Introduction
This document describes ways to install ISE patches and FAQs during installation.
Prerequisites
Requirements
Basic knowledge of the Identity Service Engine (ISE).
Components Used
The information in this document is based on these software and hardware versions:
- Cisco Identity Service Engine 2.X
The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, ensure that you understand the potential impact of any command.
Background Information
Cisco releases ISE patches on a semi-regular basis. These patches contain bug fixes and, when necessary, security fixes (for example, the Heartbleed and Poodle vulnerabilities discovered with SSL). This ensures that bug fixes are applied, security vulnerabilities are plugged in, and the solution works seamlessly.
When you install a patch on an ISE node, the node is rebooted. Restart the services after the installation is complete. Wait several minutes before you can log in again.
You can schedule patch installations during a maintenance window to avoid a temporary outage.
Install only patches that are applicable for the Cisco version deployed in your network. Cisco reports any mismatch in versions as well as any errors in the patch file.
You cannot install a patch of a lower version than the patch that is currently installed on Cisco. Similarly, you cannot roll back changes of a lower-version patch if a higher version is currently installed on Cisco.
When you install a patch from the Primary Administration Node (PAN) that is part of a distributed deployment, Cisco ISE installs the patch on the primary node and then on all the secondary nodes in the deployment. If the patch installation is successful on the PAN, Cisco ISE then continues patch installation on the secondary nodes. If it fails on the PAN, the installation does not proceed to the secondary nodes. However, if the installation fails on any of the secondary nodes for any reason, it still continues with the next secondary node in your deployment.
When you install a patch from the PAN that is part of a two-node deployment, Cisco installs the patch on the primary node and then on the secondary node.
If the patch installation is successful on the PAN, Cisco then continues patch installation on the secondary node. If it fails on the PAN, the installation does not proceed to the secondary node.
You must have the Super Admin or System Admin administrator role to install or roll back the patches. Collect configuration backup and operational backup before the patch installation starts.
Patch Installation With GUI
To download the ISE Patches from Cisco.com, Navigate to Downloads > Products > Security > Access Control and Policy > Identity Services Engine > Identity Services Engine Software(here).
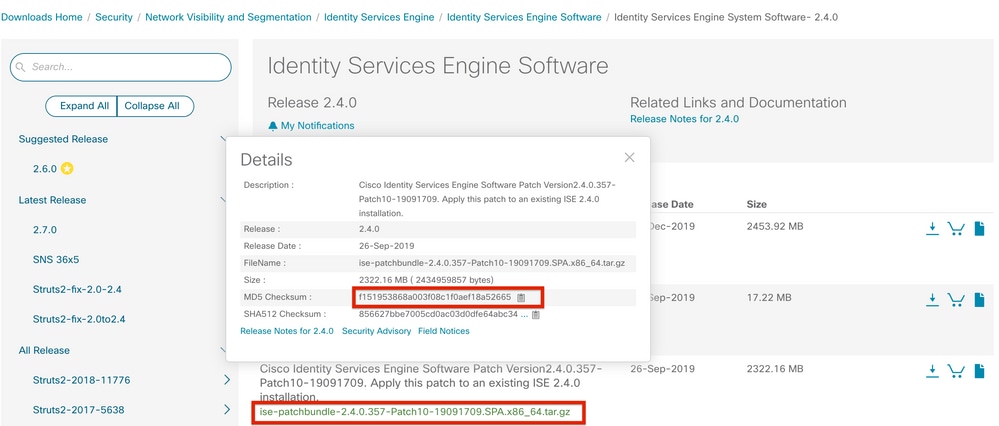
Note: Cisco ISE patches are normally cumulative, which means that patch 11 installation includes all of the patches from patch 1 to patch 10. Patch installation requires a reboot of the ISE server.
Note: Verify MD5/SHA512 Checksum after the Patch file download.
