Configure HTTPS Support for ISE SCEP Integration
Available Languages
Contents
Introduction
This document describes the steps required to configure Hypertext Transfer Protocol Secure (HTTPS) support for Secure Certificate Enrollment Protocol (SCEP) integration with the Identity Services Engine (ISE).
Prerequisites
Requirements
Cisco recommends that you have knowledge of these topics:
- Basic knowledge of Microsoft's Internet Information Services (IIS) web server
- Experience in the configuration of SCEP and certificates on ISE
Components Used
The information in this document is based on these software and hardware versions:
- ISE Release 1.1.x
- Windows Server 2008 R2 Enterprise with hotfixes for KB2483564 and KB2633200 installed
The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, make sure that you understand the potential impact of any command.
The information related to Microsoft certificate services is provided as a guide specifically for Cisco Bring Your Own Device (BYOD). Refer to Microsoft's TechNet as the definitive source of truth for Microsoft certification authority, Network Device Enrollment Service (NDES), and SCEP related server configurations.
Background Information
In a BYOD deployment, one of the core components is a Microsoft 2008 R2 Enterprise server that has the NDES role installed. This server is a member of the Active Directory (AD) forest. During the initial installation of NDES, Microsoft's IIS web server is automatically installed and configured to support HTTP termination of SCEP. In some BYOD deployments, customers might want to further secure the communications between ISE and NDES using HTTPS. This procedure details the steps required to request and install a Secure Socket Layer (SSL) certificate for the SCEP website.
Configure
NDES Server Certificate Configuration
- Connect to the NDES server via console or RDP.
- Click Start -> Administrative Tools -> Internet Information Services (IIS) Manager.
- Highlight the IIS server name and click the Server Certificates icon.
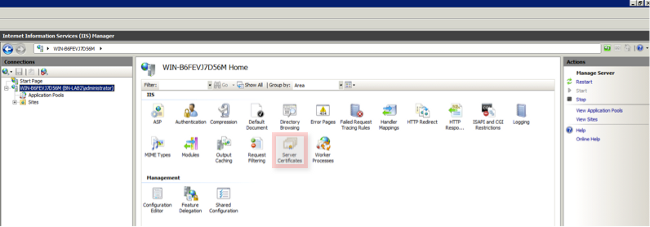
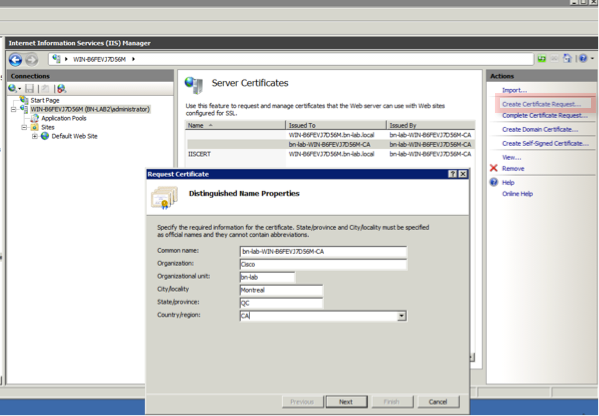
- Click on Create Certificate Request, and complete the fields.
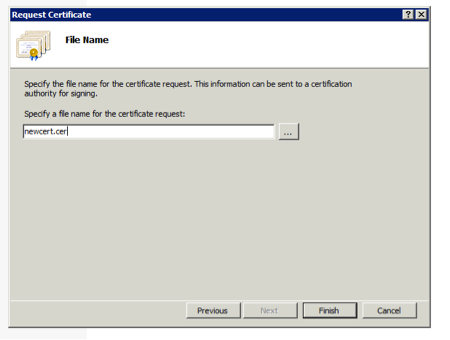
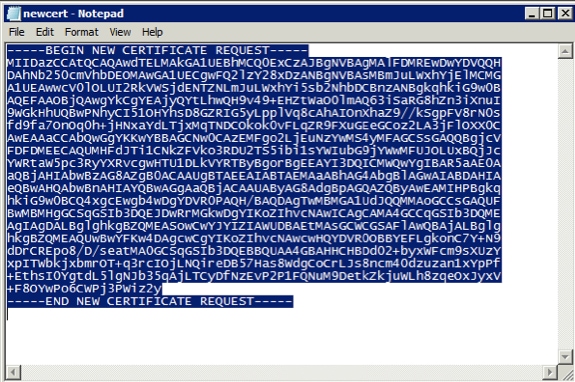
- Open the .cer file created in the previous step with a text editor and copy the content to the clipboard.
