Introduction
This document describes how to compare different Network Analysis Policies (NAP) for firepower devices managed by Firepower Management Centre (FMC).
Prerequisites
Requirements
Cisco recommends that you have knowledge of these topics:
- Knowledge of open-source Snort
- Firepower Management Center (FMC)
- Firepower Threat Defense (FTD)
Components Used
The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, ensure that you understand the potential impact of any command. The information in this document is based on these software and hardware versions:
Background Information
The Snort uses pattern matching techniques to find and prevent exploits in network packets. In order to do this, the Snort engine needs network packets to be prepared in such a way that this comparison can be done. This process is done with the help of NAP and can undergo these three stages:
- Decoding
- Normalizing
- Pre-processing
A network analysis policy processes packet in phases: first the system decodes packets through the first three TCP/IP layers, then continues with normalizing, pre-processing, and detecting protocol anomalies.
Pre-processors provide two main functionality:
- Traffic Normalization for further inspection
- Identify protocol anomalies
Note: Some Intrusion Policy rules require certain pre-processor options in order to perform detection
For information on open-source Snort, please visit https://www.snort.org/
Verify NAP Configuration
To create or edit firepower NAP policies, navigate to FMC Policies > Access Control > Intrusion, thereafter click Network Analysis Policy option in the top right corner, as shown in the image:


Verifying the default Network Analysis Policy
Check the default Network Analysis (NAP) policy applied on the Access Control Policy (ACP)
Navigate to Policies > Access Control and edit the ACP that you want to verify. Click Advanced tab and scroll down to Network Analysis and Intrusion Policies section.
The Default Network Analysis Policy associated with the ACP is Balanced Security and Connectivity, as shown in the image:
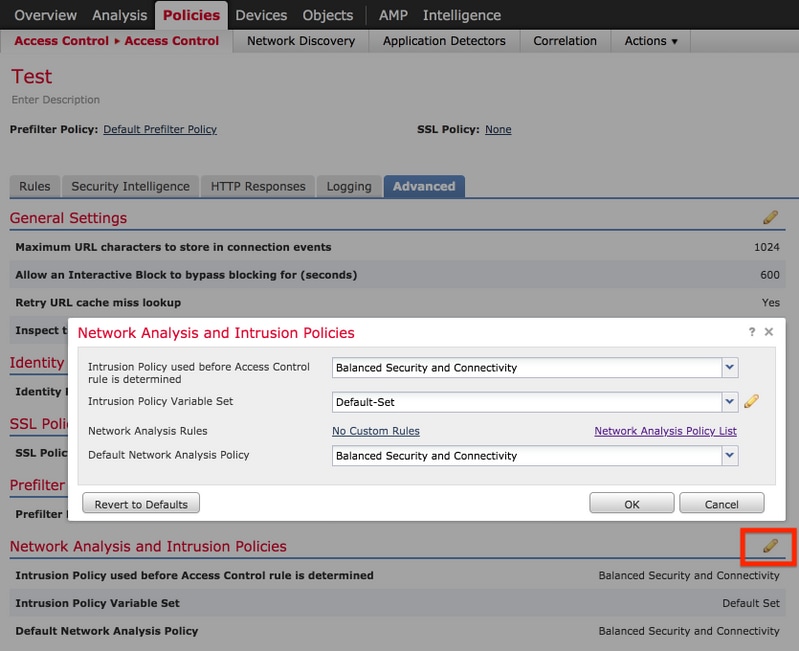
Note: Do not confuse the Balanced Security and Connectivity for Intrusion Policies and the Balanced Security and Connectivity for Network Analysis. The former one is for Snort rules while the latter is for pre-processing and decoding.
Compare Network Analysis Policy (NAP)
The NAP policies can be compared for changes done and this feature could help in identifying and troubleshooting the issues. In addition, NAP comparison reports could also be generated and exported at the same time.
Navigate to Policies > Access Control > Intrusion. Then, click Network Analysis Policy option in the top right. Under the NAP policy page you can see Compare Policies tab on the top right side, as shown in the image:

Network Analysis Policy comparison is available in two variants:
- Between two different NAP policies
- Between two different revisions of same NAP policy

The comparison window provides a comparative line by line comparison between two selected NAP policies and the same can be exported as a report from the comparison report tab on the top right, as shown in the image:

For comparison between two versions of the same NAP policy, the revision option can be opted to select the required revision id, as shown in the image:











 Feedback
Feedback