Introduction
This document describes the troubleshooting steps for CyberVision Center to ISE integration.
Overview of Best Practices
Best practices are the recommended steps that you must consider in order to ensure the correct operation of system configuration. Recommendations:
- Refer to the Cisco Cyber Vision release notes, and Cisco Identity Services Engine (ISE) release notes, for the latest features, guidelines, limitations, and caveats
- Verify and troubleshoot any new configuration changes after implementing them
CCV-ISE High-Level Flow Diagram
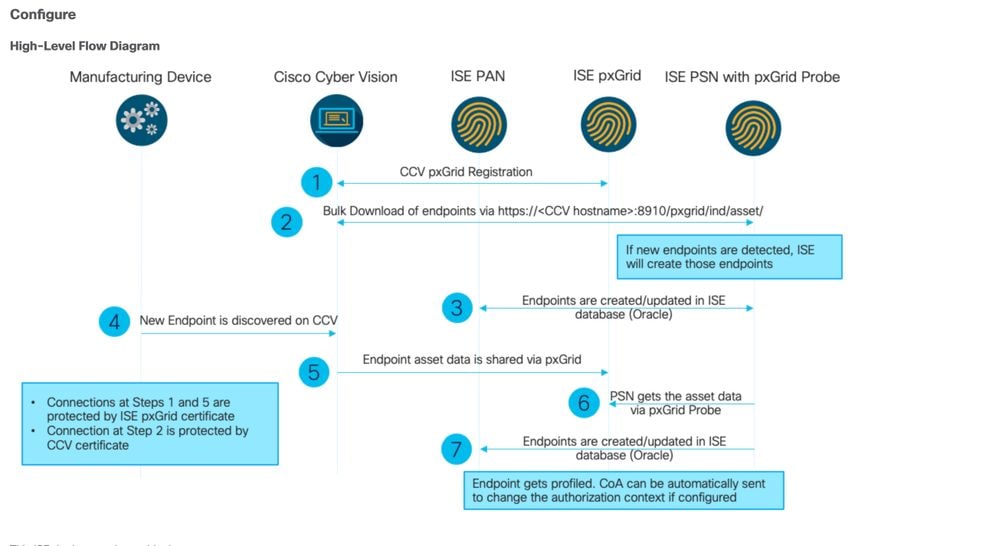
Troubleshooting Guidelines
By answering the upcoming questions, you can determine the troubleshooting path and the components that need further investigation. Respond to the subsequent questions in order to determine the status of your installation:
- Is this a newly installed system or an existing installation?
- Has the CyberVision ever been able to see the ISE?
Check the pxGrid services status using the command systemctl status pxgrid-agent.
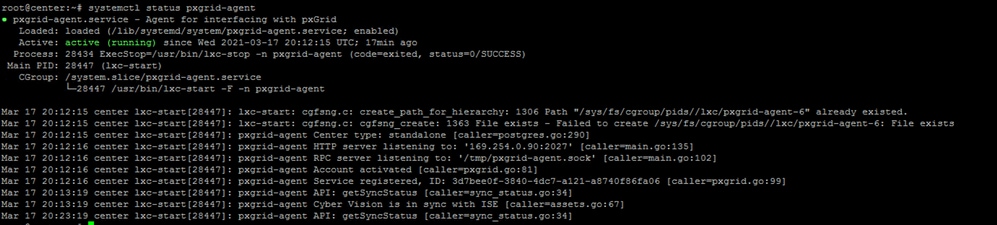
- Does ISE run pxGrid in high availability?
- What changed in the configuration or in the overall infrastructure immediately before the applications started to have problems?
In order to discover a network problem, use the general network troubleshooting steps:
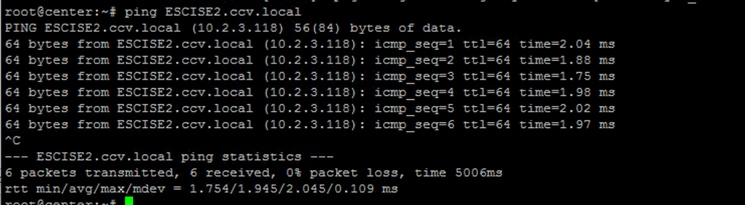
Step 1. Are you able to ping CyberVision Center Hostname from ISE?
