Introduction
This document describes how to configure an SXP (Security Group Exchange Protocol) connection between ISE (Identity Services Engine) and an ASAv (virtual Adaptive Security Appliance).
SXP is the SGT (Security Group Tag) Exchange Protocol used by TrustSec to propagate IP to SGT mappings to TrustSec Devices. SXP was developed to allow networks including third party devices or legacy Cisco devices which do not support SGT inline tagging to have TrustSec capabilities. SXP is a peering protocol, one device will act as a Speaker and the other as a Listener. The SXP speaker is responsilbe for sending the IP-SGT bindings and the listener is responsible for collecting these bindings. The SXP connection uses TCP port 64999 as the underlying transport protocol and MD5 for message integrity/authenticity.
SXP has been published as an IETF Draft at the following link:
https://datatracker.ietf.org/doc/draft-smith-kandula-sxp/
Prerequisites
Requirements
TrustSec Compatibility Matrix:
http://www.cisco.com/c/en/us/solutions/enterprise-networks/trustsec/solution-overview-listing.html
Components Used
ISE 2.3
ASAv 9.8.1
ASDM 7.8.1.150
Network Diagram

IP Addresses
ISE: 14.36.143.223
ASAv: 14.36.143.30
Initial Configuration
ISE Network Device
Register ASA as a Network Device
WorkCenters > TrutSec > Components > Network Devices > Add



Generate Out Of Band (OOB) PAC (Protected Access Credential) and download



ASDM AAA server Configuration
Create AAA server group
Configuration > Firewall > Identity by TrustSec > Server Group Setup > Manage...

AAA Server Groups > Add

- AAA Server Group: <Group Name>
- Enable dynamic authorization
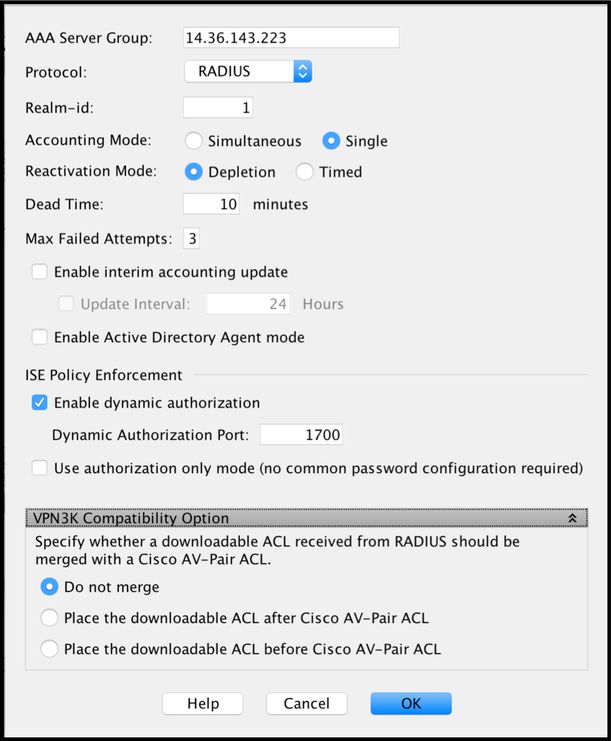
Add server to server group
Servers in the Selected Group > Add

- Server Name or IP Address: <ISE IP address>
- Server Authentication Port: 1812
- Server Accounting Port: 1813
- Server Secret Key: Cisc0123
- Common Password: Cisc0123

Import PAC downloaded from ISE
Configuration > Firewall > Identity by TrustSec > Server Group Setup > Import PAC...



Refresh Environment Data
Configuration > Firewall > Identity by TrustSec > Server Group Setup > Refresh Environment Data

Verification
ISE live logs
Operations > RADIUS > Live Logs





ISE Security Groups
Work Centers > TrustSec > Components > Security Groups

ASDM PAC
Monitoring > Properties > Identity by TrustSec > PAC

ASDM Environment Data and Security Groups
Monitoring > Properties > Identity by TrustSec > Environment Data

ASDM SXP Configuration
Enable SXP
Configuration > Firewall > Identity by TrustSec > Enable SGT Exchange Protocol (SXP)

Set Default SXP Source IP address and Default SXP password
Configuration > Firewall > Identity by TrustSec > Connection Peers

Add SXP Peer
Configuration > Firewall > Identity by TrustSec > Connection Peers > Add

- Peer IP Address: <ISE IP Address>

ISE SXP Configuration
Global SXP password setting
WorkCenters > TrustSec > Settings > SXP Settings
- Global Password: Cisc0123

Add SXP Device
WorkCenters > TrustSec > SXP > SXP Devices > Add

SXP Verification
ISE SXP verification
WorkCenters > TrustSec > SXP > SXP Devices

ISE SXP Mappings
WorkCenters > TrustSec > SXP > All SXP Mappings

ASDM SXP verification
Monitoring > Properties > Identity by TrustSec > SXP Connections

ASDM learned SXP IP to SGT Mappings
Monitoring > Properties > Identity by TrustSec > IP Mappings

Packet Capture Taken on ISE






































 Feedback
Feedback