Introduction
This document describes how to troubleshoot common guest issues in deployment, how to isolate and check the issue, and simple workarounds to try.
Prerequisite
Requirements
Cisco recommends that you have knowledge of these topics:
- ISE guest configuration
- CoA configuration on Network Access Devices(NAD)
- Capture tools on workstations are required.
Components Used
The information in this document is based on Cisco ISE, Release 2.6, and:
- WLC 5500
- Catalyst switch 3850 15.x version
- Windows 10 workstation
The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, ensure that you understand the potential impact of any command.
Guest Flow
The guest flow overview is similar to wired or wireless setups. This image of the flow diagram can be used for reference throughout the document. It helps to visualize the step and the entity.
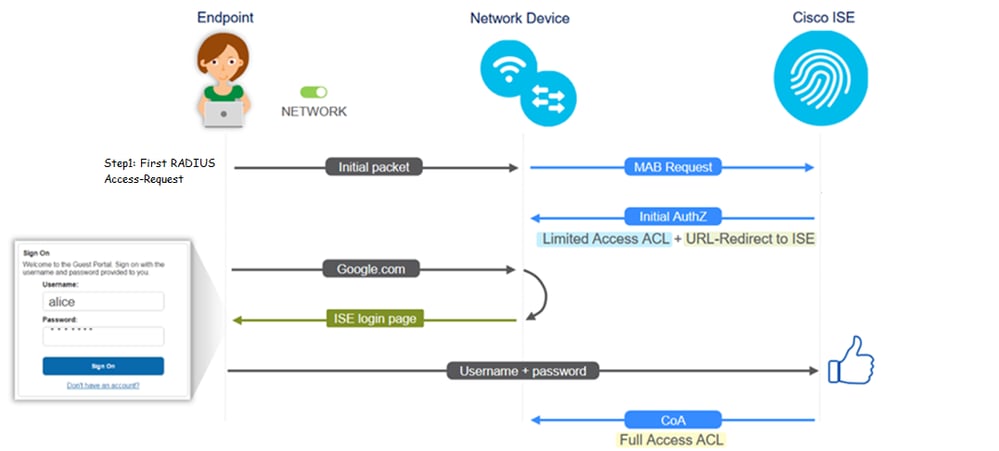
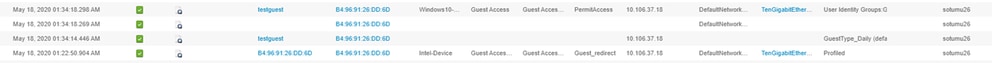
The flow can also be followed on ISE live logs [Operations > RADIUS Live Logs] by filtering the endpoint ID:
- MAB Authentication successful– username field has the MAC address- URL is pushed to the NAD - User gets the portal
- Guest Authentication successful- username field has the guest username, it has been identified as GuestType_Daily (or the configured type for the guest user)
- CoA initiated- username field is blank, detailed report shows Dynamic Authorization successful
- Guest Access provided
The sequence of events in the image (bottom to top):
Common Deployment Guides
Here are some links for configuration assistance. For any specific use case troubleshooting, it helps to be aware of the ideal or expected configuration.
Frequently Encountered Issues
This document primarily addresses these issues:
Redirection to the Guest Portal Does Not Work
Once the redirect URL and ACL are pushed from ISE, check these:
1. The client status on the switch (if wired guest access) with the command show authentication session int <interface> details:

2. The client status on the Wireless LAN Controller (if wireless guest access): Monitor > Client > MAC address

3. The reachability from the endpoint to the ISE on TCP port 8443 with the help of command prompt: C:\Users\user>telnet <ISE-IP> 8443.
4. If the portal redirect URL has an FQDN, check if the client is able to resolve from the command prompt: C:\Users\user>nslookup guest.ise.com.
5. In flex connect setup, ensure the same ACL name is configured under ACL and flex ACLs. Also, verify if the ACL is mapped to the APs. Refer to the config guide from the previous section-Steps 7 b and c for more information.

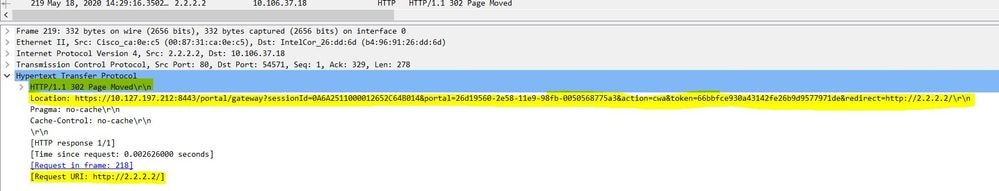
6. Take a packet capture from the client, and check for the redirection. The packet HTTP/1.1 302 Page Moved is to indicate the WLC/Switch redirected the accessed site to the ISE guest portal (redirected URL):

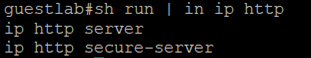
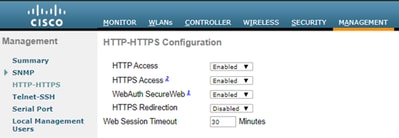
7. HTTP(s) engine is enabled on the Network Access Devices:
8. If the WLC is in a foreign-anchor setup, check these:
Step 1. The client status must be the same on both the WLCs.
Step 2. Redirect URL must be seen on both the WLCs.
Step 3. RADIUS Accounting must be disabled on the anchor WLC.

