Introduction
This document describes how to configure and verify TrustSec on a Catalyst Switch and Wireless LAN Controller with the Identity Services Engine.
Prerequisites
Cisco recommends that you have knowledge of these topics:
- Basic knowledge of Cisco TrustSec (CTS) components
- Basic knowledge of CLI configuration of Catalyst switches
- Basic knowledge of GUI configuration of Cisco Wireless LAN Controllers (WLC)
- Experience with Identity Services Engine (ISE) configuration
Requirements
You must have Cisco ISE deployed in your network, and end users must authenticate to Cisco ISE with 802.1x (or other method) when they connect to wireless or wired. Cisco ISE assigns their traffic a Security Group Tag (SGT) once they authenticate to your wireless network.
In our example, end users are redirected to the Cisco ISE Bring Your Own Device (BYOD) portal and are provisioned a certificate so they can securely access the wireless network with Extensible Authentication Protocol-Transport Layer Security (EAP-TLS) once they complete the BYOD portal steps.
Components Used
The information in this document is based on these hardware and software versions:
- Cisco Identity Services Engine, version 2.4
- Cisco Catalyst 3850 Switch, version 3.7.5E
- Cisco WLC, version 8.5.120.0
- Cisco Aironet Wireless Access Point in Local mode
Before deployment of Cisco TrustSec, verify your Cisco Catalyst Switch and/or Cisco WLC+AP models + software version has support for:
- TrustSec/Security Group Tags
- Inline Tagging (if not, you can use SXP instead of Inline Tagging)
- Static IP-to-SGT mappings (if needed)
- Static Subnet-to-SGT mappings (if needed)
- Static VLAN-to-SGT mappings (if needed)
The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, ensure that you understand the potential impact of any command.
Configure
Network Diagram

