Patch/Update Installation in FirePOWER Module Using ASDM (On-Box Management)
Available Languages
Bias-Free Language
The documentation set for this product strives to use bias-free language. For the purposes of this documentation set, bias-free is defined as language that does not imply discrimination based on age, disability, gender, racial identity, ethnic identity, sexual orientation, socioeconomic status, and intersectionality. Exceptions may be present in the documentation due to language that is hardcoded in the user interfaces of the product software, language used based on RFP documentation, or language that is used by a referenced third-party product. Learn more about how Cisco is using Inclusive Language.
Contents
Introduction
This document describes the various Upgrade/Update/Patch available in Firepower module and their installation procedure using Adaptive Security Device Manager (On-Box Management).
Contributed by Avinash, Prashant Joshi, and Sunil Kumar, Cisco TAC Engineers.
Prerequisites
Requirements
Cisco recommends that you have knowledge of these topics:
- Knowledge of Adaptive Security Appliance(ASA) firewall and Adaptive Security Device Manager (ASDM)
- Firepower Appliance Knowledge
Components Used
The information in this document is based on these software and hardware versions:
- ASA Firepower modules (ASA 5506X/5506H-X/5506W-X, ASA 5508-X, ASA 5516-X ) running software version 5.4.1 and above
- ASA Firepower module (ASA 5515-X, ASA 5525-X, ASA 5545-X, ASA 5555-X) running software version 6.0.0 and above
- The version of ASDM depends on the version running on the ASA. A detailed compatibility matrix ASA and ASDM Compatibility
The information in this document is created from the devices in a particular lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, make sure that you understand the potential impact of any command.
Background Information
Type of Updates
Firepower module has these types of updates:
- Product (Firmware) Upgrade/ Patch
- Vulnerability Database (VDB) Update
- Rule (Signature) Update
- Geolocation Update
Configure Firepower Module Updates
Install Product (Firmware) Update
Product Updates are of two types.
Type 1. Product upgrade is the upgrading system from minor version to major version.
For Example: Upgrading Firepower from version 5.4.x to 6.0.x. These updates contain major enhancement in product functionality.
