Firepower eXtensible Operating System (FXOS) 2.2: Chassis Authentication/Authorization for remote management with ISE using RADIUS
Available Languages
Bias-Free Language
The documentation set for this product strives to use bias-free language. For the purposes of this documentation set, bias-free is defined as language that does not imply discrimination based on age, disability, gender, racial identity, ethnic identity, sexual orientation, socioeconomic status, and intersectionality. Exceptions may be present in the documentation due to language that is hardcoded in the user interfaces of the product software, language used based on RFP documentation, or language that is used by a referenced third-party product. Learn more about how Cisco is using Inclusive Language.
Contents
Introduction
This document describes how to configure RADIUS Authentication and Authorization for the Firepower eXtensible Operating System (FXOS) chassis via Identity Services Engine (ISE).
The FXOS chassis includes the following User Roles:
- Administrator - Complete read-and-write access to the entire system. The default admin account is assigned this role by default and it cannot be changed.
- Read-Only - Read-only access to system configuration with no privileges to modify the system state.
- Operations - Read-and-write access to NTP configuration, Smart Call Home configuration for Smart Licensing, and system logs, including syslog servers and faults. Read access to the rest of the system.
- AAA - Read-and-write access to users, roles, and AAA configuration. Read access to the rest of the system.
Via CLI this can be seen as follows:
fpr4120-TAC-A /security* # show role
Role:
Role Name Priv
---------- ----
aaa aaa
admin admin
operations operations
read-only read-only
Contributed by Tony Remirez, Jose Soto, Cisco TAC Engineers.
Prerequisites
Requirements
Cisco recommends that you have knowledge of these topics:
- Knowledge of Firepower eXtensible Operating System (FXOS)
- Knowledge of ISE configuration
Components Used
The information in this document is based on these software and hardware versions:
- Cisco Firepower 4120 Security Appliance version 2.2
- Virtual Cisco Identity Services Engine 2.2.0.470
The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, make sure that you understand the potential impact of any command.
Configure
The goal of the configuration is to:
- Authenticate users logging into the FXOS’s Web-based GUI and SSH by means of ISE
- Authorize users logging into the FXOS’s Web-based GUI and SSH according to their respective User Role by means of ISE.
- Verify the proper operation of authentication and authorization on the FXOS by means of ISE
Network Diagram
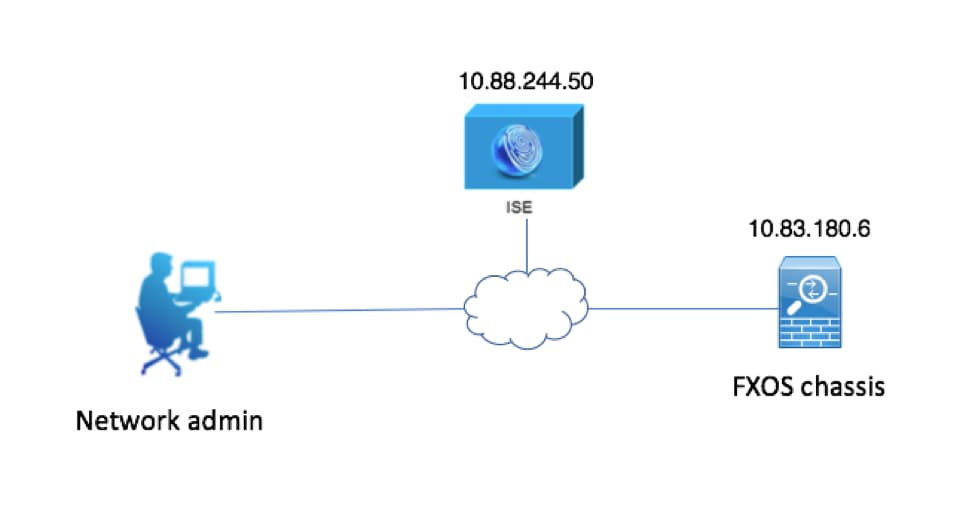
Configurations
Configuring the FXOS Chassis
Creating a RADIUS Provider using Chassis Manager
Step 1. Navigate to Platform Settings > AAA.
Step 2. Click the RADIUS tab.
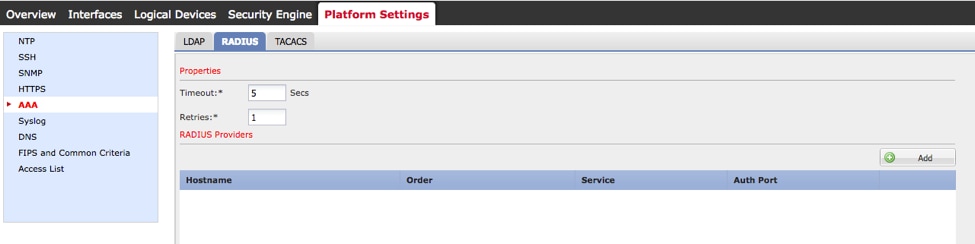
Step 3. For each RADIUS provider that you want to add (Up to 16 providers).