In order to apply the patch on ISE, log in to ISE Primary Administration Node (PAN) GUI and execute these instructions:
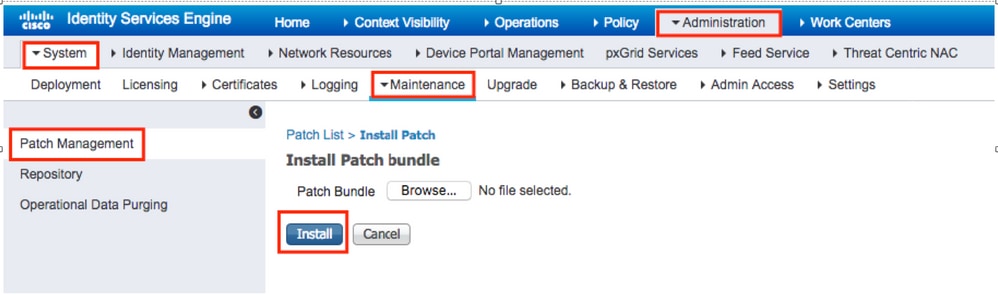
Step 1. Navigate to Administration > System > Maintenance > Patch Management > Install.
Step 2. Click Browse and choose the patch file that was downloaded from Cisco.com.
Step 3. Click Install to install the Patch.
Patch Installation With CLI
Step 1. Configure an ISE repository and place the required ISE patch in the repository. To configure the ISE repository refer How to Configure Repository on ISE
Step 2. Log in to ISE CLI with SSH.
Step 3. Ensure the ISE CLI can list the repository content.
ISE/admin# show repository FTP_repository
ise-patchbundle-10.2.0.7-Patch6-19021923.SPA.x86_64.tar.gz
ise-patchbundle-10.2.0.7-Patch9-19062923.SPA.x86_64.tar.gz
ise-patchbundle-10.1.0.0-Ptach3-19110111.SPA.x86_64.tar.gz
Step 4. In order to install patch on a specific ISE node from the CLI, run the patch install command in EXEC mode.
Patch install <patch_file_name> <FTP_repository>
Log in to the CLI of the ISE node via SSH and run these commands:
ISE/admin#patch install ise-patchbundle-10.1.0.0-Ptach3-19110111.SPA.x86_64.tar.gz FTP_repository
% Warning: Patch installs only on this node. Install with Primary Administration node GUI to install on all nodes in deployment. Continue? (yes/no) [yes] ? yes
Save the current ADE-OS run configuration? (yes/no) [yes] ? yes
Generating configuration...
Saved the ADE-OS run Configuration to startup successfully
Initiating Application Patch installation...
Getting bundle to local machine...
Unbundling Application Package...
Verifying Application Signature...
patch successfully installed
% This application Install or Upgrade requires reboot, rebooting now...
Broadcast message from root@ISE (pts/1) (Fri Feb 14 01:06:21 2020):
Trying to stop processes gracefully. Reload lasts approximately 3 mins
Broadcast message from root@ISE (pts/1) (Fri Feb 14 01:06:21 2020):
Trying to stop processes gracefully. Reload takes approximately 3 mins
Broadcast message from root@ISE (pts/1) (Fri Feb 14 01:06:41 2020):
The system is going down for reboot NOW
Broadcast message from root@ISE (pts/1) (Fri Feb 14 01:06:41 2020):
The system is going down for reboot NOW
How to Install the Patch on all the ISE Nodes in the Deployment
When you install a patch from the PAN that is part of a distributed deployment, Cisco ISE installs the patch on the primary node and then all the secondary nodes in the deployment. If the patch installation is successful on the Primary PAN, Cisco ISE then continues patch installation on the secondary nodes. If it fails on the PAN, the installation does not proceed to the secondary nodes.
However, if the installation fails on any of the secondary nodes for any reason, it still continues with the next secondary node in your deployment.
How to Roll Back the Patch on all the ISE Nodes in the Deployment
To roll back a patch from Cisco ISE nodes in a deployment, you must first roll back the change from the PAN. If this is successful, the patch is then rolled back from the secondary nodes. If the rollback process fails on the PAN, the patches are not rolled back from the secondary nodes. However, if the patch rollback fails on any secondary node, it still continues to roll back the patch from the next secondary node in your deployment.
While Cisco ISE rolls back the patch from the secondary nodes, you can continue to perform other tasks from the PAN GUI. The secondary nodes restart after the rollback.
To roll back the ISE patches, log in to ISE GUI and navigate to Administration > System > Maintenance > Patch Management and select the required patch and click Rollback,as shown:

How to Rollback the Patch from the ISE CLI
Step 1. SSH to the ISE node in which you would like to remove the patch.
