks connected to your Virtual Private Cloud) which use Private Cloud can lose connectivity to the Virtual Cloud and they can have impaired functionality because of that.
1. Update download and installation
Make sure that your FireAMP Virtual Private Cloud 2.4.4 is up to date.
Step 1. Navigate to Operations -> Update Device in Administrator Portal.
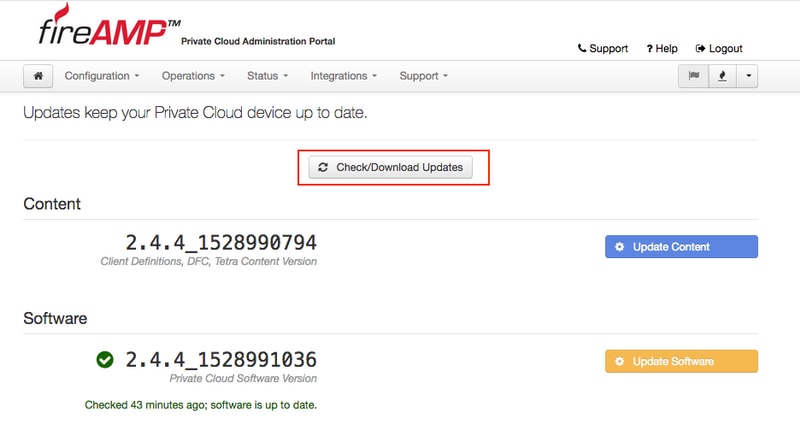
Step 2. Click Check/Download Updates button, as shown in the image, to make sure that your FireAMP Virtual Private Cloud, from where backup collection takes place, is up to date (Content and Software wise).
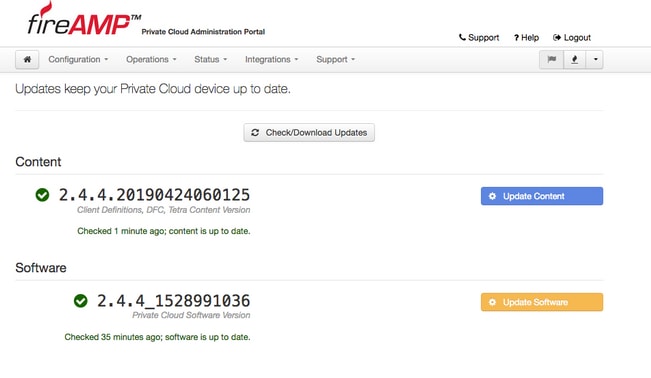
Step 3. Once Content and Software updates are installed, the update page shows the information that the device is up to date, as shown in the image.
2. Backup collection and shutdown
Step 1. Navigate to Operations -> Backups.
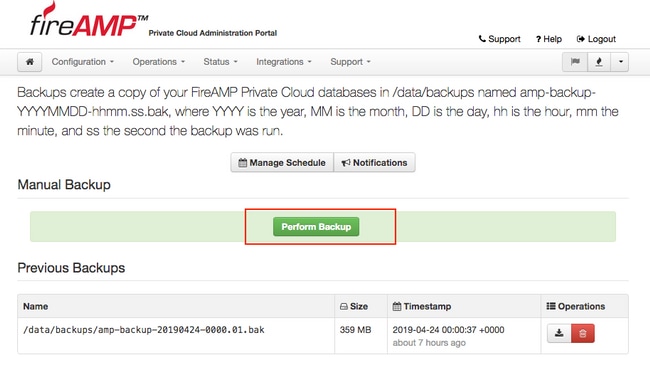
Step 2. In the Manual Backup section, click Perform Backup button. The procedure starts a backup creation.
Step 3. When the process finishes successfully, the successful notification appears, as shown in the image.
