Understand Wifi Analytics for Endpoint Classification on ISE 3.3
Available Languages
Download Options
Bias-Free Language
The documentation set for this product strives to use bias-free language. For the purposes of this documentation set, bias-free is defined as language that does not imply discrimination based on age, disability, gender, racial identity, ethnic identity, sexual orientation, socioeconomic status, and intersectionality. Exceptions may be present in the documentation due to language that is hardcoded in the user interfaces of the product software, language used based on RFP documentation, or language that is used by a referenced third-party product. Learn more about how Cisco is using Inclusive Language.
Contents
Introduction
This document describes how WiFi Analytics for Endpoint Classification works. It also describes how to configure, verify, and troubleshoot it.
Prerequisites
Requirements
Cisco recommends that you have knowledge of these topics:
- 9800 Wireless LAN Controllers (WLC) configuration
- Identity Services Engine (ISE) configuration
- RADIUS Authentication. Authorization and Accounting (AAA) packet flow and terminology
This document assumes that there is already a working WLAN authenticating clients using ISE as RADIUS server.
For this feature to work, it is required to have at least:
- 9800 WLC Cisco IOS® XE Dublin 17.10.1
- Identify Services Engine v3.3.
- 802.11ac Wave2 or 802.11ax (Wi-Fi 6/6E) access points
Components Used
The information in this document is based on these software and hardware versions:
- 9800 WLC Cisco IOSXE v17.12.x
- Identity Services Engine (ISE) v3.3
- Android 13 Device
The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, ensure that you understand the potential impact of any command.
Background information
Through WiFi Device Analytics, Cisco 9800 WLC can learn attributes, such as model number and OS version from a set of endpoints connected to this device, and share it with ISE. ISE then can use this information for Endpoint Classification, also known as Profiling, purposes.
Currently, WiFi Analytics is supported for these vendors:
- Apple
- Intel
- Samsung
The WLC shares the attribute information with ISE server using RADIUS Accounting packets. WiFi Analytics Data Flow
WiFi Analytics Data Flow
It is important to remember that RADIUS Accounting packets on a RADIUS AAA flow are sent only after the RADIUS server sends a RADIUS Access-Accept packet as a reply to the endpoint authentication attempt. In order words, WLC shares the endpoint attribute information only after a RADIUS session for that endpoint is established between the RADIUS server (ISE) and Network Access Device (WLC).
These are all the attributes that ISE can make use of for Endpoint Classification and authorization:
- DEVICE_INFO_FIRMWARE_VERSION
- DEVICE_INFO_HW_MODEL
- DEVICE_INFO_MANUFACTURER_MODEL
- DEVICE_INFO_MODEL_NAME
- DEVICE_INFO_MODEL_NUM
- DEVICE_INFO_OS_VERSION
- DEVICE_INFO_VENDOR_TYPE

Note: WLC can send more attributes depending on the endpoint type connecting, but only the listed ones can be used for Authorization Policies creation in ISE.
Once ISE receives the Accounting packet, it can process and consume this analytics data within it, and use it to reassign an endpoint profile/identity group.
The WiFi Endpoint Analytics attributes are listed under the WiFi_Device_Analytics dictionary. Network administrators can include these attributes on the endpoint authorization policies and conditions.
 WiFi Device Analytics Dictionary
WiFi Device Analytics Dictionary
If any changes in the current attribute values that ISE stores for the endpoint take place, ISE then initiates a Change of Authorization (CoA), allowing the endpoint to be evaluated taking in count the updated attributes.
Configure
Configurations on WLC
Step 1. Enable Globally the Device Classification Feature
Navigate to Configuration > Wireless > Wireless Global and mark the Device Classification checkbox.
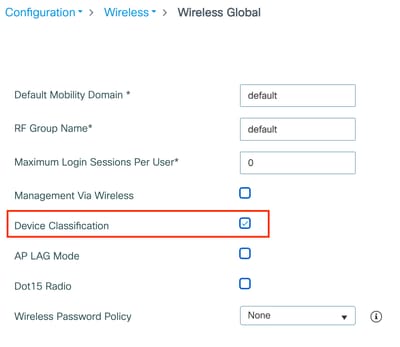 Device Classification Configuration
Device Classification Configuration
Step 2. Enable TLV Caching and RADIUS Profiling
Navigate to Configuration > Tags and Profiles > Policy and select the Policy Profile used by the WLAN where the RADIUS clients are connecting.
 Wireless Policy Selection
Wireless Policy Selection
Click Access Policies and check the RADIUS Profiling, HTTP TLV Caching and DHCP TLV Caching options. Due to action taken in previous step, Global State of Device Classification now shows on Enabled status.  RADIUS Profiling and Caching Configuration
RADIUS Profiling and Caching Configuration
Log in to WLC CLI and enable dot11 TLV Accounting.
vimontes-wlc#configure terminal
vimontes-wlc(config)#wireless profile policy policy-profile-name
vimontes-wlc(config-wireless-policy)#dot11-tlv-accounting

Note: Wireless policy profile must be disabled before using this command. This command is only available on Cisco IOS XE Dublin 17.10.1 version and beyond.
Configurations on ISE
Step 1. Enable Profiling Services in the PSNs in the Deployment
Navigate to Administration > Deployment and click the name of the PSN.
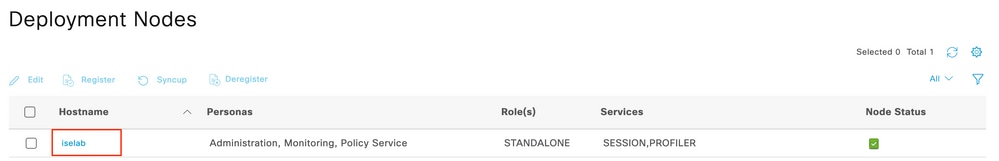 ISE PSN Node Selection
ISE PSN Node Selection
Scroll down to Policy Service section and mark the Enable Profiling Service checkbox. Click the Save button.