Type 2. Patch installation is a minor upgrade which includes the bug fixes for the current version.
For Example: Upgrading Firepower Module from Version 5.4.1 to 5.4.x.
Note: Cisco recommends to review Release Notes before installation of any update/patch.
In order to install product updates/patch for the Firepower Module, navigate to Configuration > ASA Firepower Configuration > Updates.
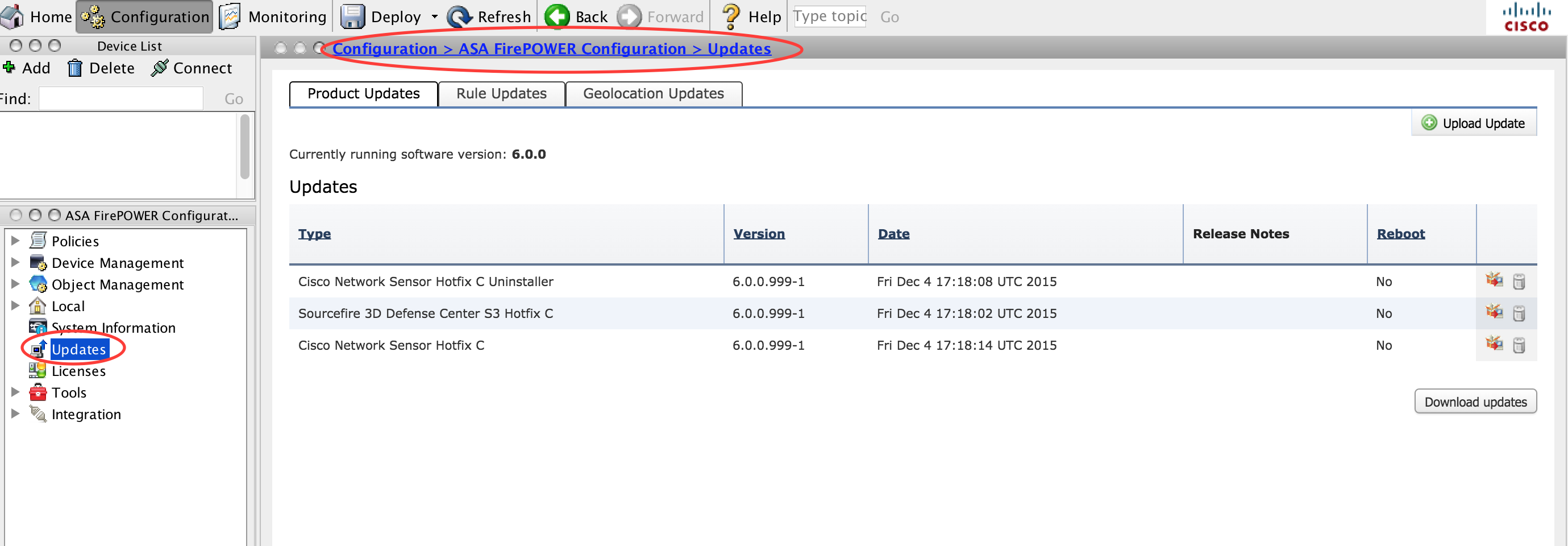
Here, you get two options.
Auto Download: If Firepower Module has Internet access, updates can be downloaded directly from the Cisco site by clicking the Download Updates.
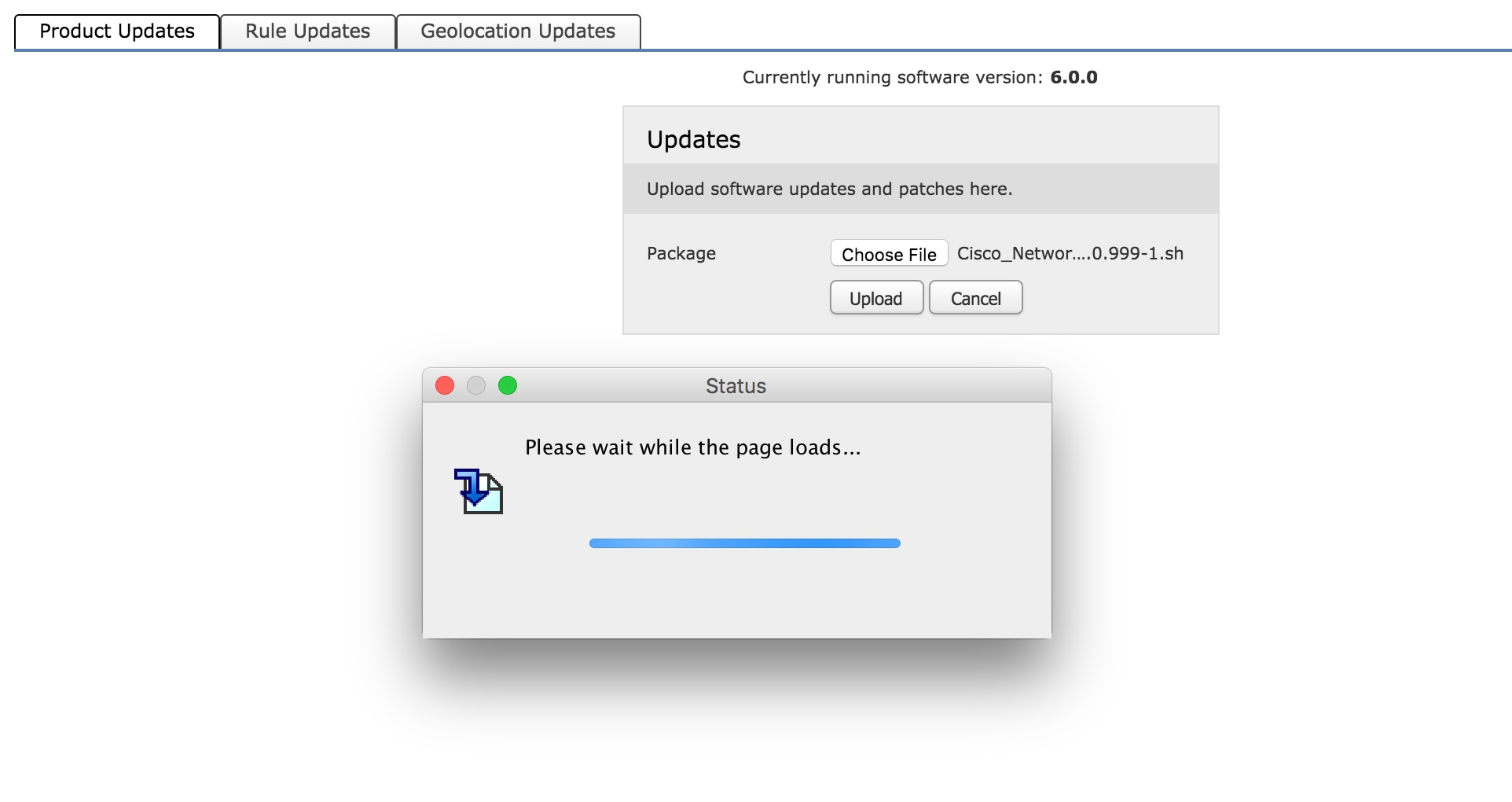
Manual Update: Download the Product Upgrade/ Patch from Cisco site to the local system and upload it manually by clicking Upload Update. Select Choose File and browse the file from the local system then click Upload.
As shown in the image, a progress bar appears while uploading a file to Firepower module.
Once the update is manually uploaded or downloaded from Cisco site, Select the version and click the install icon, as shown in the image.
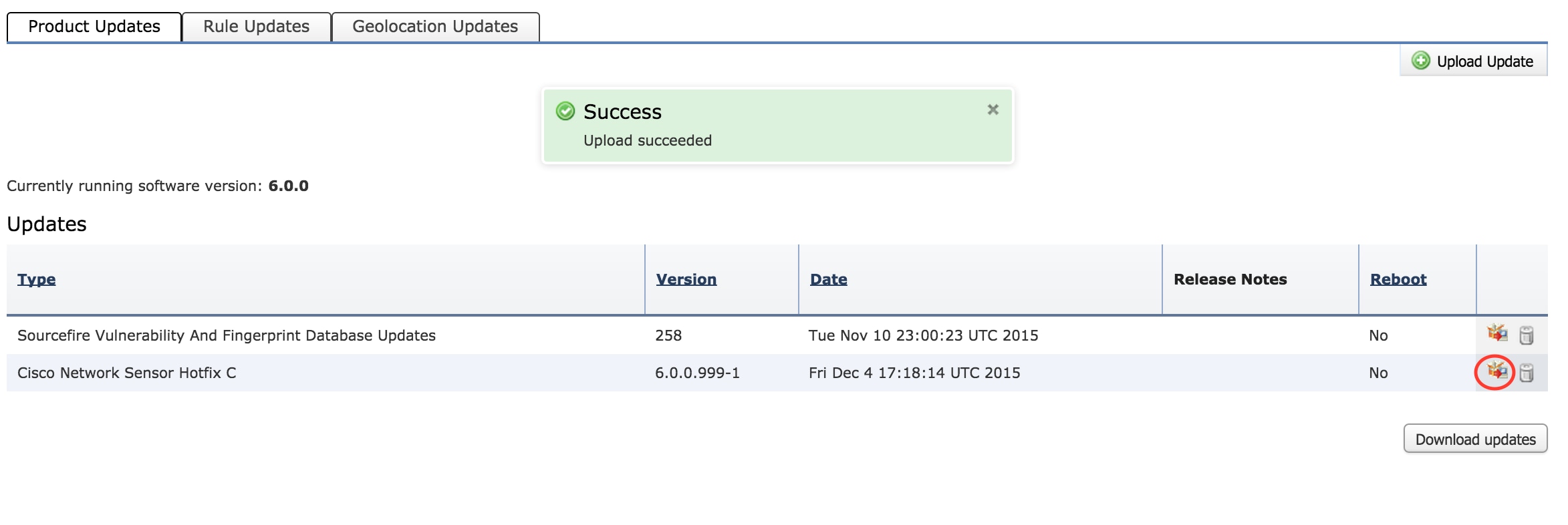
-
Tip: Navigate to Monitoring > Task Status to monitor the upgrade installation.
