Configuration of LDAP Authentication Object on FireSIGHT System
Available Languages
Introduction
Authentication Objects are server profiles for external authentication servers, containing connection settings and authentication filter settings for those servers. You can create, manage, and delete Authentication Objects on a FireSIGHT Management Center. This document describes how to configure LDAP Authentication Object on FireSIGHT System.
Configuration of an LDAP Authentication Object
1. Login to the web user interface of the FireSIGHT Management Center.
2. Navigate to System > Local > User Management.

Select the Login Authentication tab.

Click on Create Authentication Object.

3. Select an Authentication Method and a Server Type.
- Authentication Method : LDAP
- Name: <Authentication Object Name>
- Server Type: MS Active Directory

4. Specify the Primary and Backup Server Host Name or IP Address. A Backup Server is optional. However, any Domain Controller within the same domain can be used as a backup server.
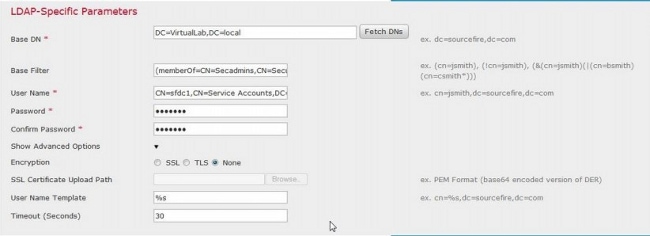
5. Specify the LDAP-Specific Parameters as shown below:
- Base DN - Domain or Specific OU DN
- Base Filter - The group DN that users are member of.
- User Name - Impersonation account for the DC
- Password: <password>
- Confirm Password: <password>
Advanced Options:
- Encryption: SSL, TLS or None
- SSL Certificate Upload Path: Upload the CA certification (Optional)
- User Name Template: %s
- Timeout (Seconds) : 30
In the Domain Security Policy Setting of the AD, if LDAP server Signing requirement is set to Require Signing, SSL or TLS must be used.
LDAP server Signing requirement
- None: Data signing is not required in order to bind with server. If the client requests data signing, the server supports it.
- Require signing: Unless TLS\SSL is being used, the LDAP data signing option must be negotiated.
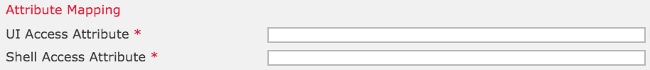
6. Specify Attribute Mapping
- UI Access Attribute: sAMAccountName
- Shell Access Attribute: sAMAccountName
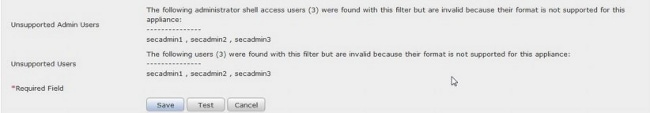
7. Configure Group Controlled Access Roles
On ldp.exe, browse to each groups and copy the corresponding group DN to the Authentication Object as shown below:
- <Group Name> Group DN: <group dn>
- Group Member Attribute: should always be member
Example:
- Administrator Group DN: CN=DC admins,CN=Security Groups,DC=VirtualLab,DC=local
- Group Member Attribute: member
An AD security group has an attribute of member followed by the DN of member users. The number preceding member attribute indicates the number of member users.
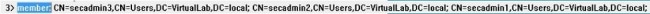
8. Select Same as Base Filter for Shell Access Filter, or specify memberOf attribute as indicated in step 5.
Shell Access Filter: (memberOf=<group DN>)
As example,
Shell Access Filter: (memberOf=CN=Shell users,CN=Security Groups,DC=VirtualLab,DC=local)
9. Save the Authentication Object and perform a test. A successful test result looks like below:

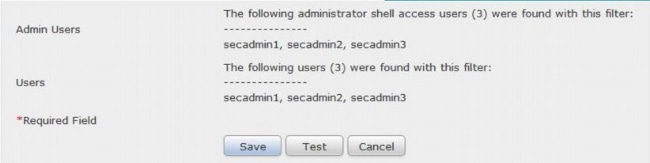
10. Once the Authentication Object passes the test, enable the object in the System Policy and reapply the policy to your appliance.
Related Document
Revision History
| Revision | Publish Date | Comments |
|---|---|---|
1.0 |
05-Jan-2015 |
Initial Release |
Contact Cisco
- Open a Support Case

- (Requires a Cisco Service Contract)
 Feedback
Feedback