 Profiler Services Configuration
Profiler Services Configuration
Step 2. Enable the RADIUS Profiling Probe on ISE PSN
Scroll up to the top of the page and click Profiling Configuration tab. This displays all the profiling probes available to use on ISE. Enable the RADIUS Probe and click Save.
 RADIUS Profiling Probe Configuration
RADIUS Profiling Probe Configuration
Step 3. Set CoA Type and Endpoint Attribute Filter
Navigate to Administration > System > Settings > Profiling. Set CoA Type to Reauth and ensure that Endpoint Attribute Filter checkbox is unchecked.
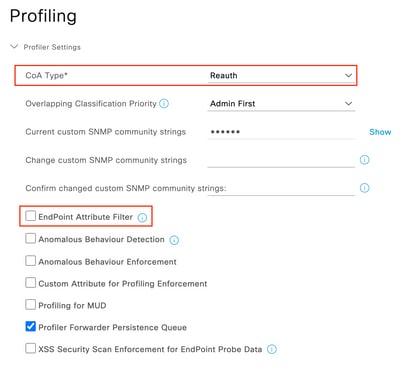 CoA Type and Attribute Filter Configuration
CoA Type and Attribute Filter Configuration
Step 4. Configure Authorization Policies with WiFi Analytics Data Attributes
Navigate to Policy > Policy Sets menu and select the Policy Set used by your wireless network.
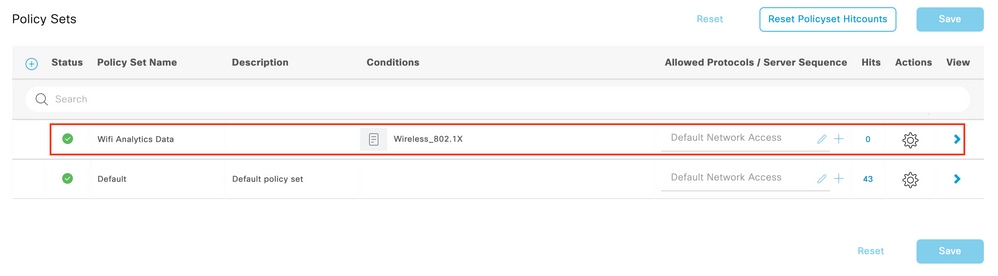 Policy Set Selection
Policy Set Selection
Click Authorization Policies and configure the Authorization Conditions to include the Endpoint Policy and WiFi Device Analytics dictionary attributes. Authorization Policy Configuration
Authorization Policy Configuration
Verify
On ISE GUI, navigate to Operations > RADIUS > Live logs. You can use several fields to filter the entries on this window and locate the testing endpoint records.
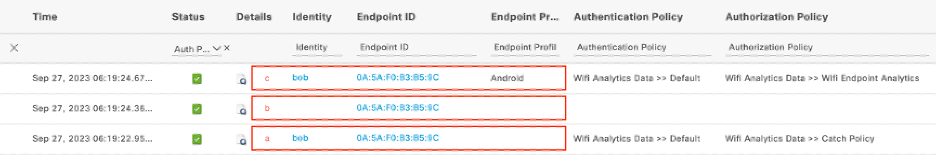 ISE Live Logs for Testing Endpoint
ISE Live Logs for Testing Endpoint
a. Initial endpoint Authentication request reaches ISE. Endpoint profile field is empty since Accounting packet for this session has not reached ISE at this point.
b. CoA is sent from ISE towards the NAD since Accounting packet containing endpoint attributes has now been received.
c. After successfully sending the CoA, endpoint gets reauthenticated. This time you can observe the new assigned endpoint profile, and see that a different Authorization result has been assigned.

Note: CoA packet always has an empty identity field, but endpoint ID is the same as in the first Authentication packet.
Click the icon located in the Details column on the Change of Authorization record.
 Access to CoA Packet Details
Access to CoA Packet Details
The CoA detailed information is displayed in a new browser tab. Scroll down to the Other Attributes section.
CoA source component displays as profiler. CoA Reason displays as Change in endpoint identity group/policy/logical profile which are used in Authorization policies.
 CoA Triggering Component and Reason
CoA Triggering Component and Reason
Navigate to Context Visibility > Endpoints > Authentication tab. On this tab, use the filters to locate the testing endpoint.
Click the endpoint MAC Address to access the endpoint attributes.
 Endpoint on Context Visibility
Endpoint on Context Visibility
This action displays all the information ISE is storing about this endpoint. Click Attributes section and then select Other Attributes.
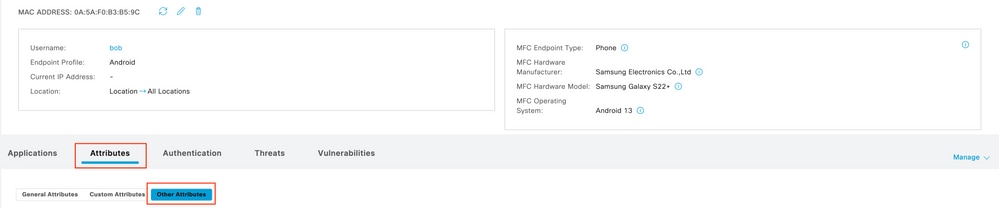 Endpoint Other Attribute Selection on Context Visibility
Endpoint Other Attribute Selection on Context Visibility
Scroll down until you find the WiFi_Device_Analytics dictionary attributes. Locating these attributes on this section means that ISE received them successfully through the Accounting packets and can be used for Endpoint Classification.
