Introduction
This document describes how to integrate Identity Services Engine (ISE) 3.3 patch 1 with Duo for Multi-factor Authentication. From version 3.3 patch 1 ISE can be configured for native integration with Duo services hence eliminating the need for Authentication Proxy.
Prerequisites
Requirements
Cisco recommends that you have basic knowledge of these topics:
Components Used
The information in this document is based on:
- Cisco ISE Version 3.3 patch 1
- Duo
- Cisco ASA version 9.16(4)
- Cisco Secure Client version 5.0.04032
The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, ensure that you understand the potential impact of any command.
Configure
Flow Diagram
 Flow Diagram
Flow Diagram
Steps
0. Configuration Phase includes the selection of the Active Directory Groups, from which users are synced up, the sync happens once the MFA wizard is completed. It consists of two steps. Lookups to Active Directory to get the list of users and certain attributes. A call to Duo Cloud with Cisco ISE Admin API is made to push users there. Administrators are required to enroll users. Enrolling can include the optional step of activating the user for Duo Mobile, which allows your users to use one-tap authentication with Duo Push
1. VPN connection is initiated, user inputs the username and password and clicks on OK. Network device sends RADIUS Access-Request is sent to PSN
2. PSN node authenticates the user via Active Directory
3. When authentication succeeds and MFA Policy is configured, PSN engages PAN in order to contact Duo Cloud
4. A call to Duo Cloud with Cisco ISE Auth API is made to invoke a second-factor authentication with Duo. ISE communicates with Duo's service on SSL TCP port 443.
5. Second-factor authentication takes place. User completes the second-factor authentication process
6. Duo responds to PAN with the result of the second-factor authentication
7. PAN responds to PSN with the result of the second-factor authentication
8. Access-Accept is sent to the Network Device, VPN Connection is established
Configurations
Select Applications to Protect
Navigate to Duo Admin Dashboard https://admin.duosecurity.com/login. Login with Admin credentials.
Navigate to Dashboard > Applications > Protect an Application. Look for Cisco ISE Auth API and select Protect.
 Auth API 1
Auth API 1
Make a note of Integration key and Secret key.
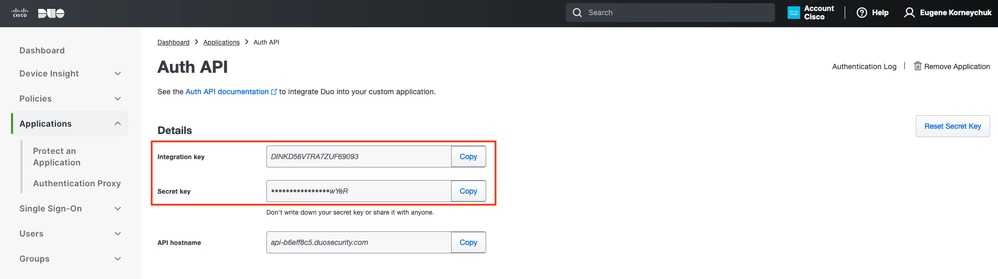 Auth API 2
Auth API 2
Navigate to Dashboard > Applications > Protect an Application. Look for Cisco ISE Admin API and select Protect.
Note: Only administrators with the Owner role can create or modify Cisco ISE Admin API application in the Duo Admin Panel.
 Auth API 1
Auth API 1
Make a note of Integration key and Secret key and API hostname.
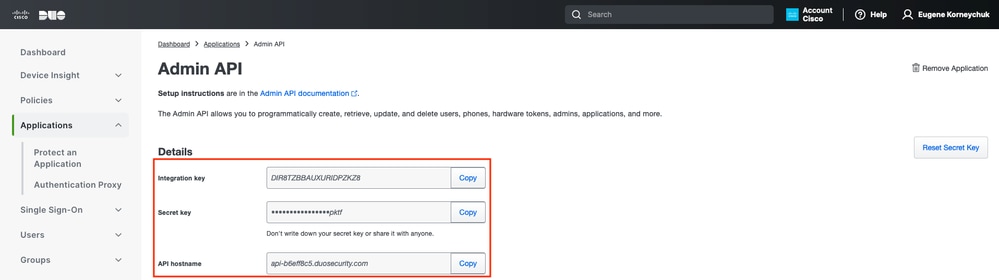 Admin API 2
Admin API 2
Configure API Permissions
Navigate to Dashboard > Applications > Application. Select Cisco ISE Admin API.
