Configure and Troubleshoot Posture State Synchronization
Available Languages
Download Options
Bias-Free Language
The documentation set for this product strives to use bias-free language. For the purposes of this documentation set, bias-free is defined as language that does not imply discrimination based on age, disability, gender, racial identity, ethnic identity, sexual orientation, socioeconomic status, and intersectionality. Exceptions may be present in the documentation due to language that is hardcoded in the user interfaces of the product software, language used based on RFP documentation, or language that is used by a referenced third-party product. Learn more about how Cisco is using Inclusive Language.
Contents
Introduction
This document describes the configuration and use of Posture State Synchronization introduced in the Cisco Identity Service Engine(ISE) 3.1 version.
Prerequisites
Requirements
Cisco recommends that you have knowledge of these topics:
- Posture flow on Cisco ISE
- Configuration of posture components on Cisco ISE
It is supposed that you have a Posture configuration in place of any type.
To better understand the concepts described later, it is recommended to go through:
- Cisco Identity Services Engine Administrator Guide, Release 3.1
- Compare Earlier ISE Versions to ISE Posture Flow in ISE 2.2
- ISE Session Management and Posture
Components Used
The information in this document is based on these software and hardware versions:
- Cisco ISE version 3.1
- Cisco Secure Client 5.0.00556
The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, ensure that you understand the potential impact of any command.
Background information
ISE Posture flow usually does not allow Posture status to be updated on the Client from the ISE. Cisco Secure Client Posture Module is used to evaluate the Posture status of the endpoint and keeps it until network change, Periodic Reassessment, or other client-side triggers. If the endpoint Posture status changes on ISE due to a session termination or other reasons, the Secure Client Posture Module could be unaware of that change, so the Endpoint stays in Posture Unknown state with limited network access until one of the client-side triggers happens.
This document is focused on a new feature - Posture Status Synchronisation, which was developed to address this kind of issue and allow ISE to provide feedback to the Secure Client Posture Module on the current Posture Status of the endpoint.
Configure
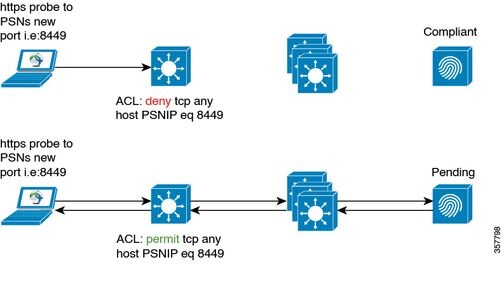
The Posture status probe port was introduced on each ISE PSN node when Posture State Synchronization is enabled - TCP 8449 by default. It is supposed to be reachable from the Endpoint if the Endpoint Posture status is Unknown or Pending and unreachable if the Endpoint status is Compliant.
Network Diagram
Configurations
Posture State Synchronisation feature configuration consists of two parts:
- AnyConnect Posture Profile configuration
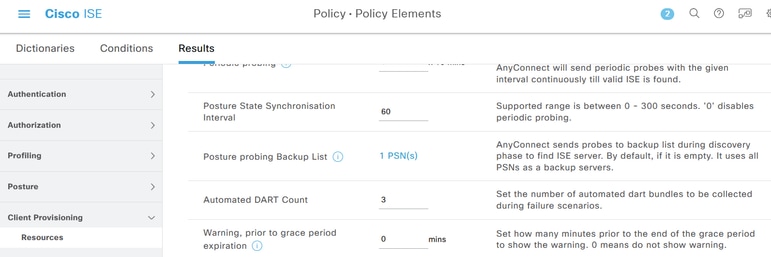
1.1 In the Cisco ISE GUI, navigate to Policy > Policy Elements > Results > Client Provisioning > Resources.
1.2 Select the AnyConnect Posture Profile you already use or create a new one.
1.3 In the Agent Behavior area, configure the Posture State Synchronisation Interval to any value between 1 and 300 seconds, 0 - disables Posture State Synchronisation
1.4 You can configure Posture Probing Backup List - Secure Client uses this list to check the Posture State on selected PSNs. If you do not choose any PSN, the connected PSN and any two backup servers are used as backups for posture state synchronization.