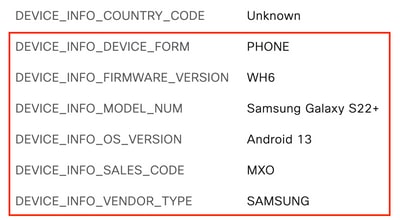 WiFi Analytics Attributes on Context Visibility
WiFi Analytics Attributes on Context Visibility
For your reference, here are examples of Windows 10 and iPhone attributes:
 Example of Windows 10 Endpoint Attributes
Example of Windows 10 Endpoint Attributes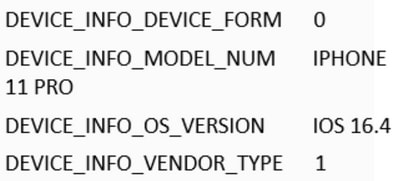 Example of iPhone Endpoint Attributes
Example of iPhone Endpoint Attributes
Troubleshoot
Step 1. Accounting Packets reach ISE
On WLC CLI, ensure that DOT11 TLV accounting, DHCP TLV caching and HTTP TLV caching are enabled on the policy profile configurations.
vimontes-wlc#show running-config | section wireless profile policy policy-profile-name
wireless profile policy policy-profile-name
aaa-override
accounting-list AAA-LIST
dhcp-tlv-caching
dot11-tlv-accounting
http-tlv-caching
radius-profiling
no shutdown
Collect packet captures on either WLC or ISE ends while connecting an endpoint. You can use any well-known packet analysis tool, such as Wireshark, to analyze the collected files.
Filter by RADIUS Accounting packets and by Calling Station ID (testing endpoint MAC Address). For example, this filter can be used:
radius.code == 4 && radius.Calling_Station_Id == "xx-xx-xx-xx-xx-xx"
Once located, expand the Cisco-AVPair fields to locate the WiFi Analytics Data within the Accounting packet.
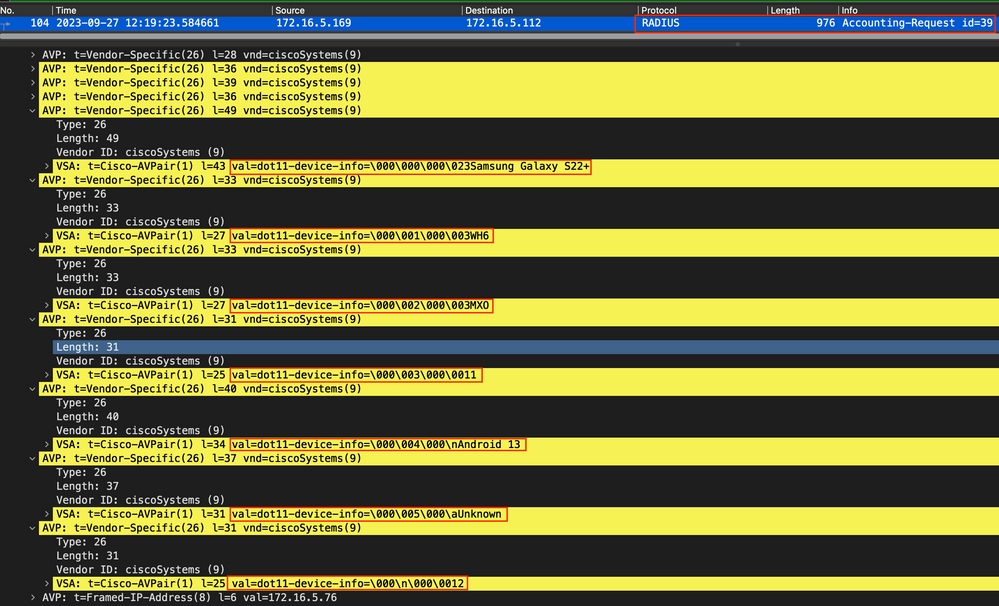 Endpoint TLV Attributes within an Accounting Packet
Endpoint TLV Attributes within an Accounting Packet
Step 2. ISE Parses the Accounting Packet with the Endpoint Attributes
On ISE end, these components can be set to DEBUG level to ensure that RADIUS Accounting packets sent by then WLC reach ISE and are correctly processed.
You can then collect ISE Support Bundle to gather the log files. For more information about how to collect Support Bundle, please refer to the Related Information section.
 Components to Debug for Troubleshoot
Components to Debug for Troubleshoot

Note: Components are enabled to DEBUG level only on the PSN that authenticates the endpoints.
On iseLocalStore.log, Accounting-Start message is logged without the need of enabling any component to DEBUG level. Here, ISE must see the incoming Accounting packet containing the WiFi Analytics attributes.