In this example, the WLC tags the packets as SGT 15 if from a Consultant, and + SGT 7 if from an Employee.
The switch denies those packets if they are from SGT 15 to SGT 8 (consultants cannot access servers tagged as SGT 8).
The switch allows those packets if they are from SGT 7 to SGT 8 (employees can access servers tagged as SGT 8).
Goal
Let anyone access GuestSSID.
Let Consultants access EmployeeSSID, but with restricted access.
Let Employees access EmployeeSSID with full access.
| Device |
IP address |
VLAN |
| ISE |
10.201.214.230 |
463 |
| Catalyst Switch |
10.201.235.102 |
1115 |
| WLC |
10.201.214.229 |
463 |
| Access Point |
10.201.214.138 |
455 |
| Name |
Username |
AD Group |
SG |
SGT |
| Jason Smith |
jsmith |
Consultants |
BYODconsultants |
15 |
| Sally Smith |
ssmith |
Employees |
BYODemployees |
7 |
| n/a |
n/a |
n/a |
TrustSec_Devices |
2 |
Configurations
Configure TrustSec on ISE
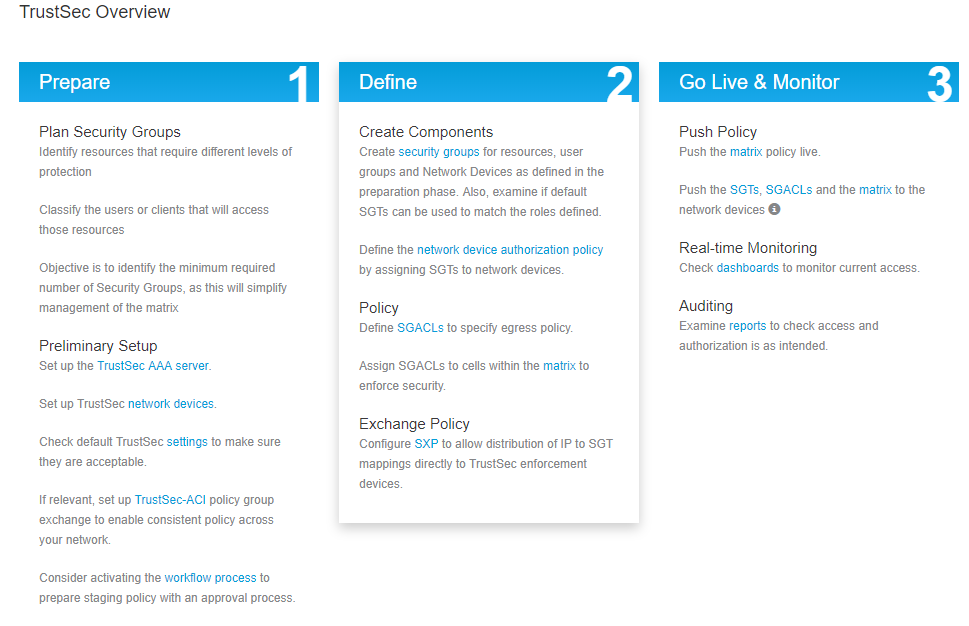
Configure Cisco ISE as a TrustSec AAA Server
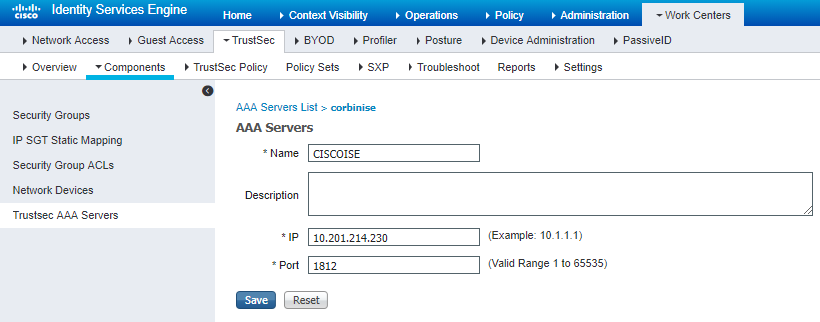
Configure and Verify Switch is Added as a RADIUS Device in Cisco ISE
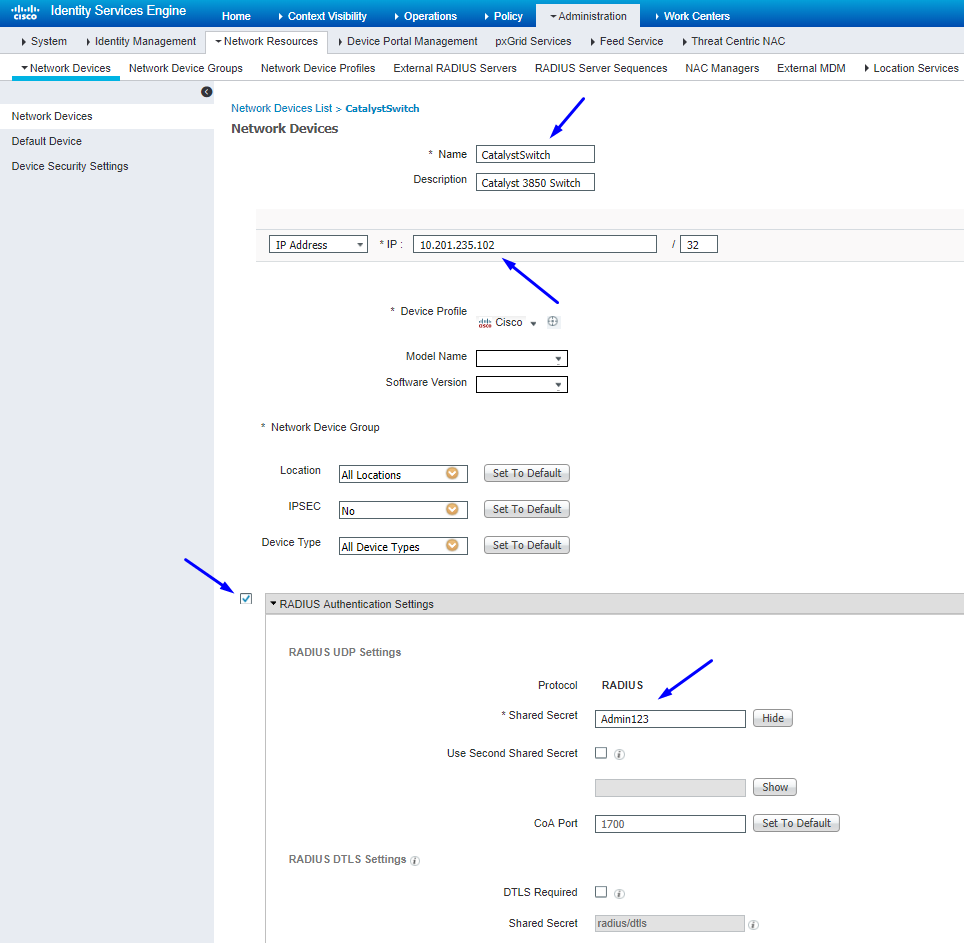
Configure and Verify WLC is Added as a TrustSec Device in Cisco ISE
Enter your log in credentials for SSH. This enables Cisco ISE to deploy the static IP-to-SGT Mappings to the switch.
You create these in the Cisco ISE Web GUI under Work Centers > TrustSec > Components > IP SGT Static Mappings as shown here:


Tip: If you do not want to enable Cisco ISE to access your Catalyst Switch over SSH, you can create Static IP-to-SGT mappings on the Catalyst Switch with the CLI instead (shown in a step here).
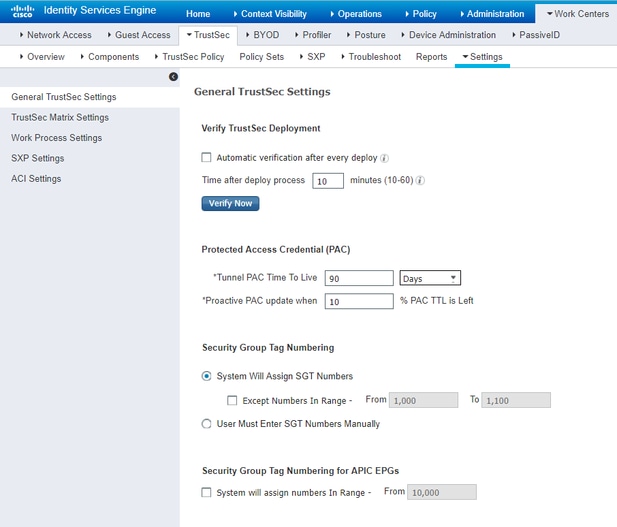
Verify Default TrustSec Settings to Make Sure They are Acceptable (Optional)
Create Security Group Tags for Wireless Users
Create Security Group for BYODconsultants - SGT 15
Create Security Group for BYODemployees - SGT 7