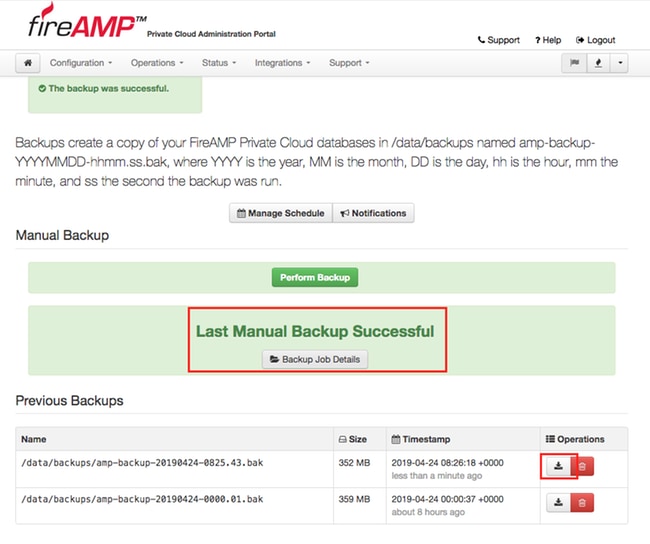
Step 4. Click  button. Make sure that the backup is properly downloaded and saved in a safe location.
button. Make sure that the backup is properly downloaded and saved in a safe location.
3. New version installation
This section assumes that Virtual Machine for 3.0.1 FireAMP Virtual Private Cloud is already deployed. Install procedure in regards of Virtual Machine for 3.0.1 OVA on VMWare ESXi can be found under the link: Deploy an OVA File on an ESX Server.
Note: Procedure presented in the article uses exactly the same hostnames and IP addresses for FireAMP Virtual Private Cloud 2.4.4 and 3.0.1. When you follow this guide, you must shutdown FireAMP Virtual Private Cloud 2.4.4 after backup is collected.
Step 1. Open console terminal for newly created Virtual Machine instance with 3.0.1 version installed. You can navigate through Tab, Enter and arrow keys.
Step 2. Navigate to CONFIG_NETWORK and click the Enter key on your keyboard to begin the configuration of the management IP address for the FireAMP Private Cloud. If you do not want to use DHCP, select No and press Enter.
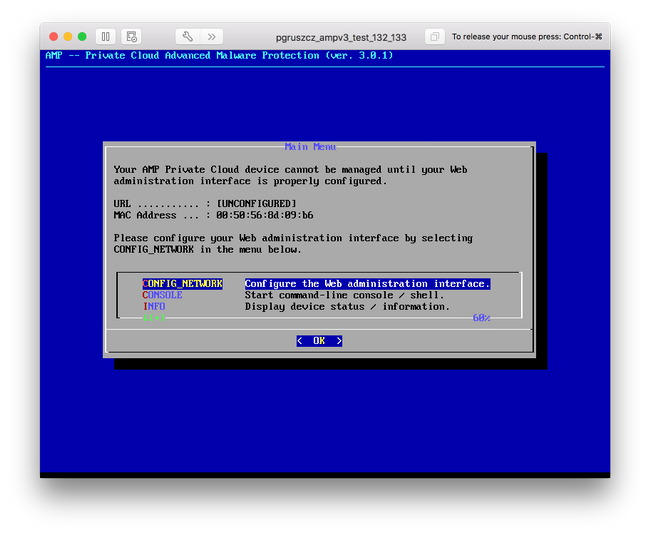
Step 3. Enter the IP address, Network Mask and Default Gateway. Navigate to OK, as shown in the image. Press Enter key.
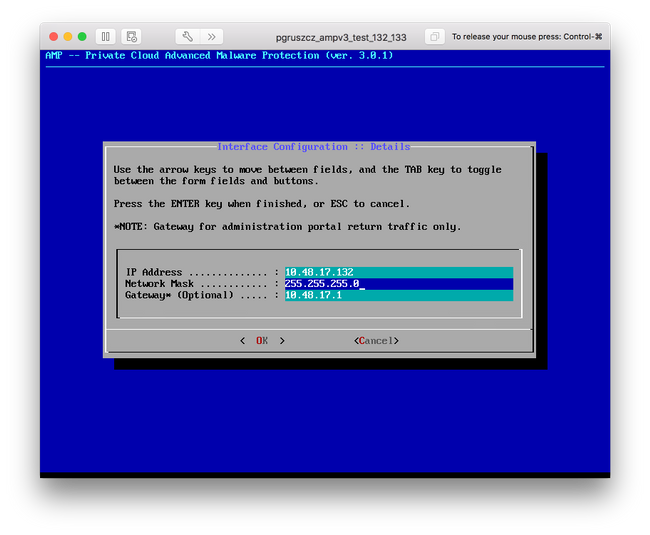
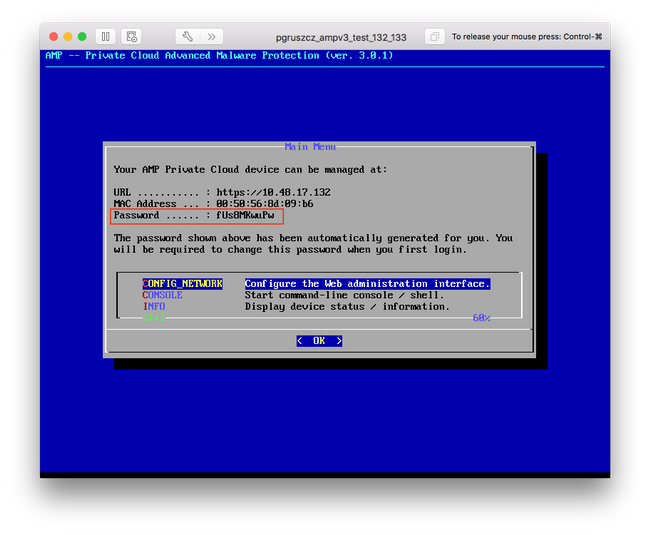
Step 4. Network configuration change requires a restart of the interface. After the restart, main console menu reappears, as shown in the image. This time you see an IP address on the URL line. Also, note that the initial Password is displayed. This is a one-time password (later referenced as initial password) which is used in the web-based setup.