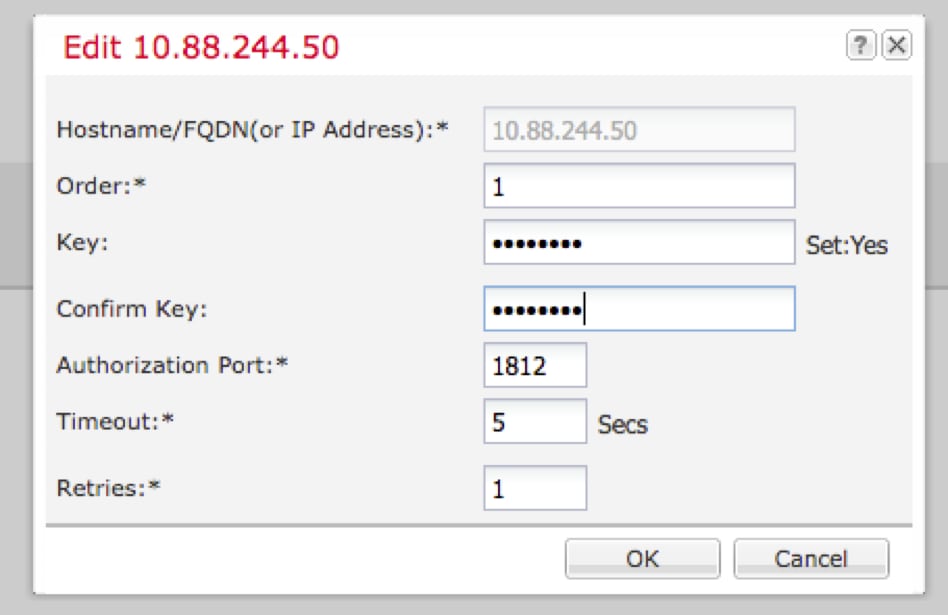
3.1. In RADIUS Providers area, click Add.
3.2. Once the Add RADIUS Provider dialog box opens, enter the required values.
3.3. Click OK to close the Add RADIUS Provider dialog box.
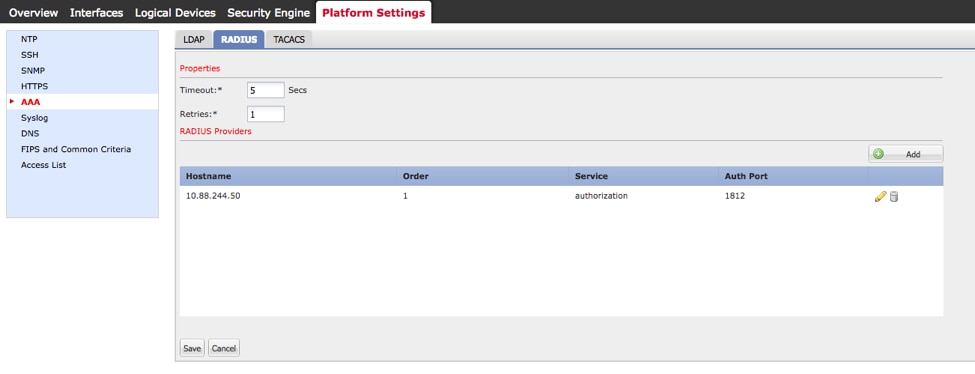
Step 4. Click Save.
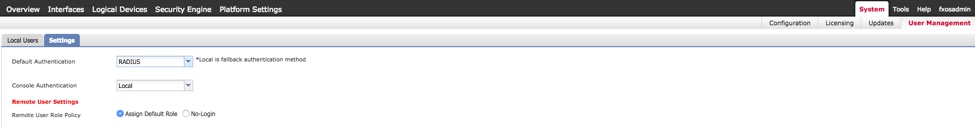
Step 5. Navigate to System > User Management > Settings.
Step 6. Under Default Authentication choose RADIUS.
Creating a RADIUS Provider using CLI
Step 1. In order to enable RADIUS authentication, run the following commands.
fpr4120-TAC-A# scope security
fpr4120-TAC-A /security # scope default-auth
fpr4120-TAC-A /security/default-auth # set realm radius
Step 2. Use the show detail command to display the results.
fpr4120-TAC-A /security/default-auth # show detail
Default authentication:
Admin Realm: Radius
Operational Realm: Radius
Web session refresh period(in secs): 600
Session timeout(in secs) for web, ssh, telnet sessions: 600
Absolute Session timeout(in secs) for web, ssh, telnet sessions: 3600
Serial Console Session timeout(in secs): 600
Serial Console Absolute Session timeout(in secs): 3600
Admin Authentication server group:
Operational Authentication server group:
Use of 2nd factor: No
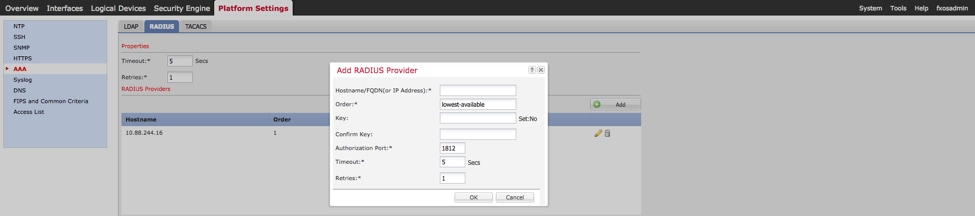
Step 3. In order to configure RADIUS server parameters run the following commands.
fpr4120-TAC-A# scope security
fpr4120-TAC-A /security # scope radius
fpr4120-TAC-A /security/radius # enter server 10.88.244.50
fpr4120-TAC-A /security/radius/server # set descr "ISE Server"
fpr4120-TAC-A /security/radius/server* # set key
Enter the key: ******
Confirm the key: ******
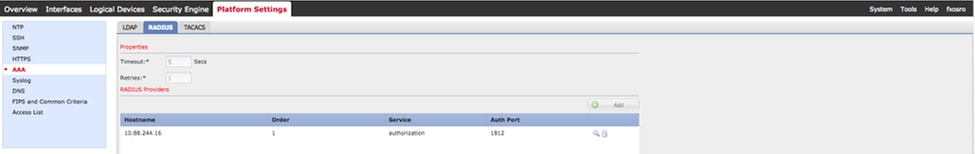
Step 4. Use the show detail command to display the results.
fpr4120-TAC-A /security/radius/server* # show detail
RADIUS server:
Hostname, FQDN or IP address: 10.88.244.50
Descr:
Order: 1
Auth Port: 1812
Key: ****
Timeout: 5
Configuring the ISE server
Adding the FXOS as a network resource
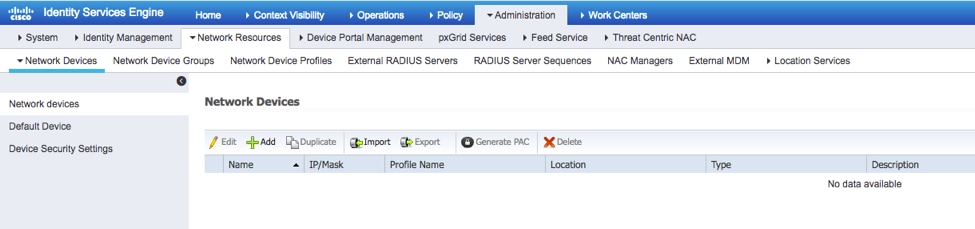
Step 1. Navigate to Administration > Network Resources > Network Devices.