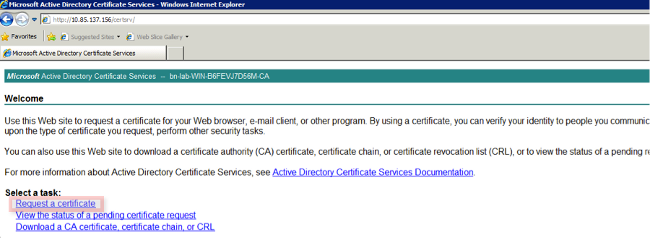
- Access the Microsoft CA Web Enrollment website and click Request a Certificate.
Example URL: http://yourCAIP/certsrv
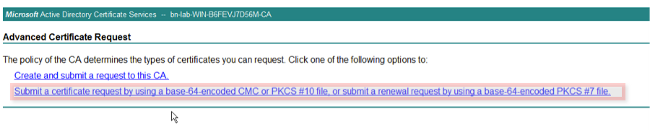
- Click Submit a certificate request by using.... Paste in the certificate content from the clipboard, and choose the Web Server template.
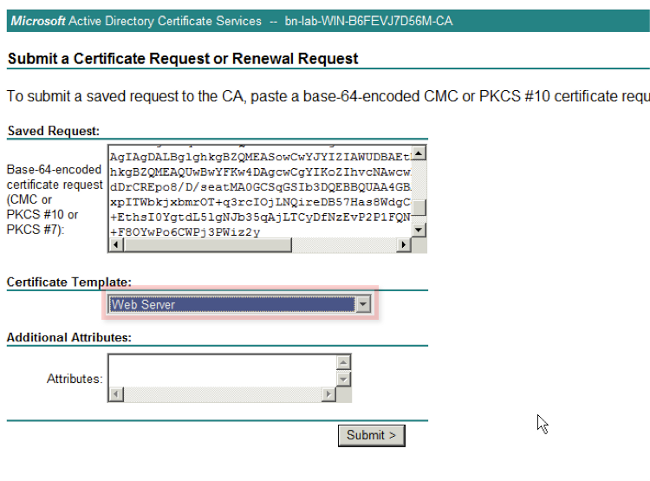
- Click Submit and then save the certificate file to the desktop.
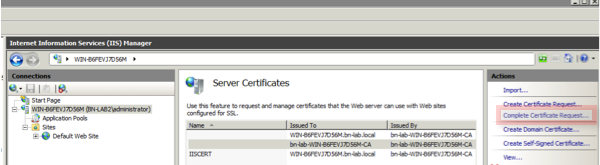
- Return to the NDES server and open the IIS Manager utilty. Click on the server name and then click Complete Certificate Request in order to import the newly created server certificate.
NDES Server IIS Binding Configuration
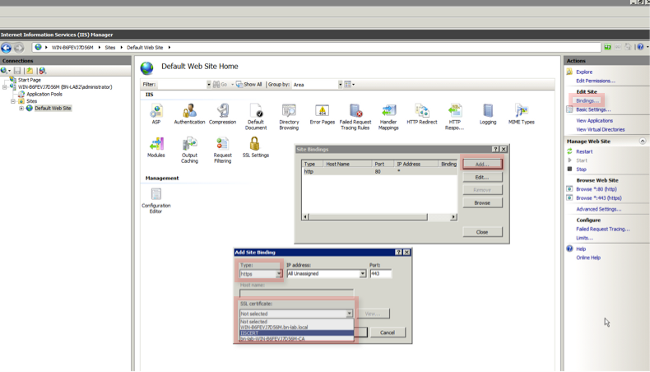
- Expand the server name, expand Sites, click Default Web Site.
