Use OpenAPI to Retrieve ISE Policy Information on ISE 3.3
Available Languages
Download Options
Bias-Free Language
The documentation set for this product strives to use bias-free language. For the purposes of this documentation set, bias-free is defined as language that does not imply discrimination based on age, disability, gender, racial identity, ethnic identity, sexual orientation, socioeconomic status, and intersectionality. Exceptions may be present in the documentation due to language that is hardcoded in the user interfaces of the product software, language used based on RFP documentation, or language that is used by a referenced third-party product. Learn more about how Cisco is using Inclusive Language.
Contents
Introduction
This document describes the procedure for utilizing OpenAPI to manage Cisco Identity Services Engine (ISE) Policy.
Prerequisites
Requirements
Cisco recommends that you have knowledge of these topics:
- Cisco Identity Services Engine (ISE)
- REST API
- Python
Components Used
- ISE 3.3
- Python 3.10.0
The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, ensure that you understand the potential impact of any command.
Background Information
From Cisco ISE 3.1 onwards, newer APIs are available in the OpenAPI format. Management policy optimizes network security and management by enhancing interoperability, improving automation efficiency, strengthening security, fostering innovation, and reducing costs. This policy allows ISE to seamlessly integrate with other systems, achieve automated configuration and management, provide granular access control, encourage third-party innovation, and simplify management processes, thereby reducing maintenance costs and increasing overall return on investment.
Configure
Network Diagram
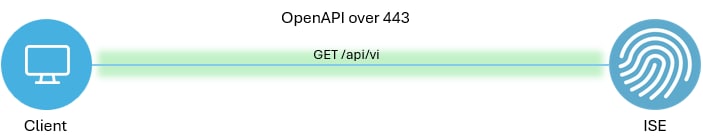 Topology
Topology
Configuration on ISE
Step 1. Add anOpenAPI admin account.
To add an API admin, navigate toAdministration > System > Admin Access > Administrators > Admin Users > Add.
 API Admin
API Admin
Step 2. Enable OpenAPI on ISE.
Open API is disabled by default on ISE. To enable it, navigate to Administration > System > Settings > API Settings > API Service Settings. Toggle the OpenAPI options. Click Save.
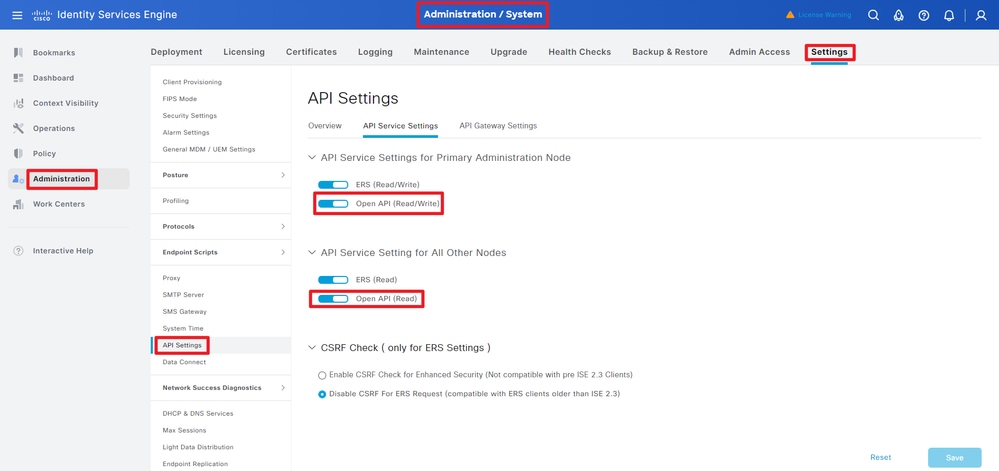 Enable OpenAPI
Enable OpenAPI
Step 3. Explore ISE OpenAPI.
Navigate to Administration > System > Settings > API Settings > Overview. Click OpenAPI to visit link.
 Visit OpenAPI
Visit OpenAPI
Python Examples
Device Admin - List Of Policy Sets
This API retrieves device admin policy sets information.
Step 1. Required information for an API call.
| Method | GET |
| URL |
https://<ISE-PAN-IP>/api/v1/policy/device-admin/policy-set
|
| Credentials | Use OpenAPI account credentials. |
| Headers |
Accept: application/json
Content-Type: application/json
|
Step 2. Locate the URL that is utilized to retrieve device admin policy sets information.
 API URI
API URI
Step 3. This is an example of Python code. Copy and paste the content. Replace the ISE IP, username, and password. Save as a python file to execute.