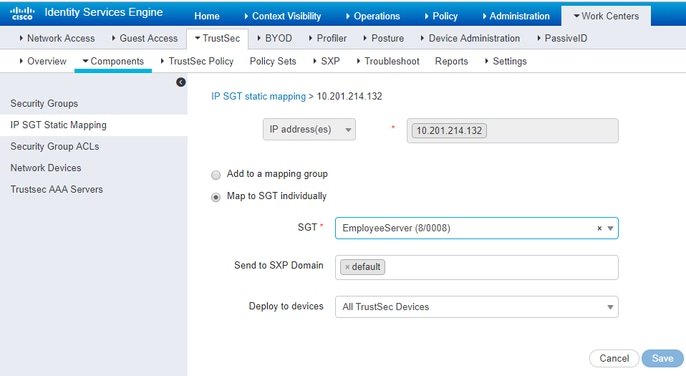
Create Static IP-to-SGT Mapping for the Restricted Web Server
Do this for any other IP addresses or subnets in your network that do not authenticate to Cisco ISE with MAC Authentication Bypass (MAB), 802.1x, Profiles, and so on.
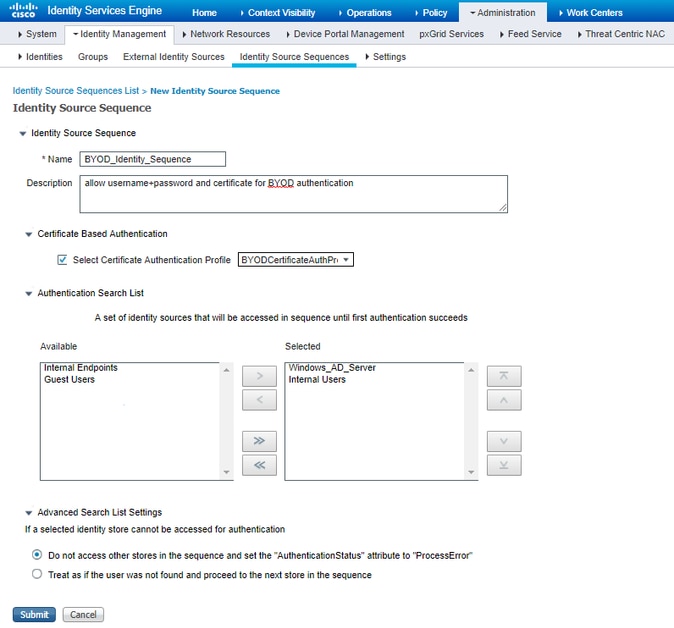
Create Certificate Authentication Profile

Create Identity Source Sequence with the Certificate Authentication Profile from Before
Assign Wireless Users (Employees and Consultants) an Appropriate SGT
| Name |
Username |
AD Group |
SG |
SGT |
| Jason Smith |
jsmith |
Consultants |
BYODconsultants |
15 |
| Sally Smith |
ssmith |
Employees |
BYODemployees |
7 |
| n/a |
n/a |
n/a |
TrustSec_Devices |
2 |
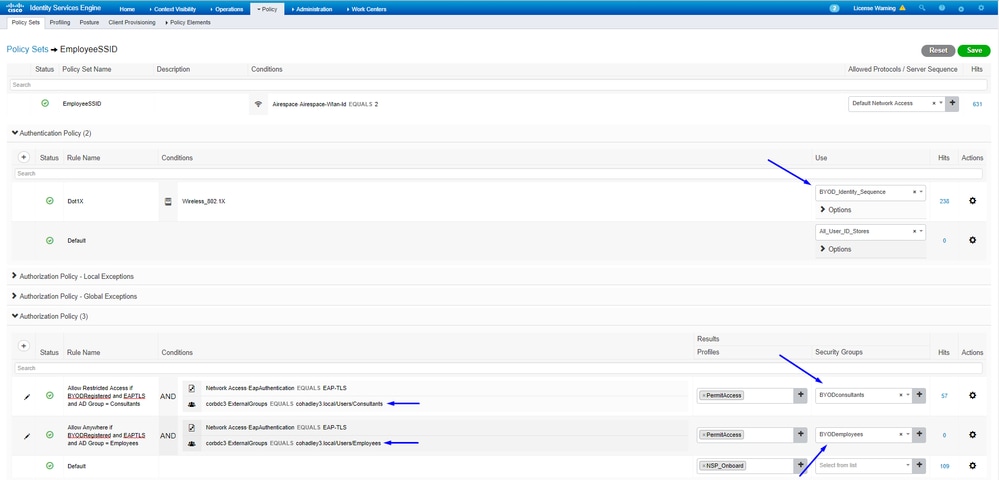
Assign SGTs to the Actual Devices (Switch and WLC)