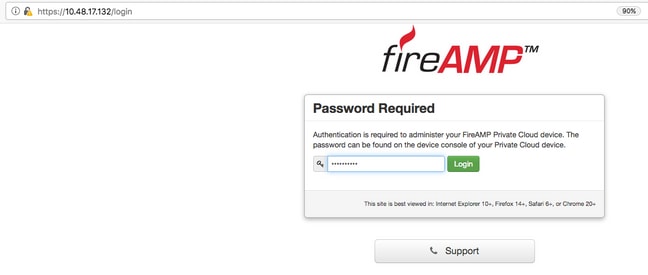
Step 5. Open a web browser and navigate to the management IP address of the appliance. You receive a certificate error as the FireAMP Private Cloud initially generates its own HTTPS certificate. Configure your browser to temporarily trust the self-signed certificate of the FireAMP Private Cloud.
Step 6. You get a screen to enter a password, as shown in the image. Use the initial password from the console. Click on Login.
Step 7. After successful login, you are required to change the password. Use the initial password from the console in the Old Password field. Use your new password twice in the New Password fields. Click Change Password.
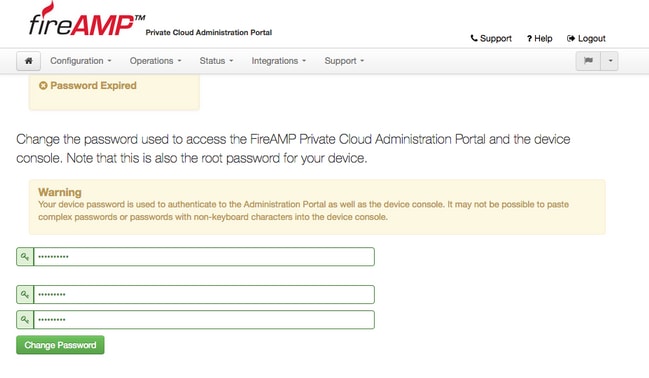
4. Backup restore
Step 1. Welcome page of Admin portal presents two ways of 3.0.1 FireAMP Virtual Cloud installation, as shown in the image.
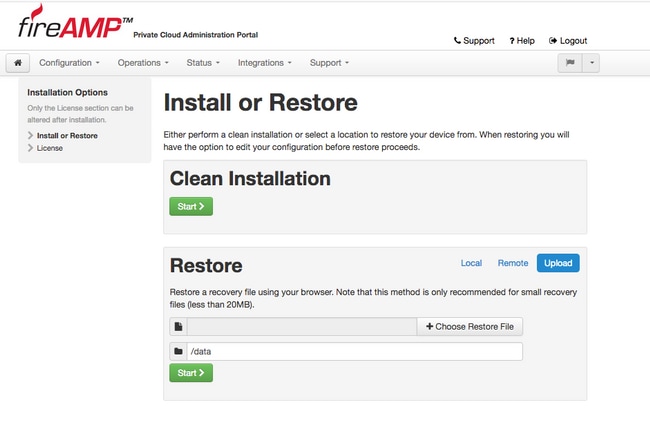
Step 2. You can choose one of three different methods to upload the backup file to the newly created FireAMP Virtual Private Cloud instance:
Local - Restores the configuration from a backup file already presented on the device (you must put the file on the appliance via SFTP or SCP). Files are extracted to the correct directory once the restore process begins. For this reason, recommended is /data directory.
