Introduction
This document explains how the Cisco Intrusion Prevention System (IPS) displays untranslated real IP addressess in the event logs, although the Adaptive Security Appliance (ASA) sends traffic to the IPS after it performs Network Address Translation (NAT).
Background Information
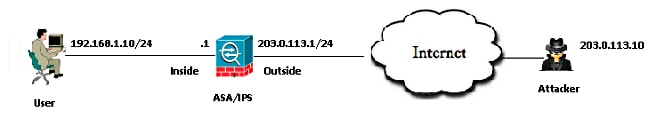
Topology
- The Private IP address of the server: 192.168.1.10
- The Public IP address of the server (Natted): 203.0.113.2
- The attacker's IP address: 203.0.113.10
How does IPS display untranslated real IP addresses in event logs?
Explanation
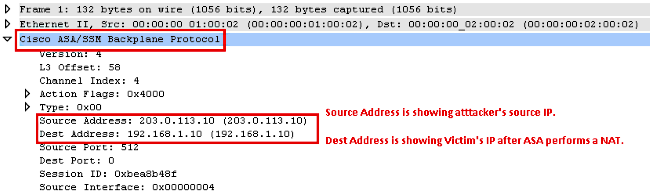
When the ASA sends a packet to IPS, it encapsulates that packet into a Cisco ASA/Security Services Module (SSM) Backplane Protocol header. This header contains a field that represents the real IP address of the inside user behind the ASA.
These logs show an attacker that sends Internet Control Message Protocol (ICMP) packets to the public IP address of the server, 203.0.113.2. The packet captured on the IPS shows that the ASA punts the packets to IPS after performing NAT.
IPS# packet display PortChannel0/0
Warning: This command will cause significant performance degradation
tcpdump: WARNING: po0_0: no IPv4 address assigned
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on po0_0, link-type EN10MB (Ethernet), capture size 65535 bytes
03:40:06.239024 IP 203.0.113.10 > 192.168.1.10: ICMP echo request, id 512, seq
31232, length 40
03:40:06.239117 IP 203.0.113.10 > 192.168.1.10: ICMP echo request, id 512, seq
31232, length 40
03:40:06.239903 IP 203.0.113.2 > 203.0.113.10: ICMP echo reply, id 512, seq
31232, length 40
03:40:06.239946 IP 203.0.113.2 > 203.0.113.10: ICMP echo reply, id 512, seq
31232, length 40
Here are the event logs on IPS for ICMP Request packets from the attacker.
evIdsAlert: eventId=6821490063343 vendor=Cisco severity=informational
originator:
hostId: IPS
appName: sensorApp
appInstanceId: 1305
time: Dec 24, 2014 03:43:57 UTC offset=0 timeZone=UTC
signature: description=ICMP Echo Request id=2004 version=S666 type=other
created=20001127
subsigId: 0
sigDetails: ICMP Echo Request
interfaceGroup: vs0
vlan: 0
participants:
attacker:
addr: 203.0.113.10 locality=OUT
target:
addr: 192.168.1.10 locality=OUT
os: idSource=unknown type=unknown relevance=relevant
alertDetails: InterfaceAttributes: context="single_vf" physical="Unknown"
backplane="PortChannel0/0" ;
riskRatingValue: 35 targetValueRating=medium attackRelevanceRating=relevant
threatRatingValue: 35
interface: PortChannel0/0 context=single_vf physical=Unknown backplane=
PortChannel0/0
protocol: icmp
Here are the event logs on IPS for ICMP Reply from the inside server.
evIdsAlert: eventId=6821490063344 vendor=Cisco severity=informational
originator:
hostId: IPS
appName: sensorApp
appInstanceId: 1305
time: Dec 24, 2014 03:43:57 UTC offset=0 timeZone=UTC
signature: description=ICMP Echo Reply id=2000 version=S666 type=other
created=20001127
subsigId: 0
sigDetails: ICMP Echo Reply
interfaceGroup: vs0
vlan: 0
participants:
attacker:
addr: 192.168.1.10 locality=OUT
target:
addr: 203.0.113.10 locality=OUT
os: idSource=unknown type=unknown relevance=relevant
alertDetails: InterfaceAttributes: context="single_vf" physical="Unknown"
backplane="PortChannel0/0" ;
riskRatingValue: 35 targetValueRating=medium attackRelevanceRating=relevant
threatRatingValue: 35
interface: PortChannel0/0 context=single_vf physical=Unknown backplane=
PortChannel0/0
protocol: icmp
Here are captures collected on the ASA Data Plane.
1: 09:55:50.203267 203.0.113.10 > 192.168.1.10: icmp: echo request
2: 09:55:50.203877 203.0.113.2 > 203.0.113.10: icmp: echo reply
3: 09:55:51.203541 203.0.113.10 > 192.168.1.10: icmp: echo request
4: 09:55:51.204182 203.0.113.2 > 203.0.113.10: icmp: echo reply
Decoded ASA Data Plane Captures.
Related Information