Define SGACLs to Specify the Egress Policy
Allow Consultants to access anywhere external, but restrict internal:

Allow Employees to access anywhere external and anywhere internal:

Allow other devices access to basic services (Optional):
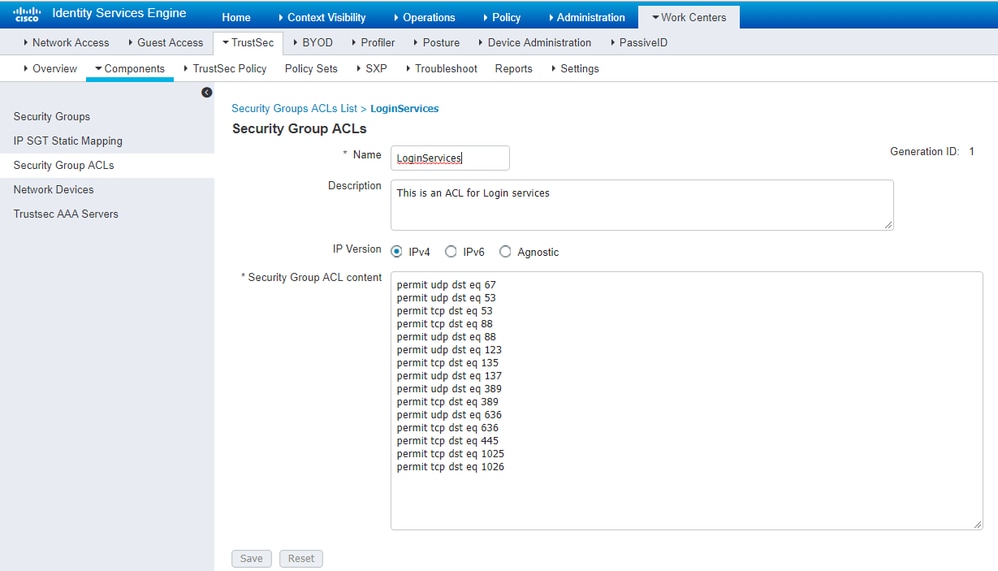
Redirect all end users to Cisco ISE (for BYOD portal redirection). Do not include DNS, DHCP, ping, or WebAuth traffic as those cannot go to Cisco ISE:

Enforce Your ACLs on the TrustSec Policy Matrix in Cisco ISE
Allow Consultants to access anywhere external, but restrict internal web servers, such as https://10.201.214.132
Allow Employees to access anywhere external and allow internal web servers:

Allow management traffic (SSH, HTTPS, and CAPWAP) to/from your devices on the network (switch and WLC) so you do not lose SSH or HTTPS access once you deploy Cisco TrustSec:
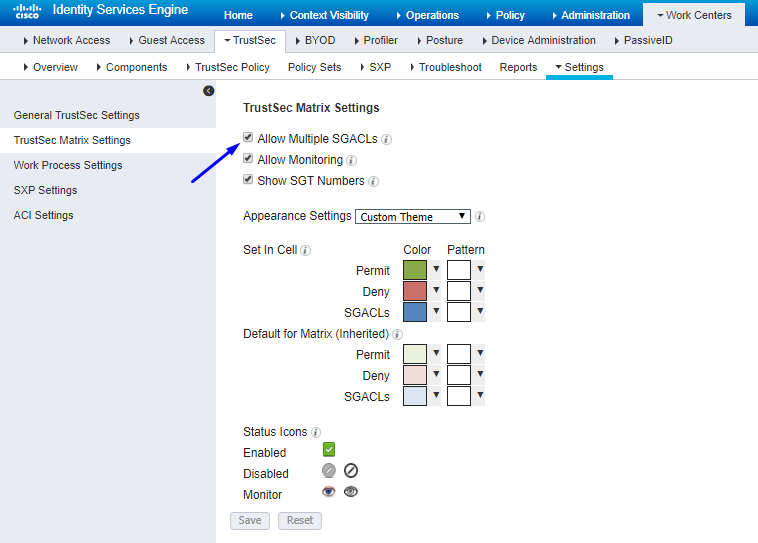
Enable Cisco ISE to Allow Multiple SGACLs:
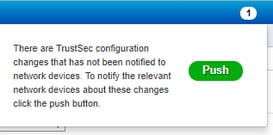
Click Push in the top-right corner of Cisco ISE, to push your configuration down to your devices. You need to do this again later as well:
Configure TrustSec on Catalyst Switch
Configure Switch to Use Cisco TrustSec for AAA on Catalyst Switch