Step 2. Click ADD
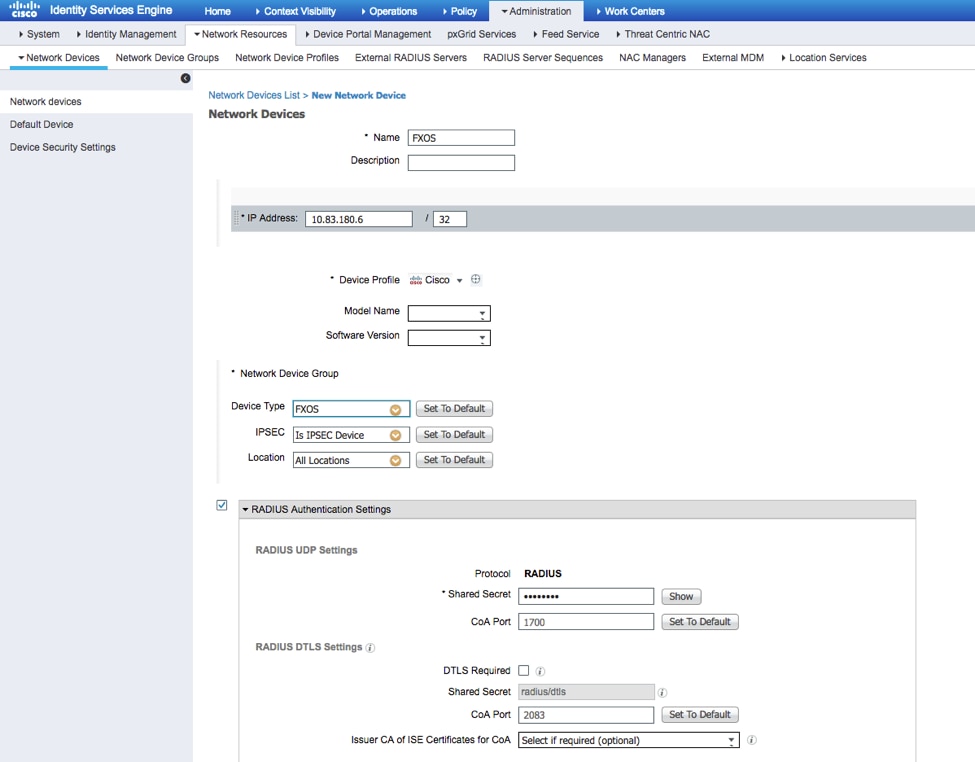
Step 3. Enter the required values (Name, IP Address, Device Type and Enable RADIUS and add the KEY), click Submit.
Creating the Identity groups and Users
Step 1. Navigate to Administration > Identity Management > Groups > User Identity Groups.
Step 2. Click ADD.
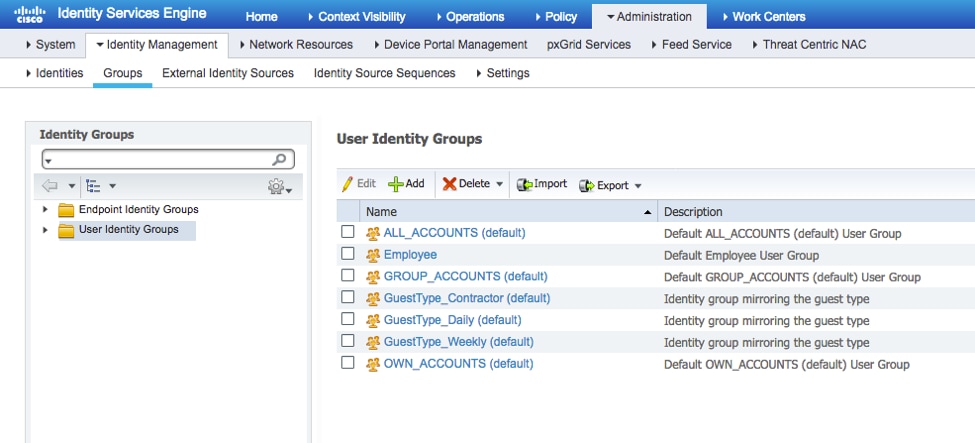
Step 3. Enter the value for Name and click Submit.
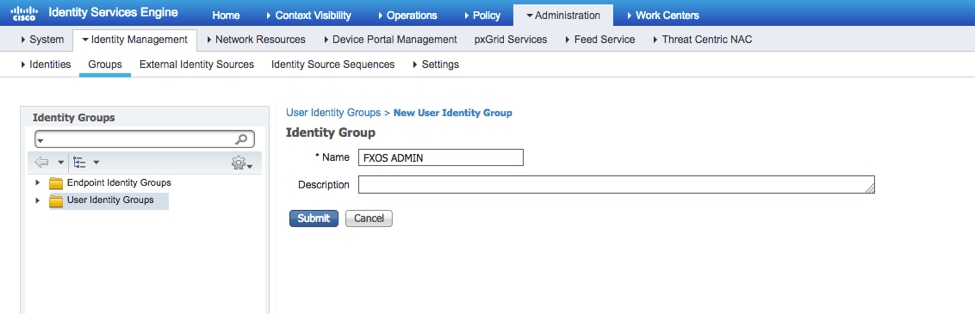
Step 4. Repeat step 3 for all the required User Roles.
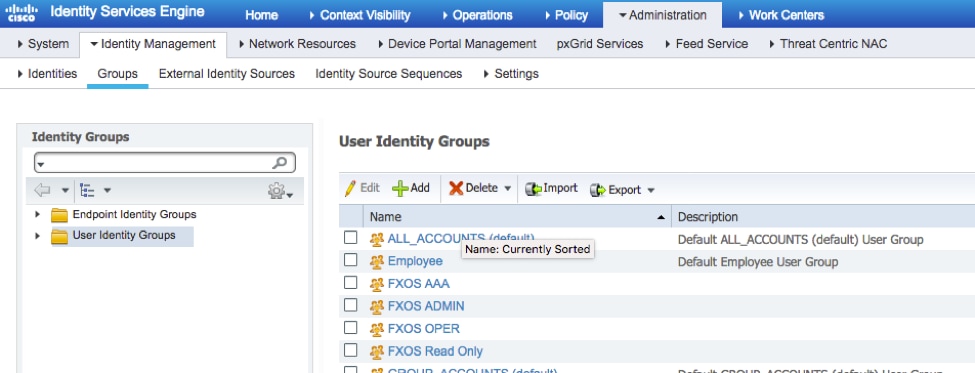
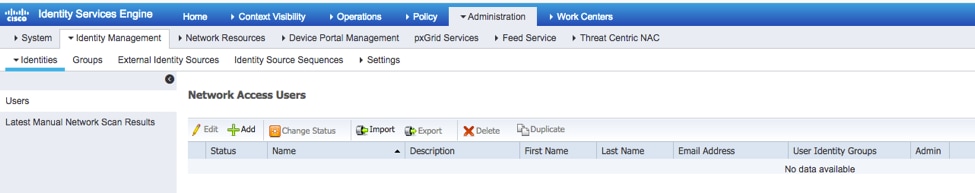
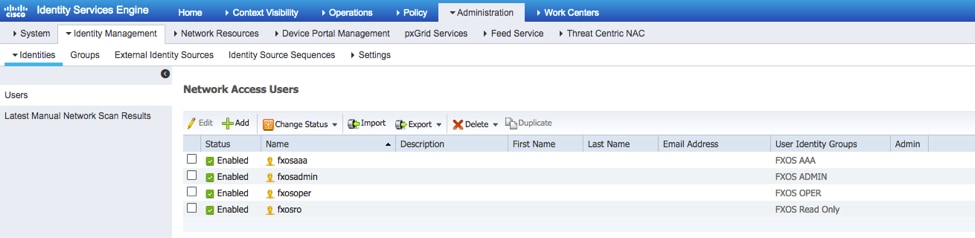
Step 5. Navigate to Administration > Identity Management > Identity > Users.