2. Configuration of a downloadable ACL(dACL) to block access to the Posture State Synchronization port on Cisco ISE when the client posture status is Compliant or Non Compliant. You need to add access control deny entry with the Posture State Synchronization port for every PSN at the top of ACLs used for Compliant endpoints to restrict access to the Posture State Synchronization port if the endpoint status is known, for example:
deny tcp any host PSN1-IP-ADDRESS eq 8449
deny tcp any host PSN2-IP-ADDRESS eq 8449
permit ip any anypermit ip any any is not mandatory, you can replace it with any set of rules according to your needs.

Note: If deny entry in dACL is not configured, the Posture Configuration Detection alarm is triggered on the Cisco ISE dashboard and Posture State Synchronization is disabled on the endpoint until Cisco Secure Client is restarted.
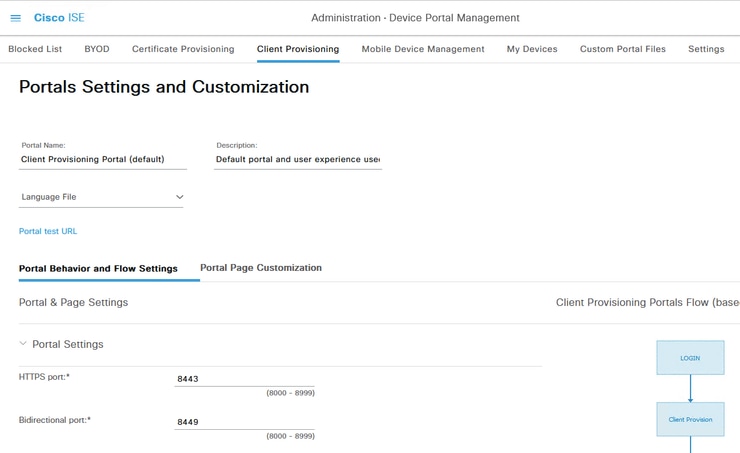
Posture State Synchronization port(Bidirectional port) can be changed on the Client Provisioning Portal configuration page. Navigate to Administration > Device Portal Management > Client Provisioning > Select desired portal > Portal Behavior and Flow Settings and open Portal Settings. The Posture State Synchronization port for the default Client Provisioning Portal cannot be changed.
Verify
From DART Bundle
Posture Status Synchronization can be verified from the Client side by looking into Cisco Secure Client Posture Module logs(AnyConnect_ISEPosture.txt) from DART Bundle:
1. Posture evaluation is finished, Posture status is Compliant.
2022/11/09 12:22:47 [Information] aciseagent Function: Authenticator::sendUIStatus Thread Id: 0xC60 File: authenticator.cpp Line: 1905 Level: debug MSG_SU_STEP_STATUS, {Status:4,Compliant:2,RemStatus:2,Phase:0,StepNumber:-1,Progress:-1,Attention:1,Cancellable:0,Restartable:0,ErrorMessage:0,Description1:"Compliant.",Description2:"Network access allowed."}. 2. Posture Status Synchronization probing is started.
2022/11/09 12:22:47 [Information] aciseagent Function: PeriodicProbe::ProcessMessage Thread Id: 0xC60 File: periodic_probe.cpp Line: 143 Level: info Session Sync Periodic Probing start.
2022/11/09 12:22:47 [Information] aciseagent Function: PeriodicProbe::sessionSyncProbe Thread Id: 0x296C File: periodic_probe.cpp Line: 335 Level: info Session sync periodic probing thread start. 3. HTTPS connection to ISE PSN on the Posture State Synchronization port(8449) is initiated.
2022/11/09 12:22:47 [Information] aciseagent Function: PeriodicProbe::sessionSyncProbe Thread Id: 0x296C File: periodic_probe.cpp Line: 357 Level: debug Sending http session sync periodic probe to [ISE-PSN-FQDN].