Tip: This document assumes your wireless users are already successful with BYOD by Cisco ISE before the configuration shown here.
The commands shown in bold were already configured prior to this (in order for BYOD Wireless to work with ISE).
CatalystSwitch(config)#aaa new-model
CatalystSwitch(config)#aaa server radius policy-device
CatalystSwitch(config)#ip device tracking
CatalystSwitch(config)#radius server CISCOISE
CatalystSwitch(config-radius-server)#address ipv4 10.201.214.230 auth-port 1812 acct-port 1813
CatalystSwitch(config)#aaa group server radius AAASERVER
CatalystSwitch(config-sg-radius)#server name CISCOISE
CatalystSwitch(config)#aaa authentication dot1x default group radius
CatalystSwitch(config)#cts authorization list SGLIST
CatalystSwitch(config)#aaa authorization network SGLIST group radius
CatalystSwitch(config)#aaa authorization network default group AAASERVER
CatalystSwitch(config)#aaa authorization auth-proxy default group AAASERVER
CatalystSwitch(config)#aaa accounting dot1x default start-stop group AAASERVER
CatalystSwitch(config)#aaa server radius policy-device
CatalystSwitch(config)#aaa server radius dynamic-author
CatalystSwitch(config-locsvr-da-radius)#client 10.201.214.230 server-key Admin123

Note: The PAC key must be the same as the RADIUS Shared Secret that you specified in the Administration > Network Devices > Add Device > RADIUS Authentication Settings section.
CatalystSwitch(config)#radius-server attribute 6 on-for-login-auth
CatalystSwitch(config)#radius-server attribute 6 support-multiple
CatalystSwitch(config)#radius-server attribute 8 include-in-access-req
CatalystSwitch(config)#radius-server attribute 25 access-request include
CatalystSwitch(config)#radius-server vsa send authentication
CatalystSwitch(config)#radius-server vsa send accounting
CatalystSwitch(config)#dot1x system-auth-control
Configure PAC Key Under the RADIUS Server to Authenticate the Switch to Cisco ISE
CatalystSwitch(config)#radius server CISCOISE
CatalystSwitch(config-radius-server)#address ipv4 10.201.214.230 auth-port 1812 acct-port 1813
CatalystSwitch(config-radius-server)#pac key Admin123


Note: The PAC key must be the same as the RADIUS Shared Secret that you specified under the Administration > Network Devices > Add Device > RADIUS Authentication Settings section in Cisco ISE (as shown in the screen capture).
Configure CTS Credentials to Authenticate the Switch to Cisco ISE
CatalystSwitch#cts credentials id CatalystSwitch password Admin123