Step 6. Click ADD.
Step 7. Enter the required values (Name, User Group, Password).
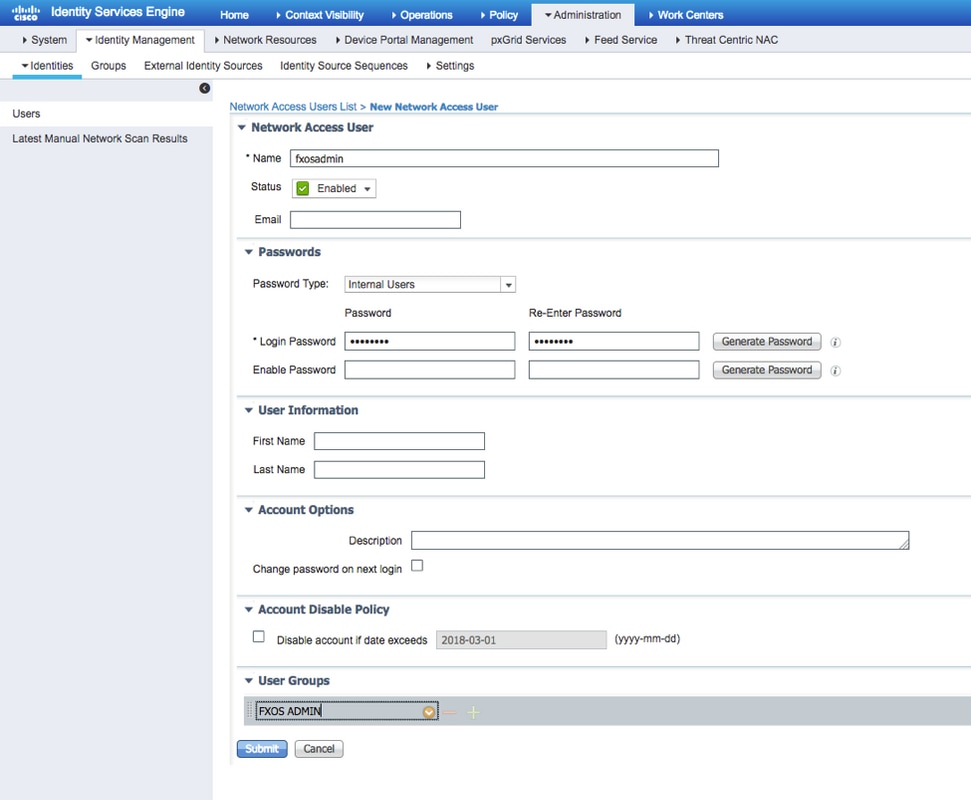
Step 8. Repeat step 6 for all required users.
Creating the Authorization Profile for each User Role
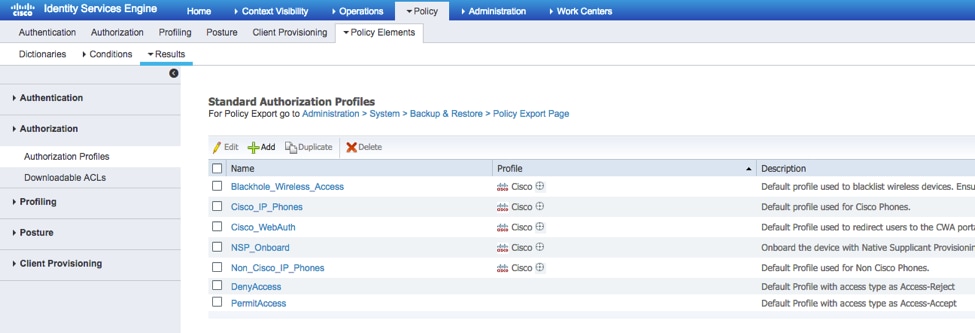
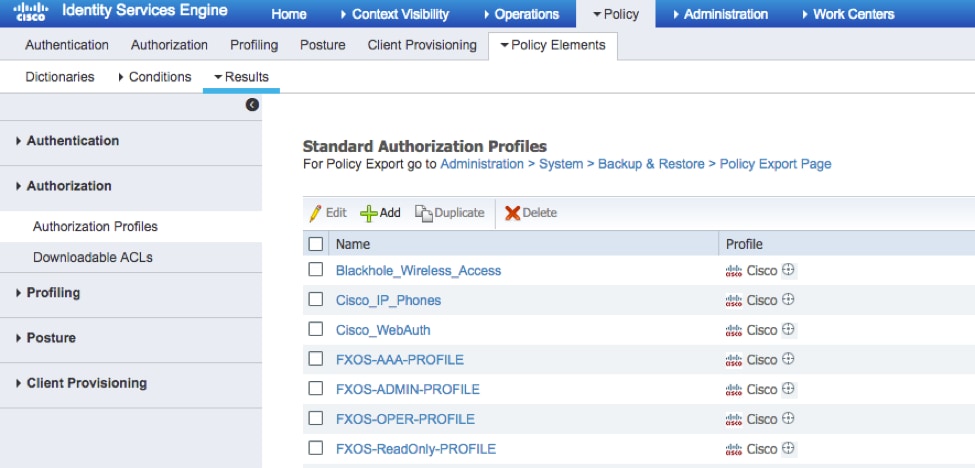
Step 1. Navigate to Policy > Policy Elements > Results > Authorization > Authorization Profiles.
Step 2. Fill all the attributes for the Authorization Profile.