Check Grant Read Resource and Grant Write Resource permissions. Click on Save Changes.
 Admin API 3
Admin API 3
Integrate ISE with Active Directory
1. Navigate to Administration > Identity Management > External Identity Stores > Active Directory > Add. Provide the Join Point Name, Active Directory Domain and click Submit.
 Active Directory 1
Active Directory 1
2. When prompted to Join all ISE Nodes to this Active Directory Domain, click Yes.
 Active Directory 2
Active Directory 2
3. Provide AD User Name and Password, click OK.
 Active Directory 3
Active Directory 3
AD account required for domain access in ISE can have either of these:
- Add workstations to domain user right in respective domain
- Create Computer Objects or Delete Computer Objects permission on respective computers container where ISE machine's account is created before it joins ISE machine to the domain
Note: Cisco recommends to disable the lockout policy for the ISE account and configure the AD infrastructure to send alerts to the admin if a wrong password is used for that account. When the wrong password is entered, ISE does not create or modify its machine account when it is necessary and therefore possibly deny all authentications.
4. Status of AD is Operational.
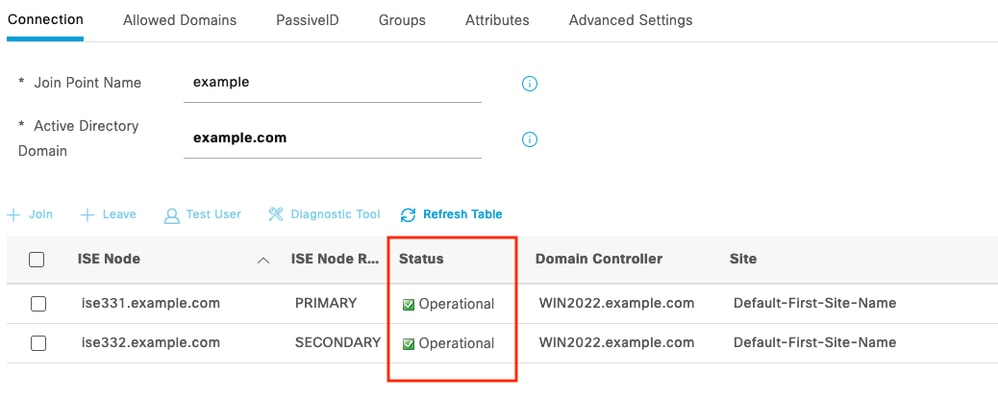 Active Directory 4
Active Directory 4
5. Navigate to Groups > Add > Select Groups From Directory > Retrieve Groups. Select checkboxes against AD Groups of your choice (which are used to sync users and for Authorization Policy), as shown in this image.
 Active Directory 5
Active Directory 5
6. Click Save to save retrieved AD Groups.
 Active Directory 6
Active Directory 6
Enable Open API
Navigate to Administration > System > Settings > API Settings > API Service Settings. Enable Open API and click on Save.