Dynamic Authorization Fails
If the end-user is able to access the guest portal and log in successfully, the next step would be a change of authorization to give full guest access to the user. If this does not work, you see a Dynamic Authorization failure on ISE Radius Live Logs. To remedy the issue, check these:
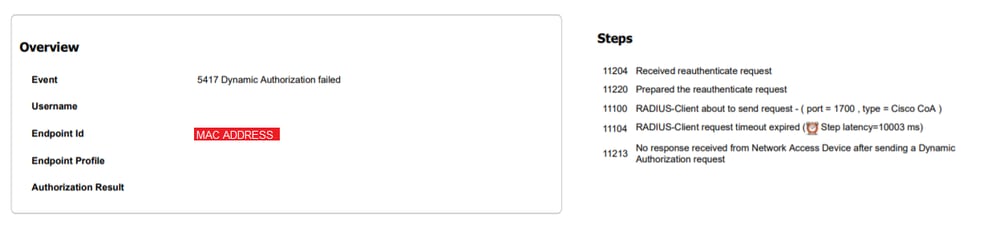
1. Change of Authorization (CoA) must be enabled/configured on the NAD:
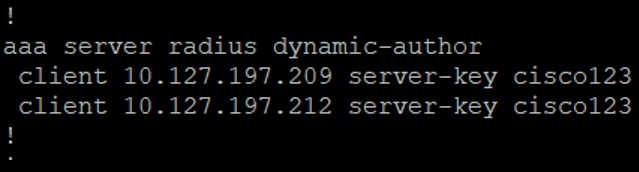
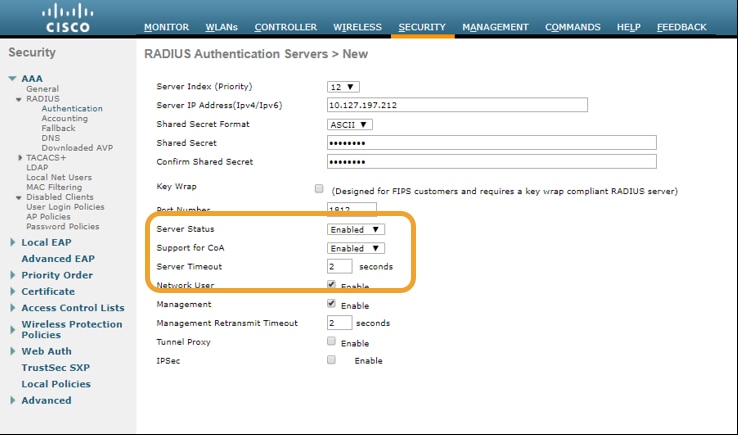
2. UDP Port 1700 must be allowed on the firewall.
3. NAC state on WLC is incorrect. Under Advanced settings on WLC GUI > WLAN, change the NAC state to ISE NAC.

SMS/EMAIL Notifications Are Not Sent
1. Check the SMTP configuration under Administration > System > Settings > SMTP.
2. Check the API for SMS/Email gateways outside ISE:
Test the URL(s) provided by the vendor on an API client or a browser, replace the variables like usernames, passwords, mobile number, and test the reachability [Administration > System > Settings > SMS Gateways].

Alternatively, if you test from the ISE sponsor groups [Workcentres > Guest Access > Portals and Components > Guest Types], take a packet capture on ISE and the SMS/SMTP gateway to check if:
- The request packet reaches the server untampered.
- ISE server has the vendor recommended permissions/privilege for the gateway to process this request.

Manage the Accounts Page is Not Reachable
1. The Workcentres > Guest Access > Manage accounts button redirects to the ISE FQDN on port 9002 for the ISE admin to access the sponsor portal:
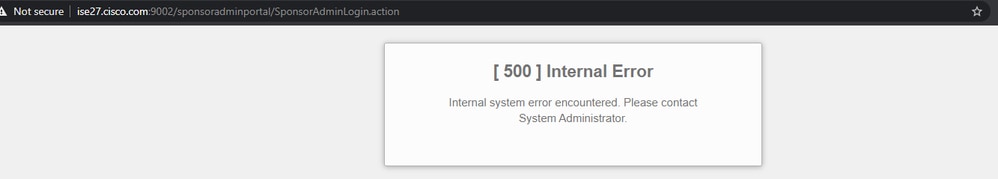
2. Check if the FQDN is resolved by the workstation from which Sponsor Portal is accessed with the command nslookup <FQDN of ISE PAN>.
3. Check if ISE TCP port 9002 is open from the CLI of the ISE with the command show ports | include 9002.
Portal Certificate Best Practices
- For a seamless user experience, the certificate used for portals and admin roles must be signed by a well-known public Certificate Authority (example: GoDaddy, DigiCert, VeriSign, etc), commonly trusted by browsers (example: Google Chrome, Firefox, and so on).
- It is not recommended to use a static IP for guest redirection, since that makes the private IP of ISE visible to all users. Most of the vendors do not provide third party-signed certificates for private IPs.
- When you move from ISE 2.4 p6 to p8 or p9, there is a known bug: Cisco bug ID CSCvp75207, where the Trust for authentication within ISE and Trust for client authentication and Syslog boxes must be manually checked after the patch upgrade. This ensures that ISE sends out the full cert chain for the TLS flow when the guest portal is accessed.
If these actions do not resolve guest access problems, please reach out to TAC with a support bundle collected with instructions from the document: Debugs to enable on ISE.
Related Information


















 Feedback
Feedback