Step 2. Verify the installed patches on the ISE node with the command Show Version
ISE/admin# show version
Cisco Application Deployment Engine OS Release: 3.0
ADE-OS Build Version: 3.0.5.144
ADE-OS System Architecture: x86_64
Copyright (c) 2005-2019 by Cisco Systems, Inc.
All rights reserved.
Hostname: ISE
Version information of installed applications
---------------------------------------------
Cisco Identity Services Engine
---------------------------------------------
Version : 10.1.0.0
Build Date : Tue Feb 12 00:45:06 2019
Install Date : Mon Sep 30 12:17:29 2019
Cisco Identity Services Engine Patch
---------------------------------------------
Version : 1
Install Date : Tue Oct 01 01:30:12 2019
Cisco Identity Services Engine Patch
---------------------------------------------
Version : 3
Install Date : Tue Mar 24 05:35:19 2020
Step 3. Run the command patch remove <application name> <patch file number to be removed>
For example:- patch remove ise 2
ISE/admin# patch remove ise 3
Continue with application patch uninstall? [y/n] y
% Warning: Patch is removed only from this node. Remove patch with Primary Administration node GUI to remove from all nodes in deployment.
Patch successfully uninstalled
% This application Install or Upgrade requires reboot, rebooting now...
Broadcast message from root@ISE (pts/1) (Sun Mar 8 03:16:29 2020):
Trying to stop processes gracefully. Reload takes approximately 3 mins
Broadcast message from root@ISE (pts/1) (Sun Mar 8 03:16:29 2020):
Trying to stop processes gracefully. Reload takes approximately 3 mins
Broadcast message from root@ISE (pts/1) (Sun Mar 8 03:17:41 2020):
The system is going down for reboot NOW
Broadcast message from root@ISE (pts/1) (Sun Mar 8 03:17:41 2020):
The system is going down for reboot NOW
Note: ISE Patches are cumulative in nature and cannot be rolled back while a newer version exists. The newer version requires to roll back first.
To uninstall the previous patch, uninstall the latest patch first and then the previous patch version.
ISE/admin#patch remove ise 1
Continue with application patch uninstall? [y/n] y
% Warning: Patch is removed only from this node. Remove patch with Primary Administration node GUI to remove from all nodes in deployment.
Continue? (yes/no) [yes] ? yes
% Patch cannot be rolled back while a newer version exists, which needs to rolled back first.
Verify
In order to view the ISE patch installation progress, navigate to Administration > System > Maintenance > Patch Management > Show Node Status as shown in the image:
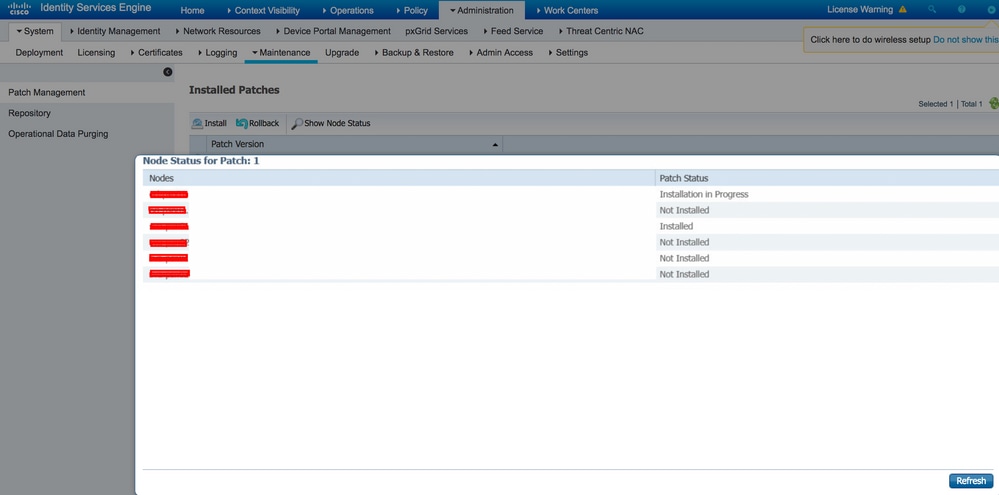
Verify patch installation status from ISE node. Log to the same ISE server and run the command Show Version
ISE1/admin# show version
Cisco Application Deployment Engine OS Release: 3.0
ADE-OS Build Version: 3.0.5.144
ADE-OS System Architecture: x86_64
Copyright (c) 2005-2019 by Cisco Systems, Inc.