Remote - Restore from a file on a remotely accessible HTTP server.
Upload - Restore from the file uploaded by your browser. Works only if your backup file is smaller than 20MB.
In this example, the remote option was chosen.
Note: Proper connectivity must be allowed for the HTTP server. Backup file needs to be accessible from the Private Cloud perspective.
Click Start button to proceed with the restore, as shown in the image.
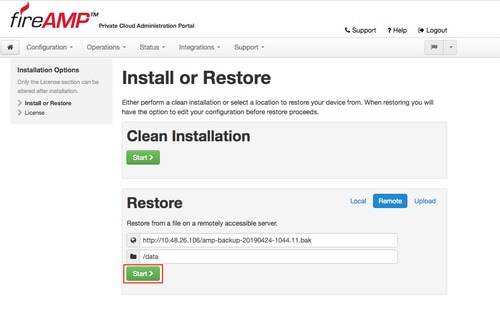
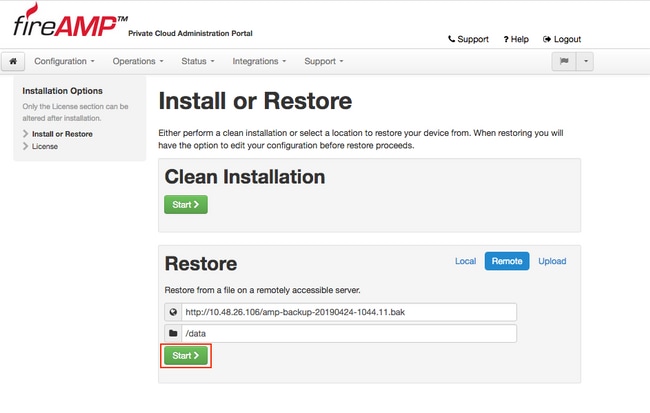
Step 3. Restore procedure from a backup replaces your current configuration. Your device's SSH host keys and Administration Portal password are replaced. You can review parts of your configuration in regards of installation.
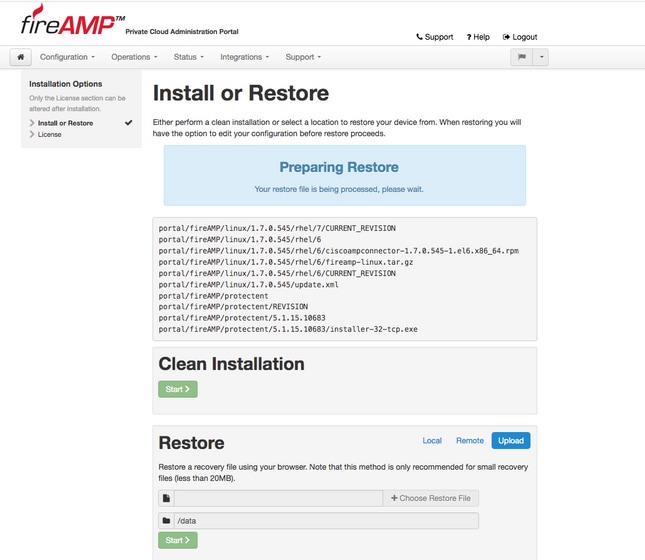
Step 4. After a successful copy of the backup file, restore page presents pop-up message as shown on the image. Click Reconfigure Administration Portal Now button to finish the restore procedure.

