Introduction
This document describes the Network Advanced Malware Protection (AMP)/file access control functionality of the FirePOWER module and the method to configure them with Adaptive Security Device Manager (ASDM).
Prerequisites
Requirements
Cisco recommends that you have knowledge of these topics:
- Knowledge of the Adaptive Security Appliance (ASA) firewall and ASDM.
- FirePOWER appliance Knowledge.
Components Used
The information in this document is based on these software and hardware versions:
- ASA Firepower modules (ASA 5506X/5506H-X/5506W-X, ASA 5508-X, ASA 5516-X) running software version 5.4.1 and later.
- ASA Firepower module (ASA 5515-X, ASA 5525-X, ASA 5545-X, ASA 5555-X) that run Software Version 6.0.0 and later.
- ASDM 7.5.1 and later.
The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, make sure that you understand the potential impact of any command.
Background Information
Malicious software/malware can enter in an organization's network via multiple ways. In order to identify and mitigate the effects of this malicious software and malware, the FirePOWER's AMP features can be used in order to detect and optionally block the transmission of malicious software and malware in the network.
With file control functionality, you can choose to monitor (detect), block, or allow the transfer of file upload and download. For example, a file policy can be implemented which blocks the download of executable files by the user.
With Network AMP functionality, you can select file types that you wish to monitor over commonly used protocols and send SHA 256 hashes, metadata from the files, or even copies of the files themselves to the Cisco Security Intelligence Cloud for malware analysis. Cloud returns disposition for file hashes as clean or malicious based on file analysis.
File control and AMP for Firepower can be configured as a file policy and used as part of your overall access control configuration. File policies associated with access control rules inspect network traffic that meets rule conditions.
Note: Ensure that the FirePOWER Module has a Protect/Control/Malware license in order to configure this functionality. In order to verify the licenses, choose Configuration > ASA FirePOWER Configuration > License.
Configure the File Policy for File Control/Network AMP
Configure File Access Control
Log in to ASDM and choose Configuration > ASA Firepower Configuration > Policies > Files. The New File Policy dialog box appears.
Enter a Name and optional Description for your new policy, then click Store ASA Firepower Changes option. The File Policy Rule page appears.

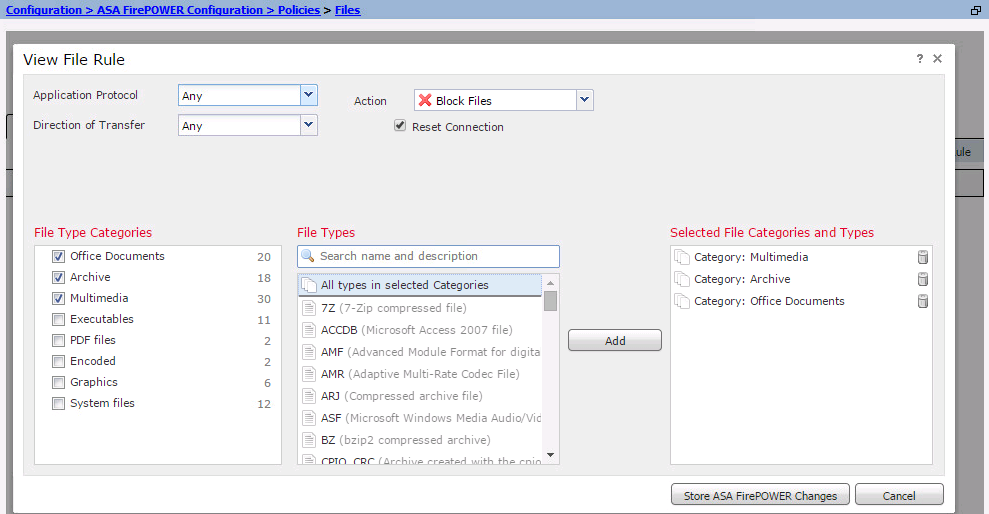
Click Add File Rule in order to add a rule to the file policy. The file rule gives you the granular control over file types that you want to log, block, or scan for malware.
Application Protocol: Specify the application protocol as either Any (default) or the specific protocol (HTTP, SMTP, IMAP, POP3, FTP, SMB).
Direction of Transfer: Specify the direction of file transfer. It could be either Any or Upload/Download based on the Application protocol. You can inspect protocol (HTTP, IMAP, POP3, FTP, SMB) for the file download and protocol (HTTP, SMTP, FTP, SMB) for the file upload. Use the Any option in order to detect files over multiple application protocols, regardless of whether users send or receive the file.
Action: Specify the Action for File Access Control functionality. Action would be either Detect Files or Block Files. Detect File action generates the event and Block Files action generate the event and block the file transmission. With Block Files action, you can optionally select Reset Connection to terminate the connection.