2023-09-27 18:19:23.600 +00:00 0000035538 3000 NOTICE Radius-Accounting: RADIUS Accounting start request, ConfigVersionId=1493,
Device IP Address=172.16.5.169, UserName=bob, NetworkDeviceName=lab-wlc, User-Name=bob, NAS-IP-Address=172.16.5.169, NAS-Port=260613,
Framed-IP-Address=172.16.5.76, Class=CACS:A90510AC0000005BD7DDDAA7:iselab/484624451/303, Called-Station-ID=00-1e-f6-5c-16-ff,
Calling-Station-ID=0a-5a-f0-b3-b5-9c, NAS-Identifier=vimontes-wlc, Acct-Status-Type=Start, Acct-Delay-Time=0, Acct-Session-Id=00000018,
Acct-Authentic=Remote, Event-Timestamp=1695838756, NAS-Port-Type=Wireless - IEEE 802.11, cisco-av-pair=dc-profile-name=Samsung Galaxy S22+,
cisco-av-pair=dc-device-name=Victor-s-S22, cisco-av-pair=dc-device-class-tag=Samsung Galaxy S22+, cisco-av-pair=dc-certainty-metric=40,
cisco-av-pair=64:63:2d:6f:70:61:71:75:65:3d:01:00:00:00:00:00:00:00:00:00:00:00, cisco-av-pair=dc-protocol-map=1025, cisco-av-pair=dhcp-option=host-name=Victor-s-S22,
cisco-av-pair=dhcp-option=dhcp-class-identifier=android-dhcp-13, cisco-av-pair=dhcp-option=dhcp-parameter-request-list=1\, 3\, 6\, 15\, 26\, 28\, 51\, 58\, 59\, 43\, 114\, 108,
cisco-av-pair=dot11-device-info=DEVICE_INFO_MODEL_NUM=Samsung Galaxy S22+, cisco-av-pair=dot11-device-info=DEVICE_INFO_FIRMWARE_VERSION=WH6,
cisco-av-pair=dot11-device-info=DEVICE_INFO_SALES_CODE=MXO, cisco-av-pair=dot11-device-info=DEVICE_INFO_DEVICE_FORM=1,
cisco-av-pair=dot11-device-info=DEVICE_INFO_OS_VERSION=Android 13, cisco-av-pair=dot11-device-info=DEVICE_INFO_COUNTRY_CODE=Unknown,
cisco-av-pair=dot11-device-info=DEVICE_INFO_VENDOR_TYPE=2, cisco-av-pair=audit-session-id=A90510AC0000005BD7DDDAA7, cisco-av-pair=vlan-id=2606, cisco-av-pair=method=dot1x,
cisco-av-pair=cisco-wlan-ssid=VIcSSID, cisco-av-pair=wlan-profile-name=ISE-AAA, Airespace-Wlan-Id=1, AcsSessionID=iselab/484624451/304, SelectedAccessService=Default Network Access,
RequestLatency=15, Step=11004, Step=11017, Step=15049, Step=15008, Step=22083, Step=11005, NetworkDeviceGroups=IPSEC#Is IPSEC Device#No, NetworkDeviceGroups=Location#All Locations,
NetworkDeviceGroups=Device Type#All Device Types, CPMSessionID=A90510AC0000005BD7DDDAA7, TotalAuthenLatency=15, ClientLatency=0, Network Device Profile=Cisco, Location=Location#All Locations,
Device Type=Device Type#All Device Types, IPSEC=IPSEC#Is IPSEC Device#No,
On prrt-server.log, ISE parses the received accounting packet syslog message including the WiFi Analytics attributes. Use the CallingStationID and CPMSessionID fields to ensure that the correct session and endpoint are tracked.
Radius,2023-09-27 18:19:23,586,DEBUG,0x7f50a2b67700,cntx=0000192474,sesn=iselab/484624451/304,
CPMSessionID=A90510AC0000005BD7DDDAA7,CallingStationID=0a-5a-f0-b3-b5-9c,FramedIPAddress=172.16.5.76,RADIUS PACKET::
Code=4(AccountingRequest) Identifier=39 Length=934 [1] User-Name - value: [bob] [4] NAS-IP-Address - value: [172.16.5.169] [5] NAS-Port - value: [260613] [8] Framed-IP-Address - value: [172.16.5.76] [25] Class - value: [****] [30] Called-Station-ID - value: [00-1e-f6-5c-16-ff] [31] Calling-Station-ID - value: [0a-5a-f0-b3-b5-9c] [32] NAS-Identifier - value: [vimontes-wlc] [40] Acct-Status-Type - value: [Start] [41] Acct-Delay-Time - value: [0] [44] Acct-Session-Id - value: [00000018] [45] Acct-Authentic - value: [Remote] [55] Event-Timestamp - value: [1695838756] [61] NAS-Port-Type - value: [Wireless - IEEE 802.11] [26] cisco-av-pair - value: [dc-profile-name=Samsung Galaxy S22+] [26] cisco-av-pair - value: [dc-device-name=Victor-s-S22] [26] cisco-av-pair - value: [dc-device-class-tag=Samsung Galaxy S22+] [26] cisco-av-pair - value: [dc-certainty-metric=40] [26] cisco-av-pair - value: [dc-opaque=<01><00><00><00><00><00><00><00><00><00><00><00>] [26] cisco-av-pair - value: [dc-protocol-map=1025] [26] cisco-av-pair - value: [dhcp-option=<00><0c><00><0c>Victor-s-S22] [26] cisco-av-pair - value: [dhcp-option=<00><<00><0f>android-dhcp-13] [26] cisco-av-pair - value: [dhcp-option=<00>7<00><0c><01><03><06><0f><1a><1c>3:;+rl] [26] cisco-av-pair - value: [dot11-device-info=<00><00><00><13>Samsung Galaxy S22+] [26] cisco-av-pair - value: [dot11-device-info=<00><01><00><03>WH6] [26] cisco-av-pair - value: [dot11-device-info=<00><02><00><03>MXO] [26] cisco-av-pair - value: [dot11-device-info=<00><03><00><01>1] [26] cisco-av-pair - value: [dot11-device-info=<00><04><00> Android 13] [26] cisco-av-pair - value: [dot11-device-info=<00><05><00><07>Unknown] [26] cisco-av-pair - value: [dot11-device-info=<00> <00><01>2] [26] cisco-av-pair - value: [audit-session-id=A90510AC0000005BD7DDDAA7] [26] cisco-av-pair - value: [vlan-id=2606] [26] cisco-av-pair - value: [method=dot1x] [26] cisco-av-pair - value: [cisco-wlan-ssid=VIcSSID] [26] cisco-av-pair - value: [wlan-profile-name=ISE-AAA] [26] Airespace-Wlan-Id - value: [<00><00><00><01>] ,RADIUSHandler.cpp:2453
Step 3. Endpoint Attributes are Updated and Endpoint is Classified
This syslog message is then shared with the profiler component. Profiler.log receives the parsed syslog message and extracts the endpoint attributes.