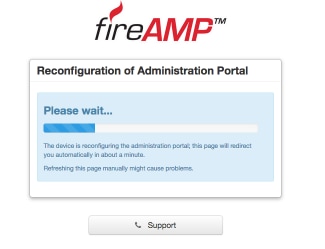
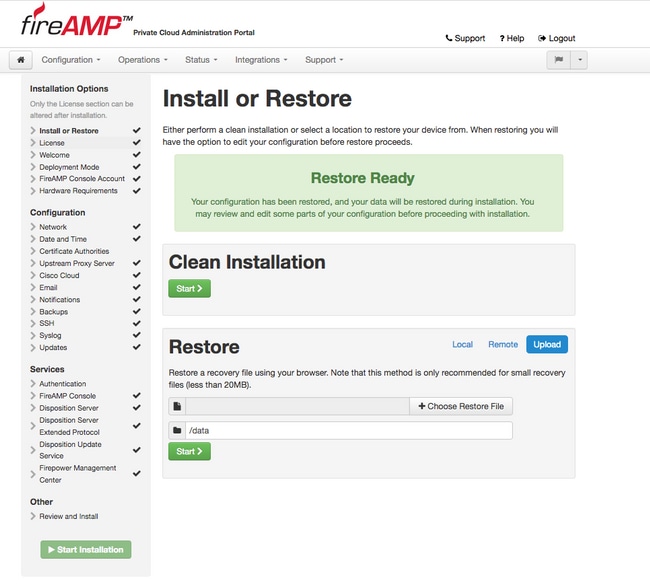
Step 5. Once reconfiguration is finished, the Administration portal page is displayed again, as shown in the image. From now on, to login you must use the password from 2.4.4 FireAMP Virtual Private Cloud backup.
Image shows most of the work for the proper installation as already done (checkpoint marks). It is expected since backup restores the configuration from FireAMP Virtual Private Cloud 2.4.4.
5. Certificate Authorities
Version 3.0.1 of FireAMP Virtual Private Cloud introduces new features and behaviors in terms of how the system operates. Those need to be configured and completed before you can begin the installation.
The first component which is new and was not present in the earlier release is Certificate Authorities.
Certificate Authorities page allows you to manage root certificates for your services if you want to use a custom certificate authority. You can download or delete your root certificate if needed.
Note: Certificate Authorities trusted store is used only for Virtual Cloud services (to build and validate the proper certificate chain). It is not used for various vPC integrations, like ThreatGrid.
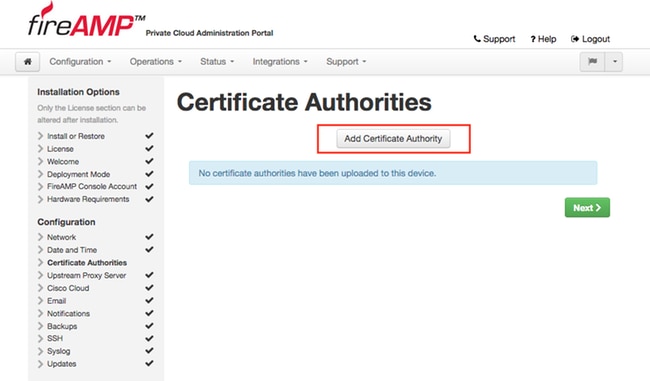
Step 1. Navigate to Configuration -> Certificate Authorities section in Installation Options panel. Click Add Certificate Authority button, as shown in the image.
Step 2. Click Add Certificate Root, as shown in the image, to upload the certificate. All listed requirements need to be met for Virtual Private Cloud to accept the certificate.
Note: During the upgrade procedure, you must add root certificate used to sign the Authentication service certificate, explained in the next section.
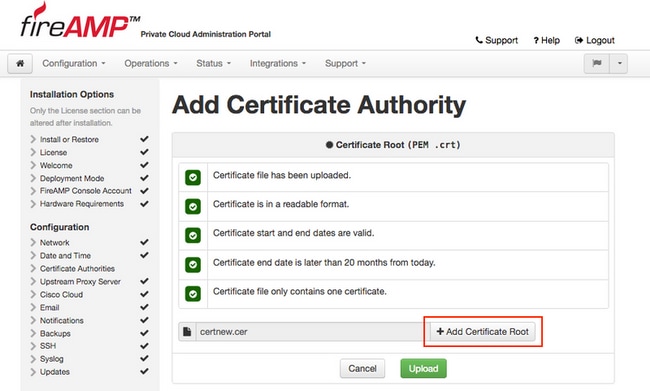
Step 3. Once the certificate is updated, click Upload button, as shown in the image, to upload the certificate.
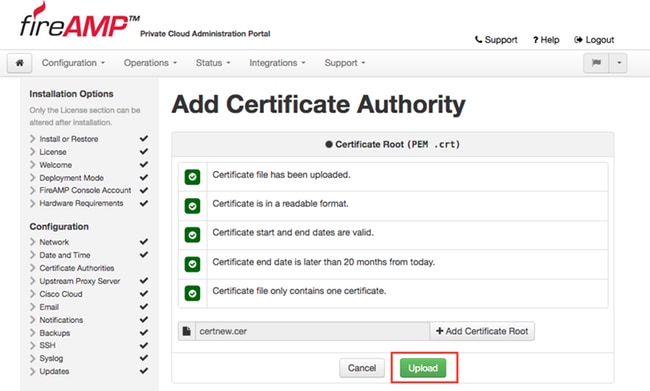
If you use any subordinate certificates authority to sign any service certificates, upload them in this section as well.