File Type Categories: Select the File Type Categories for which you want to either block file or generate the alert.
File Types: Select the File Types. File Types option gives a more granular option to choose the specific file type.
Choose Store ASA Firepower Changes option to save the configuration.
Configure Network Malware Protection (Network AMP)
Log in to ASDM and navigate to Configuration > ASA Firepower Configuration > Policies > Files. The File Policy page appears. Now click on the The New File Policy dialog box appears.
Enter a Name and optional Description for your new policy, then click on the Store ASA Firepower Changes option. The File Policy Rules page appears.
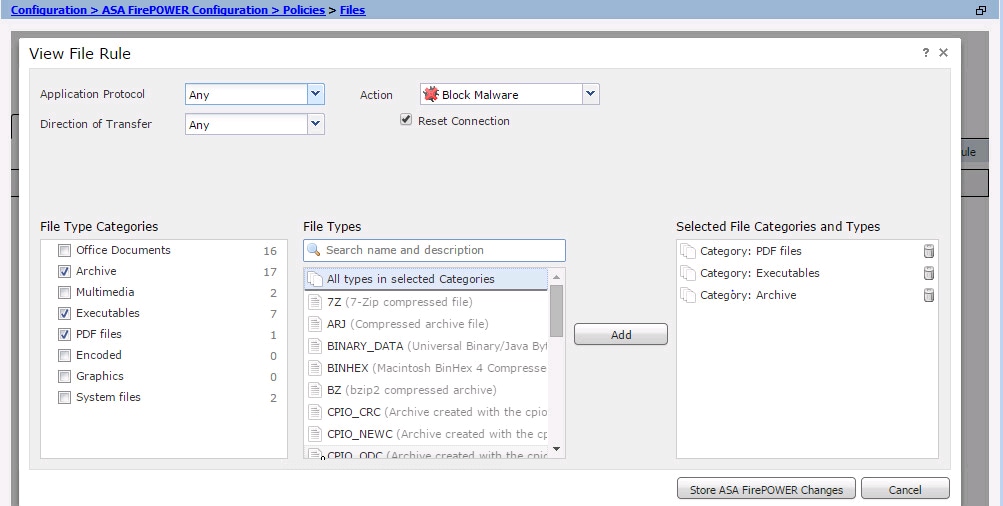
Click the Add File Rule option to add a rule to file policy. File rule gives you the granular control over file types that you want to log, block, or scan for malware.
Application Protocol: Specify either Any (default) or specific protocol (HTTP, SMTP, IMAP, POP3, FTP, SMB)
Direction of Transfer: Specify the direction of file transfer. It could be either Any or Upload/ Download based on Application protocol. You can inspect protocol (HTTP, IMAP, POP3, FTP, SMB) for file download and protocol (HTTP, SMTP, FTP, SMB) for file upload. Use Any option to detect files over multiple application protocols, regardless of users sending or receiving the file.
Action: For Network Malware Protection functionality, Action would be either Malware Cloud Lookup or Block Malware. Action Malware Cloud Lookup generates only an event whereas action Block Malware generates the event as well as block the malware file transmission.
Note: Malware Cloud Lookup andBlock Malware rules allow the Firepower to calculate the SHA-256 hash and send it for cloud lookup process to determine if files traversing the network contain malware.
File Type Categories: Select the specific File Categories.
File Types: Select the specific File Types for more granular file types.
Choose option Store ASA Firepower Changes to save the configuration.
Note: File policies handle files in the following rule-action order: Blocking takes precedence over malware inspection, which takes precedence over simple detection and logging.
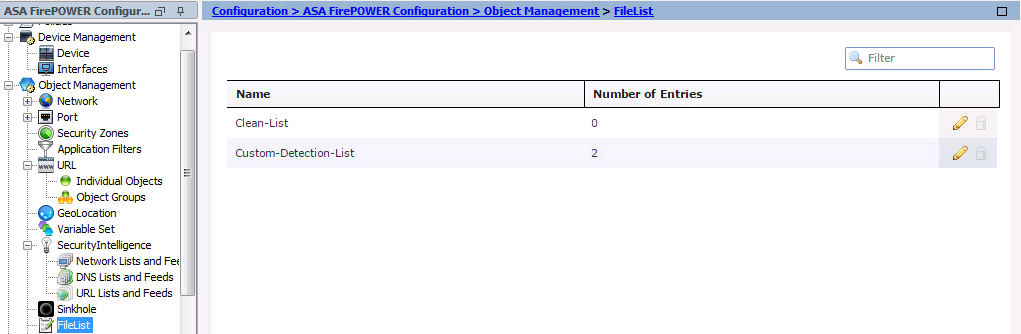
If you configure network-based advanced malware protection (AMP), and Cisco Cloud incorrectly detects a file’s disposition, you can add the file to file list using an SHA-256 hash value to improve detect the file disposition in the future. depending on the type of file list, you can do:
- To treat a file as if the cloud assigned a clean disposition, add the file to the clean list.