2022/11/09 12:22:47 [Information] aciseagent Function: HttpConnection::MakeRequest Thread Id: 0x296C File: httpconnection.cpp Line: 330 Level: debug Url=https://ISE-PSN-FQDN:8449/auth/StateSynch. 4. Timeout for Posture Status Synchronization probing.
2022/11/09 12:22:54 [Information] aciseagent Function: hs_transport_winhttp_post Thread Id: 0x296C File: hs_transport_winhttp.c Line: 5815 Level: debug unable to send request: 12002.
2022/11/09 12:22:54 [Information] aciseagent Function: hs_transport_post Thread Id: 0x296C File: hs_transport.c Line: 1425 Level: trace posting data failed.
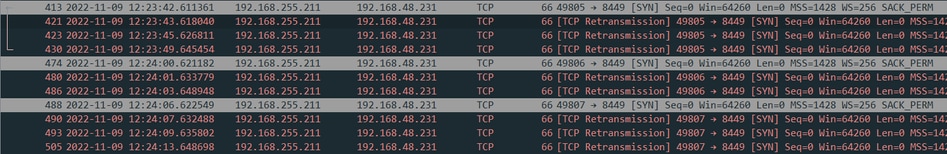
2022/11/09 12:22:54 [Information] aciseagent Function: PeriodicProbe::sessionSyncProbe Thread Id: 0x296C File: periodic_probe.cpp Line: 394 Level: debug HTTP Probe failed/timed-out, Retrying... From Packet Capture on the Client
Packet capture taken on the Client shows SYN packets sent towards the ISE PSN node on the Posture State Synchronization port(8449) without SYN-ACK response from ISE PSN:
From ISE
Correct Posture Status Synchronization configuration cannot be verified from the ISE side as the connection on the Posture State Synchronization port(8449) is supposed to fail.
Posture Restart on Posture Status Change
1) Session state information has been received from ISE with Posture Status "Unknown" while Cisco Secure Client is in a "Compliant" state.
2022/11/09 12:26:24 [Information] aciseagent Function: dump_http_headers Thread Id: 0x296C File: hs_httpheader.c Line: 430 Level: debug --- Http Response Headers ---.
2022/11/09 12:26:24 [Information] aciseagent Function: dump_http_headers Thread Id: 0x296C File: hs_httpheader.c Line: 437 Level: debug HTTP-Version: 1.1.
2022/11/09 12:26:24 [Information] aciseagent Function: dump_http_headers Thread Id: 0x296C File: hs_httpheader.c Line: 437 Level: debug Status-Code: 200.
2022/11/09 12:26:24 [Information] aciseagent Function: dump_http_headers Thread Id: 0x296C File: hs_httpheader.c Line: 437 Level: debug Connection: keep-alive.
2022/11/09 12:26:24 [Information] aciseagent Function: dump_http_headers Thread Id: 0x296C File: hs_httpheader.c Line: 437 Level: debug Date: Wed, 09 Nov 2022 11:26:24 GMT.
2022/11/09 12:26:24 [Information] aciseagent Function: dump_http_headers Thread Id: 0x296C File: hs_httpheader.c Line: 437 Level: debug Keep-Alive: timeout=20.
2022/11/09 12:26:24 [Information] aciseagent Function: dump_http_headers Thread Id: 0x296C File: hs_httpheader.c Line: 437 Level: debug Content-Length: 0.
2022/11/09 12:26:24 [Information] aciseagent Function: dump_http_headers Thread Id: 0x296C File: hs_httpheader.c Line: 437 Level: debug Server: server.
2022/11/09 12:26:24 [Information] aciseagent Function: dump_http_headers Thread Id: 0x296C File: hs_httpheader.c Line: 437 Level: debug X-Frame-Options: SAMEORIGIN.