Note: The CTS credentials must be the same as the Device ID + password that you specified in The CTS credentials must be the same as the Device ID + password that you specified in the Administration > Network Devices > Add Device > Advanced TrustSec Settings section in Cisco ISE (shown in the screen capture).
Then, refresh your PAC so it reaches out to Cisco ISE again:
CatalystSwitch(config)#radius server CISCOISE
CatalystSwitch(config-radius-server)#exit
Request successfully sent to PAC Provisioning driver.
Enable CTS Globally on Catalyst Switch
CatalystSwitch(config)#cts role-based enforcement
CatalystSwitch(config)#cts role-based enforcement vlan-list 1115 (choose the vlan that your end user devices are on only)
Make a Static IP-to-SGT Mapping for the Restricted Web Servers (Optional)
That Restricted Web Server does not come through ISE for authentication ever, so you must tag it manually with the Switch CLI or ISE Web GUI, that is just one of many web servers in Cisco.
CatalystSwitch(config)#cts role-based sgt-map 10.201.214.132 sgt 8
Verify TrustSec on Catalyst Switch
CatalystSwitch#show cts pac
AID: EF2E1222E67EB4630A8B22D1FF0216C1
PAC-Info:
PAC-type = Cisco Trustsec
AID: EF2E1222E67EB4630A8B22D1FF0216C1
I-ID: CatalystSwitch
A-ID-Info: Identity Services Engine
Credential Lifetime: 23:43:14 UTC Nov 24 2018
PAC-Opaque: 000200B80003000100040010EF2E1222E67EB4630A8B22D1FF0216C10006009C0003010025D40D409A0DDAF352A3F1A9884AC3F6000000135B7B521C00093A801FDEE189F60E30C0A161D16267E8C01B7EBE13EAEAFE31D6CF105961F877CD87DFB13D8ED5EBFFB5234FD78E01ECF034431C1AA4B25F3629E7037F386106110A1C450A57FFF49E3BB8973164B2710FB514697AD916BBF7052983B2DCA1951B936243E7D2A2D873C9D263F34C9F5F9E7E38249FD749125B5DD02962C2
Refresh timer is set for 12w5d
CatalystSwitch#cts refresh environment-data
Environment data download in progress
CatalystSwitch#show cts environment-data
CTS Environment Data
====================
Current state = COMPLETE
Last status = Successful
Local Device SGT:
SGT tag = 2-02:TrustSec_Devices
Server List Info:
Installed list: CTSServerList1-0001, 1 server(s):
*Server: 10.201.214.230, port 1812, A-ID EF2E1222E67EB4630A8B22D1FF0216C1
Status = ALIVE flag(0x11)
auto-test = TRUE, keywrap-enable = FALSE, idle-time = 60 mins, deadtime = 20 secs
Multicast Group SGT Table:
Security Group Name Table:
0001-31 :
0-00:Unknown
2-00:TrustSec_Devices
3-00:Network_Services
4-00:Employees
5-00:Contractors
6-00:Guests
7-00:BYODemployees
8-00:EmployeeServer
15-00:BYODconsultants
255-00:Quarantined_Systems
Transport type = CTS_TRANSPORT_IP_UDP
Environment Data Lifetime = 86400 secs
Last update time = 16:04:29 UTC Sat Aug 25 2018
Env-data expires in 0:23:57:01 (dd:hr:mm:sec)
Env-data refreshes in 0:23:57:01 (dd:hr:mm:sec)
Cache data applied = NONE
State Machine is running
CatalystSwitch#show cts role-based sgt-map all
Active IPv4-SGT Bindings Information
IP Address SGT Source
============================================
10.201.214.132 8 CLI
10.201.235.102 2 INTERNAL
IP-SGT Active Bindings Summary
============================================
Total number of CLI bindings = 1
Total number of INTERNAL bindings = 1
Total number of active bindings = 2
Configure TrustSec on WLC
Configure and Verify WLC is Added as a RADIUS Device in Cisco ISE
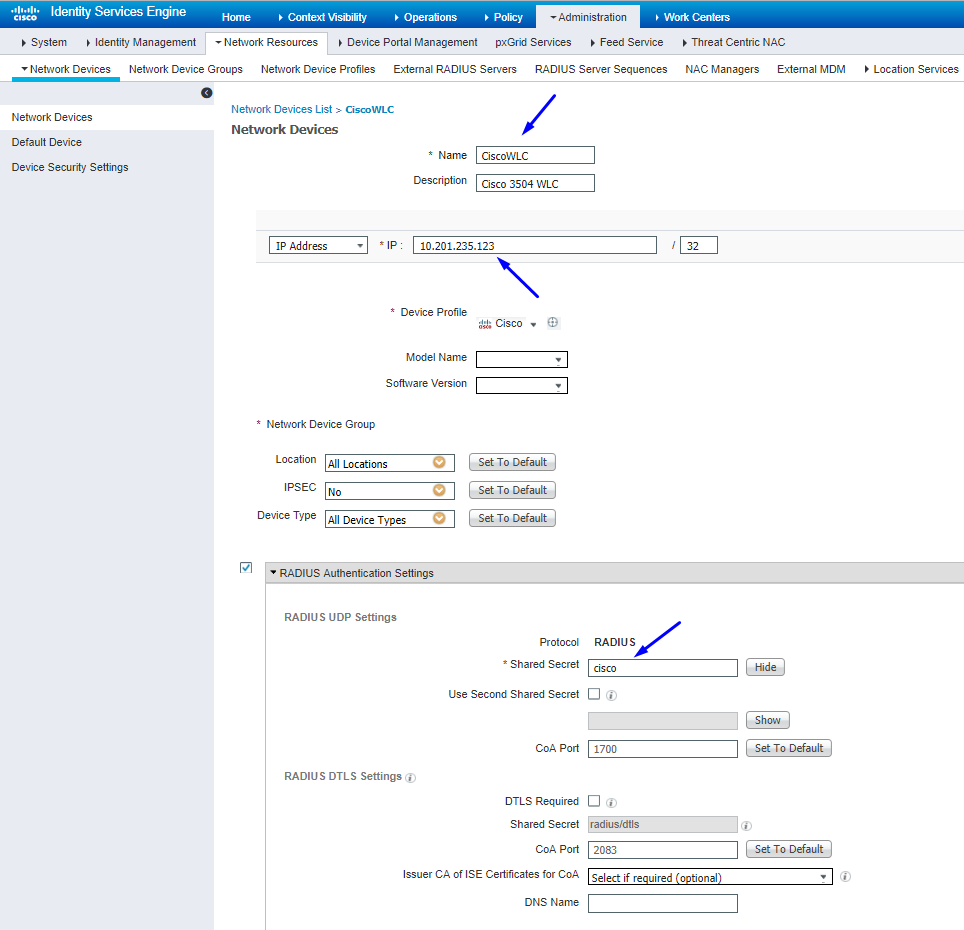
Configure and Verify WLC is Added as a TrustSec Device in Cisco ISE
This step enables Cisco ISE to deploy static IP-to-SGT Mappings to the WLC. You created these mappings in the Cisco ISE Web GUI in Work Centers > TrustSec > Components > IP SGT Static Mappings in a previous step.