Ensure good connectivity between ISE and the device running the python code example.
from requests.auth import HTTPBasicAuth
import requests
requests.packages.urllib3.disable_warnings()
if __name__ == "__main__":
url = "https://10.106.33.92/api/v1/policy/device-admin/policy-set"
headers = {"Accept": "application/json", "Content-Type": "application/json"}
basicAuth = HTTPBasicAuth("ApiAdmin", "Admin123")
response = requests.get(url=url, auth=basicAuth, headers=headers, verify=False)
print("Return Code:")
print(response.status_code)
print("Expected Outputs:")
print(response.json())This is the example of expected outputs.
Return Code:
200
Expected Outputs:
{'version': '1.0.0', 'response': [{'default': True, 'id': '41ed8579-429b-42a8-879e-61861cb82bbf', 'name': 'Default', 'description': 'Tacacs Default policy set', 'hitCounts': 0, 'rank': 0, 'state': 'enabled', 'condition': None, 'serviceName': 'Default Device Admin', 'isProxy': False, 'link': {'rel': 'self', 'href': 'https://10.106.33.92/api/v1/policy/device-admin/policy-set/41ed8579-429b-42a8-879e-61861cb82bbf', 'type': 'application/json'}}]}Device Admin - Get Authentication Rules
This API retrieves authentication rules of a particular policy set.
Step 1. Required information for an API call.
| Method | GET |
| URL |
https://<ISE-PAN-IP>/api/v1/policy/device-admin/policy-set/<ID-Of-Policy-Set>/authentication
|
| Credentials | Use OpenAPI account credentials. |
| Headers |
Accept: application/json
Content-Type: application/json
|
Step 2. Locate the URL that is utilized to retrieve authentication rule information.
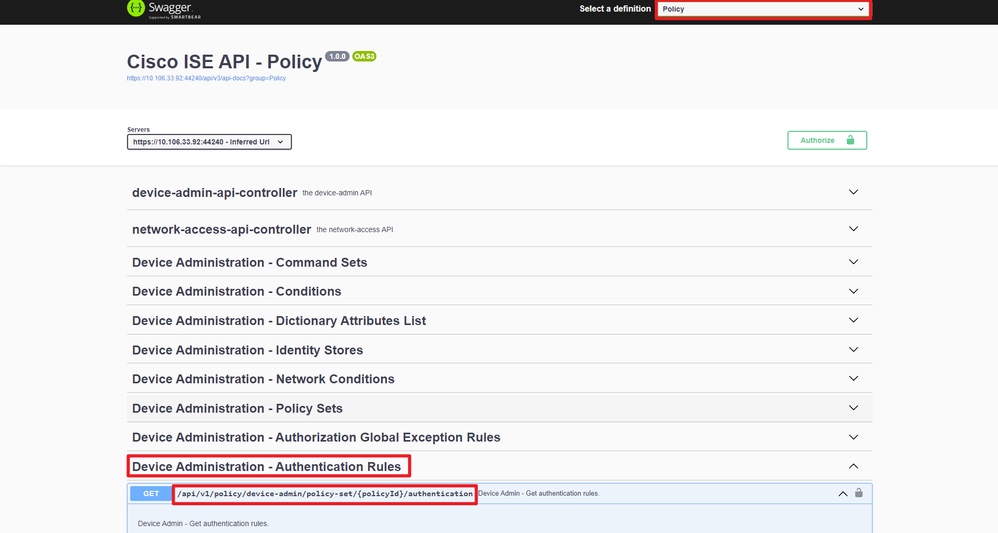 API URI
API URI
Step 3. This is an example of Python code. Copy and paste the content. Replace the ISE IP, username, and password. Save as a python file to execute.
Ensure good connectivity between ISE and the device running the python code example.
from requests.auth import HTTPBasicAuth
import requests
requests.packages.urllib3.disable_warnings()
if __name__ == "__main__":
url = "https://10.106.33.92/api/v1/policy/device-admin/policy-set/41ed8579-429b-42a8-879e-61861cb82bbf/authentication"
headers = {"Accept": "application/json", "Content-Type": "application/json"}
basicAuth = HTTPBasicAuth("ApiAdmin", "Admin123")
response = requests.get(url=url, auth=basicAuth, headers=headers, verify=False)
print("Return Code:")
print(response.status_code)
print("Expected Outputs:")
print(response.json())
Note: The ID is from API outputs in step 3 of Device Admin - List Of Policy Sets. For example, 41ed8579-429b-42a8-879e-61861cb82bbf is TACACS Default policy set.
This is the example of expected outputs.