Install VDB Update
Vulnerability Database ( VDB) update contains updates for Application Detection (Application Filter) and VDB update. VDB update is listed under Product Updates.
In order to configure VDB update, navigate to Configuration > ASA Firepower Configuration > Updates. Hereyou get two options.
Auto Download: If Firepower Module has Internet access, Firepower Module can download the VDB updates directly from Cisco website by clicking on the Download Updates.
Manual Update: Download the VDB update from the Cisco website to the local system and upload it manually by clicking the Upload Update. Select Choose File and browse the file from the local system then click Upload.
Once the update is manually uploaded or downloaded from Cisco website, Select the version and click the install icon, as shown in the image.
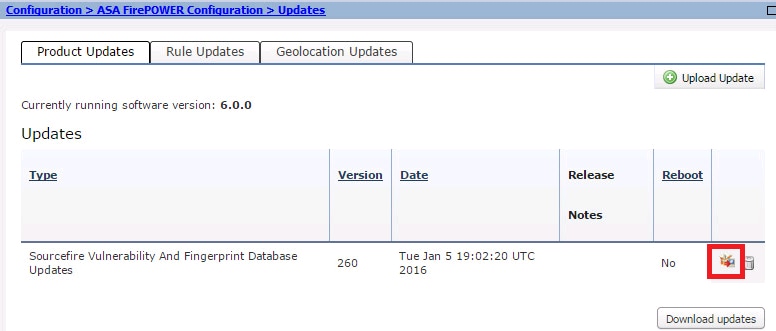
-
Tip: Navigate to Monitoring > Task Status, in order to monitor the VDB installation.
Install Rule Updates
Rule (Signature) updates are Cisco IOS Intrusion Prevention System (IPS) signature updates which Cisco TALOS team releases on a regular basis to provide the coverage for latest threats.
In order to install Rule Updates, navigate to Configuration > ASA Firepower Configuration > Updates and then click Rule Updates.
There are two options to configure the rule updates.