Note: We use this Device ld and Password in a later step, in Security > TrustSec > General in the WLC Web UI.
Enable PAC Provision of WLC
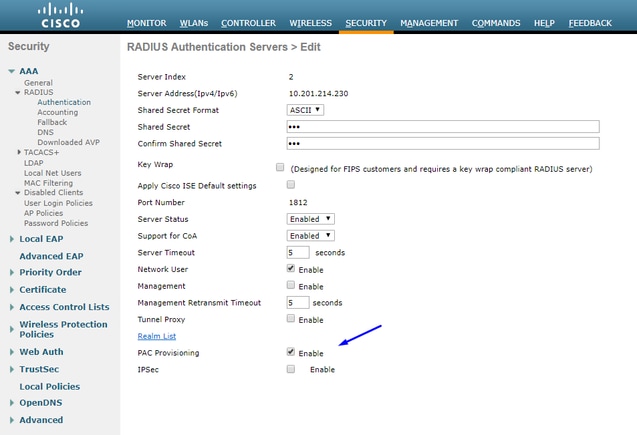
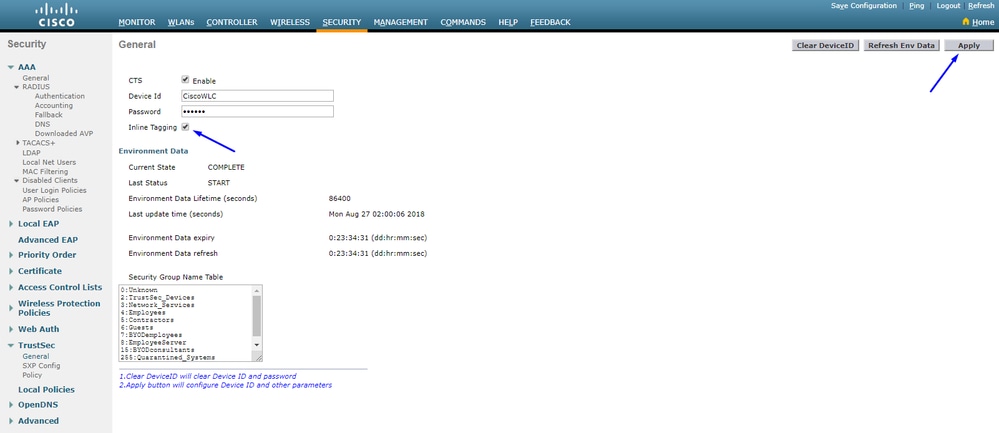
Enable TrustSec on WLC
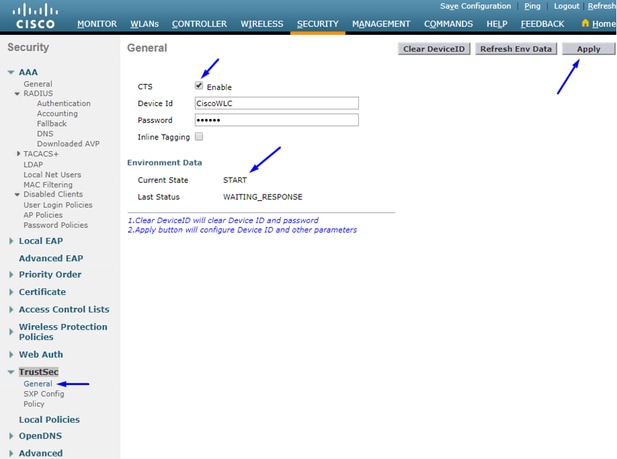

Note: The CTS Device Id and Password must be the same as the Device Id and Password that you specified in Administration > Network Devices > Add Device > Advanced TrustSec Settings section in Cisco ISE.
Verify PAC has been Provisioned on WLC
You see the WLC has the PAC provisioned successfully after you click Refresh Env Data (you do this in this step):

Download CTS Environment Data from Cisco ISE to WLC
After you click Refresh Env Data, your WLC downloads your SGTs.
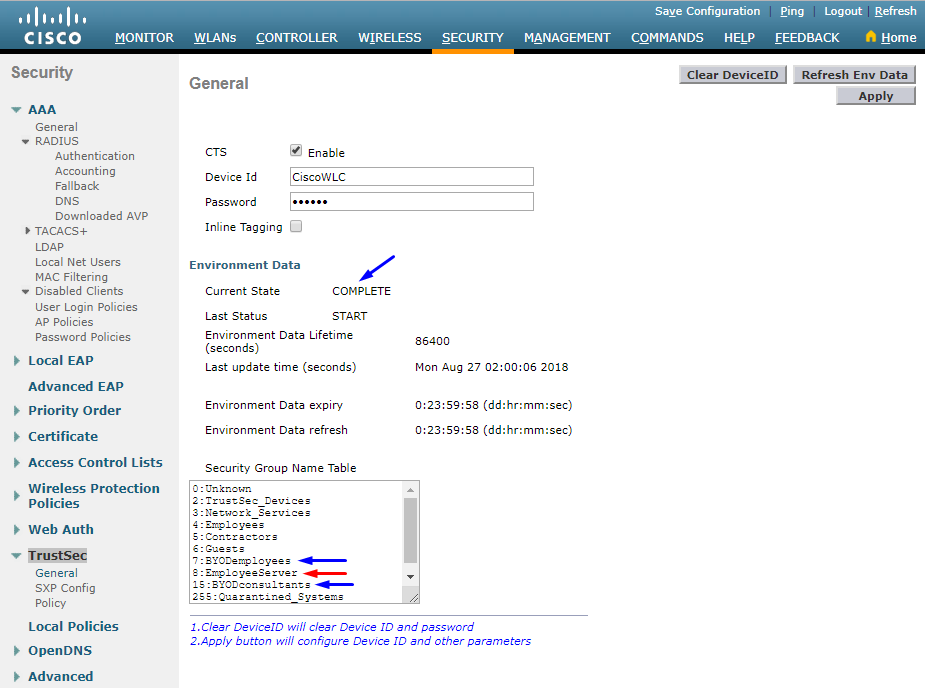
Enable SGACL Downloads and Enforcement on Traffic

