Introduction
This document describes the behavioral changes introduced by the new signatures after updating Cisco Intrusion Prevention System (IPS) to a new signature package.
Prerequisites
Requirements
Cisco recommends that you have knowledge of these topics:
- Signature Update feature on IPS
Components Used
The information in this document is based on these software and hardware versions:
- IPS 4XXX series sensors
- ASA 5585-X IPS SSP series
- ASA 5500-X IPS SSP series
- ASA 5500 IPS SSM series
Version 7.1(10)E4
Version 7.3(4)E4
Refer to Cisco Technical Tips Conventions for more information on document conventions.
Problem
There could be multiple issues such as packet drops and connectivity issues with certain applications after performing a signature update on the IPS.To troubleshoot such issues it would be very helpful if you can understand the changes in active signature set post the signature update.
Solution
Step 1.
The first thing that you need to check is the upgrade history for the signature. This tells the previous signature pack that was running on IPS and the current version of signature pack.
This can be found out from the output of the command show version or from the upgrade history section of the show tech. Snippet from the same is mentioned here:
Upgrade History
* IPS-sig-S733-req-E4 19:59:50 UTC Fri Aug 09 2015
IPS-sig-S734-req-E4.pkg 19:59:49 UTC Tue Aug 13 2015
Now you can make out that the previous signature pack that was running on the IPS was s733 and has been upgraded to s734 which is current signature pack.
Step 2.
The second step is to understand the changes that have been made and that can be checked through the IME/IDM.
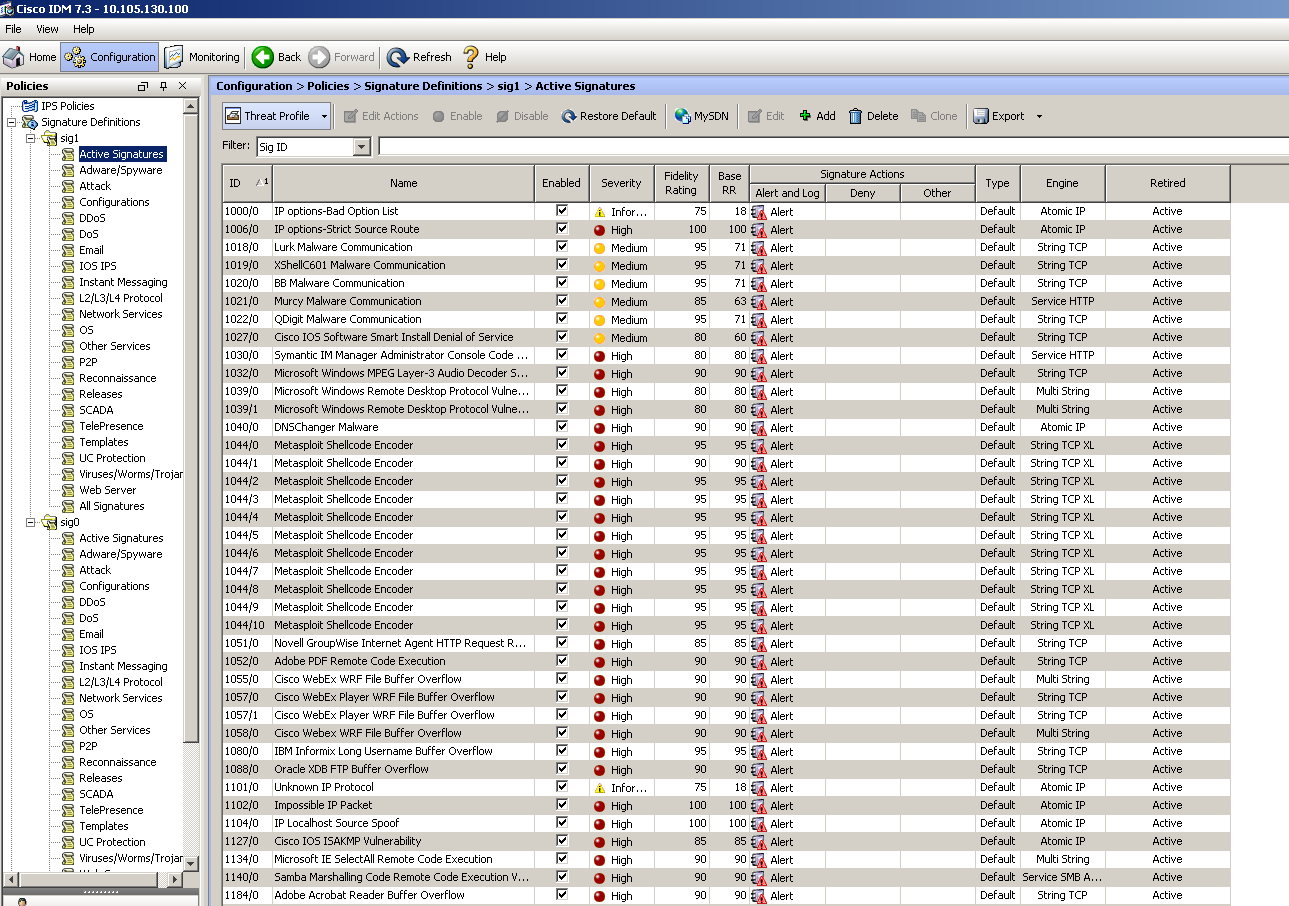
1. The active signature tab on the IME/IDM is shown in this image.
Navigate to Configuration > Policies > Signature Definitions > Sig1 > Active Signatures.
