Introduction
This document describes how to enable Transport Layer Security version 1.0 (TLSv1.0) on the Cisco Email Security Appliance (ESA) and Cisco Cloud Email Security (CES) allocations.
How can you enable TLSv1.0 on the Cisco ESA and CES?
Note: Cisco CES allocations provisioned have TLSv1.0 disabled by default as per security requirements due to vulnerability impacts on the TLSv1.0 protocol. This includes the cipher string to remove all usage of the SSLv3 shared cipher suite.
Caution: The SSL/TLS methods and ciphers are set based on the specific security policies and preferences of your company. For third-party information in regards to ciphers, refer to the Security/Server Side TLS Mozilla document for recommended server configurations and detailed information.
In order to enable TLSv1.0 on your Cisco ESA or CES, you can do so from the Graphical User Interface (GUI) or Command Line Interface (CLI).
Note: In order to get access to your CES on the CLI please review: Accessing the Command Line Interface (CLI) of Your Cloud Email Security (CES) Solution
Graphical User Interface
- Log into the GUI.
- Navigate to System Administration > SSL Configuration.
- Select Edit Settings.
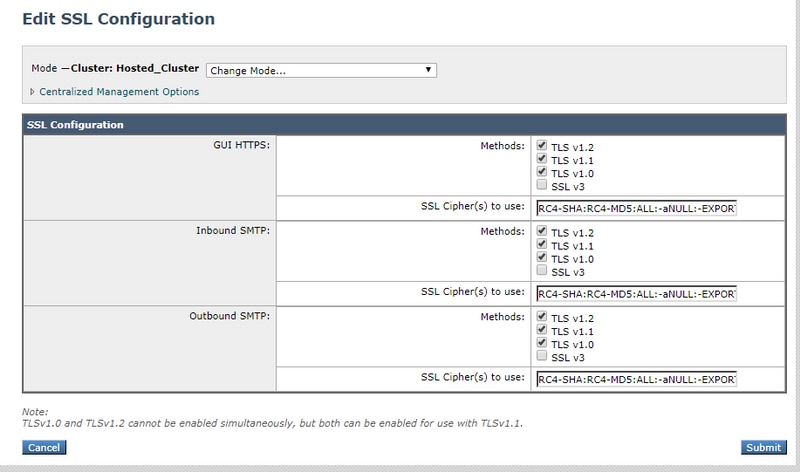
- Check the TLSv1.0 box. It is important to note that TLSv1.2 and cannot be enabled in conjunction with TLSv1.0 unless the bridging protocol TLSv1.1 is also enabled as shown in the image:
Command Line Interface
- Run the command sslconfig.
- Run the command GUI or INBOUND or OUTBOUND depending on which item you want to enable TLSv1.0 for:
(Cluster Hosted_Cluster)> sslconfig
sslconfig settings:
GUI HTTPS method: tlsv1_2
GUI HTTPS ciphers:
RC4-SHA
RC4-MD5
ALL
-aNULL
-EXPORT
Inbound SMTP method: tlsv1_2
Inbound SMTP ciphers:
RC4-SHA
RC4-MD5
ALL
-aNULL
-EXPORT
Outbound SMTP method: tlsv1_2
Outbound SMTP ciphers:
RC4-SHA
RC4-MD5
ALL
-aNULL
-EXPORT
Choose the operation you want to perform:
- GUI - Edit GUI HTTPS ssl settings.
- INBOUND - Edit Inbound SMTP ssl settings.
- OUTBOUND - Edit Outbound SMTP ssl settings.
- VERIFY - Verify and show ssl cipher list.
- CLUSTERSET - Set how ssl settings are configured in a cluster.
- CLUSTERSHOW - Display how ssl settings are configured in a cluster.
[]> INBOUND
Enter the inbound SMTP ssl method you want to use.
1. TLS v1.0
2. TLS v1.1
3. TLS v1.2
4. SSL v2
5. SSL v3
[3]> 1-3
Enter the inbound SMTP ssl cipher you want to use.
[RC4-SHA:RC4-MD5:ALL:-aNULL:-EXPORT]>
Ciphers
ESAs and CES allocations can be configured with strict cipher suites, it is important to ensure SSLv3 ciphers are not blocked when you enable the TLSv1.0 protocol. Failure to allow the SSLv3 cipher suites result in TLS negotiation failures or abrupt TLS connection closures.
Sample cipher string:
HIGH:MEDIUM:@STRENGTH:!aNULL:!eNULL:!LOW:!DES:!MD5:!EXP:!PSK:!DSS:!RC2:!RC4:!SEED:!ECDSA:!ADH:!IDEA:!3DES:!SSLv2:!SSLv3:!TLSv1:-aNULL:-EXPORT:-IDEA
This cipher string stops the ESA/CES from allowing negotiation on SSLv3 ciphers as indicated on !SSLv3:, this means when the protocol is requested in the handshake, the SSL handshake fails as there are no shared ciphers available for negotiation.
In order to ensure the sample cipher string functions with TLSv1.0, it needs to be modified to remove !SSLv3:!TLSv1: seen in the replaced cipher string:
HIGH:MEDIUM:@STRENGTH:!aNULL:!eNULL:!LOW:!DES:!MD5:!EXP:!PSK:!DSS:!RC2:!RC4:!SEED:!ECDSA:!ADH:!IDEA:!3DES:!SSLv2:-aNULL:-EXPORT:-IDEA
Note: You can verify the cipher suites shared on SSL handshake on the ESA/CES CLI with the VERIFY command.
Possible errors logged in the mail_logs/Message Tracking but not limited to:
Sun Feb 23 10:07:07 2020 Info: DCID 1407038 TLS failed: (336032784, 'error:14077410:SSL routines:SSL23_GET_SERVER_HELLO:sslv3 alert handshake failure')
Sun Feb 23 10:38:56 2020 Info: DCID 1407763 TLS failed: (336032002, 'error:14077102:SSL routines:SSL23_GET_SERVER_HELLO:unsupported protocol')
Related Information

 Feedback
Feedback