Assign WLC and Access Point the SGT of 2 (TrustSec_Devices)
Give the WLC+WLAN an SGT of 2 (TrustSec_Devices) to allow traffic (SSH, HTTPS, and CAPWAP) to/from the WLC + AP through the switch.
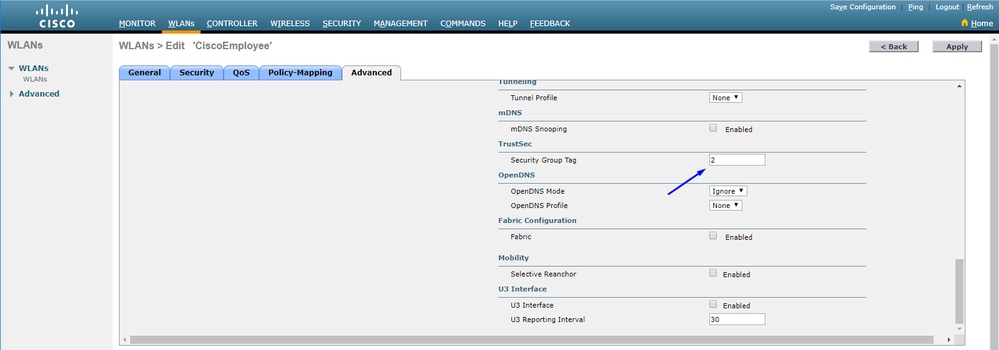
Enable Inline Tagging on WLC
Under Wireless > Access Points > Global Configuration scroll down and select TrustSec Config.

Enable Inline Tagging on Catalyst Switch
CatalystSwitch(config)#interface TenGigabitEthernet1/0/48
CatalystSwitch(config-if)#description goestoWLC
CatalystSwitch(config-if)#switchport trunk native vlan 15
CatalystSwitch(config-if)#switchport trunk allowed vlan 15,455,463,1115
CatalystSwitch(config-if)#switchport mode trunk
CatalystSwitch(config-if)#cts role-based enforcement
CatalystSwitch(config-if)#cts manual
CatalystSwitch(config-if-cts-manual)#policy static sgt 2 trusted
Verify
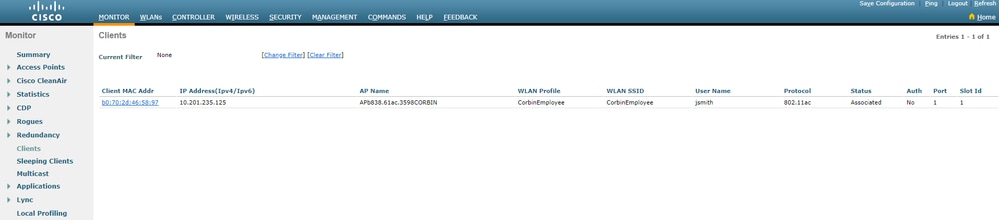


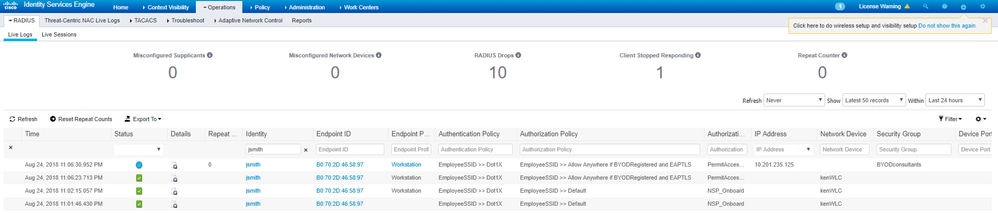
CatalystSwitch#show platform acl counters hardware | inc SGACL
Egress IPv4 SGACL Drop (454): 10 frames
Egress IPv6 SGACL Drop (455): 0 frames
Egress IPv4 SGACL Cell Drop (456): 0 frames
Egress IPv6 SGACL Cell Drop (457): 0 frames

Tip: If you use a Cisco ASR, Nexus, or Cisco ASA instead, the document listed here can help verify your SGT taggings are enforced: TrustSec Troubleshooting Guide.
Authenticate to wireless with username jsmith password Admin123 - you encounter the deny ACL in the switch:










































 Feedback
Feedback