2. This image shows how to select a specific signature release.
Navigate to Configuration > Policies > Signature Definitions > Sig1 > Releases.
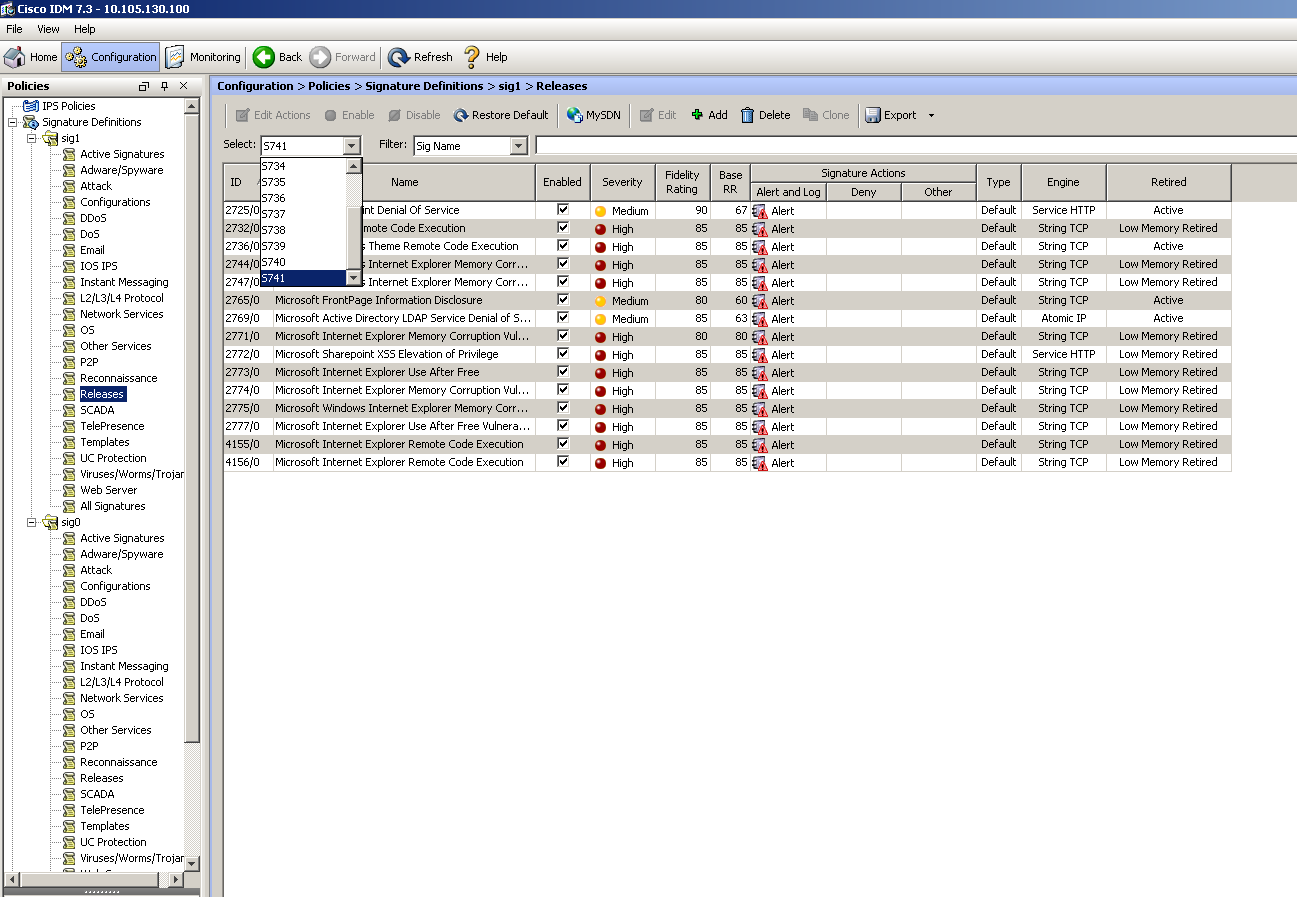
Further using the filter option you have obtained all the signatures from a particular release, you can filter them based on engine, fidelity, severity etc.
By doing this you must be able to narrow down on the changes in signature release that can be a potential cause for the issue based on which you align your troubleshooting.