Caution: Even if you generate a self-signed certificate for the Authentication Service, make sure that it is uploaded in the Certificate Authority section before you go to the next steps.
6. Authentication Service
The second component which is added in 3.0.1 version, and not imported from the backup, is Authentication under the Services section.
Authentication service will be used in future versions of Private Cloud to handle user authentication requests. It is added in 3.0.1 version for future compatibility.
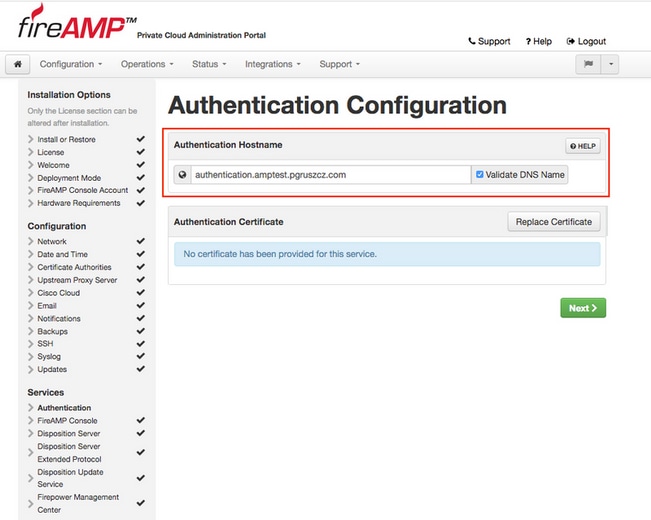
Step 1. Navigate to Services -> Authentication section in the Installation Options panel. Enter unique Authentication Hostname, DNS entry specified in the hostname section must be correctly configured on the DNS server and points to the Virtual Private Cloud console interface IP address.
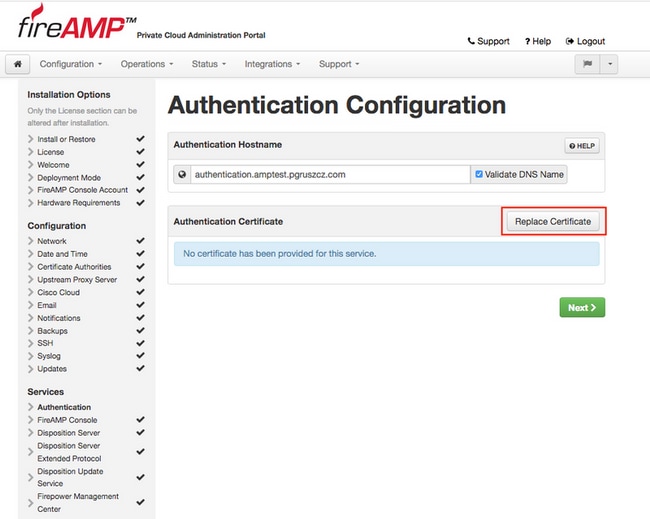
Step 2. Once the hostname is specified and properly resolvable, click Replace Certificate button, as showed in image.
Note: If you need help with the Certificate generation, please visit the article: How to Generate and Add Certificates that are Required for Installation of AMP VPC 3.x Onwards for more information about Hardware Requirements.
Step 3. Click Choose Certificate button to upload the Authentication Service certificate, as showed in image.
