Introduction
This document describes what to verify in the mail logs on the Cisco Email Security Appliance (ESA) when messages are received with a valid Secure/Multipurpose Internet Mail Extensions (S/MIME) configuration.
How to verify messages received with S/MIME on ESA
S/MIME is a standards-based method for sending and receiving secure, verified email messages. S/MIME uses public/private key pair to encrypt or sign messages.
• If the message is encrypted, only the message recipient can open the encrypted message.
• If the message is signed, the message recipient can validate the identity of the sender and can be assured that the message has not been altered while in transit.
With a valid S/MIME sending profile configured on the ESA, messages can be sent with one of four modes:
• Sign
• Encrypt
• Sign/Encrypt (Sign and then encrypt)
• Triple (Sign, encrypt, and then sign again)
Likewise, messages can be received from other senders that have used valid S/MIME certificates for signing or encryption.
For the recipient, they will need to be using an email application in order to properly process, view, and accept the associated digital signature or encryption. Common email applications that will present the digital signature or encryption option are Microsoft Outlook, Mail (OSX), and Mozilla Thunderbird. The message itself will contain a .p7s (smime.p7s) or .p7m (smime.p7m) attachment. These attachment files will be recorded with the message ID (MID) in the mail logs.
The appearance of an attachment with the .p7s file is flag that the message carries a digital signature.
The appearance of an attachment with the .p7m file is a flag that the message carries an encrypted S/MIME signature and encryption. The message contents and attachments are enveloped in an smime.p7m file. A private key matching the public key in the message is needed to open the document file.
If an email application does not handle digital signatures, a .p7s of .p7m file may appear as an attachment to the email message.
Sign
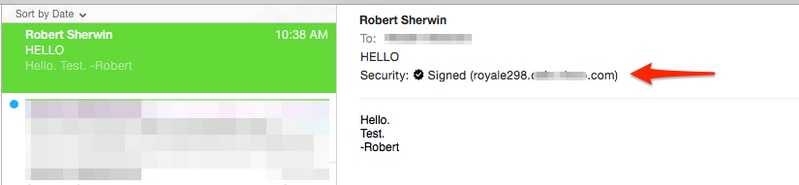
If the message was sent from the sender with a S/MIME sending profile that was set to Sign, on the recipient ESA, when viewing the mail logs for inbound messages it would indicate a .p7s attachement :
Fri Dec 5 10:38:12 2014 Info: MID 471 attachment 'smime.p7s'
In the recipient email application this would be seen similar to the following.
Example as shown Outlook 2013 (Windows), notice the badge or certificate symbol indicated:

Example as shown Mail (OSX):
Encrypt
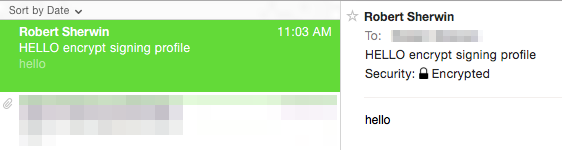
If the message was sent from the sender with a S/MIME sending profile that was set to Encrypt, on the recipient ESA, when viewing the mail logs for inbound messages it would indicate a .p7m attachement :
Fri Dec 5 11:03:44 2014 Info: MID 474 attachment 'smime.p7m'
In the recipient email application this would be seen similar to the following, notice the padlock symbol indicated for both examples.
Example as shown Outlook 2013 (Windows):

Example as shown Mail (OSX):
Sign/Encrypt
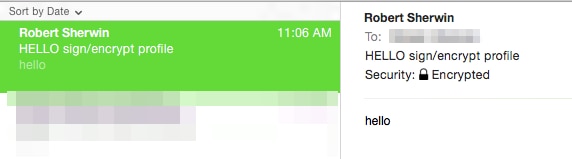
If the message was sent from the sender with a S/MIME sending profile that was set to Sign/Encrypt, on the recipient ESA, when viewing the mail logs for inbound messages it would indicate a .p7m attachement :
Fri Dec 5 11:06:43 2014 Info: MID 475 attachment 'smime.p7m'
In the recipient email application this would be seen similar to the following, notice the padlock symbol indicated.
Example as shown Outlook 2013 (Windows):

Example as shown Mail (OSX):
Triple
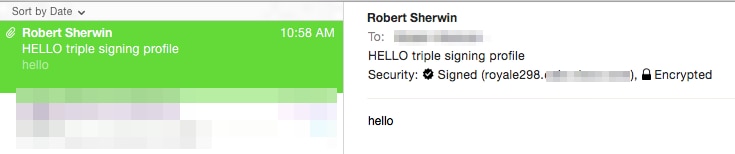
Finally, if the message was sent from the sender with a S/MIME sending profile that was set to Triple, on the recipient ESA, when viewing the mail logs for inbound messages it would indicate both a .p7m and .p7s attachment:
Fri Dec 5 10:58:11 2014 Info: MID 473 attachment 'smime.p7m'
Fri Dec 5 10:58:11 2014 Info: MID 473 attachment 'smime.p7s'
In the recipient email application this may vary, based on the email application in use.
Example as shown Outlook 2013 (Windows), notice the badge or certificate symbol indicated:

Example as shown Mail (OSX), notice that both the badge for signed is presented and the padlock for encryption indicated:
Example as shown Office 2011 (OSX), notice the padlock indicated and the message, "This message was digitally signed and encrypted" included:
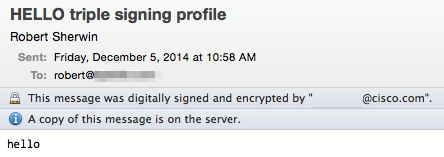
Certificate Verification
Based on the email application in use, and the recipient's preference, or company security policies, viewing and accepting the certificate will vary.
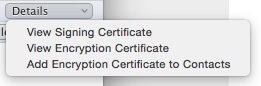
For the Triple example above, with Office 2011 (OSX), on the signed and encrypted message line there is a details dropdown option:
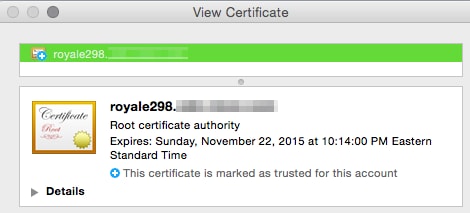
Selecting View Signing Certificate presents the actual signing certificate information of the ESA this was originally sent from:
Related Information












 Feedback
Feedback