All rights reserved.
Hostname: ISE1
Version information of installed applications
---------------------------------------------
Cisco Identity Services Engine
---------------------------------------------
Version : 10.1.0.0
Build Date : Tue Feb 12 06:15:06 2019
Install Date : Thu Nov 21 16:39:02 2019
Cisco Identity Services Engine Patch
---------------------------------------------
Version : 1
Install Date : Thu Apr 02 11:00:08 2020
ISE1/admin#
Verify successful and failed patch messages in ISE alarms:

Successful Patch Installation Log Reference
isea/admin# sh logging system ade/ADE.log tail
2020-04-19T15:38:01.634794+05:30 isea ADEOSJAVAAPI[26999]: ADEAUDIT 2030, type=PATCH INSTALL, name=PATCH INSTALL STARTED, username=kopriadm, cause=Application patch install has been inititated, adminipaddress=10.65.80.116, interface=GUI,
detail=Patch Install initiated with bundle - ise-patchbundle-10.1.0.0-Patch3-19110111.SPA.x86_64.tar.gz, repo - tmplocalpatchinstallrepo
2020-04-19T15:38:01.635194+05:30 isea ADE-SERVICE[1158]: [26999]:[info] application:install cars_install.c[796] [test]: Install initiated with bundle - ise-patchbundle-10.1.0.0-Patch3-19110111.SPA.x86_64.tar.gz, repo - tmplocalpatchinsta
llrepo
2020-04-19T15:38:01.784100+05:30 isea ADE-SERVICE[1158]: [26999]:[info] application:install cars_install.c[913] [test]: Stage area - /storeddata/Install/.1587290881
2020-04-19T15:38:01.827925+05:30 isea ADE-SERVICE[1158]: [26999]:[info] application:install cars_install.c[918] [test]: Getting bundle to local machine
2020-04-19T15:38:01.829562+05:30 isea ADE-SERVICE[1158]: [26999]:[error] config:repository: rm_repos_cfg.c[552] [test]: server not found in url
2020-04-19T15:38:01.830656+05:30 isea ADE-SERVICE[1158]: [26999]:[info] transfer: cars_xfer.c[66] [test]: local copy in of ise-patchbundle-10.1.0.0-Patch3-19110111.SPA.x86_64.tar.gz requested
2020-04-19T15:38:02.873630+05:30 isea ADE-SERVICE[1158]: [26999]:[info] transfer: cars_xfer_util.c[2293] [test]: Properties file /tmp/.cars_repodownload.props exists need to cleanup after a SIGNAL or download complete
2020-04-19T15:38:03.247065+05:30 isea ADE-SERVICE[1158]: [26999]:[info] application:install cars_install.c[954] [test]: Got bundle at - /storeddata/Install/.1587290881/ise-patchbundle-10.1.0.0-Patch3-19110111.SPA.x86_64.tar.gz
2020-04-19T15:38:03.247424+05:30 isea ADE-SERVICE[1158]: [26999]:[info] application:install cars_install.c[1002] [test]: Unbundling package ise-patchbundle-10.1.0.0-Patch3-19110111.SPA.x86_64.tar.gz
2020-04-19T15:38:09.066295+05:30 isea ADE-SERVICE[1158]: [26999]:[info] application:install cars_install.c[1064] [test]: Verifying signature for package ise-patchbundle-10.1.0.0-Patch3-19110111.SPA.x86_64.tar.gz
2020-04-19T15:38:13.171615+05:30 isea ADE-SERVICE[1158]: [26999]:[info] application:install cars_install.c[1073] [test]: Signed bundle /storeddata/Install/.1587290881/ise-patchbundle-10.1.0.0-Patch3-19110111.SPA.x86_64.tar.gz confirme
d with release key
2020-04-19T15:38:18.816986+05:30 isea ADE-SERVICE[1158]: [26999]:[info] application:install cars_install.c[1166] [test]: Unbundling done. Verifying input parameters...