2022/11/09 12:26:24 [Information] aciseagent Function: dump_http_headers Thread Id: 0x296C File: hs_httpheader.c Line: 437 Level: debug Strict-Transport-Security: max-age=31536000; includeSubDomains.
2022/11/09 12:26:24 [Information] aciseagent Function: dump_http_headers Thread Id: 0x296C File: hs_httpheader.c Line: 437 Level: debug X-Content-Type-Options: nosniff.
2022/11/09 12:26:24 [Information] aciseagent Function: dump_http_headers Thread Id: 0x296C File: hs_httpheader.c Line: 437 Level: debug Content-Security-Policy: default-src 'self'; script-src 'self' 'unsafe-inline' 'unsafe-eval'; style-src 'self' 'unsafe-inline'; img-src 'self' http://www.cisco.com/ data:;.
2022/11/09 12:26:24 [Information] aciseagent Function: dump_http_headers Thread Id: 0x296C File: hs_httpheader.c Line: 437 Level: debug X-XSS-Protection: 1; mode=block.
2022/11/09 12:26:24 [Information] aciseagent Function: dump_http_headers Thread Id: 0x296C File: hs_httpheader.c Line: 437 Level: debug Accept-CH: Sec-CH-UA-Arch, Sec-CH-UA-Full-Version, Sec-CH-UA-Mobile, Sec-CH-UA-Model, Sec-CH-UA-Platform-Version, Sec-CH-UA-Platform, Sec-CH-UA.
2022/11/09 12:26:24 [Information] aciseagent Function: dump_http_headers Thread Id: 0x296C File: hs_httpheader.c Line: 437 Level: debug X-ISE-POSTURE_STATUS: Unknown.
2022/11/09 12:26:24 [Information] aciseagent Function: dump_http_headers Thread Id: 0x296C File: hs_httpheader.c Line: 442 Level: debug --------------------.
2) Cisco Secure Client acknowledges the Posture status change and restarts the Posture Discovery:
2022/11/09 12:26:24 [Information] aciseagent Function: PeriodicProbe::sessionSyncProbe Thread Id: 0x296C File: periodic_probe.cpp Line: 379 Level: debug Different Session state on ISE = [ ISE-PSN-FQDN]. Restarting discovery.
2022/11/09 12:26:24 [Information] aciseagent Function: PeriodicProbe::sessionSyncProbe Thread Id: 0x296C File: periodic_probe.cpp Line: 387 Level: debug MSG_NS_SWIFT_RESTART_SEARCH, {manualRescan:0,stopPeriodicProbe:1}.
2022/11/09 12:26:24 [Information] aciseagent Function: SwiftHttpRunner::restartDiscovery Thread Id: 0xC60 File: swifthttprunner.cpp Line: 1431 Level: debug Restarting Discovery.
3) Cisco Secure Client stops Posture Status Synchronization until Posture assessment is performed:
2022/11/09 12:26:24 [Information] aciseagent Function: SwiftHttpRunner::processMessage Thread Id: 0xC60 File: swifthttprunner.cpp Line: 383 Level: debug Periodic Probes requested to be stopped.
2022/11/09 12:26:24 [Information] aciseagent Function: SwiftHttpRunner::restartDiscovery Thread Id: 0xC60 File: swifthttprunner.cpp Line: 1436 Level: debug MSG_PN_STOP_PERIODIC_PROBE sent.
2022/11/09 12:26:24 [Information] aciseagent Function: SwiftHttpRunner::restartDiscovery Thread Id: 0xC60 File: swifthttprunner.cpp Line: 1437 Level: debug MSG_PN_STOP_PERIODIC_PROBE, .
2022/11/09 12:26:24 [Information] aciseagent Function: hs_transport_free Thread Id: 0xC60 File: hs_transport.c Line: 606 Level: trace de-initialization done.
2022/11/09 12:26:24 [Information] aciseagent Function: PeriodicProbe::ProcessMessage Thread Id: 0xC60 File: periodic_probe.cpp Line: 210 Level: debug MSG_PN_STOP_PERIODIC_PROBE received..