- Click Bindings in the upper right corner.
- Click Add, change the Typeto HTTPS, and choose the certificate from the drop-down list.
- Click OK.
ISE Server Configuration
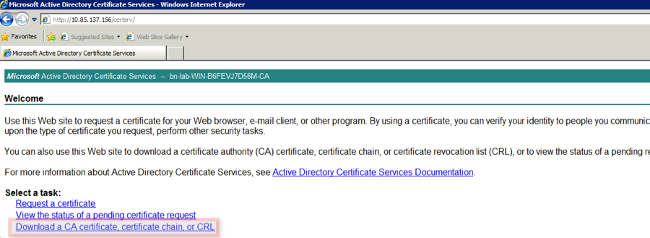
- Connect to the Web Enrollment interface of the CA server and download the CA certificate chain.
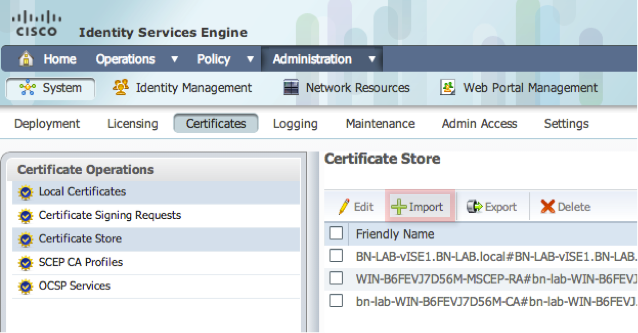
- From the ISE GUI, navigate to Administration -> Certificates -> Certificate Store and import the CA certificate chain into the ISE store.
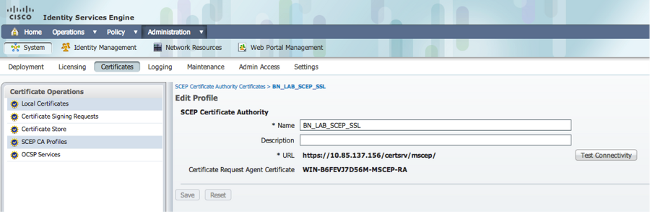
- Navigate to Administration -> Certificates -> SCEP CA Profiles and configure the URL for HTTPS. Click Test Connectivity and then click Save.
Verify
Use this section to confirm that your configuration works properly.
- Navigate to Administration -> Certificates -> Certificate Storeand verify that the CA certificate chain and the NDES server Registration Authority (RA) certificate are present.
- Use Wireshark or TCP Dump to monitor the initial SSL exchange between the ISE admin node and the NDES server.
The Output Interpreter Tool (registered customers only) supports certain show commands. Use the Output Interpreter Tool in order to view an analysis of show command output.
Troubleshoot
This section provides information you can use to troubleshoot your configuration.
- Break down the BYOD network topology into logical waypoints in order to help identify debug and capture points along the path between these endpoints - ISE, NDES, and CA.
- Ensure that TCP 443 is permitted bidirectionally between the ISE and the NDES server.
- Monitor the CA and NDES server application logs for registration errors and use Google or TechNet to research those errors.
- Use the TCP Dump utility on the ISE PSN and monitor traffic to and from the NDES server. This is located under Operations > Diagnostic Tools > General Tools.
- Install Wireshark on the NDES server or use SPAN on intermediary switches in order to capture SCEP traffic to and from the ISE PSN.
The Output Interpreter Tool (registered customers only) supports certain show commands. Use the Output Interpreter Tool in order to view an analysis of show command output.
Related Information
Revision History
| Revision | Publish Date | Comments |
|---|---|---|
1.0 |
27-May-2013 |
Initial Release |
Contact Cisco
- Open a Support Case

- (Requires a Cisco Service Contract)












 Feedback
Feedback