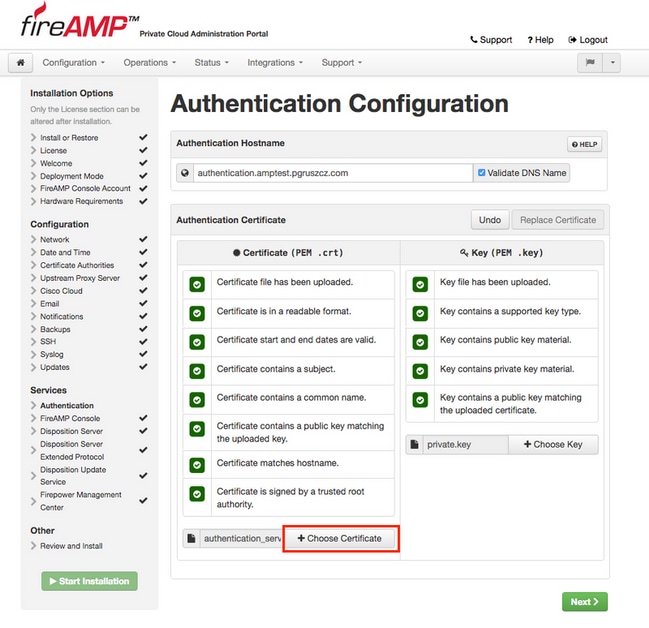
Step 4. Next step is to upload the private key file for the certificate. To add it, click Choose Key button.
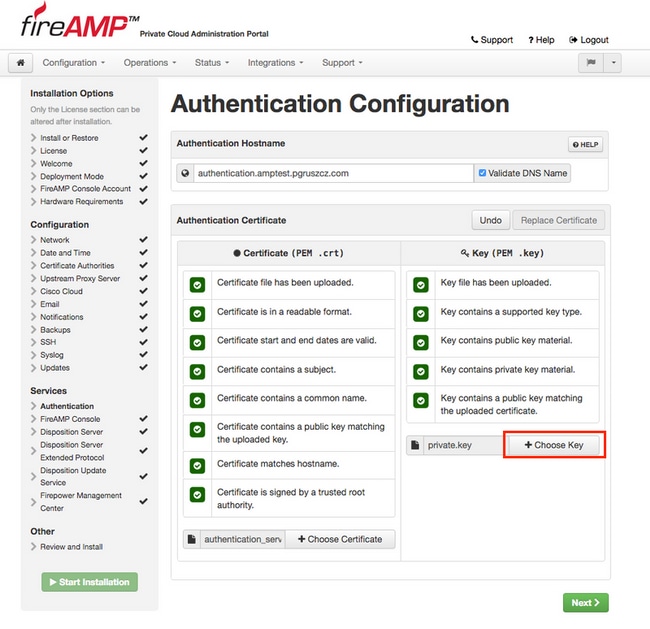
Step 5. You need to make sure all of the requirements are met before you can proceed to the next step. Highlighted requirements are met if the root certificate used to sign the Authentication service is correctly placed in the Certificate Authorities store.
Caution: You can change the hostnames for all other Services at this stage only. Once the installation is finished, hostname for the services cannot be changed. Later you can change certificates only. You need to make sure you understand the risk of such operation. If you change the hostnames of the services used by the Connectors or AMP for Network devices, they can have problems to communicate with the cloud once upgrade is completed.
7. Installation
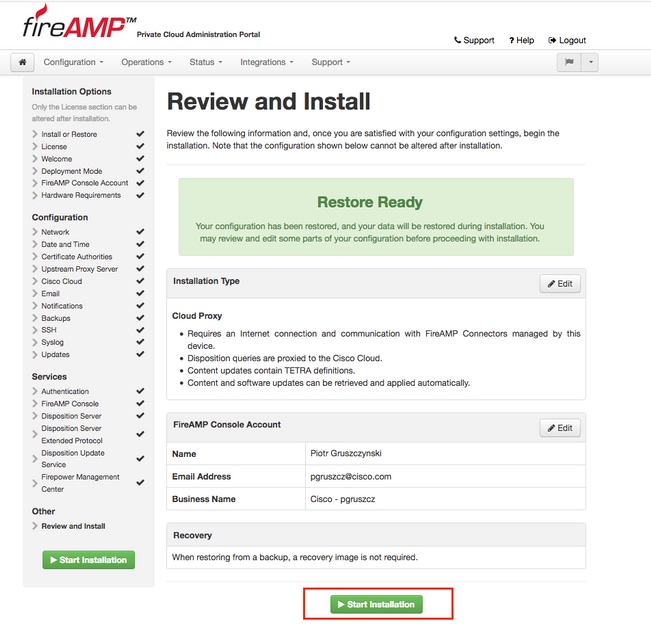
Step 1. Once every section is completed and marked as valid, you begin the installation. Navigate to Review and Install section and click Start Installation button, as shown in the image.