2023-09-27 18:19:23,601 DEBUG [SyslogListenerThread][[]] cisco.profiler.probes.radius.SyslogMonitor -:::::- Radius Packet Received 1266 2023-09-27 18:19:23,601 DEBUG [SyslogListenerThread][[]] cisco.profiler.probes.radius.SyslogDefragmenter -:::::- parseHeader inBuffer=<181>Sep 27 18:19:23 iselab
CISE_RADIUS_Accounting 0000000297 3 0 2023-09-27 18:19:23.600 +00:00 0000035538 3000 NOTICE Radius-Accounting: RADIUS Accounting start request, ConfigVersionId=1493, Device IP Address=172.16.5.169,
UserName=bob, NetworkDeviceName=lab-wlc, User-Name=bob, NAS-IP-Address=172.16.5.169, NAS-Port=260613, Framed-IP-Address=172.16.5.76, Class=CACS:A90510AC0000005BD7DDDAA7:iselab/484624451/303,
Called-Station-ID=00-1e-f6-5c-16-ff, Calling-Station-ID=0a-5a-f0-b3-b5-9c, NAS-Identifier=vimontes-wlc, Acct-Status-Type=Start, Acct-Delay-Time=0, Acct-Session-Id=00000018, Acct-Authentic=Remote,
Event-Timestamp=1695838756, NAS-Port-Type=Wireless - IEEE 802.11, cisco-av-pair=dc-profile-name=Samsung Galaxy S22+, cisco-av-pair=dc-device-name=Victor-s-S22,
cisco-av-pair=dc-device-class-tag=Samsung Galaxy S22+, cisco-av-pair=dc-certainty-metric=40,
cisco-av-pair=64:63:2d:6f:70:61:71:75:65:3d:01:00:00:00:00:00:00:00:00:00:00:00, cisco-av-pair=dc-protocol-map=1025, 2023-09-27 18:19:23,601 DEBUG [SyslogListenerThread][[]] cisco.profiler.probes.radius.SyslogMonitor -:::::- Radius Packet Received 1267 2023-09-27 18:19:23,601 DEBUG [SyslogListenerThread][[]] cisco.profiler.probes.radius.SyslogDefragmenter -:::::- parseHeader inBuffer=<181>Sep 27 18:19:23 iselab CISE_RADIUS_Accounting 0000000297 3 1
cisco-av-pair=dhcp-option=host-name=Victor-s-S22, cisco-av-pair=dhcp-option=dhcp-class-identifier=android-dhcp-13, cisco-av-pair=dhcp-option=dhcp-parameter-request-list=1\, 3\, 6\, 15\, 26\, 28\, 51\, 58\, 59\, 43\, 114\, 108,
cisco-av-pair=dot11-device-info=DEVICE_INFO_MODEL_NUM=Samsung Galaxy S22+, cisco-av-pair=dot11-device-info=DEVICE_INFO_FIRMWARE_VERSION=WH6, cisco-av-pair=dot11-device-info=DEVICE_INFO_SALES_CODE=MXO,
cisco-av-pair=dot11-device-info=DEVICE_INFO_DEVICE_FORM=1, cisco-av-pair=dot11-device-info=DEVICE_INFO_OS_VERSION=Android 13, cisco-av-pair=dot11-device-info=DEVICE_INFO_COUNTRY_CODE=Unknown,
cisco-av-pair=dot11-device-info=DEVICE_INFO_VENDOR_TYPE=2, cisco-av-pair=audit-session-id=A90510AC0000005BD7DDDAA7, cisco-av-pair=vlan-id=2606, cisco-av-pair=method=dot1x, cisco-av-pair=cisco-wlan-ssid=VIcSSID,
cisco-av-pair=wlan-profile-name=ISE-AAA, Airespace-Wlan-Id=1, AcsSessionID=iselab/484624451/304,
Endpoint attribute information is updated.