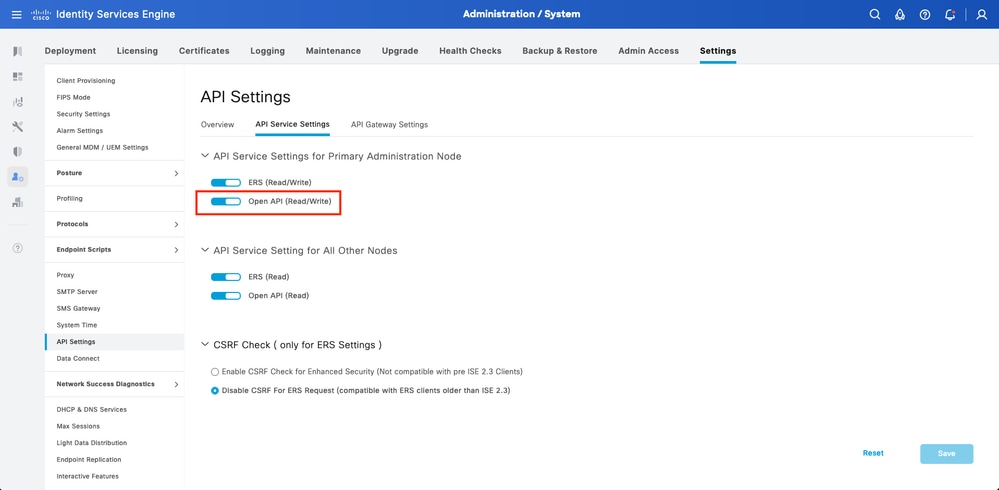 Open API
Open API
Enable MFA Identity Source
Navigate to Administration > Identity Management > Settings > External Identity Sources Settings. Enable MFA and click on Save.
 ISE MFA 1
ISE MFA 1
Configure MFA External Identity Source
Navigate to Administration > Identity Management > External Identity Sources. Click on Add. On the Welcome Screen click on Let's Do It.
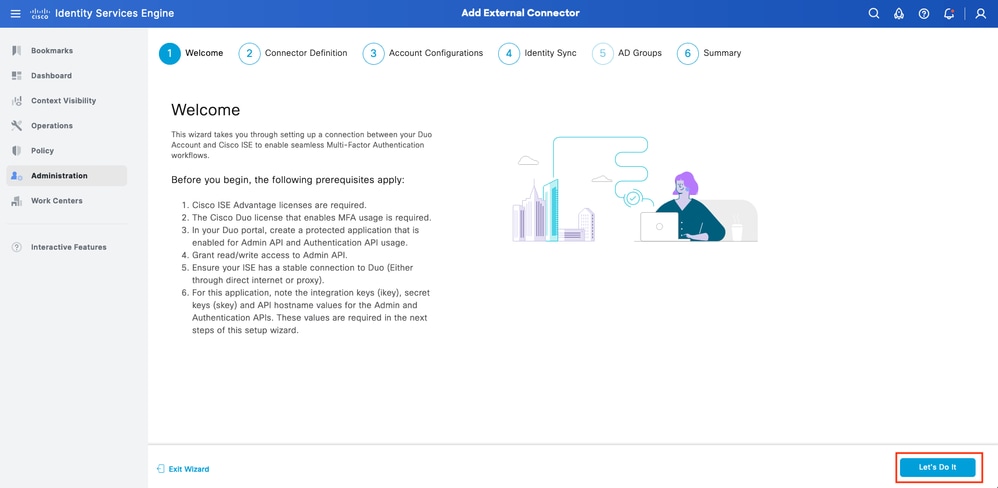 ISE Duo wizard 1
ISE Duo wizard 1
On the next screen configure Connection Name and click on Next.
 ISE Duo wizard 2
ISE Duo wizard 2
Configure the values of API Hostname, Cisco ISE Admin API Integration and Secret Keys, Cisco ISE Auth API Integration and Secret Keys from Select Applications to Protect step.
 ISE Duo wizard 3
ISE Duo wizard 3
Click on Test Connection. Once the Test Connection succeeds you can click on Next.
 ISE Duo wizard 4
ISE Duo wizard 4
Configure Identity Sync. This process synchronizes users from the Active Directory groups you select into Duo Account using API credentials provided earlier. Select Active Directory Join Point. Click on Next.
Note: Active Directory configuration is outside of the scope of the document, Follow this document in order to integrate ISE with Active Directory.
 ISE Duo wizard 5
ISE Duo wizard 5
Select Active Directory Groups from which you would like users to be synchronized with Duo. Click on Next.