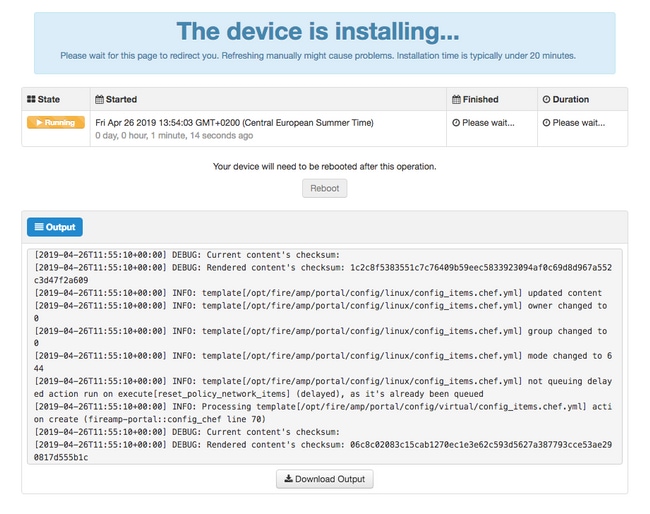
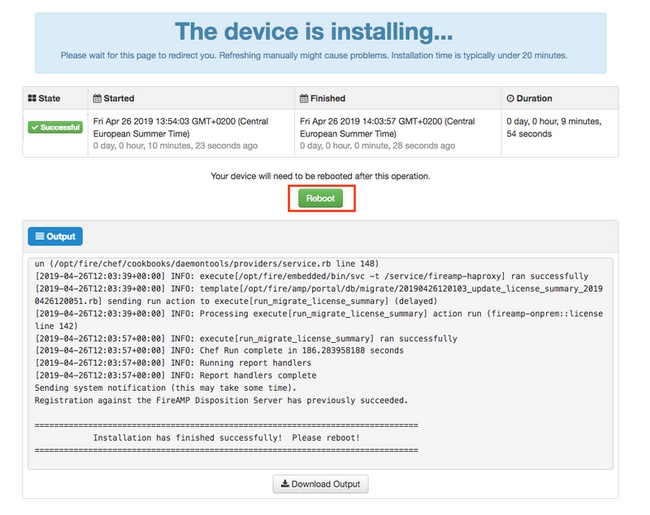
Step 2. Administrator portal presents you the current state, start date and logs. If you encounter any errors or problems which needs support attention, collect the logs by click Download Output button, as shown in the image, and attach them to the TAC case.
Step 3. When the installation is successful, you must reboot the device to finish the process. Click Reboot button to proceed with the restart procedure, as shown in the image.
Step 4. After the reboot procedure, you can login to the Administrator Portal and Console Portal. The upgrade procedure is finished.
8. Post upgrade checks
Once the device is rebooted, please make sure that restore was completed successfully:
Step 1. Check if connectors are able to communicate to the newly installed virtual appliance 3.0.1.
Step 2. Make sure that Events, Device Trajectory and Computers object are correctly restored and presented in the console portal.
Step 3. If you have any AMP for Network integrations like FMC, ESA, WSA make sure they can communicate to the File Disposition server.
Step 4. Check for any Content/Software (Operations -> Update Device) updates and proceed with the installation of such.
It is highly suggested to perform tests to assure a successful upgrade.
Changes in Virtual Private Cloud 3.0.1
1. Windows Connector version 6.1.7
Private Cloud 3.0.1 is shipped with the support for 6.1.7 Windows Connector version, you can find the documentation about it under the link: Release notes for 6.1.7
Caution: If you have made any change in certificates, make sure that before an upgrade or installation to version 6.1.7 of Windows Connector, certificates used for private cloud services are trusted on the endpoint itself. Trust needs to be on the machine level, not user. If this condition is not met, connectors do not trust the certificate presented by Private Cloud which keeps them in a disconnected state.
2. Certificate Authorities and Authentication service
Changes were thoroughly described in the user guide for 3.0: Private Cloud User Guide.
Certificate Authorities allows you to manage root certificates for your Services if you want to use a custom certificate authority. You can download or delete your root certificate if needed.
Authentication service will be used in future versions of Private Cloud to handle user authentication requests. It is added in 3.0.1 version for future compatibility.
Contributed by Cisco Engineers
- Piotr GruszczynskiTechnical Consulting Engineer
- Radek OlszowyTechnical Consulting Engineer
Contact Cisco
- Open a Support Case

- (Requires a Cisco Service Contract)
 Feedback
Feedback