Introduction
This document describes common methods for troubleshooting misclassifications and scanning failures (or misses) related to Data Loss Prevention (DLP) on the Email Security Appliance (ESA).
Prerequisites
- ESA running AsyncOS 11.x or newer.
- DLP feature key installed and in use.
Important Information
It is critical to note that DLP on the ESA is plug-and-play in the sense that you can enable it, create a policy, and start scanning for sensitive data; however, you should also be aware that the best results will only be achieved after tuning DLP to fit your company-specific requirements. This would include things such as types of DLP policies, policy matching details, adjusting the severity scale, filtering, and additional customizations.
Violation vs. No Violation Log Examples
Here are some examples of DLP violations that you may see within the mail logs and/or Message Tracking. The logline will include a timestamp, logging level, MID #, violation or no violation, severity and risk factor, and the policy that was matched.
Thu Jul 11 16:05:28 2019 Info: MID 40 DLP violation. Severity: CRITICAL (Risk Factor: 96). DLP policy match: 'US HIPAA and HITECH'.
Thu Jul 11 16:41:50 2019 Info: MID 46 DLP violation. Severity: LOW (Risk Factor: 24). DLP policy match: 'US State Regulations (Indiana HB 1101)'.
When there is no violation found, then the mail logs and/or Message Tracking will simply log DLP no violation.
Mon Jan 20 12:59:01 2020 Info: MID 26245883 DLP no violation
Troubleshooting Checklist
Provided below are common items that can be reviewed when dealing with DLP misclassifications or scanning failures/misses.
Note: This is not an exhaustive list. Please contact Cisco TAC if you have something you wish to see included.
Confirming the Version of DLP engine
DLP engine updates are not automatic by default, so it is crucial to make sure you're running the newest version that includes any recent enhancements or bug fixes.
You can navigate to Data Loss Prevention under Security Services in the GUI to confirm the current engine version and to see if any updates are available. If an update is available then you can click Update Now to perform the update.

Enabling Matched Content Logging
DLP offers the option to log the content that violates your DLP policies, along with the surrounding content. This data can then be viewed in Message Tracking to assist with tracking down what content within an email may be causing a particular violation.
Caution: It is important to know that if enabled, this content may include sensitive data such as credit card numbers and social security numbers, Etc.
You can navigate to Data Loss Prevention under Security Services in the GUI to see if Matched Content Logging is enabled.

Example of Matched Content Logging Seen in Message Tracking

Reviewing the Scan Behavior Configuration
The Scan Behavior configuration on the ESA will also impact the functionality behind DLP scanning. Looking at the screenshot below as an example, which has a configured maximum attachment scanning size of 5M, anything larger may cause DLP scanning to be missed. Also, the action for attachments with MIME types setting is another common item you'll want to review. This should be set to the default of Skip so that the MIME types listed are being skipped and everything else is being scanned. If instead it is set to Scan, then we only scan those MIME types listed in the table.
Similarly, other settings listed here may impact DLP scanning and should be taken into account depending on the attachment/email content.
You can navigate to Scan Behavior under Security Services in the GUI, or by running the scanconfig command within the CLI.

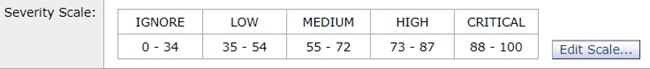
Reviewing the Severity Scale Configuration
The default severity scale thresholds are going to be sufficient for most environments; however, if you need to modify them to assist with False Negative (FN) or False Positive (FP) matching then you can do so. You can also confirm your DLP policy is utilizing the recommended default thresholds by creating a new dummy policy and then comparing them.
Note: Different predefined policies (e.g. US HIPAA vs. PCI-DSS) will have different scaling.
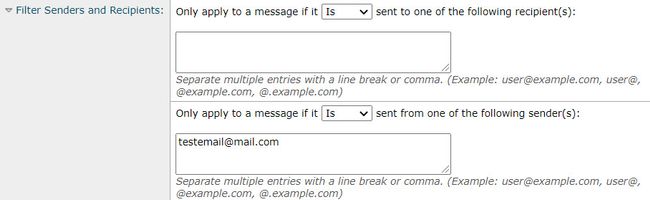
Reviewing the Email Addresses Added to the Filter Senders and Recipients Fields
Check that any entries entered into either of these fields match the correct case of the sender and/or recipient email addresses. The Filter Senders and Recipients field is case sensitive. The DLP policy will not trigger if the email address looks like "TestEmail@mail.com" in the mail client and is entered as "testemail@mail.com" into these fields.
Related Information