- One-Time Rule Update/ Rule Import
- Recurring Rule Update Import
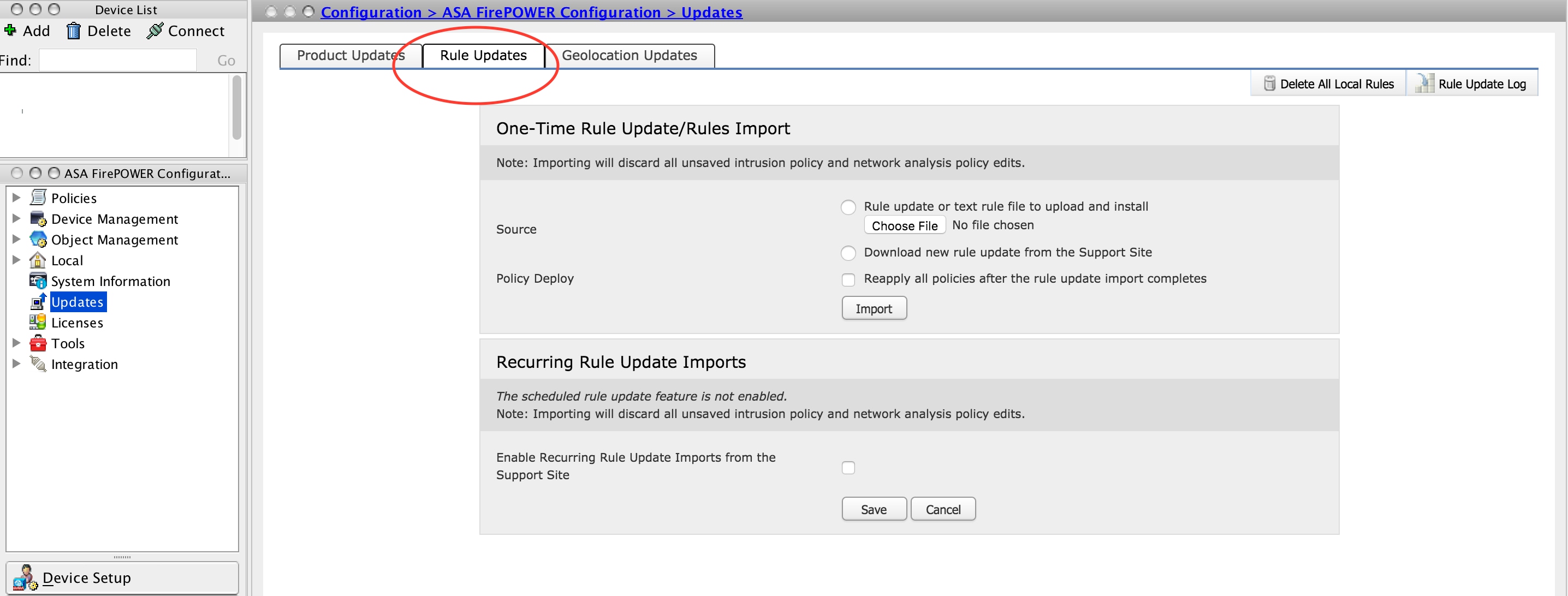
One-Time Rule Update/Rule Import
One-Time Rule Update/Rule Import is a manual process of updating signatures. Here, you have two options.
Auto download: If Firepower Module has Internet connectivity, select Download Rule update from the support site.
Manual Update: If you have manually downloaded the rule update file from Cisco website at your local system then select Rule update or text rule file to upload and install and then click Choose File to upload the signature file.
Once the upload/download of rules is complete, you can select Reapply all policies after rule update import completes then click Import to automatically apply the signature update to all Access Control policies after the Rule update/install has completed.
To apply policies manually, leave the checkbox uncheck.
-
Tip: In order to monitor rule import installation, navigate to Configuration > ASA Firepower Configuration > Updates > rule Updates > Rule Update log.