2023-09-27 18:19:23,602 DEBUG [RADIUSParser-1-thread-2][[]] cisco.profiler.probes.radius.RadiusParser -:A90510AC0000005BD7DDDAA7::::- Device Analytics data 1: DEVICE_INFO_FIRMWARE_VERSION=[WH6] 2023-09-27 18:19:23,602 DEBUG [RADIUSParser-1-thread-2][[]] cisco.profiler.probes.radius.RadiusParser -:A90510AC0000005BD7DDDAA7::::- Device Analytics data 1: DEVICE_INFO_SALES_CODE=[MXO] 2023-09-27 18:19:23,602 DEBUG [RADIUSParser-1-thread-2][[]] cisco.profiler.probes.radius.RadiusParser -:A90510AC0000005BD7DDDAA7::::- Device Analytics data 1: DEVICE_INFO_DEVICE_FORM=[1] 2023-09-27 18:19:23,602 DEBUG [RADIUSParser-1-thread-2][[]] cisco.profiler.probes.radius.RadiusParser -:A90510AC0000005BD7DDDAA7::::- Device Analytics data 1: DEVICE_INFO_OS_VERSION=[Android 13] 2023-09-27 18:19:23,602 DEBUG [RADIUSParser-1-thread-2][[]] cisco.profiler.probes.radius.RadiusParser -:A90510AC0000005BD7DDDAA7::::- Device Analytics data 1: DEVICE_INFO_COUNTRY_CODE=[Unknown] 2023-09-27 18:19:23,602 DEBUG [RADIUSParser-1-thread-2][[]] cisco.profiler.probes.radius.RadiusParser -:A90510AC0000005BD7DDDAA7::::- Device Analytics data 1: DEVICE_INFO_VENDOR_TYPE=[2]
2023-09-27 18:19:23,602 DEBUG [RADIUSParser-1-thread-2][[]] cisco.profiler.probes.radius.RadiusParser -:A90510AC0000005BD7DDDAA7::::- Endpoint: EndPoint[id=,name=] MAC: 0A:5A:F0:B3:B5:9C Attribute:AAA-Server value:iselab Attribute:Acct-Authentic value:Remote Attribute:Acct-Delay-Time value:0 Attribute:Acct-Session-Id value:00000018 Attribute:Acct-Status-Type value:Start Attribute:AcsSessionID value:iselab/484624451/304 Attribute:Airespace-Wlan-Id value:1 Attribute:BYODRegistration value:Unknown Attribute:CPMSessionID value:A90510AC0000005BD7DDDAA7 Attribute:Called-Station-ID value:00-1e-f6-5c-16-ff Attribute:Calling-Station-ID value:0a-5a-f0-b3-b5-9c Attribute:Class value:CACS:A90510AC0000005BD7DDDAA7:iselab/484624451/303 Attribute:ClientLatency value:0 Attribute:DEVICE_INFO_COUNTRY_CODE value:Unknown Attribute:DEVICE_INFO_DEVICE_FORM value:PHONE Attribute:DEVICE_INFO_FIRMWARE_VERSION value:WH6 Attribute:DEVICE_INFO_MODEL_NUM value:Samsung Galaxy S22+ Attribute:DEVICE_INFO_OS_VERSION value:Android 13 Attribute:DEVICE_INFO_SALES_CODE value:MXO Attribute:DEVICE_INFO_VENDOR_TYPE value:SAMSUNG Attribute:Device IP Address value:172.16.5.169 Attribute:Device Type value:Device Type#All Device Types Attribute:DeviceRegistrationStatus value:NotRegistered Attribute:EndPointPolicy value:Unknown Attribute:EndPointPolicyID value: Attribute:EndPointSource value:RADIUS Probe Attribute:Event-Timestamp value:1695838756 Attribute:Framed-IP-Address value:172.16.5.76 Attribute:IPSEC value:IPSEC#Is IPSEC Device#No Attribute:Location value:Location#All Locations Attribute:MACAddress value:0A:5A:F0:B3:B5:9C Attribute:MatchedPolicy value:Unknown Attribute:MatchedPolicyID value: Attribute:MessageCode value:3000 Attribute:NAS-IP-Address value:172.16.5.169 Attribute:NAS-Identifier value:vimontes-wlc Attribute:NAS-Port value:260613 Attribute:NAS-Port-Type value:Wireless - IEEE 802.11 Attribute:Network Device Profile value:Cisco Attribute:NetworkDeviceGroups value:IPSEC#Is IPSEC Device#No, Location#All Locations, Device Type#All Device Types Attribute:NetworkDeviceName value:lab-wlc Attribute:NmapSubnetScanID value:0 Attribute:OUI value:UNKNOWN Attribute:PolicyVersion value:0 Attribute:PortalUser value: Attribute:PostureApplicable value:Yes Attribute:RequestLatency value:15 Attribute:StaticAssignment value:false Attribute:StaticGroupAssignment value:false Attribute:Total Certainty Factor value:0 Attribute:TotalAuthenLatency value:15 Attribute:User-Name value:bob Attribute:cisco-av-pair value:dc-profile-name=Samsung Galaxy S22+, dc-device-name=Victor-s-S22, dc-device-class-tag=Samsung Galaxy S22+, dc-certainty-metric=40, 64:63:2d:6f:70:61:71:75:65:3d:01:00:00:00:00:00:00:00:00:00:00:00, dc-protocol-map=1025, dhcp-option=host-name=Victor-s-S22, dhcp-option=dhcp-class-identifier=android-dhcp-13, dhcp-option=dhcp-parameter-request-list=1\, 3\, 6\, 15\, 26\, 28\, 51\, 58\, 59\, 43\, 114\, 108, dot11-device-info=DEVICE_INFO_MODEL_NUM=Samsung Galaxy S22+, dot11-device-info=DEVICE_INFO_FIRMWARE_VERSION=WH6, dot11-device-info=DEVICE_INFO_SALES_CODE=MXO, dot11-device-info=DEVICE_INFO_DEVICE_FORM=1, dot11-device-info=DEVICE_INFO_OS_VERSION=Android 13, dot11-device-info=DEVICE_INFO_COUNTRY_CODE=Unknown, dot11-device-info=DEVICE_INFO_VENDOR_TYPE=2, audit-session-id=A90510AC0000005BD7DDDAA7, vlan-id=2606, method=dot1x, cisco-wlan-ssid=VIcSSID, wlan-profile-name=ISE-AAA Attribute:dhcp-class-identifier value:android-dhcp-13 Attribute:dhcp-parameter-request-list value:1, 3, 6, 15, 26, 28, 51, 58, 59, 43, 114, 108 Attribute:host-name value:Victor-s-S22 Attribute:ip value:172.16.5.76 Attribute:SkipProfiling value:false
The attribute update triggers a new endpoint profiling event. Profiling policies are evaluated again, and a new profile is assigned.