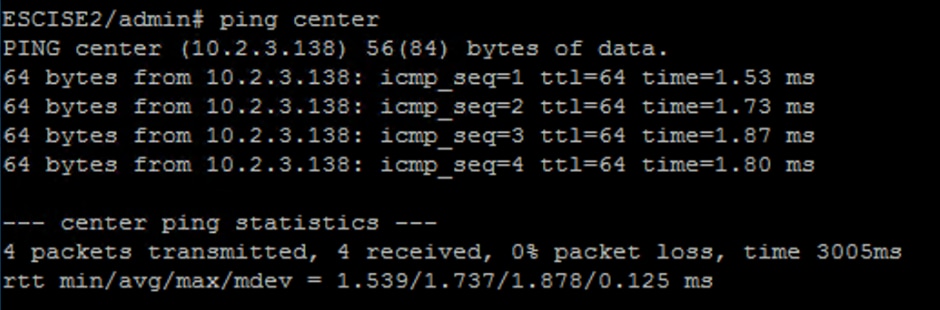
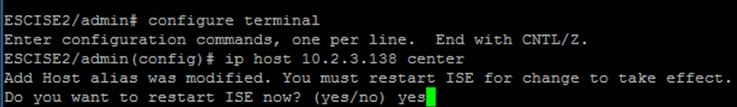
If unable to ping, connect to ISE CLI using Secure Shell (SSH) and Add hostname.
Step 2. Are you able to ping ISE Hostname from CyberVisiion Center?
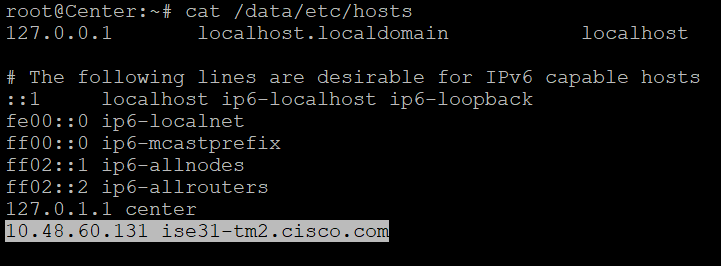
If not, try to add the ISE hostname to the /data/etc/hosts file in Center.
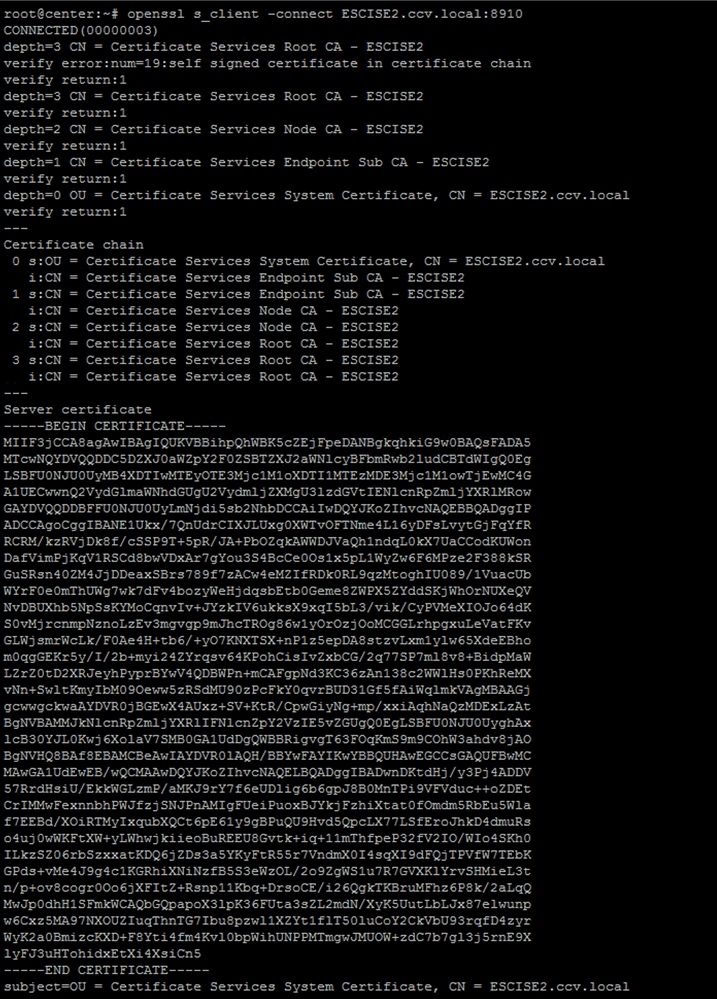
Step 3. Discover certificate issues.