- To treat a file as if the cloud assigned a malware disposition, add the file to the custom list.
To configure this, navigate to Configuration > ASA FirePOWER Configuration > Object Management > File List and edit the list to add SHA-256.
Configure Access Control Policy for File Policy
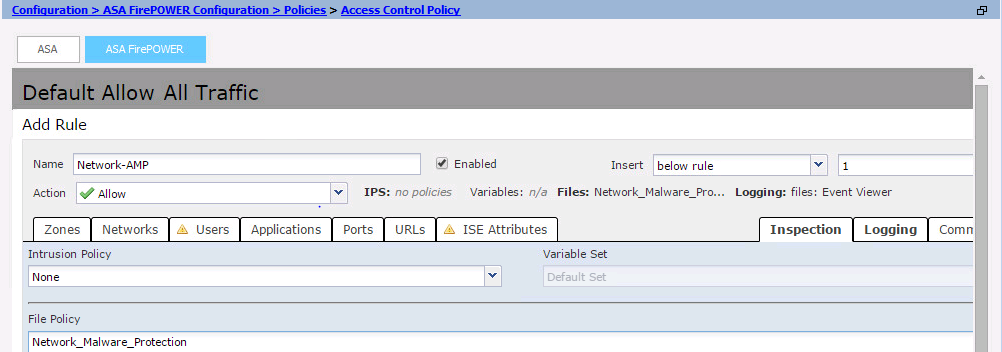
Navigate to Configuration > ASA Firepower Configuration > Policies > Access Control Policy, and create either new Access rule or edit existing Access Rule, as shown in this image.
To configure File Policy, Action should be Allow. Navigate to Inspection tab,and select the File Policy from the drop down menu.
To enable logging, navigate the logging option, and select appropriate logging option & Log Files option. Click the Save/Add button to save the configuration.
Choose option Store ASA Firepower Changes to save the AC policy changes.
Deploy Access Control Policy
Navigate to ASDM's Deploy option, and choose Deploy Firepower Change option from the drop down menu. Click on Deploy option to deploy the changes.

Navigate to Monitoring > ASA Firepower Monitoring > Task Status. Ensure that task must complete to apply the configuration change.
Note: In version 5.4.x, To apply the Access policy to the sensor, you need to clickApply ASA FirePOWER Changes.
Monitor Connection for File Policy Events
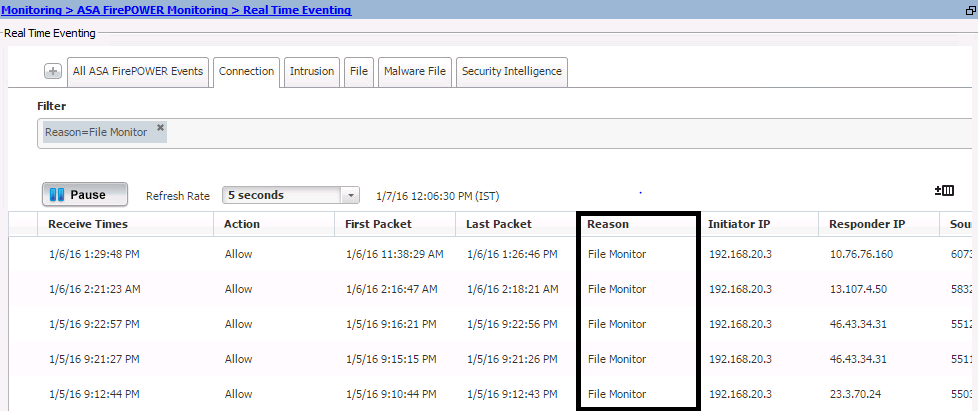
In order to see the events generated by the Firepower Module related to file policy, navigate to Monitoring > ASA Firepower Monitoring > Real Time Eventing.
Verify
There is currently no verification procedure available for this configuration.
Troubleshoot
Ensure that File Policy is correctly conifigured with protocol/ direction/ Action/ File Types. Ensure that correct File Policy included in Access Rules.
Ensure that Access Control Policy deployment completes successfully.
Monitor the Connection events & File events (Monitoring > ASA Firepower Monitoring > Real Time Eventing) to verify if the traffic flow is hitting correct rule or not.
Related Information









 Feedback
Feedback