2.1. Configure the profile Name.
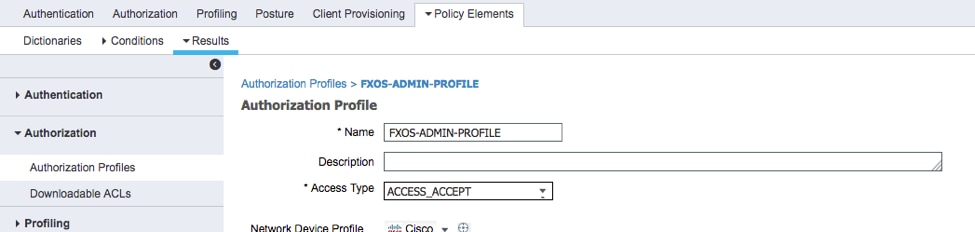
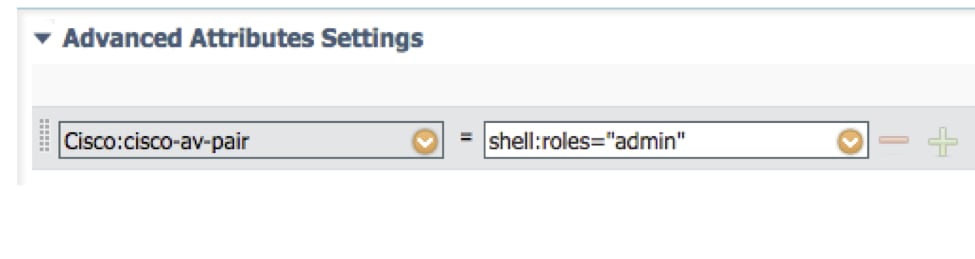
2.2. In Advanced Attributes Settings configure the following CISCO-AV-PAIR
cisco-av-pair=shell:roles="admin"
2.3. Click Save.
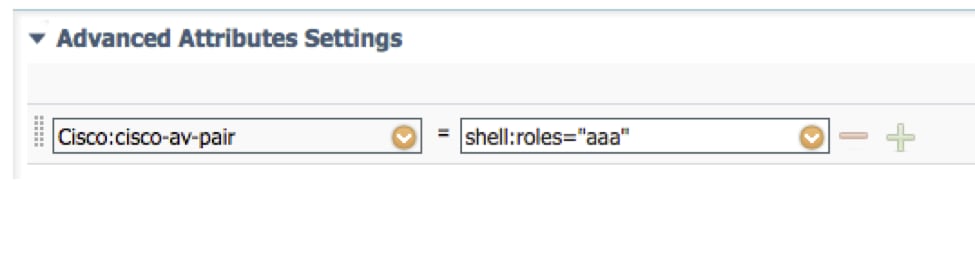
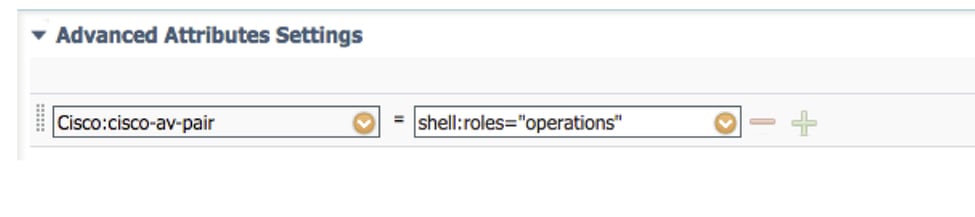
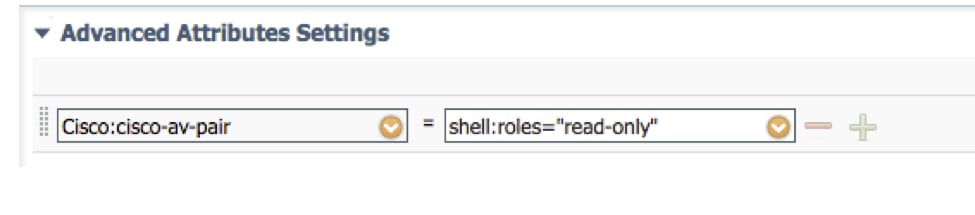
Step 3. Repeat step 2 for the remaining User Roles using the following Cisco-AV-Pairs
cisco-av-pair=shell:roles="aaa"
cisco-av-pair=shell:roles="operations"
cisco-av-pair=shell:roles="read-only"
Creating the Authentication Policy
Step 1. Navigate to Policy > Authentication > And click the arrow next to edit where you want to create the rule.
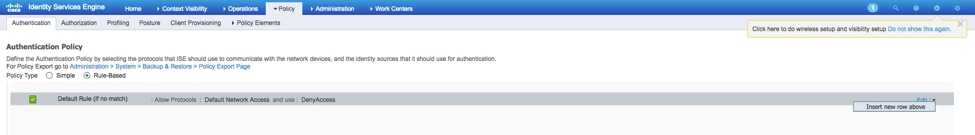
Step 2. The setup is simple; it can be done more granular but for this example we will use the device type:
Name: FXOS AUTHENTICATION RULE
IF Select new attribute/value: Device:Device Type Equals All Devices Types #FXOS
Allow Protocols: Default network Access
Use: Internal Users

Creating the Authorization Policy
Step 1. Navigate to Policy > Authorization > And click the arrow net to edit where you want to create the rule.
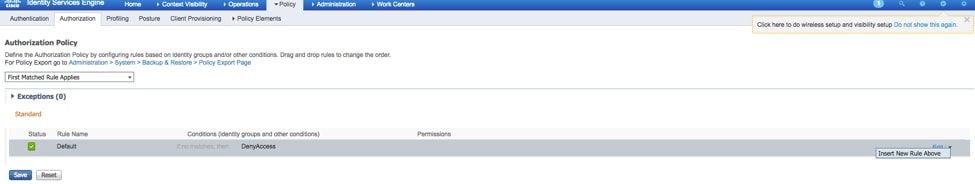
Step 2. Enter the values for the Authorization rule with the required parameters.