Enter the command openssl s_client -connect YourISEHostname:8910 from CyberVision Center.
Data to Collect
For network issues:
A scheme showing those details between the center and ISE is helpful:
- Firewall rules
- Static routes
- Configuration of the Gateway
- VLAN configurations
- Logs to collect for all ISE issues:
You can start by collecting a Center diagnostic file in order to avoid losing data.
Then activate advanced logs on the center using this procedure:
Create two files in the folder /data/etc/sbs.
The first file must be named listener.conf and contain the content:
(Note the leading space in front of the loglevel.)
root@Center:~# cat /data/etc/sbs/listener.conf
configlog:
loglevel: debug
root@Center:~#
The second file must be named pxgrid-agent.conf and contain the content:
(Note the leading space in front of the loglevel.)
root@Center:~# cat /data/etc/sbs/pxgrid-agent.conf
configlog:
loglevel: debug
Once both files are created, reboot the Center, or restart the sbs-burrow and pxgrid-agent services.
Restart service using the command:
#systemctl restart sbs-burrow
#systemctl restart pxgrid-agent
Then collect the pxGrid logs (use the filetransfer tools in order to export the logs from the Center).
root@Center:~# journalctl -u pxgrid-agent > /data/tmp/pxgridLogs.log
Collect tcpdump captures for analyzing communication flow between the Center and ISE.
root@Center:~# tcpdump -i eth0 -n host CCV_IP and host ISE_IP -w /data/tmp/ccv_ise.pcap
- Enable Debugs on ISE and collect support bundle.
In order to enable debugs on ISE, navigate to Administration > System > Logging > Debug Log Configuration. Set log levels to these:
|
Persona
|
Component Name
|
Log Level
|
File to Check
|
|
|
PAN (optional)
|
profiler
|
DEBUG
|
profiler.log
|
|
|
PSN with pxGrid probe enabled
|
profiler
|
DEBUG
|
profiler.log
|
|
|
PxGrid
|
pxgrid
|
TRACE
|
pxgrid-server.log
|
|
Expected Log Messages
Debug logs of the pxGrid-agent in the center show the agent being started, service registered, Cisco Cyber Vision (CCV) Establishing Simple (or Streaming) Text Orientated Messaging Protocol (STOMP) connection with ISE, and sending update operation for an asset/component:
Jul 11 13:05:02 center systemd[1]: Started Agent for interfacing with pxGrid.