2023-09-27 18:19:24,098 DEBUG [pool-533-thread-35][[]] cisco.profiler.infrastructure.profiling.ProfilerManager -:A90510AC0000005BD7DDDAA7::62cc7a10-5d62-11ee-bf1f-b6bb1580ab0d:Profiling:- Policy Android matched 0A:5A:F0:B3:B5:9C (certainty 30) 2023-09-27 18:19:24,098 DEBUG [pool-533-thread-35][[]] cisco.profiler.infrastructure.profiling.ProfilerManager -:A90510AC0000005BD7DDDAA7::62cc7a10-5d62-11ee-bf1f-b6bb1580ab0d:Profiling:- EndPoint is profiled by Admin First: ADMINFIRST 2023-09-27 18:19:24,098 DEBUG [pool-533-thread-35][[]] cisco.profiler.infrastructure.profiling.ProfilerManager -:A90510AC0000005BD7DDDAA7::62cc7a10-5d62-11ee-bf1f-b6bb1580ab0d:Profiling:- Policy Android matched 0A:5A:F0:B3:B5:9C (certainty 30)com.cisco.profiler.infrastructure.profiling.ProfilerManager$MatchingPolicyInternal@14ec7800
Step 4. CoA and Reauthentication
ISE must send a CoA for the endpoint session as a change in the WiFi Device Analytics attributes took place.
2023-09-27 18:19:24,103 DEBUG [pool-533-thread-35][[]] cisco.profiler.infrastructure.profiling.ProfilerManager -:A90510AC0000005BD7DDDAA7::62cc7a10-5d62-11ee-bf1f-b6bb1580ab0d:Profiling:- Endpoint 0A:5A:F0:B3:B5:9C IdentityGroup / Logical Profile Changed/ WiFi device analytics attribute changed. Issuing a Conditional CoA
2023-09-27 18:19:24,103 DEBUG [pool-533-thread-35][[]] cisco.profiler.infrastructure.profiling.ProfilerManager -:A90510AC0000005BD7DDDAA7::62cc7a10-5d62-11ee-bf1f-b6bb1580ab0d:Profiling:- ConditionalCoAEvent with Endpoint Details : EndPoint[id=62caa550-5d62-11ee-bf1f-b6bb1580ab0d,name=]
MAC: 0A:5A:F0:B3:B5:9C
Attribute:AAA-Server value:iselab
Attribute:Airespace-Wlan-Id value:1
Attribute:AllowedProtocolMatchedRule value:Default
Attribute:AuthenticationIdentityStore value:Internal Users
Attribute:AuthenticationMethod value:MSCHAPV2
Attribute:AuthenticationStatus value:AuthenticationPassed
Attribute:AuthorizationPolicyMatchedRule value:Catch Policy
Attribute:BYODRegistration value:Unknown
Attribute:CLASSIFICATION_FLOW value:none
Attribute:CacheUpdateTime value:1695838764086
Attribute:Called-Station-ID value:00-1e-f6-5c-16-ff
Attribute:Calling-Station-ID value:0a-5a-f0-b3-b5-9c
Attribute:ClientLatency value:0
Attribute:DEVICE_INFO_COUNTRY_CODE value:Unknown
Attribute:DEVICE_INFO_DEVICE_FORM value:PHONE
Attribute:DEVICE_INFO_FIRMWARE_VERSION value:WH6
Attribute:DEVICE_INFO_MODEL_NUM value:Samsung Galaxy S22+
Attribute:DEVICE_INFO_OS_VERSION value:Android 13
Attribute:DEVICE_INFO_SALES_CODE value:MXO
Attribute:DEVICE_INFO_VENDOR_TYPE value:SAMSUNG
Attribute:DTLSSupport value:Unknown
Attribute:DestinationIPAddress value:172.16.5.112
Attribute:DestinationPort value:1812<
Attribute:Device IP Address value:172.16.5.169
Attribute:Device Type value:Device Type#All Device Types
Attribute:DeviceRegistrationStatus value:NotRegistered
Attribute:DoReplicate value:false
Attribute:EnableFlag value:Enabled
Attribute:EndPointMACAddress value:0A-5A-F0-B3-B5-9C
Attribute:EndPointPolicy value:Android
Attribute:EndPointPolicyID value:ffafa000-8bff-11e6-996c-525400b48521
Attribute:EndPointProfilerServer value:iselab.vimontes.cisco.com
Attribute:EndPointSource value:RADIUS Probe
Attribute:EndPointVersion value:4
Attribute:FailureReason value:-
Attribute:FirstCollection value:1695838763963
Attribute:Framed-IP-Address value:172.16.5.76
Attribute:IPSEC value:IPSEC#Is IPSEC Device#No
Attribute:IdentityGroup value:Android
Attribute:IdentityGroupID value:ffa36b00-8bff-11e6-996c-525400b48521
Attribute:IdentityPolicyMatchedRule value:Default
Attribute:IdentitySelectionMatchedRule value:Default
Attribute:IsThirdPartyDeviceFlow value:false
Attribute:LastActivity value:1695838764083
Attribute:LastNmapScanTime value:0