2.1. Rule Name: Fxos <USER ROLE> Rule.
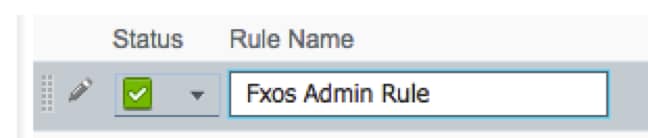
2.2. If: User Identity Groups > Select <USER ROLE>.
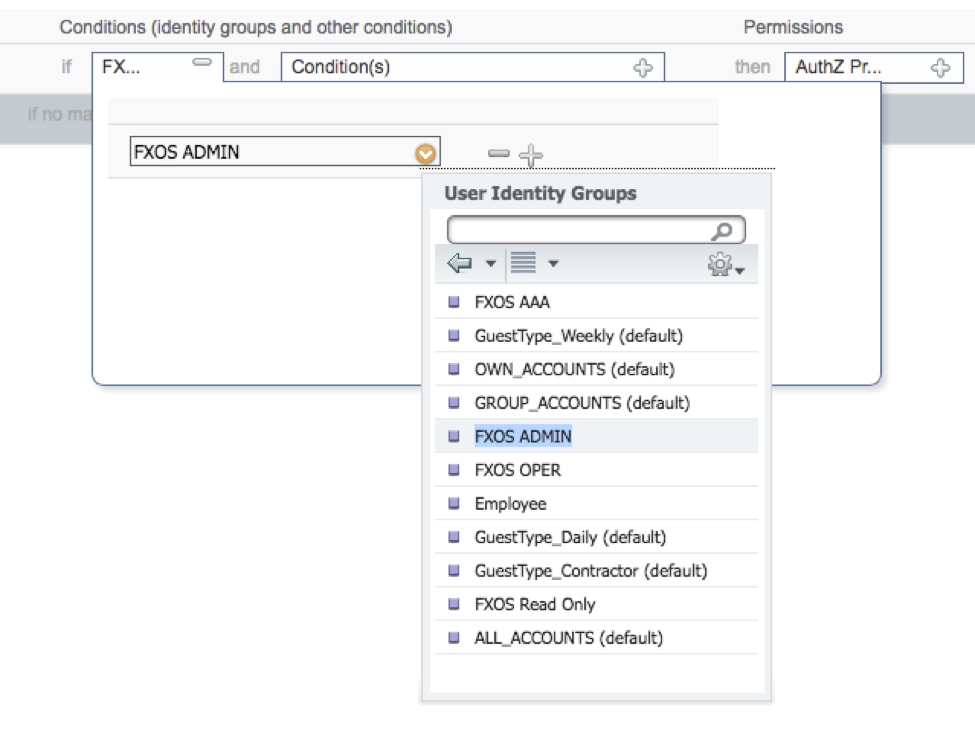
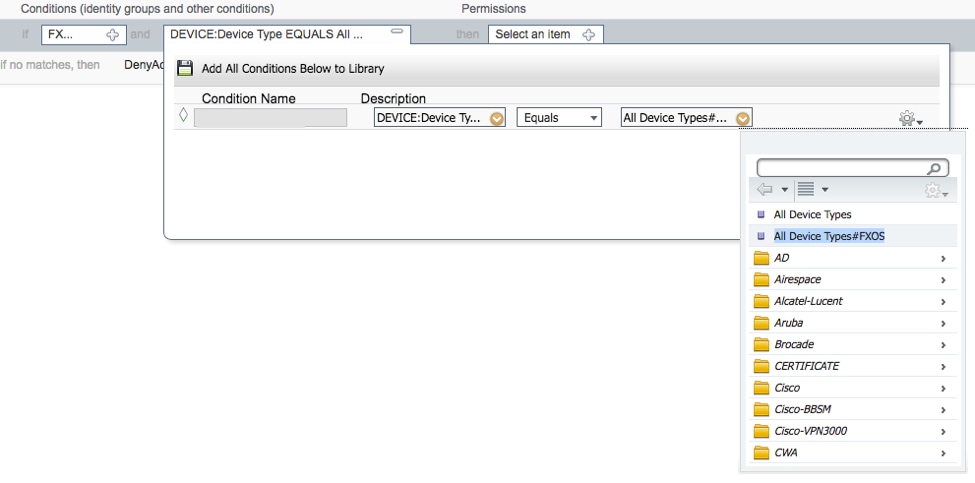
2.3. AND: Create New Condition > Device:Device type Equals All Devices Types #FXOS.
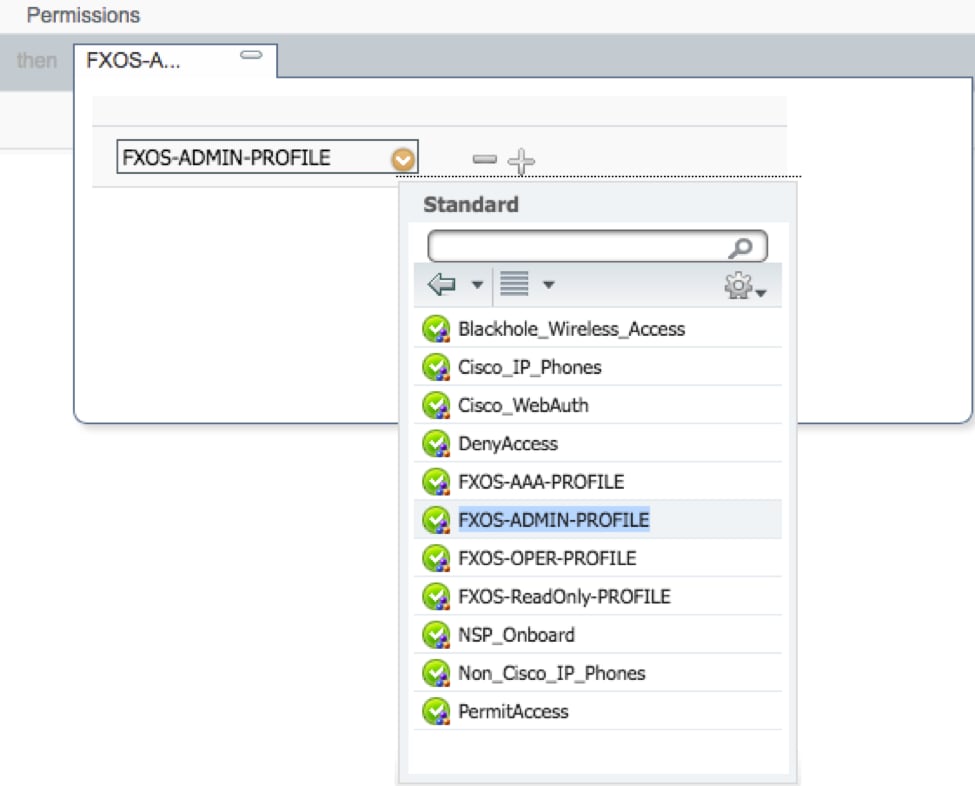
2.4. Permissions: Standard > Choose the User Role Profile
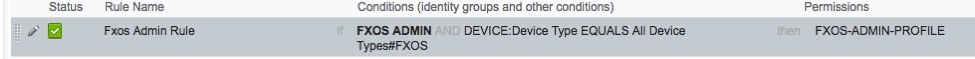
Step 3. Repeat step 2 for all User Roles.