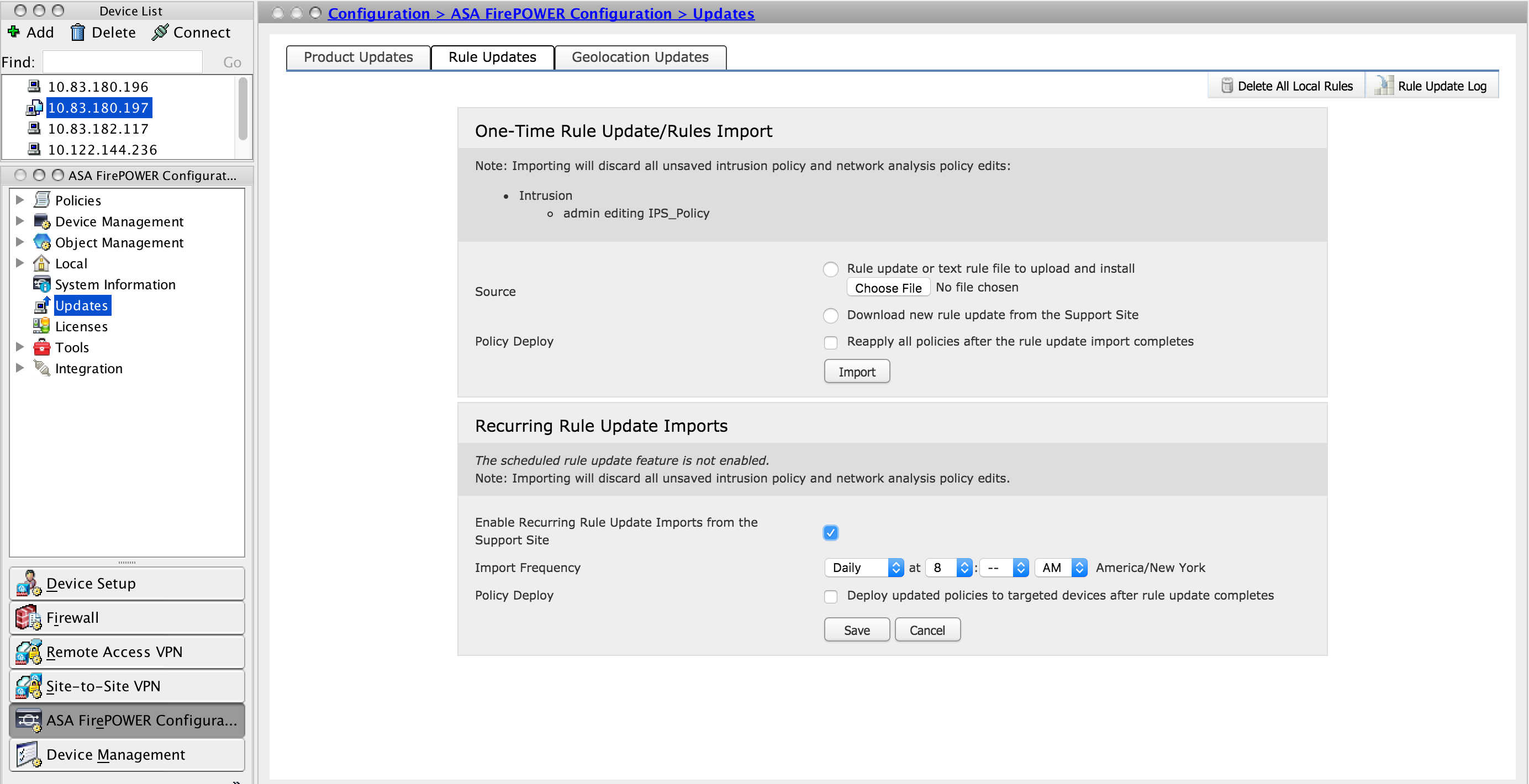
Recurring Rule Update Imports
Recurring Rule Update option is to schedule the Firepower Module to check for rule updates. Download and install new rule if new rule database is available.
Note: Firepower Module must have connectivity to Cisco Support Site.
In order to configure Recurring Rule Updates, Select Enable Recurring Rule Update Imports from the Support Site. Configure frequency to check for the new Rule Update and download/ install rule update if available.
You can choose to apply access policies automatically by selecting Deploy updated policies to targeted devices after rule update completes if you want to apply new rule changes to the module and then click Save.
-
Tip: In order to monitor rule import installation, navigate to Configuration > ASA Firepower Configuration > Updates > Rule Updates > Rule Update log.
Install Geolocation Updates
Geolocation update contains an updated mapping of IP address to the Country and Continent.
There are two options to configure the Geolocation updates, they are as follows:
One-Time Geolocation Updates
One-Time Geolocation Updates is a manual process of updating Geolocation database. There are two ways to get these updates.
Manual Update: If you have manually downloaded the geolocation file from Cisco website then select Upload and install geolocation update and click Choose File to upload the geolocation file.
Auto download: If Firepower Module has internet connectivity, select Download and Install geolocation update from the Support Site and click Import.