2020-04-19T15:38:18.877267+05:30 isea ADE-SERVICE[1158]: [26999]:[info] application:install cars_install.c[1195] [test]: Manifest file is at - /storeddata/Install/.1587290881/manifest.xml
2020-04-19T15:38:18.877604+05:30 isea ADE-SERVICE[1158]: [26999]:[info] application:install cars_install.c[1234] [test]: Manifest file appname - ise
2020-04-19T15:38:18.878051+05:30 isea ADE-SERVICE[1158]: [26999]:[info] application:install cars_install.c[1286] [test]: Patch bundle contains patch(3) for app version(10.1.0.0)
2020-04-19T15:38:18.878254+05:30 isea ADE-SERVICE[1158]: [26999]:[info] application:install ci_util.c[305] [test]: Comparing installed app version:(10.1.0.0) and version of app the patch is meant for:(10.1.0.0)
2020-04-19T15:38:18.878517+05:30 isea ADE-SERVICE[1158]: [26999]:[info] application:install cars_install.c[1321] [test]: Manifest file pkgtype - CARS
2020-04-19T15:38:18.878712+05:30 isea ADE-SERVICE[1158]: [26999]:[info] application:install cars_install.c[1735] [test]: Verifying zip...
2020-04-19T15:38:27.006433+05:30 isea ADE-SERVICE[1158]: [26999]:[info] application:install cars_install.c[1796] [test]: Executing patch install script patchinstall.sh from patch.zip
2020-04-19T15:38:27.209692+05:30 isea test: info:[patchinstall.sh] START PATCH INSTALL SCRIPT. PATCHDIR: /storeddata/Install/.1587290881 INSTALLDIRS:
2020-04-19T15:38:27.211274+05:30 isea test: info:[patchinstall.sh] NEW PATCH VER: 3 PRIOR PATCH VER: 0
2020-04-19T15:38:27.213166+05:30 isea test: info:[patchinstall.sh] IRF-RABBITMQ-RUNTIME and IRF-CORE-ENGINE-RUNTIME Remove Begin
2020-04-19T15:38:27.214840+05:30 isea test: info:[patchinstall.sh] Remove IRF-Rabbitmq container
2020-04-19T15:38:27.753502+05:30 isea test: info:[patchinstall.sh] IRF-Rabbitmq container id -
2020-04-19T15:38:27.755172+05:30 isea test: info:[patchinstall.sh] No IRF-Rabbitmq container exist to remove.\n
2020-04-19T15:38:27.756631+05:30 isea test: info:[patchinstall.sh] Remove IRF-Core-Engine container
2020-04-19T15:38:27.781127+05:30 isea test: info:[patchinstall.sh] IRF-Core-Engine container id -
2020-04-19T15:38:27.783028+05:30 isea test: info:[patchinstall.sh] No IRF-Core-Engine container exist to remove.\n
2020-04-19T15:38:27.784724+05:30 isea test: info:[patchinstall.sh] IRF-RABBITMQ-RUNTIME and IRF-CORE-ENGINE-RUNTIME Remove Completed
2020-04-19T15:38:33.077501+05:30 isea test: info:[application:operation:cpmcontrol.sh] In Stop Monit
2020-04-19T15:38:33.197734+05:30 isea test: Monit daemon with pid [12796] killed
2020-04-19T15:38:34.289656+05:30 isea test: info:[application:operation:cpmcontrol.sh] Done Stop Monit
2020-04-19T15:38:34.671998+05:30 isea ADEOSShell[28278]: ADEAUDIT 2062, type=USER, name=M&T Log Processor, username=system, cause=M&T Log Processor Stopped, adminipaddress=127.0.0.1, interface=CLI, detail=Stopping M&T Log Processor
2020-04-19T15:38:43.621160+05:30 isea test: info:[application:operation:adprobe.sh] adprobe:Stopping wmi probe...
2020-04-19T15:38:43.657769+05:30 isea test: info:[application:operation:adprobe.sh] adprobe:wmi probe is disabled
2020-04-19T15:38:43.989085+05:30 isea test: info:[application:operation:syslogprobe.sh] syslogprobe:Stopping syslog probe...