2022/11/09 12:26:24 [Information] aciseagent Function: PeriodicProbe::ProcessMessage Thread Id: 0xC60 File: periodic_probe.cpp Line: 224 Level: debug Periodic Probing stopped.
2022/11/09 12:26:24 [Information] aciseagent Function: PeriodicProbe::sessionSyncProbe Thread Id: 0x296C File: periodic_probe.cpp Line: 411 Level: info Session sync periodic probing thread end.Troubleshoot
Posture Status Synchronization does not Start
If there is no indication of Posture Status Synchronization start in AnyConnect_ISEPosture.txt log file and the Client does not try to establish a connection with the ISE PSN node on Posture State Synchronization port(8449) check the Posture configuration file ISEPostureCFG.xml from DART bundle or directly on the Client machine: "%ProgramData%\Cisco\Cisco Secure Client\ISE Posture\" for a Windows PC.
The parameter responsible for Posture Status Synchronization is "StateSyncProbeInterval", it is supposed to be set with a value higher than 0:
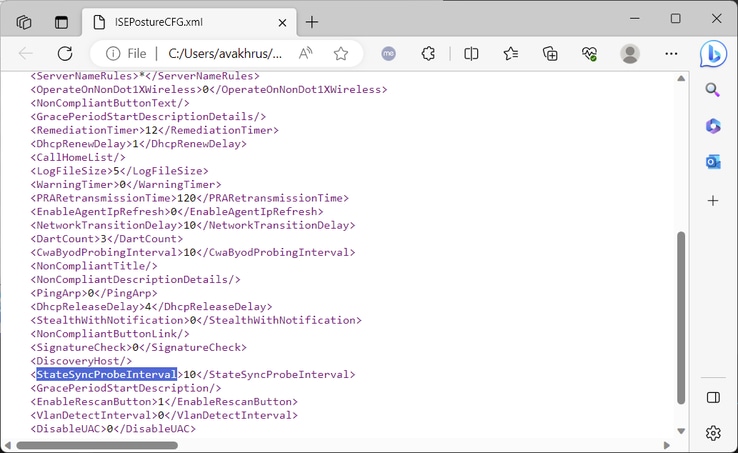
The absence of "StateSyncProbeInterval" or a value of "0" means that Posture Status Synchronization is disabled.
If "Posture State Synchronisation Interval" is set in Posture Profile on ISE but it is not reflected in a configuration file on the Client then Posture provisioning needs to be investigated.
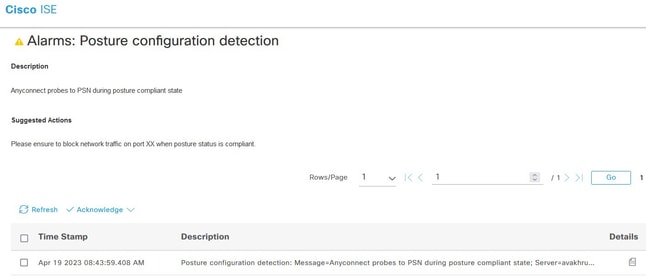
Posture Status Synchronization Fails with Alarm on ISE Dashboard
If Posture State Synchronisation fails with alarm on ISE, it means that Cisco Secure Client was able to reach ISE on the Posture State Synchronization port(8449) and requested a status for the session with "Compliant" status.
- Alarm in ISE GUI:
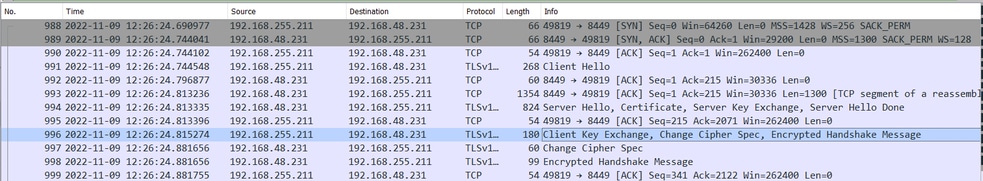
- Validate from packet capture
TCP connection on Posture State Synchronization port(8449) is established:
- Validate from the Cisco Secure Client Posture Module log
Check AnyConnect_ISEPosture.txt from DART bundle:
1) HTTPS connection to ISE PSN on the Posture State Synchronization port(8449) is initiated.