 ISE Duo wizard 6
ISE Duo wizard 6
Verify the settings are correct and click on Done.
 ISE Duo wizard 7
ISE Duo wizard 7
Enroll User into Duo
Note: Duo User Enrollment is outside of the scope of the document, consider this document to learn more about enrolling the users. For the purpose of this document, manual user enrolment is used.
Open Duo Admin Dashboard. Navigate to Dashboard > Users. Click on the user synchronized from ISE.
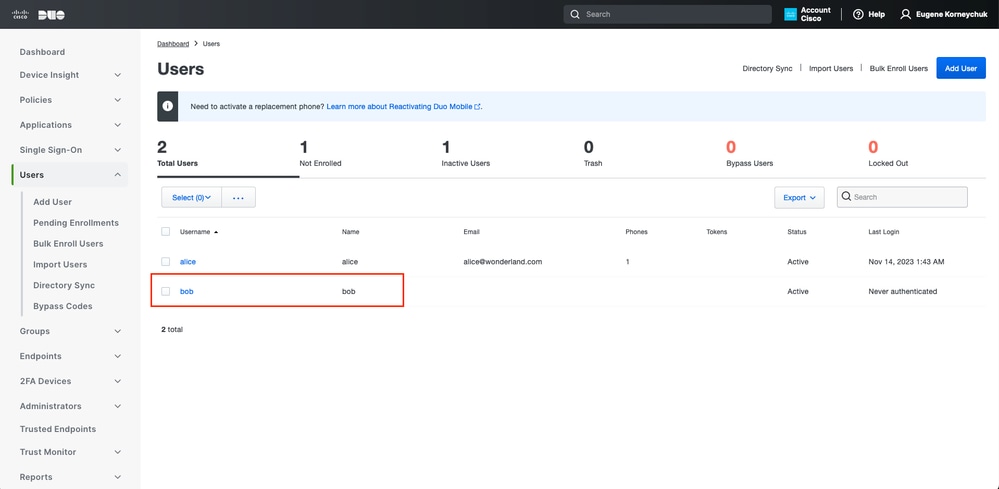 Duo enroll 1
Duo enroll 1
Scroll down to the Phones. Click on Add Phone.
 Duo enroll 2
Duo enroll 2
Enter the Phone Number and click on Add Phone.
 Duo Enroll 3
Duo Enroll 3
Configure Policy Sets
1. Configure Authentication Policy
Navigate to Policy > Policy Set. Select the Policy Set for which you would like to enable MFA. Configure Authentication Policy with Primary Authentication Identity Store as Active Directory.
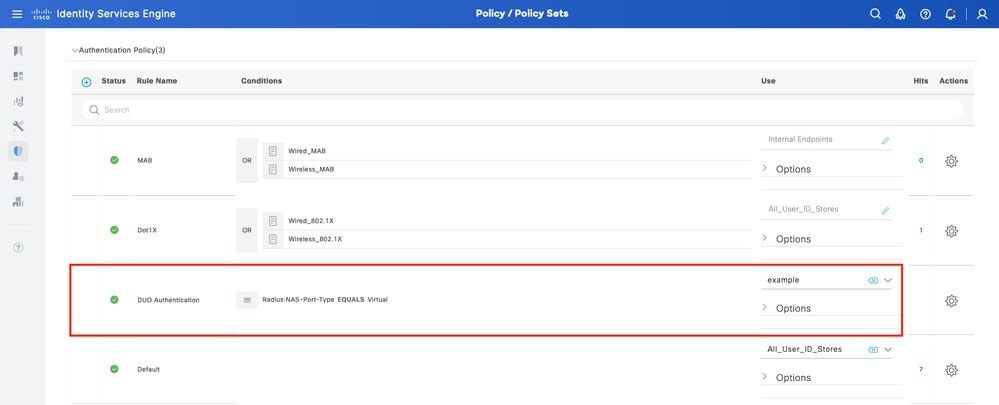 Policy Set 1
Policy Set 1
2. Configure MFA Policy
Once MFA is enabled on ISE, a new section in ISE Policy Sets is available. Expand MFA Policy and click on + in order to add MFA Policy. Configure MFA Conditions of your choice, select DUO-MFA configured previously in Use section. Click on Save.