2020-04-19T15:38:44.019674+05:30 isea test: info:[application:operation:syslogprobe.sh] syslogprobe:syslog probe is disabled
2020-04-19T15:38:44.367442+05:30 isea test: info:[application:operation:restprobe.sh] restprobe:Stopping rest probe...
2020-04-19T15:38:44.400103+05:30 isea test: info:[application:operation:restprobe.sh] restprobe:rest probe is disabled
2020-04-19T15:38:44.713844+05:30 isea test: info:[application:operation:agentprobe.sh] agentprobe:Stopping agent probe...
2020-04-19T15:38:44.753547+05:30 isea test: info:[application:operation:agentprobe.sh] agentprobe:agent probe is disabled
2020-04-19T15:38:46.166418+05:30 isea test: info:[application:operation:appservercontrol.sh] Stopping ISE Application Server...
2020-04-19T15:38:46.168374+05:30 isea ADEOSShell[29231]: ADEAUDIT 2062, type=USER, name=Application server status, username=system, cause=Application server stopped, adminipaddress=127.0.0.1, interface=CLI, detail=Application server stopped
2020-04-19T15:41:37.224949+05:30 isea test: info:[patchinstall.sh] ISE 10.1.0.0 patch 3 installFileSystem() INVOKED
2020-04-19T15:41:37.245321+05:30 isea test: info:[patchinstall.sh] Updating patched file: /storeddata/Install/.1587290881/filesystem/opt/CSCOcpm/mnt/xde/xdeRuntime/packages/std/WorkflowsProject.xar
2020-04-19T15:41:37.251672+05:30 isea test: info:[patchinstall.sh] Updating patched file: /storeddata/Install/.1587290881/filesystem/opt/CSCOcpm/mnt/bin/ctl/radius_auth.ctl
2020-04-19T15:41:37.258874+05:30 isea test: info:[patchinstall.sh] Updating patched file: /storeddata/Install/.1587290881/filesystem/opt/CSCOcpm/mnt/report-definitionsV2/Audit/Internal-Administrator-Summary.xml
2020-04-19T15:41:37.265939+05:30 isea test: info:[patchinstall.sh] Updating patched file: /storeddata/Install/.1587290881/filesystem/opt/CSCOcpm/mnt/report-definitionsV2/Endpoints and Users/Posture-Assessment-by-Endpoint.xml
2020-04-19T15:41:37.273866+05:30 isea test: info:[patchinstall.sh] Updating patched file: /storeddata/Install/.1587290881/filesystem/opt/CSCOcpm/mnt/report-definitionsV2/Endpoints and Users/Posture-Assessment-by-Condition.xml
2020-04-19T15:41:37.280143+05:30 isea test: info:[patchinstall.sh] Updating patched file: /storeddata/Install/.1587290881/filesystem/opt/CSCOcpm/mnt/lib/mnt-collection.jar
2020-04-19T15:41:37.288008+05:30 isea test: info:[patchinstall.sh] Updating patched file: /storeddata/Install/.1587290881/filesystem/opt/CSCOcpm/mnt/lib/libJniCollector.so
2020-04-19T15:41:37.295128+05:30 isea test: info:[patchinstall.sh] Updating patched file: /storeddata/Install/.1587290881/filesystem/opt/CSCOcpm/appsrv/apache-tomcat-ca-8.5.32/apr/lib/libapr-1.a
2020-04-19T15:41:37.302031+05:30 isea test: info:[patchinstall.sh] Updating patched file: /storeddata/Install/.1587290881/filesystem/opt/CSCOcpm/appsrv/apache-tomcat-ca-8.5.32/apr/lib/libtcnative-1.a
2020-04-19T15:41:37.308615+05:30 isea test: info:[patchinstall.sh] Updating patched file: /storeddata/Install/.1587290881/filesystem/opt/CSCOcpm/appsrv/apache-tomcat-ca-8.5.32/webapps/ocsp-responder-webapp/WEB-INF/lib/import-export-2.6
.0-156.jar
Broadcast message from root@isea (Sun Apr 19 15:50:40 2020):
Trying to stop processes gracefully. Reload takes approximately 3 mins
Broadcast message from root@isea (Sun Apr 19 15:51:01 2020):
The system is going down for reboot NOW
Session terminated, killing shell... ...killed.






 Feedback
Feedback