2022/11/09 12:26:34 [Information] aciseagent Function: PeriodicProbe::sessionSyncProbe Thread Id: 0x2750 File: periodic_probe.cpp Line: 357 Level: debug Sending http session sync periodic probe to [ISE-PSN-FQDN]. 2) Session state information has been received from ISE with Posture Status "Compliant".
2022/11/09 12:26:34 [Information] aciseagent Function: dump_http_headers Thread Id: 0x2750 File: hs_httpheader.c Line: 430 Level: debug --- Http Response Headers ---.
2022/11/09 12:26:34 [Information] aciseagent Function: dump_http_headers Thread Id: 0x2750 File: hs_httpheader.c Line: 437 Level: debug HTTP-Version: 1.1.
2022/11/09 12:26:34 [Information] aciseagent Function: dump_http_headers Thread Id: 0x2750 File: hs_httpheader.c Line: 437 Level: debug Status-Code: 200.
2022/11/09 12:26:34 [Information] aciseagent Function: dump_http_headers Thread Id: 0x2750 File: hs_httpheader.c Line: 437 Level: debug Connection: keep-alive.
2022/11/09 12:26:34 [Information] aciseagent Function: dump_http_headers Thread Id: 0x2750 File: hs_httpheader.c Line: 437 Level: debug Date: Wed, 09 Nov 2022 11:26:34 GMT.
2022/11/09 12:26:34 [Information] aciseagent Function: dump_http_headers Thread Id: 0x2750 File: hs_httpheader.c Line: 437 Level: debug Keep-Alive: timeout=20.
2022/11/09 12:26:34 [Information] aciseagent Function: dump_http_headers Thread Id: 0x2750 File: hs_httpheader.c Line: 437 Level: debug Content-Length: 0.
2022/11/09 12:26:34 [Information] aciseagent Function: dump_http_headers Thread Id: 0x2750 File: hs_httpheader.c Line: 437 Level: debug Server: server.
2022/11/09 12:26:34 [Information] aciseagent Function: dump_http_headers Thread Id: 0x2750 File: hs_httpheader.c Line: 437 Level: debug X-Frame-Options: SAMEORIGIN.
2022/11/09 12:26:34 [Information] aciseagent Function: dump_http_headers Thread Id: 0x2750 File: hs_httpheader.c Line: 437 Level: debug Strict-Transport-Security: max-age=31536000; includeSubDomains.
2022/11/09 12:26:34 [Information] aciseagent Function: dump_http_headers Thread Id: 0x2750 File: hs_httpheader.c Line: 437 Level: debug X-Content-Type-Options: nosniff.
2022/11/09 12:26:34 [Information] aciseagent Function: dump_http_headers Thread Id: 0x2750 File: hs_httpheader.c Line: 437 Level: debug Content-Security-Policy: default-src 'self'; script-src 'self' 'unsafe-inline' 'unsafe-eval'; style-src 'self' 'unsafe-inline'; img-src 'self' http://www.cisco.com/ data:;.
2022/11/09 12:26:34 [Information] aciseagent Function: dump_http_headers Thread Id: 0x2750 File: hs_httpheader.c Line: 437 Level: debug X-XSS-Protection: 1; mode=block.
2022/11/09 12:26:34 [Information] aciseagent Function: dump_http_headers Thread Id: 0x2750 File: hs_httpheader.c Line: 437 Level: debug Accept-CH: Sec-CH-UA-Arch, Sec-CH-UA-Full-Version, Sec-CH-UA-Mobile, Sec-CH-UA-Model, Sec-CH-UA-Platform-Version, Sec-CH-UA-Platform, Sec-CH-UA.