Return Code:
200
Expected Outputs:
{'version': '1.0.0', 'response': [{'rule': {'default': True, 'id': '73461597-0133-45ce-b4cb-6511ce56f262', 'name': 'Default', 'hitCounts': 0, 'rank': 0, 'state': 'enabled', 'condition': None}, 'identitySourceName': 'All_User_ID_Stores', 'ifAuthFail': 'REJECT', 'ifUserNotFound': 'REJECT', 'ifProcessFail': 'DROP', 'link': {'rel': 'self', 'href': 'https://10.106.33.92/api/v1/policy/device-admin/policy-set/41ed8579-429b-42a8-879e-61861cb82bbf/authentication/73461597-0133-45ce-b4cb-6511ce56f262', 'type': 'application/json'}}]}Device Admin - Get Authorization Rules
This API retrieves authorization rules of a particular policy set.
Step 1. Required information for an API call.
| Method | GET |
| URL |
https://<ISE-PAN-IP>/api/v1/policy/device-admin/policy-set/<ID-Of-Policy-Set>/authorization
|
| Credentials | Use OpenAPI account credentials. |
| Headers |
Accept: application/json
Content-Type: application/json
|
Step 2. Locate the URL that is utilized to retrieve the authorization rule information.
 API URI
API URI
Step 3. This is an example of Python code. Copy and paste the content. Replace the ISE IP, username, and password. Save as a python file to execute.
Ensure good connectivity between ISE and the device running the python code example.
from requests.auth import HTTPBasicAuth
import requests
requests.packages.urllib3.disable_warnings()
if __name__ == "__main__":
url = "https://10.106.33.92/api/v1/policy/device-admin/policy-set/41ed8579-429b-42a8-879e-61861cb82bbf/authorization"
headers = {"Accept": "application/json", "Content-Type": "application/json"}
basicAuth = HTTPBasicAuth("ApiAdmin", "Admin123")
response = requests.get(url=url, auth=basicAuth, headers=headers, verify=False)
print("Return Code:")
print(response.status_code)
print("Expected Outputs:")
print(response.json())
Note: The ID is from API outputs in step 3 of Device Admin - List Of Policy Sets. For example, 41ed8579-429b-42a8-879e-61861cb82bbf is TACACS Default policy set.
This is the example of expected outputs.
Return Code:
200
Expected Outputs:
{'version': '1.0.0', 'response': [{'rule': {'default': True, 'id': '39d9f546-e58c-4f79-9856-c0a244b8a2ae', 'name': 'Default', 'hitCounts': 0, 'rank': 0, 'state': 'enabled', 'condition': None}, 'commands': ['DenyAllCommands'], 'profile': 'Deny All Shell Profile', 'link': {'rel': 'self', 'href': 'https://10.106.33.92/api/v1/policy/device-admin/policy-set/41ed8579-429b-42a8-879e-61861cb82bbf/authorization/39d9f546-e58c-4f79-9856-c0a244b8a2ae', 'type': 'application/json'}}]}Network Access - List Of Policy Sets
This API retrieves network access policy sets of ISE deployments.
Step 1. Required information for an API call.
| Method | GET |
| URL |
https://<ISE-PAN-IP>/api/v1/policy/network-access/policy-set
|
| Credentials | Use OpenAPI account credentials. |
| Headers |
Accept: application/json
Content-Type: application/json
|
Step 2. Locate the URL that is utilized to retrieve the specific ISE node information.
 API URI
API URI
Step 3. This is an example of Python code. Copy and paste the content. Replace the ISE IP, username, and password. Save as a python file to execute.
Ensure good connectivity between ISE and the device running the python code example.
from requests.auth import HTTPBasicAuth
import requests
requests.packages.urllib3.disable_warnings()
if __name__ == "__main__":
url = "https://10.106.33.92/api/v1/policy/network-access/policy-set"
headers = {"Accept": "application/json", "Content-Type": "application/json"}
basicAuth = HTTPBasicAuth("ApiAdmin", "Admin123")
response = requests.get(url=url, auth=basicAuth, headers=headers, verify=False)
print("Return Code:")
print(response.status_code)
print("Expected Outputs:")
print(response.json())This is the example of expected outputs.