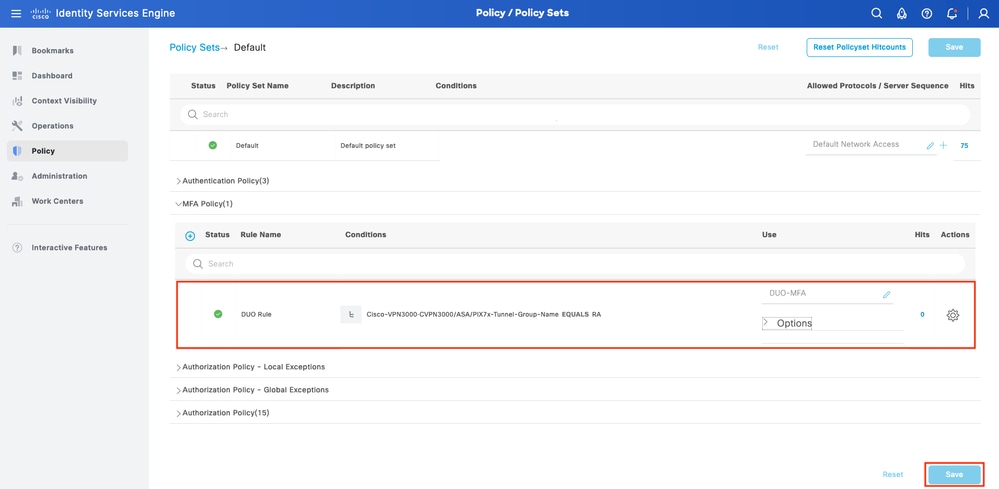 ISE Policy
ISE Policy
Note: Policy configured above relies on the Tunnel-Group Named RA. Users connected to RA tunnel group are forced to perform MFA. ASA/FTD configuration is outside of the scope of this document. Use this document in order to configure ASA/FTD
3. Configure Authorization Policy
Configure Authorization Policy with Active Directory Group condition and permissions of your choice.
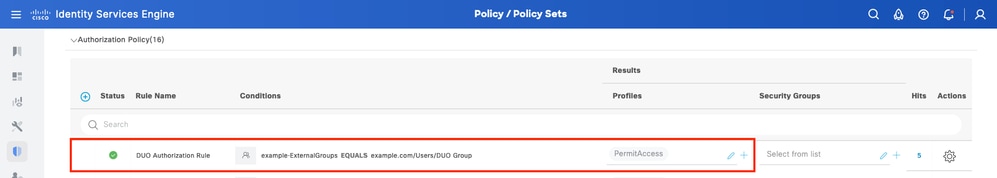 Policy Set 3
Policy Set 3
Limitations
At the time of writing this document:
1. Only Duo push and phone are supported as a second-factor authentication method
2. No Groups are pushed to Duo Cloud, only User sync is supported
3. Only the following multifactor authentication use cases are supported:
- VPN user authentication
- TACACS+ admin access authentication
Verify
Open Cisco Secure Client, click on Connect. Provide Username and Password and click OK.
 VPN Client
VPN Client
Users Mobile Device must receive a Duo Push Notification. Approve it. VPN Connection is Established.
 Duo Push
Duo Push
Navigate to ISE Operations > Live Logs to confirm User Authentication.