2022/11/09 12:26:34 [Information] aciseagent Function: dump_http_headers Thread Id: 0x2750 File: hs_httpheader.c Line: 437 Level: debug X-ISE-POSTURE_STATUS: Compliant.
2022/11/09 12:26:34 [Information] aciseagent Function: dump_http_headers Thread Id: 0x2750 File: hs_httpheader.c Line: 442 Level: debug --------------------. 3) Posture State Synchronisation stops due to detection of an incorrect configuration:
2022/11/09 12:26:34 [Error] aciseagent Function: PeriodicProbe::sessionSyncProbe Thread Id: 0x2750 File: periodic_probe.cpp Line: 370 Level: error Incorrect configuration detected by ISE = [ISE-PSN-FQDN], compliant status is not expected.
2022/11/09 12:26:34 [Information] aciseagent Function: PeriodicProbe::sessionSyncProbe Thread Id: 0x2750 File: periodic_probe.cpp Line: 371 Level: debug MSG_PN_STOP_PERIODIC_PROBE, .
2022/11/09 12:26:34 [Information] aciseagent Function: PeriodicProbe::ProcessMessage Thread Id: 0xC60 File: periodic_probe.cpp Line: 210 Level: debug MSG_PN_STOP_PERIODIC_PROBE received..
2022/11/09 12:26:34 [Information] aciseagent Function: PeriodicProbe::ProcessMessage Thread Id: 0xC60 File: periodic_probe.cpp Line: 224 Level: debug Periodic Probing stopped. Posture State Synchronisation cannot be restarted from the Cisco Secure Client GUI by restarting the Posture assessment or a network change. Instead, the Cisco Secure Client needs to be restarted in order for Posture State Synchronisation to work again.
Verify dACL Configured for Posture "Compliant" authorization profile
1. Validate proper dACL is configured for Posture "Compliant" authorization profile:
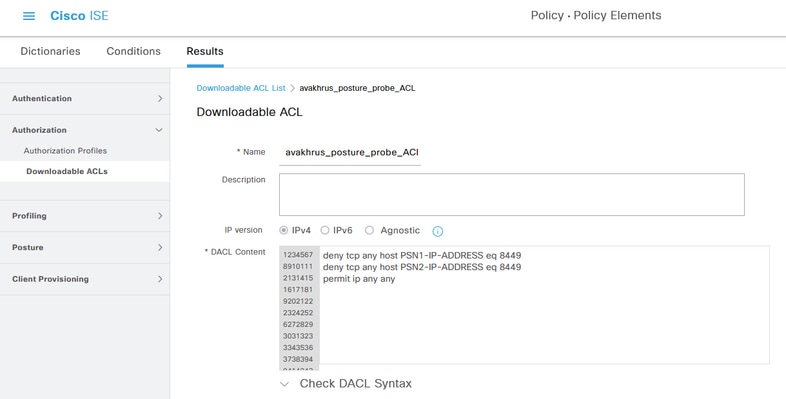
2. Validate detailed authentication report dACL was sent correctly as a result of authentication of the "Compliant" endpoint.