Attribute:Location value:Location#All Locations
Attribute:LogicalProfile value:
Attribute:MACAddress value:0A:5A:F0:B3:B5:9C
Attribute:MatchedPolicy value:Android
Attribute:MatchedPolicyID value:ffafa000-8bff-11e6-996c-525400b48521
Attribute:MessageCode value:3000
Attribute:NAS-IP-Address value:172.16.5.169
Attribute:NAS-Identifier value:vimontes-wlc
Attribute:NAS-Port value:260613
Attribute:NAS-Port-Type value:Wireless - IEEE 802.11
Attribute:Network Device Profile value:Cisco
Attribute:NetworkDeviceGroups value:IPSEC#Is IPSEC Device#No, Location#All Locations, Device Type#All Device Types
Attribute:NetworkDeviceName value:lab-wlc
Attribute:NetworkDeviceProfileId value:b0699505-3150-4215-a80e-6753d45bf56c
Attribute:NetworkDeviceProfileName value:Cisco
Attribute:NmapScanCount value:0
Attribute:NmapSubnetScanID value:0
Attribute:OUI value:UNKNOWN
Attribute:PolicyVersion value:0
Attribute:PortalUser value:
Attribute:PostureApplicable value:Yes
Attribute:PostureAssessmentStatus value:NotApplicable
Attribute:PreviousMACAddress value:0A:5A:F0:B3:B5:9C
Attribute:RadiusFlowType value:Wireless802_1x
Attribute:Response value:{Class=CACS:A90510AC0000005BD7DDDAA7:iselab/484624451/303; EAP-Key-Name=19:12:31:7e:8a:2e:d7:9f:3b:00:3e:ab:bd:27:22:2a:30:45:b8:7a:1b:ab:b6:1a:b1:e6:21:ee:bd:b1:2c:b8:f5:a8:c9:27:27:c1:0e:95:fa:a0:b6:dc:1f:a4:e6:98:2c:89:5e:b1:5c:11:56:ea:d9:93:a8:92:b0:47:57:3a:6e; MS-MPPE-Send-Key=****; MS-MPPE-Recv-Key=****; LicenseTypes=1; }
Attribute:SSID value:3c-41-0e-31-77-80:VIcSSID
Attribute:SelectedAccessService value:Default Network Access
Attribute:SelectedAuthenticationIdentityStores value:Internal Users, All_AD_Join_Points, Guest Users
Attribute:SelectedAuthorizationProfiles value:PermitAccess
Attribute:Service-Type value:Framed
Attribute:StaticAssignment value:false
Attribute:StaticGroupAssignment value:false
Attribute:StepData value:4= Normalised Radius.RadiusFlowType, 71=All_User_ID_Stores, 72=Internal Users, 95= WiFi_Device_Analytics.DEVICE_INFO_MODEL_NUM, 96= WiFi_Device_Analytics.DEVICE_INFO_MODEL_NUM, 97= WiFi_Device_Analytics.DEVICE_INFO_MODEL_NUM, 98= WiFi_Device_Analytics.DEVICE_INFO_MODEL_NUM, 99= EndPoints.EndPointPolicy, 100= EndPoints.EndPointPolicy, 101= EndPoints.EndPointPolicy
Attribute:TLSCipher value:ECDHE-RSA-AES256-GCM-SHA384
Attribute:TLSVersion value:TLSv1.2
Attribute:TimeToProfile value:139
Attribute:Total Certainty Factor value:30
Attribute:TotalAuthenLatency value:15
Attribute:UpdateTime value:0
Attribute:User-Name value:bob
Attribute:UserType value:User
Attribute:allowEasyWiredSession value:false
Attribute:dhcp-class-identifier value:android-dhcp-13
Attribute:dhcp-parameter-request-list value:1, 3, 6, 15, 26, 28, 51, 58, 59, 43, 114, 108
Attribute:epid value:epid:293810839814635520
Attribute:host-name value:Victor-s-S22
Attribute:ip value:172.16.5.76
Attribute:undefined-186 value:00:0f:ac:04
Attribute:undefined-187 value:00:0f:ac:04
Attribute:undefined-188 value:00:0f:ac:01
Attribute:undefined-189 value:00:0f:ac:06
Attribute:SkipProfiling value:false
Packet capture helps to ensure that ISE sends out the CoA to the WLC. It also shows that a new Access-Request packet is received after processing the CoA.
 Radius CoA Packet after Endpoint Profiling
Radius CoA Packet after Endpoint Profiling
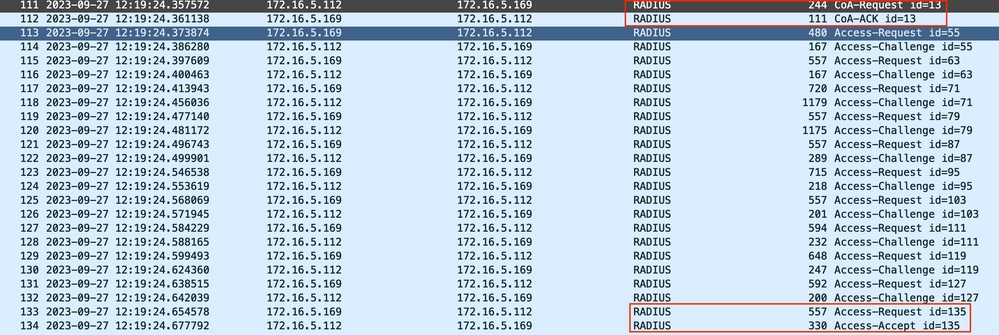 Radius CoA and New Access-Request after Endpoint Profiling
Radius CoA and New Access-Request after Endpoint Profiling
Related Information
Revision History
| Revision | Publish Date | Comments |
|---|---|---|
1.0 |
05-Oct-2023 |
Initial Release |
Contributed by Cisco Engineers
- Victor Montes AngelesSecurity Escalation Engineer
Contact Cisco
- Open a Support Case

- (Requires a Cisco Service Contract)
 Feedback
Feedback