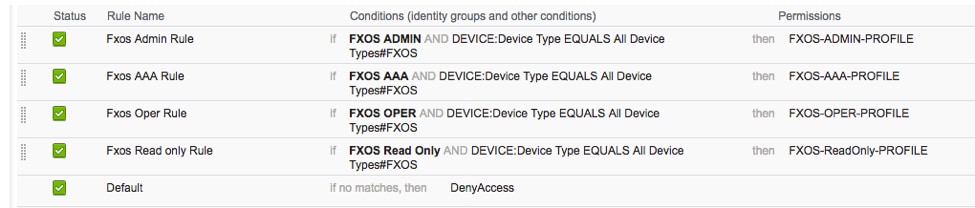
Step 4. Click Save at the bottom of the page.
Verify
You may now test each user and verify the assigned User Role.
FXOS Chasis verification
- Telnet or SSH to the FXOS Chassis and login using any of the created users on the ISE.
Username: fxosadmin
Password:
fpr4120-TAC-A# scope security
fpr4120-TAC-A /security # show remote-user detail
Remote User fxosaaa:
Description:
User Roles:
Name: aaa
Name: read-only
Remote User fxosadmin:
Description:
User Roles:
Name: admin
Name: read-only
Remote User fxosoper:
Description:
User Roles:
Name: operations
Name: read-only
Remote User fxosro:
Description:
User Roles:
Name: read-only
Depending on the username entered the FXOS chassis cli will only display the commands authorized for the User Role assigned.
Admin User Role.
fpr4120-TAC-A /security # ?
acknowledge Acknowledge
clear-user-sessions Clear User Sessions
create Create managed objects
delete Delete managed objects
disable Disables services
enable Enables services
enter Enters a managed object
scope Changes the current mode
set Set property values
show Show system information
terminate Active cimc sessions
fpr4120-TAC-A# connect fxos
fpr4120-TAC-A (fxos)# debug aaa aaa-requests
fpr4120-TAC-A (fxos)#
Read-Only User Role.
fpr4120-TAC-A /security # ?
scope Changes the current mode
set Set property values
show Show system information
fpr4120-TAC-A# connect fxos
fpr4120-TAC-A (fxos)# debug aaa aaa-requests
% Permission denied for the role
- Browse to the FXOS Chassis IP address and login using any of the created users on the ISE.
Admin User Role.
Read-only User Role.
Note: Notice that the ADD button is greyed out.
ISE 2.0 Verification
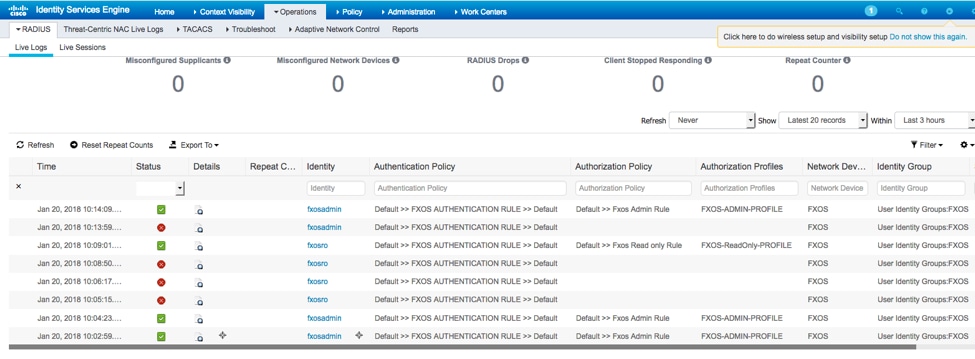
- Navigate to Operations > RADIUS > Live logs. You should be able to see successful and failed attempts.
Troubleshoot
In order to debug AAA authentication and authorization run the following commands in the FXOS cli.
fpr4120-TAC-A# connect fxos
fpr4120-TAC-A (fxos)# debug aaa aaa-requests
fpr4120-TAC-A (fxos)# debug aaa event
fpr4120-TAC-A (fxos)# debug aaa errors
fpr4120-TAC-A (fxos)# term mon
After a successful authentication attempt, you will see the following output.