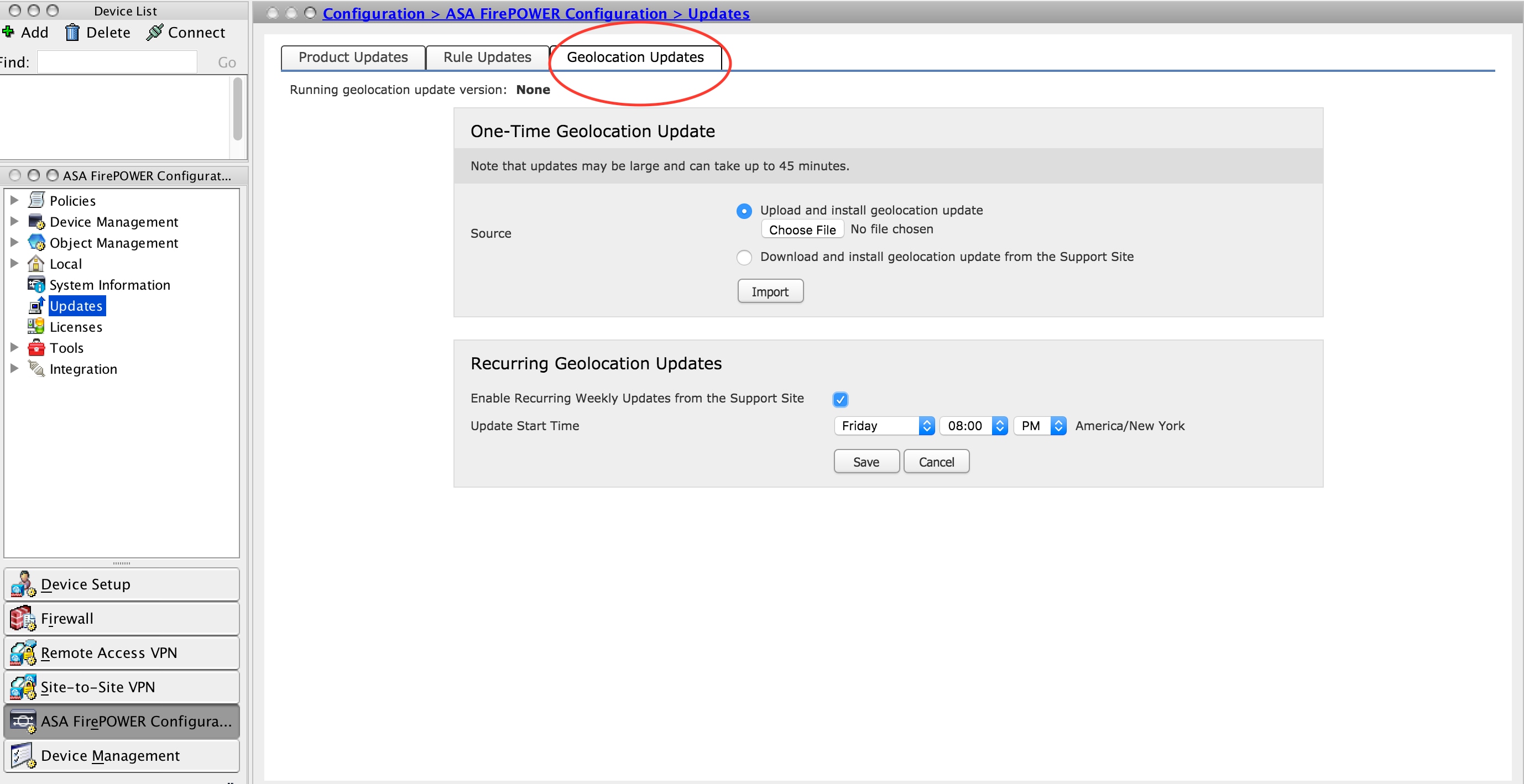
Recurring Geolocation Updates
Recurring Geolocation Updates option is an user-defined schedule to check for the availability of geolocation updates. It downloads and installs the new database if available.