Jul 11 13:05:02 center pxgrid-agent[5404]: pxgrid-agent Center type: standalone [caller=postgres.go:543]
Jul 11 13:05:03 center pxgrid-agent[5404]: pxgrid-agent RPC server listening to: '/tmp/pxgrid-agent.sock' [caller=main.go:119]
Jul 11 13:05:03 center pxgrid-agent[5404]: pxgrid-agent HTTP server listening to: '169.254.0.90:2027' [caller=main.go:154]
Jul 11 13:05:03 center pxgrid-agent[5404]: pxgrid-agent Request path=/pxgrid/control/AccountActivate body={} [caller=control.go:147]
Jul 11 13:05:03 center pxgrid-agent[5404]: pxgrid-agent Account activated [caller=pxgrid.go:58]
Jul 11 13:05:03 center pxgrid-agent[5404]: pxgrid-agent Request path=/pxgrid/control/ServiceRegister body={"name":"com.cisco.endpoint.asset","properties":{"assetTopic":"/topic/com.cisco.endpoint.asset","restBaseUrl":"https://Center:8910/
Jul 11 13:05:04 center pxgrid-agent[5404]: pxgrid-agent Service registered, ID: c514c790-2361-47b5-976d-4a1b5ccfa8b7 [caller=pxgrid.go:76]
Jul 11 13:05:04 center pxgrid-agent[5404]: pxgrid-agent Request path=/pxgrid/control/ServiceLookup body={"name":"com.cisco.ise.pubsub"} [caller=control.go:147]
Jul 11 13:05:05 center pxgrid-agent[5404]: pxgrid-agent Request path=/pxgrid/control/AccessSecret body={"peerNodeName":"com.cisco.ise.pubsub"} [caller=control.go:147]
Jul 11 13:05:06 center pxgrid-agent[5404]: pxgrid-agent Websocket connect url=wss://labise. aaalab .com:8910/pxgrid/ise/pubsub [caller=endpoint.go:129]
Jul 11 13:05:07 center pxgrid-agent[5404]: pxgrid-agent STOMP CONNECT host=10.48.78.177 [caller=endpoint.go:138]
Jul 11 13:06:59 center pxgrid-agent[5404]: pxgrid-agent STOMP SEND destination=/topic/com.cisco.endpoint.asset body={"opType":"UPDATE","asset":{"assetId":"01:80:c2:00:00:00","assetName":"LLDP/STP bridges Multicast 0:0:0","assetIpAddress"
Jul 11 13:10:04 center pxgrid-agent[5404]: pxgrid-agent Request path=/pxgrid/control/ServiceReregister body={"id":"c514c790-2361-47b5-976d-4a1b5ccfa8b7"} [caller=control.go:147]
Expected message format post successful integration and assetGroup attribute is published without a value, as shown:
Jan 25 11:05:49 center pxgrid-agent[1063977]: pxgrid-agent STOMP SEND destination=/topic/com.cisco.endpoint.asset body={"opType":"UPDATE","asset":{"assetId":"48:4d:7e:e0:e2:52","assetName":"Dell 10.234.176.35","assetIpAddress":"10.234.176.35","assetMacAddress":"48:4d:7e:e0:e2:52","assetVendor":"Dell Inc.","assetProductId":"","assetSerialNumber":"","assetDeviceType":"","assetSwRevision":"","assetHwRevision":"","assetProtocol":"SMB","assetCustomAttributes":[{"key":"assetSource","value":"CCV"},{"key":"assetGroup","value":""},{"key":"assetCustomName","value":"test"},{"key":"assetGroupPath","value":""}],"assetConnectedLinks":[]}} length=513 [caller=endpoint.go:149] Expected message format (assetGroup with a value, as shown). This confirms that CyberVision Center is sending the attributes and if the same is not further reflected on the ISE side, you must investigate with ISE further.
Jan 25 11:09:28 center pxgrid-agent[1063977]: pxgrid-agent STOMP SEND destination=/topic/com.cisco.endpoint.asset body={"opType":"UPDATE","asset":{"assetId":"48:4d:7e:e0:e2:52","assetName":"Dell 10.234.176.35","assetIpAddress":"10.234.176.35","assetMacAddress":"48:4d:7e:e0:e2:52","assetVendor":"Dell Inc.","assetProductId":"","assetSerialNumber":"","assetDeviceType":"","assetSwRevision":"","assetHwRevision":"","assetProtocol":"SMB","assetCustomAttributes":[{"key":"assetSource","value":"CCV"},{"key":"assetGroup","value":"test group"},{"key":"assetCustomName","value":"test"},{"key":"assetGroupPath","value":"test group"}],"assetConnectedLinks":[]}} length=533 [caller=endpoint.go:149]
Related Information








 Feedback
Feedback