Return Code:
200
Expected Outputs:
{'version': '1.0.0', 'response': [{'default': False, 'id': 'ba71a417-4a48-4411-8bc3-d5df9b115769', 'name': 'BGL_CFME02-FMC', 'description': None, 'hitCounts': 0, 'rank': 0, 'state': 'enabled', 'condition': {'link': None, 'conditionType': 'ConditionAndBlock', 'isNegate': False, 'children': [{'link': None, 'conditionType': 'ConditionAttributes', 'isNegate': False, 'dictionaryName': 'DEVICE', 'attributeName': 'Location', 'operator': 'equals', 'dictionaryValue': None, 'attributeValue': 'All Locations#BGL_CFME02'}, {'link': None, 'conditionType': 'ConditionAttributes', 'isNegate': False, 'dictionaryName': 'DEVICE', 'attributeName': 'Device Type', 'operator': 'equals', 'dictionaryValue': None, 'attributeValue': 'All Device Types#FMCv'}]}, 'serviceName': 'Default Network Access', 'isProxy': False, 'link': {'rel': 'self', 'href': 'https://10.106.33.92/api/v1/policy/network-access/policy-set/ba71a417-4a48-4411-8bc3-d5df9b115769', 'type': 'application/json'}}, {'default': False, 'id': 'f7d82b2d-1007-44f6-961b-efa721d6ebec', 'name': 'SPRT', 'description': None, 'hitCounts': 0, 'rank': 1, 'state': 'enabled', 'condition': {'link': None, 'conditionType': 'ConditionAttributes', 'isNegate': False, 'dictionaryName': 'DEVICE', 'attributeName': 'Device Type', 'operator': 'equals', 'dictionaryValue': None, 'attributeValue': 'All Device Types#SPRT'}, 'serviceName': 'Default Network Access', 'isProxy': False, 'link': {'rel': 'self', 'href': 'https://10.106.33.92/api/v1/policy/network-access/policy-set/f7d82b2d-1007-44f6-961b-efa721d6ebec', 'type': 'application/json'}}, {'default': True, 'id': '467f6a69-344d-407f-81a4-e87c5dc7e438', 'name': 'Default', 'description': 'Default policy set', 'hitCounts': 0, 'rank': 2, 'state': 'enabled', 'condition': None, 'serviceName': 'Default Network Access', 'isProxy': False, 'link': {'rel': 'self', 'href': 'https://10.106.33.92/api/v1/policy/network-access/policy-set/467f6a69-344d-407f-81a4-e87c5dc7e438', 'type': 'application/json'}}]}Network Access - Get Authentication Rules
This API retrieves authentication rules of a particular policy set.
Step 1. Required information for an API call.
| Method | GET |
| URL |
https://<ISE-PAN-IP>/api/v1/policy/network-access/policy-set/<ID-Of-Policy-Set>/authentication
|
| Credentials | Use OpenAPI account credentials. |
| Headers |
Accept: application/json
Content-Type: application/json
|
Step 2. Locate the URL that is utilized to retrieve the authentication rule information.
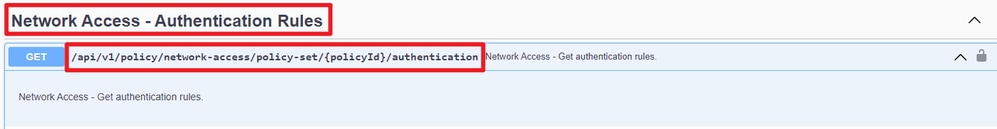 API URI
API URI
Step 3. This is an example of Python code. Copy and paste the content. Replace the ISE IP, username, and password. Save as a python file to execute.
Ensure good connectivity between ISE and the device running the python code example.
from requests.auth import HTTPBasicAuth
import requests
requests.packages.urllib3.disable_warnings()
if __name__ == "__main__":
url = "https://10.106.33.92/api/v1/policy/network-access/policy-set/ba71a417-4a48-4411-8bc3-d5df9b115769/authentication"
headers = {"Accept": "application/json", "Content-Type": "application/json"}
basicAuth = HTTPBasicAuth("ApiAdmin", "Admin123")
response = requests.get(url=url, auth=basicAuth, headers=headers, verify=False)
print("Return Code:")
print(response.status_code)
print("Expected Outputs:")
print(response.json())
Note: The ID is from API outputs in step 3 of Network Access - List Of Policy Sets. For example, ba71a417-4a48-4411-8bc3-d5df9b115769 is BGL_CFME02-FMC.
This is the example of expected outputs.
Return Code:
200
Expected Outputs:
{'version': '1.0.0', 'response': [{'rule': {'default': True, 'id': '03875777-6c98-4114-a72e-a3e1651e533a', 'name': 'Default', 'hitCounts': 0, 'rank': 0, 'state': 'enabled', 'condition': None}, 'identitySourceName': 'S.H.I.E.L.D', 'ifAuthFail': 'REJECT', 'ifUserNotFound': 'REJECT', 'ifProcessFail': 'DROP', 'link': {'rel': 'self', 'href': 'https://10.106.33.92/api/v1/policy/network-access/policy-set/ba71a417-4a48-4411-8bc3-d5df9b115769/authentication/03875777-6c98-4114-a72e-a3e1651e533a', 'type': 'application/json'}}]}Network Access - Get Authorization Rules
This API retrieves authorization rules of a particular policy set.