Note: Firepower Module must have connectivity to Cisco Support Site.
In order to configure Recurring Geolocation Updates, Select Enable Recurring Weekly Updates from the Support Site and define the frequency to check the Geolocation Updates & download/ install the updates if it is available and then click Save.
-
Tip: In order to monitor the upgrade installation, navigate to Monitoring > Task Status.
Verify the Update Installation
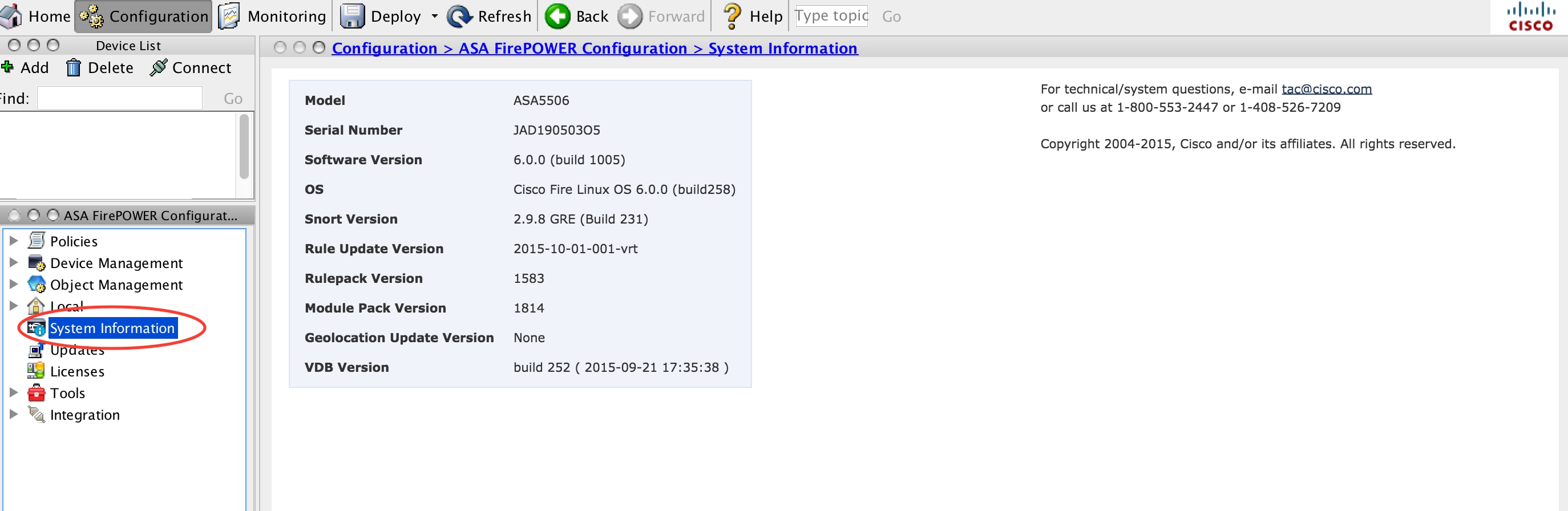
In order to verify the various update installation, navigate to Configuration > ASA Firepower Configuration > System Information.
Software version and OS: The OS section shows the upgraded version of the software
VDB Version: VDB shows the upgraded version of VDB
Geolocation Update version: Geolocation Update Version
Rule Update Version: Shows SRU version
Troubleshoot
There is currently no specific troubleshooting information available for this configuration.
Related Information
Contributed by Cisco Engineers
- AvinashCisco TAC Engineer
- Prashant JoshiCisco TAC Engineer
- Sunil KumarCisco TAC Engineer
Contact Cisco
- Open a Support Case

- (Requires a Cisco Service Contract)
 Feedback
Feedback