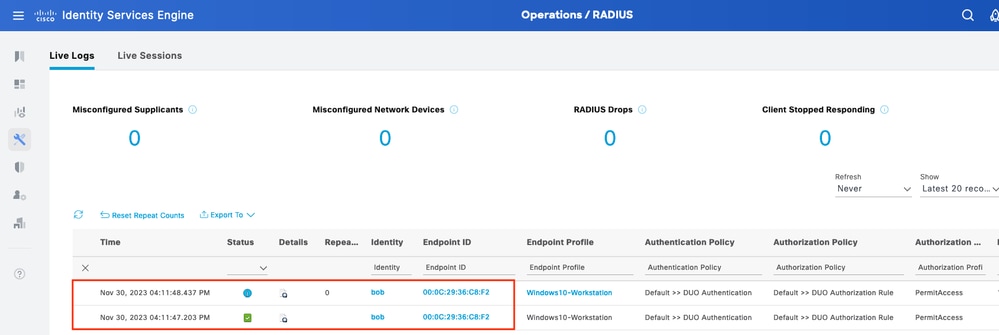 Live Logs 1
Live Logs 1
Click on the Details Authentication Report, verify Authentication Policy, Authorization Policy and Authorization Result. Scroll through the Steps on the right. To confirm MFA was successful the following line should be present:
Multi-Factor Authentication is Successful
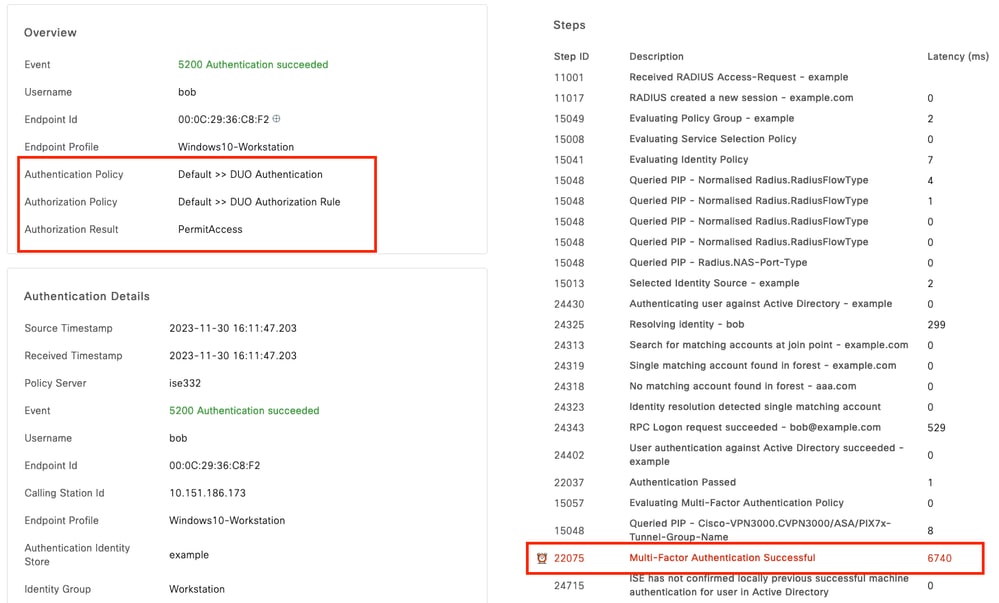 Live Logs 2
Live Logs 2
Troubleshoot
Debugs to enable on ISE.
| Use Case |
Log Component |
Log File |
Key Log Messages |
| MFA related logs |
policy-engine |
ise-psc.log |
DuoMfaAuthApiUtils -:::::- Submitted request to Duo Client manager
DuoMfaAuthApiUtils --> Duo response |
| Policy related logs |
prrt-JNI |
prrt-management.log |
RadiusMfaPolicyRequestProcessor
TacacsMfaPolicyRequestProcessor |
| Authentication related logs |
runtime-AAA |
prrt-server.log |
MfaAuthenticator::onAuthenticateEvent
MfaAuthenticator::sendAuthenticateEvent
MfaAuthenticator::onResponseEvaluatePolicyEvent |
| Duo Authentcation, ID Sync related logs |
|
duo-sync-service.log |
|
































 Feedback
Feedback