Step 1. Required information for an API call.
| Method | GET |
| URL |
https://<ISE-PAN-IP>/api/v1/policy/network-access/policy-set/<ID-Of-Policy-Set>/authorization
|
| Credentials | Use OpenAPI account credentials. |
| Headers |
Accept: application/json
Content-Type: application/json
|
Step 2. Locate the URL that is utilized to retrieve the authorization rule information.
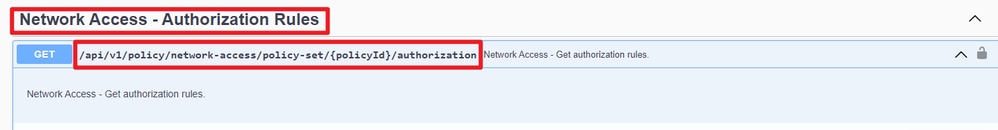 API URI
API URI
Step 3. This is an example of Python code. Copy and paste the content. Replace the ISE IP, username, and password. Save as a python file to execute.
Ensure good connectivity between ISE and the device running the python code example.
from requests.auth import HTTPBasicAuth
import requests
requests.packages.urllib3.disable_warnings()
if __name__ == "__main__":
url = "https://10.106.33.92/api/v1/policy/network-access/policy-set/ba71a417-4a48-4411-8bc3-d5df9b115769/authorization"
headers = {"Accept": "application/json", "Content-Type": "application/json"}
basicAuth = HTTPBasicAuth("ApiAdmin", "Admin123")
response = requests.get(url=url, auth=basicAuth, headers=headers, verify=False)
print("Return Code:")
print(response.status_code)
print("Expected Outputs:")
print(response.json())
Note: The ID is from API outputs in step 3 of Network Access - List Of Policy Sets. For example, ba71a417-4a48-4411-8bc3-d5df9b115769 is BGL_CFME02-FMC.
This is the example of expected outputs.
Return Code:
200
Expected Outputs:
{'version': '1.0.0', 'response': [{'rule': {'default': False, 'id': 'bc67a4e5-9000-4645-9d75-7c2403ca22ac', 'name': 'FMC Admin', 'hitCounts': 0, 'rank': 0, 'state': 'enabled', 'condition': {'link': None, 'conditionType': 'ConditionAttributes', 'isNegate': False, 'dictionaryName': 'S.H.I.E.L.D', 'attributeName': 'ExternalGroups', 'operator': 'equals', 'dictionaryValue': None, 'attributeValue': 'cisco.com/Cisco/Lab/Groups/FmcAdmin'}}, 'profile': ['FMC-BGL_CFME02-Admin'], 'securityGroup': None, 'link': {'rel': 'self', 'href': 'https://10.106.33.92/api/v1/policy/network-access/policy-set/ba71a417-4a48-4411-8bc3-d5df9b115769/authorization/bc67a4e5-9000-4645-9d75-7c2403ca22ac', 'type': 'application/json'}}, {'rule': {'default': True, 'id': 'e9f3034c-b768-4479-b6c3-3bb64bb6722c', 'name': 'Default', 'hitCounts': 0, 'rank': 1, 'state': 'enabled', 'condition': None}, 'profile': ['DenyAccess'], 'securityGroup': None, 'link': {'rel': 'self', 'href': 'https://10.106.33.92/api/v1/policy/network-access/policy-set/ba71a417-4a48-4411-8bc3-d5df9b115769/authorization/e9f3034c-b768-4479-b6c3-3bb64bb6722c', 'type': 'application/json'}}]}Troubleshoot
To troubleshoot issues that are related to the OpenAPIs, set theLog Level for theapiservicecomponent toDEBUGin theDebug Log Configurationwindow.
To enable debug, navigate toOperations > Troubleshoot > Debug Wizard > Debug Log Configuration > ISE Node > apiservice.
 API Service Debug
API Service Debug
To download debug log file, navigate to Operations > Troubleshoot > Download Logs > ISE PAN Node > Debug Logs.
 Download Debug Logs
Download Debug Logs
Revision History
| Revision | Publish Date | Comments |
|---|---|---|
1.0 |
18-Sep-2024
|
Initial Release |
Contributed by Cisco Engineers
- Bo PangTechnical Consulting Engineer
Contact Cisco
- Open a Support Case

- (Requires a Cisco Service Contract)
 Feedback
Feedback