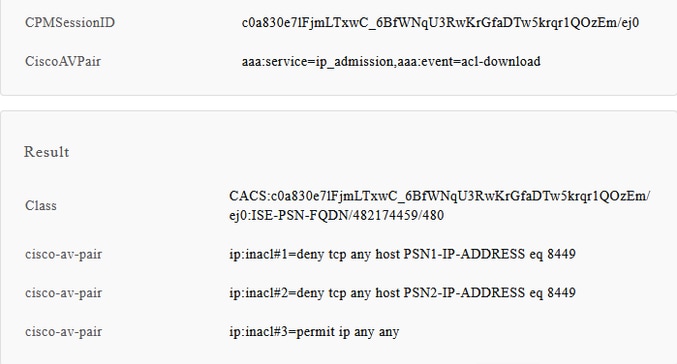
3. Validate that dACL is correctly applied on a network access device:
avakhrus_3560C#sh authe sess int fa0/12 det
Interface: FastEthernet0/12
MAC Address: 0050.56a8.be02
IPv6 Address: Unknown
IPv4 Address: 192.168.255.193
User-Name: TRAINING\bob
Status: Authorized
Domain: DATA
Oper host mode: multi-auth
Oper control dir: both
Session timeout: N/A
Restart timeout: N/A
Periodic Acct timeout: 172800s (local), Remaining: 92111s
Session Uptime: 1515s
Common Session ID: C0A8FF0C00000012679EAF14
Acct Session ID: 0x00000012
Handle: 0x5D000005
Current Policy: POLICY_Fa0/12
Local Policies:
Service Template: DEFAULT_LINKSEC_POLICY_SHOULD_SECURE (priority 150)
Server Policies:
ACS ACL: xACSACLx-IP-avakhrus_posture_probe_ACL-636b75ac
Method status list:
Method State
mab Stopped
dot1x Authc Success
avakhrus_3560C#sh access-lists | s xACSACLx-IP-avakhrus_posture_probe_ACL-636b75ac
Extended IP access list xACSACLx-IP-avakhrus_posture_probe_ACL-636b75ac (per-user)
1 deny tcp any host PSN1-IP-ADDRESS eq 8449
2 deny tcp any host PSN2-IP-ADDRESS eq 8449
3 permit ip any anyKnown Issues
Posture State Synchronisation Fails with Alarm on ISE
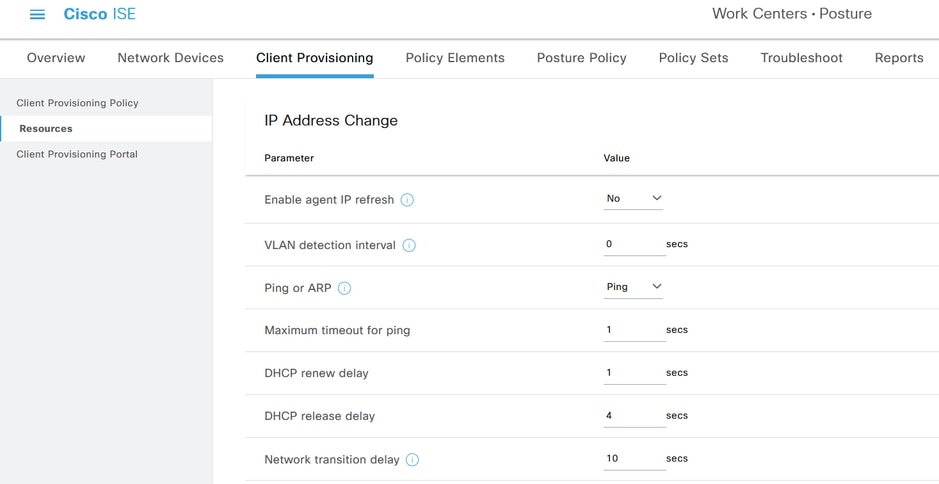
Posture State Synchronisation can fail with alarm on ISE even if proper dACL is applied on a network access device to the Client endpoint. It happens if Posture State Synchronisation Probe is performed faster than dACL is applied or if the Posture State Synchronisation Probe is already in progress when dACL is being applied. The issue was investigated in Cisco bug ID CSCwd58316  . As a workaround, you need to set "Network transition delay" to 10 seconds in the Anyconnect Posture profile(ISE Posture Agent Profile Settings).
. As a workaround, you need to set "Network transition delay" to 10 seconds in the Anyconnect Posture profile(ISE Posture Agent Profile Settings).
Revision History
| Revision | Publish Date | Comments |
|---|---|---|
1.0 |
18-Oct-2024 |
Initial Release |
Contributed by Cisco Engineers
- Alex VakhrushevTechnical Consulting Engineer
Contact Cisco
- Open a Support Case

- (Requires a Cisco Service Contract)
 Feedback
Feedback