2018 Jan 20 17:18:02.410275 aaa: aaa_req_process for authentication. session no 0
2018 Jan 20 17:18:02.410297 aaa: aaa_req_process: General AAA request from appln: login appln_subtype: default
2018 Jan 20 17:18:02.410310 aaa: try_next_aaa_method
2018 Jan 20 17:18:02.410330 aaa: total methods configured is 1, current index to be tried is 0
2018 Jan 20 17:18:02.410344 aaa: handle_req_using_method
2018 Jan 20 17:18:02.410356 aaa: AAA_METHOD_SERVER_GROUP
2018 Jan 20 17:18:02.410367 aaa: aaa_sg_method_handler group = radius
2018 Jan 20 17:18:02.410379 aaa: Using sg_protocol which is passed to this function
2018 Jan 20 17:18:02.410393 aaa: Sending request to RADIUS service
2018 Jan 20 17:18:02.412944 aaa: mts_send_msg_to_prot_daemon: Payload Length = 374
2018 Jan 20 17:18:02.412973 aaa: session: 0x8dfd68c added to the session table 1
2018 Jan 20 17:18:02.412987 aaa: Configured method group Succeeded
2018 Jan 20 17:18:02.656425 aaa: aaa_process_fd_set
2018 Jan 20 17:18:02.656447 aaa: aaa_process_fd_set: mtscallback on aaa_q
2018 Jan 20 17:18:02.656470 aaa: mts_message_response_handler: an mts response
2018 Jan 20 17:18:02.656483 aaa: prot_daemon_reponse_handler
2018 Jan 20 17:18:02.656497 aaa: session: 0x8dfd68c removed from the session table 0
2018 Jan 20 17:18:02.656512 aaa: is_aaa_resp_status_success status = 1
2018 Jan 20 17:18:02.656525 aaa: is_aaa_resp_status_success is TRUE
2018 Jan 20 17:18:02.656538 aaa: aaa_send_client_response for authentication. session->flags=21. aaa_resp->flags=0.
2018 Jan 20 17:18:02.656550 aaa: AAA_REQ_FLAG_NORMAL
2018 Jan 20 17:18:02.656577 aaa: mts_send_response Successful
2018 Jan 20 17:18:02.700520 aaa: aaa_process_fd_set: mtscallback on aaa_accounting_q
2018 Jan 20 17:18:02.700688 aaa: OLD OPCODE: accounting_interim_update
2018 Jan 20 17:18:02.700702 aaa: aaa_create_local_acct_req: user=, session_id=, log=added user fxosro
2018 Jan 20 17:18:02.700725 aaa: aaa_req_process for accounting. session no 0
2018 Jan 20 17:18:02.700738 aaa: MTS request reference is NULL. LOCAL request
2018 Jan 20 17:18:02.700749 aaa: Setting AAA_REQ_RESPONSE_NOT_NEEDED
2018 Jan 20 17:18:02.700762 aaa: aaa_req_process: General AAA request from appln: default appln_subtype: default
2018 Jan 20 17:18:02.700774 aaa: try_next_aaa_method
2018 Jan 20 17:18:02.700798 aaa: no methods configured for default default
2018 Jan 20 17:18:02.700810 aaa: no configuration available for this request
2018 Jan 20 17:18:02.700997 aaa: aaa_send_client_response for accounting. session->flags=254. aaa_resp->flags=0.
2018 Jan 20 17:18:02.701010 aaa: response for accounting request of old library will be sent as SUCCESS
2018 Jan 20 17:18:02.701021 aaa: response not needed for this request
2018 Jan 20 17:18:02.701033 aaa: AAA_REQ_FLAG_LOCAL_RESP
2018 Jan 20 17:18:02.701044 aaa: aaa_cleanup_session
2018 Jan 20 17:18:02.701055 aaa: aaa_req should be freed.
2018 Jan 20 17:18:02.701067 aaa: Fall back method local succeeded
2018 Jan 20 17:18:02.706922 aaa: aaa_process_fd_set
2018 Jan 20 17:18:02.706937 aaa: aaa_process_fd_set: mtscallback on aaa_accounting_q
2018 Jan 20 17:18:02.706959 aaa: OLD OPCODE: accounting_interim_update
2018 Jan 20 17:18:02.706972 aaa: aaa_create_local_acct_req: user=, session_id=, log=added user:fxosro to the role:read-only
After a failed authentication attempt, you will see the following output.
2018 Jan 20 17:15:18.102130 aaa: aaa_process_fd_set
2018 Jan 20 17:15:18.102149 aaa: aaa_process_fd_set: mtscallback on aaa_q
2018 Jan 20 17:15:18.102267 aaa: aaa_process_fd_set
2018 Jan 20 17:15:18.102281 aaa: aaa_process_fd_set: mtscallback on aaa_q
2018 Jan 20 17:15:18.102363 aaa: aaa_process_fd_set
2018 Jan 20 17:15:18.102377 aaa: aaa_process_fd_set: mtscallback on aaa_q
2018 Jan 20 17:15:18.102456 aaa: aaa_process_fd_set
2018 Jan 20 17:15:18.102468 aaa: aaa_process_fd_set: mtscallback on aaa_q
2018 Jan 20 17:15:18.102489 aaa: mts_aaa_req_process
2018 Jan 20 17:15:18.102503 aaa: aaa_req_process for authentication. session no 0
2018 Jan 20 17:15:18.102526 aaa: aaa_req_process: General AAA request from appln: login appln_subtype: default
2018 Jan 20 17:15:18.102540 aaa: try_next_aaa_method
2018 Jan 20 17:15:18.102562 aaa: total methods configured is 1, current index to be tried is 0
2018 Jan 20 17:15:18.102575 aaa: handle_req_using_method
2018 Jan 20 17:15:18.102586 aaa: AAA_METHOD_SERVER_GROUP
2018 Jan 20 17:15:18.102598 aaa: aaa_sg_method_handler group = radius
2018 Jan 20 17:15:18.102610 aaa: Using sg_protocol which is passed to this function
2018 Jan 20 17:15:18.102625 aaa: Sending request to RADIUS service
2018 Jan 20 17:15:18.102658 aaa: mts_send_msg_to_prot_daemon: Payload Length = 371
2018 Jan 20 17:15:18.102684 aaa: session: 0x8dfd68c added to the session table 1
2018 Jan 20 17:15:18.102698 aaa: Configured method group Succeeded
2018 Jan 20 17:15:18.273682 aaa: aaa_process_fd_set
2018 Jan 20 17:15:18.273724 aaa: aaa_process_fd_set: mtscallback on aaa_q
2018 Jan 20 17:15:18.273753 aaa: mts_message_response_handler: an mts response
2018 Jan 20 17:15:18.273768 aaa: prot_daemon_reponse_handler
2018 Jan 20 17:15:18.273783 aaa: session: 0x8dfd68c removed from the session table 0
2018 Jan 20 17:15:18.273801 aaa: is_aaa_resp_status_success status = 2
2018 Jan 20 17:15:18.273815 aaa: is_aaa_resp_status_success is TRUE
2018 Jan 20 17:15:18.273829 aaa: aaa_send_client_response for authentication. session->flags=21. aaa_resp->flags=0.
2018 Jan 20 17:15:18.273843 aaa: AAA_REQ_FLAG_NORMAL
2018 Jan 20 17:15:18.273877 aaa: mts_send_response Successful
2018 Jan 20 17:15:18.273902 aaa: aaa_cleanup_session
2018 Jan 20 17:15:18.273916 aaa: mts_drop of request msg
2018 Jan 20 17:15:18.273935 aaa: aaa_req should be freed.
2018 Jan 20 17:15:18.280416 aaa: aaa_process_fd_set
2018 Jan 20 17:15:18.280443 aaa: aaa_process_fd_set: mtscallback on aaa_q
2018 Jan 20 17:15:18.280454 aaa: aaa_enable_info_config: GET_REQ for aaa login error message
2018 Jan 20 17:15:18.280460 aaa: got back the return value of configuration operation:unknown security item
Related Information
Ethanalyzer command on FX-OS cli will prompt for password for a password when TACACS/RADIUS authentication is enabled. This behavior is caused by a bug.
Bug id: CSCvg87518
Revision History
| Revision | Publish Date | Comments |
|---|---|---|
1.0 |
22-Jan-2018 |
Initial Release |
Contributed by Cisco Engineers
- Tony Remirez HarfuchTAC
- Jose Soto NolascoTAC
- Ezequiel TlecuitlTAC
Contact Cisco
- Open a Support Case

- (Requires a Cisco Service Contract)
 Feedback
Feedback